Lab Report: Cracking WPA2-PSK Passphrase and Wireless Security
VerifiedAdded on 2020/04/01
|9
|1108
|143
Practical Assignment
AI Summary
This practical assignment explores the process of cracking WPA2-PSK passphrases, a common wireless network security protocol. The assignment details the setup, tools, and steps involved in capturing and analyzing network traffic to extract the passphrase. The student utilizes Kali Linux, a penetration testing distribution, along with tools like airodump-ng and aircrack-ng, to perform the attack. The report covers the configuration of a wireless access point (AP), setting the wireless adapter in monitor mode, capturing the WPA4-way handshake, and finally, cracking the password using brute-force techniques. The assignment also includes screenshots of the process and answers to review questions, discussing methods to overcome vulnerabilities and improve network security. The conclusion summarizes the practical application of the learned techniques, emphasizing the importance of understanding wireless security for ethical hacking and network administration. The document is a comprehensive guide to understanding and demonstrating WPA2-PSK cracking, and it is designed to enhance the understanding of network security principles.

Table of Contents
1. Introduction................................................................................................................................2
2. Lab 2-Worksheet.........................................................................................................................2
2.1 Objective...................................................................................................................................3
2.2 Configuration............................................................................................................................3
2.3 How WPA-PSK passphrase is cracked......................................................................................4
2.4 Screenshots................................................................................................................................5
2.5 Results.......................................................................................................................................8
2.6 Activity review questions...........................................................................................................8
3. Conclusion...................................................................................................................................9
References...........................................................................................................................................9
1
1. Introduction................................................................................................................................2
2. Lab 2-Worksheet.........................................................................................................................2
2.1 Objective...................................................................................................................................3
2.2 Configuration............................................................................................................................3
2.3 How WPA-PSK passphrase is cracked......................................................................................4
2.4 Screenshots................................................................................................................................5
2.5 Results.......................................................................................................................................8
2.6 Activity review questions...........................................................................................................8
3. Conclusion...................................................................................................................................9
References...........................................................................................................................................9
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1. Introduction
The WPA2-PSK will be studied along with the WPA4-way handshake. The brute force
password crack will be used to extract the passphrase. The wireless network traffic will be
collected to find out the WEP key. For doing this action, some software and hardware tools are
required. By using the SSID, the AP WEP configuration will be performed. AP is an access
point. To connect wired LAN into wireless device, AP is used as a hub. It provides secure
connection. The MAC addresses of wireless network will be monitored. For providing the gain
address to the AP, MAC addresses will be predicted. MAC stands for Media Access Control. It
is a unique identifier. It is used for making the communication at the data link layer. The
Microsoft windows 2012 server will be installed. It will perform the authentication in active
directory domain. The client and server configuration of will be done in windows 2012 server
using some software and hardware. To carry out the MAC, address spoofing, WEP and WPA2
encryption, implementation is carried out in Kali Linux. Kali Linux is chosen to carry out the
process since it is easy for handling the encryption and recording, capturing and storing the
traffic. Kali Linux is one of the Linux platform derived based on Debian. Kali Linux is used for
penetration testing. Kali Linux has its host applications like back track, wire shark. Kali Linux
can be easily installed via bootable CD OR DVD. Kali Linux is mostly used for carrying out
forensic activities. Kali Linux has many tools. Some of the tools are wire shark, kismet, Maitego,
Ettercap and many. Kali Linux is also used for Ethical hacking techniques.
2. Lab 2-Worksheet
WPA2-PSK stands for Wi-Fi protected Access 2 -pre shared key. It is also known as WPA2
personal. IT is one type of network security. It is designed instead of WEP. It is designed only
for the home users. It does not need the enterprise authentication server. It is used for securing
the network. Using TKIP with the network SSID, one could perform the passphrase. It is also
used to create the similar encryption keys for each wireless client. The WEP also supported for
passphrase. The encryption and authentication is components of WPA2.These two components
are needed to secure the WLAN. The authentication component has two modes: personal and
enterprise.
Steps for cracking the WPA2-PSK passwords:
2
The WPA2-PSK will be studied along with the WPA4-way handshake. The brute force
password crack will be used to extract the passphrase. The wireless network traffic will be
collected to find out the WEP key. For doing this action, some software and hardware tools are
required. By using the SSID, the AP WEP configuration will be performed. AP is an access
point. To connect wired LAN into wireless device, AP is used as a hub. It provides secure
connection. The MAC addresses of wireless network will be monitored. For providing the gain
address to the AP, MAC addresses will be predicted. MAC stands for Media Access Control. It
is a unique identifier. It is used for making the communication at the data link layer. The
Microsoft windows 2012 server will be installed. It will perform the authentication in active
directory domain. The client and server configuration of will be done in windows 2012 server
using some software and hardware. To carry out the MAC, address spoofing, WEP and WPA2
encryption, implementation is carried out in Kali Linux. Kali Linux is chosen to carry out the
process since it is easy for handling the encryption and recording, capturing and storing the
traffic. Kali Linux is one of the Linux platform derived based on Debian. Kali Linux is used for
penetration testing. Kali Linux has its host applications like back track, wire shark. Kali Linux
can be easily installed via bootable CD OR DVD. Kali Linux is mostly used for carrying out
forensic activities. Kali Linux has many tools. Some of the tools are wire shark, kismet, Maitego,
Ettercap and many. Kali Linux is also used for Ethical hacking techniques.
2. Lab 2-Worksheet
WPA2-PSK stands for Wi-Fi protected Access 2 -pre shared key. It is also known as WPA2
personal. IT is one type of network security. It is designed instead of WEP. It is designed only
for the home users. It does not need the enterprise authentication server. It is used for securing
the network. Using TKIP with the network SSID, one could perform the passphrase. It is also
used to create the similar encryption keys for each wireless client. The WEP also supported for
passphrase. The encryption and authentication is components of WPA2.These two components
are needed to secure the WLAN. The authentication component has two modes: personal and
enterprise.
Steps for cracking the WPA2-PSK passwords:
2

1. Set the WIFI adapter in monitor mode.
2. Capture traffic
3. Focus one AP in one channel.
4. Aire play.
5. Capture the handshake.
2.1 Objective
To do the activity - Cracking WPA2-PSK, the below mentioned hardware and software
tools are required.
Software tool- Kali Linux virtual machine.
Hardware tools
2-installed virtual machine in windows 7.
2-wireless adapters
1-access point.
2.2 Configuration
Initially the Access point (AP) is placed.
SSID is 6EWSx for AP.
The WPA2-PSK is configured with AP.
Now one could note down the password (passphrase).
With the help of WPA2-PSK passphrase, the wireless client pc is connected to the
AP for configuration.
Kali Linux adapter
The kali Linux is connected with BT virtual machine. The VM removable device
is attached with adapter.
To find out the Mode of wireless adapter and MAC address in the Kali Linux, one
could open the terminal.
ifconfig-command is used for interfacing the name and HWaddr in adapters.
iwconfig-command is used for interfacing name and Mode in wireless interfaces.
Change the wireless adapter, from the managed mode to monitor mode.
In the monitor mode, write down the name for adapter.
3
2. Capture traffic
3. Focus one AP in one channel.
4. Aire play.
5. Capture the handshake.
2.1 Objective
To do the activity - Cracking WPA2-PSK, the below mentioned hardware and software
tools are required.
Software tool- Kali Linux virtual machine.
Hardware tools
2-installed virtual machine in windows 7.
2-wireless adapters
1-access point.
2.2 Configuration
Initially the Access point (AP) is placed.
SSID is 6EWSx for AP.
The WPA2-PSK is configured with AP.
Now one could note down the password (passphrase).
With the help of WPA2-PSK passphrase, the wireless client pc is connected to the
AP for configuration.
Kali Linux adapter
The kali Linux is connected with BT virtual machine. The VM removable device
is attached with adapter.
To find out the Mode of wireless adapter and MAC address in the Kali Linux, one
could open the terminal.
ifconfig-command is used for interfacing the name and HWaddr in adapters.
iwconfig-command is used for interfacing name and Mode in wireless interfaces.
Change the wireless adapter, from the managed mode to monitor mode.
In the monitor mode, write down the name for adapter.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Get the wireless information
The 2nd terminal is opened to run the airodump with the help of "airodump-ng
wlan0' command.
It provides the information like which networks are present.
Predict the wireless traffic
Set the channel for monitor by opening the new terminal. Type "airodump-ng -c 6
-w psk --bssid (AP_MAC address) wlan0" to capturing the packets from the
channel.
For disconnecting the connected station, send the DE authentication to AP by
using airplay.one could use the airplay during the process of capturing.
Then one could view the WPA4 way handshake. This is captured by airodump.
2.3 How WPA-PSK passphrase is cracked
The airodump is stopped. Now the air crack is used by the new terminal.
This is Pre-shared key.
4
The 2nd terminal is opened to run the airodump with the help of "airodump-ng
wlan0' command.
It provides the information like which networks are present.
Predict the wireless traffic
Set the channel for monitor by opening the new terminal. Type "airodump-ng -c 6
-w psk --bssid (AP_MAC address) wlan0" to capturing the packets from the
channel.
For disconnecting the connected station, send the DE authentication to AP by
using airplay.one could use the airplay during the process of capturing.
Then one could view the WPA4 way handshake. This is captured by airodump.
2.3 How WPA-PSK passphrase is cracked
The airodump is stopped. Now the air crack is used by the new terminal.
This is Pre-shared key.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
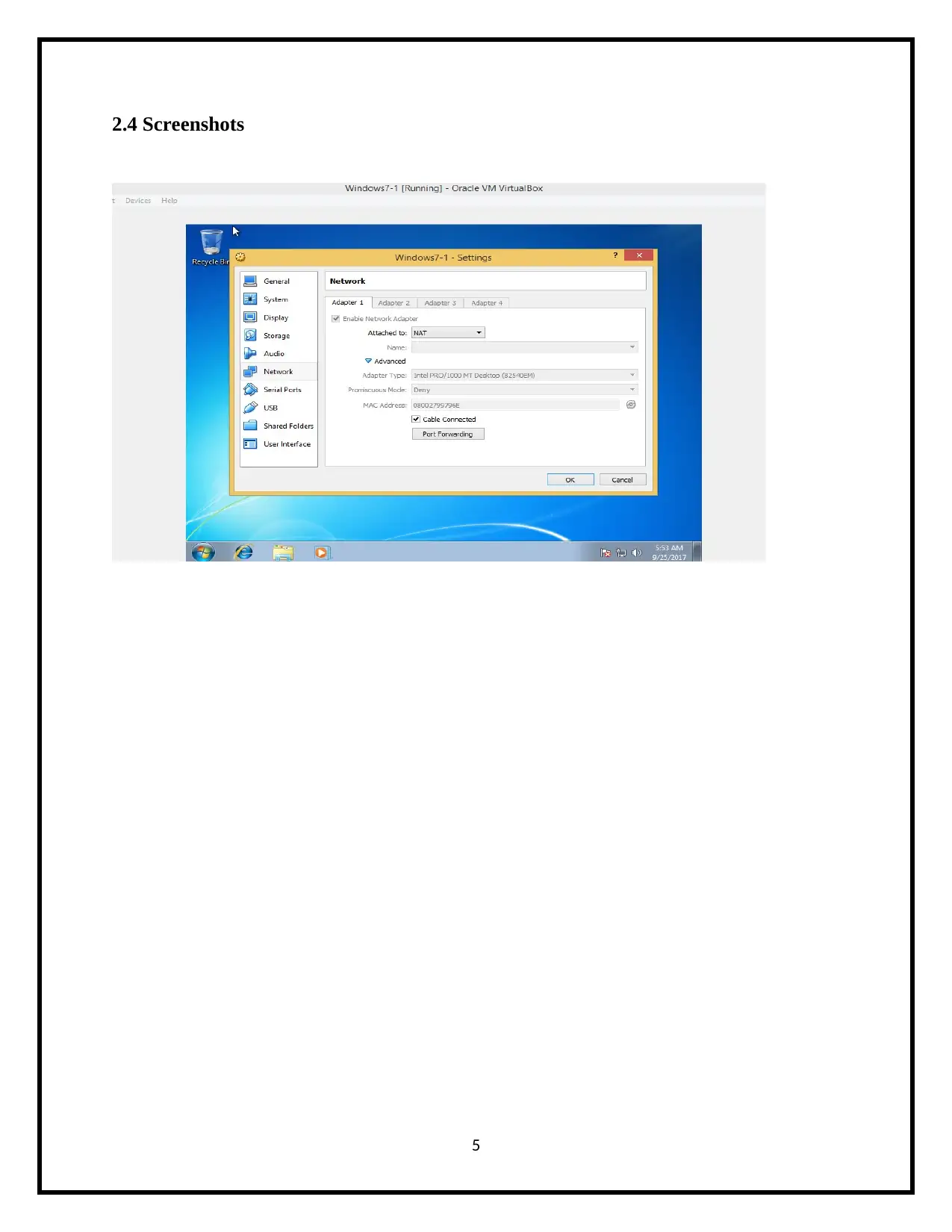
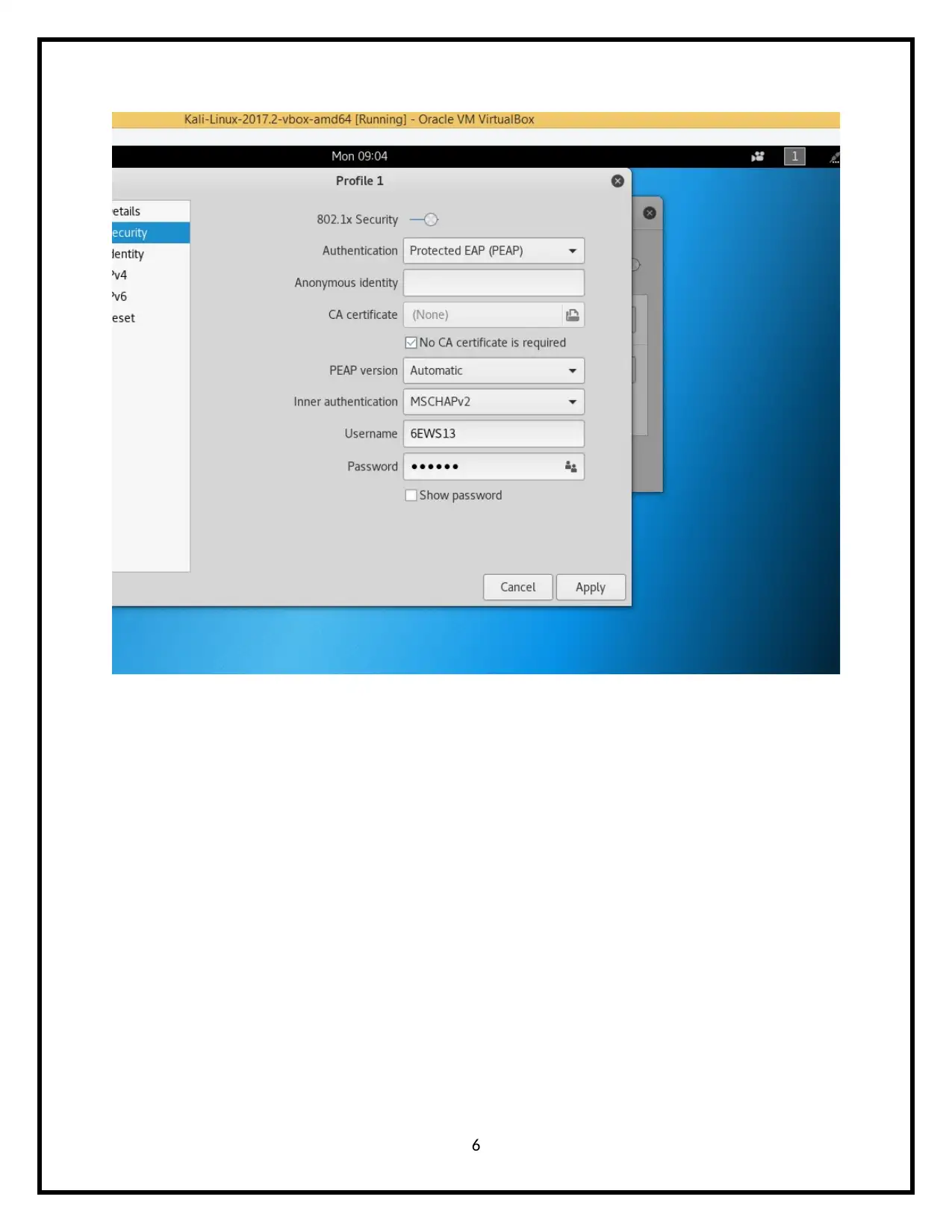
2.4 Screenshots
5
5
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
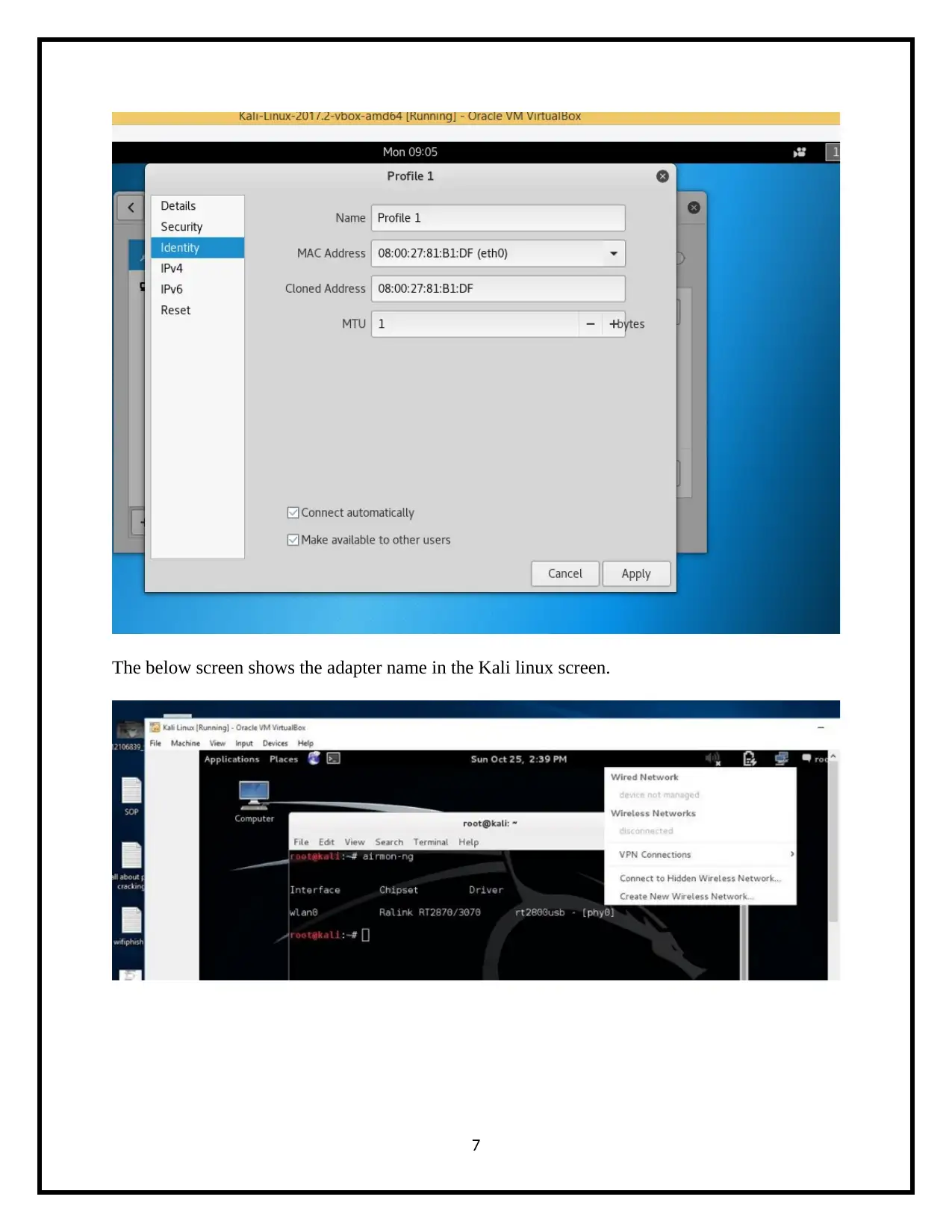
The below screen shows the adapter name in the Kali linux screen.
7
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
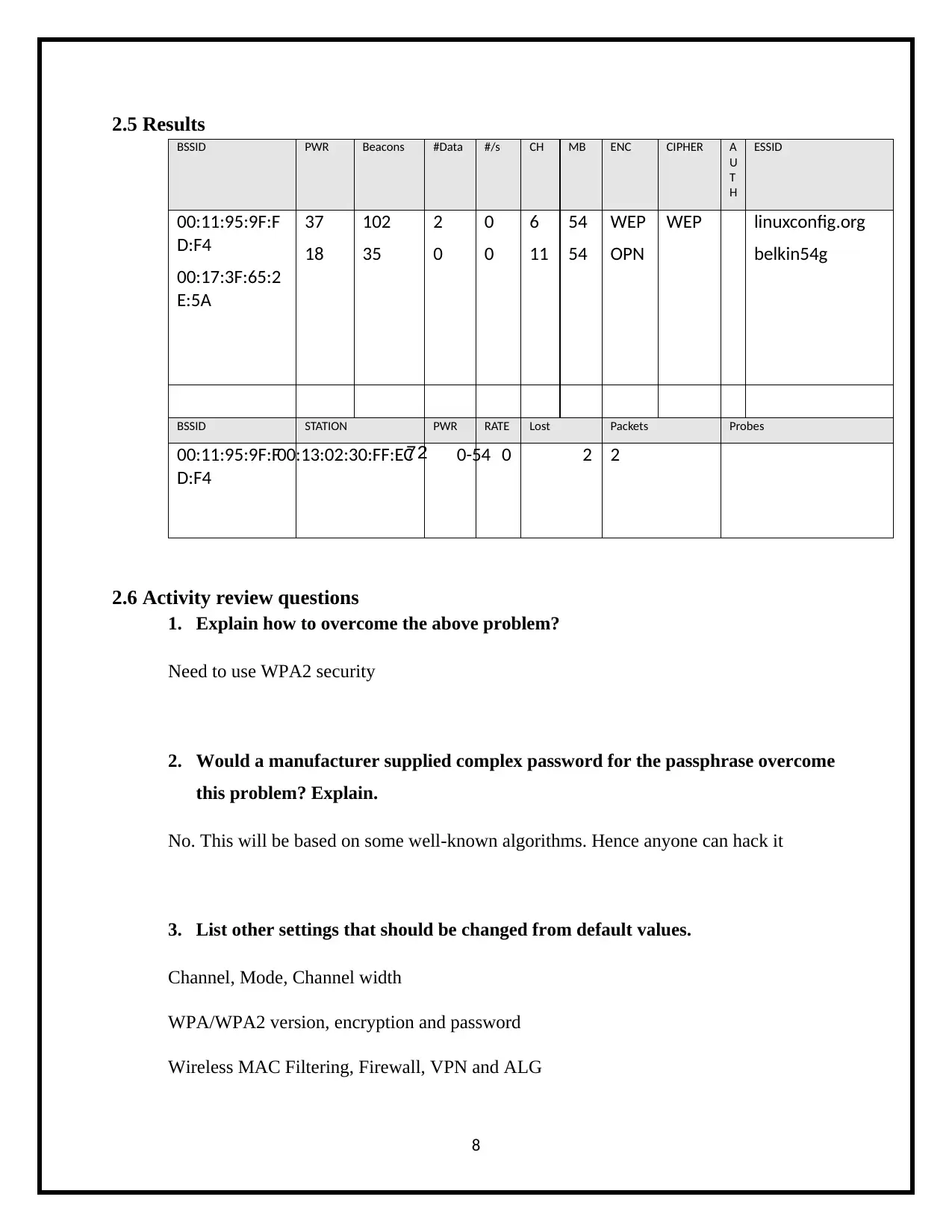
2.5 Results
BSSID PWR Beacons #Data #/s CH MB ENC CIPHER A
U
T
H
ESSID
00:11:95:9F:F
D:F4
00:17:3F:65:2
E:5A
37
18
102
35
2
0
0
0
6
11
54
54
WEP
OPN
WEP linuxconfig.org
belkin54g
BSSID STATION PWR RATE Lost Packets Probes
00:11:95:9F:F
D:F4
00:13:02:30:FF:EC72 0-54 0 2 2
2.6 Activity review questions
1. Explain how to overcome the above problem?
Need to use WPA2 security
2. Would a manufacturer supplied complex password for the passphrase overcome
this problem? Explain.
No. This will be based on some well-known algorithms. Hence anyone can hack it
3. List other settings that should be changed from default values.
Channel, Mode, Channel width
WPA/WPA2 version, encryption and password
Wireless MAC Filtering, Firewall, VPN and ALG
8
BSSID PWR Beacons #Data #/s CH MB ENC CIPHER A
U
T
H
ESSID
00:11:95:9F:F
D:F4
00:17:3F:65:2
E:5A
37
18
102
35
2
0
0
0
6
11
54
54
WEP
OPN
WEP linuxconfig.org
belkin54g
BSSID STATION PWR RATE Lost Packets Probes
00:11:95:9F:F
D:F4
00:13:02:30:FF:EC72 0-54 0 2 2
2.6 Activity review questions
1. Explain how to overcome the above problem?
Need to use WPA2 security
2. Would a manufacturer supplied complex password for the passphrase overcome
this problem? Explain.
No. This will be based on some well-known algorithms. Hence anyone can hack it
3. List other settings that should be changed from default values.
Channel, Mode, Channel width
WPA/WPA2 version, encryption and password
Wireless MAC Filtering, Firewall, VPN and ALG
8

3. Conclusion
The WPA2-PSK is studied along with the WPA4-way handshake. The brute force
password crack is used to extract the passphrase. The wireless network traffic is collected
to find out the WEP key. By using the SSID, the AP WEP configuration is performed.
The MAC addresses of wireless network is monitored. For providing the gain address to
the AP, MAC addresses is predicted. The Kali Linux is used for the process.
References
1. Ramachandran, V., & Buchanan, C. Kali Linux wireless penetration testing.
2. Wrightson, T. (2012). Wireless network security. New York: McGraw-Hill
9
The WPA2-PSK is studied along with the WPA4-way handshake. The brute force
password crack is used to extract the passphrase. The wireless network traffic is collected
to find out the WEP key. By using the SSID, the AP WEP configuration is performed.
The MAC addresses of wireless network is monitored. For providing the gain address to
the AP, MAC addresses is predicted. The Kali Linux is used for the process.
References
1. Ramachandran, V., & Buchanan, C. Kali Linux wireless penetration testing.
2. Wrightson, T. (2012). Wireless network security. New York: McGraw-Hill
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




