Crypto Currency Report: Bitcoin Case Study and Web Survey Results
VerifiedAdded on 2020/05/04
|16
|3561
|209
Report
AI Summary
This report provides a comprehensive analysis of crypto currencies, with a specific focus on Bitcoin. It begins with an executive summary outlining the report's objectives, which include examining the opportunities and challenges associated with crypto currency mechanisms. A case study on Bitcoin is presented, alongside findings from a web survey conducted to achieve the report's goals. The discussion covers peer-to-peer electronic transfer systems, the process of mining crypto currencies, the costs and viability of Bitcoin mining, and the potential threats and criminal uses of crypto currencies. The report also touches on the interest of the Chinese government in Bitcoin. The analysis reveals the advantages and disadvantages of crypto currencies and their global impact. The report concludes by highlighting obstacles that must be addressed before crypto currencies can replace traditional banking methods. Recommendations are provided to prevent the misuse of crypto currencies and to ensure their secure operation. The report includes an introduction, discussion, conclusion, and references.

Running head: CRYPTO CURRENCY
Crypto Currency
Name of the student
Name of the university
Author note
Crypto Currency
Name of the student
Name of the university
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CRYPTOCURRENCY
Executive summary:
This report aims to analyze the opportunities and challenges surrounding the crypto currency
mechanisms. A case study was provided to analyze the various aspects led forward in context
with the Bitcoin and accordingly, web survey was conducted to achieve the objectives of the
report. The results show the various pros and cons of the crypto currency and its relative impact
worldwide. This report concludes on the fact that still many obstacles are there to be overcome to
potentially present crypto currency as a replacement for the present banking methods. It is
recommended to develop measures to prevent the misuse of the crypto currency by the attackers.
Executive summary:
This report aims to analyze the opportunities and challenges surrounding the crypto currency
mechanisms. A case study was provided to analyze the various aspects led forward in context
with the Bitcoin and accordingly, web survey was conducted to achieve the objectives of the
report. The results show the various pros and cons of the crypto currency and its relative impact
worldwide. This report concludes on the fact that still many obstacles are there to be overcome to
potentially present crypto currency as a replacement for the present banking methods. It is
recommended to develop measures to prevent the misuse of the crypto currency by the attackers.

2CRYPTOCURRENCY
Table of Contents
INTRODUCTION:..........................................................................................................................3
DISCUSSION:.................................................................................................................................3
1. Peer-to-Peer Electronic Transfer System:............................................................................3
2. Mining Crypto-Currency:........................................................................................................7
3. Costs and Viability of Mining Bitcoin:................................................................................8
4. Threat of Crypto Currencies:...................................................................................................9
5. Criminal Usage of Crypto Currencies:...................................................................................9
6. Interest of government of China in Bitcoin:..........................................................................10
CONCLUSION:............................................................................................................................10
REFERENCES:.............................................................................................................................12
Table of Contents
INTRODUCTION:..........................................................................................................................3
DISCUSSION:.................................................................................................................................3
1. Peer-to-Peer Electronic Transfer System:............................................................................3
2. Mining Crypto-Currency:........................................................................................................7
3. Costs and Viability of Mining Bitcoin:................................................................................8
4. Threat of Crypto Currencies:...................................................................................................9
5. Criminal Usage of Crypto Currencies:...................................................................................9
6. Interest of government of China in Bitcoin:..........................................................................10
CONCLUSION:............................................................................................................................10
REFERENCES:.............................................................................................................................12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CRYPTOCURRENCY
INTRODUCTION:
Crypto Currency refers to the digital asset configured to be set as a medium for the
exchange, utilizing the cryptography to provide a secured transaction and hence, offering a
control and limiting the introduction of any additional units relative to currency. The relevant
keys, which are private enough are secured and stored in a wallet, technically known as the
crypto currency wallets. These crypto currencies are provided with a classification of being a
subset to the digital currencies as well as for the alternative currency methodology and the virtual
means of value transaction. Among the many, Bitcoin is the first decentralized crypto currency to
be launched in 2009. This report presents an insight on the various aspects of crypto currency
surrounding different crypto currencies. The report discusses the case study put forward, dealing
with the paper on the Bitcoin and its relevance in the crypto currency revolution and in the later
sections of the report the required analysis on crypto currencies is presented in a descriptive
manner.
DISCUSSION:
1. Peer-to-Peer Electronic Transfer System:
E-commerce these days have become a potential market player concerned with the
electronic transactions regarding the financial transfers. In relevance to the case study provided,
an analysis is led out on the Bitcoin as the crypto currencies used for the electronic
transmissions, the related procedures and conquests (Nakamoto 2008). However, the system is
well capable of most of the transactions while, it fails to gain its importance regarding a value-
based model. The major feature of this type of transaction is the fact that it is completely
INTRODUCTION:
Crypto Currency refers to the digital asset configured to be set as a medium for the
exchange, utilizing the cryptography to provide a secured transaction and hence, offering a
control and limiting the introduction of any additional units relative to currency. The relevant
keys, which are private enough are secured and stored in a wallet, technically known as the
crypto currency wallets. These crypto currencies are provided with a classification of being a
subset to the digital currencies as well as for the alternative currency methodology and the virtual
means of value transaction. Among the many, Bitcoin is the first decentralized crypto currency to
be launched in 2009. This report presents an insight on the various aspects of crypto currency
surrounding different crypto currencies. The report discusses the case study put forward, dealing
with the paper on the Bitcoin and its relevance in the crypto currency revolution and in the later
sections of the report the required analysis on crypto currencies is presented in a descriptive
manner.
DISCUSSION:
1. Peer-to-Peer Electronic Transfer System:
E-commerce these days have become a potential market player concerned with the
electronic transactions regarding the financial transfers. In relevance to the case study provided,
an analysis is led out on the Bitcoin as the crypto currencies used for the electronic
transmissions, the related procedures and conquests (Nakamoto 2008). However, the system is
well capable of most of the transactions while, it fails to gain its importance regarding a value-
based model. The major feature of this type of transaction is the fact that it is completely
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CRYPTOCURRENCY
irreversible as the financial institutions neglect the mediating any discrepancies or disputes. To
an extent, a considerable amount of fraud is present as that cannot be avoided. This provoked the
need for the cryptographic mode of transfer no basing the transmission process only on trust but
proof instead, allowing the two main people in business to carry forward the transmission
without the presence of a third-party. This system provides a better computational and
irreversible proof for the customers. However, the analysis prove that the paper is focused on the
providing the solution for the double-spending problem and henceforth, offering proof for the
chronological statement for the transactions.
Next is the concept of transaction involved in the digital process of financial transfer.
This section of the model introduced the digital coins, associated with digital signature. Signing a
hash relative to a previous transaction allows an owner to the transfer the coin to the other and
the same is applicable for the consecutive owners (Nakamoto 2008). A payee in charge can
proceed with the verification of the signatures for the authentication of the owners. To
implement the verification for the double spending by any of the owner, the direct solution for
the same is to introduce a central unit, which can be a replicate to the commercial banks that
would be responsible for the maintenance of records. To avoid any double-spending from the
owners, only the first transaction was approved to be considered so that this provides a relevant
record to the payee to understand and trust.
The solution to this particular criterion was the introduction of timestamp, which collects
the hash relative to a block of commodities that needs to be included. This provides the proof to
the existence of a particular data corresponding to a particular phase in order to be in the hash
collection. This mechanism helps in the formation of a chain containing the present and the
irreversible as the financial institutions neglect the mediating any discrepancies or disputes. To
an extent, a considerable amount of fraud is present as that cannot be avoided. This provoked the
need for the cryptographic mode of transfer no basing the transmission process only on trust but
proof instead, allowing the two main people in business to carry forward the transmission
without the presence of a third-party. This system provides a better computational and
irreversible proof for the customers. However, the analysis prove that the paper is focused on the
providing the solution for the double-spending problem and henceforth, offering proof for the
chronological statement for the transactions.
Next is the concept of transaction involved in the digital process of financial transfer.
This section of the model introduced the digital coins, associated with digital signature. Signing a
hash relative to a previous transaction allows an owner to the transfer the coin to the other and
the same is applicable for the consecutive owners (Nakamoto 2008). A payee in charge can
proceed with the verification of the signatures for the authentication of the owners. To
implement the verification for the double spending by any of the owner, the direct solution for
the same is to introduce a central unit, which can be a replicate to the commercial banks that
would be responsible for the maintenance of records. To avoid any double-spending from the
owners, only the first transaction was approved to be considered so that this provides a relevant
record to the payee to understand and trust.
The solution to this particular criterion was the introduction of timestamp, which collects
the hash relative to a block of commodities that needs to be included. This provides the proof to
the existence of a particular data corresponding to a particular phase in order to be in the hash
collection. This mechanism helps in the formation of a chain containing the present and the

5CRYPTOCURRENCY
preceding timestamp in the hash ensuring that every additional timestamp reinforces the previous
one.
The proof-of-work is the standard method to implement distributed network for the
timestamp based on the peer-to-peer system. This methodology helps in ensuring that each hash
initiates with a number of zero-digits. This mechanism increments each nonce present in the
block until it locates the presence of zero bits. If at any instance the CPU expended to satisfy the
method, the corresponding block cannot be configures unless a redo is available. Proof-of-work
satisfies the majority decision-making procedure as it is based on one-CPU-one-vote. The only
technical limitation orienting this methodology was the increasing speed of the hardware was
resolved with the evaluation of transfer of average number of blocks each hour.
Following few relevant steps as is presented in the study, helped in the easy networking
of the blocks. Adding to this, the nodes are the longest chain that can be considered as the correct
one. At the instances of mismatching information from the nodes, the first received broadcast by
the nodes is considered while the other is stored and the following proof reading method
provides the longest branch. On missing any node, the blocks potentially report about the same
with the receiving of the next one.
Regarding the initial transaction a new coin is achieved by the creator of the blocks. This
way the addition of incentives leads to the circulation of the coins in the system. In this
systematic proceeding, the CPU time and the electricity is on the expenditure. Transaction fee is
possibly funded for the incentive. Any predetermined entry of coins leads to the transition
entirely surrounding the transaction fee and the same is without any inflation. This incentive
preceding timestamp in the hash ensuring that every additional timestamp reinforces the previous
one.
The proof-of-work is the standard method to implement distributed network for the
timestamp based on the peer-to-peer system. This methodology helps in ensuring that each hash
initiates with a number of zero-digits. This mechanism increments each nonce present in the
block until it locates the presence of zero bits. If at any instance the CPU expended to satisfy the
method, the corresponding block cannot be configures unless a redo is available. Proof-of-work
satisfies the majority decision-making procedure as it is based on one-CPU-one-vote. The only
technical limitation orienting this methodology was the increasing speed of the hardware was
resolved with the evaluation of transfer of average number of blocks each hour.
Following few relevant steps as is presented in the study, helped in the easy networking
of the blocks. Adding to this, the nodes are the longest chain that can be considered as the correct
one. At the instances of mismatching information from the nodes, the first received broadcast by
the nodes is considered while the other is stored and the following proof reading method
provides the longest branch. On missing any node, the blocks potentially report about the same
with the receiving of the next one.
Regarding the initial transaction a new coin is achieved by the creator of the blocks. This
way the addition of incentives leads to the circulation of the coins in the system. In this
systematic proceeding, the CPU time and the electricity is on the expenditure. Transaction fee is
possibly funded for the incentive. Any predetermined entry of coins leads to the transition
entirely surrounding the transaction fee and the same is without any inflation. This incentive
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CRYPTOCURRENCY
helps in effective fraud management as the greedy owner, if any will discover to steal his own
transferred payments or will end up crating new coins.
The role of the disk space proves to be beneficial as prior to discarding of the transaction
in coin the disk space is saved accordingly. Merkel tree is beneficial equipment for restricting the
breaking of the block’s hash without the need of storage for the earlier interior hashes. Following
the corresponding block header with the absence of any transaction estimates to be 80 bytes.
This Bitcoin methodology was introduced with an advantage of payment verification
mode, following which, it became easy to run a full check on the network node to find the
longest proof-of-work in the present copy of the block header and utilizing the Merkel tree this
can be added on to the time-stamped block chain. However, there is a percentage of vulnerability
in concern to an attacker. Business receiving payments on a frequent basis will be more reliable
on a personalized network.
Developing a system to handle each coin on an individual approach is not a feasible
option, following this a set up with multiple units as input and outputs were used to split and
combine each transaction to provide an efficient transfer system. The fan-out option based on
inter-linked transaction is not a limitation in this case as the extraction transaction record is not
important.
Regarding the security concept especially surrounding the banking model, keeping the
private keys anonymous potential will break the flow of information especially surrounding the
identity of the individuals concerned with the transaction, similar to the stock exchange
mechanism. An introduction to another feasible firewall is the utilization of a new pair of keys to
avoid the linking with any common owner (Nakamoto 2008).
helps in effective fraud management as the greedy owner, if any will discover to steal his own
transferred payments or will end up crating new coins.
The role of the disk space proves to be beneficial as prior to discarding of the transaction
in coin the disk space is saved accordingly. Merkel tree is beneficial equipment for restricting the
breaking of the block’s hash without the need of storage for the earlier interior hashes. Following
the corresponding block header with the absence of any transaction estimates to be 80 bytes.
This Bitcoin methodology was introduced with an advantage of payment verification
mode, following which, it became easy to run a full check on the network node to find the
longest proof-of-work in the present copy of the block header and utilizing the Merkel tree this
can be added on to the time-stamped block chain. However, there is a percentage of vulnerability
in concern to an attacker. Business receiving payments on a frequent basis will be more reliable
on a personalized network.
Developing a system to handle each coin on an individual approach is not a feasible
option, following this a set up with multiple units as input and outputs were used to split and
combine each transaction to provide an efficient transfer system. The fan-out option based on
inter-linked transaction is not a limitation in this case as the extraction transaction record is not
important.
Regarding the security concept especially surrounding the banking model, keeping the
private keys anonymous potential will break the flow of information especially surrounding the
identity of the individuals concerned with the transaction, similar to the stock exchange
mechanism. An introduction to another feasible firewall is the utilization of a new pair of keys to
avoid the linking with any common owner (Nakamoto 2008).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CRYPTOCURRENCY
This is a digital mechanism of electronic transaction based on the utilization of Bitcoin
with various ways to provide security without solely depending on trusting third parties or
involving them but just on the expenditure of CPU time and electricity (Kogias et al. 2016).
2. Mining Crypto-Currency:
Crypto currency mining states to the procedure through which verifications of
transactions are done and likewise added to the segment of public ledger, technically termed as
the block chain (Vigna and Casey 2016). Through this procedure new coins are released. There
are various kinds of crypto currencies, few which can be stated are Bitcoin, Ethereum and Zcash.
Comparison on the resources for the mining of crypto currencies is provided.
For regular users using the computer daily, the technique of CPU mining is designed that
can be used for the purpose (Lewenberg et al. 2015). In this case, the CPU mining method
utilizes the general processor of the residential computers. GPU mining refers to Graphics
Processing Unit, which is especially used in a gaming computer as this is available in a high end
machine. The GPU is potential for the mining of different kinds of crypto currencies and the
most profitable of them varies with time. Coins providing minor advantages are easily CPU
mined.
While, another method for mining crypto currency is the ASICs, these are specially
configured machines that are built especially for the mining tasks. This method is a microchip
configured system launched in 2013 (Narayanan et al. 2016). These systems consume a great
level of power. Pools were arranged to vary the gain of blocks more evenly between the
companies set to compete for the limited amount of blocks available.
This is a digital mechanism of electronic transaction based on the utilization of Bitcoin
with various ways to provide security without solely depending on trusting third parties or
involving them but just on the expenditure of CPU time and electricity (Kogias et al. 2016).
2. Mining Crypto-Currency:
Crypto currency mining states to the procedure through which verifications of
transactions are done and likewise added to the segment of public ledger, technically termed as
the block chain (Vigna and Casey 2016). Through this procedure new coins are released. There
are various kinds of crypto currencies, few which can be stated are Bitcoin, Ethereum and Zcash.
Comparison on the resources for the mining of crypto currencies is provided.
For regular users using the computer daily, the technique of CPU mining is designed that
can be used for the purpose (Lewenberg et al. 2015). In this case, the CPU mining method
utilizes the general processor of the residential computers. GPU mining refers to Graphics
Processing Unit, which is especially used in a gaming computer as this is available in a high end
machine. The GPU is potential for the mining of different kinds of crypto currencies and the
most profitable of them varies with time. Coins providing minor advantages are easily CPU
mined.
While, another method for mining crypto currency is the ASICs, these are specially
configured machines that are built especially for the mining tasks. This method is a microchip
configured system launched in 2013 (Narayanan et al. 2016). These systems consume a great
level of power. Pools were arranged to vary the gain of blocks more evenly between the
companies set to compete for the limited amount of blocks available.

8CRYPTOCURRENCY
3. Costs and Viability of Mining Bitcoin:
The profitability of mining the Bitcoin in the present situation is dependable on certain
various variables; these variable parameters that influence the calculation are the electricity
costs, the hardware cost and other rates of variables. The fact relative to the mining of the
Bitcoin is that it ranges from the initial phase of involving few enthusiastic to specialized or
customized high industry venture (Raymaekers 2015). The easily accessible money oriented with
the procedure has expended long time ago and the now only remains low probabilities of
cryptographic equivalents. The most realistic fact is the organizations that develop and adapt
specialized and skilled mechanisms through launching machines are capable of extracting
Bitcoin at present (Courtois and Bahack 2014). In other words, even if mining is possible for
regular users, this would not prove to be beneficial or profitable for them as it consumes
maximum of the investment.
Electricity used per seconds of consumption relative to hash-rates is the major investment
linked with the mining method. The future profitability associated with the mining of the Bitcoin
is an unpredictable stance, especially owing to the constantly changing graph highlighting the
difficulty modifier and the relative price (Eyal and Sirer 2014). To initiate the mining, there is a
requirement of ASICs rig, which is as previously mentioned, designed specifically for mining.
There are present various anti-miners such as Anti-miner S9, which is available at an estimated
value of $1800 to $2400 and there is another associated cost of electricity. Henceforth, it is
understandable that Bitcoin mining cannot provide huge profitability until the investment
regarding the power consumption and equipments is high enough as in cases of big industries.
Numeric data relative to the crypto Currency profitability and trends is presented through
the following figures:
3. Costs and Viability of Mining Bitcoin:
The profitability of mining the Bitcoin in the present situation is dependable on certain
various variables; these variable parameters that influence the calculation are the electricity
costs, the hardware cost and other rates of variables. The fact relative to the mining of the
Bitcoin is that it ranges from the initial phase of involving few enthusiastic to specialized or
customized high industry venture (Raymaekers 2015). The easily accessible money oriented with
the procedure has expended long time ago and the now only remains low probabilities of
cryptographic equivalents. The most realistic fact is the organizations that develop and adapt
specialized and skilled mechanisms through launching machines are capable of extracting
Bitcoin at present (Courtois and Bahack 2014). In other words, even if mining is possible for
regular users, this would not prove to be beneficial or profitable for them as it consumes
maximum of the investment.
Electricity used per seconds of consumption relative to hash-rates is the major investment
linked with the mining method. The future profitability associated with the mining of the Bitcoin
is an unpredictable stance, especially owing to the constantly changing graph highlighting the
difficulty modifier and the relative price (Eyal and Sirer 2014). To initiate the mining, there is a
requirement of ASICs rig, which is as previously mentioned, designed specifically for mining.
There are present various anti-miners such as Anti-miner S9, which is available at an estimated
value of $1800 to $2400 and there is another associated cost of electricity. Henceforth, it is
understandable that Bitcoin mining cannot provide huge profitability until the investment
regarding the power consumption and equipments is high enough as in cases of big industries.
Numeric data relative to the crypto Currency profitability and trends is presented through
the following figures:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
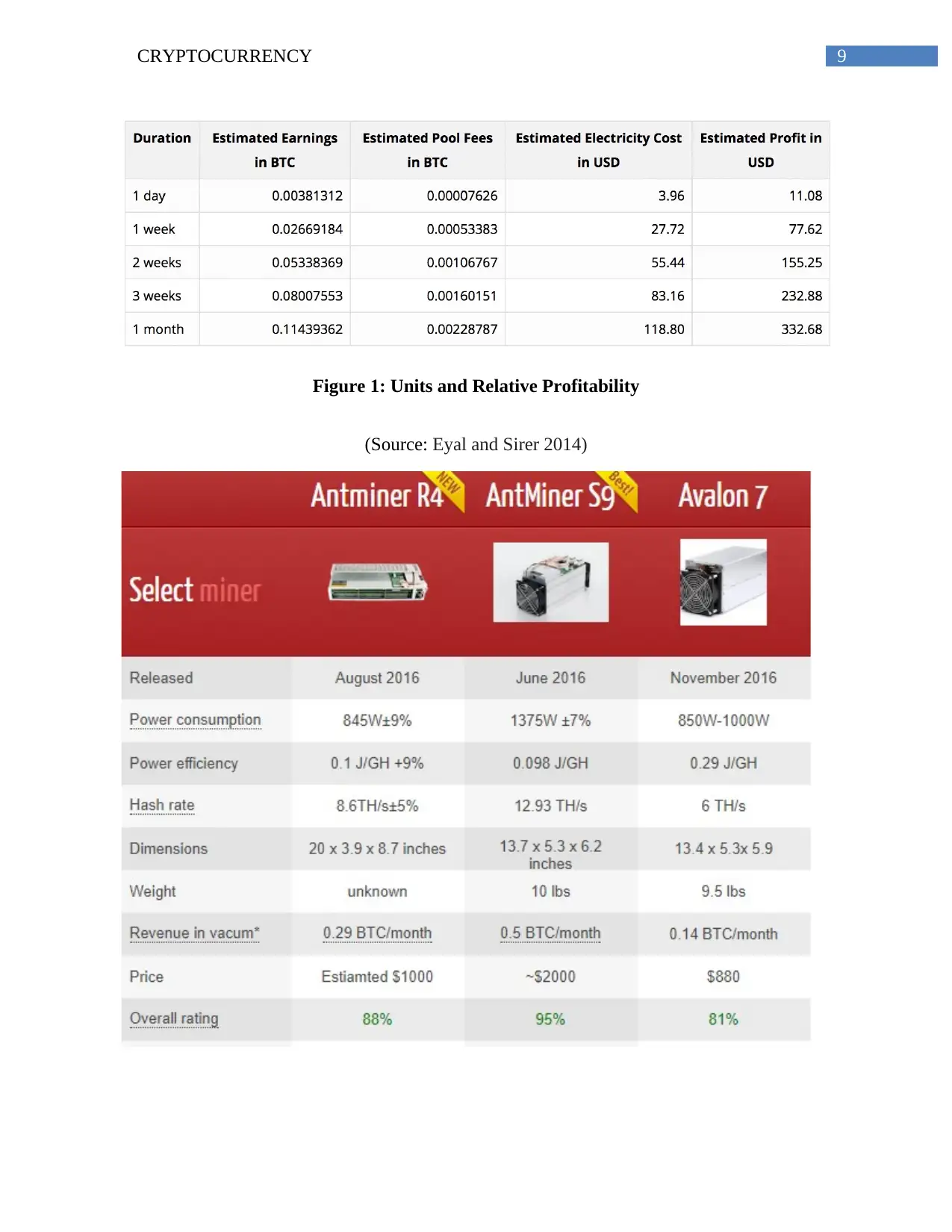
9CRYPTOCURRENCY
Figure 1: Units and Relative Profitability
(Source: Eyal and Sirer 2014)
Figure 1: Units and Relative Profitability
(Source: Eyal and Sirer 2014)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CRYPTOCURRENCY
Figure 2: Anti Miners for Bitcoin. (Source: Moore 2013 )
4. Threat of Crypto Currencies:
The introduction of crypto currency has caused a major shift on the ways people handle
business and the transaction methods. This has launched a model based on which the value
exchange is done even beyond traditional banking technologies with the simple utilization of
mobile phones (Moore 2013). This is making the people independent of the traditional banking
methodologies, as peer-to-peer networks based on the cryptographic transfer are gaining the
market attention and has reveled another way of financing.
Conceptually the direct response orienting the query of whether this is posing a threat to
the traditional concepts is a yes. The major industrialist with keen attention has already been
capable of identifying the industry for the crypto currency as a threat for on the banks stating that
this invention has the potential to transform the arena of finance. Analyzing the trending reports
and the studies it can be stated that crypto currency is a major threat to the banks especially
surrounding the customer care and their customized preferences associated with the financial
transfer (King 2013). This is especially due to the fact that the Bitcoin users are potential enough
to manage their own financial dealing without being dependent on banks. Crypto currency rely
on their own, which is supposedly uninterrupted technology to provide the full guaranteed value.
5. Criminal Usage of Crypto Currencies:
Higher regulation should be provided with the usage of Bitcoin to prevent the criminals
or the web-attackers from utilizing the benefits of crypto currency (Hayes 2017). This has
introduced a great level of opportunities for the criminals as recorded in the mid-May the hackers
Figure 2: Anti Miners for Bitcoin. (Source: Moore 2013 )
4. Threat of Crypto Currencies:
The introduction of crypto currency has caused a major shift on the ways people handle
business and the transaction methods. This has launched a model based on which the value
exchange is done even beyond traditional banking technologies with the simple utilization of
mobile phones (Moore 2013). This is making the people independent of the traditional banking
methodologies, as peer-to-peer networks based on the cryptographic transfer are gaining the
market attention and has reveled another way of financing.
Conceptually the direct response orienting the query of whether this is posing a threat to
the traditional concepts is a yes. The major industrialist with keen attention has already been
capable of identifying the industry for the crypto currency as a threat for on the banks stating that
this invention has the potential to transform the arena of finance. Analyzing the trending reports
and the studies it can be stated that crypto currency is a major threat to the banks especially
surrounding the customer care and their customized preferences associated with the financial
transfer (King 2013). This is especially due to the fact that the Bitcoin users are potential enough
to manage their own financial dealing without being dependent on banks. Crypto currency rely
on their own, which is supposedly uninterrupted technology to provide the full guaranteed value.
5. Criminal Usage of Crypto Currencies:
Higher regulation should be provided with the usage of Bitcoin to prevent the criminals
or the web-attackers from utilizing the benefits of crypto currency (Hayes 2017). This has
introduced a great level of opportunities for the criminals as recorded in the mid-May the hackers

11CRYPTOCURRENCY
were able to receive thousand dollars through Bitcoin by attacking the global networking system
by a malware named WannaCry (Hurlbur and Bojanova 2014). Bitcoin is as introduced earlier in
the report is anonymous and thus is easy for the criminals to use. The malware pot5enmtially
locked the computers and demanded money in form of Bitcoin to unlock the systems. This
provided the criminals with huge amount of money (Kaplanov 2012). The release of the Bitcoin
usage critically questions the security oriented with the utilization of Bitcoin especially the
misuse of the same by the attackers. Likewise, the Bitcoin do not deserve to be illegal but a
pointer to note is the feature of anonymity of the Bitcoin has risen the bars of criminal attacks in
the recent past by helping the ransomware attacks (Apostolaki, Zohar and Vanbever 2016).
6. Interest of government of China in Bitcoin:
China is involved in the procedure of mining, which is estimated to be the most of
Bitcoin and henceforth, potentially can export most of the Bitcoins. The power consumption
relative to the technique of mining requires electricity, which is available in China at cheaper
rates as compared to the world around (Bonneau et al. 2015). This particular fact has allowed the
Bitcoin miners to gain a high level of hash power. Based on research it is discovered that most of
the electricity companies in there utilize or channelize their power towards the mining of
Bitcoins. The concept of Bitcoin started as a sovereign authority that as a liberal property even
free from the government. The largest mining pools controlled by Bitman, situated in Beijing
consume or controls almost 30% of the entire processing of power focused on the mining of
Bitcoins.
China is the place of origin for many Bitcoin mining units suchas F2Pool, AnPool and
BTCC. They mine about 60% of the entirely new Bitcoins.
were able to receive thousand dollars through Bitcoin by attacking the global networking system
by a malware named WannaCry (Hurlbur and Bojanova 2014). Bitcoin is as introduced earlier in
the report is anonymous and thus is easy for the criminals to use. The malware pot5enmtially
locked the computers and demanded money in form of Bitcoin to unlock the systems. This
provided the criminals with huge amount of money (Kaplanov 2012). The release of the Bitcoin
usage critically questions the security oriented with the utilization of Bitcoin especially the
misuse of the same by the attackers. Likewise, the Bitcoin do not deserve to be illegal but a
pointer to note is the feature of anonymity of the Bitcoin has risen the bars of criminal attacks in
the recent past by helping the ransomware attacks (Apostolaki, Zohar and Vanbever 2016).
6. Interest of government of China in Bitcoin:
China is involved in the procedure of mining, which is estimated to be the most of
Bitcoin and henceforth, potentially can export most of the Bitcoins. The power consumption
relative to the technique of mining requires electricity, which is available in China at cheaper
rates as compared to the world around (Bonneau et al. 2015). This particular fact has allowed the
Bitcoin miners to gain a high level of hash power. Based on research it is discovered that most of
the electricity companies in there utilize or channelize their power towards the mining of
Bitcoins. The concept of Bitcoin started as a sovereign authority that as a liberal property even
free from the government. The largest mining pools controlled by Bitman, situated in Beijing
consume or controls almost 30% of the entire processing of power focused on the mining of
Bitcoins.
China is the place of origin for many Bitcoin mining units suchas F2Pool, AnPool and
BTCC. They mine about 60% of the entirely new Bitcoins.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





