Comprehensive Analysis of Cryptocurrency and Cryptocurrency Hijacking
VerifiedAdded on 2023/04/20
|9
|1276
|419
Report
AI Summary
This report examines the growing issue of cryptocurrency and cryptocurrency hijacking, focusing on the security challenges in the digital financial landscape. It begins by explaining the fundamentals of cryptocurrency, its blockchain technology, and how these systems operate, emphasizing the importance of security in financial transactions. The report then delves into the specifics of cryptocurrency hijacking, detailing how attackers exploit system resources to gain access to servers and web pages, and the various methods used to carry out these attacks. It provides a comprehensive overview of protective measures, including testing tools, antivirus software, firewalls, browser security, endpoint and gateway protection, and the use of browser functionalities to block crypto-jacking attacks. The report also highlights the use of anti-crypto-mining extensions, ad blockers, ad filters, and script-blocking extensions. Furthermore, it emphasizes the importance of network monitoring, corporate security awareness, and the use of cloud-based web browsers to enhance security. The report concludes by offering a detailed reference list, providing resources for further study and research on the topic.

Cryptocurrency and Cryptocurrency hijacking 1
CRYPTOCURRENCY AND CRYPTOCURRENCY HIJACKING
Student’s name
Name of the University
Date of submission
CRYPTOCURRENCY AND CRYPTOCURRENCY HIJACKING
Student’s name
Name of the University
Date of submission
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cryptocurrency and Cryptocurrency Hijacking 2
Cryptocurrency and Cryptocurrency Hijacking
In the current world, Security of financial organizations has become the most significant
issue and concern of all the parties conducting the transaction over the internet. This has caused a
lot of insecurity in these organizations and parties involved in transaction form attacks and loss
of their good, services offered and money paid or stolen in the process. The emergence of
cryptocurrency systems has led to further security, safe transactions and improvement of
integrity in the systems.
Cryptocurrencies are global decentralized systems designed on a blockchain technology
to generate and regulates the use of the digital currency exchanged digitally without any
limitation of supply. Blockchain technology keeps cryptocurrencies on track irrespective of if
they are being held in a digital wallet or used in the transaction (Hileman & Rauchs 2017).
How cryptocurrencies systems work
The cryptocurrencies require an infrastructure that ensures security for the effective
running of the system. It has a ledger, where all transactions that are made visible for all the
users thus improving integrity and trust among the parties. Ledger provides a list of entries in a
database that cannot be changed by any party without satisfying certain conditions. Ledger and
the cryptocurrency blockchain are decentralized meaning running without the interference of
outside parties (Higbee 2018).
Cryptocurrency and Cryptocurrency Hijacking
In the current world, Security of financial organizations has become the most significant
issue and concern of all the parties conducting the transaction over the internet. This has caused a
lot of insecurity in these organizations and parties involved in transaction form attacks and loss
of their good, services offered and money paid or stolen in the process. The emergence of
cryptocurrency systems has led to further security, safe transactions and improvement of
integrity in the systems.
Cryptocurrencies are global decentralized systems designed on a blockchain technology
to generate and regulates the use of the digital currency exchanged digitally without any
limitation of supply. Blockchain technology keeps cryptocurrencies on track irrespective of if
they are being held in a digital wallet or used in the transaction (Hileman & Rauchs 2017).
How cryptocurrencies systems work
The cryptocurrencies require an infrastructure that ensures security for the effective
running of the system. It has a ledger, where all transactions that are made visible for all the
users thus improving integrity and trust among the parties. Ledger provides a list of entries in a
database that cannot be changed by any party without satisfying certain conditions. Ledger and
the cryptocurrency blockchain are decentralized meaning running without the interference of
outside parties (Higbee 2018).

Cryptocurrency and Cryptocurrency Hijacking 3
After the purchase, the transaction undergoes through a verification process after which is
recorded in the history of operations on the blockchain public ledger and the miner is given a
reward for their efforts based on the cryptocurrency.
Cryptocurrency Hijacking
Cryptocurrency hijacking is a type of an attack that allows websites or hackers to intrude
into the system resources of remote computer users where it gains access into a server or a web
page to take advantage of the user's resources.
How to Protect Against Cryptocurrency Hijacking
Testing
There are tools and methods available to test web browsers to confirm that anti-crypto-
jacking tools are working. e.g., cryptojackingtest.com. The use of other technologies of testing
like browser and gateway solutions can also help limit the risk of cryptocurrency attacks.
Antivirus software.
Use of antivirus recognizes and protects a computer against attack and malware,
providing the user with the ability to detect and mitigate potentially malware and intrusion before
they cause any damage in the system.
Firewall installation
After the purchase, the transaction undergoes through a verification process after which is
recorded in the history of operations on the blockchain public ledger and the miner is given a
reward for their efforts based on the cryptocurrency.
Cryptocurrency Hijacking
Cryptocurrency hijacking is a type of an attack that allows websites or hackers to intrude
into the system resources of remote computer users where it gains access into a server or a web
page to take advantage of the user's resources.
How to Protect Against Cryptocurrency Hijacking
Testing
There are tools and methods available to test web browsers to confirm that anti-crypto-
jacking tools are working. e.g., cryptojackingtest.com. The use of other technologies of testing
like browser and gateway solutions can also help limit the risk of cryptocurrency attacks.
Antivirus software.
Use of antivirus recognizes and protects a computer against attack and malware,
providing the user with the ability to detect and mitigate potentially malware and intrusion before
they cause any damage in the system.
Firewall installation
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cryptocurrency and Cryptocurrency Hijacking 4
Firewalls prevent attack by blocking malicious incoming and outgoing traffic before it gets
access to a computer system and restricting unnecessary communications based on the set of
security riles laid. A firewall establishes a barrier between the internal network and external
network, e.g. the Internet (Apostolaki, Zohar &Vanbever, 2017).
Security of the Browser
Different browsers offer a varying degree of protection when it comes to cryptocurrency
protection. Browsers including safari by apple and google chrome have the capabilities of ad-
blocking few of cryptocurrency miners. This protection is available in other web browsers such
as Opera and Mozilla Firefox.
Endpoint Protection
Endpoint Detection tools are used to identify and block crypto-jacking attacks on
endpoints through browser scripts. Endpoint detection offers continuous monitoring and
response to advanced security threats.
Gateway Protection
Web gateway protection technologies provide site filtering rules that will block
cryptocurrency miners at the gateway.
High Resource Utilization
Firewalls prevent attack by blocking malicious incoming and outgoing traffic before it gets
access to a computer system and restricting unnecessary communications based on the set of
security riles laid. A firewall establishes a barrier between the internal network and external
network, e.g. the Internet (Apostolaki, Zohar &Vanbever, 2017).
Security of the Browser
Different browsers offer a varying degree of protection when it comes to cryptocurrency
protection. Browsers including safari by apple and google chrome have the capabilities of ad-
blocking few of cryptocurrency miners. This protection is available in other web browsers such
as Opera and Mozilla Firefox.
Endpoint Protection
Endpoint Detection tools are used to identify and block crypto-jacking attacks on
endpoints through browser scripts. Endpoint detection offers continuous monitoring and
response to advanced security threats.
Gateway Protection
Web gateway protection technologies provide site filtering rules that will block
cryptocurrency miners at the gateway.
High Resource Utilization
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cryptocurrency and Cryptocurrency Hijacking 5
Browsers provide resource utilization metrics that can help pinpoint potential
cryptocurrency mining activities.
The browser that provides the best way to block crypto jacking attack
Opera mini being the best web browser with Virtual Private Network installed in it offers
the best protection to crypto-jacking attacks . The protection measures proposed will be achieved
by the browser providing no clues while browsing on your device hence ends up not exposing
the device to mining. Opera mini browser has a feature that protects users from attacks that
involve cryptocurrency highjacking.
How to Use Browser Functionality to Block Crypto Jacking Attack
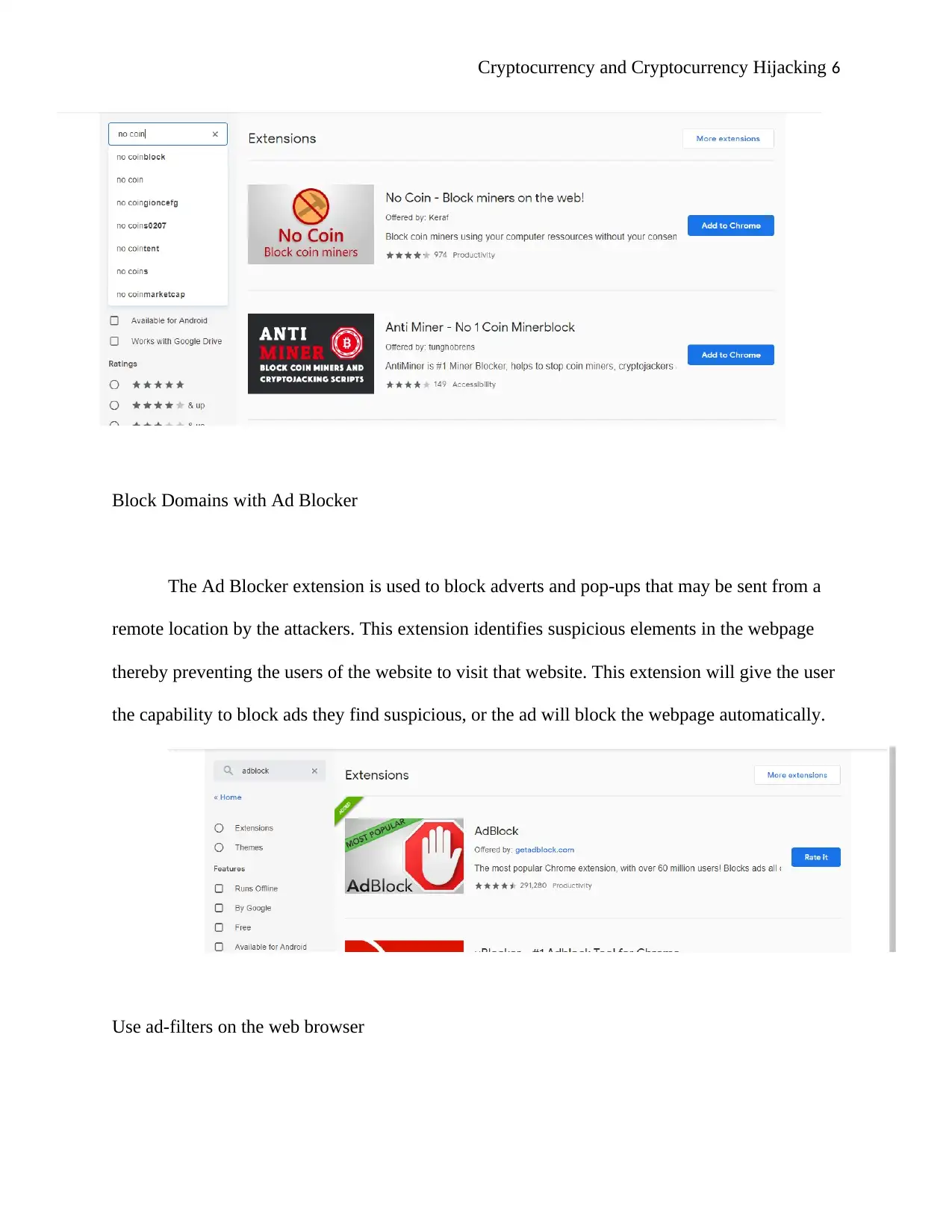
Anti-crypto-mining extensions
There are many extensions available in various platforms, and they include the following;
No Coin for Google Chrome or Firefox, and Miner-Block for Chrome which attempts to block
all connections that match with that of a known crypto-jackers. Ad-blockers may be constructed
to prevent all known and newly recognized crypto-jacking domain names (Sigler 2018).
Browsers provide resource utilization metrics that can help pinpoint potential
cryptocurrency mining activities.
The browser that provides the best way to block crypto jacking attack
Opera mini being the best web browser with Virtual Private Network installed in it offers
the best protection to crypto-jacking attacks . The protection measures proposed will be achieved
by the browser providing no clues while browsing on your device hence ends up not exposing
the device to mining. Opera mini browser has a feature that protects users from attacks that
involve cryptocurrency highjacking.
How to Use Browser Functionality to Block Crypto Jacking Attack
Anti-crypto-mining extensions
There are many extensions available in various platforms, and they include the following;
No Coin for Google Chrome or Firefox, and Miner-Block for Chrome which attempts to block
all connections that match with that of a known crypto-jackers. Ad-blockers may be constructed
to prevent all known and newly recognized crypto-jacking domain names (Sigler 2018).
Cryptocurrency and Cryptocurrency Hijacking 6
Block Domains with Ad Blocker
The Ad Blocker extension is used to block adverts and pop-ups that may be sent from a
remote location by the attackers. This extension identifies suspicious elements in the webpage
thereby preventing the users of the website to visit that website. This extension will give the user
the capability to block ads they find suspicious, or the ad will block the webpage automatically.
Use ad-filters on the web browser
Block Domains with Ad Blocker
The Ad Blocker extension is used to block adverts and pop-ups that may be sent from a
remote location by the attackers. This extension identifies suspicious elements in the webpage
thereby preventing the users of the website to visit that website. This extension will give the user
the capability to block ads they find suspicious, or the ad will block the webpage automatically.
Use ad-filters on the web browser
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cryptocurrency and Cryptocurrency Hijacking 7
This ad-filter uses script blocking extensions on the website to neutralize JavaScript they
include; script-safe for Chrome and Firefox which warns you before scripts to run, and No-Script
for Mozilla. Note that disabling JavaScript can cripple the functionality of many websites, so use
these tools with caution.
Close infected browser tabs
Attacks happening as a result of cryptocurrency may happen on the internet through a
script injected on the webpage. Closing the browser tabs will prevent the attack from taking over
computers on the network.
Destroy protocols for web-delivered
Network administrators check on the history of the extensions of the web browsers from
which scripts originate from and update network web filters to block the unwanted web pages in
future.
Monitoring devices, networks, and resources
Monitoring should check out that there are no anonymous increments in the hardware
activity and protocols to make sure that they are in place to isolate any error encountered by the
devices or processes that are notorious. An example is the use of antiviruses like Esset, Avast or
Windows Defender.
This ad-filter uses script blocking extensions on the website to neutralize JavaScript they
include; script-safe for Chrome and Firefox which warns you before scripts to run, and No-Script
for Mozilla. Note that disabling JavaScript can cripple the functionality of many websites, so use
these tools with caution.
Close infected browser tabs
Attacks happening as a result of cryptocurrency may happen on the internet through a
script injected on the webpage. Closing the browser tabs will prevent the attack from taking over
computers on the network.
Destroy protocols for web-delivered
Network administrators check on the history of the extensions of the web browsers from
which scripts originate from and update network web filters to block the unwanted web pages in
future.
Monitoring devices, networks, and resources
Monitoring should check out that there are no anonymous increments in the hardware
activity and protocols to make sure that they are in place to isolate any error encountered by the
devices or processes that are notorious. An example is the use of antiviruses like Esset, Avast or
Windows Defender.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Cryptocurrency and Cryptocurrency Hijacking 8
Using cloud-based web browsers
These run off sites and remote in the cloud rather than locally, with centralized, managed
and supervised security measures that are superior to those that can be provided by the user
interacting with the system or organizations that use the system to perform their interaction and
day to day activities.
Corporate security awareness training
Corporate security awareness includes informing all the parties involved to be aware of
the warning signs and messages that indicate a crypto-jacking attack as well as knowing website
that are unwanted.
Using cloud-based web browsers
These run off sites and remote in the cloud rather than locally, with centralized, managed
and supervised security measures that are superior to those that can be provided by the user
interacting with the system or organizations that use the system to perform their interaction and
day to day activities.
Corporate security awareness training
Corporate security awareness includes informing all the parties involved to be aware of
the warning signs and messages that indicate a crypto-jacking attack as well as knowing website
that are unwanted.

Cryptocurrency and Cryptocurrency Hijacking 9
Reference List
Apostolaki, M., Zohar, A. and Vanbever, L., 2017, May. Hijacking bitcoin: Routing attacks on
cryptocurrencies. In 2017 IEEE Symposium on Security and Privacy (SP) (pp. 375-392). IEEE.
Hileman, G. and Rauchs, M., 2017. Global cryptocurrency benchmarking study. Cambridge
Centre for Alternative Finance, 33.
Higbee, A., 2018. The role of crypto-currency in cybercrime. Computer Fraud &
Security, 2018(7), pp.13-15.
Sigler, K., 2018. Crypto-jacking: how cyber-criminals are exploiting the crypto-currency
boom. Computer Fraud & Security, 2018(9), pp.12-14.
Reference List
Apostolaki, M., Zohar, A. and Vanbever, L., 2017, May. Hijacking bitcoin: Routing attacks on
cryptocurrencies. In 2017 IEEE Symposium on Security and Privacy (SP) (pp. 375-392). IEEE.
Hileman, G. and Rauchs, M., 2017. Global cryptocurrency benchmarking study. Cambridge
Centre for Alternative Finance, 33.
Higbee, A., 2018. The role of crypto-currency in cybercrime. Computer Fraud &
Security, 2018(7), pp.13-15.
Sigler, K., 2018. Crypto-jacking: how cyber-criminals are exploiting the crypto-currency
boom. Computer Fraud & Security, 2018(9), pp.12-14.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





