Applying Cryptographic Algorithms to the Australian My Health Record
VerifiedAdded on 2022/12/30
|6
|1809
|47
Report
AI Summary
This report examines the application of cybersecurity algorithms to the Australian My Health Record (MHR) system. It begins with an introduction to cybersecurity and its importance in protecting sensitive data. The report then delves into the use cases and misuse cases within the MHR system, identifying potential vulnerabilities and threats. It explores symmetric and asymmetric cryptographic algorithms, discussing their strengths and weaknesses in securing data transmission and storage. Furthermore, the report analyzes recent cryptographic algorithms, such as the Hash-based Message Authentication Code (HMAC), and their role in enhancing security. Recommendations are provided to improve the overall security posture of the MHR system, emphasizing the importance of implementing robust cryptographic solutions. The report concludes by summarizing the key findings and reiterating the significance of cybersecurity in safeguarding patient information.

Cyber Algorithms 1
CRYPTOGRAPHIC ALGORITHMS FOR AUSTRALIAN MY HEALTH RECORD SYSTEM
By
Student’s Name
Student ID
Course Name
Instructor’s Name
University
City and State
Date
CRYPTOGRAPHIC ALGORITHMS FOR AUSTRALIAN MY HEALTH RECORD SYSTEM
By
Student’s Name
Student ID
Course Name
Instructor’s Name
University
City and State
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber Algorithms 2
Cyber Algorithms
Introduction
Cyber security is the process of safeguarding servers in a network, computer systems, electronic
devices such as the mobile and the electronic devices, protection of information and computer networks
against the attackers. In the security of the information, Cybersecurity is responsible for the protection
of data privacy and integrity. The data is protected can either be in a database or transit. We can apply
the cybersecurity algorithms in Australian My Health Record - MHR system application to secure the
information in the database and also the data under transit. Implementation of both algorithms of cyber
security which include the symmetrical and asymmetrical we will be able to achieve the appropriate
protection.
Activity 1
The use case and the misuse cases descriptions in MHR
A use case is a description that is written which shows how the users will carry out their duties on the
Australian My Health Record (MHR). The use case describes from the perspective of the user when it
is providing a response as requested. Use cases highlight the number of goals that are considered in
evaluating the complexity and the cost of the system as discussed by Jacobson, Spence and Kerr
(2016).
In the case of the MHR, the use case is highlighting to use the group of people using the website which
includes the doctors, pharmacists and the patients. Furthermore, the use case is describing the goals of
what the doctors want to do in the system, what the patient intends to achieve and what the system
administrator wishes to do. The administrator may decide to allow more data into the system or wipe
out the data present in the database of the system.
Use Cases
The use case is the one that can allow the users to achieve their goal; for instance, the doctor can give a
prescription to a patient on the MHR system. The fourth use case provides the steps to be taken by the
user achieve specific tasks such as the procedures followed when locking into the system by the users
of the MHR system. The last use case the way the website of MHR responds primarily in situations
when information about a patient is required.
Misuse Cases
Misuses case is a situation which occurs when an actor is hostile and poses some risks to the system as
explained by Yoo, Vaca and Kim (2017). The possible misuse cases or the above illustrated use cases
in the MHR system include the failure of the organization to secure the MHR system will attract the
attackers, when a doctor fails to log out of the system when using a public computer, a patient provides
Cyber Algorithms
Introduction
Cyber security is the process of safeguarding servers in a network, computer systems, electronic
devices such as the mobile and the electronic devices, protection of information and computer networks
against the attackers. In the security of the information, Cybersecurity is responsible for the protection
of data privacy and integrity. The data is protected can either be in a database or transit. We can apply
the cybersecurity algorithms in Australian My Health Record - MHR system application to secure the
information in the database and also the data under transit. Implementation of both algorithms of cyber
security which include the symmetrical and asymmetrical we will be able to achieve the appropriate
protection.
Activity 1
The use case and the misuse cases descriptions in MHR
A use case is a description that is written which shows how the users will carry out their duties on the
Australian My Health Record (MHR). The use case describes from the perspective of the user when it
is providing a response as requested. Use cases highlight the number of goals that are considered in
evaluating the complexity and the cost of the system as discussed by Jacobson, Spence and Kerr
(2016).
In the case of the MHR, the use case is highlighting to use the group of people using the website which
includes the doctors, pharmacists and the patients. Furthermore, the use case is describing the goals of
what the doctors want to do in the system, what the patient intends to achieve and what the system
administrator wishes to do. The administrator may decide to allow more data into the system or wipe
out the data present in the database of the system.
Use Cases
The use case is the one that can allow the users to achieve their goal; for instance, the doctor can give a
prescription to a patient on the MHR system. The fourth use case provides the steps to be taken by the
user achieve specific tasks such as the procedures followed when locking into the system by the users
of the MHR system. The last use case the way the website of MHR responds primarily in situations
when information about a patient is required.
Misuse Cases
Misuses case is a situation which occurs when an actor is hostile and poses some risks to the system as
explained by Yoo, Vaca and Kim (2017). The possible misuse cases or the above illustrated use cases
in the MHR system include the failure of the organization to secure the MHR system will attract the
attackers, when a doctor fails to log out of the system when using a public computer, a patient provides
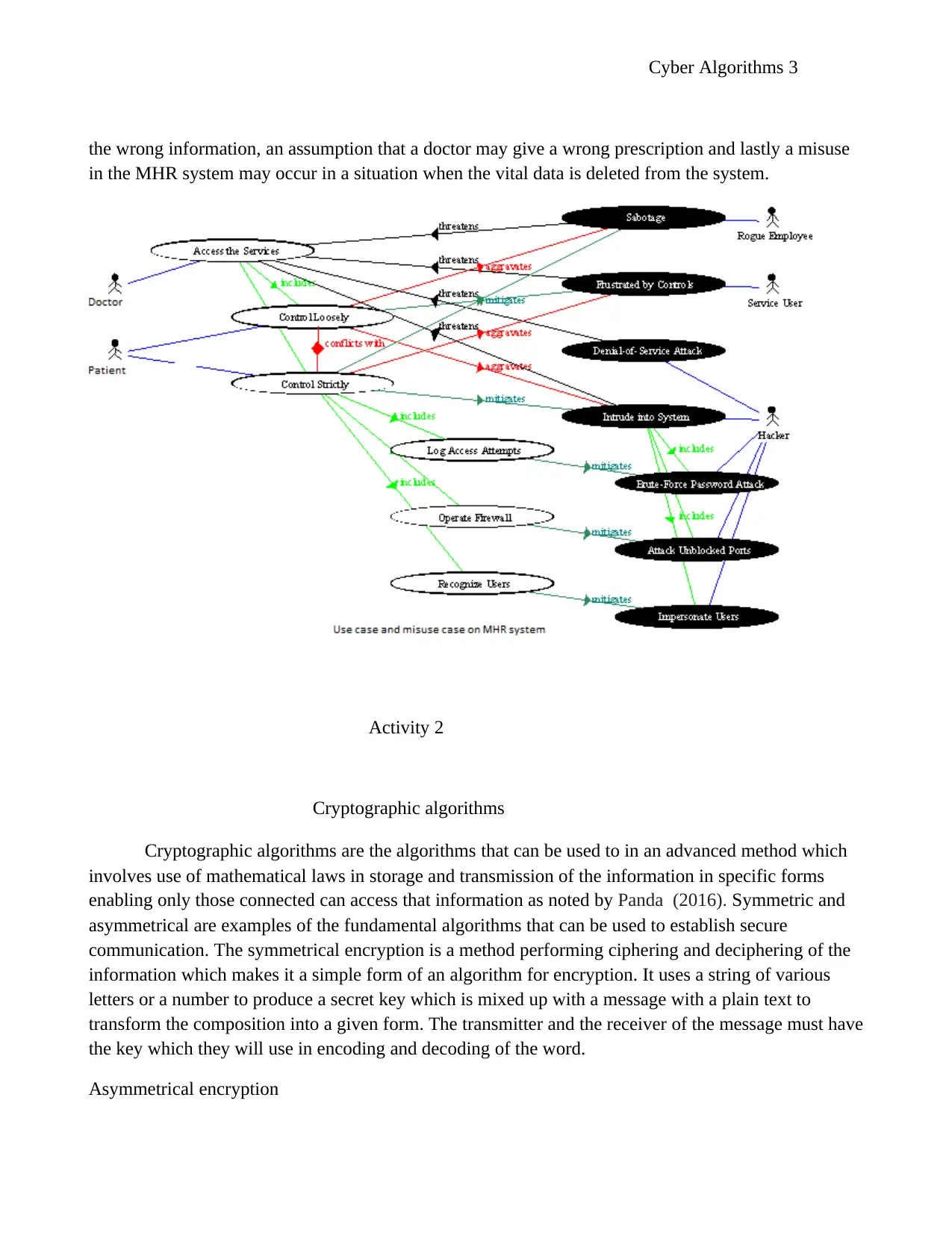
Cyber Algorithms 3
the wrong information, an assumption that a doctor may give a wrong prescription and lastly a misuse
in the MHR system may occur in a situation when the vital data is deleted from the system.
Activity 2
Cryptographic algorithms
Cryptographic algorithms are the algorithms that can be used to in an advanced method which
involves use of mathematical laws in storage and transmission of the information in specific forms
enabling only those connected can access that information as noted by Panda (2016). Symmetric and
asymmetrical are examples of the fundamental algorithms that can be used to establish secure
communication. The symmetrical encryption is a method performing ciphering and deciphering of the
information which makes it a simple form of an algorithm for encryption. It uses a string of various
letters or a number to produce a secret key which is mixed up with a message with a plain text to
transform the composition into a given form. The transmitter and the receiver of the message must have
the key which they will use in encoding and decoding of the word.
Asymmetrical encryption
the wrong information, an assumption that a doctor may give a wrong prescription and lastly a misuse
in the MHR system may occur in a situation when the vital data is deleted from the system.
Activity 2
Cryptographic algorithms
Cryptographic algorithms are the algorithms that can be used to in an advanced method which
involves use of mathematical laws in storage and transmission of the information in specific forms
enabling only those connected can access that information as noted by Panda (2016). Symmetric and
asymmetrical are examples of the fundamental algorithms that can be used to establish secure
communication. The symmetrical encryption is a method performing ciphering and deciphering of the
information which makes it a simple form of an algorithm for encryption. It uses a string of various
letters or a number to produce a secret key which is mixed up with a message with a plain text to
transform the composition into a given form. The transmitter and the receiver of the message must have
the key which they will use in encoding and decoding of the word.
Asymmetrical encryption
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cyber Algorithms 4
Asymmetrical encryption is encoding method which encrypts a plain text in a message using two keys,
unlike symmetrical way which uses one key. Panda (2016) say on the internet or abroad connection the
two secret keys are interchanged which prohibit attackers from using the key in malicious ways. The
asymmetrical method is more secured because it uses two keys such that each anyone who wishes to
decrypt the message will need both keys. It is also called public key since it allows various senders to
send to one person who will be the only one who can access the message.
Reflection of different Cipher Substitution Algorithms
Caesar Cipher
This is the most straightforward cypher technique which involves shifting of each character in the
plaintext for a given step down the alphabet. In this case, the B will replace A and E will replace D
when a shift of 1 is performed. AtBash Substitution Cipher works in the process of replacing the
alphabets by swapping the first letter with the last such as "A" is interchanged with "Z" and "B" with
"Y". For a two-way communication to be established both parties communicating must have the key
for ciphering in that the receiver will decode the encrypted message from the sender. Therefore, to be
applied in MHR both users interacting must have a key which has the number of the alphabets to be
shifted according to Gautam et al. (2018).
To justify the use of the public and secret keys within the communication concerning the MHR system,
it will be reasonable for the communicating parties to ensure encryption of the data under transit. The
appropriate substitution algorithm will be used such as the Caesar cipher and the cryptographic
algorithms. Substitution algorithms such as Atbash and Caesar is not the most secured establishment of
the channel.
Activity 3
Recent Cryptographic Algorithm
Hash-based Message Authentication Code (HMAC) algorithm is a recently developed from
asymmetrical cryptographic functions which are more secure because it uses a double hashing
technique to encrypt a message for transit. For this reason, HMAC has been used to implement the
security of the IP as explained by Ovsienko (2014). The HMAC has the following objectives; it aims
to be, but it can quickly generate the output from the input, receive minimal effects from collisions the
normal hash functions and finally it attempts to use the most straightforward way in handling the keys.
HMAC algorithm takes a message which is comprised of words with length measured in bits. On the
left side of the message an input signature is inserted, and the combination is provided as the input of a
hash function which provides a temporary message. To obtain the final word which is a digest, the
temporary message is inserted at the end of the output signature which is then applied to the hash
function. HMAC includes a compression point in a standard hash function whereby this structure of
Asymmetrical encryption is encoding method which encrypts a plain text in a message using two keys,
unlike symmetrical way which uses one key. Panda (2016) say on the internet or abroad connection the
two secret keys are interchanged which prohibit attackers from using the key in malicious ways. The
asymmetrical method is more secured because it uses two keys such that each anyone who wishes to
decrypt the message will need both keys. It is also called public key since it allows various senders to
send to one person who will be the only one who can access the message.
Reflection of different Cipher Substitution Algorithms
Caesar Cipher
This is the most straightforward cypher technique which involves shifting of each character in the
plaintext for a given step down the alphabet. In this case, the B will replace A and E will replace D
when a shift of 1 is performed. AtBash Substitution Cipher works in the process of replacing the
alphabets by swapping the first letter with the last such as "A" is interchanged with "Z" and "B" with
"Y". For a two-way communication to be established both parties communicating must have the key
for ciphering in that the receiver will decode the encrypted message from the sender. Therefore, to be
applied in MHR both users interacting must have a key which has the number of the alphabets to be
shifted according to Gautam et al. (2018).
To justify the use of the public and secret keys within the communication concerning the MHR system,
it will be reasonable for the communicating parties to ensure encryption of the data under transit. The
appropriate substitution algorithm will be used such as the Caesar cipher and the cryptographic
algorithms. Substitution algorithms such as Atbash and Caesar is not the most secured establishment of
the channel.
Activity 3
Recent Cryptographic Algorithm
Hash-based Message Authentication Code (HMAC) algorithm is a recently developed from
asymmetrical cryptographic functions which are more secure because it uses a double hashing
technique to encrypt a message for transit. For this reason, HMAC has been used to implement the
security of the IP as explained by Ovsienko (2014). The HMAC has the following objectives; it aims
to be, but it can quickly generate the output from the input, receive minimal effects from collisions the
normal hash functions and finally it attempts to use the most straightforward way in handling the keys.
HMAC algorithm takes a message which is comprised of words with length measured in bits. On the
left side of the message an input signature is inserted, and the combination is provided as the input of a
hash function which provides a temporary message. To obtain the final word which is a digest, the
temporary message is inserted at the end of the output signature which is then applied to the hash
function. HMAC includes a compression point in a standard hash function whereby this structure of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber Algorithms 5
implementing algorithms is useful for Message Authentication Code (MAC) values which are short.
HMAC uses the two computations of the function that is the secret key which is the first key that is
used to generate the inner and the outer keys. To create the internal hash, the first pass is used which is
formed from the secret key and the message. Finally, the HMAC code is produced by the outer key
which gives the best security against the extension of length attacks.
Recommendation
Having studied the MHR system and the full analysis of the security of the system, more secured
cryptographic algorithms will have to be implemented to secure the MHR system fully. The
asymmetrical algorithm will be more suitable to be used due to its advanced security capabilities and
the ability to secure communication between the users of the MHR system. Implementation of hash-
based message authentication code which not only verifies that integrity of the data but also message
authenticity in every MAC. This approaches will help reduce the cases of the misuse cases of the MHR
system.
Conclusions
Implementation of the cybersecurity to protect the network and the communication between the users
of the MHR system against the malicious attackers. Cryptographic algorithms that can be used are
symmetrical, and the asymmetrical, asymmetrical is more secure because it uses two secret keys which
must be possessed by those in communication. The use case describes what the actors of the MHR
system will perform on the system while the misuse cases will occur when any of the users such as the
doctors or the patients act maliciously to the system. The most recent cryptographic algorithm such as
the HMAC is the most immune algorithm to the malicious people who employ the double hashing
techniques, and it uses to key which closely resembles the asymmetrical algorithm.
implementing algorithms is useful for Message Authentication Code (MAC) values which are short.
HMAC uses the two computations of the function that is the secret key which is the first key that is
used to generate the inner and the outer keys. To create the internal hash, the first pass is used which is
formed from the secret key and the message. Finally, the HMAC code is produced by the outer key
which gives the best security against the extension of length attacks.
Recommendation
Having studied the MHR system and the full analysis of the security of the system, more secured
cryptographic algorithms will have to be implemented to secure the MHR system fully. The
asymmetrical algorithm will be more suitable to be used due to its advanced security capabilities and
the ability to secure communication between the users of the MHR system. Implementation of hash-
based message authentication code which not only verifies that integrity of the data but also message
authenticity in every MAC. This approaches will help reduce the cases of the misuse cases of the MHR
system.
Conclusions
Implementation of the cybersecurity to protect the network and the communication between the users
of the MHR system against the malicious attackers. Cryptographic algorithms that can be used are
symmetrical, and the asymmetrical, asymmetrical is more secure because it uses two secret keys which
must be possessed by those in communication. The use case describes what the actors of the MHR
system will perform on the system while the misuse cases will occur when any of the users such as the
doctors or the patients act maliciously to the system. The most recent cryptographic algorithm such as
the HMAC is the most immune algorithm to the malicious people who employ the double hashing
techniques, and it uses to key which closely resembles the asymmetrical algorithm.

Cyber Algorithms 6
Reference
Gautam, D., Agrawal, C., Sharma, P., Mehta, M. and Saini, P., 2018, May. An Enhanced Cipher
Technique Using Vigenere and Modified Caesar Cipher. In 2018 2nd International Conference on
Trends in Electronics and Informatics (ICOEI)(pp. 1-9). IEEE.
Jacobson, I., Spence, I. and Kerr, B., 2016. Use-Case 2.0. Commun. ACM, 59(5), pp.61-69.
Ovsienko, D., 2014. Babel Hashed Message Authentication Code (HMAC) Cryptographic
Authentication (No. RFC 7298).
Panda, M., 2016, October. Performance analysis of encryption algorithms for security. In 2016
International Conference on Signal Processing, Communication, Power and Embedded System
(SCOPES) (pp. 278-284). IEEE.
Yoo, S.G., Vaca, H.P. and Kim, J., 2017, October. Enhanced Misuse Cases for Prioritization of
Security Requirements. In Proceedings of the 9th International Conference on Information
Management and Engineering (pp. 1-10). ACM.
Yamaguchi, Y., Ogawa, A., Takeda, A. and Iwata, S., 2015. Cybersecurity analysis of power networks
by hypergraph cut algorithms. IEEE Transactions on Smart Grid, 6(5), pp.2189-2199.
Reference
Gautam, D., Agrawal, C., Sharma, P., Mehta, M. and Saini, P., 2018, May. An Enhanced Cipher
Technique Using Vigenere and Modified Caesar Cipher. In 2018 2nd International Conference on
Trends in Electronics and Informatics (ICOEI)(pp. 1-9). IEEE.
Jacobson, I., Spence, I. and Kerr, B., 2016. Use-Case 2.0. Commun. ACM, 59(5), pp.61-69.
Ovsienko, D., 2014. Babel Hashed Message Authentication Code (HMAC) Cryptographic
Authentication (No. RFC 7298).
Panda, M., 2016, October. Performance analysis of encryption algorithms for security. In 2016
International Conference on Signal Processing, Communication, Power and Embedded System
(SCOPES) (pp. 278-284). IEEE.
Yoo, S.G., Vaca, H.P. and Kim, J., 2017, October. Enhanced Misuse Cases for Prioritization of
Security Requirements. In Proceedings of the 9th International Conference on Information
Management and Engineering (pp. 1-10). ACM.
Yamaguchi, Y., Ogawa, A., Takeda, A. and Iwata, S., 2015. Cybersecurity analysis of power networks
by hypergraph cut algorithms. IEEE Transactions on Smart Grid, 6(5), pp.2189-2199.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





