European University Cyprus: CYS625X Cryptography Homework Solution
VerifiedAdded on 2022/08/30
|12
|2602
|34
Homework Assignment
AI Summary
This document provides a comprehensive solution to a cryptography homework assignment, addressing key concepts such as Chaffing and Winnowing, encryption algorithms, one-time pads, and Kerckhoff's principle. The assignment explores symmetric-key cryptography, including its advantages and disadvantages, and differentiates between shift, mono-alphabetic, and poly-alphabetic ciphers. It further explains perfect secrecy, computational security, and pseudo-random number generators (PRNGs). The document also delves into stream ciphers, confidentiality, integrity, message authentication codes (MACs), hash functions, password hashing techniques, and key distribution centers (KDCs). This assignment offers a detailed overview of fundamental cryptographic principles and their practical applications.

Running head: BASICS OF CRYPTOGRAPHY
BASICS OF CRYPTOGRAPHY
Name of the student:
Name of the university:
Author Note:
BASICS OF CRYPTOGRAPHY
Name of the student:
Name of the university:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1BASICS OF CRYPTOGRAPHY
Table of Contents
Answer 1:...................................................................................................................................2
Answer 2:...................................................................................................................................2
Answer 3:...................................................................................................................................3
Answer 4:...................................................................................................................................3
Answer 5:...................................................................................................................................4
Answer 6:...................................................................................................................................5
Answer 7:...................................................................................................................................5
Answer 8:...................................................................................................................................5
Answer 9:...................................................................................................................................6
Answer 10:.................................................................................................................................6
Answer 11:.................................................................................................................................7
Answer 12:.................................................................................................................................7
Answer 13:.................................................................................................................................7
Answer 14:.................................................................................................................................8
Answer 15:.................................................................................................................................8
Answer 16:.................................................................................................................................8
References..................................................................................................................................9
Table of Contents
Answer 1:...................................................................................................................................2
Answer 2:...................................................................................................................................2
Answer 3:...................................................................................................................................3
Answer 4:...................................................................................................................................3
Answer 5:...................................................................................................................................4
Answer 6:...................................................................................................................................5
Answer 7:...................................................................................................................................5
Answer 8:...................................................................................................................................5
Answer 9:...................................................................................................................................6
Answer 10:.................................................................................................................................6
Answer 11:.................................................................................................................................7
Answer 12:.................................................................................................................................7
Answer 13:.................................................................................................................................7
Answer 14:.................................................................................................................................8
Answer 15:.................................................................................................................................8
Answer 16:.................................................................................................................................8
References..................................................................................................................................9
2BASICS OF CRYPTOGRAPHY
Answer 1:
The terms ‘Chaffing’ and ‘Winnowing’ defines a cryptographic technique that is
applied for security while sending messages from the sender to the receiver without the help
of the encryption and decryption of the messages. False packets are used in this procedure
along with the actual messages. Chaffing is the process where each legitimate message packet
as well as the false packet have a serial number and a MAC (message authentication code)
associated with it (Samid 2018). Winnowing is referred to the process when the invalid MAC
numbers are discarded and the valid MAC numbers are considered as that implies the actual
messages.
Serial Number Transmitted Packet MAC Code Status
1 I am 4j850k3 valid
1 I am 8dF7j89 invalid
2 Reading a book 79Kdu65p7 valid
2 Reading a book 65Dhu34l7 invalid
3 Called ‘Jack Reaper’ 9Oph12Dfhk6 valid
3 Called ‘Jack
Reaper’
4Fgh23Cytk5 invalid
However, the chaffing must be identical to the actual messages because here the
language of the message is English. If the false message is anything random, then the actual
message can be easily reconstructed.
Answer 1:
The terms ‘Chaffing’ and ‘Winnowing’ defines a cryptographic technique that is
applied for security while sending messages from the sender to the receiver without the help
of the encryption and decryption of the messages. False packets are used in this procedure
along with the actual messages. Chaffing is the process where each legitimate message packet
as well as the false packet have a serial number and a MAC (message authentication code)
associated with it (Samid 2018). Winnowing is referred to the process when the invalid MAC
numbers are discarded and the valid MAC numbers are considered as that implies the actual
messages.
Serial Number Transmitted Packet MAC Code Status
1 I am 4j850k3 valid
1 I am 8dF7j89 invalid
2 Reading a book 79Kdu65p7 valid
2 Reading a book 65Dhu34l7 invalid
3 Called ‘Jack Reaper’ 9Oph12Dfhk6 valid
3 Called ‘Jack
Reaper’
4Fgh23Cytk5 invalid
However, the chaffing must be identical to the actual messages because here the
language of the message is English. If the false message is anything random, then the actual
message can be easily reconstructed.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3BASICS OF CRYPTOGRAPHY
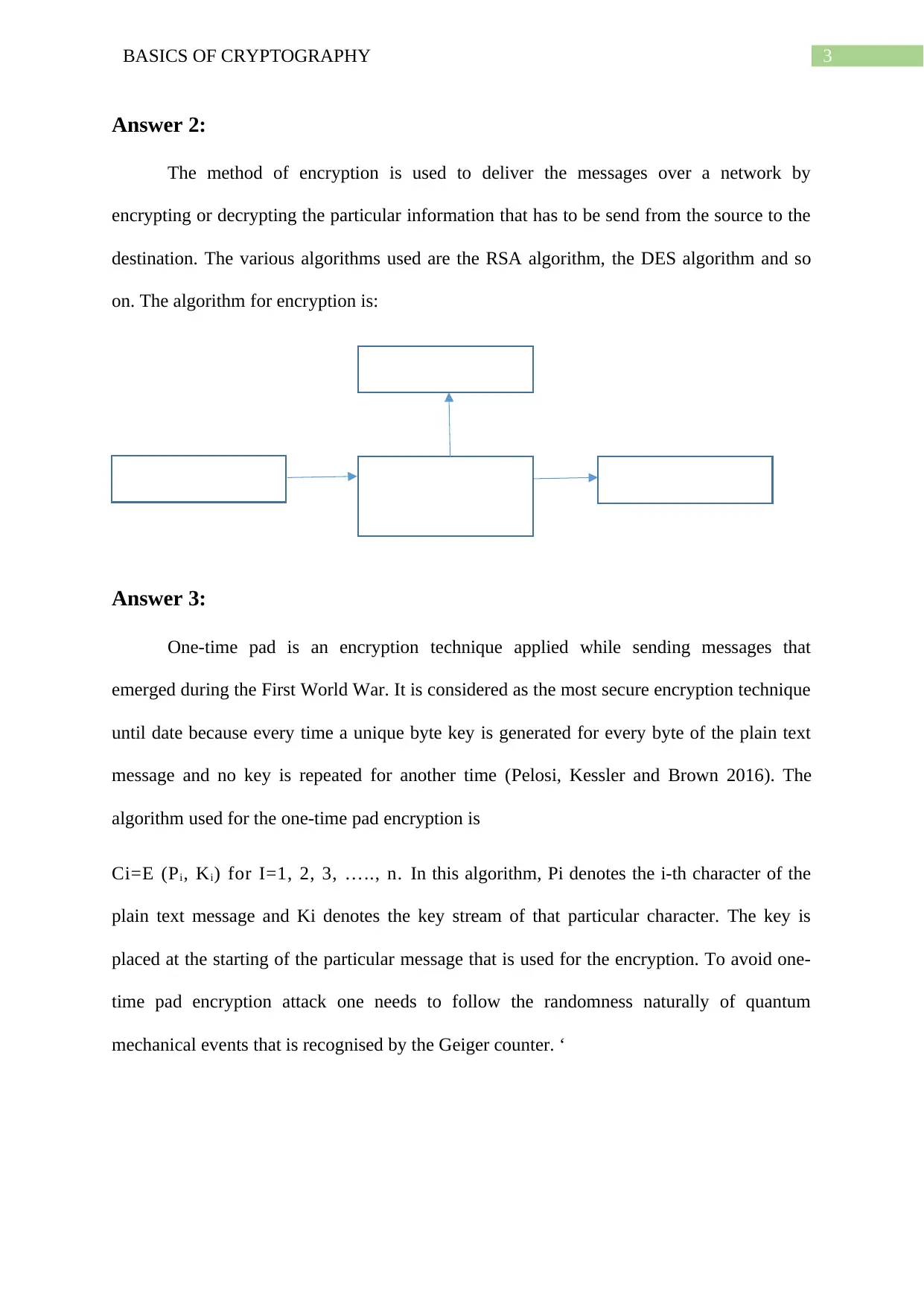
Answer 2:
The method of encryption is used to deliver the messages over a network by
encrypting or decrypting the particular information that has to be send from the source to the
destination. The various algorithms used are the RSA algorithm, the DES algorithm and so
on. The algorithm for encryption is:
Answer 3:
One-time pad is an encryption technique applied while sending messages that
emerged during the First World War. It is considered as the most secure encryption technique
until date because every time a unique byte key is generated for every byte of the plain text
message and no key is repeated for another time (Pelosi, Kessler and Brown 2016). The
algorithm used for the one-time pad encryption is
Ci=E (Pi, Ki) for I=1, 2, 3, ….., n. In this algorithm, Pi denotes the i-th character of the
plain text message and Ki denotes the key stream of that particular character. The key is
placed at the starting of the particular message that is used for the encryption. To avoid one-
time pad encryption attack one needs to follow the randomness naturally of quantum
mechanical events that is recognised by the Geiger counter. ‘
Cryptographic Key
Plain text Message Cryptographic
Algorithm
Encrypted Message
Answer 2:
The method of encryption is used to deliver the messages over a network by
encrypting or decrypting the particular information that has to be send from the source to the
destination. The various algorithms used are the RSA algorithm, the DES algorithm and so
on. The algorithm for encryption is:
Answer 3:
One-time pad is an encryption technique applied while sending messages that
emerged during the First World War. It is considered as the most secure encryption technique
until date because every time a unique byte key is generated for every byte of the plain text
message and no key is repeated for another time (Pelosi, Kessler and Brown 2016). The
algorithm used for the one-time pad encryption is
Ci=E (Pi, Ki) for I=1, 2, 3, ….., n. In this algorithm, Pi denotes the i-th character of the
plain text message and Ki denotes the key stream of that particular character. The key is
placed at the starting of the particular message that is used for the encryption. To avoid one-
time pad encryption attack one needs to follow the randomness naturally of quantum
mechanical events that is recognised by the Geiger counter. ‘
Cryptographic Key
Plain text Message Cryptographic
Algorithm
Encrypted Message
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4BASICS OF CRYPTOGRAPHY
Answer 4:
Kerckhoff’s principle states that ‘a cryptosystem should be secure even if everything
about the system, except the key, is public knowledge’. The cryptographer Auguste
Kerckhoff stated this law (Knoll 2018). This principle is important for the cryptographic
systems because it gives a practical approach in their methodology. According to this
principle, the system should be practically indecipherable. Although the enemy attacks the
system, he should not be able to crack the system conveniently. The correspondents should be
able to modify the key or derive it without any help of documentation. The system should be
easy to use without involving innumerable people in it and telegraphic correspondence should
be applicable.
Answer 5:
The encryption methodology used to encrypt or decrypt data both by using a single
key is known as the symmetric encryption. This secret key is applied to the message that has
to be delivered and can be of any form- either number or letters. It can be shared only
between the sender and the receiver (Ilayaraja, Shankar and Devika 2017). The message is
first encrypted and a key is associated along with it while sending to the receiver. The
receiver decrypts the message using the same key.
Hello Alice ! Encrypt Message
6EB695708E03C
E4
Decrypt MessageHello Alice!
Secret Key
Answer 4:
Kerckhoff’s principle states that ‘a cryptosystem should be secure even if everything
about the system, except the key, is public knowledge’. The cryptographer Auguste
Kerckhoff stated this law (Knoll 2018). This principle is important for the cryptographic
systems because it gives a practical approach in their methodology. According to this
principle, the system should be practically indecipherable. Although the enemy attacks the
system, he should not be able to crack the system conveniently. The correspondents should be
able to modify the key or derive it without any help of documentation. The system should be
easy to use without involving innumerable people in it and telegraphic correspondence should
be applicable.
Answer 5:
The encryption methodology used to encrypt or decrypt data both by using a single
key is known as the symmetric encryption. This secret key is applied to the message that has
to be delivered and can be of any form- either number or letters. It can be shared only
between the sender and the receiver (Ilayaraja, Shankar and Devika 2017). The message is
first encrypted and a key is associated along with it while sending to the receiver. The
receiver decrypts the message using the same key.
Hello Alice ! Encrypt Message
6EB695708E03C
E4
Decrypt MessageHello Alice!
Secret Key

5BASICS OF CRYPTOGRAPHY
The advantageous part is that this encryption technique works fast and can be used for large
amount of data. However, managing the key is prone to attacks and the data will be at stake if
the key is lost.
Answer 6:
The shift cipher key is an encryption key that uses a modulo operator for encrypting
and decrypting messages. An example of shift cipher is the Caesar cipher (Oktaviana and
Siahaan 2016). The key used in this cipher uses only integer values from zero to 25.
By the name of mono-alphabetic cipher, it is clearly visible that the alphabets are used
in forming the key of the encryption only alphabets are used. Although the letters and
alphabets are mixed up with each other, the arrangement is kept same throughout the
message.
In poly-alphabetic cipher, there exists substitution of multiple alphabets for a single
text message. Caesar cipher can be implemented multiple times to generate a poly-alphabetic
cipher.
Answer 7:
Perfect secrecy is a method used for encrypting messages such that no message is
revealed neither about the cipher text nor about the key used in the encryption of the
message. No matter what the scheme is and how long the plain-text are, by this perfect
secrecy method, one can hide and maintain secrecy about all types information associated
with the encryption.
In perfect secrecy, P (M=m | C=c) = P (M=m), the probability of seeing a message
‘m’, is same as the probability of seeing a cipher text. Again, P (C=c |M=m0) = P (C=c |
The advantageous part is that this encryption technique works fast and can be used for large
amount of data. However, managing the key is prone to attacks and the data will be at stake if
the key is lost.
Answer 6:
The shift cipher key is an encryption key that uses a modulo operator for encrypting
and decrypting messages. An example of shift cipher is the Caesar cipher (Oktaviana and
Siahaan 2016). The key used in this cipher uses only integer values from zero to 25.
By the name of mono-alphabetic cipher, it is clearly visible that the alphabets are used
in forming the key of the encryption only alphabets are used. Although the letters and
alphabets are mixed up with each other, the arrangement is kept same throughout the
message.
In poly-alphabetic cipher, there exists substitution of multiple alphabets for a single
text message. Caesar cipher can be implemented multiple times to generate a poly-alphabetic
cipher.
Answer 7:
Perfect secrecy is a method used for encrypting messages such that no message is
revealed neither about the cipher text nor about the key used in the encryption of the
message. No matter what the scheme is and how long the plain-text are, by this perfect
secrecy method, one can hide and maintain secrecy about all types information associated
with the encryption.
In perfect secrecy, P (M=m | C=c) = P (M=m), the probability of seeing a message
‘m’, is same as the probability of seeing a cipher text. Again, P (C=c |M=m0) = P (C=c |
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6BASICS OF CRYPTOGRAPHY
M=m1), the probability of the cipher text can be two different messages (Karpuk and Chorti
2016). The key can be of the same length as the message and is unique with probability 1/|K|.
Answer 8:
Computational security involves an asymptotic approach for encrypting messages
irrespective of the keys generated, whether long or short. If the length of the key is of size n,
then it will take 2n times to run the C program of encryption (Doerner and Shelat 2017,
October). Here, n acts as the security parameter of the cryptographic scheme. The running
time of the adversary as well as the probability of success is considered as a function of the
parameter. Both the parties choose the same value of n as their parameter of security. For the
feasible strategy, considering the constants a, c, the run time of the algorithm is a.nc. For the
success probability to be less, for the constant c, the success probability is n-c, for the larger
values of n.
Answer 9:
The computational security approach can be divided into two types: the concrete
approach and the provable security or the asymptotic approach. In the former one, the
approach is practise oriented, and aims to give the complexities of the adversarial tasks.
However, in the later one, it uses the polynomial time reducibility to elaborate the problems
of the computational problems (Archer et al. 2016 ). If the length of the key is n and has an
adversary time t, then in concrete approach the probability is 2n, where as in asymptotic
approach, the probability is 2-n.
Answer 10:
The algorithm that is used to generate sequence of random numbers with the help of
mathematical formulas is known as the Pseudo Random Number Generator. A sequence of
M=m1), the probability of the cipher text can be two different messages (Karpuk and Chorti
2016). The key can be of the same length as the message and is unique with probability 1/|K|.
Answer 8:
Computational security involves an asymptotic approach for encrypting messages
irrespective of the keys generated, whether long or short. If the length of the key is of size n,
then it will take 2n times to run the C program of encryption (Doerner and Shelat 2017,
October). Here, n acts as the security parameter of the cryptographic scheme. The running
time of the adversary as well as the probability of success is considered as a function of the
parameter. Both the parties choose the same value of n as their parameter of security. For the
feasible strategy, considering the constants a, c, the run time of the algorithm is a.nc. For the
success probability to be less, for the constant c, the success probability is n-c, for the larger
values of n.
Answer 9:
The computational security approach can be divided into two types: the concrete
approach and the provable security or the asymptotic approach. In the former one, the
approach is practise oriented, and aims to give the complexities of the adversarial tasks.
However, in the later one, it uses the polynomial time reducibility to elaborate the problems
of the computational problems (Archer et al. 2016 ). If the length of the key is n and has an
adversary time t, then in concrete approach the probability is 2n, where as in asymptotic
approach, the probability is 2-n.
Answer 10:
The algorithm that is used to generate sequence of random numbers with the help of
mathematical formulas is known as the Pseudo Random Number Generator. A sequence of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7BASICS OF CRYPTOGRAPHY
numbers is generated using the properties of random numbers in the PRNG algorithm
(Couteau et al. 2018, December). The PRNG algorithm uses a seed state to start from a
random initial state. The generator that is used is defined by the recursive relation Xn+1 = (aXn
+ c) mod m, signifying X to be the sequence of the values that are pseudo random. The ‘m’
represents the modulus, ‘a’ as the multiplier, ‘c’ as the increment value and x0 as the seed
value by which the numbers are generated.
Answer 11:
Self-synchronizing stream ciphers are advantageous than synchronous ciphers in
various aspects. In synchronous stream ciphers, the sender should be synchronised with the
receiver that is not necessary for the self-synchronising stream ciphers. In the synchronous
stream ciphers there might be loss of synchronization, during the insertion and the deletion
process. Whereas, in self-synchronising stream ciphers at most t digits might be lost during
the insertion or deletion. Modified digits does not matter in the process of decryption of other
digits in the synchronous stream ciphers unlike the self-synchronising stream ciphers where
even modification of one digit leads to wrong decryption.
Answer 12:
Confidentiality is the termed referred to keeping something secret of protecting any
information from being leaked out by the hackers. Any cryptographic system allows only the
authorised users to access the data of the system. The secrecy maintained by the
cryptographic systems involves algorithms to protect the data inside it. Integrity of the
information refers to maintaining the authenticity of the information and it is an effect of the
confidentiality maintained by the system. For example, if anyone deposits an amount in the
bank and it is not updated, the integrity is not maintained. However, the secrecy about the
transaction is not leaked.
numbers is generated using the properties of random numbers in the PRNG algorithm
(Couteau et al. 2018, December). The PRNG algorithm uses a seed state to start from a
random initial state. The generator that is used is defined by the recursive relation Xn+1 = (aXn
+ c) mod m, signifying X to be the sequence of the values that are pseudo random. The ‘m’
represents the modulus, ‘a’ as the multiplier, ‘c’ as the increment value and x0 as the seed
value by which the numbers are generated.
Answer 11:
Self-synchronizing stream ciphers are advantageous than synchronous ciphers in
various aspects. In synchronous stream ciphers, the sender should be synchronised with the
receiver that is not necessary for the self-synchronising stream ciphers. In the synchronous
stream ciphers there might be loss of synchronization, during the insertion and the deletion
process. Whereas, in self-synchronising stream ciphers at most t digits might be lost during
the insertion or deletion. Modified digits does not matter in the process of decryption of other
digits in the synchronous stream ciphers unlike the self-synchronising stream ciphers where
even modification of one digit leads to wrong decryption.
Answer 12:
Confidentiality is the termed referred to keeping something secret of protecting any
information from being leaked out by the hackers. Any cryptographic system allows only the
authorised users to access the data of the system. The secrecy maintained by the
cryptographic systems involves algorithms to protect the data inside it. Integrity of the
information refers to maintaining the authenticity of the information and it is an effect of the
confidentiality maintained by the system. For example, if anyone deposits an amount in the
bank and it is not updated, the integrity is not maintained. However, the secrecy about the
transaction is not leaked.

8BASICS OF CRYPTOGRAPHY
Answer 13:
The modifications that are done on the data whether intentionally or unintentionally
are checked by the cryptographic checksum applied on the data by using a session key. This
checksum is called the Message Authentication Code or MAC (Wu et al. 2016). The MAC
uses two components, a message and a secret key, which allows the receiver to check the
authenticity and integrity of the message.
Answer 14:
The mathematical equations or the set of formulas that are used to for encrypting
message while sending them through a network are called hash functions. They are
computationally efficient in nature (Hayashi and Tsurumaru 2016). Two classes of hash
functions are Secure Hashing Algorithm and the Message Digest Algorithm. The functions
that are irreversible and can be used in a single way is called one-way hash function. The
one-way hash functions use the simple modular functions. It is very rare to find two different
inputs giving the same hash output. This is a case of collision resistant hash function.
Answer 15:
Password Hashing is a technique by which hash functions are applied on the
passwords to encrypt and hide them for security reasons. The different types of password
attacks are password guessing, password resetting, password cracking and password
capturing (Rivest and Schuldt 2016). There exists different kind of tools that are used to hack
these passwords. Hence, firewall and security should be implemented to prevent such attacks.
Answer 16:
The system that is used to provide keys to the users of a network for sharing data is
known as the key distribution centre or KDC. When the two systems are connected, both the
Answer 13:
The modifications that are done on the data whether intentionally or unintentionally
are checked by the cryptographic checksum applied on the data by using a session key. This
checksum is called the Message Authentication Code or MAC (Wu et al. 2016). The MAC
uses two components, a message and a secret key, which allows the receiver to check the
authenticity and integrity of the message.
Answer 14:
The mathematical equations or the set of formulas that are used to for encrypting
message while sending them through a network are called hash functions. They are
computationally efficient in nature (Hayashi and Tsurumaru 2016). Two classes of hash
functions are Secure Hashing Algorithm and the Message Digest Algorithm. The functions
that are irreversible and can be used in a single way is called one-way hash function. The
one-way hash functions use the simple modular functions. It is very rare to find two different
inputs giving the same hash output. This is a case of collision resistant hash function.
Answer 15:
Password Hashing is a technique by which hash functions are applied on the
passwords to encrypt and hide them for security reasons. The different types of password
attacks are password guessing, password resetting, password cracking and password
capturing (Rivest and Schuldt 2016). There exists different kind of tools that are used to hack
these passwords. Hence, firewall and security should be implemented to prevent such attacks.
Answer 16:
The system that is used to provide keys to the users of a network for sharing data is
known as the key distribution centre or KDC. When the two systems are connected, both the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9BASICS OF CRYPTOGRAPHY
systems share a common KDC password and thus the data is shared between them (Han et al.
2019). One advantage of this system is that the chance of being attacked by the hacker is less.
However, if the KDC fails to transfer data, all the users will be affected.
systems share a common KDC password and thus the data is shared between them (Han et al.
2019). One advantage of this system is that the chance of being attacked by the hacker is less.
However, if the KDC fails to transfer data, all the users will be affected.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10BASICS OF CRYPTOGRAPHY
References
Archer, D.W., Bogdanov, D., Pinkas, B. and Pullonen, P., 2016. Maturity and performance of
programmable secure computation. IEEE security & privacy, 14(5), pp.48-56.
Couteau, G., Dupin, A., Méaux, P., Rossi, M. and Rotella, Y., 2018, December. On the
concrete security of Goldreich’s pseudorandom generator. In International Conference on the
Theory and Application of Cryptology and Information Security (pp. 96-124). Springer,
Cham.
Doerner, J. and Shelat, A., 2017, October. Scaling ORAM for secure computation.
In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications
Security (pp. 523-535). ACM.
Han, Q.I.U., Meikang, Q.I.U., Zhihui, L.U. and Memmi, G., 2019. An efficient key
distribution system for data fusion in V2X heterogeneous networks. Information Fusion, 50,
pp.212-220.
Hayashi, M. and Tsurumaru, T., 2016. More efficient privacy amplification with less random
seeds via dual universal hash function. IEEE Transactions on Information Theory, 62(4),
pp.2213-2232.
Ilayaraja, M., Shankar, K. and Devika, G., 2017. A modified symmetric key cryptography
method for secure data transmission. International Journal of Pure and Applied
Mathematics, 116(10), pp.301-308.
Karpuk, D.A. and Chorti, A., 2016. Perfect secrecy in physical-layer network coding systems
from structured interference. IEEE Transactions on Information Forensics and
Security, 11(8), pp.1875-1887.
References
Archer, D.W., Bogdanov, D., Pinkas, B. and Pullonen, P., 2016. Maturity and performance of
programmable secure computation. IEEE security & privacy, 14(5), pp.48-56.
Couteau, G., Dupin, A., Méaux, P., Rossi, M. and Rotella, Y., 2018, December. On the
concrete security of Goldreich’s pseudorandom generator. In International Conference on the
Theory and Application of Cryptology and Information Security (pp. 96-124). Springer,
Cham.
Doerner, J. and Shelat, A., 2017, October. Scaling ORAM for secure computation.
In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications
Security (pp. 523-535). ACM.
Han, Q.I.U., Meikang, Q.I.U., Zhihui, L.U. and Memmi, G., 2019. An efficient key
distribution system for data fusion in V2X heterogeneous networks. Information Fusion, 50,
pp.212-220.
Hayashi, M. and Tsurumaru, T., 2016. More efficient privacy amplification with less random
seeds via dual universal hash function. IEEE Transactions on Information Theory, 62(4),
pp.2213-2232.
Ilayaraja, M., Shankar, K. and Devika, G., 2017. A modified symmetric key cryptography
method for secure data transmission. International Journal of Pure and Applied
Mathematics, 116(10), pp.301-308.
Karpuk, D.A. and Chorti, A., 2016. Perfect secrecy in physical-layer network coding systems
from structured interference. IEEE Transactions on Information Forensics and
Security, 11(8), pp.1875-1887.

11BASICS OF CRYPTOGRAPHY
Knoll, T., 2018. Adapting Kerckhoffs’s principle. Advanced Microkernel Operating Systems,
p.93.
Oktaviana, B. and Siahaan, A.P.U., 2016. Three-Pass Protocol Implementation in Caesar
Cipher Classic Cryptography. IOSR Journal of Computer Engineering, 18(4), pp.26-29.
Pelosi, M.J., Kessler, G. and Brown, M.S.S., 2016. One-Time Pad Encryption Steganography
System.
Rivest, R.L. and Schuldt, J.C., 2016. Spritz-a spongy RC4-like stream cipher and hash
function. IACR Cryptology ePrint Archive, 2016, p.856.
Samid, G., 2018. Rivest Chaffing and Winnowing Cryptography Elevated into a Full-Fledged
Cryptographic Strategy. In Proceedings of the International Conference on e-Learning, e-
Business, Enterprise Information Systems, and e-Government (EEE) (pp. 76-80). The
Steering Committee of The World Congress in Computer Science, Computer Engineering
and Applied Computing (WorldComp).
Wu, X., Yang, Z., Ling, C. and Xia, X.G., 2016. Artificial-noise-aided message
authentication codes with information-theoretic security. IEEE Transactions on Information
Forensics and Security, 11(6), pp.1278-1290.
Knoll, T., 2018. Adapting Kerckhoffs’s principle. Advanced Microkernel Operating Systems,
p.93.
Oktaviana, B. and Siahaan, A.P.U., 2016. Three-Pass Protocol Implementation in Caesar
Cipher Classic Cryptography. IOSR Journal of Computer Engineering, 18(4), pp.26-29.
Pelosi, M.J., Kessler, G. and Brown, M.S.S., 2016. One-Time Pad Encryption Steganography
System.
Rivest, R.L. and Schuldt, J.C., 2016. Spritz-a spongy RC4-like stream cipher and hash
function. IACR Cryptology ePrint Archive, 2016, p.856.
Samid, G., 2018. Rivest Chaffing and Winnowing Cryptography Elevated into a Full-Fledged
Cryptographic Strategy. In Proceedings of the International Conference on e-Learning, e-
Business, Enterprise Information Systems, and e-Government (EEE) (pp. 76-80). The
Steering Committee of The World Congress in Computer Science, Computer Engineering
and Applied Computing (WorldComp).
Wu, X., Yang, Z., Ling, C. and Xia, X.G., 2016. Artificial-noise-aided message
authentication codes with information-theoretic security. IEEE Transactions on Information
Forensics and Security, 11(6), pp.1278-1290.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

