Cryptography in Information Security: Challenges and Applications
VerifiedAdded on 2021/05/30
|8
|3872
|245
Report
AI Summary
This report provides a comprehensive overview of cryptography techniques and their applications in information security. It begins with an introduction to cryptography, highlighting its importance in securing sensitive data transmitted over networks and stored in various locations. The report addresses the research problem of data leakage and unauthorized access, emphasizing cryptography's role in ensuring data confidentiality and integrity. It then delves into the different types of cryptography, including symmetric, asymmetric, and cryptographic hash functions, detailing their functions, strengths, and weaknesses. The report further explores the applications of cryptography in various fields, such as email security, electronic money transfer, secure communication, and digital signatures. It also reviews the challenges and risks associated with cryptography, including interruption, interception, and fabrication. The report concludes by discussing the future of cryptography, the impact of quantum computation, and the increasing importance of cyber security, while also addressing potential attacks and the purpose of cryptography in maintaining authentication, confidentiality, integrity, and non-repudiation.

Information SecurityABSTRACT – This document depicts the limelight on
cryptography techniques. The use of cryptography in
various technologies and its challenges has been
discussed. There are various challenges associated with
cryptography techniques that have been underlined in this
article.Keywords— Cryptography, encryption, secret keys,
networking channels, unauthorized users.
INTRODUCTION
Cryptography techniques have been used to secure the
sensitive data before transmitting over the network. The
data are transmitted via internet and stored in such a way
that it is accessible from anywhere. There are chances of
data leakage through network that may breach the
security of data as it directly affects the privacy of
information. To make sure that even if data gets leaked
due to some bugs the information is not in a readable
format. To assure that the data leakage will no cause
leakage of actual information cryptography techniques are
used.
A. Research problem
Most of the information is shared over internet, thus it is
possible that some third part access the information. To
avoid such cases cryptography is used as it provides
verification that the data is sent by correct user and also
make sure that information is delivered to valid user.
Overview of Cryptography
Cryptography techniques are used to improve the security
of information so that users can make use of availability of
applications on the network as all the applications uses
high quality of cryptography technology. These are
basically used to get secure communication as it is
necessary to keep the information confidential. Some
basics functions that are covered in cryptography
technique are encryption and decryption (Staff, 2015).
Encryption means transforming the actual text of data in
the form that is not readable by humans and decryption is
getting back the text in a human readable form (Lin, 2015).
This technology requires the uses of secret key. This can
be assumed as a password without it the actual data will
not be unlocked. The password is shared only between
actual sender and receiver.
There are basically three forms of cryptography
techniques and they are used at different point of time.
Symmetric, asymmetric and cryptographic hash functions
are three forms and all make use of a secret key (Jisc,
2018). The strength of the cryptography algorithm is
directly related to the length of key. In case of symmetric
cryptography algorithm same key need to be used for
encrypting and decrypting the data. The advantage of
using this method is speed of transmission. There are
several issues associated with the symmetric cryptography
that is every channel needs a separate secret key and
sometimes it doesn’t provide authenticity of the data
(Rivest, Shamir & Adleman, 2013). It creates the problem
of sharing the key to long distance.
Asymmetric cryptography uses the method of public and
private keys. It provides better security as compared to
symmetric cryptography as it assures that authenticity of
data packets is met. However, it lowers the speed of
transmission of data packets and also utilizes more
number of resources (Tassel, 2016). The increasing use of
cryptography technology has raised various risks as it can
be used in some legal copyright issues. Additionally,
cryptography gives the right to have secret
communication which leads to increase in criminal
activities (Wilkins, Keefe & Rehman, 2015).
Cryptography technology is one of the essential
techniques used for building secure VPN. It assures that
messages are received securely to the end users this is
done by using the secret. It makes sure that two entities
can have secure communication on the network by
encrypting the message. The complete process includes
encrypting the text message by using the public key, and
then the message is forwarded in the network channels
(Chaudhry, Farash, Naqvi & Sher, 2016). The encrypted
message could not be read by any third party user and it
will only get decrypted by using private key that is known
only to the valid receiver and it has not been disclosed on
the entire network. The intended user will get the data
packets from the channel and will decrypt the encrypted
text and read the original message. This guarantees that
cryptography techniques. The use of cryptography in
various technologies and its challenges has been
discussed. There are various challenges associated with
cryptography techniques that have been underlined in this
article.Keywords— Cryptography, encryption, secret keys,
networking channels, unauthorized users.
INTRODUCTION
Cryptography techniques have been used to secure the
sensitive data before transmitting over the network. The
data are transmitted via internet and stored in such a way
that it is accessible from anywhere. There are chances of
data leakage through network that may breach the
security of data as it directly affects the privacy of
information. To make sure that even if data gets leaked
due to some bugs the information is not in a readable
format. To assure that the data leakage will no cause
leakage of actual information cryptography techniques are
used.
A. Research problem
Most of the information is shared over internet, thus it is
possible that some third part access the information. To
avoid such cases cryptography is used as it provides
verification that the data is sent by correct user and also
make sure that information is delivered to valid user.
Overview of Cryptography
Cryptography techniques are used to improve the security
of information so that users can make use of availability of
applications on the network as all the applications uses
high quality of cryptography technology. These are
basically used to get secure communication as it is
necessary to keep the information confidential. Some
basics functions that are covered in cryptography
technique are encryption and decryption (Staff, 2015).
Encryption means transforming the actual text of data in
the form that is not readable by humans and decryption is
getting back the text in a human readable form (Lin, 2015).
This technology requires the uses of secret key. This can
be assumed as a password without it the actual data will
not be unlocked. The password is shared only between
actual sender and receiver.
There are basically three forms of cryptography
techniques and they are used at different point of time.
Symmetric, asymmetric and cryptographic hash functions
are three forms and all make use of a secret key (Jisc,
2018). The strength of the cryptography algorithm is
directly related to the length of key. In case of symmetric
cryptography algorithm same key need to be used for
encrypting and decrypting the data. The advantage of
using this method is speed of transmission. There are
several issues associated with the symmetric cryptography
that is every channel needs a separate secret key and
sometimes it doesn’t provide authenticity of the data
(Rivest, Shamir & Adleman, 2013). It creates the problem
of sharing the key to long distance.
Asymmetric cryptography uses the method of public and
private keys. It provides better security as compared to
symmetric cryptography as it assures that authenticity of
data packets is met. However, it lowers the speed of
transmission of data packets and also utilizes more
number of resources (Tassel, 2016). The increasing use of
cryptography technology has raised various risks as it can
be used in some legal copyright issues. Additionally,
cryptography gives the right to have secret
communication which leads to increase in criminal
activities (Wilkins, Keefe & Rehman, 2015).
Cryptography technology is one of the essential
techniques used for building secure VPN. It assures that
messages are received securely to the end users this is
done by using the secret. It makes sure that two entities
can have secure communication on the network by
encrypting the message. The complete process includes
encrypting the text message by using the public key, and
then the message is forwarded in the network channels
(Chaudhry, Farash, Naqvi & Sher, 2016). The encrypted
message could not be read by any third party user and it
will only get decrypted by using private key that is known
only to the valid receiver and it has not been disclosed on
the entire network. The intended user will get the data
packets from the channel and will decrypt the encrypted
text and read the original message. This guarantees that
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cryptography 1
integrity, authenticity and confidentiality of data packets
are met.
The use cryptography increases the overall security of
network by maintaining confidentiality and can be used
for communication of data in order to make
eavesdropping attack a difficult task for hackers (Cimato &
Yang, 2017). It does not require any sophisticated
technology for encoding or decoding the information. As
the information has been scattered over the
communication channels thus theft of information is
increasing day by day (Tong, Duan, Zhuang, Cao, Wei &
Lin, 2014). Cryptography resolves the problem and make
sure that even if the information has been leaked, it won’t
be possible for the third party users to read the actual
text.
B. APPLICATIONS OF CRYPTOGRAPHY
TECHNOLOGIES
Cryptography technologies have been used in various
applications in modern time. The use of cryptography has
expanded in every field and has been used in day to day
security. In a modern world, delivery of emails and online
communication is a common thing for business, friends or
multinational companies (Trilightzone, 2016). Thus it is
important that communication in the giant network is
done through protected measure because the networks
are unprotected and attackable. There are numerous
attackers present on the channels to steal data and miss-
use them (Utexas, 2017). Cryptography has important
existence in our daily life and resolves the issues of data
leakage.
It has been used for transferring money electronically over
the network by using a proper encryption system.
It has used by organisation to have secure communication
by avoiding the third party to read the data (Chhibber &
Patra, 2015).
It can also be used for storage of data as it provides
secrecy in storage as it automatically encrypts the
information stored on the network.
Digital signature is another application of cryptography
that is used to provide authentication and gain trust
among users.
It can also be used for time stamping as that make sure
that document is delivered within a particular time
(Berger, Gueye & Klamti, 2017).
Cryptography has made the tasks easy in daily life, as now
days it has been used for electronic voting.
LITERATURE REVIEW
There are various challenges that a network face due to
cryptography. Interruption is one of them as it makes the
information unavailable or unusable on the system by
valid users. This attack destroys the availability of
information by disabling the communication in between
which can cause huge loss to the organisation
(Verbauwhede, Balasch, Roy & Van Herrewege, 2015).
Interception is other challenge that a network faces due
to the use of cryptography as it sometimes allow
unauthorized party to gains access to the data packet by
side channels. This violet the confidentiality of data
packets as the channels is not secure (Hemalatha &
George, 2015). Cryptography makes sure that actual data
is not read by the unauthorized user but they can modify
the assets. This can be done by altering the encryption
codes and changing the values in the file this leads to loss
of integrity. Fabrication is another issue as it unknowingly
inserts objects into the system.
Other than that cryptography is a very complex
technology as it requires management of encryption keys
that add additional burden on the network. One big
disadvantage of cryptography is that it secures the data
but on the other side it increases the importance to
securing the secret keys. The entire security is dependent
on the secret keys thus if secret key gets lost it will create
loss of data packets (Tutorialspoint, 2015). This is a very
expensive process as it requires use of additional
resources and requires full disk involvement which
reduces the overall performance of the system which also
opens the doors for attackers. Apart from that of
encryption is done correctly it may lead to false sense of
security.
The problem with cryptography is that it is not scalable as
it is difficult to perform cryptographic hashing, exchange
of keys, digital signature construction and batch
processing in large distance. The data stored on cloud
integrity, authenticity and confidentiality of data packets
are met.
The use cryptography increases the overall security of
network by maintaining confidentiality and can be used
for communication of data in order to make
eavesdropping attack a difficult task for hackers (Cimato &
Yang, 2017). It does not require any sophisticated
technology for encoding or decoding the information. As
the information has been scattered over the
communication channels thus theft of information is
increasing day by day (Tong, Duan, Zhuang, Cao, Wei &
Lin, 2014). Cryptography resolves the problem and make
sure that even if the information has been leaked, it won’t
be possible for the third party users to read the actual
text.
B. APPLICATIONS OF CRYPTOGRAPHY
TECHNOLOGIES
Cryptography technologies have been used in various
applications in modern time. The use of cryptography has
expanded in every field and has been used in day to day
security. In a modern world, delivery of emails and online
communication is a common thing for business, friends or
multinational companies (Trilightzone, 2016). Thus it is
important that communication in the giant network is
done through protected measure because the networks
are unprotected and attackable. There are numerous
attackers present on the channels to steal data and miss-
use them (Utexas, 2017). Cryptography has important
existence in our daily life and resolves the issues of data
leakage.
It has been used for transferring money electronically over
the network by using a proper encryption system.
It has used by organisation to have secure communication
by avoiding the third party to read the data (Chhibber &
Patra, 2015).
It can also be used for storage of data as it provides
secrecy in storage as it automatically encrypts the
information stored on the network.
Digital signature is another application of cryptography
that is used to provide authentication and gain trust
among users.
It can also be used for time stamping as that make sure
that document is delivered within a particular time
(Berger, Gueye & Klamti, 2017).
Cryptography has made the tasks easy in daily life, as now
days it has been used for electronic voting.
LITERATURE REVIEW
There are various challenges that a network face due to
cryptography. Interruption is one of them as it makes the
information unavailable or unusable on the system by
valid users. This attack destroys the availability of
information by disabling the communication in between
which can cause huge loss to the organisation
(Verbauwhede, Balasch, Roy & Van Herrewege, 2015).
Interception is other challenge that a network faces due
to the use of cryptography as it sometimes allow
unauthorized party to gains access to the data packet by
side channels. This violet the confidentiality of data
packets as the channels is not secure (Hemalatha &
George, 2015). Cryptography makes sure that actual data
is not read by the unauthorized user but they can modify
the assets. This can be done by altering the encryption
codes and changing the values in the file this leads to loss
of integrity. Fabrication is another issue as it unknowingly
inserts objects into the system.
Other than that cryptography is a very complex
technology as it requires management of encryption keys
that add additional burden on the network. One big
disadvantage of cryptography is that it secures the data
but on the other side it increases the importance to
securing the secret keys. The entire security is dependent
on the secret keys thus if secret key gets lost it will create
loss of data packets (Tutorialspoint, 2015). This is a very
expensive process as it requires use of additional
resources and requires full disk involvement which
reduces the overall performance of the system which also
opens the doors for attackers. Apart from that of
encryption is done correctly it may lead to false sense of
security.
The problem with cryptography is that it is not scalable as
it is difficult to perform cryptographic hashing, exchange
of keys, digital signature construction and batch
processing in large distance. The data stored on cloud

Cryptography 2
need to be protected by using cryptography. Internet
provides the ability to communicate freely with vast
number of parties group but is important to protect the
data from denial of service attacks. Problem with
cryptography technology is that if it is not regulated
regularly then it wouldn’t be possible to filter the wrong
data and can cause false information to reach to the end
users (Menezes, Sarkar & Singh, 2016). If cryptography is
monitored regularly then it does not address concerns
related to security but is difficult to manage the in
cryptography as it is based on electronic commerce
system.
Various challenges that can be seen in an organisation due
to cryptography is difficulty in identifying and
implementing appropriate organizational structures as
there are various processes that require legal assistance to
discovery which data can be encrypted and which cannot
be (Bojinov, Sanchez, Reber, Boneh & Lincoln, 2014). It is
also difficult to understand the existing compliance and
audit standards as every organisation has different
information management lifecycle. Encryption and key
management is the biggest challenge in binding
cryptographic operations and maintain the identity of
users and information (Poornachander. 2017).
Additionally disadvantage of using cryptography for
encrypting the data is speed which is more than the
traditional encrypting method. Sometimes the encryption
done using cryptography makes the authorised user
difficult to access the data. If in some cases complete
breakdown of information occurs cryptography
technology will not able to handle some cases (Buchmann,
et. al, 2017). Apart from that applying cryptography
increases the cost as it does not provide protection against
the vulnerabilities that occur due to poor design of
network protocols and procedures (Kocher, 2018).
PURPOSE AND POSSIBLE ATTACK OF CRYPTOGRAPHY
Purpose
The main purpose of cryptography is transmitting the
information over large network while maintaining the
authentication, confidentiality, integrity and non-
repudiation cases. It maintains the authentication of data
that is verifying the actual identity of user so that it is sure
that data is not received from wrong user. Cryptography
helps in maintaining data confidentiality as it makes the
actual data set unavailable to unauthorized user. It is only
possible by use of encryption that makes the data
exchange possible with valid users.
Attacks due to cryptography
The attacks that occur on the system due to cryptography
are cipher text attack, known plaintext attack, chosen
plaintext attack, brute force attack, birthday attack, man in
middle attack, side channel attack, timing attacks and fault
analysis attack. These attacks simply focus on attacking the
keys and try to break the chipper text (Goud & Reddy,
2016). The time taken to break the key is dependent on
length of key. These attacks are used to find collisions that
happen in the hash function.
FUTURE OF CRYPTOGRAPHY TECHNIQUES
There are a number of advantages and disadvantages of
use of cryptography in today’s business world. Due to
technological advancements, the process of encryption
and decryption has become more efficient and it also
enables more information to pass over a single network.
The technology of quantum computation has become
substantially popular nowadays which is used by
enterprises for storing their business data as quantum
superposition which resulted in increasing the speed of
computation than compared to old methods.
Furthermore, this technology has a promising future as it
increases the security of data and by using secret keys
which protects it from cyber criminals over a wide range of
network. All these technologies have become possible due
to the implementation of cryptography. The significance of
cyber security is growing parallel with the importance of
cryptography as the demand for securely sending data
over large networks grows as well by using quantum
physics. Moreover, cryptography is a crucial element in
the cyber security since it prevents the risk of potential
side-channel attack on the system. As the amount of data
increases over the internet, the risk of cyber security
grows as well. Therefore, the popularity of cryptography
will increase with time as the demand for cyber security
increases for avoiding unauthorised access to the data.
Classical Cryptographic Algorithm Techniques
need to be protected by using cryptography. Internet
provides the ability to communicate freely with vast
number of parties group but is important to protect the
data from denial of service attacks. Problem with
cryptography technology is that if it is not regulated
regularly then it wouldn’t be possible to filter the wrong
data and can cause false information to reach to the end
users (Menezes, Sarkar & Singh, 2016). If cryptography is
monitored regularly then it does not address concerns
related to security but is difficult to manage the in
cryptography as it is based on electronic commerce
system.
Various challenges that can be seen in an organisation due
to cryptography is difficulty in identifying and
implementing appropriate organizational structures as
there are various processes that require legal assistance to
discovery which data can be encrypted and which cannot
be (Bojinov, Sanchez, Reber, Boneh & Lincoln, 2014). It is
also difficult to understand the existing compliance and
audit standards as every organisation has different
information management lifecycle. Encryption and key
management is the biggest challenge in binding
cryptographic operations and maintain the identity of
users and information (Poornachander. 2017).
Additionally disadvantage of using cryptography for
encrypting the data is speed which is more than the
traditional encrypting method. Sometimes the encryption
done using cryptography makes the authorised user
difficult to access the data. If in some cases complete
breakdown of information occurs cryptography
technology will not able to handle some cases (Buchmann,
et. al, 2017). Apart from that applying cryptography
increases the cost as it does not provide protection against
the vulnerabilities that occur due to poor design of
network protocols and procedures (Kocher, 2018).
PURPOSE AND POSSIBLE ATTACK OF CRYPTOGRAPHY
Purpose
The main purpose of cryptography is transmitting the
information over large network while maintaining the
authentication, confidentiality, integrity and non-
repudiation cases. It maintains the authentication of data
that is verifying the actual identity of user so that it is sure
that data is not received from wrong user. Cryptography
helps in maintaining data confidentiality as it makes the
actual data set unavailable to unauthorized user. It is only
possible by use of encryption that makes the data
exchange possible with valid users.
Attacks due to cryptography
The attacks that occur on the system due to cryptography
are cipher text attack, known plaintext attack, chosen
plaintext attack, brute force attack, birthday attack, man in
middle attack, side channel attack, timing attacks and fault
analysis attack. These attacks simply focus on attacking the
keys and try to break the chipper text (Goud & Reddy,
2016). The time taken to break the key is dependent on
length of key. These attacks are used to find collisions that
happen in the hash function.
FUTURE OF CRYPTOGRAPHY TECHNIQUES
There are a number of advantages and disadvantages of
use of cryptography in today’s business world. Due to
technological advancements, the process of encryption
and decryption has become more efficient and it also
enables more information to pass over a single network.
The technology of quantum computation has become
substantially popular nowadays which is used by
enterprises for storing their business data as quantum
superposition which resulted in increasing the speed of
computation than compared to old methods.
Furthermore, this technology has a promising future as it
increases the security of data and by using secret keys
which protects it from cyber criminals over a wide range of
network. All these technologies have become possible due
to the implementation of cryptography. The significance of
cyber security is growing parallel with the importance of
cryptography as the demand for securely sending data
over large networks grows as well by using quantum
physics. Moreover, cryptography is a crucial element in
the cyber security since it prevents the risk of potential
side-channel attack on the system. As the amount of data
increases over the internet, the risk of cyber security
grows as well. Therefore, the popularity of cryptography
will increase with time as the demand for cyber security
increases for avoiding unauthorised access to the data.
Classical Cryptographic Algorithm Techniques
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cryptography 3
In cryptographic algorithms, there are three techniques
which differ based on encryption and decryption
technique.
1. Secret Key Cryptography: It is also called
asymmetric encryption, and in this technique, a
single key is used for both encryption and
decryption of data packers. This technique is not
suitable for sending information to a long
distance because it uses a single key. In case the
receiver is situated in another country or a far
region, it becomes difficult to transfer the key as
it requires more time.
2. Public Key Cryptography: It is also called
asymmetric encryption, and in this technique,
different keys are used for encryption and
decryption of data. Primarily, this technique was
used for authentication of data and key
exchange.
3. Hash Function: In this technique, mathematical
formulates are used by organisations for
transforming their data into ciphertext format by
effectively using a digital fingerprint. This
technology was primarily used by corporations
for maintaining the authenticity of their data.
In the current literature, the key issue which is addressed
is that it is necessary to properly handle the process of
cryptography so that third parties are not able to enter
into the system and change the encryption codes. In case
third parties are able to modify the encryption code then
the data will not be able to decrypt which resulted in data
loss. In some instances, there are chances of data leakage
because the information is secured through encryption;
however, the entire system is not completely secured.
Another issue with the use of cryptography is that in case
the keys get lost than the entire data lost as well;
therefore, it is essential for organisations to protect the
keys in order to prevent data loss.
In the current scenario, many issues have not been
addressed; therefore, an advanced version of
cryptography is needed in the future for ensuring that
there are some alternatives available for protection of
keys. In case of corporations, these issues are critical since
they affect the security of their data. In case engineers are
performing symmetric cryptography to protect their data
while transferring and the receiver is situated in another
country than it becomes difficult for them to send the
required key to the receiver in time because it takes
considerably longer to send a key to another party that is
situated in another nation. Therefore, it is necessary to
take care and protect the keys while using cryptography
along with the network. In today’s rapidly changing
business world, the number of enterprises which use the
cryptography technology for protecting their data from
data breaches and cyber-attacks has increased
considerably. Along with the increase in the use of
cryptography technology, the risks associated with the
technology has increased substantially as well which
makes it difficult for companies to protect their encryption
and decryption keys for cyber criminals. Furthermore, it
can be stated that the security of data packets is another
significant concern for corporations. These data packets
contain confidential and sensitive information of people,
companies, and governments which can be leaked in the
hands of cyber criminals. With the growing popularity of
social media sites and online based services such as net
banking and mobile wallet, the requirement of protecting
data packets for unauthorised access has grown
considerably. The cryptographic algorithms are designed is
a way which assist organisations in protecting their
networks from digital threats which attack on their
network to collect confidential data. The technology
enables enterprises to secure their data while transferring
it across different nations which assist in avoiding data
leak and unauthorised access. The cryptography security
models ensure that confidentiality, integrity and
availability of organisations’ data are maintained.
In cryptographic algorithms, there are three techniques
which differ based on encryption and decryption
technique.
1. Secret Key Cryptography: It is also called
asymmetric encryption, and in this technique, a
single key is used for both encryption and
decryption of data packers. This technique is not
suitable for sending information to a long
distance because it uses a single key. In case the
receiver is situated in another country or a far
region, it becomes difficult to transfer the key as
it requires more time.
2. Public Key Cryptography: It is also called
asymmetric encryption, and in this technique,
different keys are used for encryption and
decryption of data. Primarily, this technique was
used for authentication of data and key
exchange.
3. Hash Function: In this technique, mathematical
formulates are used by organisations for
transforming their data into ciphertext format by
effectively using a digital fingerprint. This
technology was primarily used by corporations
for maintaining the authenticity of their data.
In the current literature, the key issue which is addressed
is that it is necessary to properly handle the process of
cryptography so that third parties are not able to enter
into the system and change the encryption codes. In case
third parties are able to modify the encryption code then
the data will not be able to decrypt which resulted in data
loss. In some instances, there are chances of data leakage
because the information is secured through encryption;
however, the entire system is not completely secured.
Another issue with the use of cryptography is that in case
the keys get lost than the entire data lost as well;
therefore, it is essential for organisations to protect the
keys in order to prevent data loss.
In the current scenario, many issues have not been
addressed; therefore, an advanced version of
cryptography is needed in the future for ensuring that
there are some alternatives available for protection of
keys. In case of corporations, these issues are critical since
they affect the security of their data. In case engineers are
performing symmetric cryptography to protect their data
while transferring and the receiver is situated in another
country than it becomes difficult for them to send the
required key to the receiver in time because it takes
considerably longer to send a key to another party that is
situated in another nation. Therefore, it is necessary to
take care and protect the keys while using cryptography
along with the network. In today’s rapidly changing
business world, the number of enterprises which use the
cryptography technology for protecting their data from
data breaches and cyber-attacks has increased
considerably. Along with the increase in the use of
cryptography technology, the risks associated with the
technology has increased substantially as well which
makes it difficult for companies to protect their encryption
and decryption keys for cyber criminals. Furthermore, it
can be stated that the security of data packets is another
significant concern for corporations. These data packets
contain confidential and sensitive information of people,
companies, and governments which can be leaked in the
hands of cyber criminals. With the growing popularity of
social media sites and online based services such as net
banking and mobile wallet, the requirement of protecting
data packets for unauthorised access has grown
considerably. The cryptographic algorithms are designed is
a way which assist organisations in protecting their
networks from digital threats which attack on their
network to collect confidential data. The technology
enables enterprises to secure their data while transferring
it across different nations which assist in avoiding data
leak and unauthorised access. The cryptography security
models ensure that confidentiality, integrity and
availability of organisations’ data are maintained.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cryptography 4
CONCLUSION
From this report it can be concluded that use of
cryptography is emerging in every field as data is stored
online and it can to be protected from hackers.
Cryptography is used to make sure that secure
communication take place over untrusted network as it
involves multiple clients and serves over the public
network. And increase the chances of attacks. Thus
various challenges that are associated with cryptography
technology have been discussed so that these issues could
be resolved to attain good security. Cryptography protocols
provide confidentiality and integrity of data and act as
saviour for data leakage. In order to secure the data
cryptography is not sufficient it is also necessary to secure
the keys and there are various ways to secure the key in a
cryptosystem.
CONCLUSION
From this report it can be concluded that use of
cryptography is emerging in every field as data is stored
online and it can to be protected from hackers.
Cryptography is used to make sure that secure
communication take place over untrusted network as it
involves multiple clients and serves over the public
network. And increase the chances of attacks. Thus
various challenges that are associated with cryptography
technology have been discussed so that these issues could
be resolved to attain good security. Cryptography protocols
provide confidentiality and integrity of data and act as
saviour for data leakage. In order to secure the data
cryptography is not sufficient it is also necessary to secure
the keys and there are various ways to secure the key in a
cryptosystem.

Cryptography 5
REFERENCES
Cimato, S., & Yang, C. N. (Eds.). (2017).
Visual cryptography and secret image
sharing. CRC press.
Bojinov, H., Sanchez, D., Reber, P., Boneh, D., & Lincoln, P.
(2014). Neuroscience meets cryptography: crypto
primitives secure against rubber hose
attacks.
Communications of the ACM,
57(5), 110-
118.
Buchmann, J., Lauter, K., Mosca, M., Mulholland, J., Braun,
J., Ding, J., ... & Chen, L. (2017). Postquantum
Cryptography, Part.
Chaudhry, S. A., Farash, M. S., Naqvi, H., & Sher, M. (2016).
A secure and efficient authenticated encryption
for electronic payment systems using elliptic
curve cryptography.
Electronic Commerce
Research,
16(1), 113-139.
Choo, K. K. R., Domingo-Ferrer, J., & Zhang, L. (2016).
Cloud Cryptography: Theory, Practice and Future
Research Directions.
Future Generation Comp.
Syst.,
62, 51-53.
Chhibber, N., & Patra, G. (2015, August). Synchronization
of chaos in multiple three-dimensional chaotic
maps and its application in cryptography.
In
Technology Management and Emerging
Technologies (ISTMET), 2015 International
Symposium on (pp. 355-359). IEEE.
Berger, T. P., Gueye, C. T., & Klamti, J. B. (2017, April). A
NP-complete problem in coding theory with
application to code based cryptography.
In
International Conference on Codes, Cryptology,
and Information Security (pp. 230-237). Springer,
Cham.
Desmedt, Y. (2016). What is the Future of Cryptography?.
In
The New Codebreakers (pp. 109-122). Springer,
Berlin, Heidelberg.
Goud, N. P. K., & Reddy, P. R. (2016). A ROBUST PRIMITIVE
FOR AVOIDING DATA ATTACKS USING
CRYPTOGRAPHY.
IJITR,
4(4), 3406-3408.
Hemalatha. D. & George. J. (2015). Cryptographic
Techniques, Threats and Privacy Challenges in
Cloud Computing. Retrieved from
https://pdfs.semanticscholar.org/b92e/11b2af6a
22d3475eaacf1ca4e77455387885.pdf.
Jisc. (2018). ntroduction-cryptographic-techniques.
Retrieved from
https://community.jisc.ac.uk/library/advisory-
services/introduction-cryptographic-techniques..
Kocher, P. C. (2018).
U.S. Patent No. 9,940,772.
Washington, DC: U.S. Patent and Trademark
Office.
Lin, Y. (2015). A Survey on Biometric Cryptographic
Technology.
Journal of Hangzhou Dianzi
University (Natural Sciences),
3, 001.
Menezes, A., Sarkar, P., & Singh, S. (2016, December).
Challenges with assessing the impact of NFS
advances on the security of pairing-based
cryptography. In
International Conference on
Cryptology in Malaysia (pp. 83-108). Springer,
Cham.
Poornachander. V. (2017). Security Issues on Cryptography
and Network Security. Retrieved from
http://ijcsit.com/docs/Volume%207/vol7issue3/ij
csit20160703130.pdf.
Rivest, R. L., Shamir, A., & Adleman, L. M. (2013).
U.S.
Patent No. 4,405,829. Washington, DC: U.S.
Patent and Trademark Office.
Sasi, S. B., & Sivanandam, N. (2015). A survey on
cryptography using optimization algorithms in
WSNs.
Indian Journal of Science and
Technology,
8(3), 216-221.
Staff. C. (2015). Cryptography Techniques for Secure
Communications. Retrieved from
REFERENCES
Cimato, S., & Yang, C. N. (Eds.). (2017).
Visual cryptography and secret image
sharing. CRC press.
Bojinov, H., Sanchez, D., Reber, P., Boneh, D., & Lincoln, P.
(2014). Neuroscience meets cryptography: crypto
primitives secure against rubber hose
attacks.
Communications of the ACM,
57(5), 110-
118.
Buchmann, J., Lauter, K., Mosca, M., Mulholland, J., Braun,
J., Ding, J., ... & Chen, L. (2017). Postquantum
Cryptography, Part.
Chaudhry, S. A., Farash, M. S., Naqvi, H., & Sher, M. (2016).
A secure and efficient authenticated encryption
for electronic payment systems using elliptic
curve cryptography.
Electronic Commerce
Research,
16(1), 113-139.
Choo, K. K. R., Domingo-Ferrer, J., & Zhang, L. (2016).
Cloud Cryptography: Theory, Practice and Future
Research Directions.
Future Generation Comp.
Syst.,
62, 51-53.
Chhibber, N., & Patra, G. (2015, August). Synchronization
of chaos in multiple three-dimensional chaotic
maps and its application in cryptography.
In
Technology Management and Emerging
Technologies (ISTMET), 2015 International
Symposium on (pp. 355-359). IEEE.
Berger, T. P., Gueye, C. T., & Klamti, J. B. (2017, April). A
NP-complete problem in coding theory with
application to code based cryptography.
In
International Conference on Codes, Cryptology,
and Information Security (pp. 230-237). Springer,
Cham.
Desmedt, Y. (2016). What is the Future of Cryptography?.
In
The New Codebreakers (pp. 109-122). Springer,
Berlin, Heidelberg.
Goud, N. P. K., & Reddy, P. R. (2016). A ROBUST PRIMITIVE
FOR AVOIDING DATA ATTACKS USING
CRYPTOGRAPHY.
IJITR,
4(4), 3406-3408.
Hemalatha. D. & George. J. (2015). Cryptographic
Techniques, Threats and Privacy Challenges in
Cloud Computing. Retrieved from
https://pdfs.semanticscholar.org/b92e/11b2af6a
22d3475eaacf1ca4e77455387885.pdf.
Jisc. (2018). ntroduction-cryptographic-techniques.
Retrieved from
https://community.jisc.ac.uk/library/advisory-
services/introduction-cryptographic-techniques..
Kocher, P. C. (2018).
U.S. Patent No. 9,940,772.
Washington, DC: U.S. Patent and Trademark
Office.
Lin, Y. (2015). A Survey on Biometric Cryptographic
Technology.
Journal of Hangzhou Dianzi
University (Natural Sciences),
3, 001.
Menezes, A., Sarkar, P., & Singh, S. (2016, December).
Challenges with assessing the impact of NFS
advances on the security of pairing-based
cryptography. In
International Conference on
Cryptology in Malaysia (pp. 83-108). Springer,
Cham.
Poornachander. V. (2017). Security Issues on Cryptography
and Network Security. Retrieved from
http://ijcsit.com/docs/Volume%207/vol7issue3/ij
csit20160703130.pdf.
Rivest, R. L., Shamir, A., & Adleman, L. M. (2013).
U.S.
Patent No. 4,405,829. Washington, DC: U.S.
Patent and Trademark Office.
Sasi, S. B., & Sivanandam, N. (2015). A survey on
cryptography using optimization algorithms in
WSNs.
Indian Journal of Science and
Technology,
8(3), 216-221.
Staff. C. (2015). Cryptography Techniques for Secure
Communications. Retrieved from
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cryptography 6
http://certmag.com/cryptography-techniques-
for-secure-communications/.
Tassel. D. (2016). Cryptographic techniques for computers.
Retrieved from
https://www.computer.org/csdl/proceedings/afip
s/1969/5073/00/50730367.pdf.
Tong, D., Duan, H., Zhuang, H., Cao, J., Wei, Z., & Lin, Y.
(2014). Using T–Hg–T and C–Ag–T: a four-input
dual-core molecular logic gate and its new
application in cryptography.
RSC Advances,
4(11),
5363-5366.
Trilightzone. (2016). Cryptography in Daily Life. Retrieved
from
https://www.trilightzone.org/cryptography_in_da
ily_life.html
Tutorialspoint. (2015). Cryptography Benefits &
Drawbacks. Retrieved from
https://www.tutorialspoint.com/cryptography/be
nefits_and_drawbacks.htm.
Utexas. (2017). Cryptography in Everyday Life. Retrieved
from
http://www.laits.utexas.edu/~anorman/BUS.FOR
/course.mat/SSim/life.html.
Verbauwhede, I., Balasch, J., Roy, S. S., & Van Herrewege,
A. (2015, February). 24.1 Circuit challenges from
cryptography. In
Solid-State Circuits Conference-
(ISSCC), 2015 IEEE International (pp. 1-2). IEEE.
Wilkins, J., Keefe, M., & Rehman, S. (2015).
U.S. Patent No.
9,002,018. Washington, DC: U.S. Patent and
Trademark Office.
http://certmag.com/cryptography-techniques-
for-secure-communications/.
Tassel. D. (2016). Cryptographic techniques for computers.
Retrieved from
https://www.computer.org/csdl/proceedings/afip
s/1969/5073/00/50730367.pdf.
Tong, D., Duan, H., Zhuang, H., Cao, J., Wei, Z., & Lin, Y.
(2014). Using T–Hg–T and C–Ag–T: a four-input
dual-core molecular logic gate and its new
application in cryptography.
RSC Advances,
4(11),
5363-5366.
Trilightzone. (2016). Cryptography in Daily Life. Retrieved
from
https://www.trilightzone.org/cryptography_in_da
ily_life.html
Tutorialspoint. (2015). Cryptography Benefits &
Drawbacks. Retrieved from
https://www.tutorialspoint.com/cryptography/be
nefits_and_drawbacks.htm.
Utexas. (2017). Cryptography in Everyday Life. Retrieved
from
http://www.laits.utexas.edu/~anorman/BUS.FOR
/course.mat/SSim/life.html.
Verbauwhede, I., Balasch, J., Roy, S. S., & Van Herrewege,
A. (2015, February). 24.1 Circuit challenges from
cryptography. In
Solid-State Circuits Conference-
(ISSCC), 2015 IEEE International (pp. 1-2). IEEE.
Wilkins, J., Keefe, M., & Rehman, S. (2015).
U.S. Patent No.
9,002,018. Washington, DC: U.S. Patent and
Trademark Office.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Cryptography 7
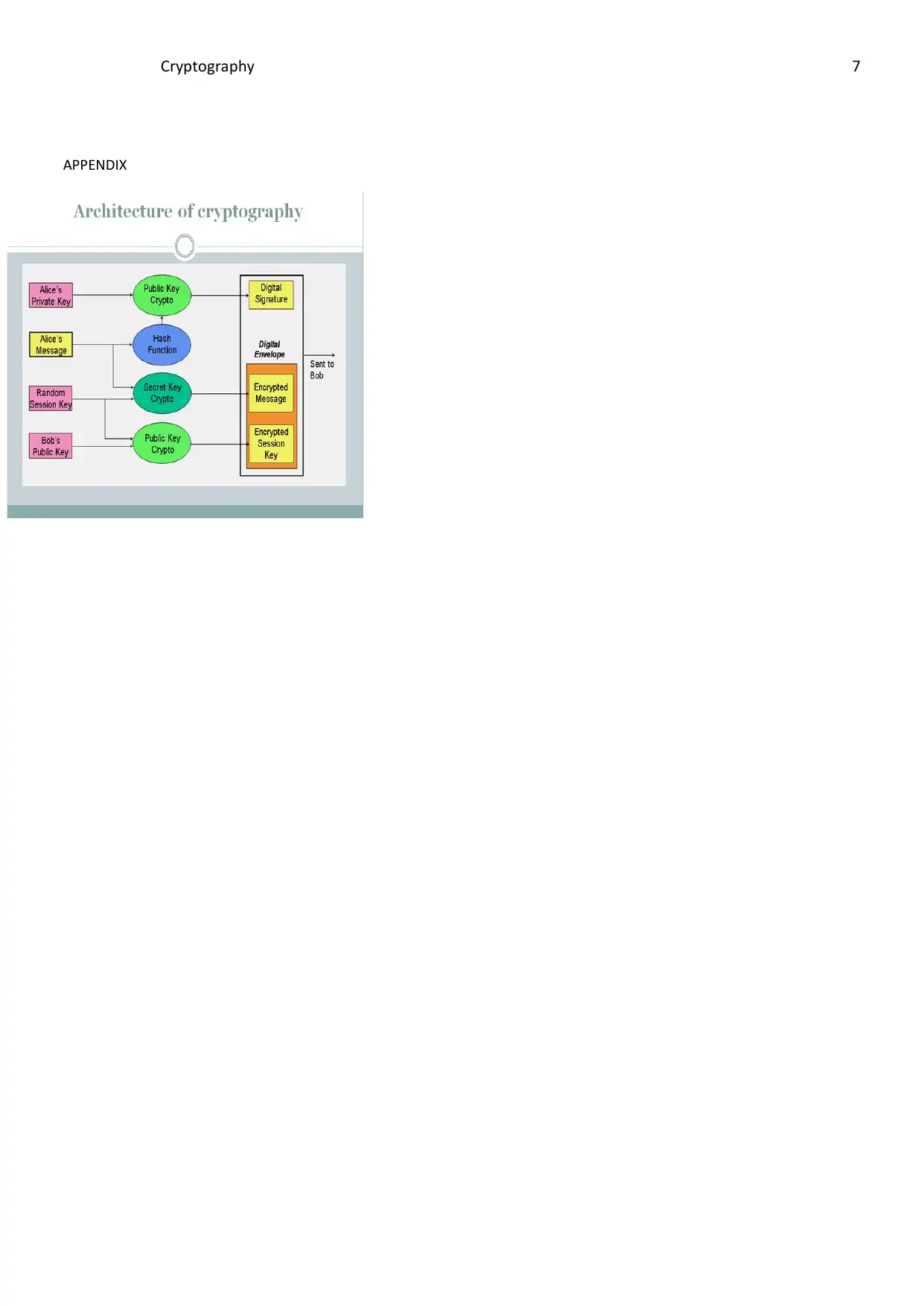
APPENDIX
APPENDIX
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


