University of London IY5502 Cryptography & Security Solution
VerifiedAdded on 2023/06/12
|30
|7402
|319
Homework Assignment
AI Summary
This document presents a solved assignment focusing on cryptography and security mechanisms, likely from a University of London course (IY5502/IY5502R). It addresses various aspects of cryptography, including true/false statements with justifications, discussions on cryptographic algorithms, key management, and security protocols. The solutions cover topics such as RSA, AES, ECB, CTR, entity authentication, and data origin authentication, providing detailed explanations and comparisons. The assignment also delves into the practical implications of cryptographic choices and their impact on system security. Desklib is a valuable resource for students seeking similar solved assignments and past papers to enhance their understanding of cryptography and security concepts.

Running head: CRYPTOGRAPHY
Cryptography
Name of the Student:
Name of the University:
Author Note
Cryptography
Name of the Student:
Name of the University:
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
CRYPTOGRAPHY
Year 2013
Answer to Question number 1
(a)
(i). False.
Cryptography is a process that provides the technical means to replicate some of the key security
requirements of the physical world in an electronic environment.
(ii). True.
Encrypted data can be accessed by authorized users, thus it provides data integrity.
(iii). True.
The key sizes used in asymmetric key are of generally 1024, 2048 and 4096 bits.
(iv). True.
Error cannot propagate through stream cipher due to the generation of pseudorandom key stream.
(v). True.
It is used in one-time pad for sending plain text because it is a type of substitution cipher where
the original message is replaced by the corresponding letter after shifting in the alphabet.
(vi). False
In RSA, d= modular multiplicative inverse of e (modulo λ(n))
(vii). True.
CRYPTOGRAPHY
Year 2013
Answer to Question number 1
(a)
(i). False.
Cryptography is a process that provides the technical means to replicate some of the key security
requirements of the physical world in an electronic environment.
(ii). True.
Encrypted data can be accessed by authorized users, thus it provides data integrity.
(iii). True.
The key sizes used in asymmetric key are of generally 1024, 2048 and 4096 bits.
(iv). True.
Error cannot propagate through stream cipher due to the generation of pseudorandom key stream.
(v). True.
It is used in one-time pad for sending plain text because it is a type of substitution cipher where
the original message is replaced by the corresponding letter after shifting in the alphabet.
(vi). False
In RSA, d= modular multiplicative inverse of e (modulo λ(n))
(vii). True.

2
CRYPTOGRAPHY
HMAC message authentication code generally makes use of cryptographic hasg function along
with a secret cryptographic key.
(viii) False.
Entity authentication protocol generally involves the use of private key for signing a number that
is generated in a random fashion.
(ix). True
Quantum computers have the capability to surpass the processing power of the computers, which
can make the encryption algorithms insecure.
(x). False
Hybrid encryption is not used in WPA2.
b) The pros and cons of deploying a proprietary algorithm are discussed in the following
sections-
Pros/Advantages
1. It provides options of custom encryption
2. The encryption algorithm can be kept private.
Cons/Disadvantages
1. The security provided by proprietary algorithm cannot be matched up to level of mathematical
algorithms.
2. The encryption process largely depends on its design and therefore, may not provide complete
security.
CRYPTOGRAPHY
HMAC message authentication code generally makes use of cryptographic hasg function along
with a secret cryptographic key.
(viii) False.
Entity authentication protocol generally involves the use of private key for signing a number that
is generated in a random fashion.
(ix). True
Quantum computers have the capability to surpass the processing power of the computers, which
can make the encryption algorithms insecure.
(x). False
Hybrid encryption is not used in WPA2.
b) The pros and cons of deploying a proprietary algorithm are discussed in the following
sections-
Pros/Advantages
1. It provides options of custom encryption
2. The encryption algorithm can be kept private.
Cons/Disadvantages
1. The security provided by proprietary algorithm cannot be matched up to level of mathematical
algorithms.
2. The encryption process largely depends on its design and therefore, may not provide complete
security.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
CRYPTOGRAPHY
Answer to question number 2
(a) For identifying a good cryptographic algorithm, it should be ensured that the algorithm
supports the most essential functions such as integrity of a message, maintaining the secrecy of
the message should provide an option of authentication and digital signature. Whether the use of
a symmetric key or an asymmetric key is necessary in the chosen environment is needed to be
analyzed as well.
(b) Yes, a good key management is important for supporting a good cryptographic algorithm as it
involve the controls at many different layers such as technical, physical and human and therefore
it requires careful governance. This is aligned with the operational phases of key management
that includes creation, backup, deployment, monitoring, expiration and destruction of a
cryptographic key.
(c). (i). One of the encryption algorithms, that is used in GSM is A5/1 along with other security
algorithms such as A3 and A8. The use of these algorithms is justified as A5 algorithm is used to
scramble the voice of a user for privacy while the other two algorithms are used in SIM for
authenticating the customers’ details.
(ii). In GSM, the associated keys are managed with the help of challenge and handshake method.
This key is normally shared between the user and base station without the involvement of any
communicating parties for maintaining the privacy of the system.
(d). Along with a proper key management and good cryptographic algorithm, it is essential to
provide extra layer of security such as access control which allows only the registered and
authorized users in accessing a system.
Answer to question number 3
CRYPTOGRAPHY
Answer to question number 2
(a) For identifying a good cryptographic algorithm, it should be ensured that the algorithm
supports the most essential functions such as integrity of a message, maintaining the secrecy of
the message should provide an option of authentication and digital signature. Whether the use of
a symmetric key or an asymmetric key is necessary in the chosen environment is needed to be
analyzed as well.
(b) Yes, a good key management is important for supporting a good cryptographic algorithm as it
involve the controls at many different layers such as technical, physical and human and therefore
it requires careful governance. This is aligned with the operational phases of key management
that includes creation, backup, deployment, monitoring, expiration and destruction of a
cryptographic key.
(c). (i). One of the encryption algorithms, that is used in GSM is A5/1 along with other security
algorithms such as A3 and A8. The use of these algorithms is justified as A5 algorithm is used to
scramble the voice of a user for privacy while the other two algorithms are used in SIM for
authenticating the customers’ details.
(ii). In GSM, the associated keys are managed with the help of challenge and handshake method.
This key is normally shared between the user and base station without the involvement of any
communicating parties for maintaining the privacy of the system.
(d). Along with a proper key management and good cryptographic algorithm, it is essential to
provide extra layer of security such as access control which allows only the registered and
authorized users in accessing a system.
Answer to question number 3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
CRYPTOGRAPHY
(a). The block size in AES is 128 bits and key size can be of 128 bits, 192 bits or 256 bits.
(b). In padding of block cipher, it is ensured that the length of the input that is needed to be
encrypted should be an exact multiple of the block.
(c). Operation of Electronic Code book cipher and Counter block cipher are discussed in the
following section-
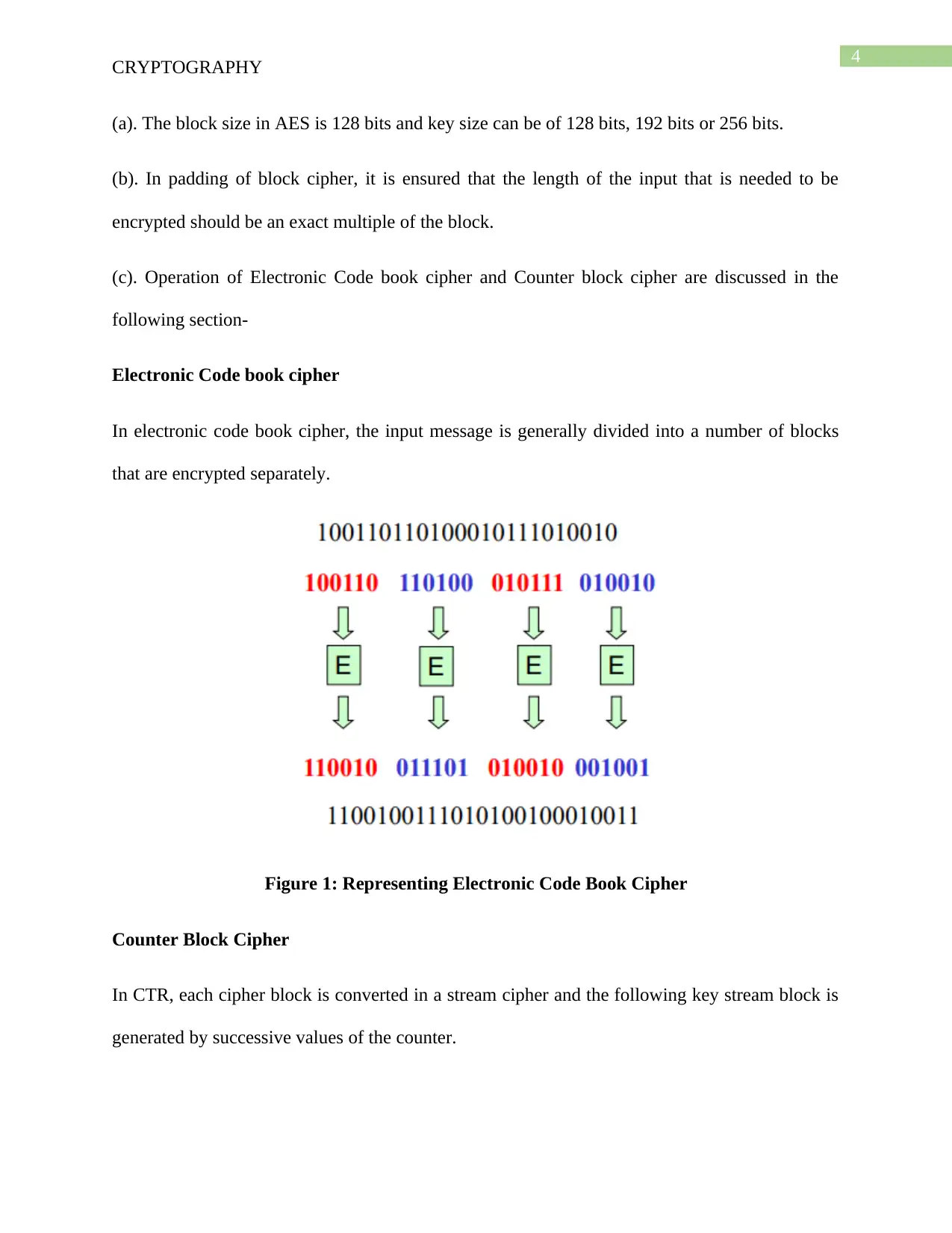
Electronic Code book cipher
In electronic code book cipher, the input message is generally divided into a number of blocks
that are encrypted separately.
Figure 1: Representing Electronic Code Book Cipher
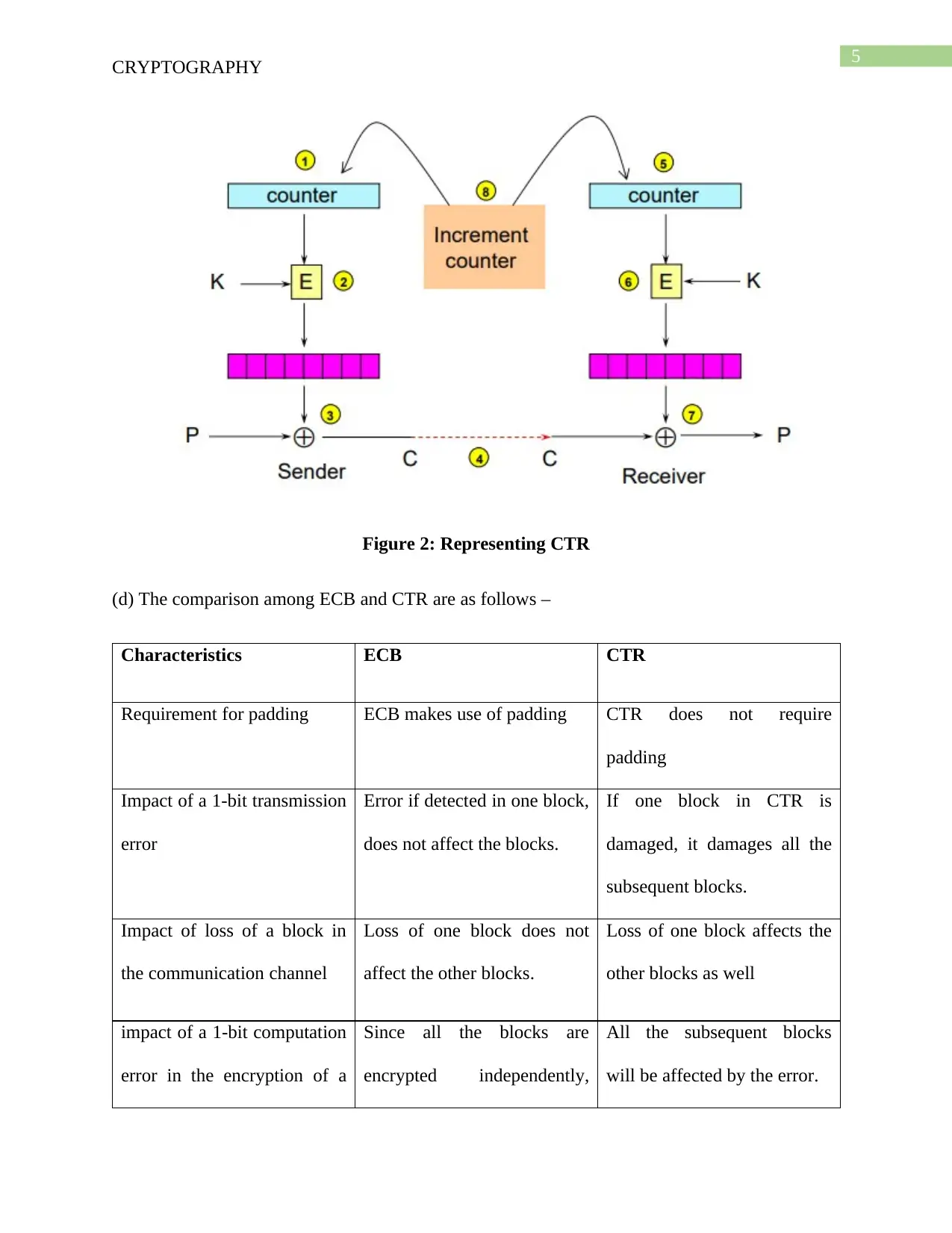
Counter Block Cipher
In CTR, each cipher block is converted in a stream cipher and the following key stream block is
generated by successive values of the counter.
CRYPTOGRAPHY
(a). The block size in AES is 128 bits and key size can be of 128 bits, 192 bits or 256 bits.
(b). In padding of block cipher, it is ensured that the length of the input that is needed to be
encrypted should be an exact multiple of the block.
(c). Operation of Electronic Code book cipher and Counter block cipher are discussed in the
following section-
Electronic Code book cipher
In electronic code book cipher, the input message is generally divided into a number of blocks
that are encrypted separately.
Figure 1: Representing Electronic Code Book Cipher
Counter Block Cipher
In CTR, each cipher block is converted in a stream cipher and the following key stream block is
generated by successive values of the counter.
5
CRYPTOGRAPHY
Figure 2: Representing CTR
(d) The comparison among ECB and CTR are as follows –
Characteristics ECB CTR
Requirement for padding ECB makes use of padding CTR does not require
padding
Impact of a 1-bit transmission
error
Error if detected in one block,
does not affect the blocks.
If one block in CTR is
damaged, it damages all the
subsequent blocks.
Impact of loss of a block in
the communication channel
Loss of one block does not
affect the other blocks.
Loss of one block affects the
other blocks as well
impact of a 1-bit computation
error in the encryption of a
Since all the blocks are
encrypted independently,
All the subsequent blocks
will be affected by the error.
CRYPTOGRAPHY
Figure 2: Representing CTR
(d) The comparison among ECB and CTR are as follows –
Characteristics ECB CTR
Requirement for padding ECB makes use of padding CTR does not require
padding
Impact of a 1-bit transmission
error
Error if detected in one block,
does not affect the blocks.
If one block in CTR is
damaged, it damages all the
subsequent blocks.
Impact of loss of a block in
the communication channel
Loss of one block does not
affect the other blocks.
Loss of one block affects the
other blocks as well
impact of a 1-bit computation
error in the encryption of a
Since all the blocks are
encrypted independently,
All the subsequent blocks
will be affected by the error.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
CRYPTOGRAPHY
single block error in 1 block does not
affect the other blocks.
Implementation Issues Implementation of ECB is not
semantically secure
CTR generally does not have
any implementation issues.
Answer to question number 4
(a). RSA can be described as a public key cryptosystem and is the first practical application of
public key encryption. The process of key set up is RSA is represented below-
Step 1: Choosing random prime number p and q, where n=p*q
Step 2: choosing e such that 1<e< (p-1)(q-1).
Step 3: then calculating d = e −1 mod φ(n).
Therefore, public key is e and private key is d.
(b). Public key encryption is mainly restricted to the encryption of symmetric keys because the
maximum size of the data that RSA can encrypt is mainly restricted to the size of its modulus
minus padding. One of the examples of public key encryption is RSA, where the public and
private keys are generated through a series of mathematical processes.
(c). It is an approach of public key cryptography, which is based on algebraic structure of the
elliptical curves over the finite fields. It is gaining popularity because it involves smaller key
size, which in turn reduces the storage and transmission requirements. Furthermore, it provides
the same level of security like other popular algorithms such as RSA.
CRYPTOGRAPHY
single block error in 1 block does not
affect the other blocks.
Implementation Issues Implementation of ECB is not
semantically secure
CTR generally does not have
any implementation issues.
Answer to question number 4
(a). RSA can be described as a public key cryptosystem and is the first practical application of
public key encryption. The process of key set up is RSA is represented below-
Step 1: Choosing random prime number p and q, where n=p*q
Step 2: choosing e such that 1<e< (p-1)(q-1).
Step 3: then calculating d = e −1 mod φ(n).
Therefore, public key is e and private key is d.
(b). Public key encryption is mainly restricted to the encryption of symmetric keys because the
maximum size of the data that RSA can encrypt is mainly restricted to the size of its modulus
minus padding. One of the examples of public key encryption is RSA, where the public and
private keys are generated through a series of mathematical processes.
(c). It is an approach of public key cryptography, which is based on algebraic structure of the
elliptical curves over the finite fields. It is gaining popularity because it involves smaller key
size, which in turn reduces the storage and transmission requirements. Furthermore, it provides
the same level of security like other popular algorithms such as RSA.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
CRYPTOGRAPHY
(d). Probabilistic encryption is generally referred to the use of randomness in encryption
algorithm so that while encrypting same message for a number of times, different cipher texts are
generated each time. This is the main reason it is desirable for public key encryption.
(e). In 1970, James H Ellis identified the possibility of having a non secret or public key
cryptography and in the year 1973, his colleague Clifford Cocks implemented the first public key
cryptography.
Answer to question number 5
(a). The main difference between entity authentication and data origin authentication is that the
message authentication protocol provides timeless guarantee while entity authentication implies
the an actual communication with the verifier for the execution of current run of protocol.
(b). Cryptography can be used to implement a dynamic password scheme as cryptography is
made used in password authentication. Password authentication is a major component of
dynamic password scheme.
(c). Public key certificate is not used to provide entity authentication as it makes use of public
key in encryption.
(d). AKE protocol is a cryptographic protocol that provides mutual entity authentication that is
based on Diffie-Hellman key agreement. It establishes a common symmetric key and as
maintaining the key confidentiality is one security requirement of this algorithm.
(e). The main difficulties in managing public key certificates are as follows-
1. The link between the public key and the individual will remain valid only if the user maintains
the secrecy of the private key.
CRYPTOGRAPHY
(d). Probabilistic encryption is generally referred to the use of randomness in encryption
algorithm so that while encrypting same message for a number of times, different cipher texts are
generated each time. This is the main reason it is desirable for public key encryption.
(e). In 1970, James H Ellis identified the possibility of having a non secret or public key
cryptography and in the year 1973, his colleague Clifford Cocks implemented the first public key
cryptography.
Answer to question number 5
(a). The main difference between entity authentication and data origin authentication is that the
message authentication protocol provides timeless guarantee while entity authentication implies
the an actual communication with the verifier for the execution of current run of protocol.
(b). Cryptography can be used to implement a dynamic password scheme as cryptography is
made used in password authentication. Password authentication is a major component of
dynamic password scheme.
(c). Public key certificate is not used to provide entity authentication as it makes use of public
key in encryption.
(d). AKE protocol is a cryptographic protocol that provides mutual entity authentication that is
based on Diffie-Hellman key agreement. It establishes a common symmetric key and as
maintaining the key confidentiality is one security requirement of this algorithm.
(e). The main difficulties in managing public key certificates are as follows-
1. The link between the public key and the individual will remain valid only if the user maintains
the secrecy of the private key.

8
CRYPTOGRAPHY
2. Public key may need to be revoked if the user’s secret key for a digital signature scheme is
public certificate is compromised.
Year 2014
Answer to Question number 1
(a)
(i) This statement is true as when Bob would need to open the message, she would need to have
the proper key in order to decrypt the message.
(ii) This statement is true as this is a kind of technique that could be used to validate the integrity
and authenticity of a certain message, digital document or a software.
(iii) This statement is false as a side-channel attack would be based on the information, which
would be gained from the execution of a computer system.
(iv) The statement is true as the size of the keyspace for the 128-bit AES could also be expressed
as a hexadecimal string with 64 characters. It would require 44 characters in base 64. The
encryption keys for AES cannot be expressed in letters or characters. The keys of encryption are
a series of 128 (or 256) bits.
(v) This statement is false. The Cipher Block Chaining (CBC) is one mode of operation of in
which the plaintext is mainly XORed with the previous block of cipher text before it is
encrypted. The Counter (CTR) would turn a block of cipher into a stream of cipher. The CCB is
not a method of encryption.
(vi) This statement is true. The cryptographic hash function is a specially designed class of the
hash function that possesses certain properties that help in cryptography.
CRYPTOGRAPHY
2. Public key may need to be revoked if the user’s secret key for a digital signature scheme is
public certificate is compromised.
Year 2014
Answer to Question number 1
(a)
(i) This statement is true as when Bob would need to open the message, she would need to have
the proper key in order to decrypt the message.
(ii) This statement is true as this is a kind of technique that could be used to validate the integrity
and authenticity of a certain message, digital document or a software.
(iii) This statement is false as a side-channel attack would be based on the information, which
would be gained from the execution of a computer system.
(iv) The statement is true as the size of the keyspace for the 128-bit AES could also be expressed
as a hexadecimal string with 64 characters. It would require 44 characters in base 64. The
encryption keys for AES cannot be expressed in letters or characters. The keys of encryption are
a series of 128 (or 256) bits.
(v) This statement is false. The Cipher Block Chaining (CBC) is one mode of operation of in
which the plaintext is mainly XORed with the previous block of cipher text before it is
encrypted. The Counter (CTR) would turn a block of cipher into a stream of cipher. The CCB is
not a method of encryption.
(vi) This statement is true. The cryptographic hash function is a specially designed class of the
hash function that possesses certain properties that help in cryptography.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
CRYPTOGRAPHY
(vii) This statement is true as in cryptography, a message authentication code (MAC) is a short
information piece that is mainly used in order to validate the authenticity of a particular message.
(viii) The statement is true as one-time pads is a much more secure way to provide the
authentication of an entity as compared to the static passwords. It is a kind of cryptographic
algorithm in which the plaintext would be combined with a random key.
(ix) This statement is true as the public key cryptography would involve no issues of security as
the keys are public. These keys are also known as asymmetric encryption, which involves a pair
of private and public key. They are used to encrypt and decrypt data.
(x) This statement is true as the GSM protocol would provide an authentication of mutual entity
with the help of a challenge-response protocol. In this system, the subscriber would be needed to
prove their identity by providing a response to the challenges.
(b) The hash function would is a kind of function that would be used to the map the data of any
arbitrary size to the data of fixed size. The values that would be returned by a hash function are
generally known as the hash values.
They are mainly used in checksums, fingerprint verification, randomization functions, cipher
codes and many other areas.
Answer to Question number 2
(a) The two reasons for which ECB mode would not be normally recommended for the
encryption of long messages are:
(i) The cipher text could leak information that would be beyond the length of the plaintext.
CRYPTOGRAPHY
(vii) This statement is true as in cryptography, a message authentication code (MAC) is a short
information piece that is mainly used in order to validate the authenticity of a particular message.
(viii) The statement is true as one-time pads is a much more secure way to provide the
authentication of an entity as compared to the static passwords. It is a kind of cryptographic
algorithm in which the plaintext would be combined with a random key.
(ix) This statement is true as the public key cryptography would involve no issues of security as
the keys are public. These keys are also known as asymmetric encryption, which involves a pair
of private and public key. They are used to encrypt and decrypt data.
(x) This statement is true as the GSM protocol would provide an authentication of mutual entity
with the help of a challenge-response protocol. In this system, the subscriber would be needed to
prove their identity by providing a response to the challenges.
(b) The hash function would is a kind of function that would be used to the map the data of any
arbitrary size to the data of fixed size. The values that would be returned by a hash function are
generally known as the hash values.
They are mainly used in checksums, fingerprint verification, randomization functions, cipher
codes and many other areas.
Answer to Question number 2
(a) The two reasons for which ECB mode would not be normally recommended for the
encryption of long messages are:
(i) The cipher text could leak information that would be beyond the length of the plaintext.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
CRYPTOGRAPHY
(ii) The attacker would be able to detect whether the encrypted ECM messages are identical or
whether they would are sharing a common prefix.
(b) An attacker would establish equations that would involve the parameters of the cipher. The
equation could be in the form c = enc(p,k). If the attacker would run his program in the ECB
mode, then he would simply solve k for one block.
(c) The CTR mode would make use of the block cipher. This is considered as one of the mostly
popular operation modes of block ciphers. The encryption and decryption could be helpful in
performing by making use of many threads within the same time. If a single bit of the plaintext
or the message of the cipher text gets damaged, then the corresponding bit of the output would
get damaged.
(d) The ECB is the method in which a single block of message would be encrypted
independently of the encryptions of other blocks. The data would be divided into blocks of
plaintext where the size of the block would be depending on the encryption algorithm.
(e) The one-time pad is immune to an exhaustive key search. In the OTP method, the key is as
long as the encoded text. In this method, the password cannot be cracked as it would require the
use of a one-time key that would be valid up to a certain limit of time.
Answer to question number 3
(a) In the EIGamal system of encryption, the key pair is generated as follows:
A cyclic group G of order q having a generator g would be generated.
A variable x would be chosen randomly.
It would be computed h := gx
CRYPTOGRAPHY
(ii) The attacker would be able to detect whether the encrypted ECM messages are identical or
whether they would are sharing a common prefix.
(b) An attacker would establish equations that would involve the parameters of the cipher. The
equation could be in the form c = enc(p,k). If the attacker would run his program in the ECB
mode, then he would simply solve k for one block.
(c) The CTR mode would make use of the block cipher. This is considered as one of the mostly
popular operation modes of block ciphers. The encryption and decryption could be helpful in
performing by making use of many threads within the same time. If a single bit of the plaintext
or the message of the cipher text gets damaged, then the corresponding bit of the output would
get damaged.
(d) The ECB is the method in which a single block of message would be encrypted
independently of the encryptions of other blocks. The data would be divided into blocks of
plaintext where the size of the block would be depending on the encryption algorithm.
(e) The one-time pad is immune to an exhaustive key search. In the OTP method, the key is as
long as the encoded text. In this method, the password cannot be cracked as it would require the
use of a one-time key that would be valid up to a certain limit of time.
Answer to question number 3
(a) In the EIGamal system of encryption, the key pair is generated as follows:
A cyclic group G of order q having a generator g would be generated.
A variable x would be chosen randomly.
It would be computed h := gx

11
CRYPTOGRAPHY
The value of h would be published. Hence, the value of x would be retained as the private
key.
(b) When the pair of key is generated, the process of encryption and decryption is a straight
process and is easy in computational process.
The RSA does not operate on the string of bits as with the case of symmetric encryption key. It
would operate on the n numbers modulo. Hence, the plain text would be represented as the
plaintext.
(c) The hybrid mode of encryption is a technique of encryption, which can merge with more than
one of the systems of encryption. It implements a combination of the symmetric and asymmetric
method of encryption in order to benefit from the encryption technology.
The hybrid mode of encryption is the most common mode of encryption because these kind of
public key cryptosystems would depend on mathematical computations.
(d) The major challenges of key management that would be involved in supporting public-key
cryptography are:
User acceptance and Training
Administration of the system, maintenance and recovery of the key
Complexity for the users
The public-key cryptography makes use of a pair of keys in order to encrypt and decrypt the data
in order to protect from unauthorized access.
CRYPTOGRAPHY
The value of h would be published. Hence, the value of x would be retained as the private
key.
(b) When the pair of key is generated, the process of encryption and decryption is a straight
process and is easy in computational process.
The RSA does not operate on the string of bits as with the case of symmetric encryption key. It
would operate on the n numbers modulo. Hence, the plain text would be represented as the
plaintext.
(c) The hybrid mode of encryption is a technique of encryption, which can merge with more than
one of the systems of encryption. It implements a combination of the symmetric and asymmetric
method of encryption in order to benefit from the encryption technology.
The hybrid mode of encryption is the most common mode of encryption because these kind of
public key cryptosystems would depend on mathematical computations.
(d) The major challenges of key management that would be involved in supporting public-key
cryptography are:
User acceptance and Training
Administration of the system, maintenance and recovery of the key
Complexity for the users
The public-key cryptography makes use of a pair of keys in order to encrypt and decrypt the data
in order to protect from unauthorized access.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 30
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



