Cryptography Homework: Steganalysis, Cipher Comparison and MD5 Hash
VerifiedAdded on 2023/05/26
|10
|1022
|100
Homework Assignment
AI Summary
This document presents a comprehensive solution to a cryptography homework assignment. It begins with an exploration of steganography, detailing its methods and applications in concealing messages, including technical and linguistic approaches, and how it relates to ATM security and digital structures. The assignment then delves into public key structures, explaining asymmetric cryptography and the roles of public and private keys in authentication and encryption. A comparison of block and stream ciphers is provided, highlighting their complexities and algorithmic modes. The document also includes a comparison of monoalphabetic and polyalphabetic ciphers and demonstrates the decryption of a Caesar cipher. Finally, the solution covers the MD5 hash generator, explaining its function in creating 128-bit fingerprints and its applications in data integrity and password storage, including the MD5 algorithm steps.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Task-steganalysis................................................................................................................3
2. Task- public key structure...................................................................................................3
3. Task –comparison...............................................................................................................4
4. Task - WinMD5 or MD5 hash generator............................................................................8
References................................................................................................................................10
1. Task-steganalysis................................................................................................................3
2. Task- public key structure...................................................................................................3
3. Task –comparison...............................................................................................................4
4. Task - WinMD5 or MD5 hash generator............................................................................8
References................................................................................................................................10
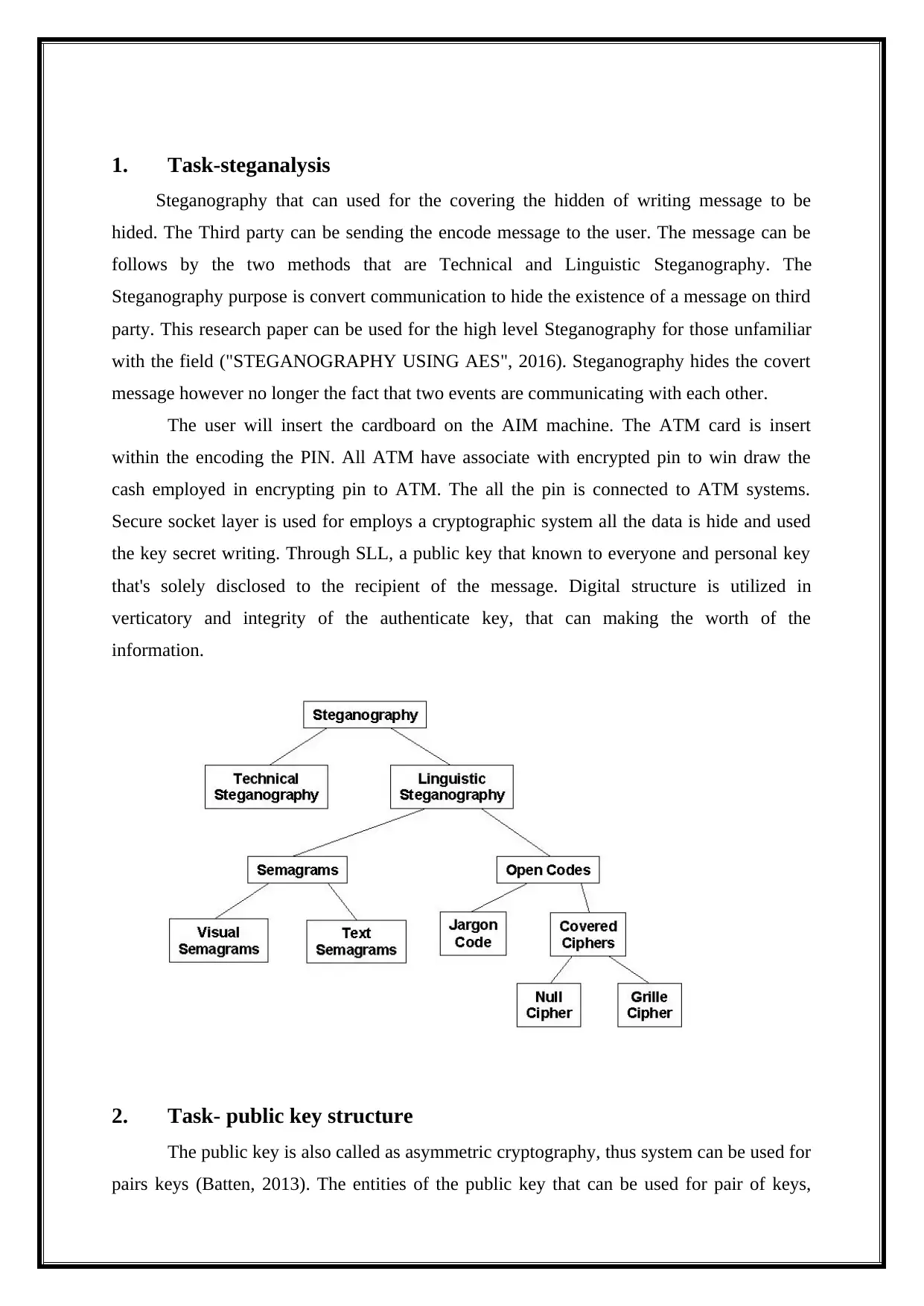
1. Task-steganalysis
Steganography that can used for the covering the hidden of writing message to be
hided. The Third party can be sending the encode message to the user. The message can be
follows by the two methods that are Technical and Linguistic Steganography. The
Steganography purpose is convert communication to hide the existence of a message on third
party. This research paper can be used for the high level Steganography for those unfamiliar
with the field ("STEGANOGRAPHY USING AES", 2016). Steganography hides the covert
message however no longer the fact that two events are communicating with each other.
The user will insert the cardboard on the AIM machine. The ATM card is insert
within the encoding the PIN. All ATM have associate with encrypted pin to win draw the
cash employed in encrypting pin to ATM. The all the pin is connected to ATM systems.
Secure socket layer is used for employs a cryptographic system all the data is hide and used
the key secret writing. Through SLL, a public key that known to everyone and personal key
that's solely disclosed to the recipient of the message. Digital structure is utilized in
verticatory and integrity of the authenticate key, that can making the worth of the
information.
2. Task- public key structure
The public key is also called as asymmetric cryptography, thus system can be used for
pairs keys (Batten, 2013). The entities of the public key that can be used for pair of keys,
Steganography that can used for the covering the hidden of writing message to be
hided. The Third party can be sending the encode message to the user. The message can be
follows by the two methods that are Technical and Linguistic Steganography. The
Steganography purpose is convert communication to hide the existence of a message on third
party. This research paper can be used for the high level Steganography for those unfamiliar
with the field ("STEGANOGRAPHY USING AES", 2016). Steganography hides the covert
message however no longer the fact that two events are communicating with each other.
The user will insert the cardboard on the AIM machine. The ATM card is insert
within the encoding the PIN. All ATM have associate with encrypted pin to win draw the
cash employed in encrypting pin to ATM. The all the pin is connected to ATM systems.
Secure socket layer is used for employs a cryptographic system all the data is hide and used
the key secret writing. Through SLL, a public key that known to everyone and personal key
that's solely disclosed to the recipient of the message. Digital structure is utilized in
verticatory and integrity of the authenticate key, that can making the worth of the
information.
2. Task- public key structure
The public key is also called as asymmetric cryptography, thus system can be used for
pairs keys (Batten, 2013). The entities of the public key that can be used for pair of keys,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
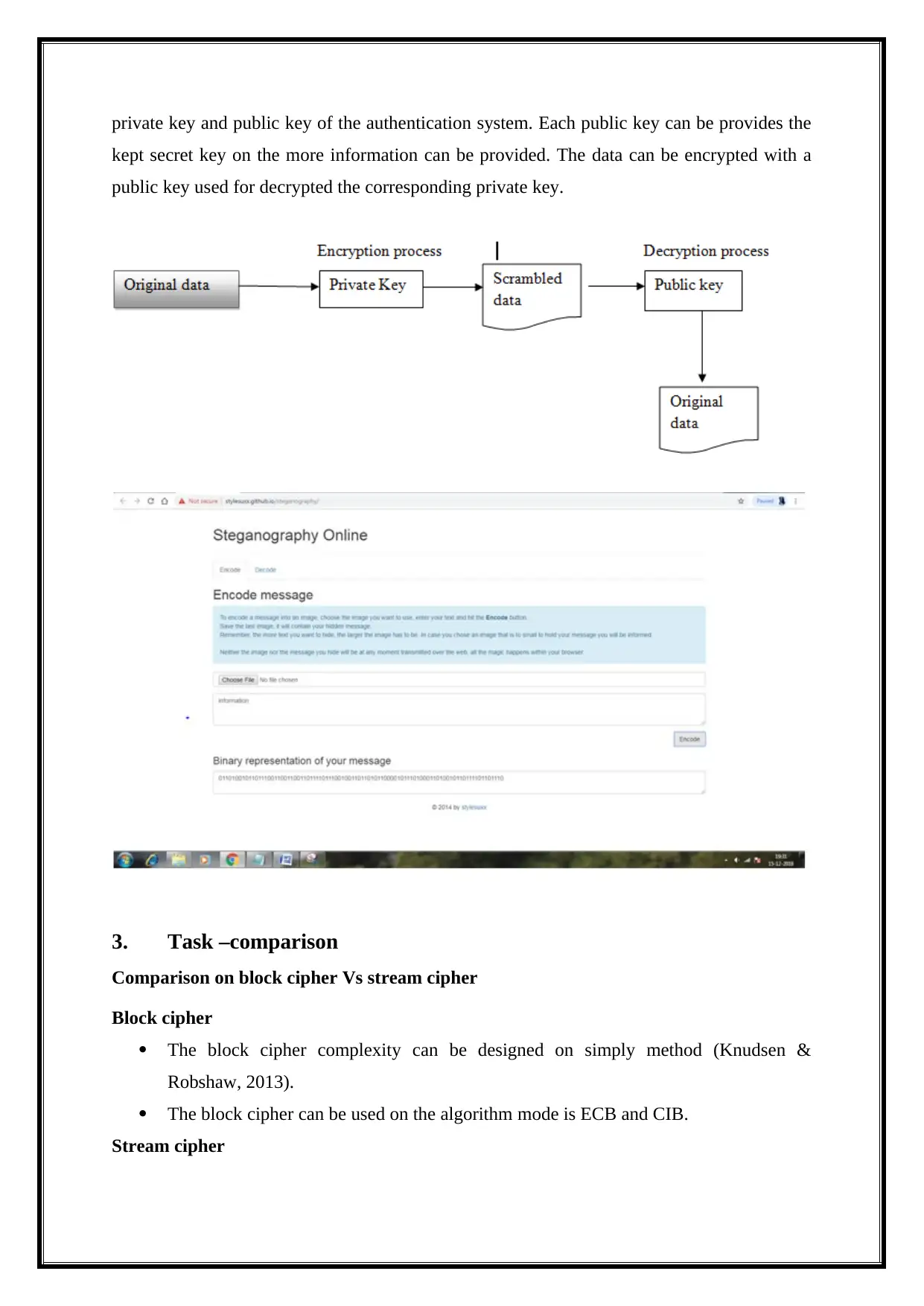
private key and public key of the authentication system. Each public key can be provides the
kept secret key on the more information can be provided. The data can be encrypted with a
public key used for decrypted the corresponding private key.
3. Task –comparison
Comparison on block cipher Vs stream cipher
Block cipher
The block cipher complexity can be designed on simply method (Knudsen &
Robshaw, 2013).
The block cipher can be used on the algorithm mode is ECB and CIB.
Stream cipher
kept secret key on the more information can be provided. The data can be encrypted with a
public key used for decrypted the corresponding private key.
3. Task –comparison
Comparison on block cipher Vs stream cipher
Block cipher
The block cipher complexity can be designed on simply method (Knudsen &
Robshaw, 2013).
The block cipher can be used on the algorithm mode is ECB and CIB.
Stream cipher
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
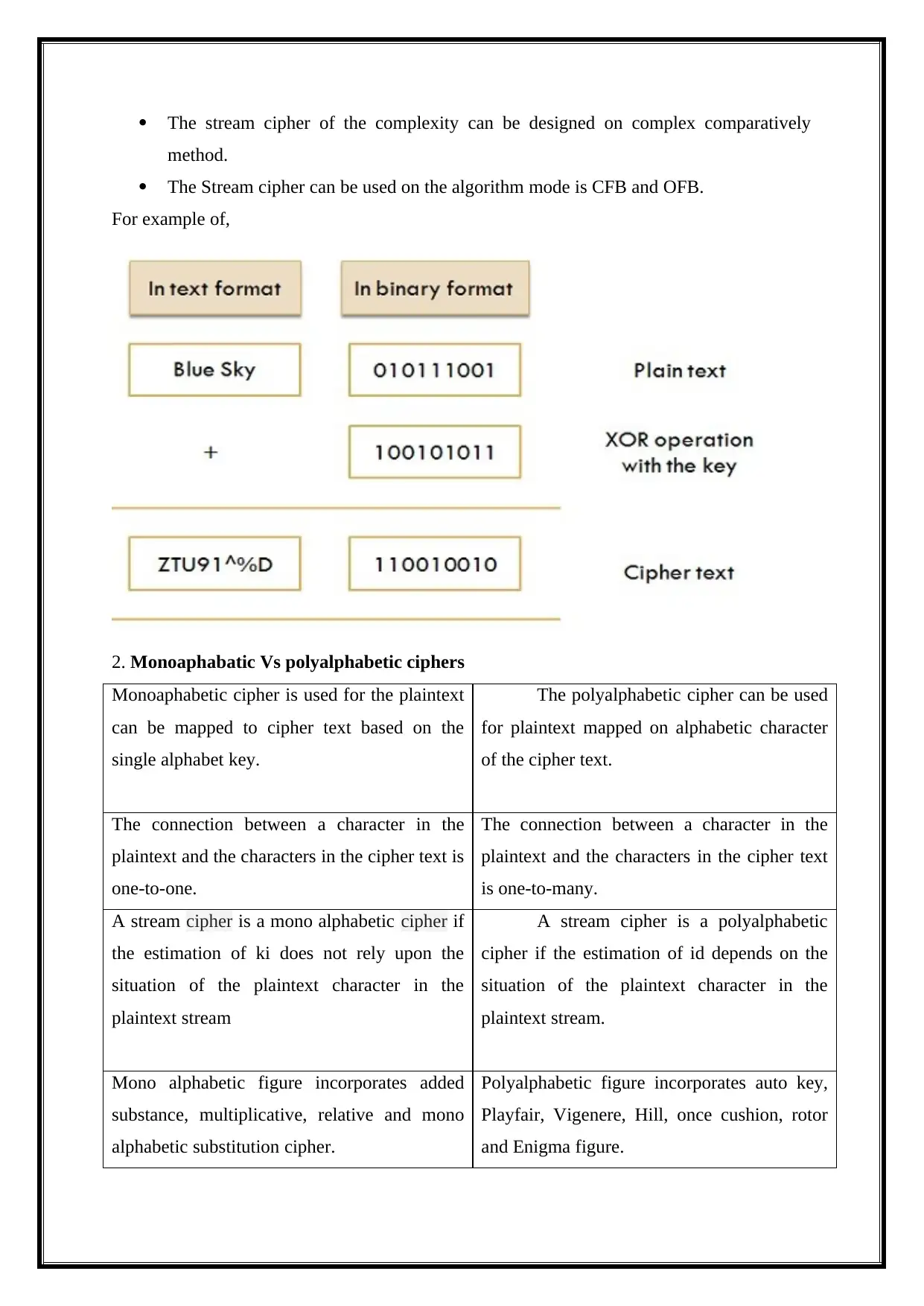
The stream cipher of the complexity can be designed on complex comparatively
method.
The Stream cipher can be used on the algorithm mode is CFB and OFB.
For example of,
2. Monoaphabatic Vs polyalphabetic ciphers
Monoaphabetic cipher is used for the plaintext
can be mapped to cipher text based on the
single alphabet key.
The polyalphabetic cipher can be used
for plaintext mapped on alphabetic character
of the cipher text.
The connection between a character in the
plaintext and the characters in the cipher text is
one-to-one.
The connection between a character in the
plaintext and the characters in the cipher text
is one-to-many.
A stream cipher is a mono alphabetic cipher if
the estimation of ki does not rely upon the
situation of the plaintext character in the
plaintext stream
A stream cipher is a polyalphabetic
cipher if the estimation of id depends on the
situation of the plaintext character in the
plaintext stream.
Mono alphabetic figure incorporates added
substance, multiplicative, relative and mono
alphabetic substitution cipher.
Polyalphabetic figure incorporates auto key,
Playfair, Vigenere, Hill, once cushion, rotor
and Enigma figure.
method.
The Stream cipher can be used on the algorithm mode is CFB and OFB.
For example of,
2. Monoaphabatic Vs polyalphabetic ciphers
Monoaphabetic cipher is used for the plaintext
can be mapped to cipher text based on the
single alphabet key.
The polyalphabetic cipher can be used
for plaintext mapped on alphabetic character
of the cipher text.
The connection between a character in the
plaintext and the characters in the cipher text is
one-to-one.
The connection between a character in the
plaintext and the characters in the cipher text
is one-to-many.
A stream cipher is a mono alphabetic cipher if
the estimation of ki does not rely upon the
situation of the plaintext character in the
plaintext stream
A stream cipher is a polyalphabetic
cipher if the estimation of id depends on the
situation of the plaintext character in the
plaintext stream.
Mono alphabetic figure incorporates added
substance, multiplicative, relative and mono
alphabetic substitution cipher.
Polyalphabetic figure incorporates auto key,
Playfair, Vigenere, Hill, once cushion, rotor
and Enigma figure.
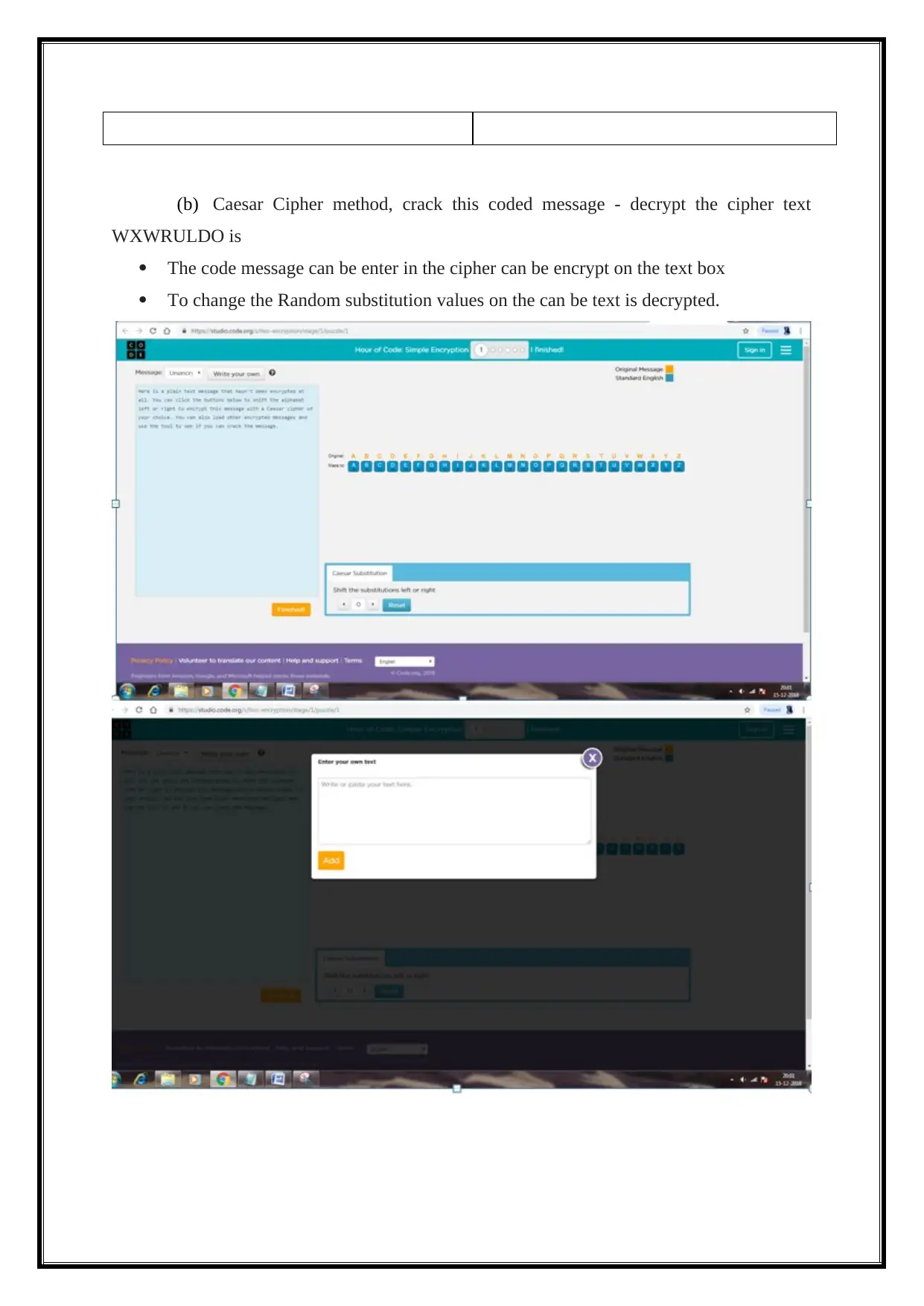
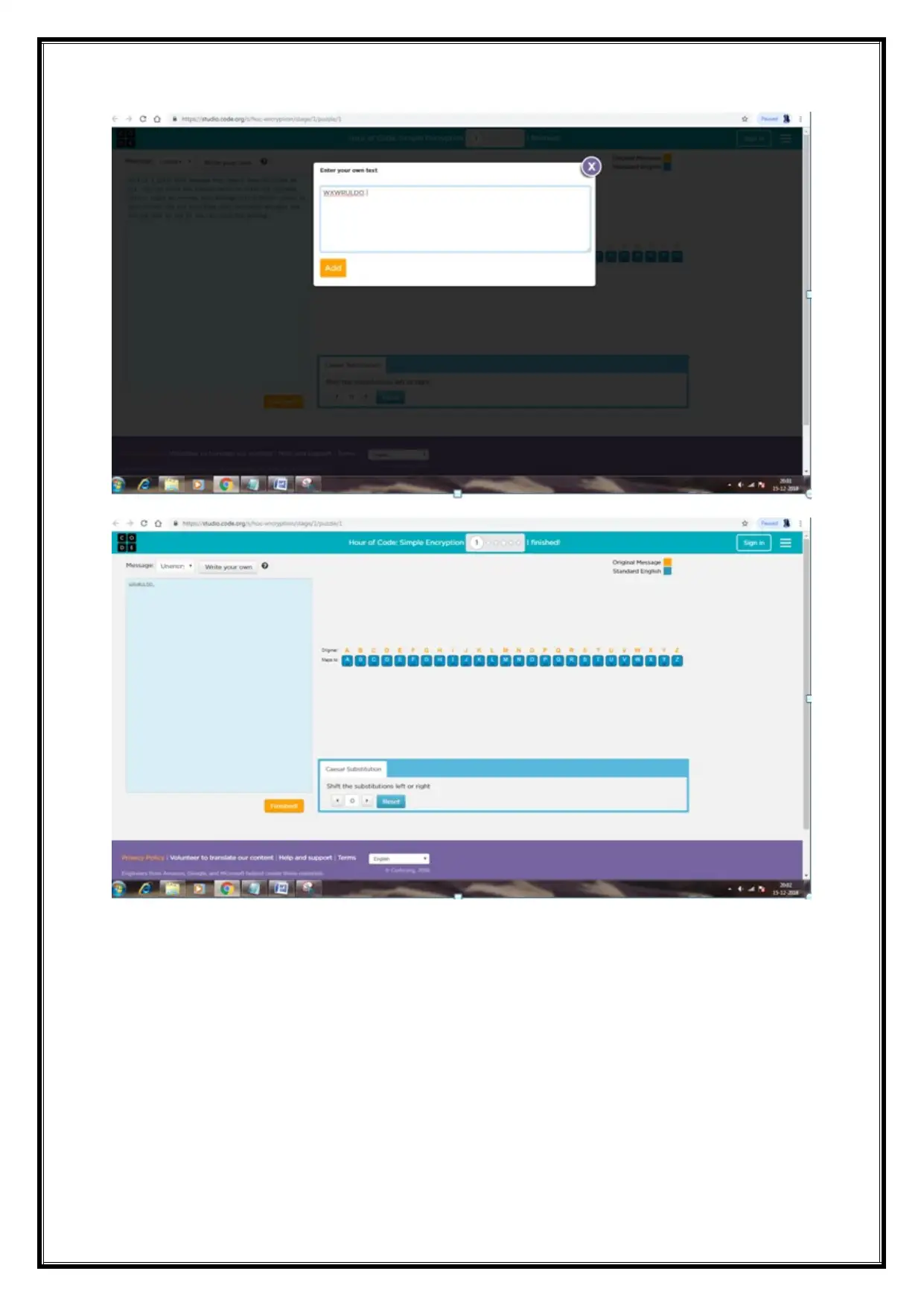
(b) Caesar Cipher method, crack this coded message - decrypt the cipher text
WXWRULDO is
The code message can be enter in the cipher can be encrypt on the text box
To change the Random substitution values on the can be text is decrypted.
WXWRULDO is
The code message can be enter in the cipher can be encrypt on the text box
To change the Random substitution values on the can be text is decrypted.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4. Task - WinMD5 or MD5 hash generator
The downloading on MD5 hash to be used the created on taking string and counting
on the length of encoding in 128 big finger print. The encoding of the string can be used for
MD5 algorithm it can be provided by the string length is 128 bit of the hash value output
(Menezes, 2010). The MD5 hashes can be used for storing the password and credit card
number of the sensitive data integrity of files.
The downloading on MD5 hash to be used the created on taking string and counting
on the length of encoding in 128 big finger print. The encoding of the string can be used for
MD5 algorithm it can be provided by the string length is 128 bit of the hash value output
(Menezes, 2010). The MD5 hashes can be used for storing the password and credit card
number of the sensitive data integrity of files.
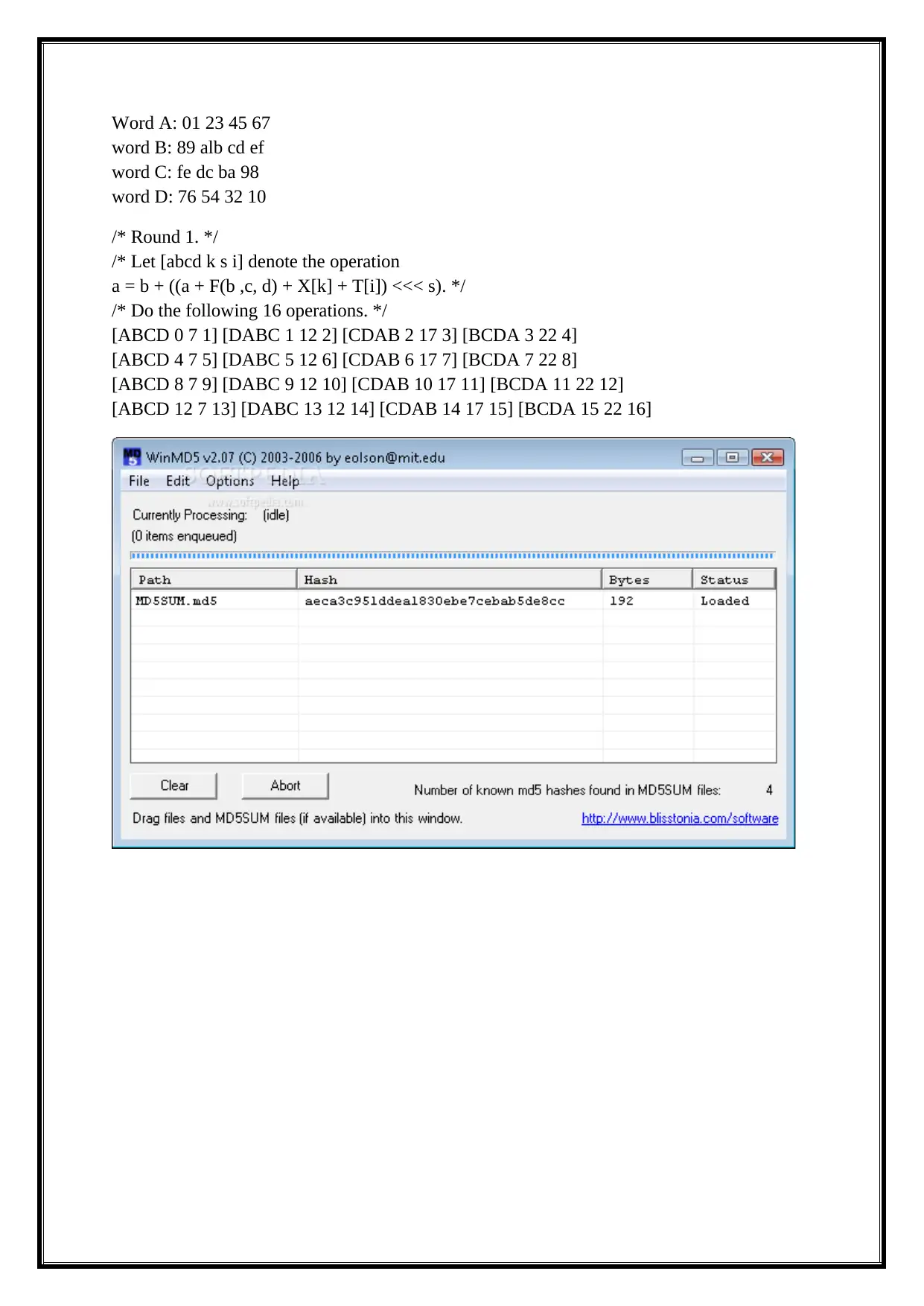
Word A: 01 23 45 67
word B: 89 alb cd ef
word C: fe dc ba 98
word D: 76 54 32 10
/* Round 1. */
/* Let [abcd k s i] denote the operation
a = b + ((a + F(b ,c, d) + X[k] + T[i]) <<< s). */
/* Do the following 16 operations. */
[ABCD 0 7 1] [DABC 1 12 2] [CDAB 2 17 3] [BCDA 3 22 4]
[ABCD 4 7 5] [DABC 5 12 6] [CDAB 6 17 7] [BCDA 7 22 8]
[ABCD 8 7 9] [DABC 9 12 10] [CDAB 10 17 11] [BCDA 11 22 12]
[ABCD 12 7 13] [DABC 13 12 14] [CDAB 14 17 15] [BCDA 15 22 16]
word B: 89 alb cd ef
word C: fe dc ba 98
word D: 76 54 32 10
/* Round 1. */
/* Let [abcd k s i] denote the operation
a = b + ((a + F(b ,c, d) + X[k] + T[i]) <<< s). */
/* Do the following 16 operations. */
[ABCD 0 7 1] [DABC 1 12 2] [CDAB 2 17 3] [BCDA 3 22 4]
[ABCD 4 7 5] [DABC 5 12 6] [CDAB 6 17 7] [BCDA 7 22 8]
[ABCD 8 7 9] [DABC 9 12 10] [CDAB 10 17 11] [BCDA 11 22 12]
[ABCD 12 7 13] [DABC 13 12 14] [CDAB 14 17 15] [BCDA 15 22 16]
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
Batten, L. (2013). Public key cryptography. Hoboken, N.J.: Chichester.
Knudsen, L., & Robshaw, M. (2013). The Block Cipher Companion. Berlin: Springer Berlin.
Menaces, A. (2010). Advances in cryptology - CRYPTO 2007. Berlin: Springer.
STEGANOGRAPHY USING AES. (2016). International Journal Of Modern Trends In
Engineering & Research, 3(8), 139-146. doi: 10.21884/ijmter.2016.3018.fe7ds
Batten, L. (2013). Public key cryptography. Hoboken, N.J.: Chichester.
Knudsen, L., & Robshaw, M. (2013). The Block Cipher Companion. Berlin: Springer Berlin.
Menaces, A. (2010). Advances in cryptology - CRYPTO 2007. Berlin: Springer.
STEGANOGRAPHY USING AES. (2016). International Journal Of Modern Trends In
Engineering & Research, 3(8), 139-146. doi: 10.21884/ijmter.2016.3018.fe7ds
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





