Evaluating Cryptographic Techniques: Security and Future Trends
VerifiedAdded on 2023/06/14
|13
|3580
|427
Report
AI Summary
This report provides an overview of cryptographic techniques in the context of evolving technologies, emphasizing the importance of data security. It discusses the historical evolution of cryptography, from ancient ciphers to modern encryption methods, and highlights the crucial role of cryptography in ensuring confidentiality, integrity, and authentication of data. The report categorizes encryption techniques into symmetric, asymmetric, and hashing methods, detailing their respective applications and challenges. It addresses research gaps in cryptographic techniques, including the need for new asymmetric algorithms and improved security modeling. The report also identifies limitations in current research, such as unrealistic simplifying assumptions and the lack of comprehensive approaches to security modeling. It concludes by emphasizing the continuous evolution of cryptographic technology and the ongoing need for advancements to address emerging security threats. This report is available on Desklib, a platform providing study tools and solved assignments for students.

1
CRYPTOGRAPHIC TECHNIQUE
Name
Course
Professor
School
City
Date
CRYPTOGRAPHIC TECHNIQUE
Name
Course
Professor
School
City
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
Abstract
In recent years, the use of advanced
technology has increased and the demand
for protecting data in a more secure way. In
order to do there are few certain changes
happened in the cryptographic techniques.
Until 1970, the term cryptography refers to
the protection of data from unauthorized
access and it was said providing security of
the data would help to validate all the data
security criteria [5]. The new perspective of
the cryptography had been introduced by the
Diffie and Hellman. The advancement of the
cryptography has developed the different
methods of cryptographic techniques.
Different cryptographic techniques have
been developed and the application of the
different types of technique depends on the
requirement of the situation. The main
purpose of this paper is to understand the
cryptographic techniques and its different
types with the perspective of the emerging
technologies and the impact of
cryptographic techniques in the changing
scenario of the technology. This will help to
generate the basic understanding of the
cryptographic technique along with
providing the problem-solving solutions
with the help of these techniques [14]. The
advantages and disadvantages of using these
techniques are needed to be evaluated in the
context of the information security. The
cryptography in general consists of the two
sections- cryptography and the
cryptanalysis. In order to understand the
cryptographic technique, the difference and
the relation between these two terms are
needed to be analyzed. The result that has
been found from the analysis will help to
indicate the benefits of different
cryptographic techniques along with the
future improvement and possibilities of the
further application.
Keywords- security issues, cryptography,
encryption, decryption
Abstract
In recent years, the use of advanced
technology has increased and the demand
for protecting data in a more secure way. In
order to do there are few certain changes
happened in the cryptographic techniques.
Until 1970, the term cryptography refers to
the protection of data from unauthorized
access and it was said providing security of
the data would help to validate all the data
security criteria [5]. The new perspective of
the cryptography had been introduced by the
Diffie and Hellman. The advancement of the
cryptography has developed the different
methods of cryptographic techniques.
Different cryptographic techniques have
been developed and the application of the
different types of technique depends on the
requirement of the situation. The main
purpose of this paper is to understand the
cryptographic techniques and its different
types with the perspective of the emerging
technologies and the impact of
cryptographic techniques in the changing
scenario of the technology. This will help to
generate the basic understanding of the
cryptographic technique along with
providing the problem-solving solutions
with the help of these techniques [14]. The
advantages and disadvantages of using these
techniques are needed to be evaluated in the
context of the information security. The
cryptography in general consists of the two
sections- cryptography and the
cryptanalysis. In order to understand the
cryptographic technique, the difference and
the relation between these two terms are
needed to be analyzed. The result that has
been found from the analysis will help to
indicate the benefits of different
cryptographic techniques along with the
future improvement and possibilities of the
further application.
Keywords- security issues, cryptography,
encryption, decryption

3
Introduction
The elevated improvement to the network
technological innovation contributes to a
standard culture to interchange the data
among various consumers extensively [1].
Therefore, this causes a major issue to the
privacy, identity theft, electronic payments
and security concerns since it is much more
accessible to rebuild a copy of a data which
the hazardous user steal from the guided end
user. It is necessary for information to be
protected from these hackers and it should
be read or maybe employed only by
personnel who are authorized to do so [12].
The sensitive data such as ATM cards,
banking dealings and public security
numbers requires more security. The data
such as texts, images are divulged via the
network [2]. The mobile coverage
communication continues to grow since
people can easily access the internet via the
mobile every time they are use them [4].
The mobile Ad-hoc Network generally
consists of a group of the mobile nodes
which have the functionality of the self-
company, particularly in the decentralized
manner without the present infrastructure.
Cryptography is widely seen as the standard
way in which electronic documents are
protected. Cryptography is also regarded as
hiding of the data and substantiation. It
consists of protocols, algorithms and
methods to prevent access of the hackers
protected data [2]. There are various
encryption approaches that are used to
protect secret data from the unauthorized use
[2]. Encryption is a method that is utilized to
promote the security of data. This method
generally converts the data to a format that
is considered cipher text and decryption
techniques. With regards to the
cryptography, a block cipher operates to the
fixed length groups of the bits, which can be
termed as blocks with a regular
transformation. When it comes to encrypting
a block cipher usually takes 128 bits input
Introduction
The elevated improvement to the network
technological innovation contributes to a
standard culture to interchange the data
among various consumers extensively [1].
Therefore, this causes a major issue to the
privacy, identity theft, electronic payments
and security concerns since it is much more
accessible to rebuild a copy of a data which
the hazardous user steal from the guided end
user. It is necessary for information to be
protected from these hackers and it should
be read or maybe employed only by
personnel who are authorized to do so [12].
The sensitive data such as ATM cards,
banking dealings and public security
numbers requires more security. The data
such as texts, images are divulged via the
network [2]. The mobile coverage
communication continues to grow since
people can easily access the internet via the
mobile every time they are use them [4].
The mobile Ad-hoc Network generally
consists of a group of the mobile nodes
which have the functionality of the self-
company, particularly in the decentralized
manner without the present infrastructure.
Cryptography is widely seen as the standard
way in which electronic documents are
protected. Cryptography is also regarded as
hiding of the data and substantiation. It
consists of protocols, algorithms and
methods to prevent access of the hackers
protected data [2]. There are various
encryption approaches that are used to
protect secret data from the unauthorized use
[2]. Encryption is a method that is utilized to
promote the security of data. This method
generally converts the data to a format that
is considered cipher text and decryption
techniques. With regards to the
cryptography, a block cipher operates to the
fixed length groups of the bits, which can be
termed as blocks with a regular
transformation. When it comes to encrypting
a block cipher usually takes 128 bits input
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4
and output as well as a secret key. In this
research study, it will discuss various
methods of the cryptographic. The main
purpose of the study would be to gain a
understanding of cryptographic approaches
due to changing scenario of the technology.
Research problem
In this research, it aims to address the aspect
of cryptographic techniques. Hence, the
research problem which has been
highlighted to this topic are as below:
• What are the cryptographic techniques?
• What are the various research gaps
which exist in cryptographic techniques?
• What are the challenges/problems
associated with the cryptographic
techniques?
Research justification
The purpose of this research is aimed to
discuss the topic in cryptographic
techniques. There are numerous aspects that
will be discussed in the research [5]. The
new knowledge would add new literature for
the learners and at the same time identify
research gaps in the subject which would
form the further studies.
Literature review
Overview of the technology involved
Cryptography has a long history, which is
from ancients’ ciphers, for example, Ceaser
Cipher, machine cipher during the WWI and
WWII along with the modern ciphers [3].
These play a crucial role when it comes to
offering confidentiality, Integrity and
Authentication of the services particularly in
transmission, processing and storage of the
sensitive data over open networks [10]. The
cryptographic protocols makes agreements
or decisions between the two parties through
the internet using cryptosystems and hash
functions that provide key management,
verification, authentication and
identification protocols to the practice [6].
and output as well as a secret key. In this
research study, it will discuss various
methods of the cryptographic. The main
purpose of the study would be to gain a
understanding of cryptographic approaches
due to changing scenario of the technology.
Research problem
In this research, it aims to address the aspect
of cryptographic techniques. Hence, the
research problem which has been
highlighted to this topic are as below:
• What are the cryptographic techniques?
• What are the various research gaps
which exist in cryptographic techniques?
• What are the challenges/problems
associated with the cryptographic
techniques?
Research justification
The purpose of this research is aimed to
discuss the topic in cryptographic
techniques. There are numerous aspects that
will be discussed in the research [5]. The
new knowledge would add new literature for
the learners and at the same time identify
research gaps in the subject which would
form the further studies.
Literature review
Overview of the technology involved
Cryptography has a long history, which is
from ancients’ ciphers, for example, Ceaser
Cipher, machine cipher during the WWI and
WWII along with the modern ciphers [3].
These play a crucial role when it comes to
offering confidentiality, Integrity and
Authentication of the services particularly in
transmission, processing and storage of the
sensitive data over open networks [10]. The
cryptographic protocols makes agreements
or decisions between the two parties through
the internet using cryptosystems and hash
functions that provide key management,
verification, authentication and
identification protocols to the practice [6].
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
The security of cryptographic protocols for
most of the times need be proved in details
that are under theoretical assumptions before
practical harness [9]. Currently, there has
been new kind of secure or private protocols
which have become more practical. There
have been new types of cyber business
which are available [6]. Each day
individuals enjoy cryptography since they
can send secure messages over the SNS to
friends, and they can secure their financial
transactions over the internet. Each
individual understands that the security and
privacy with use of cryptography are
everywhere.
Relevant technologies and applications of
those technologies
There are various technologies which are
used for encrypting and keeping the
information secure. One of the technologies
is selective encryption. This is a technique
for encrypting some parts of a condensed
information file and leaving the other
section of the plaintext unencrypted [7].
This type of encryption saves time and cost
of the data to be encrypted. The encryption
techniques are classified into 3 types these
are; symmetric, asymmetric and hashing.
Symmetric vital cryptography technology is
an algorithm which utilizes similar
cryptographic keys to both the encryption
and decryption purposes. It might be
indistinguishable [8]. To maintain a personal
data link this type of algorithm utilizes
special key which represents a secret that is
to be shared among the users. Another type
of technology is asymmetric cryptosystems
which uses one key to encrypt the message
and another key to decrypt the same kind of
message which is transferred to the
destination [5]. It is also considered the
public key cryptosystems. In asymmetric
algorithm, the secret could be shared among
many users who require that type of data.
The hash technologies are the algorithms
which use no key. There are considered one-
The security of cryptographic protocols for
most of the times need be proved in details
that are under theoretical assumptions before
practical harness [9]. Currently, there has
been new kind of secure or private protocols
which have become more practical. There
have been new types of cyber business
which are available [6]. Each day
individuals enjoy cryptography since they
can send secure messages over the SNS to
friends, and they can secure their financial
transactions over the internet. Each
individual understands that the security and
privacy with use of cryptography are
everywhere.
Relevant technologies and applications of
those technologies
There are various technologies which are
used for encrypting and keeping the
information secure. One of the technologies
is selective encryption. This is a technique
for encrypting some parts of a condensed
information file and leaving the other
section of the plaintext unencrypted [7].
This type of encryption saves time and cost
of the data to be encrypted. The encryption
techniques are classified into 3 types these
are; symmetric, asymmetric and hashing.
Symmetric vital cryptography technology is
an algorithm which utilizes similar
cryptographic keys to both the encryption
and decryption purposes. It might be
indistinguishable [8]. To maintain a personal
data link this type of algorithm utilizes
special key which represents a secret that is
to be shared among the users. Another type
of technology is asymmetric cryptosystems
which uses one key to encrypt the message
and another key to decrypt the same kind of
message which is transferred to the
destination [5]. It is also considered the
public key cryptosystems. In asymmetric
algorithm, the secret could be shared among
many users who require that type of data.
The hash technologies are the algorithms
which use no key. There are considered one-
6
way encryption. At any given plaintext a
fixed size hash value is generally calculated
[13]. This is because of the content which is
contained in the plaintext and it cannot be
brought back.
The symmetric and asymmetric encryption
techniques that are available are DES,
3DES, Blowfish, and RSA.
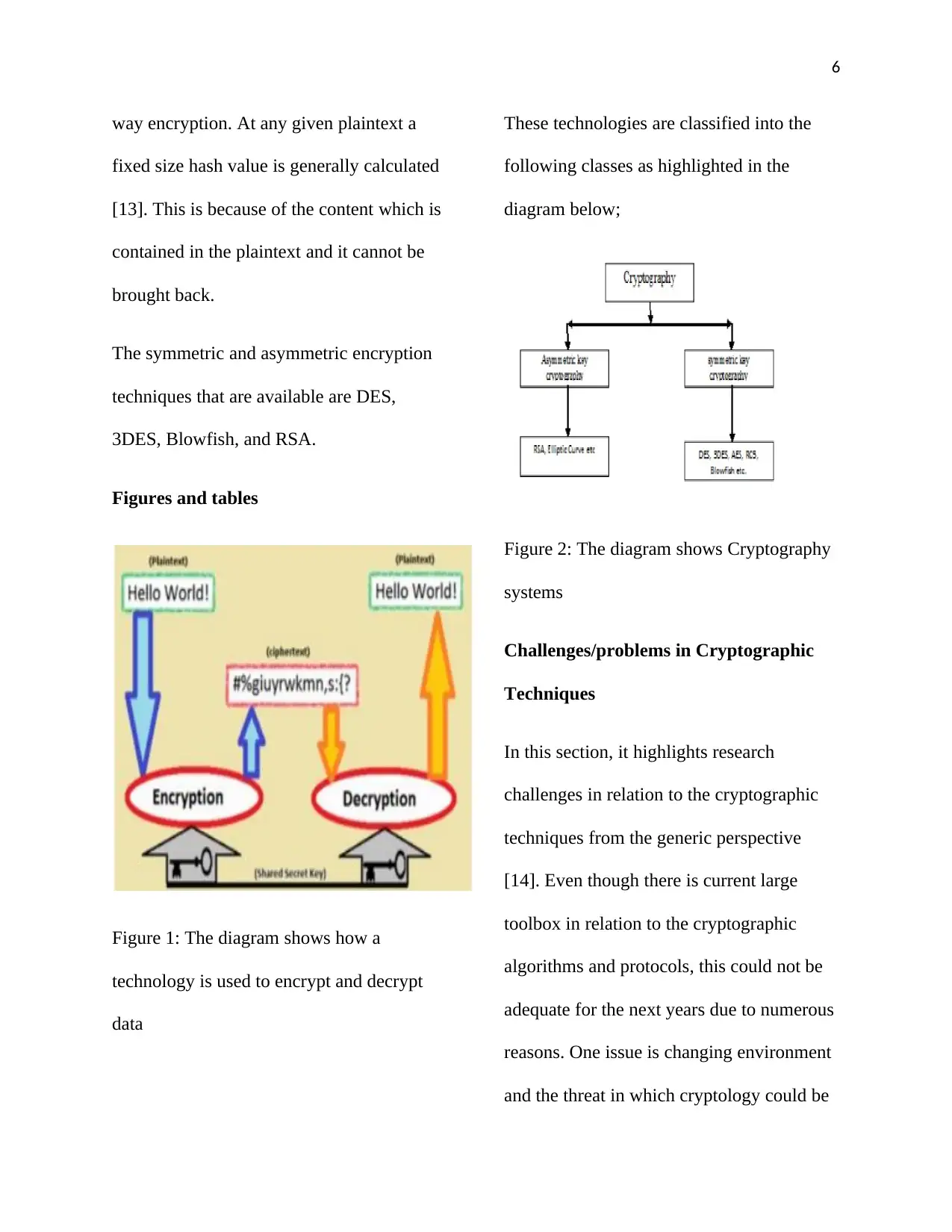
Figures and tables
Figure 1: The diagram shows how a
technology is used to encrypt and decrypt
data
These technologies are classified into the
following classes as highlighted in the
diagram below;
Figure 2: The diagram shows Cryptography
systems
Challenges/problems in Cryptographic
Techniques
In this section, it highlights research
challenges in relation to the cryptographic
techniques from the generic perspective
[14]. Even though there is current large
toolbox in relation to the cryptographic
algorithms and protocols, this could not be
adequate for the next years due to numerous
reasons. One issue is changing environment
and the threat in which cryptology could be
way encryption. At any given plaintext a
fixed size hash value is generally calculated
[13]. This is because of the content which is
contained in the plaintext and it cannot be
brought back.
The symmetric and asymmetric encryption
techniques that are available are DES,
3DES, Blowfish, and RSA.
Figures and tables
Figure 1: The diagram shows how a
technology is used to encrypt and decrypt
data
These technologies are classified into the
following classes as highlighted in the
diagram below;
Figure 2: The diagram shows Cryptography
systems
Challenges/problems in Cryptographic
Techniques
In this section, it highlights research
challenges in relation to the cryptographic
techniques from the generic perspective
[14]. Even though there is current large
toolbox in relation to the cryptographic
algorithms and protocols, this could not be
adequate for the next years due to numerous
reasons. One issue is changing environment
and the threat in which cryptology could be
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
deployed [8]. Currently, we are evolving
towards ambient intelligence, ubiquitous
computing and pervasive networking which
has completely new characteristics [1]. The
next challenge is the erosion of
computational difficulty in relation to the
mathematical issues that cryptology
continues to be based. This type of erosion
is created in part by the development in the
computation and part of the development of
the cryptographic implementations including
insufficient physical security in the devices
[17].
The research issues in the asymmetric
cryptology system are definitely not smaller.
The first one is on security reductions that
are more focused on asymmetric cryptology
[15]. In relation to this kind of research, one
attempt to prove that security of the
cryptographic primitive protocol might be
reduced the assumption of problems in
mathematical concern. The research focuses
on studies efficient and meaningful
reductions, to reduce the assumptions that
are utilized in the proof [18]. It needs to be
noted that security of majority of
asymmetric primitives depends on small set
of issues from the algebraic number theory
[16]. Any of the breakthroughs in solving
some of the issues could have dramatic
consequences. This clearly shows there is a
need for new asymmetric algorithms that
depends on new issues.
Identification of any gaps in the literature
by:
Discussions of areas/issues that you
believe have been addressed in the
current literature.
In this research, it has discussed different
methods of cryptographic techniques. There
have been different cryptographic
techniques that have been developed and
applications with the perspective to the
emerging technologies [19]. This research
will help in understanding of the
deployed [8]. Currently, we are evolving
towards ambient intelligence, ubiquitous
computing and pervasive networking which
has completely new characteristics [1]. The
next challenge is the erosion of
computational difficulty in relation to the
mathematical issues that cryptology
continues to be based. This type of erosion
is created in part by the development in the
computation and part of the development of
the cryptographic implementations including
insufficient physical security in the devices
[17].
The research issues in the asymmetric
cryptology system are definitely not smaller.
The first one is on security reductions that
are more focused on asymmetric cryptology
[15]. In relation to this kind of research, one
attempt to prove that security of the
cryptographic primitive protocol might be
reduced the assumption of problems in
mathematical concern. The research focuses
on studies efficient and meaningful
reductions, to reduce the assumptions that
are utilized in the proof [18]. It needs to be
noted that security of majority of
asymmetric primitives depends on small set
of issues from the algebraic number theory
[16]. Any of the breakthroughs in solving
some of the issues could have dramatic
consequences. This clearly shows there is a
need for new asymmetric algorithms that
depends on new issues.
Identification of any gaps in the literature
by:
Discussions of areas/issues that you
believe have been addressed in the
current literature.
In this research, it has discussed different
methods of cryptographic techniques. There
have been different cryptographic
techniques that have been developed and
applications with the perspective to the
emerging technologies [19]. This research
will help in understanding of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
cryptographic techniques and how to solve
the problems. In this research, it has
proposed comparison to numerous
cryptographic algorithms. Algorithms have
been evaluated to the numerous files. The
area of the research has also been on
information security which aims to protect
the information from hazardous attackers
whilst permitting legitimate customers to
manipulate data easily [20]. The study also
discussed what cryptography is which is
regarded as the branch of information
security that covers study of the algorithms
and protocols which secure the data. This
area of research is diverse and it takes on the
components of the electronic engineering,
computer science, algebraic number theory,
mathematics including the computational
number theory [12]. The research would
also study theoretical limitations and some
practical implications. There has been a
wide range of issues in this field for the
provable aspect of security, which focus on
the problems associated with the random
oracle model. There have been also issues
related to challenges which are associated
with the cryptographic securities [15].
Highlighting areas/issues that have not
been addressed or adequately addressed
Despite many significant successes in the
research of cryptographic techniques,
research has not advanced as far as one
could think. There has been heated debate
on how we should formally model security
in relation to cryptographic, relationship
between provable securities and complexity
theory which is still not understood well
[12]. Moreover, it is important to note that
underpinning on this research area is
inconsistently applied and it is fully
unrealistic simplifying on the assumptions.
There have been limitations which are
accepted just because it is unclear on how to
proceed without them. The research has not
highlighted approaches to the security
modeling for the cryptographic techniques.
cryptographic techniques and how to solve
the problems. In this research, it has
proposed comparison to numerous
cryptographic algorithms. Algorithms have
been evaluated to the numerous files. The
area of the research has also been on
information security which aims to protect
the information from hazardous attackers
whilst permitting legitimate customers to
manipulate data easily [20]. The study also
discussed what cryptography is which is
regarded as the branch of information
security that covers study of the algorithms
and protocols which secure the data. This
area of research is diverse and it takes on the
components of the electronic engineering,
computer science, algebraic number theory,
mathematics including the computational
number theory [12]. The research would
also study theoretical limitations and some
practical implications. There has been a
wide range of issues in this field for the
provable aspect of security, which focus on
the problems associated with the random
oracle model. There have been also issues
related to challenges which are associated
with the cryptographic securities [15].
Highlighting areas/issues that have not
been addressed or adequately addressed
Despite many significant successes in the
research of cryptographic techniques,
research has not advanced as far as one
could think. There has been heated debate
on how we should formally model security
in relation to cryptographic, relationship
between provable securities and complexity
theory which is still not understood well
[12]. Moreover, it is important to note that
underpinning on this research area is
inconsistently applied and it is fully
unrealistic simplifying on the assumptions.
There have been limitations which are
accepted just because it is unclear on how to
proceed without them. The research has not
highlighted approaches to the security
modeling for the cryptographic techniques.

9
There is little research which has been
undertaken on this subject [6]. There has
been continuous fear towards the security
aspects and possibility of dependency of
system in handling the automatic systems.
There are also gaps in relation to the coding
systems with focus on encryption
techniques, mechanism and scientific
methods to assist in raising the security
efficiency. These issues have not been
addressed in this study.
Discussing your view(s) on the issue(s)
that you see as being a critic
In this research, there are issues which are
critical such as cryptography that is essential
to the security as well as the integrity of the
data [9]. In this research, it has examined on
these concepts and explained how it
enhances security within the various
applications [9]. The research has explained
security method that makes use of various
cryptographic techniques in order to encrypt
the data and at the same time make it to be
unreadable form. There have been
cryptographic techniques which have been
highlighted and discussed in details. Another
part of the research which was crucial was
on the discussion on the challenges and the
problems which have been exhibited in the
cryptographic techniques. These issues have
been discussed in details within this research
[16]. There has also been an evolution of the
cryptographic technology from the secret art
to the modern science. Another critical issue
highlighted in the research is challenging
issues in the area of the cryptographic
algorithms and protocols. How Encryption is
carried out has also been crucial and has
been examined in the study [2].
Summarize the future research directions
based on the identified gaps
The future direction would likely focus more
on use of cryptography in cloud; this would
ensure there is security of data being shared
[5]. Moreover, confidentiality, integrity and
data security will also be considered [1]. The
There is little research which has been
undertaken on this subject [6]. There has
been continuous fear towards the security
aspects and possibility of dependency of
system in handling the automatic systems.
There are also gaps in relation to the coding
systems with focus on encryption
techniques, mechanism and scientific
methods to assist in raising the security
efficiency. These issues have not been
addressed in this study.
Discussing your view(s) on the issue(s)
that you see as being a critic
In this research, there are issues which are
critical such as cryptography that is essential
to the security as well as the integrity of the
data [9]. In this research, it has examined on
these concepts and explained how it
enhances security within the various
applications [9]. The research has explained
security method that makes use of various
cryptographic techniques in order to encrypt
the data and at the same time make it to be
unreadable form. There have been
cryptographic techniques which have been
highlighted and discussed in details. Another
part of the research which was crucial was
on the discussion on the challenges and the
problems which have been exhibited in the
cryptographic techniques. These issues have
been discussed in details within this research
[16]. There has also been an evolution of the
cryptographic technology from the secret art
to the modern science. Another critical issue
highlighted in the research is challenging
issues in the area of the cryptographic
algorithms and protocols. How Encryption is
carried out has also been crucial and has
been examined in the study [2].
Summarize the future research directions
based on the identified gaps
The future direction would likely focus more
on use of cryptography in cloud; this would
ensure there is security of data being shared
[5]. Moreover, confidentiality, integrity and
data security will also be considered [1]. The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
future research would also highlight in
details cryptographic techniques since
currently there is only overview of the
research. The research would discuss in
details security and the privacy challenges
which are related to the cryptographic
techniques.
The future research directs would also
discuss methodologies in cryptographic
techniques. There would be a comparative
research in relation to symmetric encryption
techniques and images in information
techniques [11]. The major concerns in the
literature gaps are on the aspect of security,
therefore the future research directions
would focus o the different encryption
techniques which are majorly based on the
security, performance and behavior [8]. The
study would also undertake a comprehensive
research in relation to the comparative study
on the numerous security algorithms.
Conclusion
In this research study it discussed the
cryptographic techniques. The discussion
has further highlighted numerous
technologies that are related to the
cryptographic. Furthermore, it has discussed
challenges and issues related to the
cryptographic techniques along with the
research gaps which require further research
on this topic.
future research would also highlight in
details cryptographic techniques since
currently there is only overview of the
research. The research would discuss in
details security and the privacy challenges
which are related to the cryptographic
techniques.
The future research directs would also
discuss methodologies in cryptographic
techniques. There would be a comparative
research in relation to symmetric encryption
techniques and images in information
techniques [11]. The major concerns in the
literature gaps are on the aspect of security,
therefore the future research directions
would focus o the different encryption
techniques which are majorly based on the
security, performance and behavior [8]. The
study would also undertake a comprehensive
research in relation to the comparative study
on the numerous security algorithms.
Conclusion
In this research study it discussed the
cryptographic techniques. The discussion
has further highlighted numerous
technologies that are related to the
cryptographic. Furthermore, it has discussed
challenges and issues related to the
cryptographic techniques along with the
research gaps which require further research
on this topic.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11
References
[1] Belguith, S., Jemai, A. and Attia, R.,
2015. Enhancing data security in cloud
computing using a lightweight cryptographic
algorithm. In The Eleventh International
Conference On Autonomic and Systems (pp.
98-103). Retrieved At:
https://www.researchgate.net/file.PostFileLo
ader.html?
id=58821cb3b0366d338b4f8b63&assetKey
=AS
%3A452609975820288%401484922035372
[2] Büscher, N. and Katzenbeisser, S., 2017.
Introduction. In Compilation for Secure
Multi-party Computation (pp. 1-4).
Springer, Cham. Retrieved At:
https://www.econstor.eu/bitstream/10419/52
400/1/664103677.pdf
[3] Dachman-Soled, D., Liu, F.H. and Zhou,
H.S., 2015, April. Leakage-resilient circuits
revisited–optimal number of computing
components without leak-free hardware. In
Annual International Conference on the
Theory and Applications of Cryptographic
Techniques (pp. 131-158). Springer, Berlin,
Heidelberg. Retrieved At:
https://www.iacr.org/archive/eurocrypt2015/
90560217/90560217.pdf
[4] Dent, A.W., 2006. Fundamental
problems in provable security and
cryptography. Philosophical Transactions of
the Royal Society of London A:
Mathematical, Physical and Engineering
Sciences, 364(1849), pp.3215-3230.
Retrieved At:
https://pdfs.semanticscholar.org/3c74/272b9
5ca1822bc0d48b398c5a828d7c26b03.pdf
[5] Gautam, S., Mishra, S. and Shrivastava,
M., 2017. A Survey on Generation and
Evolution of Various Cryptographic
Techniques. Retrieved At:
https://irjet.net/archives/V4/i1/IRJET-
V4I1157.pdf
[6] George, J. A., & Hemalatha, M. (2015).
Cryptographic Techniques, Threats and
Privacy Challenges in Cloud Computing.
Governance, 500, 2. Retrieved At:
https://pdfs.semanticscholar.org/b92e/11b2a
f6a22d3475eaacf1ca4e77455387885.pdf
[7] Iyer, K.P., Anusha, R. and Priya, R.S.,
2014. Comparative study on various
cryptographic techniques. In International
Journal of Computer Applications,
International Conference on
Communication, Computing and
Information Technology (ICCCMIT-2014)
(pp. 37-42). Retrieved At:
https://pdfs.semanticscholar.org/69a8/b80ef
1296eb391f125a736771e58c897af8b.pdf
[8] Jain, G. and Sejwar, V., 2017, June.
Improving the security by using various
cryptographic techniques in cloud
computing. In Intelligent Computing and
Control Systems (ICICCS), 2017
International Conference on (pp. 23-28).
IEEE. Retrieved At:
https://ieeexplore.ieee.org/abstract/document
/8250721/
[9] Kirubakaramoorthi, R., Arivazhagan, D.
and Helen, D., 2015. Survey on Encryption
Techniques used to Secure Cloud Storage
System. Indian journal of Science and
Technology, 8(36). Retrieved At:
www.indjst.org/index.php/indjst/article/view
File/87861/67097
[10] Korolev, E. A., Petrunin, V. N.,
Smirnov, M. N., & Smirnova, M. A. (2015).
Development of a system of encryption with
the use of stegano-cryptographic techniques.
In The XLVI annual international
conference on Control Processes and
References
[1] Belguith, S., Jemai, A. and Attia, R.,
2015. Enhancing data security in cloud
computing using a lightweight cryptographic
algorithm. In The Eleventh International
Conference On Autonomic and Systems (pp.
98-103). Retrieved At:
https://www.researchgate.net/file.PostFileLo
ader.html?
id=58821cb3b0366d338b4f8b63&assetKey
=AS
%3A452609975820288%401484922035372
[2] Büscher, N. and Katzenbeisser, S., 2017.
Introduction. In Compilation for Secure
Multi-party Computation (pp. 1-4).
Springer, Cham. Retrieved At:
https://www.econstor.eu/bitstream/10419/52
400/1/664103677.pdf
[3] Dachman-Soled, D., Liu, F.H. and Zhou,
H.S., 2015, April. Leakage-resilient circuits
revisited–optimal number of computing
components without leak-free hardware. In
Annual International Conference on the
Theory and Applications of Cryptographic
Techniques (pp. 131-158). Springer, Berlin,
Heidelberg. Retrieved At:
https://www.iacr.org/archive/eurocrypt2015/
90560217/90560217.pdf
[4] Dent, A.W., 2006. Fundamental
problems in provable security and
cryptography. Philosophical Transactions of
the Royal Society of London A:
Mathematical, Physical and Engineering
Sciences, 364(1849), pp.3215-3230.
Retrieved At:
https://pdfs.semanticscholar.org/3c74/272b9
5ca1822bc0d48b398c5a828d7c26b03.pdf
[5] Gautam, S., Mishra, S. and Shrivastava,
M., 2017. A Survey on Generation and
Evolution of Various Cryptographic
Techniques. Retrieved At:
https://irjet.net/archives/V4/i1/IRJET-
V4I1157.pdf
[6] George, J. A., & Hemalatha, M. (2015).
Cryptographic Techniques, Threats and
Privacy Challenges in Cloud Computing.
Governance, 500, 2. Retrieved At:
https://pdfs.semanticscholar.org/b92e/11b2a
f6a22d3475eaacf1ca4e77455387885.pdf
[7] Iyer, K.P., Anusha, R. and Priya, R.S.,
2014. Comparative study on various
cryptographic techniques. In International
Journal of Computer Applications,
International Conference on
Communication, Computing and
Information Technology (ICCCMIT-2014)
(pp. 37-42). Retrieved At:
https://pdfs.semanticscholar.org/69a8/b80ef
1296eb391f125a736771e58c897af8b.pdf
[8] Jain, G. and Sejwar, V., 2017, June.
Improving the security by using various
cryptographic techniques in cloud
computing. In Intelligent Computing and
Control Systems (ICICCS), 2017
International Conference on (pp. 23-28).
IEEE. Retrieved At:
https://ieeexplore.ieee.org/abstract/document
/8250721/
[9] Kirubakaramoorthi, R., Arivazhagan, D.
and Helen, D., 2015. Survey on Encryption
Techniques used to Secure Cloud Storage
System. Indian journal of Science and
Technology, 8(36). Retrieved At:
www.indjst.org/index.php/indjst/article/view
File/87861/67097
[10] Korolev, E. A., Petrunin, V. N.,
Smirnov, M. N., & Smirnova, M. A. (2015).
Development of a system of encryption with
the use of stegano-cryptographic techniques.
In The XLVI annual international
conference on Control Processes and

12
Stability (CPS'15). Retrieved At:
http://www.apmath.spbu.ru/ru/research/conf
erence/pm/archive/2015/abstr-CPS-15.pdf
[11] Mathur, R., Agarwal, S. and Sharma,
V., 2015, May. Solving security issues in
mobile computing using cryptography
techniques—A Survey. In Computing,
Communication & Automation (ICCCA),
2015 International Conference on (pp. 492-
497). IEEE. Retrieved At:
https://ieeexplore.ieee.org/abstract/document
/7148427/
[12] Nabeel, M. and Stork, D.G., Ricoh Co
Ltd, 2015. Efficient, remote, private tree-
based
classification using cryptographic
techniques. U.S. Patent 9,002,007. Retrieved
At:
https://patents.google.com/patent/US900200
7B2/en
[13] Ogiela, L., 2016. Cryptographic
techniques of strategic data splitting and
secure information management. Pervasive
and Mobile Computing, 29, pp.130-141.
Retrieved At:
https://www.sciencedirect.com/science/articl
e/pii/S1574119215000942
[14] Patil, S.P., Solanke, P.B. and Tambe,
D.N., 2017. A Survey Paper on All
Cryptographic Techniques. International
Journal of Engineering Science, 12025.
Retrieved At:
http://ijesc.org/upload/5d5d52c12d4558d00
bf6298abc675ee5.A%20Survey%20Paper
%20on%20All%20Cryptographic
%20Techniques.pdf
[15] Prakash, G.L., Prateek, M. and Singh,
I., 2014, May. Efficient data security method
to control data in cloud storage system using
cryptographic techniques. In Recent
Advances and Innovations in Engineering
(ICRAIE), 2014 (pp. 1-6). IEEE. Retrieved
At:
https://ieeexplore.ieee.org/abstract/document
/6909225/
[16] Preneel, B., 2004, September.
ECRYPT: The cryptographic research
challenges for the next decade. In
International Conference on Security in
Communication Networks (pp. 1-15).
Springer, Berlin, Heidelberg. Retrieved At:
https://lirias.kuleuven.be/bitstream/1234567
89/73439/1/article-542.pdf
[17] Saranya, K., Mohanapriya, R. and
Udhayan, J., 2014. A review on symmetric
key encryption techniques in cryptography.
International Journal of Science,
Engineering and Technology Research
(IJSETR),volume 3 no. 3, pp.539-544.
Retrieved At:
http://ijsetr.org/wp-content/uploads/2014/03/
IJSETR-VOL-3-ISSUE-3-539-544.pdf
[18] Sawlikar, A.P., Khan, Z.J. and
Akojwar, S.G., 2016. Efficient energy
saving cryptographic techniques with
software solution in wireless network.
International Journal of Synthetic Emotions
(IJSE), 7(2), pp.78-96. Retrieved At:
https://www.igi-global.com/article/efficient-
energy-saving-cryptographic-techniques-
with-software-solution-in-wireless-
network/178522
[19] Wilkins, A., Fish, E.N. and Larson,
T.N., T0com Inc, 2016. Obfuscation of
intent in transactions using cryptographic
techniques. U.S. Patent Application
15/164,341. Retrieved At:
https://patentimages.storage.googleapis.com
/e3/e3/a5/e914d0c1a638fc/
US20160350749A1.pdf
Stability (CPS'15). Retrieved At:
http://www.apmath.spbu.ru/ru/research/conf
erence/pm/archive/2015/abstr-CPS-15.pdf
[11] Mathur, R., Agarwal, S. and Sharma,
V., 2015, May. Solving security issues in
mobile computing using cryptography
techniques—A Survey. In Computing,
Communication & Automation (ICCCA),
2015 International Conference on (pp. 492-
497). IEEE. Retrieved At:
https://ieeexplore.ieee.org/abstract/document
/7148427/
[12] Nabeel, M. and Stork, D.G., Ricoh Co
Ltd, 2015. Efficient, remote, private tree-
based
classification using cryptographic
techniques. U.S. Patent 9,002,007. Retrieved
At:
https://patents.google.com/patent/US900200
7B2/en
[13] Ogiela, L., 2016. Cryptographic
techniques of strategic data splitting and
secure information management. Pervasive
and Mobile Computing, 29, pp.130-141.
Retrieved At:
https://www.sciencedirect.com/science/articl
e/pii/S1574119215000942
[14] Patil, S.P., Solanke, P.B. and Tambe,
D.N., 2017. A Survey Paper on All
Cryptographic Techniques. International
Journal of Engineering Science, 12025.
Retrieved At:
http://ijesc.org/upload/5d5d52c12d4558d00
bf6298abc675ee5.A%20Survey%20Paper
%20on%20All%20Cryptographic
%20Techniques.pdf
[15] Prakash, G.L., Prateek, M. and Singh,
I., 2014, May. Efficient data security method
to control data in cloud storage system using
cryptographic techniques. In Recent
Advances and Innovations in Engineering
(ICRAIE), 2014 (pp. 1-6). IEEE. Retrieved
At:
https://ieeexplore.ieee.org/abstract/document
/6909225/
[16] Preneel, B., 2004, September.
ECRYPT: The cryptographic research
challenges for the next decade. In
International Conference on Security in
Communication Networks (pp. 1-15).
Springer, Berlin, Heidelberg. Retrieved At:
https://lirias.kuleuven.be/bitstream/1234567
89/73439/1/article-542.pdf
[17] Saranya, K., Mohanapriya, R. and
Udhayan, J., 2014. A review on symmetric
key encryption techniques in cryptography.
International Journal of Science,
Engineering and Technology Research
(IJSETR),volume 3 no. 3, pp.539-544.
Retrieved At:
http://ijsetr.org/wp-content/uploads/2014/03/
IJSETR-VOL-3-ISSUE-3-539-544.pdf
[18] Sawlikar, A.P., Khan, Z.J. and
Akojwar, S.G., 2016. Efficient energy
saving cryptographic techniques with
software solution in wireless network.
International Journal of Synthetic Emotions
(IJSE), 7(2), pp.78-96. Retrieved At:
https://www.igi-global.com/article/efficient-
energy-saving-cryptographic-techniques-
with-software-solution-in-wireless-
network/178522
[19] Wilkins, A., Fish, E.N. and Larson,
T.N., T0com Inc, 2016. Obfuscation of
intent in transactions using cryptographic
techniques. U.S. Patent Application
15/164,341. Retrieved At:
https://patentimages.storage.googleapis.com
/e3/e3/a5/e914d0c1a638fc/
US20160350749A1.pdf
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


