Cryptography and Security Vulnerabilities of Systems - Report Analysis
VerifiedAdded on 2022/08/27
|12
|794
|21
Report
AI Summary
This report examines cryptography and security vulnerabilities, focusing on a recently announced font-related remote code execution vulnerability affecting Windows operating systems. It details the vulnerable systems, the attack techniques employed, and the proposed mitigation strategies, such as disabling certain features and renaming critical DLL files. The report also discusses the scope of the threat, considering potential attackers and the timeline for patch availability. Furthermore, it analyzes the generation of 1024 and 2048-bit keys using GPG/PGP, including the encryption and decryption processes, while highlighting the importance of key size, entropy, and password protection for enhanced security. The report concludes with a reflection on the adequacy of the mitigation strategies, acknowledging the limitations of the proposed solutions and the ongoing risks posed by the vulnerability.

Running head: CRYPTOGRAPHY AND SECURITY VULNERABILITIES OF SYSTEMS
Cryptography and security vulnerabilities of Systems
Name of the Student
Name of the University
Authors note
Cryptography and security vulnerabilities of Systems
Name of the Student
Name of the University
Authors note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CRYPTOGRAPHY AND SECURITY VULNERABILITIES OF SYSTEMS
Threat
One of the recently announced security vulnerabilities is Font-related Remote Code
Execution Vulnerability in different Windows operating systems
Vulnerable Systems
As there are no patch releases from Microsoft thus most of the Microsoft Operating
systems as well as the Windows Server operating systems are vulnerable due to this flaw against
the attackers.
Attack Techniques
As the vulnerability includes two remote code execution flaws in the atmfd.dll that are
built in for Adobe Type Manager font management tool in the operating systems. This atmfd.dll
library is utilized in order to render different fonts depending upon the Adobe Type 1
PostScript.
Remote code execution is the one of the worst kind of attacks from the user’s perspective
as the attackers injects some specific code segment into some File or program that gets executed
by the parser/compiler and in that way the targeted computer or server gets completely
compromised. Through this compromise the attacker can gain complete control over the
vulnerable computer network or server.
Mitigation Strategies
Mitigations strategies for this threat includes, disabling Details and Preview panes while
using the windows explorer program, disable Web Client services in order to protect the
computers and servers. By disabling the WebClient services the Distributed Authoring as well
Threat
One of the recently announced security vulnerabilities is Font-related Remote Code
Execution Vulnerability in different Windows operating systems
Vulnerable Systems
As there are no patch releases from Microsoft thus most of the Microsoft Operating
systems as well as the Windows Server operating systems are vulnerable due to this flaw against
the attackers.
Attack Techniques
As the vulnerability includes two remote code execution flaws in the atmfd.dll that are
built in for Adobe Type Manager font management tool in the operating systems. This atmfd.dll
library is utilized in order to render different fonts depending upon the Adobe Type 1
PostScript.
Remote code execution is the one of the worst kind of attacks from the user’s perspective
as the attackers injects some specific code segment into some File or program that gets executed
by the parser/compiler and in that way the targeted computer or server gets completely
compromised. Through this compromise the attacker can gain complete control over the
vulnerable computer network or server.
Mitigation Strategies
Mitigations strategies for this threat includes, disabling Details and Preview panes while
using the windows explorer program, disable Web Client services in order to protect the
computers and servers. By disabling the WebClient services the Distributed Authoring as well

2CRYPTOGRAPHY AND SECURITY VULNERABILITIES OF SYSTEMS
as Versioning requests would not be transmitted by the computers running the windows OS. In
addition to that, different services that dependent on WebClient services would not start. In this
way the WebDAV shares inside a network would not be accessible from different vulnerable
computers. Another way is renaming ATMFD.DLL library.
Scope of the Threat
As from the official announcement about this vulnerability, there was no mention about
the any immediate patches for this vulnerability and it is intimidated that the patch for this
vulnerability may arrive on the next month's Patch Tuesday which is scheduled on April 14. In
that mean time the hackers or attackers can target the individual work stations or organization
servers that are running the windows Server systems with this flaw will be vulnerable to attacks.
Concluding reflection on adequacy of Mitigation strategy
Even though the disabling Preview, Details pane in Windows Explorer can help in
stopping display of different OTF fonts in Explorer function. Even though this technique stops
the malicious files to be viewed in Explorer but this this technique cannot stop any local,
suspicious authenticated users from executing some crafted program or code segment that can
exploit the identified vulnerability.
Much after with these securities are measure set up, it is still feasible for remote attackers
to execute programs situated on the focused target or neighborhood network. In any case, the
workaround will make clients alert and ask for affirmation before opening subjective
applications available from the Internet.
as Versioning requests would not be transmitted by the computers running the windows OS. In
addition to that, different services that dependent on WebClient services would not start. In this
way the WebDAV shares inside a network would not be accessible from different vulnerable
computers. Another way is renaming ATMFD.DLL library.
Scope of the Threat
As from the official announcement about this vulnerability, there was no mention about
the any immediate patches for this vulnerability and it is intimidated that the patch for this
vulnerability may arrive on the next month's Patch Tuesday which is scheduled on April 14. In
that mean time the hackers or attackers can target the individual work stations or organization
servers that are running the windows Server systems with this flaw will be vulnerable to attacks.
Concluding reflection on adequacy of Mitigation strategy
Even though the disabling Preview, Details pane in Windows Explorer can help in
stopping display of different OTF fonts in Explorer function. Even though this technique stops
the malicious files to be viewed in Explorer but this this technique cannot stop any local,
suspicious authenticated users from executing some crafted program or code segment that can
exploit the identified vulnerability.
Much after with these securities are measure set up, it is still feasible for remote attackers
to execute programs situated on the focused target or neighborhood network. In any case, the
workaround will make clients alert and ask for affirmation before opening subjective
applications available from the Internet.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3CRYPTOGRAPHY AND SECURITY VULNERABILITIES OF SYSTEMS
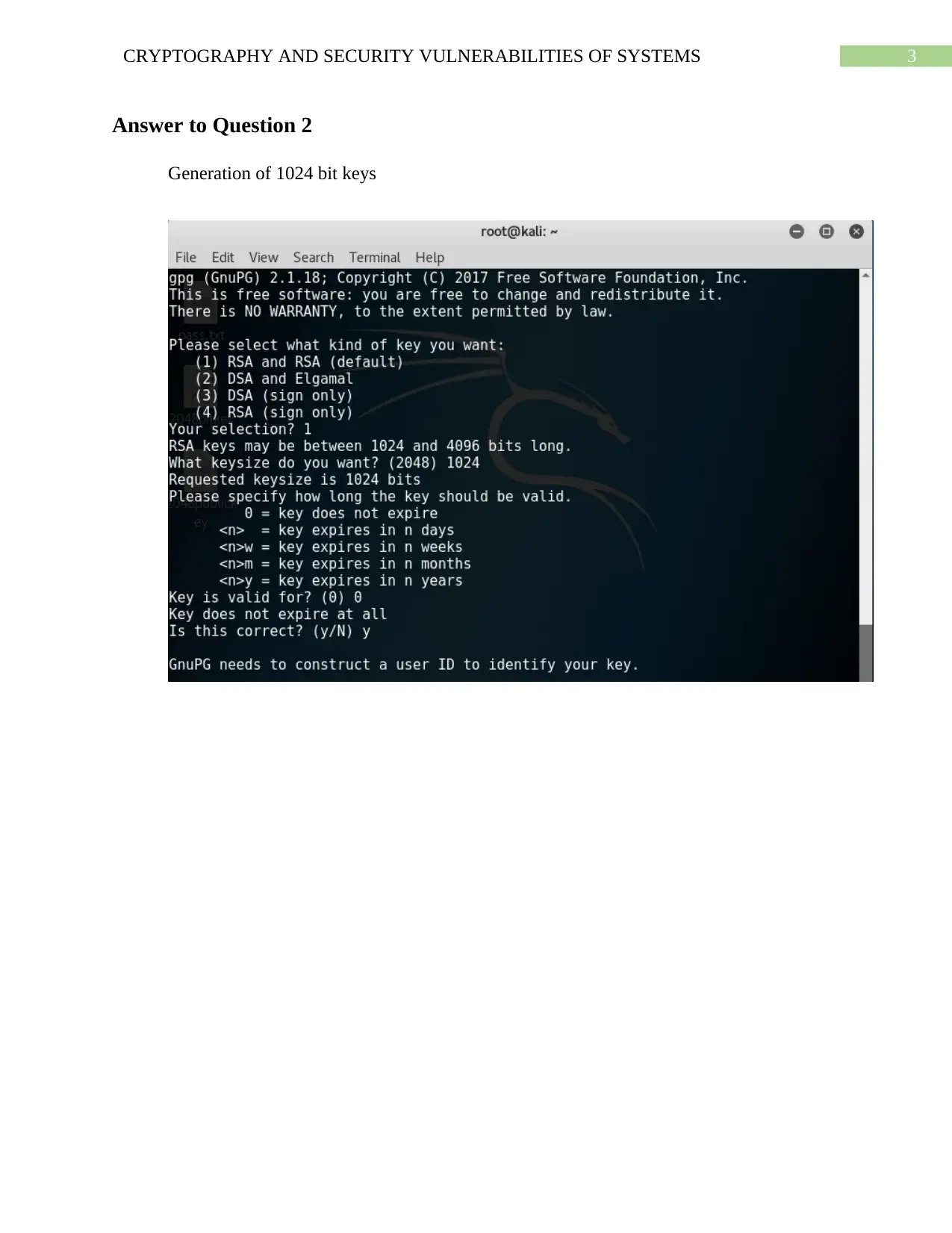
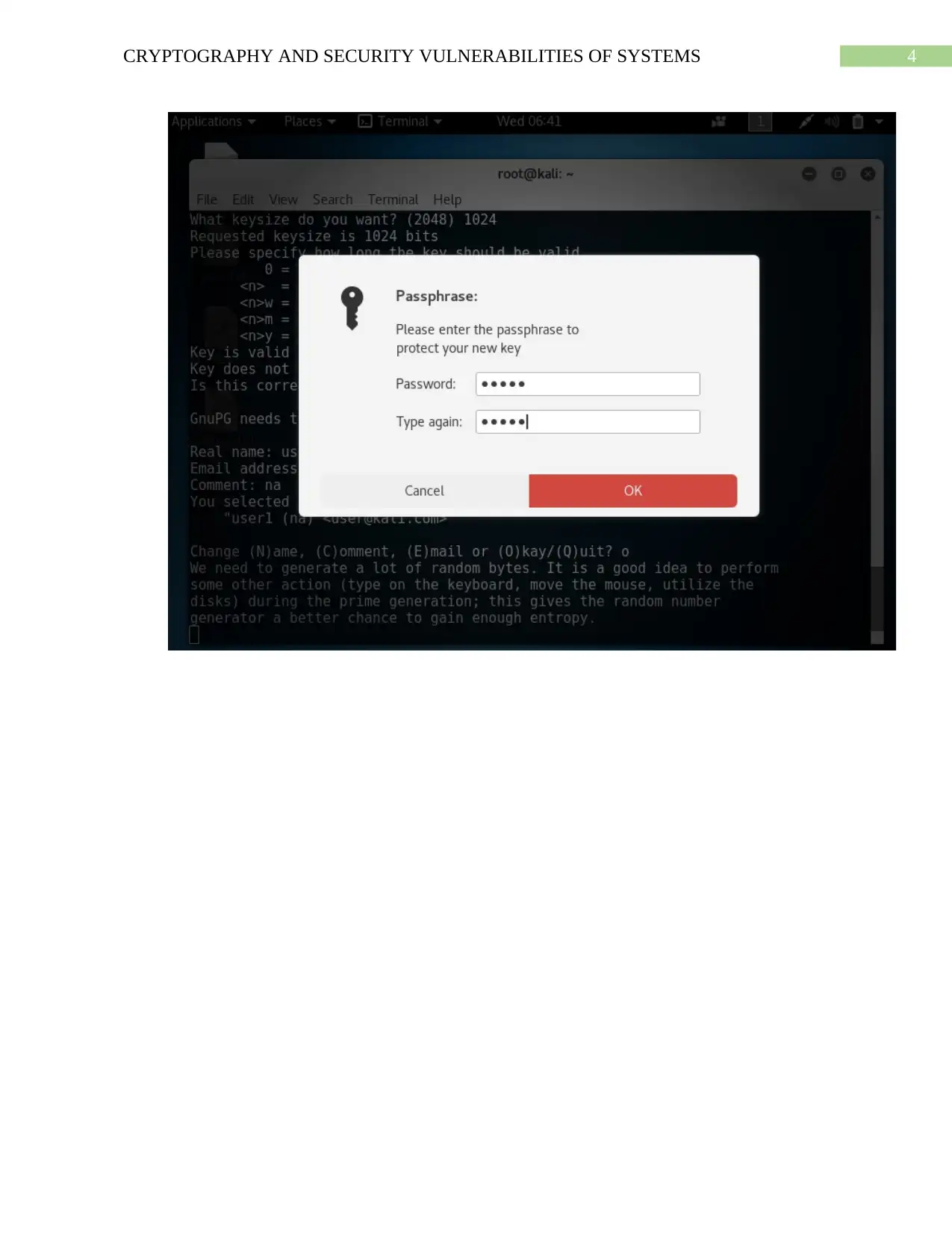
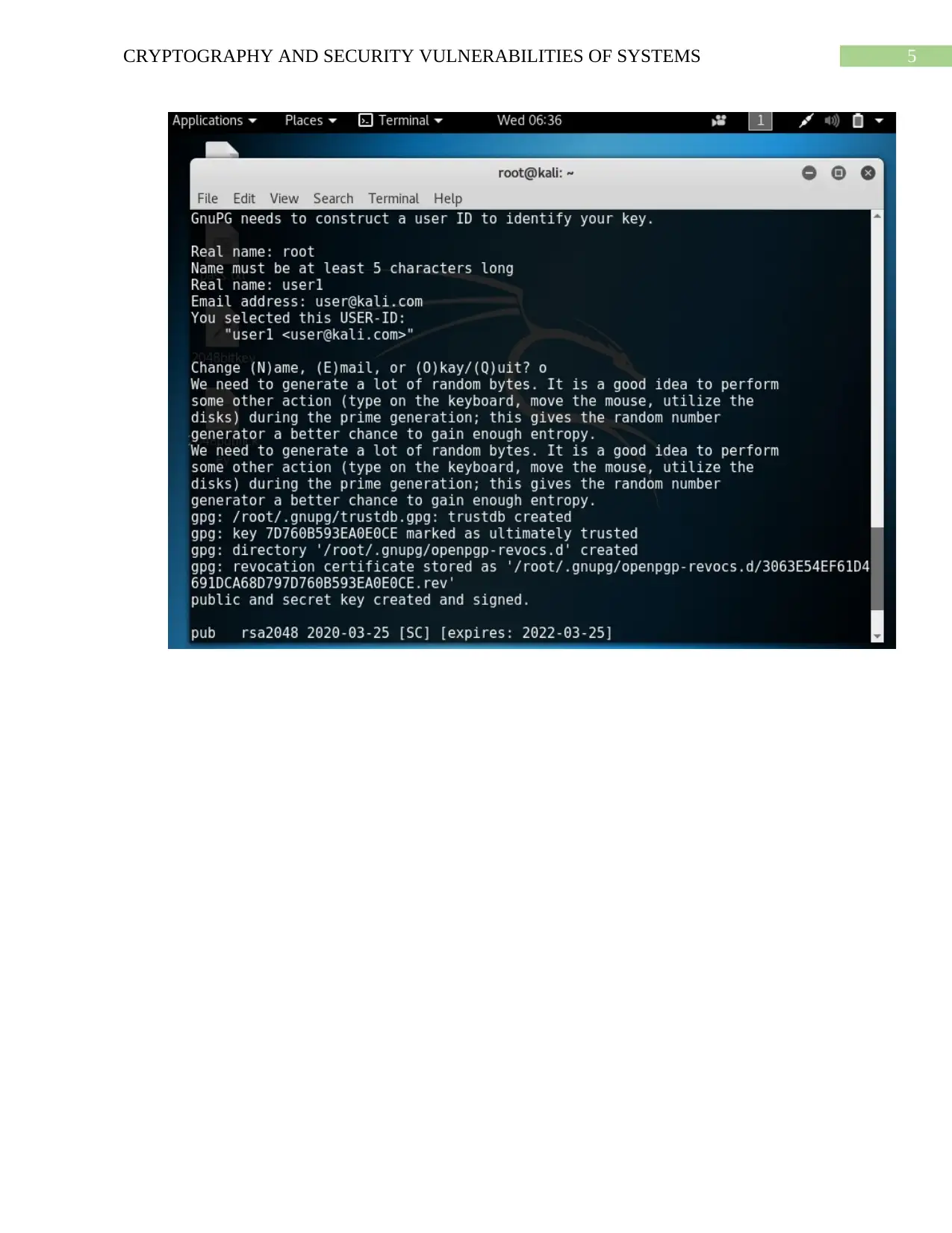
Answer to Question 2
Generation of 1024 bit keys
Answer to Question 2
Generation of 1024 bit keys
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4CRYPTOGRAPHY AND SECURITY VULNERABILITIES OF SYSTEMS
5CRYPTOGRAPHY AND SECURITY VULNERABILITIES OF SYSTEMS
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6CRYPTOGRAPHY AND SECURITY VULNERABILITIES OF SYSTEMS
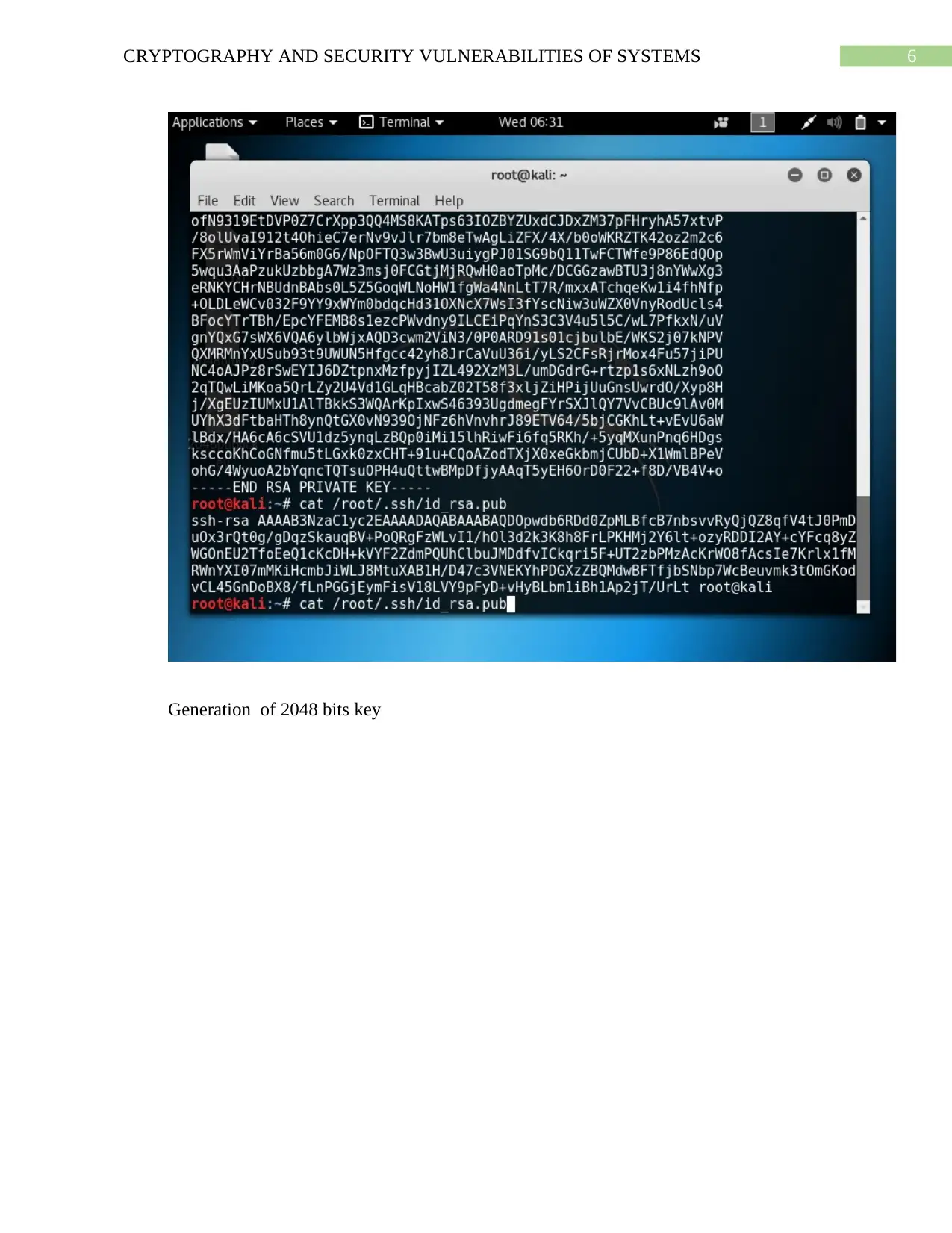
Generation of 2048 bits key
Generation of 2048 bits key
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7CRYPTOGRAPHY AND SECURITY VULNERABILITIES OF SYSTEMS
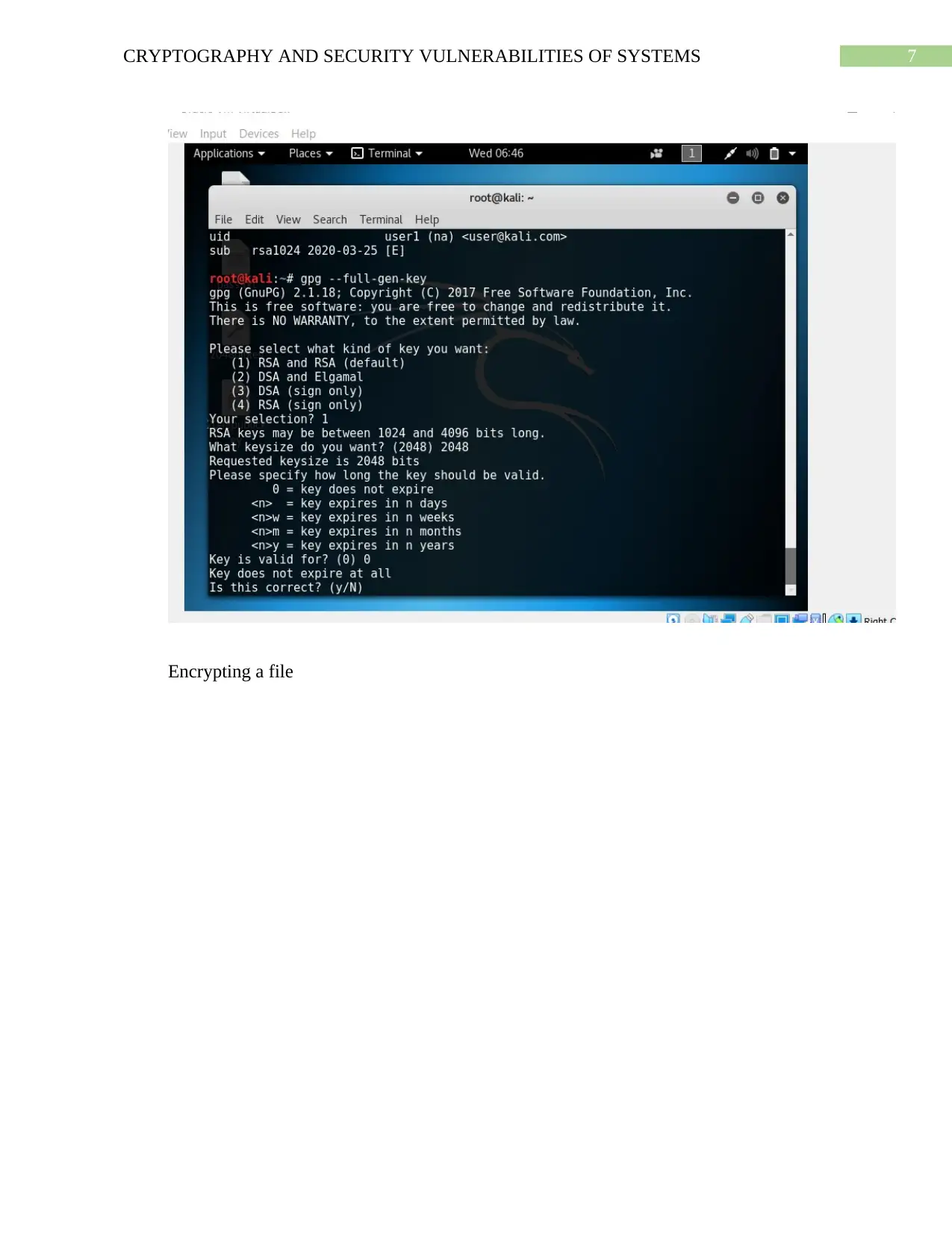
Encrypting a file
Encrypting a file
8CRYPTOGRAPHY AND SECURITY VULNERABILITIES OF SYSTEMS
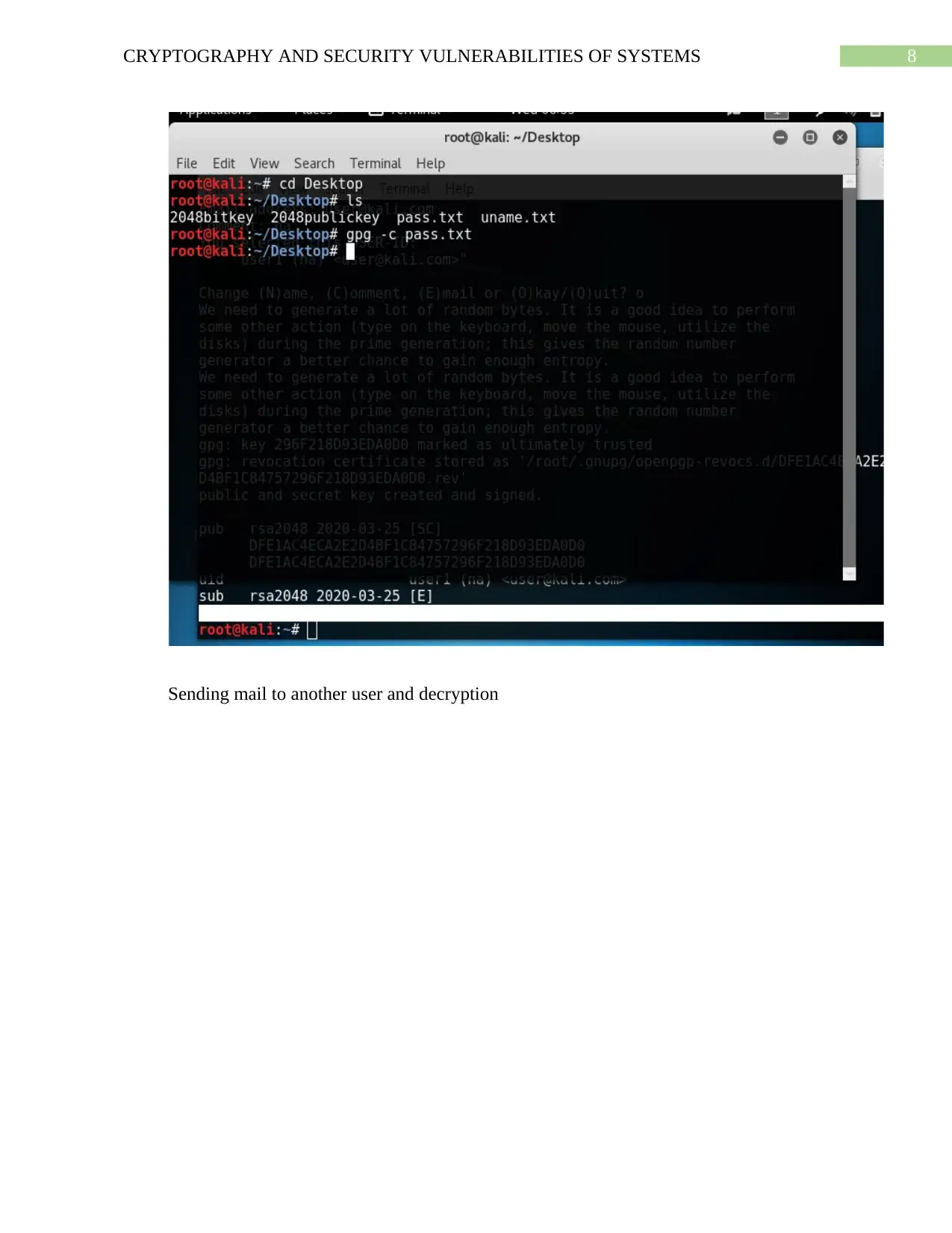
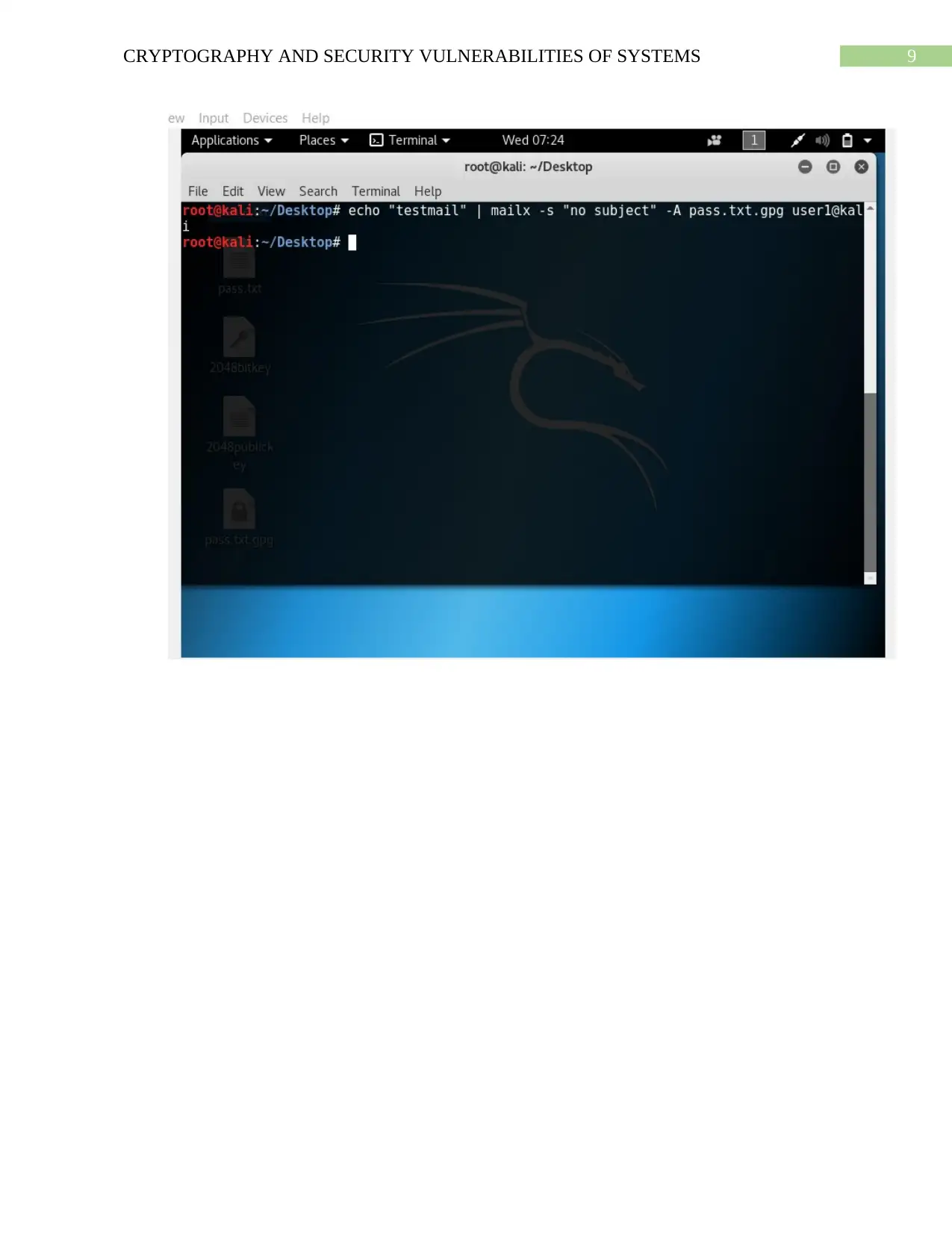
Sending mail to another user and decryption
Sending mail to another user and decryption
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9CRYPTOGRAPHY AND SECURITY VULNERABILITIES OF SYSTEMS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10CRYPTOGRAPHY AND SECURITY VULNERABILITIES OF SYSTEMS
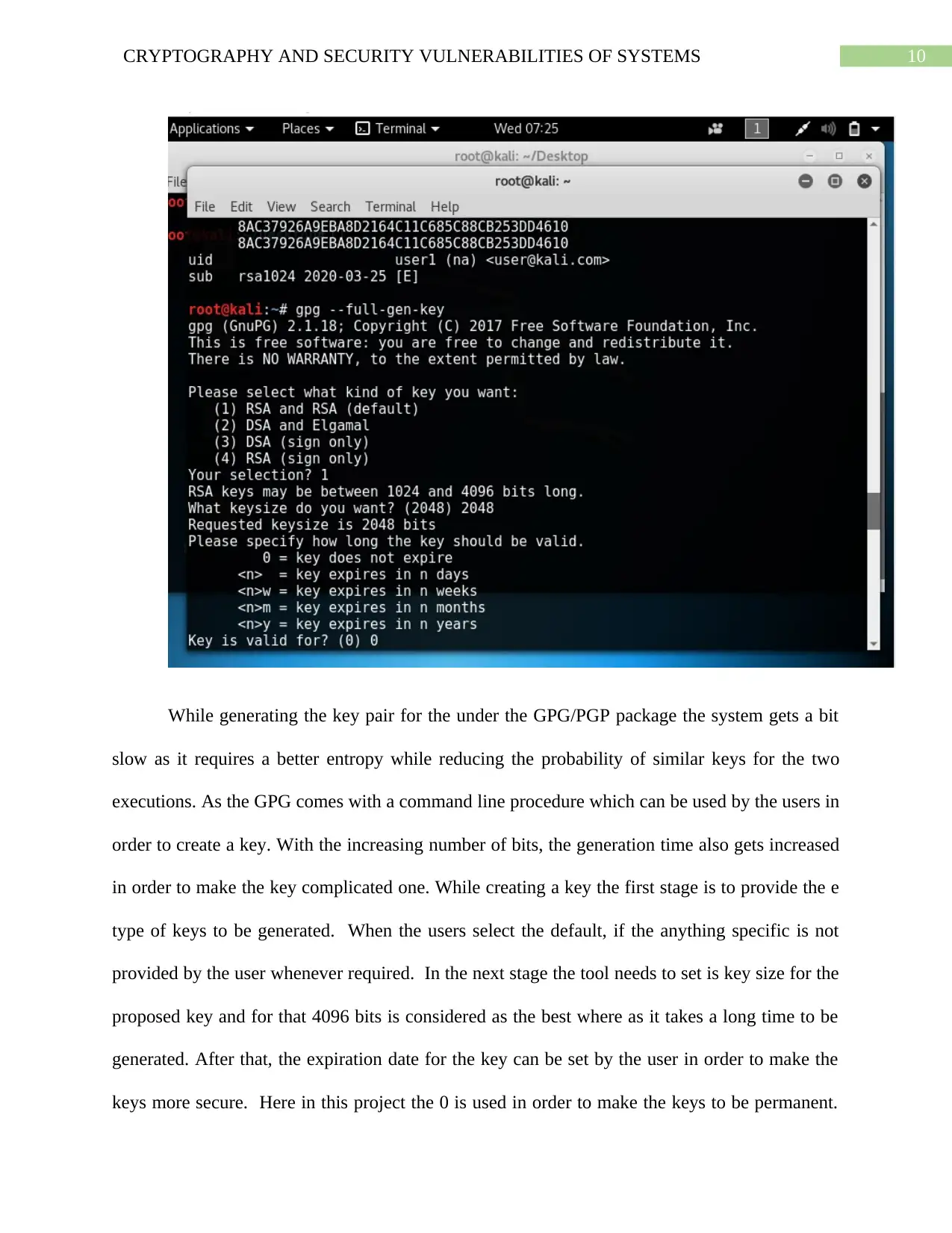
While generating the key pair for the under the GPG/PGP package the system gets a bit
slow as it requires a better entropy while reducing the probability of similar keys for the two
executions. As the GPG comes with a command line procedure which can be used by the users in
order to create a key. With the increasing number of bits, the generation time also gets increased
in order to make the key complicated one. While creating a key the first stage is to provide the e
type of keys to be generated. When the users select the default, if the anything specific is not
provided by the user whenever required. In the next stage the tool needs to set is key size for the
proposed key and for that 4096 bits is considered as the best where as it takes a long time to be
generated. After that, the expiration date for the key can be set by the user in order to make the
keys more secure. Here in this project the 0 is used in order to make the keys to be permanent.
While generating the key pair for the under the GPG/PGP package the system gets a bit
slow as it requires a better entropy while reducing the probability of similar keys for the two
executions. As the GPG comes with a command line procedure which can be used by the users in
order to create a key. With the increasing number of bits, the generation time also gets increased
in order to make the key complicated one. While creating a key the first stage is to provide the e
type of keys to be generated. When the users select the default, if the anything specific is not
provided by the user whenever required. In the next stage the tool needs to set is key size for the
proposed key and for that 4096 bits is considered as the best where as it takes a long time to be
generated. After that, the expiration date for the key can be set by the user in order to make the
keys more secure. Here in this project the 0 is used in order to make the keys to be permanent.

11CRYPTOGRAPHY AND SECURITY VULNERABILITIES OF SYSTEMS
While generating the keys, the users can also add password for keys. Even though it is
considered as optional, but it can improve the security. In the process of generation of the keys
GPG package collects entropy from users’ actions in order to increase the strength the generated
key.
While generating the keys, the users can also add password for keys. Even though it is
considered as optional, but it can improve the security. In the process of generation of the keys
GPG package collects entropy from users’ actions in order to increase the strength the generated
key.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





