CSC81001 Computer Networks Assignment 1: Protocol Analysis
VerifiedAdded on 2022/09/23
|13
|1941
|20
Homework Assignment
AI Summary
This assignment, CSC81001, focuses on computer networks and encompasses three key tasks. Task 1 requires a comparison of IPv4 and IPv6 protocols, examining their structure, addressing schemes, advantages, disadvantages, performance, and deployment trends over the past five years, with a word limit between 500-1000 words and using IEEE referencing. Task 2 involves analyzing network traffic captured in a .pcap file using Wireshark, identifying protocols, classifying them based on the TCP/IP and OSI models, and determining accessed websites, MAC and IP addresses of accessing computers, and the meaning of specific frame type values. Finally, Task 3 requires an analysis of network architecture, specifically listing APs with their locations, SSIDs, and channels, and requires the use of specific software to generate a heatmap of the Gold Coast campus Wi-Fi access points. The assignment aims to assess students' understanding of network protocols, traffic analysis, and network architecture, contributing 15% to the overall unit assessment.

MIT
Authors Name/s per 1st Affiliation (Author)
Dept. name of the organization
Name of organization, acronyms acceptable
City, Country
mail address
Authors Name/s per 1st Affiliation (Author)
Dept. name of the organization
Name of organization, acronyms acceptable
City, Country
mail address
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CSC81001 – Computer Networks Assignment-1, 2019
Table of Contents
Task-1: Protocol comparison............................................................................................................................5
The protocol structure..................................................................................................................................5
The addressing scheme................................................................................................................................6
Advantages and disadvantages....................................................................................................................6
Performance.............................................................................................................................................7
Deployment figure in the last 5 years.......................................................................................................7
Task-2: Protocol Analysis..................................................................................................................................9
Task 3: Network Architecture Analysis...........................................................................................................14
2
Table of Contents
Task-1: Protocol comparison............................................................................................................................5
The protocol structure..................................................................................................................................5
The addressing scheme................................................................................................................................6
Advantages and disadvantages....................................................................................................................6
Performance.............................................................................................................................................7
Deployment figure in the last 5 years.......................................................................................................7
Task-2: Protocol Analysis..................................................................................................................................9
Task 3: Network Architecture Analysis...........................................................................................................14
2

CSC81001 – Computer Networks Assignment-1, 2019
Task-1: Protocol comparison
The IP (Internet Protocol) is a set of rules used by computing devices send data from
one device to another over a packet-switched network. The main services provided by
the protocol in the packet-switched network is addressing and fragmentation. The
protocol generally has two parts, that is the Network part and the Local or the Host
part. IP protocol exists in two versions, the IPv4 and the IPv6. IPv4 is a 32-bit number
normally written in a dotted decimal notation whereas the IPv6 is a 128-bit number
normally written in Hexadecimal notation [1]. The details of the IP structure and
detailed comparison of the two versions are discussed below
The protocol structure
The following diagram shows the structural difference between and IPv4 and IPv6
Figure 1 IPv4 Vs IPv6 Structure
The IPv4 header represents a packet with some additional information which gets
transmitted from the source computing device to the destination computing devices
and uses the IPv4 version. The IPv6 header contains additional information that gets
transmitted from the source computing device to the destination using the IPv6.
It terms of simplicity, the structure of IPv4 is quite complex relative to the IPv6 as the
former has very many fields added to the header information. Such fields as the
header length, flags, identification are included in the header information. Whereas
the IPv6 has eliminated fields such as flags, identification, and length.
The IPv4 structure contains a special field for options whereas the IPv6 contains a field
named next header which is primarily used for extensions.
The IPv4 header structure has the TTL(Time To Live) which is used to show the number
of hops the packet has undergone. In sharp contrast, the IPv6 structure has a field
called the hop limit which is used to show the number of hops the packet has
undergone [2].
The IPv4 source address and the destination address is a 32-bit lengthwise while the
source and destination IPv6 address has a 128-bits lengthwise
3
Task-1: Protocol comparison
The IP (Internet Protocol) is a set of rules used by computing devices send data from
one device to another over a packet-switched network. The main services provided by
the protocol in the packet-switched network is addressing and fragmentation. The
protocol generally has two parts, that is the Network part and the Local or the Host
part. IP protocol exists in two versions, the IPv4 and the IPv6. IPv4 is a 32-bit number
normally written in a dotted decimal notation whereas the IPv6 is a 128-bit number
normally written in Hexadecimal notation [1]. The details of the IP structure and
detailed comparison of the two versions are discussed below
The protocol structure
The following diagram shows the structural difference between and IPv4 and IPv6
Figure 1 IPv4 Vs IPv6 Structure
The IPv4 header represents a packet with some additional information which gets
transmitted from the source computing device to the destination computing devices
and uses the IPv4 version. The IPv6 header contains additional information that gets
transmitted from the source computing device to the destination using the IPv6.
It terms of simplicity, the structure of IPv4 is quite complex relative to the IPv6 as the
former has very many fields added to the header information. Such fields as the
header length, flags, identification are included in the header information. Whereas
the IPv6 has eliminated fields such as flags, identification, and length.
The IPv4 structure contains a special field for options whereas the IPv6 contains a field
named next header which is primarily used for extensions.
The IPv4 header structure has the TTL(Time To Live) which is used to show the number
of hops the packet has undergone. In sharp contrast, the IPv6 structure has a field
called the hop limit which is used to show the number of hops the packet has
undergone [2].
The IPv4 source address and the destination address is a 32-bit lengthwise while the
source and destination IPv6 address has a 128-bits lengthwise
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CSC81001 – Computer Networks Assignment-1, 2019
The checksum field is available in the IPv4 structure for error control purposes while
IPv6 has no checksum field
IPv4 allows for broadcast messages while the IPv6 structure doesn’t allow broadcast
messages and in place, a link-local address is used to offer the functionality of
broadcast
The addressing scheme
The IPv4 addressing scheme is normally broken down into four classes namely class A,
class B, class C and Class D. The different classes are used to denote how many hosts
that the scheme can be directly connected to the network. The chart below shows a
summary of the classes [3].
Figure 2 IPv4 Address Classes
The literal numerical values of the number of hosts in each class are as shown below
Figure 3 IPv4 Address
This system presents numerous challenges including address run out especially the
class B used by many companies. This prompted the design of the IPv6 addressing
scheme which is simply aimed at lengthening the various field that has addresses. The
IPv6 has 128 bits length making it convenient for a larger number of addresses [4].
The addressing scheme is broken into the network and host address
Figure 4 IPv6 addresses
This provides more robust benefits as discussed below
4
The checksum field is available in the IPv4 structure for error control purposes while
IPv6 has no checksum field
IPv4 allows for broadcast messages while the IPv6 structure doesn’t allow broadcast
messages and in place, a link-local address is used to offer the functionality of
broadcast
The addressing scheme
The IPv4 addressing scheme is normally broken down into four classes namely class A,
class B, class C and Class D. The different classes are used to denote how many hosts
that the scheme can be directly connected to the network. The chart below shows a
summary of the classes [3].
Figure 2 IPv4 Address Classes
The literal numerical values of the number of hosts in each class are as shown below
Figure 3 IPv4 Address
This system presents numerous challenges including address run out especially the
class B used by many companies. This prompted the design of the IPv6 addressing
scheme which is simply aimed at lengthening the various field that has addresses. The
IPv6 has 128 bits length making it convenient for a larger number of addresses [4].
The addressing scheme is broken into the network and host address
Figure 4 IPv6 addresses
This provides more robust benefits as discussed below
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CSC81001 – Computer Networks Assignment-1, 2019
Advantages and disadvantages
Advantages of IPv4
i. Trusted when it comes to security due to encryption
ii. Relatively flexible and more efficient in terms of routing due to
multiple ports routing
iii. Able to handle multicast communication
Disadvantages of IPv4
i. Restricted address space hence shortages of public IP addresses
ii. Relatively difficult to configure and require expertise knowledge
iii. Compatibility issues since most devices are going towards the
IPv6
Advantages of IPv6
i. The IPv6 has reduced the burden of the router by reducing
header fields
ii. More address space
iii. Relatively simple to set up and maintain
iv. IPv6 can maximize the number of data bytes being transmitted
v. More dominant in the marked as 95% of devices currently utilize
IPv6
vi. Built-in security features that ensure confidentiality integrity and
authentification by use of IPSec
D
Performance
In terms of performance, the two protocols differ very much. The IPv6 eliminated
several headers in the structure reducing the router overheads costs in processing
hence making the protocol more efficient in terms of performance compared to the
Ipv4 with a lot of header information which the router must process before making the
decision to forward. The Ipv6 round trip is greatly reduced by the SYN handshake
mechanism making it more reliable for performance [5]
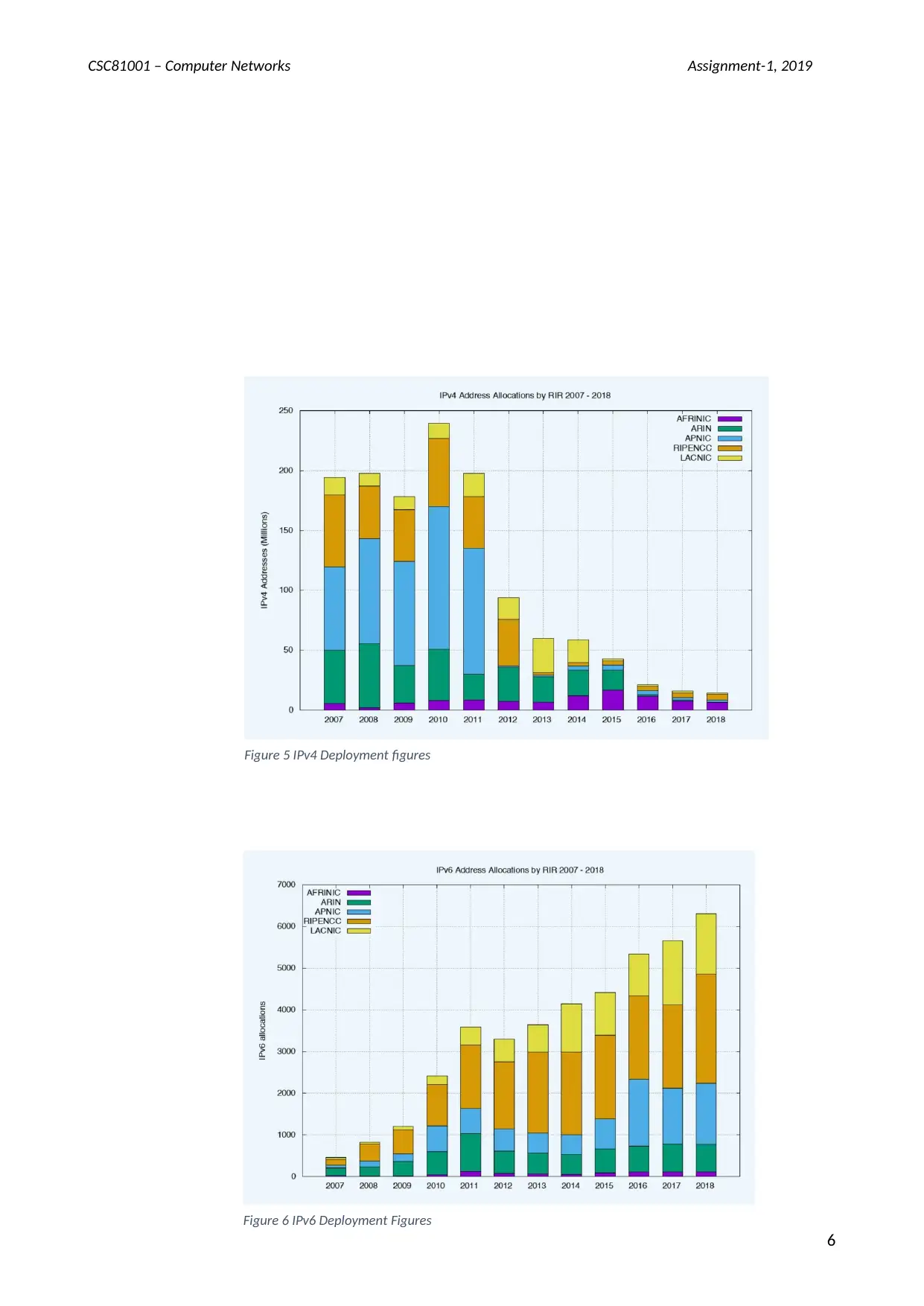
Deployment figure in the last 5 years
Generally, the trend has seen a decrease in the deployment of IPv4 addresses in the
last five years compared to its counterpart, IPv6 which has seen a tremendous
increase in the number of deployments in the last five years. The figure below shows
the different deployment figures for each
5
Advantages and disadvantages
Advantages of IPv4
i. Trusted when it comes to security due to encryption
ii. Relatively flexible and more efficient in terms of routing due to
multiple ports routing
iii. Able to handle multicast communication
Disadvantages of IPv4
i. Restricted address space hence shortages of public IP addresses
ii. Relatively difficult to configure and require expertise knowledge
iii. Compatibility issues since most devices are going towards the
IPv6
Advantages of IPv6
i. The IPv6 has reduced the burden of the router by reducing
header fields
ii. More address space
iii. Relatively simple to set up and maintain
iv. IPv6 can maximize the number of data bytes being transmitted
v. More dominant in the marked as 95% of devices currently utilize
IPv6
vi. Built-in security features that ensure confidentiality integrity and
authentification by use of IPSec
D
Performance
In terms of performance, the two protocols differ very much. The IPv6 eliminated
several headers in the structure reducing the router overheads costs in processing
hence making the protocol more efficient in terms of performance compared to the
Ipv4 with a lot of header information which the router must process before making the
decision to forward. The Ipv6 round trip is greatly reduced by the SYN handshake
mechanism making it more reliable for performance [5]
Deployment figure in the last 5 years
Generally, the trend has seen a decrease in the deployment of IPv4 addresses in the
last five years compared to its counterpart, IPv6 which has seen a tremendous
increase in the number of deployments in the last five years. The figure below shows
the different deployment figures for each
5
CSC81001 – Computer Networks Assignment-1, 2019
6
Figure 5 IPv4 Deployment figures
Figure 6 IPv6 Deployment Figures
6
Figure 5 IPv4 Deployment figures
Figure 6 IPv6 Deployment Figures
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
CSC81001 – Computer Networks Assignment-1, 2019
Aggregates for Last four years
IPV4 = 100 MILLION DEPLOYMENTS
IPV6=25.2 BILLION DEPLOYMENTS
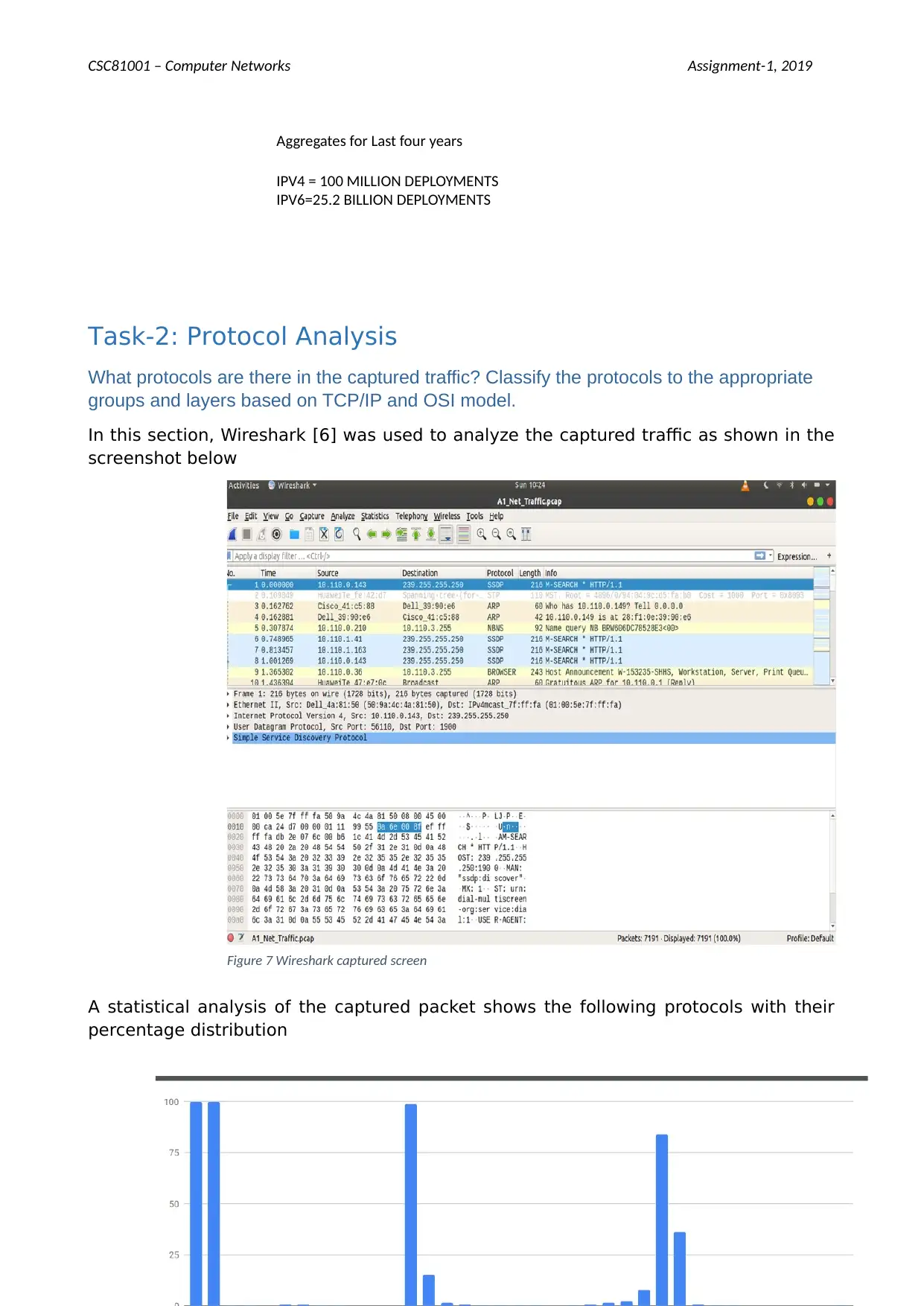
Task-2: Protocol Analysis
What protocols are there in the captured traffic? Classify the protocols to the appropriate
groups and layers based on TCP/IP and OSI model.
In this section, Wireshark [6] was used to analyze the captured traffic as shown in the
screenshot below
A statistical analysis of the captured packet shows the following protocols with their
percentage distribution
7
Figure 7 Wireshark captured screen
Aggregates for Last four years
IPV4 = 100 MILLION DEPLOYMENTS
IPV6=25.2 BILLION DEPLOYMENTS
Task-2: Protocol Analysis
What protocols are there in the captured traffic? Classify the protocols to the appropriate
groups and layers based on TCP/IP and OSI model.
In this section, Wireshark [6] was used to analyze the captured traffic as shown in the
screenshot below
A statistical analysis of the captured packet shows the following protocols with their
percentage distribution
7
Figure 7 Wireshark captured screen
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CSC81001 – Computer Networks Assignment-1, 2019
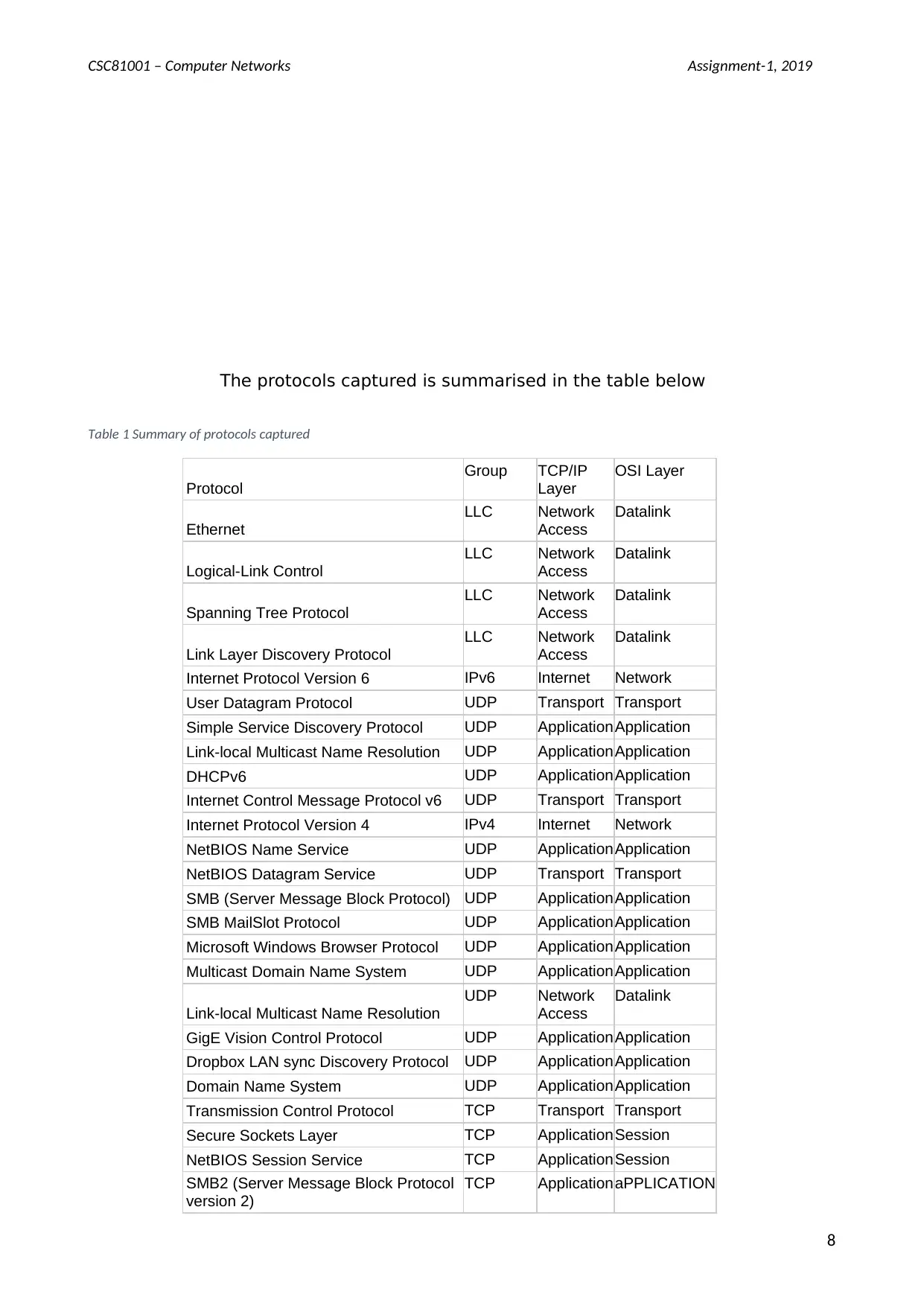
The protocols captured is summarised in the table below
Table 1 Summary of protocols captured
Protocol
Group TCP/IP
Layer
OSI Layer
Ethernet
LLC Network
Access
Datalink
Logical-Link Control
LLC Network
Access
Datalink
Spanning Tree Protocol
LLC Network
Access
Datalink
Link Layer Discovery Protocol
LLC Network
Access
Datalink
Internet Protocol Version 6 IPv6 Internet Network
User Datagram Protocol UDP Transport Transport
Simple Service Discovery Protocol UDP ApplicationApplication
Link-local Multicast Name Resolution UDP ApplicationApplication
DHCPv6 UDP ApplicationApplication
Internet Control Message Protocol v6 UDP Transport Transport
Internet Protocol Version 4 IPv4 Internet Network
NetBIOS Name Service UDP ApplicationApplication
NetBIOS Datagram Service UDP Transport Transport
SMB (Server Message Block Protocol) UDP ApplicationApplication
SMB MailSlot Protocol UDP ApplicationApplication
Microsoft Windows Browser Protocol UDP ApplicationApplication
Multicast Domain Name System UDP ApplicationApplication
Link-local Multicast Name Resolution
UDP Network
Access
Datalink
GigE Vision Control Protocol UDP ApplicationApplication
Dropbox LAN sync Discovery Protocol UDP ApplicationApplication
Domain Name System UDP ApplicationApplication
Transmission Control Protocol TCP Transport Transport
Secure Sockets Layer TCP ApplicationSession
NetBIOS Session Service TCP ApplicationSession
SMB2 (Server Message Block Protocol
version 2)
TCP ApplicationaPPLICATION
8
The protocols captured is summarised in the table below
Table 1 Summary of protocols captured
Protocol
Group TCP/IP
Layer
OSI Layer
Ethernet
LLC Network
Access
Datalink
Logical-Link Control
LLC Network
Access
Datalink
Spanning Tree Protocol
LLC Network
Access
Datalink
Link Layer Discovery Protocol
LLC Network
Access
Datalink
Internet Protocol Version 6 IPv6 Internet Network
User Datagram Protocol UDP Transport Transport
Simple Service Discovery Protocol UDP ApplicationApplication
Link-local Multicast Name Resolution UDP ApplicationApplication
DHCPv6 UDP ApplicationApplication
Internet Control Message Protocol v6 UDP Transport Transport
Internet Protocol Version 4 IPv4 Internet Network
NetBIOS Name Service UDP ApplicationApplication
NetBIOS Datagram Service UDP Transport Transport
SMB (Server Message Block Protocol) UDP ApplicationApplication
SMB MailSlot Protocol UDP ApplicationApplication
Microsoft Windows Browser Protocol UDP ApplicationApplication
Multicast Domain Name System UDP ApplicationApplication
Link-local Multicast Name Resolution
UDP Network
Access
Datalink
GigE Vision Control Protocol UDP ApplicationApplication
Dropbox LAN sync Discovery Protocol UDP ApplicationApplication
Domain Name System UDP ApplicationApplication
Transmission Control Protocol TCP Transport Transport
Secure Sockets Layer TCP ApplicationSession
NetBIOS Session Service TCP ApplicationSession
SMB2 (Server Message Block Protocol
version 2)
TCP ApplicationaPPLICATION
8
CSC81001 – Computer Networks Assignment-1, 2019
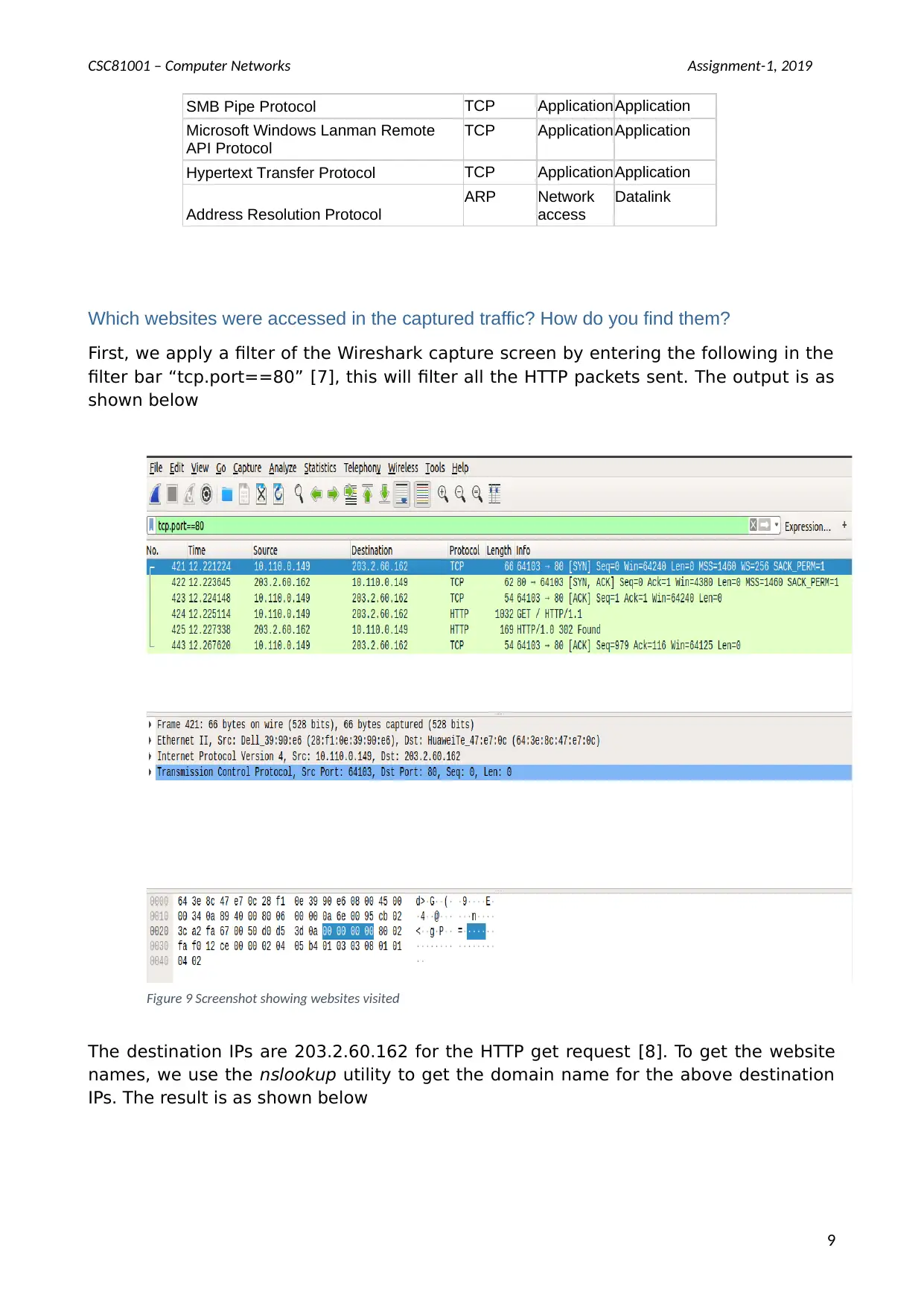
SMB Pipe Protocol TCP ApplicationApplication
Microsoft Windows Lanman Remote
API Protocol
TCP ApplicationApplication
Hypertext Transfer Protocol TCP ApplicationApplication
Address Resolution Protocol
ARP Network
access
Datalink
Which websites were accessed in the captured traffic? How do you find them?
First, we apply a filter of the Wireshark capture screen by entering the following in the
filter bar “tcp.port==80” [7], this will filter all the HTTP packets sent. The output is as
shown below
The destination IPs are 203.2.60.162 for the HTTP get request [8]. To get the website
names, we use the nslookup utility to get the domain name for the above destination
IPs. The result is as shown below
9
Figure 9 Screenshot showing websites visited
SMB Pipe Protocol TCP ApplicationApplication
Microsoft Windows Lanman Remote
API Protocol
TCP ApplicationApplication
Hypertext Transfer Protocol TCP ApplicationApplication
Address Resolution Protocol
ARP Network
access
Datalink
Which websites were accessed in the captured traffic? How do you find them?
First, we apply a filter of the Wireshark capture screen by entering the following in the
filter bar “tcp.port==80” [7], this will filter all the HTTP packets sent. The output is as
shown below
The destination IPs are 203.2.60.162 for the HTTP get request [8]. To get the website
names, we use the nslookup utility to get the domain name for the above destination
IPs. The result is as shown below
9
Figure 9 Screenshot showing websites visited
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
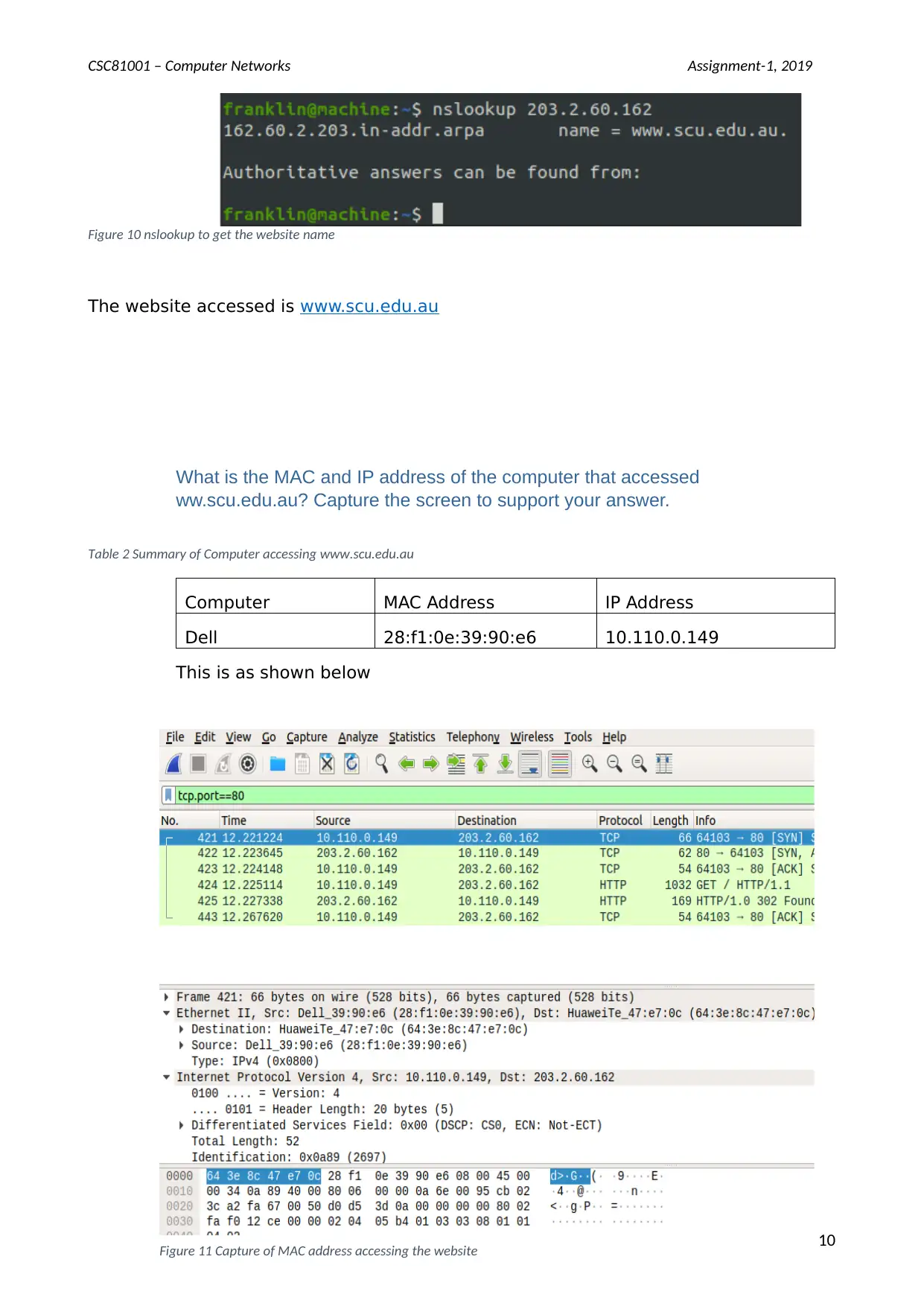
CSC81001 – Computer Networks Assignment-1, 2019
Figure 10 nslookup to get the website name
The website accessed is www.scu.edu.au
What is the MAC and IP address of the computer that accessed
ww.scu.edu.au? Capture the screen to support your answer.
Table 2 Summary of Computer accessing www.scu.edu.au
Computer MAC Address IP Address
Dell 28:f1:0e:39:90:e6 10.110.0.149
This is as shown below
10
Figure 11 Capture of MAC address accessing the website
Figure 10 nslookup to get the website name
The website accessed is www.scu.edu.au
What is the MAC and IP address of the computer that accessed
ww.scu.edu.au? Capture the screen to support your answer.
Table 2 Summary of Computer accessing www.scu.edu.au
Computer MAC Address IP Address
Dell 28:f1:0e:39:90:e6 10.110.0.149
This is as shown below
10
Figure 11 Capture of MAC address accessing the website
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
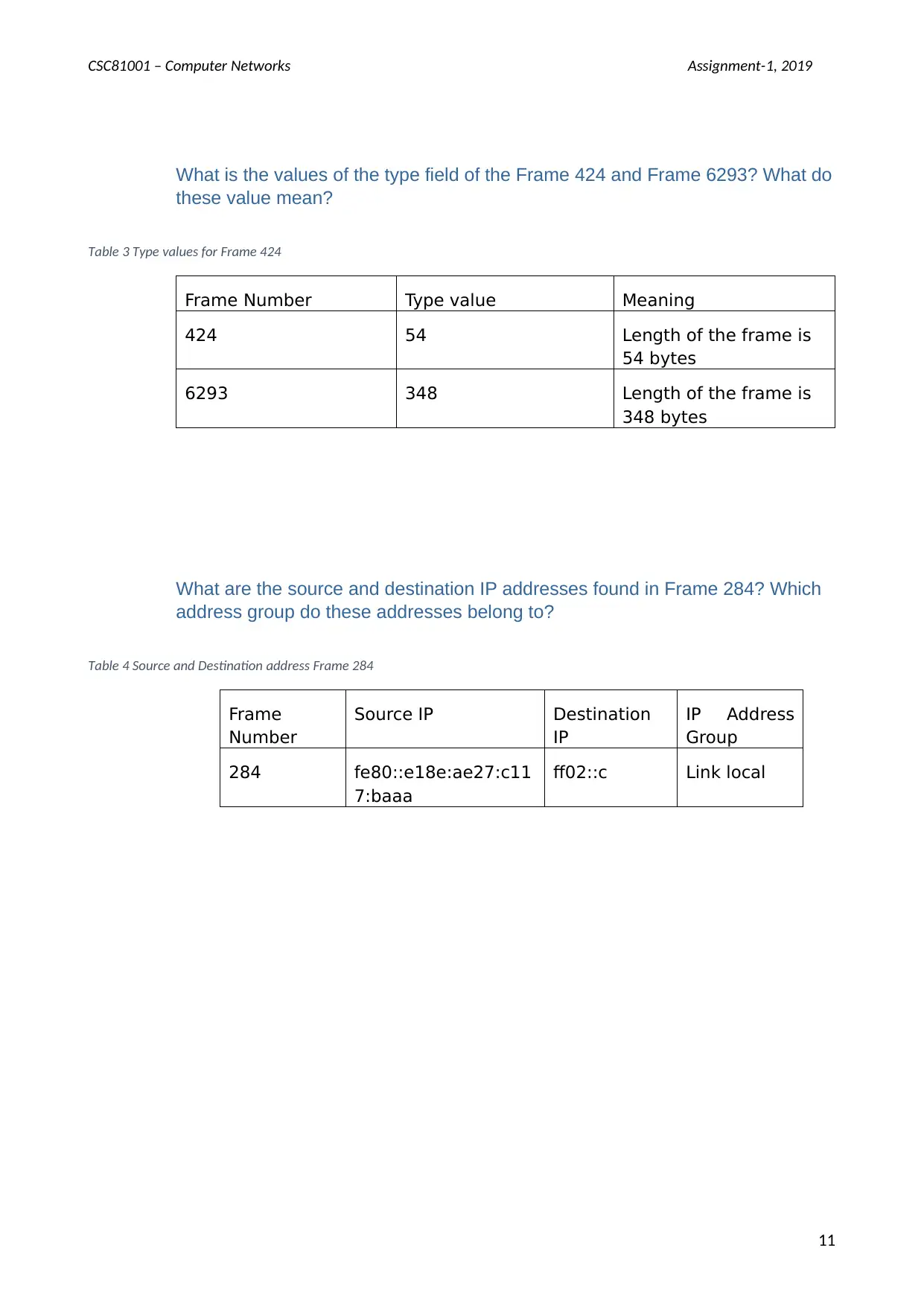
CSC81001 – Computer Networks Assignment-1, 2019
What is the values of the type field of the Frame 424 and Frame 6293? What do
these value mean?
Table 3 Type values for Frame 424
Frame Number Type value Meaning
424 54 Length of the frame is
54 bytes
6293 348 Length of the frame is
348 bytes
What are the source and destination IP addresses found in Frame 284? Which
address group do these addresses belong to?
Table 4 Source and Destination address Frame 284
Frame
Number
Source IP Destination
IP
IP Address
Group
284 fe80::e18e:ae27:c11
7:baaa
ff02::c Link local
11
What is the values of the type field of the Frame 424 and Frame 6293? What do
these value mean?
Table 3 Type values for Frame 424
Frame Number Type value Meaning
424 54 Length of the frame is
54 bytes
6293 348 Length of the frame is
348 bytes
What are the source and destination IP addresses found in Frame 284? Which
address group do these addresses belong to?
Table 4 Source and Destination address Frame 284
Frame
Number
Source IP Destination
IP
IP Address
Group
284 fe80::e18e:ae27:c11
7:baaa
ff02::c Link local
11

CSC81001 – Computer Networks Assignment-1, 2019
Task 3: Network Architecture Analysis
List APs with their locations, SSIDs and channels
STUDENT TO USE THE SOFWARE:
HTTPS://WIFI.EKAHAU.COM/HEATMAPPER OR
HTTPS://WWW.NETSPOTAPP.COM TO GET ME THE HEAT MAP FOR THE
GOLD COAST CAMPUS WIFI ACCESS POINTS
The Gold Coast campus Wi-Fi coverage
CANNOT BE DISCUSSED WITHOUT THE HEAT MAP
12
Task 3: Network Architecture Analysis
List APs with their locations, SSIDs and channels
STUDENT TO USE THE SOFWARE:
HTTPS://WIFI.EKAHAU.COM/HEATMAPPER OR
HTTPS://WWW.NETSPOTAPP.COM TO GET ME THE HEAT MAP FOR THE
GOLD COAST CAMPUS WIFI ACCESS POINTS
The Gold Coast campus Wi-Fi coverage
CANNOT BE DISCUSSED WITHOUT THE HEAT MAP
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
