Solved: Cryptography and Security - CSC8419 Assessment 1 Solution
VerifiedAdded on 2024/05/20
|12
|1975
|234
Homework Assignment
AI Summary
This document presents a detailed solution to Cryptography and Security Assessment 1, covering key concepts such as the CIA triad (Confidentiality, Integrity, Availability), design decisions for secure systems, S-box substitutions, calculations involving Rotword and Rcon in cryptographic algorithms, and a comparison between DES (Data Encryption Standard) and AES (Advanced Encryption Standard). The solution provides explanations and calculations for each task, offering insights into the principles and practical aspects of cryptography and security. Desklib is a platform where students can find more solved assignments and past papers.

Student Name Student ID
CSC8419
Cryptography and Security
Assessment 1
Student Name:
Student ID:
1
CSC8419
Cryptography and Security
Assessment 1
Student Name:
Student ID:
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Student Name Student ID
Contents
Task 1: What does CIA stand for in the context of computer security?.................................................3
Task 2: List 5 general design decisions that have to be made while constructing secure systems.........5
Task 3:...................................................................................................................................................7
Task 4:...................................................................................................................................................8
Task 5..................................................................................................................................................10
References...........................................................................................................................................12
2
Contents
Task 1: What does CIA stand for in the context of computer security?.................................................3
Task 2: List 5 general design decisions that have to be made while constructing secure systems.........5
Task 3:...................................................................................................................................................7
Task 4:...................................................................................................................................................8
Task 5..................................................................................................................................................10
References...........................................................................................................................................12
2

Student Name Student ID
Task 1: What does CIA stand for in the context of computer security?
CIA
CIA is a combined form for basic computer security. It consists of mainly three features
which ensures or assists the security levels. These terms are –
Confidentiality
Integrity
Availability
These three terms jointly conclude to system security. All these elements play a crucial role
in system security and all these parameters must be achieved. If any of the principle
components is not achieved, then there can be some serious issue in a security breach of the
data.
Confidentiality
This term is related to the privacy policy of security. In this such security measures are taken
which ensures the data to be open to genuine and authorized person and not to a wrong
person. Access of data must be restricted to an only authorized person then the parameter of
confidentiality is reached. Usage of strong password for securing the data is a known practice
for confidentiality. ACL (Access Control Lists) can be applied to control the user executions
to the data. This will ensure that there will be no damage or alteration to data from an
unauthorized person. Encryption and cryptography is a great option for the parameter of
confidentiality (Chia, 2018).
Integrity
It is the term which ensures that the through its cycle is consistent and accurate. Here attacks
are done by intercepting the data and altering the information. Data cannot be changed or
altered here from an unauthorized person. Here Access Control Lists (ACL) comes handy in
managing the user permissions for the data. Data encryption algorithms can help in the data
integrity property of the data. Therefore, integrity is somewhat dependent on the
confidentiality of data (Chia, 2018).
3
Task 1: What does CIA stand for in the context of computer security?
CIA
CIA is a combined form for basic computer security. It consists of mainly three features
which ensures or assists the security levels. These terms are –
Confidentiality
Integrity
Availability
These three terms jointly conclude to system security. All these elements play a crucial role
in system security and all these parameters must be achieved. If any of the principle
components is not achieved, then there can be some serious issue in a security breach of the
data.
Confidentiality
This term is related to the privacy policy of security. In this such security measures are taken
which ensures the data to be open to genuine and authorized person and not to a wrong
person. Access of data must be restricted to an only authorized person then the parameter of
confidentiality is reached. Usage of strong password for securing the data is a known practice
for confidentiality. ACL (Access Control Lists) can be applied to control the user executions
to the data. This will ensure that there will be no damage or alteration to data from an
unauthorized person. Encryption and cryptography is a great option for the parameter of
confidentiality (Chia, 2018).
Integrity
It is the term which ensures that the through its cycle is consistent and accurate. Here attacks
are done by intercepting the data and altering the information. Data cannot be changed or
altered here from an unauthorized person. Here Access Control Lists (ACL) comes handy in
managing the user permissions for the data. Data encryption algorithms can help in the data
integrity property of the data. Therefore, integrity is somewhat dependent on the
confidentiality of data (Chia, 2018).
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Student Name Student ID
Availability
Data availability can be understood by its name. Data and information must be available. The
authorized users must be able to access the data or information whenever required. It can be
ensured by regular checkup and maintenance of the hardware and network components to
provide consistent service. Attackers mostly find a way to discontinuing the service provided
by the system so that data is not available to the end user. (Chia, 2018)
4
Availability
Data availability can be understood by its name. Data and information must be available. The
authorized users must be able to access the data or information whenever required. It can be
ensured by regular checkup and maintenance of the hardware and network components to
provide consistent service. Attackers mostly find a way to discontinuing the service provided
by the system so that data is not available to the end user. (Chia, 2018)
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Student Name Student ID
Task 2: List 5 general design decisions that have to be made while
constructing secure systems.
5 Designs decisions
The security design is very important for implementing the security. A better security design
can lead to a good security approach. Mentioned below are the security design that can be
advantageous (Stickymind, 2016)-
1. Categorizing the source system is important. A centralized and decentralized control are
the options for design. If there is a centralized system, then all of the security is focused
on a particular central system but if it’s decentralized design then the security must be
implemented on all the components.
2. Design decision on the basis of what kind of material or data would likely to be
controlled. There are different areas which can be managed like – user, asset or data
management. In this different kinds of privileges are applied according to the authorized
user. The data stored in the system from different sources may not be reliable, so, data
integrity is really important.
3. The design of the security can also rely on the way of the system to be. Either it has to be
simple or complex. A simpler security design can be fast and easier to manage but a
minimalistic security can be implemented which provides a wide surface for the attackers
to penetrate the system security whereas a complex security design can lead to a strong
security but a bit slower than simple design.
4. The principle of least privilege can be a great option to be implemented as a security
feature. In this, the least quantity of privilege is set over a set of data or information. Least
number of privileged account will not be able to access or alter the data. Access Control
Lists (ACLs) can be set to meet the particular privileges of the users or over data. The
limited authorized user can be responsible for a security breach.
5. Always avoid Security through Obscurity. Security implementation through Obscurity is
a weak security practice and mostly fails when this is the only security control. It is the
practice of believing that any outsider from the implementation group cannot be able to
know the internal mechanism of the system.
Example – like hiding user passwords in a binary format and to assume that no one can
decode the binary.
5
Task 2: List 5 general design decisions that have to be made while
constructing secure systems.
5 Designs decisions
The security design is very important for implementing the security. A better security design
can lead to a good security approach. Mentioned below are the security design that can be
advantageous (Stickymind, 2016)-
1. Categorizing the source system is important. A centralized and decentralized control are
the options for design. If there is a centralized system, then all of the security is focused
on a particular central system but if it’s decentralized design then the security must be
implemented on all the components.
2. Design decision on the basis of what kind of material or data would likely to be
controlled. There are different areas which can be managed like – user, asset or data
management. In this different kinds of privileges are applied according to the authorized
user. The data stored in the system from different sources may not be reliable, so, data
integrity is really important.
3. The design of the security can also rely on the way of the system to be. Either it has to be
simple or complex. A simpler security design can be fast and easier to manage but a
minimalistic security can be implemented which provides a wide surface for the attackers
to penetrate the system security whereas a complex security design can lead to a strong
security but a bit slower than simple design.
4. The principle of least privilege can be a great option to be implemented as a security
feature. In this, the least quantity of privilege is set over a set of data or information. Least
number of privileged account will not be able to access or alter the data. Access Control
Lists (ACLs) can be set to meet the particular privileges of the users or over data. The
limited authorized user can be responsible for a security breach.
5. Always avoid Security through Obscurity. Security implementation through Obscurity is
a weak security practice and mostly fails when this is the only security control. It is the
practice of believing that any outsider from the implementation group cannot be able to
know the internal mechanism of the system.
Example – like hiding user passwords in a binary format and to assume that no one can
decode the binary.
5

Student Name Student ID
All of the above decisions are some of the points to ponder while constructing a security
design. But the basic triad of CIA (Confidentiality, Integrity and Availability) must always be
practised for a security implementation.
6
All of the above decisions are some of the points to ponder while constructing a security
design. But the basic triad of CIA (Confidentiality, Integrity and Availability) must always be
practised for a security implementation.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Student Name Student ID
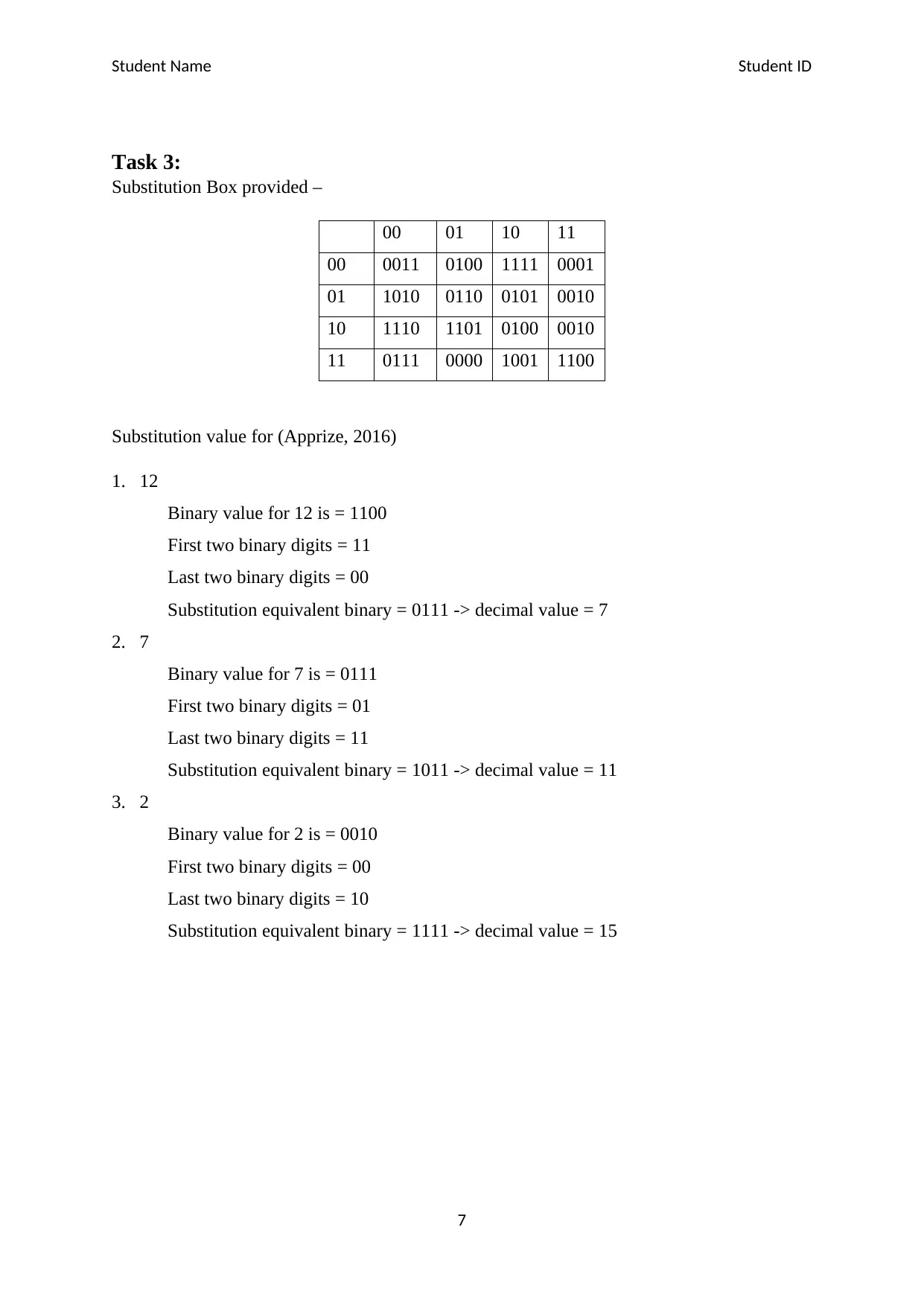
Task 3:
Substitution Box provided –
00 01 10 11
00 0011 0100 1111 0001
01 1010 0110 0101 0010
10 1110 1101 0100 0010
11 0111 0000 1001 1100
Substitution value for (Apprize, 2016)
1. 12
Binary value for 12 is = 1100
First two binary digits = 11
Last two binary digits = 00
Substitution equivalent binary = 0111 -> decimal value = 7
2. 7
Binary value for 7 is = 0111
First two binary digits = 01
Last two binary digits = 11
Substitution equivalent binary = 1011 -> decimal value = 11
3. 2
Binary value for 2 is = 0010
First two binary digits = 00
Last two binary digits = 10
Substitution equivalent binary = 1111 -> decimal value = 15
7
Task 3:
Substitution Box provided –
00 01 10 11
00 0011 0100 1111 0001
01 1010 0110 0101 0010
10 1110 1101 0100 0010
11 0111 0000 1001 1100
Substitution value for (Apprize, 2016)
1. 12
Binary value for 12 is = 1100
First two binary digits = 11
Last two binary digits = 00
Substitution equivalent binary = 0111 -> decimal value = 7
2. 7
Binary value for 7 is = 0111
First two binary digits = 01
Last two binary digits = 11
Substitution equivalent binary = 1011 -> decimal value = 11
3. 2
Binary value for 2 is = 0010
First two binary digits = 00
Last two binary digits = 10
Substitution equivalent binary = 1111 -> decimal value = 15
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Student Name Student ID
Task 4:
Given values of w[ ] are:
w[0] = 2b7e1516
w[1] = 28aed2a6
w[2] = abf71588
w[3] = 09cf4f3c
To calculate for w[4], w[5], w[6] and w[7]
Key terms:
For w[4]
Nk: It consists of 32-bit words (Cipher Key)
i=4,
Rotword: In this cycle permutation is done in 8 bytes.
For w[4] Rotword = cf 4f 3c 09
SubWords: Here substitution happens where equivalent 8 bytes from S-box are
substituted
SubWord() for 4 8a 84 eb 01
Rcon = i/Nk
For w[4], i=4 and Nk=4
Rcon[1] = 01 00 00 00
Finally, XOR of SubWord() of Rcon() then we will get 8b 84 eb 01
w[i-Nk]= 2b 7e 15 16
Now w[i] will be equal to XOR of temp and w[i-Nk], for w[4] it’ll be a0 fa fe 17
Similarly,
For w[5]
i = 5
8
Task 4:
Given values of w[ ] are:
w[0] = 2b7e1516
w[1] = 28aed2a6
w[2] = abf71588
w[3] = 09cf4f3c
To calculate for w[4], w[5], w[6] and w[7]
Key terms:
For w[4]
Nk: It consists of 32-bit words (Cipher Key)
i=4,
Rotword: In this cycle permutation is done in 8 bytes.
For w[4] Rotword = cf 4f 3c 09
SubWords: Here substitution happens where equivalent 8 bytes from S-box are
substituted
SubWord() for 4 8a 84 eb 01
Rcon = i/Nk
For w[4], i=4 and Nk=4
Rcon[1] = 01 00 00 00
Finally, XOR of SubWord() of Rcon() then we will get 8b 84 eb 01
w[i-Nk]= 2b 7e 15 16
Now w[i] will be equal to XOR of temp and w[i-Nk], for w[4] it’ll be a0 fa fe 17
Similarly,
For w[5]
i = 5
8

Student Name Student ID
temp = a0 fa fe 17
w [i-Nk] = 28 ae d2 a6
Temp XOR w [i-Nk] = 88 54 2c b1
For w[6]
i = 6
temp = 88 54 2c b1
w [i-Nk] = ab f7 15 88
Temp XOR w [i-Nk] = 23 a3 39 39
For w[7]
i = 7
temp = 23 a3 39 39
w [i-Nk] = 09 cf 4f 3c
Temp XOR w [i-Nk] = 2a 6c 76 05
9
temp = a0 fa fe 17
w [i-Nk] = 28 ae d2 a6
Temp XOR w [i-Nk] = 88 54 2c b1
For w[6]
i = 6
temp = 88 54 2c b1
w [i-Nk] = ab f7 15 88
Temp XOR w [i-Nk] = 23 a3 39 39
For w[7]
i = 7
temp = 23 a3 39 39
w [i-Nk] = 09 cf 4f 3c
Temp XOR w [i-Nk] = 2a 6c 76 05
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Student Name Student ID
Task 5
DES (Data Encryption Standard) and AES (Advanced Encryption Standard)
DES and AES both of them are symmetric block cipher encryption technique. AES was
developed to overcome existing problems which DES was going through. DES is a method in
which the entire plain text is divided in two parts and then it is passed to the main algorithm
but in AES whole plain text is taken as input in algorithm (System, 2016).
DES – Data Encryption Standard is symmetric key block which was further chosen by NIST
(National Institute of Standard and Technology) in 1977. In DES the plain text is first divided
into two parts and then passed to the algorithm for further process of encryption. It takes in
the input text i.e., plain text of 64-bit and a key of 56-bit and the resultant cipher text is of 64-
bit.
Each round of the DES algorithm includes following functions –
Expansion Permutation
XOR
S-box
P-box
AES – Advanced Encryption Standard like DES is also symmetric block cipher encryption
technique and was chosen by NIST in 2001. AES was developed to replace the old DES
because DES was using small cipher key and DES was way slower. The AES takes input of
128-bit text as a plain text and 128-bit key which when further processing according to
algorithm develops a 128-bit cipher text.
For N-1 rounds AES includes following functions –
Sub Bytes
Shift Rows
Mix Columns
Add round keys
DES and AES Comparison –
10
Task 5
DES (Data Encryption Standard) and AES (Advanced Encryption Standard)
DES and AES both of them are symmetric block cipher encryption technique. AES was
developed to overcome existing problems which DES was going through. DES is a method in
which the entire plain text is divided in two parts and then it is passed to the main algorithm
but in AES whole plain text is taken as input in algorithm (System, 2016).
DES – Data Encryption Standard is symmetric key block which was further chosen by NIST
(National Institute of Standard and Technology) in 1977. In DES the plain text is first divided
into two parts and then passed to the algorithm for further process of encryption. It takes in
the input text i.e., plain text of 64-bit and a key of 56-bit and the resultant cipher text is of 64-
bit.
Each round of the DES algorithm includes following functions –
Expansion Permutation
XOR
S-box
P-box
AES – Advanced Encryption Standard like DES is also symmetric block cipher encryption
technique and was chosen by NIST in 2001. AES was developed to replace the old DES
because DES was using small cipher key and DES was way slower. The AES takes input of
128-bit text as a plain text and 128-bit key which when further processing according to
algorithm develops a 128-bit cipher text.
For N-1 rounds AES includes following functions –
Sub Bytes
Shift Rows
Mix Columns
Add round keys
DES and AES Comparison –
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Student Name Student ID
DES first divides the plain text in two parts and then apply the algorithm for cipher
text while in AES the whole plain text is taken as input and then algorithm is
implemented to produce cipher text.
AES works on the principle of permutation and substitution whereas DES works on
the Feistel Cipher.
The key used by DES is of 56-bit which is comparatively very small in size than AES,
AES uses 128, 192 or 256-bit key.
AES is more secure than DES because of the use of bigger size of secret ey used in
algorithm. This is the biggest drawback of DES.
DES is slower when compared to AES (System, 2016).
11
DES first divides the plain text in two parts and then apply the algorithm for cipher
text while in AES the whole plain text is taken as input and then algorithm is
implemented to produce cipher text.
AES works on the principle of permutation and substitution whereas DES works on
the Feistel Cipher.
The key used by DES is of 56-bit which is comparatively very small in size than AES,
AES uses 128, 192 or 256-bit key.
AES is more secure than DES because of the use of bigger size of secret ey used in
algorithm. This is the biggest drawback of DES.
DES is slower when compared to AES (System, 2016).
11

Student Name Student ID
References
Chia, T, 2018, Confidentiality, Integrity, Availability: The three components of the CIA
Triad « Stack Exchange Security Blog, Security.blogoverflow.com, Viewed 2 April 2018,
from <https://security.blogoverflow.com/2012/08/confidentiality-integrity-availability-
the-three-components-of-the-cia-triad/>
Stickymind, 2016, Using the Principles of the CIA Triad to Implement Software Security,
StickyMinds, Viewed 2 April 2018, from <https://www.stickyminds.com/article/using-
principles-cia-triad-implement-software-security>
System, O, 2016, Difference Between DES and AES (with Comparison Chart) - Tech
Differences, Tech Differences, Viewed 2 April 2018, from
<https://techdifferences.com/difference-between-des-and-aes.html>
Apprize, 2016, Modern Cryptography: Applied Mathematics for Encryption and
Information Security, Viewed 2 April 2018, from
<http://apprize.info/security/cryptography/9.html>
12
References
Chia, T, 2018, Confidentiality, Integrity, Availability: The three components of the CIA
Triad « Stack Exchange Security Blog, Security.blogoverflow.com, Viewed 2 April 2018,
from <https://security.blogoverflow.com/2012/08/confidentiality-integrity-availability-
the-three-components-of-the-cia-triad/>
Stickymind, 2016, Using the Principles of the CIA Triad to Implement Software Security,
StickyMinds, Viewed 2 April 2018, from <https://www.stickyminds.com/article/using-
principles-cia-triad-implement-software-security>
System, O, 2016, Difference Between DES and AES (with Comparison Chart) - Tech
Differences, Tech Differences, Viewed 2 April 2018, from
<https://techdifferences.com/difference-between-des-and-aes.html>
Apprize, 2016, Modern Cryptography: Applied Mathematics for Encryption and
Information Security, Viewed 2 April 2018, from
<http://apprize.info/security/cryptography/9.html>
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


