CSC8419 Cryptography and Security Assignment: Comprehensive Solution
VerifiedAdded on 2024/05/29
|12
|1160
|229
Homework Assignment
AI Summary
This document provides a detailed solution to a Cryptography and Security assignment, focusing on several key tasks. Task 1 involves using a Debian HTTP server to download a Debian DVD ISO image file and verifying its SHA-1 encrypted signature using GNU Privacy Guard. Task 2 demonstrates the generation of public and private keys, along with shared secret keys. Task 4 provides an introduction to digital certificates, explaining their role in secure data exchange using Public Key Infrastructure (PKI). It outlines the steps to generate a digital certificate using OpenSSL, including generating a private key with RSA and a Certificate Signing Request (CSR), creating a public key, securing the private key file with a password, and verifying the digital certificate. The solution also covers creating certificates in PEM format, establishing a chain of trust, and verifying certificates with the trust chain. The assignment concludes with the process of installing the private key and certificate, followed by restarting the test and Apache server. Desklib offers more solved assignments and study resources for students.

CSC8419
Assignment 2
Cryptography and Security
Student Name:
Student Number:
Assignment 2
Cryptography and Security
Student Name:
Student Number:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Task 1...............................................................................................................................................2
Task 2...............................................................................................................................................4
Task4................................................................................................................................................8
Introduction..................................................................................................................................8
Content.........................................................................................................................................8
Conclusion.................................................................................................................................10
Reference...................................................................................................................................11
1
Task 1...............................................................................................................................................2
Task 2...............................................................................................................................................4
Task4................................................................................................................................................8
Introduction..................................................................................................................................8
Content.........................................................................................................................................8
Conclusion.................................................................................................................................10
Reference...................................................................................................................................11
1

Task 1
Debian Http server can be used to download the Debian DVD ISO image file. A link is provided
to download this file that is https://goo.gl/8CNeyc. It is requiring verifying the SHA-1 algorithm
for encrypted the signature.
In the first step, it requires listing the directory files for the confirmation that all the files
are at correct place.
The second step, the terms of the SHA-1 need the encrypted signature so check the
signature by using the GNU Privacy Guard.
o The public key is not available during the running time of the command. It is
required to get the public key through the ID = ‘6294BE9B’. This Id is used to
retrieve the public key.
The third step, the public key can be download with the id = ‘6294BE9B’ for the server
of the Debian key ring.
2
Debian Http server can be used to download the Debian DVD ISO image file. A link is provided
to download this file that is https://goo.gl/8CNeyc. It is requiring verifying the SHA-1 algorithm
for encrypted the signature.
In the first step, it requires listing the directory files for the confirmation that all the files
are at correct place.
The second step, the terms of the SHA-1 need the encrypted signature so check the
signature by using the GNU Privacy Guard.
o The public key is not available during the running time of the command. It is
required to get the public key through the ID = ‘6294BE9B’. This Id is used to
retrieve the public key.
The third step, the public key can be download with the id = ‘6294BE9B’ for the server
of the Debian key ring.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

In this step, verify the signature for SHA-1.
The authenticity of Debian DVD image is confirmed by the “Good signature from
Debian CD signature key that is <debian-cd@lists.debisn.org>". Use the fingerprints:
DF9B9C49EAA929843258, that are generated and compare with
http://www.debian.org/CD/verify. The result of this comparison shows:
In the last step, verify the ISO image with its content and check the checksum of with
file.
3
The authenticity of Debian DVD image is confirmed by the “Good signature from
Debian CD signature key that is <debian-cd@lists.debisn.org>". Use the fingerprints:
DF9B9C49EAA929843258, that are generated and compare with
http://www.debian.org/CD/verify. The result of this comparison shows:
In the last step, verify the ISO image with its content and check the checksum of with
file.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
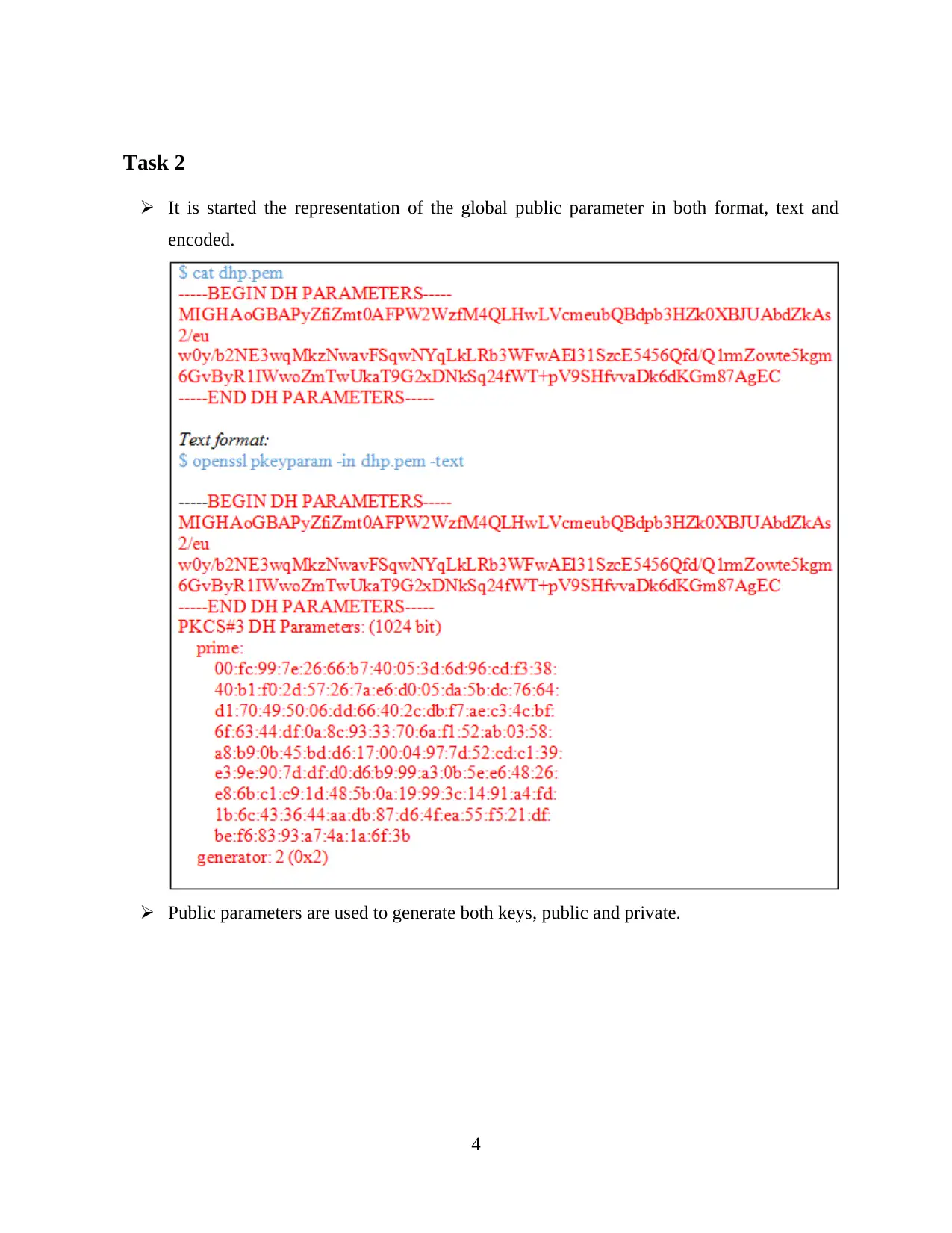
Task 2
It is started the representation of the global public parameter in both format, text and
encoded.
Public parameters are used to generate both keys, public and private.
4
It is started the representation of the global public parameter in both format, text and
encoded.
Public parameters are used to generate both keys, public and private.
4
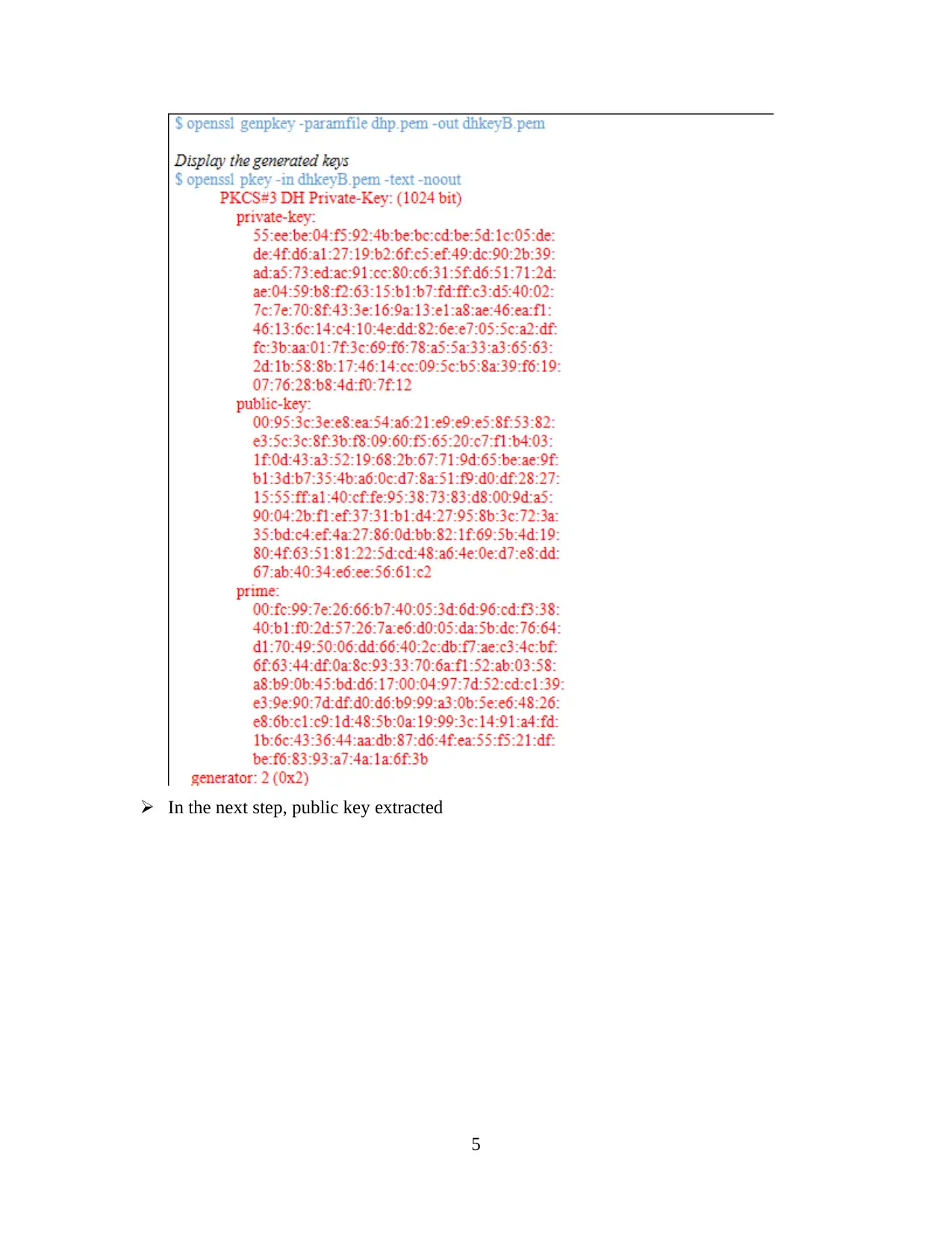
In the next step, public key extracted
5
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The shared secret key is generated by the instructor and as the instructor uses the private
and public key.
6
and public key.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
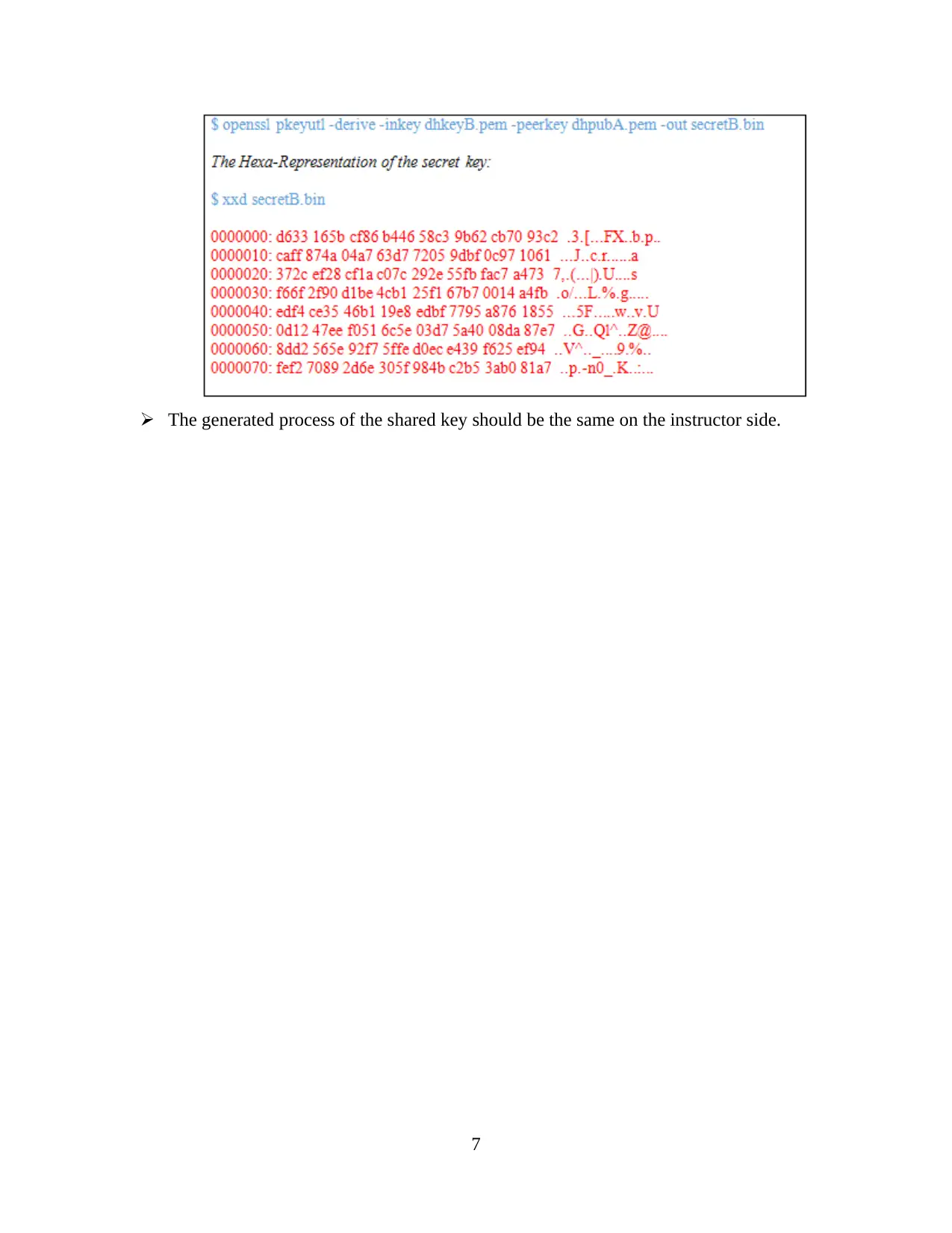
The generated process of the shared key should be the same on the instructor side.
7
7

Task4
Introduction
A digital certificate is an authentication process which uses the web credential to allow a person
or the organization to exchange the data using PKI (public key infrastructure) over the internet. It
is like an electronic password. The information which used to send and receive over the internet
are found in the form of packets and it is issued by the CA (certification authority). A digital
certificate has used the techniques, message encryption and self-signature. It another name of the
digital certification are identity certificate and public key certificates. To generate the digital
certificate the, the user needs to follow some steps which will be discussed in the report (Brands,
2000). Open SSL is a cryptography library which used for the implementation SSL (Secure
sockets layer) and also Transport layer security (TLS). These both created layers are like
protocol (Davies, 2011).
Content
Here are some steps which used to follow to generate the digital certificate using the self-signed
certificate, private key and CSR (certificate signing request).
Generate Private Key: generate a private key with RSA and CSR (certificate signing request).
This generation can happen after the request of a digital certificate for the server. The private key
can be generating with the PEM format. SAS requires using the PEM format on UNIX (Burns,
N., Schlozman, K.L. and Verba, S., 2001).
Generate the public key: the generation of the public key is an optional step using the server
and CA. There are some issues which occur during the generation of the public key like:
o The issue of an appropriate command
o Display the informational message (Bo, Y., Zhang, M. and Du, J.Q., 2016)
Security of the Private Key File: use the password to make secure the network and restrict to
access the key file by another person. This process of protecting by the password can be done
after the generation of the private key.
8
Introduction
A digital certificate is an authentication process which uses the web credential to allow a person
or the organization to exchange the data using PKI (public key infrastructure) over the internet. It
is like an electronic password. The information which used to send and receive over the internet
are found in the form of packets and it is issued by the CA (certification authority). A digital
certificate has used the techniques, message encryption and self-signature. It another name of the
digital certification are identity certificate and public key certificates. To generate the digital
certificate the, the user needs to follow some steps which will be discussed in the report (Brands,
2000). Open SSL is a cryptography library which used for the implementation SSL (Secure
sockets layer) and also Transport layer security (TLS). These both created layers are like
protocol (Davies, 2011).
Content
Here are some steps which used to follow to generate the digital certificate using the self-signed
certificate, private key and CSR (certificate signing request).
Generate Private Key: generate a private key with RSA and CSR (certificate signing request).
This generation can happen after the request of a digital certificate for the server. The private key
can be generating with the PEM format. SAS requires using the PEM format on UNIX (Burns,
N., Schlozman, K.L. and Verba, S., 2001).
Generate the public key: the generation of the public key is an optional step using the server
and CA. There are some issues which occur during the generation of the public key like:
o The issue of an appropriate command
o Display the informational message (Bo, Y., Zhang, M. and Du, J.Q., 2016)
Security of the Private Key File: use the password to make secure the network and restrict to
access the key file by another person. This process of protecting by the password can be done
after the generation of the private key.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Check the digital certificate: the checking process of the digital certificate can be done with
using the command for example:
Openssl> 509 – text –in filename. Pem
Create a certificate with using PEM format: the certificate has been generated for the client
and for the server. Identify the openSSf for trusted as the CAs. This procedure is called a chain
of trust.
Verify the certificates with the trust chain using OpenSSL: the digital certificates of servers
can be exchanged with the digital certificates of the client. This exchange process also needs to
validate the certificate of the server and create trust chain (Armknecht, F., Gasmi, Y., Sadeghi,
A.R., Stewin, P., Unger, M., Ramunno, G. and Vernizzi, D., 2008).
End OpenSSL: type quit to exit from the server.
9
using the command for example:
Openssl> 509 – text –in filename. Pem
Create a certificate with using PEM format: the certificate has been generated for the client
and for the server. Identify the openSSf for trusted as the CAs. This procedure is called a chain
of trust.
Verify the certificates with the trust chain using OpenSSL: the digital certificates of servers
can be exchanged with the digital certificates of the client. This exchange process also needs to
validate the certificate of the server and create trust chain (Armknecht, F., Gasmi, Y., Sadeghi,
A.R., Stewin, P., Unger, M., Ramunno, G. and Vernizzi, D., 2008).
End OpenSSL: type quit to exit from the server.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Conclusion
The explanation of the digital certificate is achieved successfully with OpenSSL. The generation
of the digital certificate explained with steps to follow like, generation of the private key with the
CSR (certificate signing request). The next step of the generation of the digital certificate has
deleted the passphrase. The next is to generating the certificate either with self-signed. Install
process is of the private key and the certificate is the final step and restart the test and apache.
10
The explanation of the digital certificate is achieved successfully with OpenSSL. The generation
of the digital certificate explained with steps to follow like, generation of the private key with the
CSR (certificate signing request). The next step of the generation of the digital certificate has
deleted the passphrase. The next is to generating the certificate either with self-signed. Install
process is of the private key and the certificate is the final step and restart the test and apache.
10

Reference
Armknecht, F., Gasmi, Y., Sadeghi, A.R., Stewin, P., Unger, M., Ramunno, G. and Vernizzi,
D., 2008, October. An efficient implementation of trusted channels based on OpenSSL.
In Proceedings of the 3rd ACM workshop on Scalable trusted computing (pp. 41-50). ACM.
Bo, Y., Zhang, M. and Du, J.Q., 2016. An error‐tolerant keyword search scheme based on
public‐key encryption in secure cloud computing. Concurrency and Computation: Practice
and Experience, 28(4), pp.1083-1093.
Brands, S.A., 2000. Rethinking public key infrastructures and digital certificates: building in
privacy. Mit Press.
Burns, N., Schlozman, K.L. and Verba, S., 2001. The private roots of public action. Harvard
University Press.
Davies, J., 2011. Implementing SSL/TLS using cryptography and PKI. John Wiley and Sons.
11
Armknecht, F., Gasmi, Y., Sadeghi, A.R., Stewin, P., Unger, M., Ramunno, G. and Vernizzi,
D., 2008, October. An efficient implementation of trusted channels based on OpenSSL.
In Proceedings of the 3rd ACM workshop on Scalable trusted computing (pp. 41-50). ACM.
Bo, Y., Zhang, M. and Du, J.Q., 2016. An error‐tolerant keyword search scheme based on
public‐key encryption in secure cloud computing. Concurrency and Computation: Practice
and Experience, 28(4), pp.1083-1093.
Brands, S.A., 2000. Rethinking public key infrastructures and digital certificates: building in
privacy. Mit Press.
Burns, N., Schlozman, K.L. and Verba, S., 2001. The private roots of public action. Harvard
University Press.
Davies, J., 2011. Implementing SSL/TLS using cryptography and PKI. John Wiley and Sons.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





