CSC8419 Cryptography and Security Assignment Solution with DES/AES
VerifiedAdded on 2024/06/04
|11
|1334
|458
Homework Assignment
AI Summary
This document provides a solution to a Cryptography and Security assignment (CSC8419), covering tasks related to signature verification using GNU Privacy Guard, key generation, and a review of DES and AES encryption algorithms. The signature verification process involves checking the validity of a Debian DVD image using MD5 signatures and the Debian CD signing key. The key generation tasks demonstrate the creation of public and private keys, along with the generation of a shared secret key. The review of DES and AES includes their background, working principles, security aspects, and a comparison, highlighting AES as a more secure and preferable encryption method due to its resistance to attacks and acceptable speed. Desklib is a platform that provides all the necessary AI based study tools for students.

CSC8419
Assignment 2
Cryptography and Security
Student Name:
Student Number:
Assignment 2
Cryptography and Security
Student Name:
Student Number:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Task 1.........................................................................................................................................2
Task 2.........................................................................................................................................4
Task 4.........................................................................................................................................7
Introduction............................................................................................................................7
Background............................................................................................................................7
References............................................................................................................................10
List of Figures
Figure 1: DES encryption...........................................................................................................8
Figure 2: AES.............................................................................................................................9
1
Task 1.........................................................................................................................................2
Task 2.........................................................................................................................................4
Task 4.........................................................................................................................................7
Introduction............................................................................................................................7
Background............................................................................................................................7
References............................................................................................................................10
List of Figures
Figure 1: DES encryption...........................................................................................................8
Figure 2: AES.............................................................................................................................9
1

Task 1
The files should be downloaded from the link: https://goo.gl/8CNeyc. The signature files
MD5 are done with the ISO image.
At first, list of all the available files in the directory to ensure if everything is operating
correctly.
Then second, we will verify signatures with the help of free GNU Privacy Guard
mutually for MD5.
There might be a possibility that public key is not available not the system at first. So
retrieval is done using ID = ‘6294BE9B’.
Now, downloading of public key is done by using the ID = ‘6294BE9B’.
Now, signature authentication is done.
2
The files should be downloaded from the link: https://goo.gl/8CNeyc. The signature files
MD5 are done with the ISO image.
At first, list of all the available files in the directory to ensure if everything is operating
correctly.
Then second, we will verify signatures with the help of free GNU Privacy Guard
mutually for MD5.
There might be a possibility that public key is not available not the system at first. So
retrieval is done using ID = ‘6294BE9B’.
Now, downloading of public key is done by using the ID = ‘6294BE9B’.
Now, signature authentication is done.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

“Good signature from "Debian CD signing key <debian- cd@lists.debian.org>” This will
confirm the validity of image from Debian DVD. The generated fingerprint key can also
be used, i.e., DF9B 9C49 EAA9 2984 3258 9D76 DA87 E80D 6294 BE9B.
At last, verification of the contents of an ISO image is done to ensure if the image
checksum matches with the checksum file.
3
confirm the validity of image from Debian DVD. The generated fingerprint key can also
be used, i.e., DF9B 9C49 EAA9 2984 3258 9D76 DA87 E80D 6294 BE9B.
At last, verification of the contents of an ISO image is done to ensure if the image
checksum matches with the checksum file.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
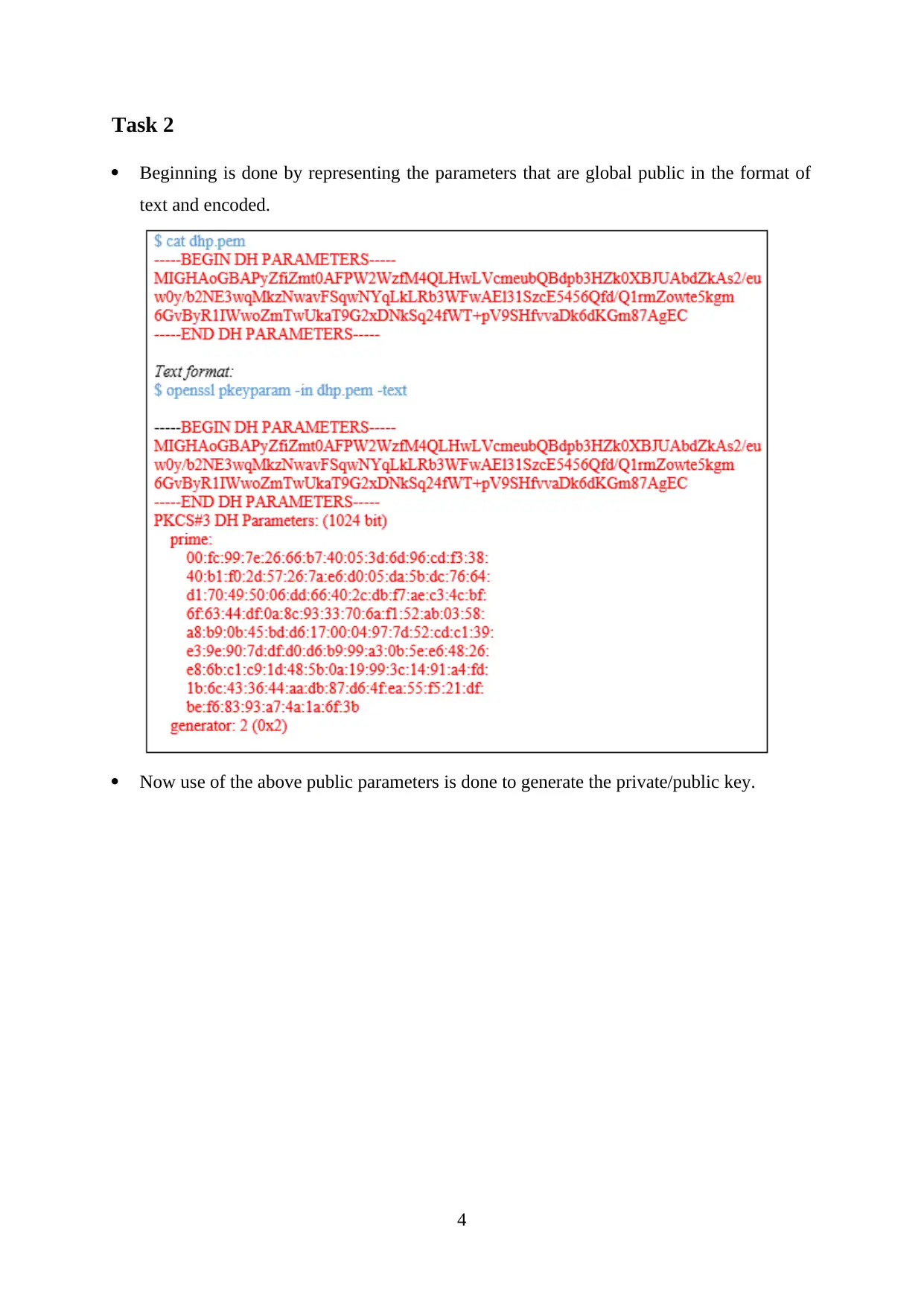
Task 2
Beginning is done by representing the parameters that are global public in the format of
text and encoded.
Now use of the above public parameters is done to generate the private/public key.
4
Beginning is done by representing the parameters that are global public in the format of
text and encoded.
Now use of the above public parameters is done to generate the private/public key.
4

Now extraction of the public key is done.
5
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
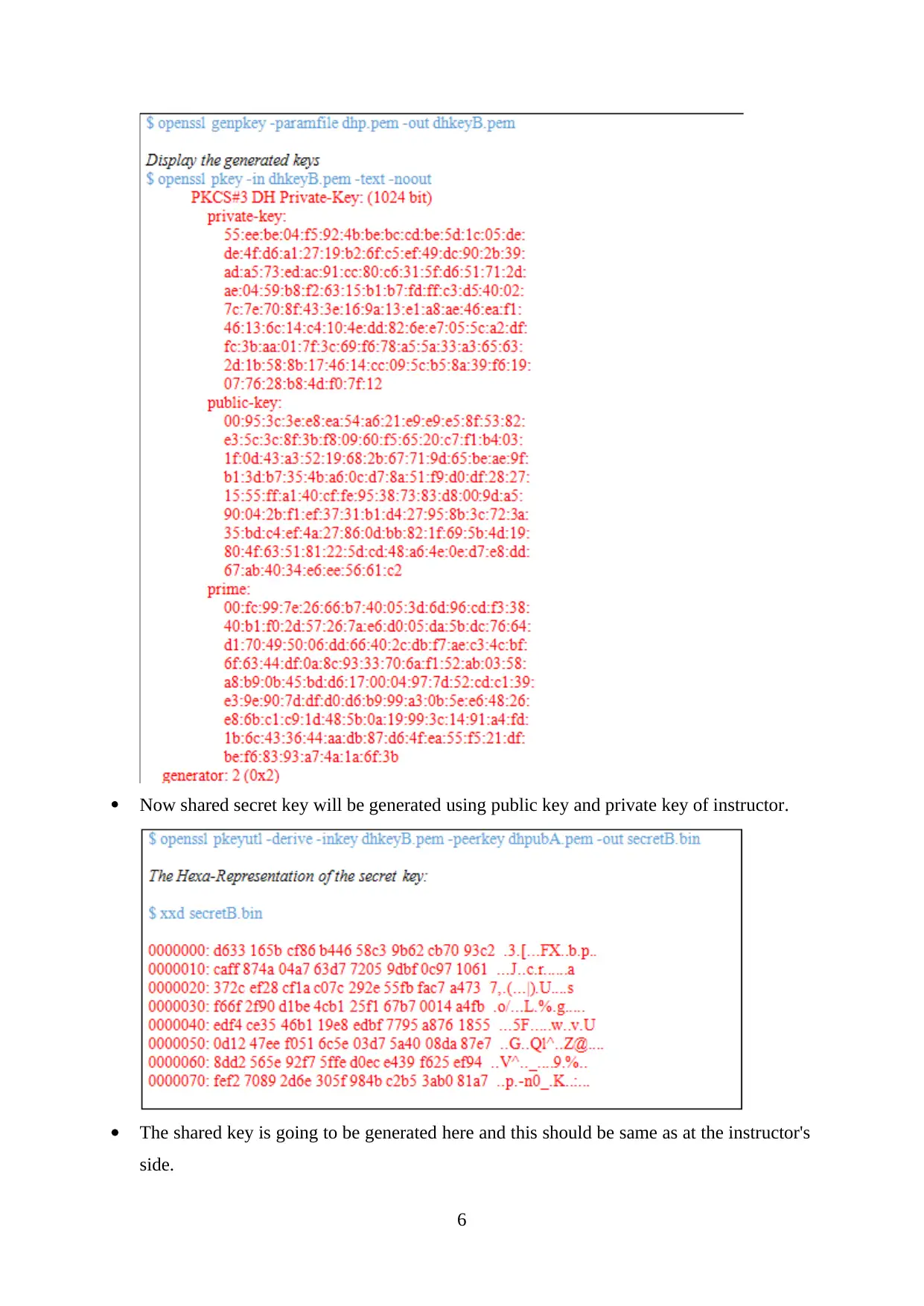
Now shared secret key will be generated using public key and private key of instructor.
The shared key is going to be generated here and this should be same as at the instructor's
side.
6
The shared key is going to be generated here and this should be same as at the instructor's
side.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Task 4
A review study of DES and AES
Introduction
Advanced Encryption Standard is termed as AES and Data Encryption Standard is termed as
DES. These are the encryption algorithms used for encrypting the text data. Encryption is the
procedure of changing a legible data into an illegible form so that it remains secure when
transmitted (Davies, 2011).
Background
In the process of encryption, the data is encoded in a certain format and then transmitted.
While transmitting the intruders can attack the data and may steal it. But due to encryption,
they fail to do so. So due to this, the data gets received safely at the receiver's side. The
encryption algorithm uses the concept of private and public keys. The public key is publically
available and anyone can use it. The private key is kept private and secured. The encryption
algorithm is classified in two ways: symmetric and asymmetric. The symmetric encryption
uses only one key method. The key is same at both sender side and receiver side. while in
asymmetric encryption algorithms, two keys are used. The AES and DES are two such
techniques of encryption (Bo, Y., Zhang, M. and Du, J.Q., 2016).
DES (Data encryption standard)
It was available via NIST. It is the most widely used algorithm all around the world. It is a
symmetric key block cypher. It is an implementation of Feistel Cipher. Sixteen rounds of
Feistel structures are used in this. The key size used is of 64 bit. The working of DES is
explained as under:
7
A review study of DES and AES
Introduction
Advanced Encryption Standard is termed as AES and Data Encryption Standard is termed as
DES. These are the encryption algorithms used for encrypting the text data. Encryption is the
procedure of changing a legible data into an illegible form so that it remains secure when
transmitted (Davies, 2011).
Background
In the process of encryption, the data is encoded in a certain format and then transmitted.
While transmitting the intruders can attack the data and may steal it. But due to encryption,
they fail to do so. So due to this, the data gets received safely at the receiver's side. The
encryption algorithm uses the concept of private and public keys. The public key is publically
available and anyone can use it. The private key is kept private and secured. The encryption
algorithm is classified in two ways: symmetric and asymmetric. The symmetric encryption
uses only one key method. The key is same at both sender side and receiver side. while in
asymmetric encryption algorithms, two keys are used. The AES and DES are two such
techniques of encryption (Bo, Y., Zhang, M. and Du, J.Q., 2016).
DES (Data encryption standard)
It was available via NIST. It is the most widely used algorithm all around the world. It is a
symmetric key block cypher. It is an implementation of Feistel Cipher. Sixteen rounds of
Feistel structures are used in this. The key size used is of 64 bit. The working of DES is
explained as under:
7
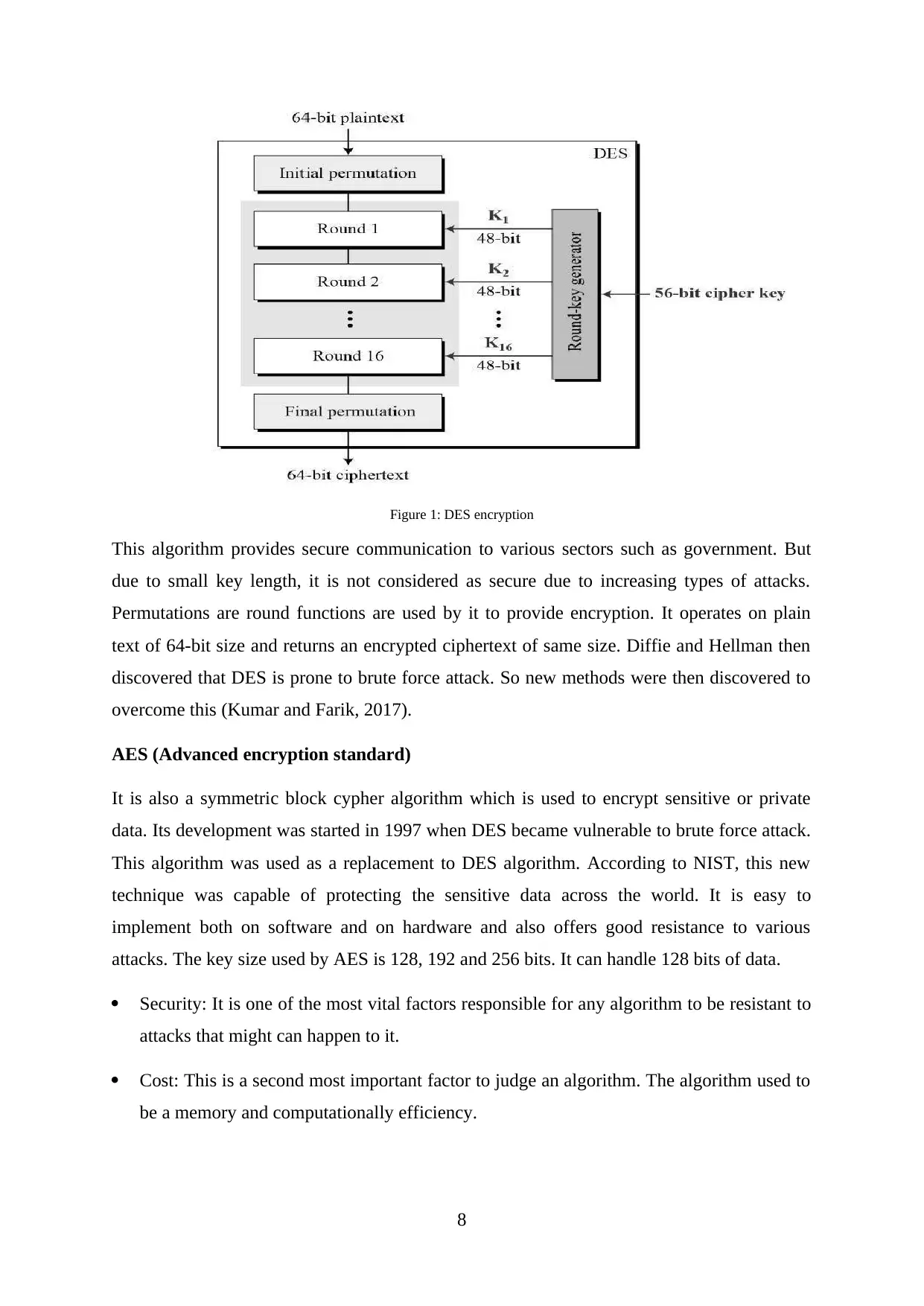
Figure 1: DES encryption
This algorithm provides secure communication to various sectors such as government. But
due to small key length, it is not considered as secure due to increasing types of attacks.
Permutations are round functions are used by it to provide encryption. It operates on plain
text of 64-bit size and returns an encrypted ciphertext of same size. Diffie and Hellman then
discovered that DES is prone to brute force attack. So new methods were then discovered to
overcome this (Kumar and Farik, 2017).
AES (Advanced encryption standard)
It is also a symmetric block cypher algorithm which is used to encrypt sensitive or private
data. Its development was started in 1997 when DES became vulnerable to brute force attack.
This algorithm was used as a replacement to DES algorithm. According to NIST, this new
technique was capable of protecting the sensitive data across the world. It is easy to
implement both on software and on hardware and also offers good resistance to various
attacks. The key size used by AES is 128, 192 and 256 bits. It can handle 128 bits of data.
Security: It is one of the most vital factors responsible for any algorithm to be resistant to
attacks that might can happen to it.
Cost: This is a second most important factor to judge an algorithm. The algorithm used to
be a memory and computationally efficiency.
8
This algorithm provides secure communication to various sectors such as government. But
due to small key length, it is not considered as secure due to increasing types of attacks.
Permutations are round functions are used by it to provide encryption. It operates on plain
text of 64-bit size and returns an encrypted ciphertext of same size. Diffie and Hellman then
discovered that DES is prone to brute force attack. So new methods were then discovered to
overcome this (Kumar and Farik, 2017).
AES (Advanced encryption standard)
It is also a symmetric block cypher algorithm which is used to encrypt sensitive or private
data. Its development was started in 1997 when DES became vulnerable to brute force attack.
This algorithm was used as a replacement to DES algorithm. According to NIST, this new
technique was capable of protecting the sensitive data across the world. It is easy to
implement both on software and on hardware and also offers good resistance to various
attacks. The key size used by AES is 128, 192 and 256 bits. It can handle 128 bits of data.
Security: It is one of the most vital factors responsible for any algorithm to be resistant to
attacks that might can happen to it.
Cost: This is a second most important factor to judge an algorithm. The algorithm used to
be a memory and computationally efficiency.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Implementation: The flexibility of an algorithm affects its implementation. The
implementation should be simple (Oukili and Bri, 2017).
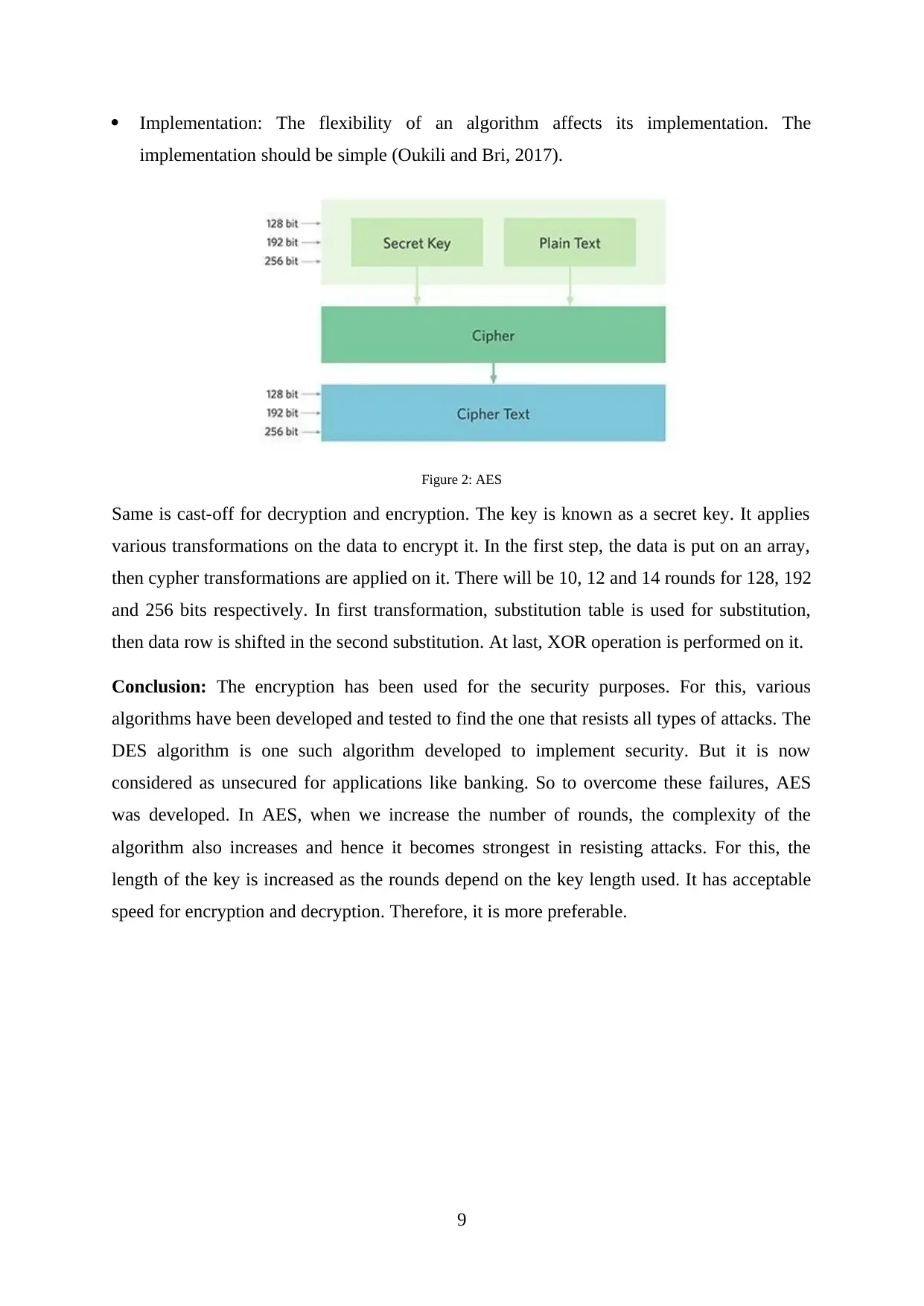
Figure 2: AES
Same is cast-off for decryption and encryption. The key is known as a secret key. It applies
various transformations on the data to encrypt it. In the first step, the data is put on an array,
then cypher transformations are applied on it. There will be 10, 12 and 14 rounds for 128, 192
and 256 bits respectively. In first transformation, substitution table is used for substitution,
then data row is shifted in the second substitution. At last, XOR operation is performed on it.
Conclusion: The encryption has been used for the security purposes. For this, various
algorithms have been developed and tested to find the one that resists all types of attacks. The
DES algorithm is one such algorithm developed to implement security. But it is now
considered as unsecured for applications like banking. So to overcome these failures, AES
was developed. In AES, when we increase the number of rounds, the complexity of the
algorithm also increases and hence it becomes strongest in resisting attacks. For this, the
length of the key is increased as the rounds depend on the key length used. It has acceptable
speed for encryption and decryption. Therefore, it is more preferable.
9
implementation should be simple (Oukili and Bri, 2017).
Figure 2: AES
Same is cast-off for decryption and encryption. The key is known as a secret key. It applies
various transformations on the data to encrypt it. In the first step, the data is put on an array,
then cypher transformations are applied on it. There will be 10, 12 and 14 rounds for 128, 192
and 256 bits respectively. In first transformation, substitution table is used for substitution,
then data row is shifted in the second substitution. At last, XOR operation is performed on it.
Conclusion: The encryption has been used for the security purposes. For this, various
algorithms have been developed and tested to find the one that resists all types of attacks. The
DES algorithm is one such algorithm developed to implement security. But it is now
considered as unsecured for applications like banking. So to overcome these failures, AES
was developed. In AES, when we increase the number of rounds, the complexity of the
algorithm also increases and hence it becomes strongest in resisting attacks. For this, the
length of the key is increased as the rounds depend on the key length used. It has acceptable
speed for encryption and decryption. Therefore, it is more preferable.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Davies, J., 2011. Implementing SSL/TLS using cryptography and PKI. John Wiley and
Sons.
Bo, Y., Zhang, M. and Du, J.Q., 2016. An error‐tolerant keyword search scheme based on
public‐key encryption in secure cloud computing. Concurrency and Computation:
Practice and Experience, 28(4), pp.1083-1093.
Kumar, J. &Farik, M. 2017, "Cracking Advanced Encryption Standard-A Review",
International Journal of Scientific & Technology Research, vol. 6, no. 7, pp. 101-105.
Oukili, S. &Bri, S. 2017, "High throughput FPGA implementation of Advanced
Encryption Standard algorithm", TELKOMNIKA, vol. 15, no. 1, pp. 494
Soltani, A. &Sharifian, S. 2015, "An ultra-high throughput and fully pipelined
implementation of AES algorithm on FPGA", Microprocessors and Microsystems, vol.
39, no. 7, pp. 480-493
10
Davies, J., 2011. Implementing SSL/TLS using cryptography and PKI. John Wiley and
Sons.
Bo, Y., Zhang, M. and Du, J.Q., 2016. An error‐tolerant keyword search scheme based on
public‐key encryption in secure cloud computing. Concurrency and Computation:
Practice and Experience, 28(4), pp.1083-1093.
Kumar, J. &Farik, M. 2017, "Cracking Advanced Encryption Standard-A Review",
International Journal of Scientific & Technology Research, vol. 6, no. 7, pp. 101-105.
Oukili, S. &Bri, S. 2017, "High throughput FPGA implementation of Advanced
Encryption Standard algorithm", TELKOMNIKA, vol. 15, no. 1, pp. 494
Soltani, A. &Sharifian, S. 2015, "An ultra-high throughput and fully pipelined
implementation of AES algorithm on FPGA", Microprocessors and Microsystems, vol.
39, no. 7, pp. 480-493
10
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





