CSCI368 Network Security Assignment 2 Solution - Session 2, 2019
VerifiedAdded on 2023/01/17
|10
|1293
|28
Homework Assignment
AI Summary
This document presents a comprehensive solution to a network security assignment, addressing key aspects of cryptography and secure communication. The solution begins by analyzing a key agreement protocol, calculating the password space, and evaluating its vulnerability to offline password guessing attacks. It then delves into the Burmester-Desmedt (BD) group key exchange protocol, exploring its security implications. The assignment further examines SSL/TLS configurations, highlighting potential vulnerabilities and mitigation strategies. The solution also covers the Diffie-Hellman key exchange protocol, explaining its functionality and security weaknesses, particularly the man-in-the-middle attack, and proposes solutions like digital signatures and other protocol variations. Finally, the assignment addresses key freshness and perfect forward secrecy in key exchange protocols, referencing relevant research papers.

Question 1
a) Lower case letters = 26
upper case letters = 26
digits = 10
Total character = 26+26+10
=62
Password lenght = 6
Possible Combination=Possible Number of CharacterPassword Length
= 626
=5.680023558 x 1010
Rate of password generation = 107 / s
Time To Crack = 5.680023558 x 1010 x 10−7
=5680.0236 s
~ 94 minutes
~ 1.5778 hours
a) Lower case letters = 26
upper case letters = 26
digits = 10
Total character = 26+26+10
=62
Password lenght = 6
Possible Combination=Possible Number of CharacterPassword Length
= 626
=5.680023558 x 1010
Rate of password generation = 107 / s
Time To Crack = 5.680023558 x 1010 x 10−7
=5680.0236 s
~ 94 minutes
~ 1.5778 hours
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Let password length be N
In binary
log2(6) ~ 2 bits
Password strenght S = 16 * 2
=32bits
Password space = 232
= 4,294,967,296 passwords
Rate = 10,000,000 passwords/ s
Total Time T = 4,294,967,296 *10−6
= 429.5 s
1
b) In case of offline brute force, this protocol is very much insecure as the computational
complexity of the protocol is less hence someone with access the to encrypted text can easily
guess the password and decrypt the ciphertext
1 Ting-Yi Chang, Min-Shiang Hwang & Chou-Chen Yang, ‘Password Authenticated Key Exchange and
Protected Password Change Protocols’, in Symmetry (20738994), vol. 9, 2017, 134.
In binary
log2(6) ~ 2 bits
Password strenght S = 16 * 2
=32bits
Password space = 232
= 4,294,967,296 passwords
Rate = 10,000,000 passwords/ s
Total Time T = 4,294,967,296 *10−6
= 429.5 s
1
b) In case of offline brute force, this protocol is very much insecure as the computational
complexity of the protocol is less hence someone with access the to encrypted text can easily
guess the password and decrypt the ciphertext
1 Ting-Yi Chang, Min-Shiang Hwang & Chou-Chen Yang, ‘Password Authenticated Key Exchange and
Protected Password Change Protocols’, in Symmetry (20738994), vol. 9, 2017, 134.

Question 2
Question 3
Algorithm
GA ist:=0;
initialize P(t);
evaluate P(t);
while not terminate P(t)
dot:=t+1;
P(t):=select P(t−1);
recombine P(t);
mutate P(t);
evaluate P(t);
end whileend GA.
Question 3
Algorithm
GA ist:=0;
initialize P(t);
evaluate P(t);
while not terminate P(t)
dot:=t+1;
P(t):=select P(t−1);
recombine P(t);
mutate P(t);
evaluate P(t);
end whileend GA.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Generational Genetic Algorithm (genGA)proc Reproductive Cycle
(ga):for s=1to MAX STEPS do
plist =Select(ga.pop);
for i=1to POB SIZE/2 doCrossover(ga.Pc, p list[i], p list[i +POB
SIZE/2],ind aux.chrom);
Mutate(ga.Pm, ind aux.chrom);
ind aux.fitness =ga.Evaluate(Decode(ind aux.chrom));
Insert New Ind(pop aux, ind aux);
end forga.pop =pop aux;
[elitist}nonelitist]Collect Statistics(ga);
end forend proc Reproductive Cycle;
Question 4
SSL/TLS shows are used to confirm data transmission yet gravely organized servers may reveal
data instead of checking it. A basic strategy to test if your webpage or web application uses a
vulnerable SSL/TLS configuration is to run a robotized check using the online Acunetix
feebleness scanner, which consolidates a framework security scanner. Meanwhile, you can
similarly test for web vulnerabilities. Requesting a demo to see how you can recognize and
report precarious setups 2.
2 KA Kumari, GS Sadasivam & L Rohini, ‘An Efficient 3D Elliptic Curve Diffie–Hellman (ECDH) Based
Two-Server Password-Only Authenticated Key Exchange Protocol with Provable Security’, in IETE
Journal of Research, vol. 62, 2016, 762–773.
(ga):for s=1to MAX STEPS do
plist =Select(ga.pop);
for i=1to POB SIZE/2 doCrossover(ga.Pc, p list[i], p list[i +POB
SIZE/2],ind aux.chrom);
Mutate(ga.Pm, ind aux.chrom);
ind aux.fitness =ga.Evaluate(Decode(ind aux.chrom));
Insert New Ind(pop aux, ind aux);
end forga.pop =pop aux;
[elitist}nonelitist]Collect Statistics(ga);
end forend proc Reproductive Cycle;
Question 4
SSL/TLS shows are used to confirm data transmission yet gravely organized servers may reveal
data instead of checking it. A basic strategy to test if your webpage or web application uses a
vulnerable SSL/TLS configuration is to run a robotized check using the online Acunetix
feebleness scanner, which consolidates a framework security scanner. Meanwhile, you can
similarly test for web vulnerabilities. Requesting a demo to see how you can recognize and
report precarious setups 2.
2 KA Kumari, GS Sadasivam & L Rohini, ‘An Efficient 3D Elliptic Curve Diffie–Hellman (ECDH) Based
Two-Server Password-Only Authenticated Key Exchange Protocol with Provable Security’, in IETE
Journal of Research, vol. 62, 2016, 762–773.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

A significant part of the time, the best way to deal with secure yourself against SSL/TLS-related
ambushes is to hinder progressively prepared show shapes. This is even a standard need for
specific endeavors. For example, June 30, 2018, was the due date for devastating assistance for
SSL and early types of TLS (up to and including TLS 1.0) as demonstrated by the PCI Data
Security Standard. The Internet Engineering Task Force (IETF) released admonitions concerning
the security of SSL: RFC 6176and RFC 7568. Putting down of TLS 1.0 and 1.1 by IETF is
typical soon.
Question 5
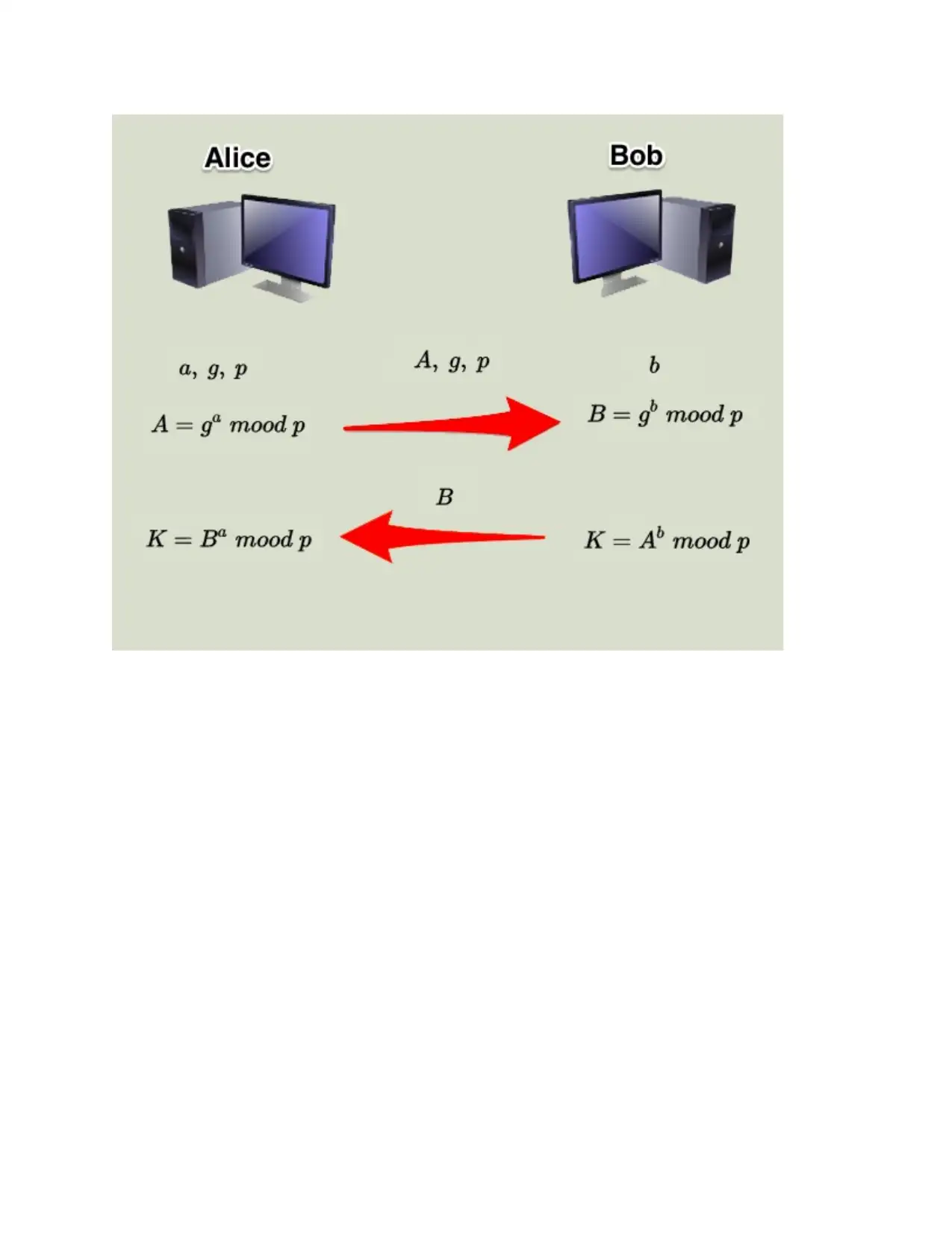
a)
the two end customers Alice and Bob, while passing on over a channel they know to be private,
generally agree on positive whole numbers p and q, with the true objective that p is a prime
number and q is a generator of p. The generator q is a number that, when raised to positive whole
number forces not as much as p, never makes a comparative result for any two such whole
numbers. The estimation of p may be broad anyway the estimation of q is pretty much nothing.
Whenever Alice and Bob have surrendered to p and q in private, they pick useful whole number
individual keys an and b, both not actually the prime-number modulus p. Neither one of the
clients reveals their very own key to anyone; ideally, they hold these numbers and don't record
them or store them wherever. Next, Alice and Bob figure open keys a* and b* subject to their
very own keys as demonstrated by the formulas
ambushes is to hinder progressively prepared show shapes. This is even a standard need for
specific endeavors. For example, June 30, 2018, was the due date for devastating assistance for
SSL and early types of TLS (up to and including TLS 1.0) as demonstrated by the PCI Data
Security Standard. The Internet Engineering Task Force (IETF) released admonitions concerning
the security of SSL: RFC 6176and RFC 7568. Putting down of TLS 1.0 and 1.1 by IETF is
typical soon.
Question 5
a)
the two end customers Alice and Bob, while passing on over a channel they know to be private,
generally agree on positive whole numbers p and q, with the true objective that p is a prime
number and q is a generator of p. The generator q is a number that, when raised to positive whole
number forces not as much as p, never makes a comparative result for any two such whole
numbers. The estimation of p may be broad anyway the estimation of q is pretty much nothing.
Whenever Alice and Bob have surrendered to p and q in private, they pick useful whole number
individual keys an and b, both not actually the prime-number modulus p. Neither one of the
clients reveals their very own key to anyone; ideally, they hold these numbers and don't record
them or store them wherever. Next, Alice and Bob figure open keys a* and b* subject to their
very own keys as demonstrated by the formulas

a* = qa mod p
b* = qb mod p
The two customers can share their open keys a* and b* over a correspondences medium idea to
be unstable, for instance, the Internet or a corporate-wide zone sort out (WAN). From these open
keys, a number x can be created by either customer dependent on their own special keys. Alice
registers x using the formula
x = (b*)a mod p
Weave registers x utilizing the equation
x = (a*)b mod p
The estimation of x winds up being equal as shown by both of the more than two conditions. In
any case, the individual keys an and b, which are essential in the estimation of x, have not been
transmitted over an open medium. Since it is a broad and obviously unpredictable number, a
potential software engineer has no chance to get of viably theorizing x, even with the help of an
earth-shattering PC to lead a considerable number of starters. The two customers can thusly, on a
fundamental level, pass on covertly over an open medium with an encryption system for their
choice using the translating key x.
b* = qb mod p
The two customers can share their open keys a* and b* over a correspondences medium idea to
be unstable, for instance, the Internet or a corporate-wide zone sort out (WAN). From these open
keys, a number x can be created by either customer dependent on their own special keys. Alice
registers x using the formula
x = (b*)a mod p
Weave registers x utilizing the equation
x = (a*)b mod p
The estimation of x winds up being equal as shown by both of the more than two conditions. In
any case, the individual keys an and b, which are essential in the estimation of x, have not been
transmitted over an open medium. Since it is a broad and obviously unpredictable number, a
potential software engineer has no chance to get of viably theorizing x, even with the help of an
earth-shattering PC to lead a considerable number of starters. The two customers can thusly, on a
fundamental level, pass on covertly over an open medium with an encryption system for their
choice using the translating key x.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

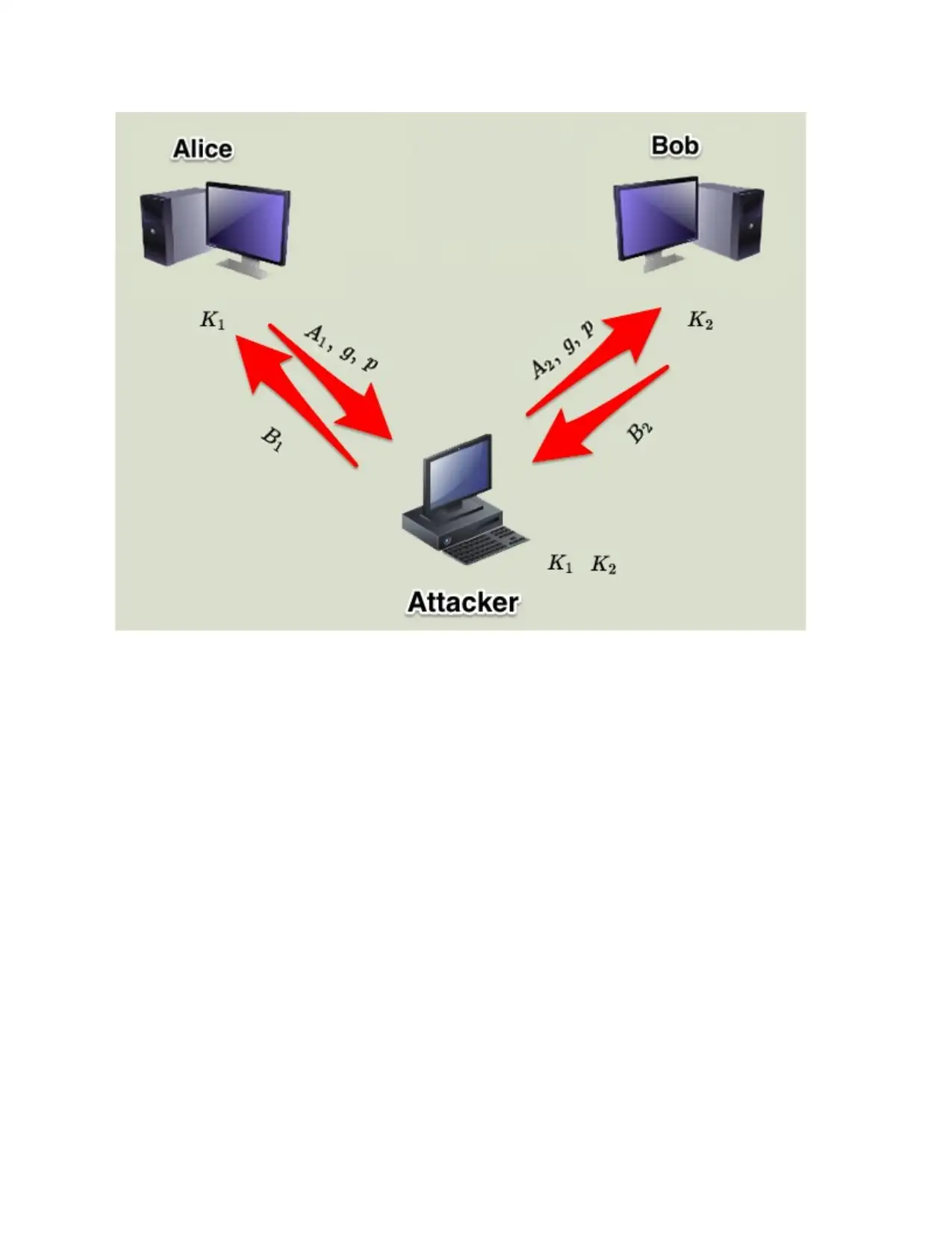
b)
The Diffie-Hellman key exchange is frail against a man-in-the-middle strike. In this attack, an
adversary Carol gets Alice's open regard and sends her very own open an impetus to Bob.
Exactly when Bob transmits his open regard, Carol substitutes it with her very own and sends it
to Alice. Song and Alice thusly surrender to one shared key and Carol and Bob agree on another
common key. After this exchange, Carol essentially unscrambles any messages passed on by
Alice or Bob, and a short time later scrutinizes and possibly modifies them before re-encoding
with the fitting key and transmitting them to the following social affair. This powerlessness is
accessible in light of the fact that Diffie-Hellman key exchange does not affirm the individuals.
Potential game plans join the use of modernized imprints and other show varieties.
c.
i. Key freshness this is achieved in using the key agreement protocol which uses counter to
know the age of keys hence can recalculate new keys when the counter expires.
ii. Perfect forward key Is achieved in Diffie Helman by the use of a random number to
generate Key like in the RSA using the key generation protocol. This protocol discards
any session keys which have expired
The Diffie-Hellman key exchange is frail against a man-in-the-middle strike. In this attack, an
adversary Carol gets Alice's open regard and sends her very own open an impetus to Bob.
Exactly when Bob transmits his open regard, Carol substitutes it with her very own and sends it
to Alice. Song and Alice thusly surrender to one shared key and Carol and Bob agree on another
common key. After this exchange, Carol essentially unscrambles any messages passed on by
Alice or Bob, and a short time later scrutinizes and possibly modifies them before re-encoding
with the fitting key and transmitting them to the following social affair. This powerlessness is
accessible in light of the fact that Diffie-Hellman key exchange does not affirm the individuals.
Potential game plans join the use of modernized imprints and other show varieties.
c.
i. Key freshness this is achieved in using the key agreement protocol which uses counter to
know the age of keys hence can recalculate new keys when the counter expires.
ii. Perfect forward key Is achieved in Diffie Helman by the use of a random number to
generate Key like in the RSA using the key generation protocol. This protocol discards
any session keys which have expired
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
Kumari, KA, GS Sadasivam, & L Rohini, ‘An Efficient 3D Elliptic Curve Diffie–Hellman
(ECDH) Based Two-Server Password-Only Authenticated Key Exchange Protocol with
Provable Security’.in IETE Journal of Research, 62, 2016, 762–773.
Ting-Yi Chang, Min-Shiang Hwang, & Chou-Chen Yang, ‘Password Authenticated Key
Exchange and Protected Password Change Protocols’.in Symmetry (20738994), 9, 2017,
134.
Kumari, KA, GS Sadasivam, & L Rohini, ‘An Efficient 3D Elliptic Curve Diffie–Hellman
(ECDH) Based Two-Server Password-Only Authenticated Key Exchange Protocol with
Provable Security’.in IETE Journal of Research, 62, 2016, 762–773.
Ting-Yi Chang, Min-Shiang Hwang, & Chou-Chen Yang, ‘Password Authenticated Key
Exchange and Protected Password Change Protocols’.in Symmetry (20738994), 9, 2017,
134.
1 out of 10
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.