IT Security Management: Comprehensive Risk Assessment Report, CSG3309
VerifiedAdded on 2023/06/14
|12
|1328
|286
Report
AI Summary
This report presents a comprehensive risk assessment conducted for an IT Security Management assignment (CSG3309), focusing on identifying, analyzing, and managing risks related to academic performance and group project completion. The assessment includes asset identification and ranking, threat identification with examples, a Threat Vulnerability Assessment (TVA) worksheet, a Risk Worksheet detailing potential risks, their severity, probability, and risk scores, and a Risk Control and Residual Risk Worksheet outlining control strategies and residual risks after implementing controls. The report covers potential threats to both individual and group performance, such as compromised intellect, deviations in quality, and failures to meet deadlines, and proposes mitigation strategies to minimize the impact of these risks. It also references relevant literature on information security management and risk assessment methodologies.

Running head: IT SECURITY MANAGEMENT
IT security management
Name of the Student
Student Number
Name of the University
Due Date
Author’s Note:
IT security management
Name of the Student
Student Number
Name of the University
Due Date
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT SECURITY MANAGEMENT
Table of Contents
Identification and Ranking of Assets.........................................................................................2
Threats........................................................................................................................................3
Threat Vulnerability Assessment Worksheet.............................................................................3
Risk Worksheet..........................................................................................................................6
Risks Control and Residual Worksheet......................................................................................8
Bibliography.............................................................................................................................10
IT SECURITY MANAGEMENT
Table of Contents
Identification and Ranking of Assets.........................................................................................2
Threats........................................................................................................................................3
Threat Vulnerability Assessment Worksheet.............................................................................3
Risk Worksheet..........................................................................................................................6
Risks Control and Residual Worksheet......................................................................................8
Bibliography.............................................................................................................................10
2
IT SECURITY MANAGEMENT
Identification and Ranking of Assets
There were various important information assets that were involved for completing as
well as exceeding expectations in my academic performance. The several information assets
that were involved for completing this assignment are given below:
i) People
ii) Data and Information
iii) Software
iv) Hardware
According to the priority of the assets, they are listed below:
Information Assets Criterion 1:
Contribution to me
Criterion 2:
Contribution to my
academic
performance
Weighted Score
Criterion Weight (1-100) 40 60
Software 1.0 1.0 100
Hardware 0.9 0.9 90
Data and Information 0.7 0.8 75
People 0.5 0.3 40
IT SECURITY MANAGEMENT
Identification and Ranking of Assets
There were various important information assets that were involved for completing as
well as exceeding expectations in my academic performance. The several information assets
that were involved for completing this assignment are given below:
i) People
ii) Data and Information
iii) Software
iv) Hardware
According to the priority of the assets, they are listed below:
Information Assets Criterion 1:
Contribution to me
Criterion 2:
Contribution to my
academic
performance
Weighted Score
Criterion Weight (1-100) 40 60
Software 1.0 1.0 100
Hardware 0.9 0.9 90
Data and Information 0.7 0.8 75
People 0.5 0.3 40
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
IT SECURITY MANAGEMENT
The software and hardware are the most important information assets that were
required towards the completion of this assignment. Next, comes the data and information. It
is ranked in three in my assets ranking. The weighted score of this particular asset is 75. This
information and data were extremely important to understand the value of the assignment and
also towards my academic performance. The final information asset is the people. It has the
weighted score of 40.
Threats
Threats are the most vulnerable risks that can occur to any person or any asset. For
this assignment, there are few threats that can occur to my group for not completing the
assignment. These threats with proper examples are given below:
Threats Examples
Compromise to intellect Piracy, copying
Deviation in quality in our group performance Failure
There are few threats for me as well if I will not be able to participate fully in the
assignment. They are as follows:
Threats Examples
Compromise to my intellect and knowledge Less marks, Lack of knowledge
Deviation in my career Failure
Threat Vulnerability Assessment Worksheet
There are few possible vulnerabilities to all the threats identified for me and my group
members. They are listed below:
IT SECURITY MANAGEMENT
The software and hardware are the most important information assets that were
required towards the completion of this assignment. Next, comes the data and information. It
is ranked in three in my assets ranking. The weighted score of this particular asset is 75. This
information and data were extremely important to understand the value of the assignment and
also towards my academic performance. The final information asset is the people. It has the
weighted score of 40.
Threats
Threats are the most vulnerable risks that can occur to any person or any asset. For
this assignment, there are few threats that can occur to my group for not completing the
assignment. These threats with proper examples are given below:
Threats Examples
Compromise to intellect Piracy, copying
Deviation in quality in our group performance Failure
There are few threats for me as well if I will not be able to participate fully in the
assignment. They are as follows:
Threats Examples
Compromise to my intellect and knowledge Less marks, Lack of knowledge
Deviation in my career Failure
Threat Vulnerability Assessment Worksheet
There are few possible vulnerabilities to all the threats identified for me and my group
members. They are listed below:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
IT SECURITY MANAGEMENT
Threats Possible Vulnerabilities
Compromise to intellect Due to the unsatisfactorily completion of the
assignment, our career would be affected.
Deviation in quality in our group performance Even if one person does not work properly, the
entire group performance would be hampered.
Compromise to my intellect and knowledge If I will not be able to participate in the
assignment completely, it would be affecting my
intellect and knowledge.
Deviation in my career When I will not be able to learn anything new,
there would a straight downfall in my career.
The Threat Vulnerability Assessment Worksheet or TVA worksheet depicts a clear
view of the priority of threats to the various assets.
Software Hardware Data and
Information
People
Compromise to intellect
Deviation in quality in our
group performance
Compromise to my
intellect and knowledge
Deviation in my career
Priority of Controls 1 2
IT SECURITY MANAGEMENT
Threats Possible Vulnerabilities
Compromise to intellect Due to the unsatisfactorily completion of the
assignment, our career would be affected.
Deviation in quality in our group performance Even if one person does not work properly, the
entire group performance would be hampered.
Compromise to my intellect and knowledge If I will not be able to participate in the
assignment completely, it would be affecting my
intellect and knowledge.
Deviation in my career When I will not be able to learn anything new,
there would a straight downfall in my career.
The Threat Vulnerability Assessment Worksheet or TVA worksheet depicts a clear
view of the priority of threats to the various assets.
Software Hardware Data and
Information
People
Compromise to intellect
Deviation in quality in our
group performance
Compromise to my
intellect and knowledge
Deviation in my career
Priority of Controls 1 2

5
IT SECURITY MANAGEMENT
IT SECURITY MANAGEMENT
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
IT SECURITY MANAGEMENT
IT SECURITY MANAGEMENT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
IT SECURITY MANAGEMENT
Risk Worksheet
List All
Activities
Your activity
name
Associated Risk(s)
Risk(s) associated with
the activity
Severity
Level of impact on
the trip and
students
Probability
The chances of
that risk
happening
Risk Score
Risk score,
found by
combining
impact and
probability on
the risk matrix
Meeting all
requirements
1. Sending wrong
deliverables.
2. Not understanding
requirements
1. Negligible
2. Negligible
1. Low
2. Low
1. Low
2. Low
Completing
within
deadline
1. Not meeting all
requirements.
2. Stuck on any
particular step
1. Critical
2. Medium
1. Low
2. Medium
1. Medium
2. High
Group
participation
1. Absence of any one
group member.
2. Reduction in
quality and
efficiency.
1. Catastrophic
2. High
1. Low
2. Critical
1. High
2.
Severity
N
E
G
L
I
G
I
B
L
E
s
m
a
l
l
/
u
n
i
m
p
o
r
t
a
n
t
C
R
I
T
I
C
A
L
s
e
r
i
o
u
s
/
i
m
p
o
r
t
a
n
t
C
A
T
A
S
T
R
O
P
H
I
C
m
a
x
i
m
u
m
i
m
p
o
r
t
a
n
c
e
;
c
o
u
l
d
r
e
s
u
l
t
i
n
IT SECURITY MANAGEMENT
Risk Worksheet
List All
Activities
Your activity
name
Associated Risk(s)
Risk(s) associated with
the activity
Severity
Level of impact on
the trip and
students
Probability
The chances of
that risk
happening
Risk Score
Risk score,
found by
combining
impact and
probability on
the risk matrix
Meeting all
requirements
1. Sending wrong
deliverables.
2. Not understanding
requirements
1. Negligible
2. Negligible
1. Low
2. Low
1. Low
2. Low
Completing
within
deadline
1. Not meeting all
requirements.
2. Stuck on any
particular step
1. Critical
2. Medium
1. Low
2. Medium
1. Medium
2. High
Group
participation
1. Absence of any one
group member.
2. Reduction in
quality and
efficiency.
1. Catastrophic
2. High
1. Low
2. Critical
1. High
2.
Severity
N
E
G
L
I
G
I
B
L
E
s
m
a
l
l
/
u
n
i
m
p
o
r
t
a
n
t
C
R
I
T
I
C
A
L
s
e
r
i
o
u
s
/
i
m
p
o
r
t
a
n
t
C
A
T
A
S
T
R
O
P
H
I
C
m
a
x
i
m
u
m
i
m
p
o
r
t
a
n
c
e
;
c
o
u
l
d
r
e
s
u
l
t
i
n
8
IT SECURITY MANAGEMENT
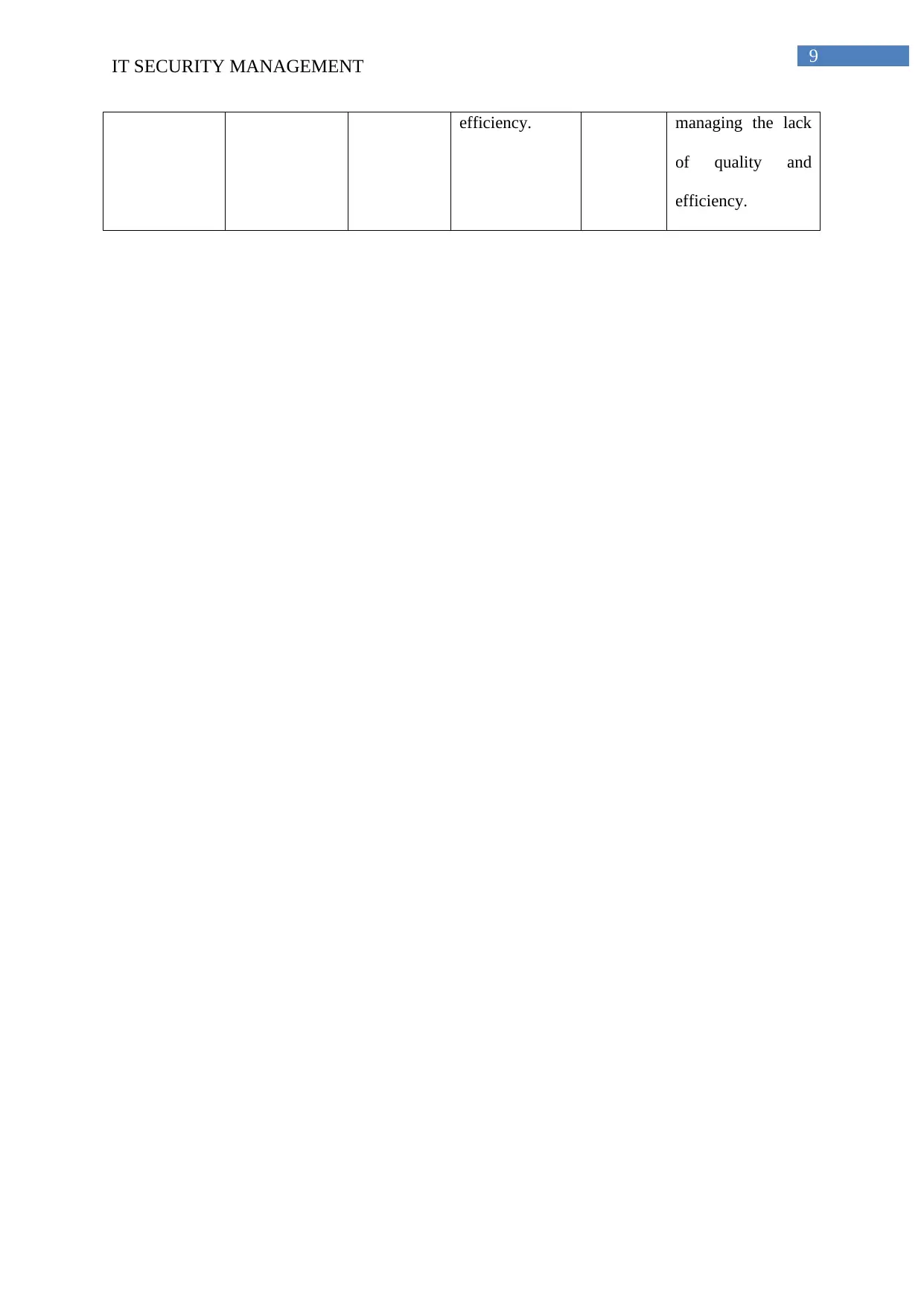
Risks Control and Residual Worksheet
Activities Identified
Risks
Initial Risk
Level
Develop
Controls
Residual
Risk
Level
Management
Strategy
1. Meeting all
requirements
1. Sending
wrong
deliverables
Low Resending the
deliverables
Critical Checking from the
supervisor and
sending new
deliverables.
2. Not
understanding
requirements.
Negligible Asking from the
supervisor or
other team
members
High Immediately clarify
from the seniors,
supervisor or team
members
2.
Completing
within
deadline
1. Not meeting
all
requirements.
Critical Asking for more
time.
High Asking more time
from the supervisor
for properly
completing it by
fulfilling all
requirements.
2. Stuck on
any particular
step
Medium Taking help
from supervisor.
Low Taking help from
supervisor or other
team members.
3. Group
Participation
1. Absence if
any one group
member.
Catastrophi
c
Contacting him
or her.
Low Trying to contact
that group member
2. Reduction in
quality and
efficiency
High Trying to make
up the loophole
in quality and
High Immediately trying
for adding another
group member for
IT SECURITY MANAGEMENT
Risks Control and Residual Worksheet
Activities Identified
Risks
Initial Risk
Level
Develop
Controls
Residual
Risk
Level
Management
Strategy
1. Meeting all
requirements
1. Sending
wrong
deliverables
Low Resending the
deliverables
Critical Checking from the
supervisor and
sending new
deliverables.
2. Not
understanding
requirements.
Negligible Asking from the
supervisor or
other team
members
High Immediately clarify
from the seniors,
supervisor or team
members
2.
Completing
within
deadline
1. Not meeting
all
requirements.
Critical Asking for more
time.
High Asking more time
from the supervisor
for properly
completing it by
fulfilling all
requirements.
2. Stuck on
any particular
step
Medium Taking help
from supervisor.
Low Taking help from
supervisor or other
team members.
3. Group
Participation
1. Absence if
any one group
member.
Catastrophi
c
Contacting him
or her.
Low Trying to contact
that group member
2. Reduction in
quality and
efficiency
High Trying to make
up the loophole
in quality and
High Immediately trying
for adding another
group member for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
IT SECURITY MANAGEMENT
efficiency. managing the lack
of quality and
efficiency.
IT SECURITY MANAGEMENT
efficiency. managing the lack
of quality and
efficiency.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
IT SECURITY MANAGEMENT
Bibliography
Alexander, D., Finch, A., & Sutton, D. (2013, June). Information security management
principles. BCS.
Covello, V. T., & Merkhoher, M. W. (2013). Risk assessment methods: approaches for
assessing health and environmental risks. Springer Science & Business Media.
Crossler, R. E., Johnston, A. C., Lowry, P. B., Hu, Q., Warkentin, M., & Baskerville, R.
(2013). Future directions for behavioral information security research. computers &
security, 32, 90-101.
Lee, S. S. (2014). Management information systems. Management, 166137(01), 02.
Li, W. (2014). Risk assessment of power systems: models, methods, and applications. John
Wiley & Sons.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines
for effective information security management. CRC Press.
Rhodes-Ousley, M. (2013). Information security: the complete reference. McGraw Hill
Education.
Sennewald, C. A., & Baillie, C. (2015). Effective security management. Butterworth-
Heinemann.
Soomro, Z. A., Shah, M. H., & Ahmed, J. (2016). Information security management needs
more holistic approach: A literature review. International Journal of Information
Management, 36(2), 215-225.
Suter II, G. W. (2016). Ecological risk assessment. CRC press.
IT SECURITY MANAGEMENT
Bibliography
Alexander, D., Finch, A., & Sutton, D. (2013, June). Information security management
principles. BCS.
Covello, V. T., & Merkhoher, M. W. (2013). Risk assessment methods: approaches for
assessing health and environmental risks. Springer Science & Business Media.
Crossler, R. E., Johnston, A. C., Lowry, P. B., Hu, Q., Warkentin, M., & Baskerville, R.
(2013). Future directions for behavioral information security research. computers &
security, 32, 90-101.
Lee, S. S. (2014). Management information systems. Management, 166137(01), 02.
Li, W. (2014). Risk assessment of power systems: models, methods, and applications. John
Wiley & Sons.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines
for effective information security management. CRC Press.
Rhodes-Ousley, M. (2013). Information security: the complete reference. McGraw Hill
Education.
Sennewald, C. A., & Baillie, C. (2015). Effective security management. Butterworth-
Heinemann.
Soomro, Z. A., Shah, M. H., & Ahmed, J. (2016). Information security management needs
more holistic approach: A literature review. International Journal of Information
Management, 36(2), 215-225.
Suter II, G. W. (2016). Ecological risk assessment. CRC press.

11
IT SECURITY MANAGEMENT
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber
security. computers & security, 38, 97-102.
IT SECURITY MANAGEMENT
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber
security. computers & security, 38, 97-102.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.