CSI5122 - Computer Security: Analysis of WannaCry and Mirai Attacks
VerifiedAdded on 2023/06/03
|8
|1304
|441
Report
AI Summary
This report provides a detailed analysis of two significant malware attacks: WannaCry ransomware and Mirai. It explores the functionality of each malware, including how WannaCry encrypts Windows files and demands ransom, and how Mirai exploits IoT devices for DDoS attacks. The report also examines real-world incidents, such as the global impact of WannaCry in 2017 and the Mirai attack on DNS providers like Dyn in 2016. It highlights the vulnerabilities exploited by these attacks and discusses the responses and mitigation strategies employed by affected organizations and individuals. The report concludes by summarizing the key differences and similarities between WannaCry and Mirai, emphasizing the importance of robust cybersecurity measures to protect against such threats. Desklib provides access to similar solved assignments and past papers for students.

Running head: MALWARE IN COMPUTER SYSTEM
Malware in computer system
Name of the student:
Name of the university:
Author note:
Malware in computer system
Name of the student:
Name of the university:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
MALWARE IN COMPUTER SYSTEM
Table of Contents
Introduction................................................................................................................................1
Discussion..................................................................................................................................1
WannaCry ransomware attack...................................................................................................1
Functionality of WannaCry....................................................................................................1
Real world incident................................................................................................................2
Mirai...........................................................................................................................................3
Functionality of Mirai............................................................................................................4
Real world incident................................................................................................................4
Summary....................................................................................................................................5
References..................................................................................................................................6
MALWARE IN COMPUTER SYSTEM
Table of Contents
Introduction................................................................................................................................1
Discussion..................................................................................................................................1
WannaCry ransomware attack...................................................................................................1
Functionality of WannaCry....................................................................................................1
Real world incident................................................................................................................2
Mirai...........................................................................................................................................3
Functionality of Mirai............................................................................................................4
Real world incident................................................................................................................4
Summary....................................................................................................................................5
References..................................................................................................................................6

2
MALWARE IN COMPUTER SYSTEM
Introduction
Malware attack is the cybercrime that performed by malicious software activities on
the user system. For this report two malware attack is selected one is WannaCry ransomware
attack and the second is Mirai attack. These two types of malware attack has different
functions and activity performed by the hacker. The main objective of cybercrime is to
demand of money from victim by the hackers. WannaCry ransomware attack has done
damage in the operating system of Windows to encrypt files and asking for payment to
resolve and decrypt system. Whereas Mirai attack was for DNS providers to disrupt major
websites such as Twitter and PayPal etc. This document will discuss about the mentioned two
attacks, which is WannaCry ransomware attack and Mirai. At first, there will be brief
description about the attack and functions of this attack. Damage faced by the industries or
company at the time of this attack and after that there will be detailed of the response from
the victims side to recover.
Discussion
WannaCry ransomware attack
This is a virus that gest spread in the operating system of windows by utilizing
vulnerability. If this software is installed in the system, it will encrypts files and then ask for
payment to resolve it or decrypt the system (Chen & Bridges, 2017). This ranosmware has two
components, one is worm module to self-propagate and second is ransom module to manage
the extrortion activities of ransom. Malware attack does not ask for any permission form the
user of the system and without informing the owner it will start its work once initialized.
MALWARE IN COMPUTER SYSTEM
Introduction
Malware attack is the cybercrime that performed by malicious software activities on
the user system. For this report two malware attack is selected one is WannaCry ransomware
attack and the second is Mirai attack. These two types of malware attack has different
functions and activity performed by the hacker. The main objective of cybercrime is to
demand of money from victim by the hackers. WannaCry ransomware attack has done
damage in the operating system of Windows to encrypt files and asking for payment to
resolve and decrypt system. Whereas Mirai attack was for DNS providers to disrupt major
websites such as Twitter and PayPal etc. This document will discuss about the mentioned two
attacks, which is WannaCry ransomware attack and Mirai. At first, there will be brief
description about the attack and functions of this attack. Damage faced by the industries or
company at the time of this attack and after that there will be detailed of the response from
the victims side to recover.
Discussion
WannaCry ransomware attack
This is a virus that gest spread in the operating system of windows by utilizing
vulnerability. If this software is installed in the system, it will encrypts files and then ask for
payment to resolve it or decrypt the system (Chen & Bridges, 2017). This ranosmware has two
components, one is worm module to self-propagate and second is ransom module to manage
the extrortion activities of ransom. Malware attack does not ask for any permission form the
user of the system and without informing the owner it will start its work once initialized.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
MALWARE IN COMPUTER SYSTEM
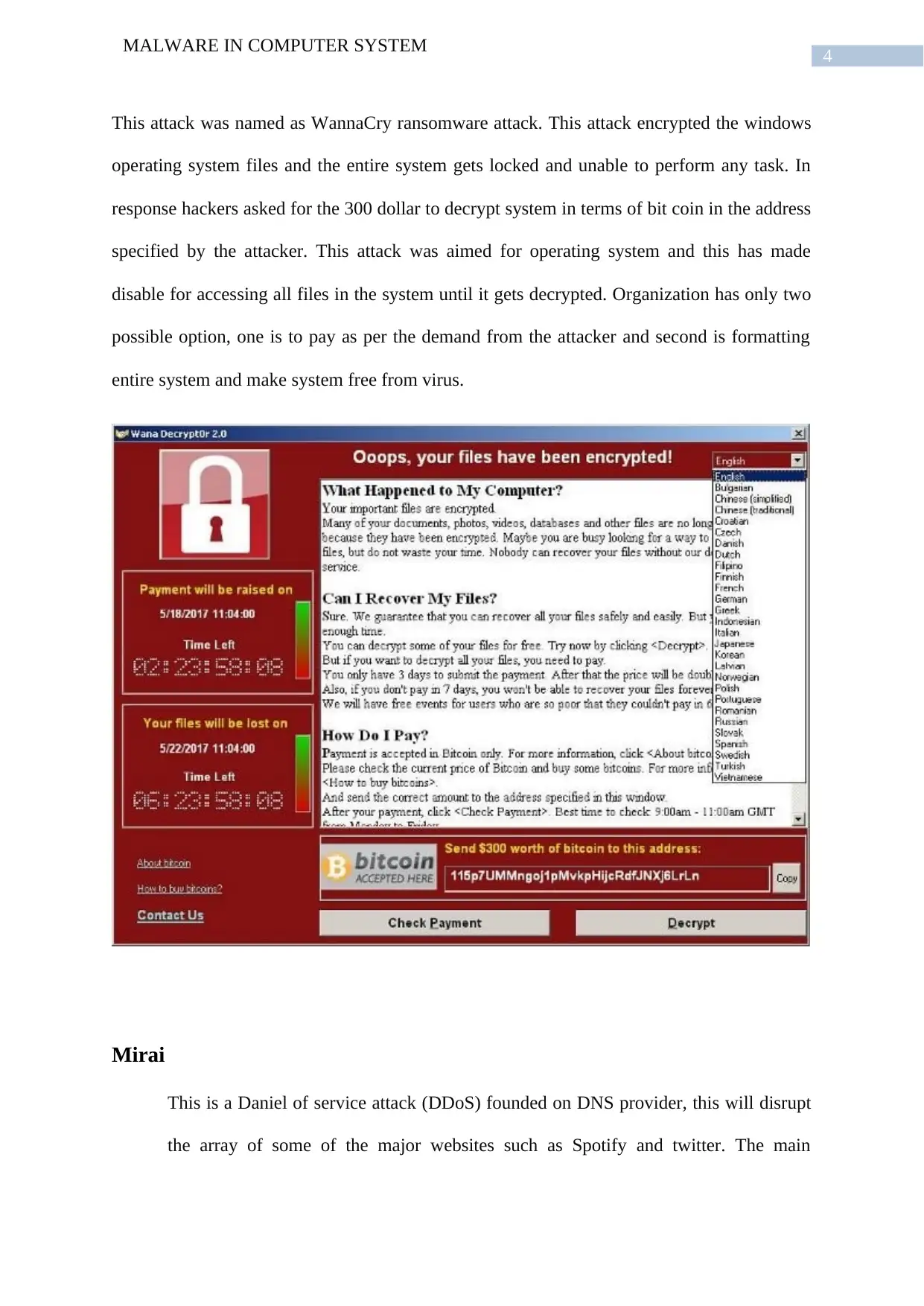
Functionality of WannaCry
Initially, this attack will at first inject an unknown vector. It will start in very small
and after some time it will expand this worm to completely attack on the system files. This
WannaCry is having two parts name as, worm module and second is ransomware module.
This attack will encrypt windows files and lock the entire system and there will be demand
for money to return system to the admin of the system. This attack has virus named as Trojan.
Ransomware attack will show an module display to give instruction to the victim and
information regarding payment and the detail of the situation. This attack will show files
encrypted and formatted as extension of .WCRY. In the message section it will contain
everything which is needed such as what happened with the system, how this system can be
recovered and payment details.
Real world incident
In 12th of May 2017, this attack was discovered. This attack has made system unable
of accessing any files in the victim’s syste.
MALWARE IN COMPUTER SYSTEM
Functionality of WannaCry
Initially, this attack will at first inject an unknown vector. It will start in very small
and after some time it will expand this worm to completely attack on the system files. This
WannaCry is having two parts name as, worm module and second is ransomware module.
This attack will encrypt windows files and lock the entire system and there will be demand
for money to return system to the admin of the system. This attack has virus named as Trojan.
Ransomware attack will show an module display to give instruction to the victim and
information regarding payment and the detail of the situation. This attack will show files
encrypted and formatted as extension of .WCRY. In the message section it will contain
everything which is needed such as what happened with the system, how this system can be
recovered and payment details.
Real world incident
In 12th of May 2017, this attack was discovered. This attack has made system unable
of accessing any files in the victim’s syste.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
MALWARE IN COMPUTER SYSTEM
This attack was named as WannaCry ransomware attack. This attack encrypted the windows
operating system files and the entire system gets locked and unable to perform any task. In
response hackers asked for the 300 dollar to decrypt system in terms of bit coin in the address
specified by the attacker. This attack was aimed for operating system and this has made
disable for accessing all files in the system until it gets decrypted. Organization has only two
possible option, one is to pay as per the demand from the attacker and second is formatting
entire system and make system free from virus.
Mirai
This is a Daniel of service attack (DDoS) founded on DNS provider, this will disrupt
the array of some of the major websites such as Spotify and twitter. The main
MALWARE IN COMPUTER SYSTEM
This attack was named as WannaCry ransomware attack. This attack encrypted the windows
operating system files and the entire system gets locked and unable to perform any task. In
response hackers asked for the 300 dollar to decrypt system in terms of bit coin in the address
specified by the attacker. This attack was aimed for operating system and this has made
disable for accessing all files in the system until it gets decrypted. Organization has only two
possible option, one is to pay as per the demand from the attacker and second is formatting
entire system and make system free from virus.
Mirai
This is a Daniel of service attack (DDoS) founded on DNS provider, this will disrupt
the array of some of the major websites such as Spotify and twitter. The main

5
MALWARE IN COMPUTER SYSTEM
interesting thing for this attack is that, it is mostly founded in Internet of things (IoT)
botnet, which is called as Mirai.
Functionality of Mirai
This Mirai attack works by utilizing low-level security on IOT devices. This attack
goes on by scanning devices of IOT, which is easily discoverable in the internet, which has
default factory settings. As per the Security Response blog of Norton security it has been
found that many IOT devices remain unchanged with default user name and password ("IoT
devices being increasingly used for DDoS attacks", 2019). This malware attack infects devices
along with malware to report central control server as forced by this malware.
Real world incident
This attack first came on 20 September 2016. In Kerbs attack was attacked as Mirai
attack on French company that hosts OVH peaked at 1Tbps. Mirai attack has made many
IOT devices user id and password attacked and losses control over it. This attack has infected
devices such as DVRs, CCTV, routers and others that has smart internet connection. Main
target is webcams to exploit Dyn attack, where as the CCTV cameras are being exploited for
OVH attack. This attack has made security very much weaker as having access on CCTV
cameras made attackers capable of managing about the situation. Access of device user id
and password is also dangerous for many aspects. From the analysis it is found that for every
2 minutes IoT devices are scanned and as consequences vulnerable devices that has default
user id and password may get compromised when going online in a minute. As per the report,
it has been found that 62 list of user id and password Symantec has found. There is no
specific action of this attack, in response system needs certain changes such as changing user
id and password and need to formatted or restart device completely to remove infected
viruses form the system.
MALWARE IN COMPUTER SYSTEM
interesting thing for this attack is that, it is mostly founded in Internet of things (IoT)
botnet, which is called as Mirai.
Functionality of Mirai
This Mirai attack works by utilizing low-level security on IOT devices. This attack
goes on by scanning devices of IOT, which is easily discoverable in the internet, which has
default factory settings. As per the Security Response blog of Norton security it has been
found that many IOT devices remain unchanged with default user name and password ("IoT
devices being increasingly used for DDoS attacks", 2019). This malware attack infects devices
along with malware to report central control server as forced by this malware.
Real world incident
This attack first came on 20 September 2016. In Kerbs attack was attacked as Mirai
attack on French company that hosts OVH peaked at 1Tbps. Mirai attack has made many
IOT devices user id and password attacked and losses control over it. This attack has infected
devices such as DVRs, CCTV, routers and others that has smart internet connection. Main
target is webcams to exploit Dyn attack, where as the CCTV cameras are being exploited for
OVH attack. This attack has made security very much weaker as having access on CCTV
cameras made attackers capable of managing about the situation. Access of device user id
and password is also dangerous for many aspects. From the analysis it is found that for every
2 minutes IoT devices are scanned and as consequences vulnerable devices that has default
user id and password may get compromised when going online in a minute. As per the report,
it has been found that 62 list of user id and password Symantec has found. There is no
specific action of this attack, in response system needs certain changes such as changing user
id and password and need to formatted or restart device completely to remove infected
viruses form the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
MALWARE IN COMPUTER SYSTEM
Summary
This paper has discussed of Malware attack in computer system. This paper has taken
two major attack for malware, one is WannaCry ransomware attack which is first come to
know in 2017 and second is Mirai that was first came to known in 2016. Both of this attack
were one of major cyber-attack in the year of 2016 to 2017. Mainly there are two sections of
this paper is discussed first is functionality of the attack and its effect and the second is real
life event of this cybercrime attack of malware. WannCry ransomware attack mainly target
for windows operating system where as Mirai considered as DDoS attack that look for IoT
devices to make system user id and password stolen and making it vulnerable. In this paper
there is detailed about the situation of this two attack and the date when this attack took place.
Lastly this report has also pictures of this attacking showing graphical that how it looks.
MALWARE IN COMPUTER SYSTEM
Summary
This paper has discussed of Malware attack in computer system. This paper has taken
two major attack for malware, one is WannaCry ransomware attack which is first come to
know in 2017 and second is Mirai that was first came to known in 2016. Both of this attack
were one of major cyber-attack in the year of 2016 to 2017. Mainly there are two sections of
this paper is discussed first is functionality of the attack and its effect and the second is real
life event of this cybercrime attack of malware. WannCry ransomware attack mainly target
for windows operating system where as Mirai considered as DDoS attack that look for IoT
devices to make system user id and password stolen and making it vulnerable. In this paper
there is detailed about the situation of this two attack and the date when this attack took place.
Lastly this report has also pictures of this attacking showing graphical that how it looks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
MALWARE IN COMPUTER SYSTEM
References
IoT devices being increasingly used for DDoS attacks. (2019). Retrieved from
https://www.symantec.com/connect/blogs/iot-devices-being-increasingly-used-ddos-
attacks
Chen, Q., & Bridges, R. A. (2017, December). Automated behavioral analysis of malware: A
case study of wannacry ransomware. In 2017 16th IEEE International Conference on
Machine Learning and Applications (ICMLA) (pp. 454-460). IEEE.
MALWARE IN COMPUTER SYSTEM
References
IoT devices being increasingly used for DDoS attacks. (2019). Retrieved from
https://www.symantec.com/connect/blogs/iot-devices-being-increasingly-used-ddos-
attacks
Chen, Q., & Bridges, R. A. (2017, December). Automated behavioral analysis of malware: A
case study of wannacry ransomware. In 2017 16th IEEE International Conference on
Machine Learning and Applications (ICMLA) (pp. 454-460). IEEE.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





