Analysis of Current Trends in Networking Technologies and Applications
VerifiedAdded on 2021/01/02
|20
|5496
|164
Report
AI Summary
This report provides a comprehensive overview of current trends in networking, comparing wired and wireless broadband technologies across performance, deployment, challenges, and speed. It delves into emerging technologies like Cognitive Radio (CR) and Unlicensed Mobile Access (UMA), analyzing their functional architecture, relative benefits, and current deployment status. The report also examines the role of cryptography in securing networks and explores next-generation applications, specifically IPTV, including their specific protocols and applications. The analysis covers the benefits of wired technology like speed, cloud access, reliability, signal strength, and bandwidth. For wireless technology, it discusses network security and mobility. The comparison of wired and wireless technologies includes their performance, speed, and deployment challenges, alongside discussions on specific examples of each technology type. The report also provides recommendations for internet service providers based on the different applications of mobile access and cognitive radio.

Current trends in networking
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................3
TASKS.............................................................................................................................................3
1) Comparison between the wired broad technology and wireless broadband with respect to
performance, deployment, challenges and speed. .................................................................3
2) Evaluate the emerging technology such as the Cognitive Radio (CR) and Unlicensed
Mobile Access (UMA) / functional architecture and their relative benefits and current
deployment status. .................................................................................................................7
3) Cryptography in securing Networks................................................................................12
4) Next Generation network Application.............................................................................14
CONCLUSION..............................................................................................................................16
REFERENCES..............................................................................................................................17
INTRODUCTION...........................................................................................................................3
TASKS.............................................................................................................................................3
1) Comparison between the wired broad technology and wireless broadband with respect to
performance, deployment, challenges and speed. .................................................................3
2) Evaluate the emerging technology such as the Cognitive Radio (CR) and Unlicensed
Mobile Access (UMA) / functional architecture and their relative benefits and current
deployment status. .................................................................................................................7
3) Cryptography in securing Networks................................................................................12
4) Next Generation network Application.............................................................................14
CONCLUSION..............................................................................................................................16
REFERENCES..............................................................................................................................17

INTRODUCTION
Wireless and wired broadband technology are the important techniques that help for
allowing for used to communicate with the help of cables and electromagnetic waves. This report
will discuss about the technologies with respects to their speed, challenges, performance and
deployment etc. there are benefits that help for managing the enterprises operations and function
in proper manner. This assignment will describe the emerging technology such as unlicensed
mobile access and cognitive radio that help for maintain their architecture and relative
advantages related to the deployment status. It will recommend to the internet service provider
on the different applications of mobile access and cognitive radio. Furthermore, This report will
discuss about the role that played through cryptography method for securing the network for
future development. At last, This assignment will describe the next generation application IPTV
and also should describe their specific protocols and application.
TASKS
1) Comparison between the wired broad technology and wireless broadband with respect to
performance, deployment, challenges and speed.
Wired Broadband technology is based on the physical connection to establish the
connection with the help of cables at workplace, homes etc. this technique will use the traditional
method to transfer the signals from one device to another by using cables. This technology is
mainly used the Direct subscriber line and their speed depend on the distance from business to
the broad band equipment. DSL is used the tradition telephone copper wires for signal
transmissions (Aldana, Maag and Zaïdi, 2018).
Wireless broadband technology allows for transmitting the signals without using any
wires. Many entities are used this technology for the purpose of communication over the long
distance. This technology is applicable the electromagnetic waves that help for providing the
messages to their destination.
Wireless and wired broadband technology are the important techniques that help for
allowing for used to communicate with the help of cables and electromagnetic waves. This report
will discuss about the technologies with respects to their speed, challenges, performance and
deployment etc. there are benefits that help for managing the enterprises operations and function
in proper manner. This assignment will describe the emerging technology such as unlicensed
mobile access and cognitive radio that help for maintain their architecture and relative
advantages related to the deployment status. It will recommend to the internet service provider
on the different applications of mobile access and cognitive radio. Furthermore, This report will
discuss about the role that played through cryptography method for securing the network for
future development. At last, This assignment will describe the next generation application IPTV
and also should describe their specific protocols and application.
TASKS
1) Comparison between the wired broad technology and wireless broadband with respect to
performance, deployment, challenges and speed.
Wired Broadband technology is based on the physical connection to establish the
connection with the help of cables at workplace, homes etc. this technique will use the traditional
method to transfer the signals from one device to another by using cables. This technology is
mainly used the Direct subscriber line and their speed depend on the distance from business to
the broad band equipment. DSL is used the tradition telephone copper wires for signal
transmissions (Aldana, Maag and Zaïdi, 2018).
Wireless broadband technology allows for transmitting the signals without using any
wires. Many entities are used this technology for the purpose of communication over the long
distance. This technology is applicable the electromagnetic waves that help for providing the
messages to their destination.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
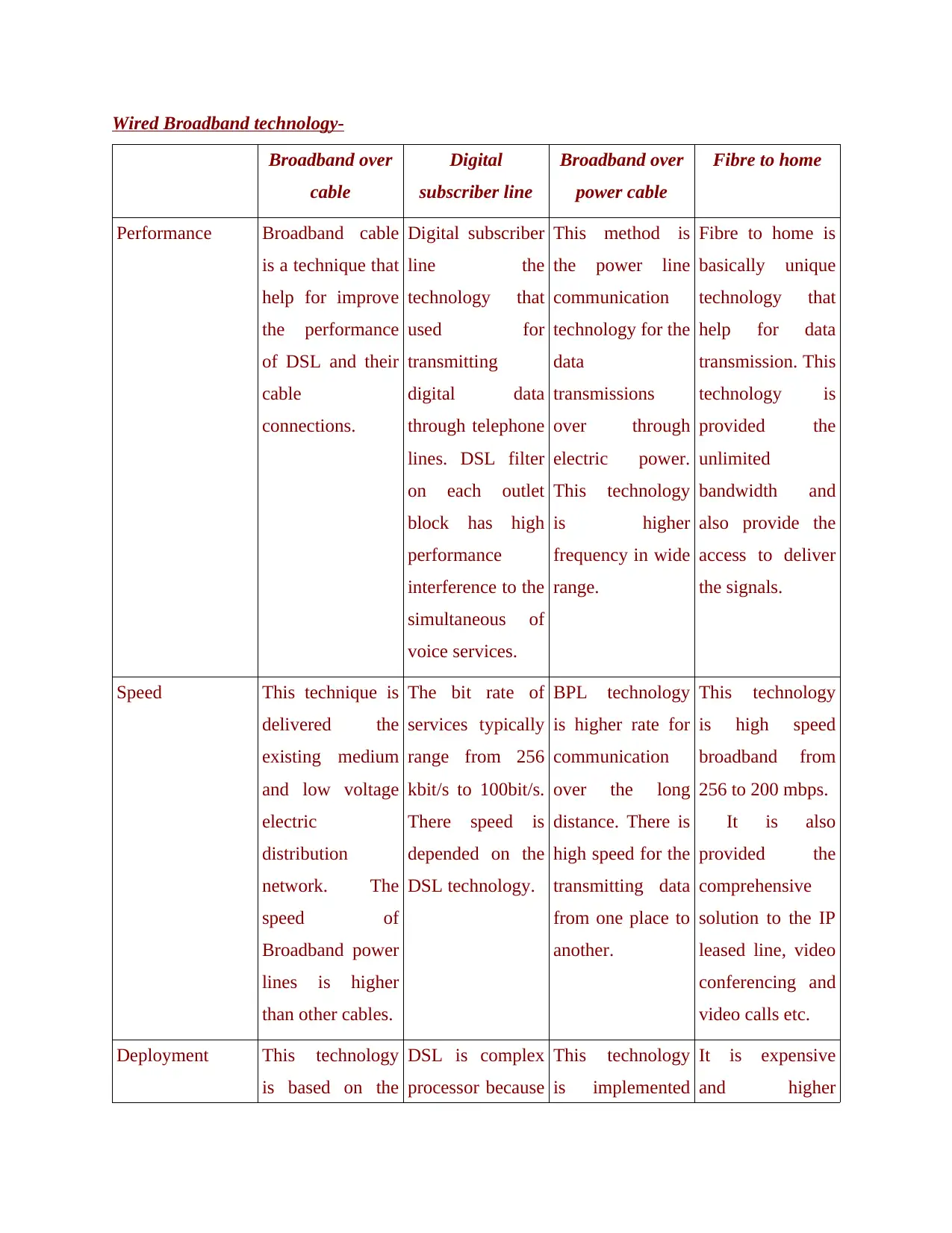
Wired Broadband technology-
Broadband over
cable
Digital
subscriber line
Broadband over
power cable
Fibre to home
Performance Broadband cable
is a technique that
help for improve
the performance
of DSL and their
cable
connections.
Digital subscriber
line the
technology that
used for
transmitting
digital data
through telephone
lines. DSL filter
on each outlet
block has high
performance
interference to the
simultaneous of
voice services.
This method is
the power line
communication
technology for the
data
transmissions
over through
electric power.
This technology
is higher
frequency in wide
range.
Fibre to home is
basically unique
technology that
help for data
transmission. This
technology is
provided the
unlimited
bandwidth and
also provide the
access to deliver
the signals.
Speed This technique is
delivered the
existing medium
and low voltage
electric
distribution
network. The
speed of
Broadband power
lines is higher
than other cables.
The bit rate of
services typically
range from 256
kbit/s to 100bit/s.
There speed is
depended on the
DSL technology.
BPL technology
is higher rate for
communication
over the long
distance. There is
high speed for the
transmitting data
from one place to
another.
This technology
is high speed
broadband from
256 to 200 mbps.
It is also
provided the
comprehensive
solution to the IP
leased line, video
conferencing and
video calls etc.
Deployment This technology
is based on the
DSL is complex
processor because
This technology
is implemented
It is expensive
and higher
Broadband over
cable
Digital
subscriber line
Broadband over
power cable
Fibre to home
Performance Broadband cable
is a technique that
help for improve
the performance
of DSL and their
cable
connections.
Digital subscriber
line the
technology that
used for
transmitting
digital data
through telephone
lines. DSL filter
on each outlet
block has high
performance
interference to the
simultaneous of
voice services.
This method is
the power line
communication
technology for the
data
transmissions
over through
electric power.
This technology
is higher
frequency in wide
range.
Fibre to home is
basically unique
technology that
help for data
transmission. This
technology is
provided the
unlimited
bandwidth and
also provide the
access to deliver
the signals.
Speed This technique is
delivered the
existing medium
and low voltage
electric
distribution
network. The
speed of
Broadband power
lines is higher
than other cables.
The bit rate of
services typically
range from 256
kbit/s to 100bit/s.
There speed is
depended on the
DSL technology.
BPL technology
is higher rate for
communication
over the long
distance. There is
high speed for the
transmitting data
from one place to
another.
This technology
is high speed
broadband from
256 to 200 mbps.
It is also
provided the
comprehensive
solution to the IP
leased line, video
conferencing and
video calls etc.
Deployment This technology
is based on the
DSL is complex
processor because
This technology
is implemented
It is expensive
and higher
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
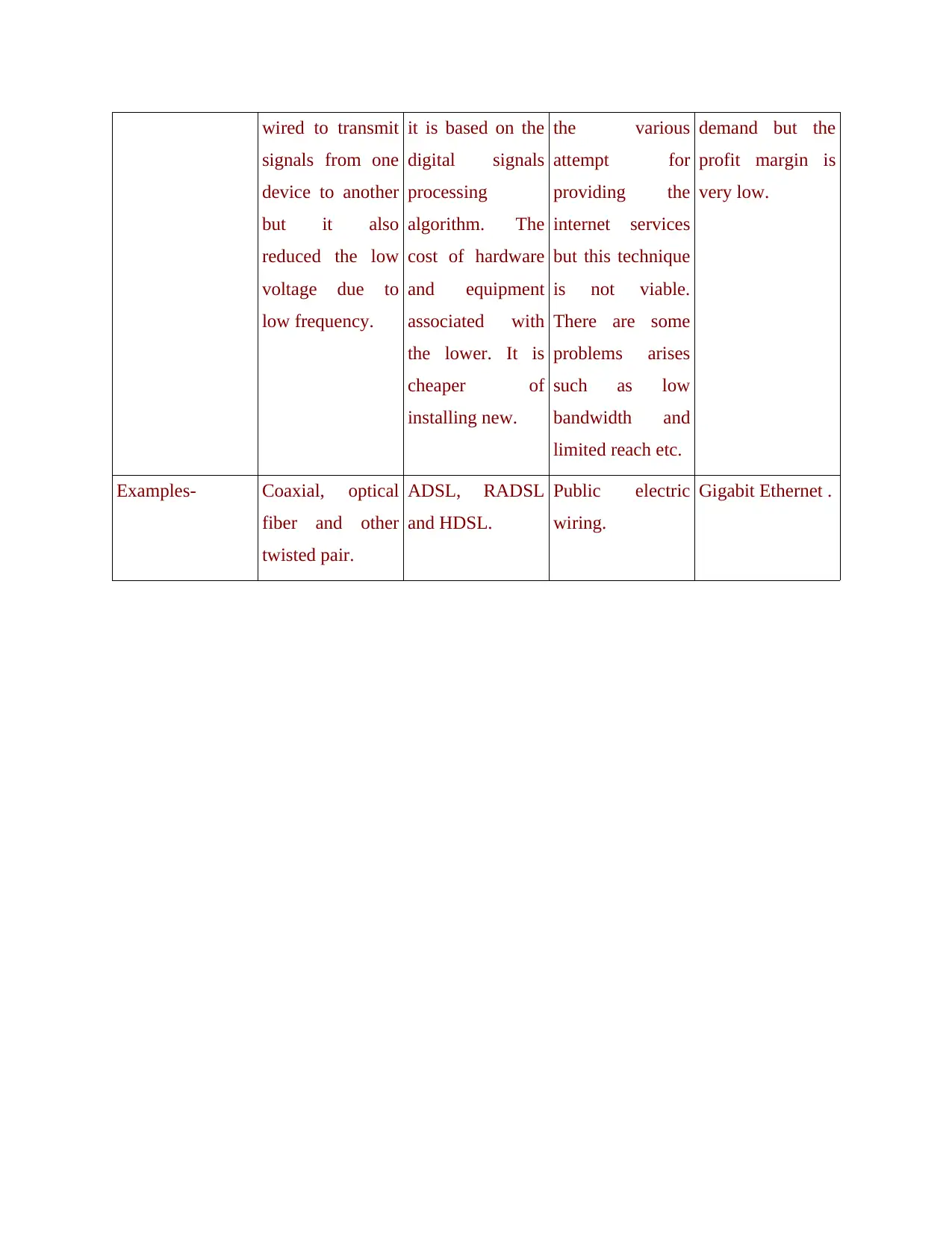
wired to transmit
signals from one
device to another
but it also
reduced the low
voltage due to
low frequency.
it is based on the
digital signals
processing
algorithm. The
cost of hardware
and equipment
associated with
the lower. It is
cheaper of
installing new.
the various
attempt for
providing the
internet services
but this technique
is not viable.
There are some
problems arises
such as low
bandwidth and
limited reach etc.
demand but the
profit margin is
very low.
Examples- Coaxial, optical
fiber and other
twisted pair.
ADSL, RADSL
and HDSL.
Public electric
wiring.
Gigabit Ethernet .
signals from one
device to another
but it also
reduced the low
voltage due to
low frequency.
it is based on the
digital signals
processing
algorithm. The
cost of hardware
and equipment
associated with
the lower. It is
cheaper of
installing new.
the various
attempt for
providing the
internet services
but this technique
is not viable.
There are some
problems arises
such as low
bandwidth and
limited reach etc.
demand but the
profit margin is
very low.
Examples- Coaxial, optical
fiber and other
twisted pair.
ADSL, RADSL
and HDSL.
Public electric
wiring.
Gigabit Ethernet .
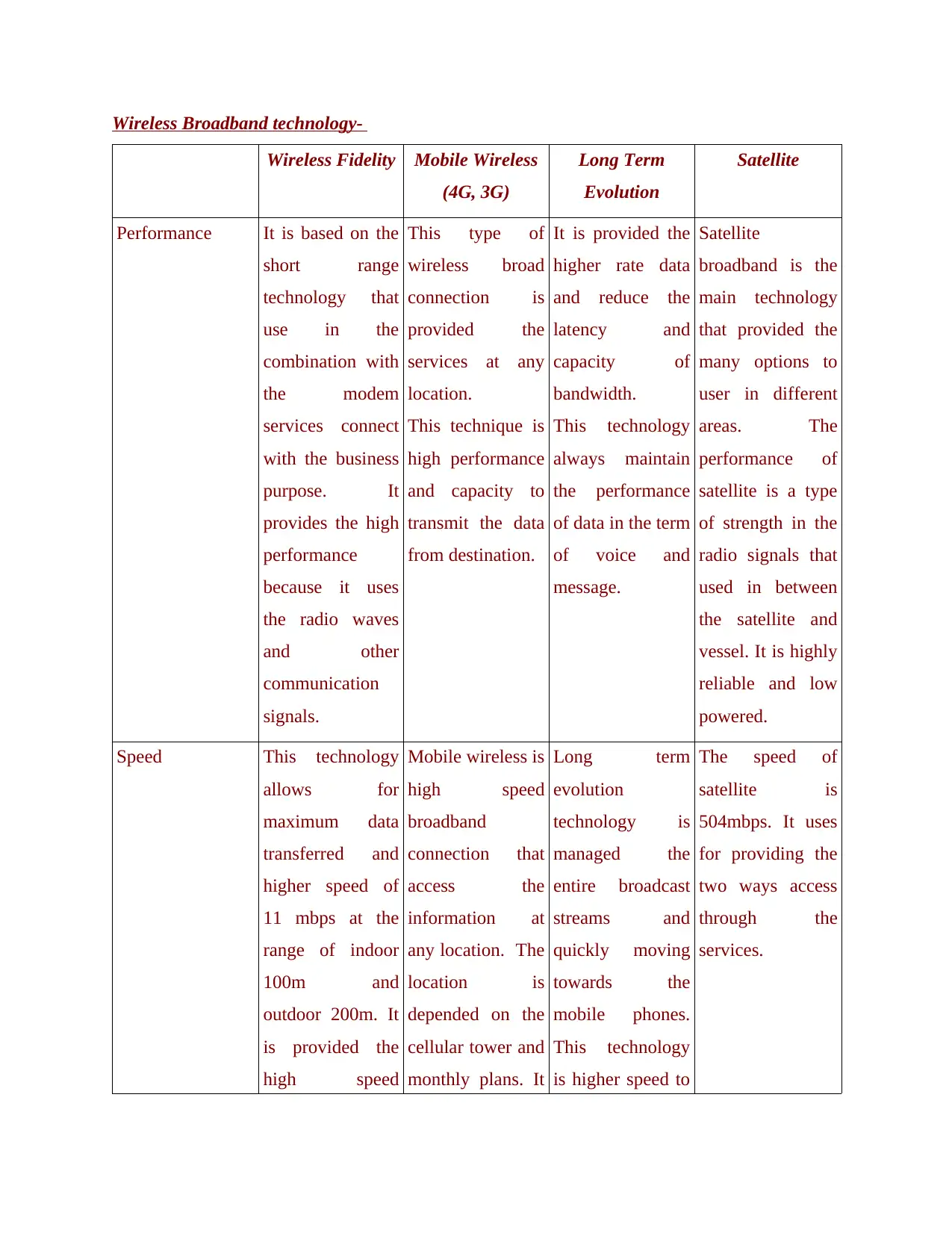
Wireless Broadband technology-
Wireless Fidelity Mobile Wireless
(4G, 3G)
Long Term
Evolution
Satellite
Performance It is based on the
short range
technology that
use in the
combination with
the modem
services connect
with the business
purpose. It
provides the high
performance
because it uses
the radio waves
and other
communication
signals.
This type of
wireless broad
connection is
provided the
services at any
location.
This technique is
high performance
and capacity to
transmit the data
from destination.
It is provided the
higher rate data
and reduce the
latency and
capacity of
bandwidth.
This technology
always maintain
the performance
of data in the term
of voice and
message.
Satellite
broadband is the
main technology
that provided the
many options to
user in different
areas. The
performance of
satellite is a type
of strength in the
radio signals that
used in between
the satellite and
vessel. It is highly
reliable and low
powered.
Speed This technology
allows for
maximum data
transferred and
higher speed of
11 mbps at the
range of indoor
100m and
outdoor 200m. It
is provided the
high speed
Mobile wireless is
high speed
broadband
connection that
access the
information at
any location. The
location is
depended on the
cellular tower and
monthly plans. It
Long term
evolution
technology is
managed the
entire broadcast
streams and
quickly moving
towards the
mobile phones.
This technology
is higher speed to
The speed of
satellite is
504mbps. It uses
for providing the
two ways access
through the
services.
Wireless Fidelity Mobile Wireless
(4G, 3G)
Long Term
Evolution
Satellite
Performance It is based on the
short range
technology that
use in the
combination with
the modem
services connect
with the business
purpose. It
provides the high
performance
because it uses
the radio waves
and other
communication
signals.
This type of
wireless broad
connection is
provided the
services at any
location.
This technique is
high performance
and capacity to
transmit the data
from destination.
It is provided the
higher rate data
and reduce the
latency and
capacity of
bandwidth.
This technology
always maintain
the performance
of data in the term
of voice and
message.
Satellite
broadband is the
main technology
that provided the
many options to
user in different
areas. The
performance of
satellite is a type
of strength in the
radio signals that
used in between
the satellite and
vessel. It is highly
reliable and low
powered.
Speed This technology
allows for
maximum data
transferred and
higher speed of
11 mbps at the
range of indoor
100m and
outdoor 200m. It
is provided the
high speed
Mobile wireless is
high speed
broadband
connection that
access the
information at
any location. The
location is
depended on the
cellular tower and
monthly plans. It
Long term
evolution
technology is
managed the
entire broadcast
streams and
quickly moving
towards the
mobile phones.
This technology
is higher speed to
The speed of
satellite is
504mbps. It uses
for providing the
two ways access
through the
services.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
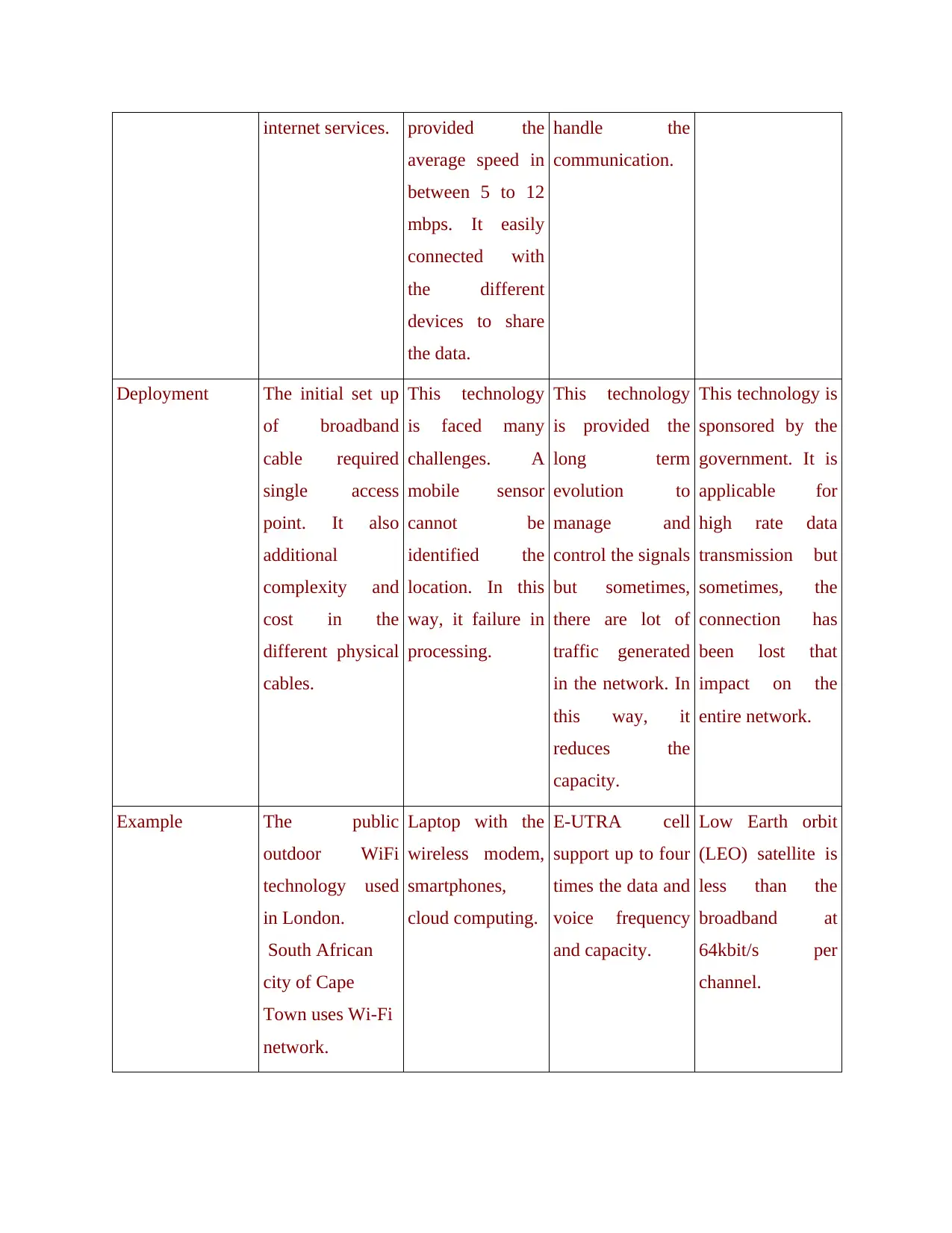
internet services. provided the
average speed in
between 5 to 12
mbps. It easily
connected with
the different
devices to share
the data.
handle the
communication.
Deployment The initial set up
of broadband
cable required
single access
point. It also
additional
complexity and
cost in the
different physical
cables.
This technology
is faced many
challenges. A
mobile sensor
cannot be
identified the
location. In this
way, it failure in
processing.
This technology
is provided the
long term
evolution to
manage and
control the signals
but sometimes,
there are lot of
traffic generated
in the network. In
this way, it
reduces the
capacity.
This technology is
sponsored by the
government. It is
applicable for
high rate data
transmission but
sometimes, the
connection has
been lost that
impact on the
entire network.
Example The public
outdoor WiFi
technology used
in London.
South African
city of Cape
Town uses Wi-Fi
network.
Laptop with the
wireless modem,
smartphones,
cloud computing.
E-UTRA cell
support up to four
times the data and
voice frequency
and capacity.
Low Earth orbit
(LEO) satellite is
less than the
broadband at
64kbit/s per
channel.
average speed in
between 5 to 12
mbps. It easily
connected with
the different
devices to share
the data.
handle the
communication.
Deployment The initial set up
of broadband
cable required
single access
point. It also
additional
complexity and
cost in the
different physical
cables.
This technology
is faced many
challenges. A
mobile sensor
cannot be
identified the
location. In this
way, it failure in
processing.
This technology
is provided the
long term
evolution to
manage and
control the signals
but sometimes,
there are lot of
traffic generated
in the network. In
this way, it
reduces the
capacity.
This technology is
sponsored by the
government. It is
applicable for
high rate data
transmission but
sometimes, the
connection has
been lost that
impact on the
entire network.
Example The public
outdoor WiFi
technology used
in London.
South African
city of Cape
Town uses Wi-Fi
network.
Laptop with the
wireless modem,
smartphones,
cloud computing.
E-UTRA cell
support up to four
times the data and
voice frequency
and capacity.
Low Earth orbit
(LEO) satellite is
less than the
broadband at
64kbit/s per
channel.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
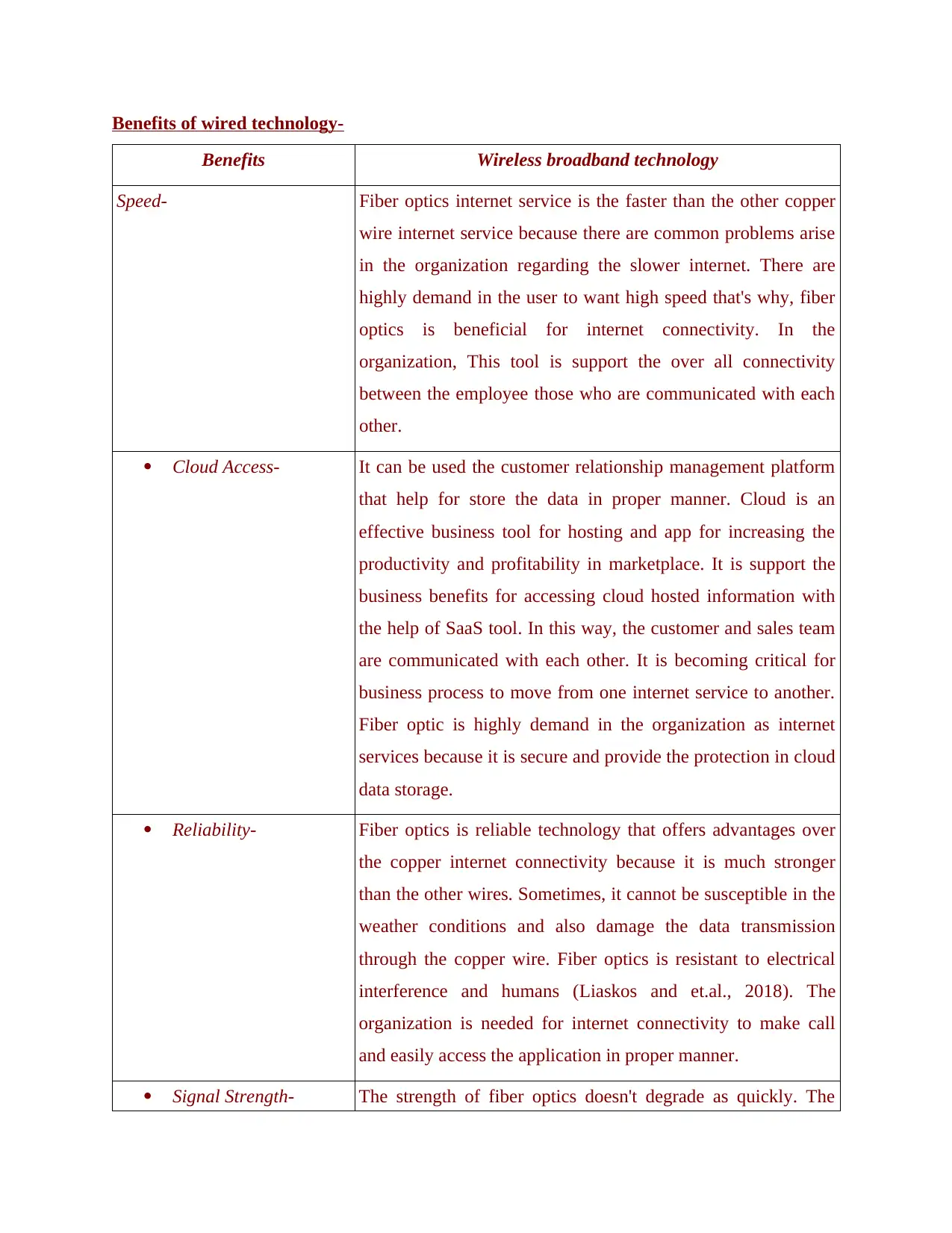
Benefits of wired technology-
Benefits Wireless broadband technology
Speed- Fiber optics internet service is the faster than the other copper
wire internet service because there are common problems arise
in the organization regarding the slower internet. There are
highly demand in the user to want high speed that's why, fiber
optics is beneficial for internet connectivity. In the
organization, This tool is support the over all connectivity
between the employee those who are communicated with each
other.
Cloud Access- It can be used the customer relationship management platform
that help for store the data in proper manner. Cloud is an
effective business tool for hosting and app for increasing the
productivity and profitability in marketplace. It is support the
business benefits for accessing cloud hosted information with
the help of SaaS tool. In this way, the customer and sales team
are communicated with each other. It is becoming critical for
business process to move from one internet service to another.
Fiber optic is highly demand in the organization as internet
services because it is secure and provide the protection in cloud
data storage.
Reliability- Fiber optics is reliable technology that offers advantages over
the copper internet connectivity because it is much stronger
than the other wires. Sometimes, it cannot be susceptible in the
weather conditions and also damage the data transmission
through the copper wire. Fiber optics is resistant to electrical
interference and humans (Liaskos and et.al., 2018). The
organization is needed for internet connectivity to make call
and easily access the application in proper manner.
Signal Strength- The strength of fiber optics doesn't degrade as quickly. The
Benefits Wireless broadband technology
Speed- Fiber optics internet service is the faster than the other copper
wire internet service because there are common problems arise
in the organization regarding the slower internet. There are
highly demand in the user to want high speed that's why, fiber
optics is beneficial for internet connectivity. In the
organization, This tool is support the over all connectivity
between the employee those who are communicated with each
other.
Cloud Access- It can be used the customer relationship management platform
that help for store the data in proper manner. Cloud is an
effective business tool for hosting and app for increasing the
productivity and profitability in marketplace. It is support the
business benefits for accessing cloud hosted information with
the help of SaaS tool. In this way, the customer and sales team
are communicated with each other. It is becoming critical for
business process to move from one internet service to another.
Fiber optic is highly demand in the organization as internet
services because it is secure and provide the protection in cloud
data storage.
Reliability- Fiber optics is reliable technology that offers advantages over
the copper internet connectivity because it is much stronger
than the other wires. Sometimes, it cannot be susceptible in the
weather conditions and also damage the data transmission
through the copper wire. Fiber optics is resistant to electrical
interference and humans (Liaskos and et.al., 2018). The
organization is needed for internet connectivity to make call
and easily access the application in proper manner.
Signal Strength- The strength of fiber optics doesn't degrade as quickly. The
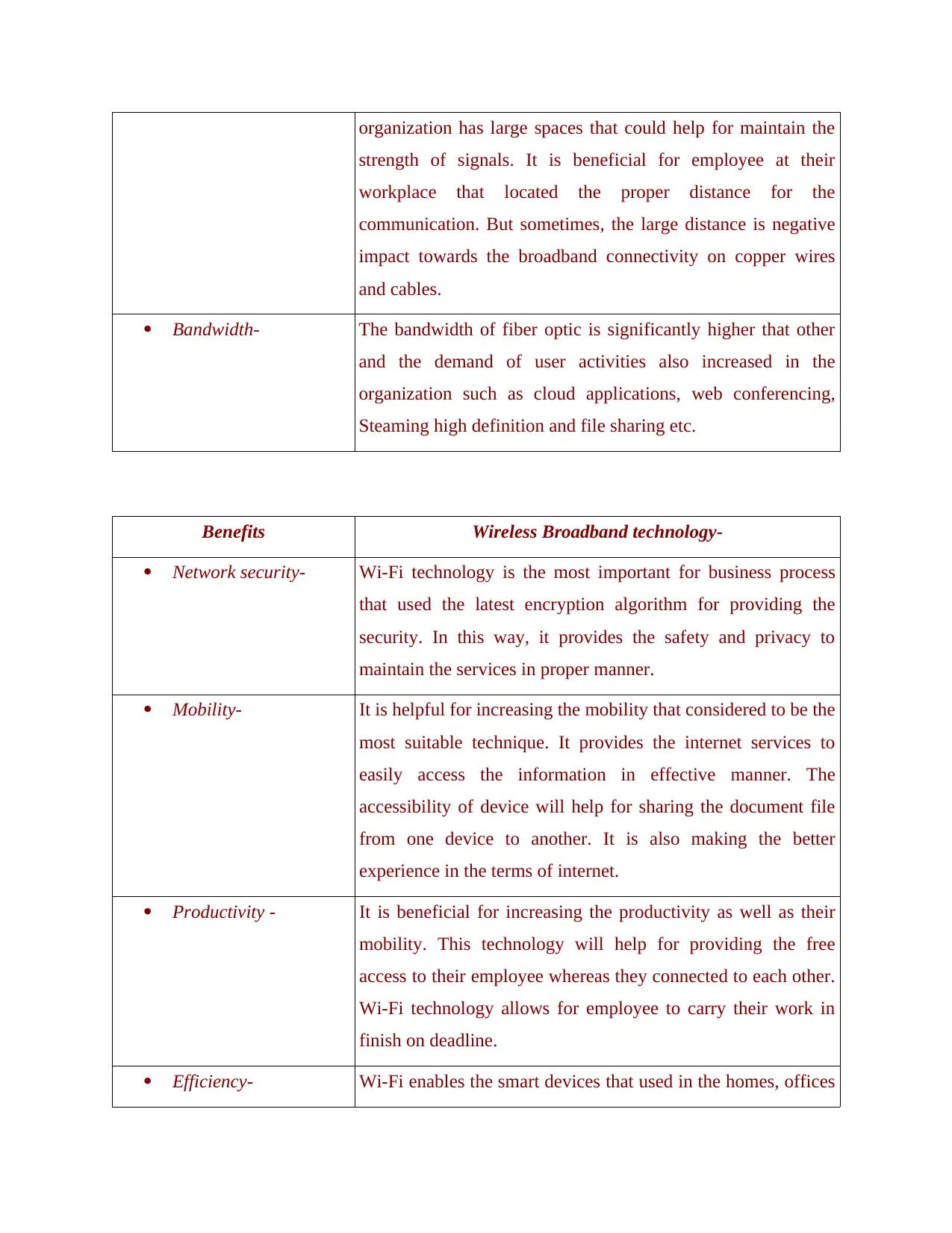
organization has large spaces that could help for maintain the
strength of signals. It is beneficial for employee at their
workplace that located the proper distance for the
communication. But sometimes, the large distance is negative
impact towards the broadband connectivity on copper wires
and cables.
Bandwidth- The bandwidth of fiber optic is significantly higher that other
and the demand of user activities also increased in the
organization such as cloud applications, web conferencing,
Steaming high definition and file sharing etc.
Benefits Wireless Broadband technology-
Network security- Wi-Fi technology is the most important for business process
that used the latest encryption algorithm for providing the
security. In this way, it provides the safety and privacy to
maintain the services in proper manner.
Mobility- It is helpful for increasing the mobility that considered to be the
most suitable technique. It provides the internet services to
easily access the information in effective manner. The
accessibility of device will help for sharing the document file
from one device to another. It is also making the better
experience in the terms of internet.
Productivity - It is beneficial for increasing the productivity as well as their
mobility. This technology will help for providing the free
access to their employee whereas they connected to each other.
Wi-Fi technology allows for employee to carry their work in
finish on deadline.
Efficiency- Wi-Fi enables the smart devices that used in the homes, offices
strength of signals. It is beneficial for employee at their
workplace that located the proper distance for the
communication. But sometimes, the large distance is negative
impact towards the broadband connectivity on copper wires
and cables.
Bandwidth- The bandwidth of fiber optic is significantly higher that other
and the demand of user activities also increased in the
organization such as cloud applications, web conferencing,
Steaming high definition and file sharing etc.
Benefits Wireless Broadband technology-
Network security- Wi-Fi technology is the most important for business process
that used the latest encryption algorithm for providing the
security. In this way, it provides the safety and privacy to
maintain the services in proper manner.
Mobility- It is helpful for increasing the mobility that considered to be the
most suitable technique. It provides the internet services to
easily access the information in effective manner. The
accessibility of device will help for sharing the document file
from one device to another. It is also making the better
experience in the terms of internet.
Productivity - It is beneficial for increasing the productivity as well as their
mobility. This technology will help for providing the free
access to their employee whereas they connected to each other.
Wi-Fi technology allows for employee to carry their work in
finish on deadline.
Efficiency- Wi-Fi enables the smart devices that used in the homes, offices
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

to easily access the files at any place or locations. It provides
more productivity for the organization.
2) Evaluate the emerging technology such as the Cognitive Radio (CR) and Unlicensed Mobile
Access (UMA) / functional architecture and their relative benefits and current deployment
status.
Cognitive Radio (CR)
It is a network technology or an intelligent radio that can be configured or programmed
dynamically that can automatically detect all the available channels in a wireless spectrum in its
vicinity to avoid users congestion and interface. It provides standardize interface to access
network. It uses OSI protocol stack so that its capabilities can be allocated to its particular layer:
Cognitive Radio consists of SDR components and also the related cognitive components of idea
CR. The cognition component of Cognitive Radio describes the SDR in RXML so that the (self)
will be able to know that it is a radio and its goal is to achieve high quality of information to its
users.
Architecture is expressed in Radio eXtensible Markup Language. RXML intelligence that
includes radio back ground and also the user stereotypes and also the knowledge of RF and also
consists of space time scenes that are perceived and experienced. It consists of both structures
reasoning of iCR peers and Cognitive wireless networks and also the adhoc reasoning with the
users. It is being used in various other technologies such as in wireless medical networks,
authentication application where it can easily identify its users and prevent unauthorized access
to the application.
It uses OSI protocol stack so that its capabilities can be allocated to its particular layer:
Application layer has personal digital assistant with simple communication capability.
Network layer allows easy interaction with heterogeneous networks that a simple radio
can achieve.
Physical and data link layer provide better performance in terms of transmission capacity,
connectivity, spectrum, bandwidth and all the other aspect of communication.
Benefits:
Cognitive radio operates purely autonomously, by using the Cognitive Radio networks it
provides the significant advantage in terms of spectrum using.
more productivity for the organization.
2) Evaluate the emerging technology such as the Cognitive Radio (CR) and Unlicensed Mobile
Access (UMA) / functional architecture and their relative benefits and current deployment
status.
Cognitive Radio (CR)
It is a network technology or an intelligent radio that can be configured or programmed
dynamically that can automatically detect all the available channels in a wireless spectrum in its
vicinity to avoid users congestion and interface. It provides standardize interface to access
network. It uses OSI protocol stack so that its capabilities can be allocated to its particular layer:
Cognitive Radio consists of SDR components and also the related cognitive components of idea
CR. The cognition component of Cognitive Radio describes the SDR in RXML so that the (self)
will be able to know that it is a radio and its goal is to achieve high quality of information to its
users.
Architecture is expressed in Radio eXtensible Markup Language. RXML intelligence that
includes radio back ground and also the user stereotypes and also the knowledge of RF and also
consists of space time scenes that are perceived and experienced. It consists of both structures
reasoning of iCR peers and Cognitive wireless networks and also the adhoc reasoning with the
users. It is being used in various other technologies such as in wireless medical networks,
authentication application where it can easily identify its users and prevent unauthorized access
to the application.
It uses OSI protocol stack so that its capabilities can be allocated to its particular layer:
Application layer has personal digital assistant with simple communication capability.
Network layer allows easy interaction with heterogeneous networks that a simple radio
can achieve.
Physical and data link layer provide better performance in terms of transmission capacity,
connectivity, spectrum, bandwidth and all the other aspect of communication.
Benefits:
Cognitive radio operates purely autonomously, by using the Cognitive Radio networks it
provides the significant advantage in terms of spectrum using.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
It is lower in cost, it improves the link reliability, it less complex, Cognitive Radio uses
advanced network topologies and has simple network architecture and it can be upgraded
easily.
Cognitive Radio are more feasible as compared to the single cognitive radio. Its is a
miraculous helping technology and its users are increasing in the number.
Network layer allows easy interaction with heterogeneous networks that a simple radio
can achieve (Molina, and Jacob 2018).
Physical and data link layer provide better performance in terms of transmission capacity,
connectivity, spectrum, bandwidth and all the other aspect of communication.
Application layer has personal digital assistant with simple communication capability.
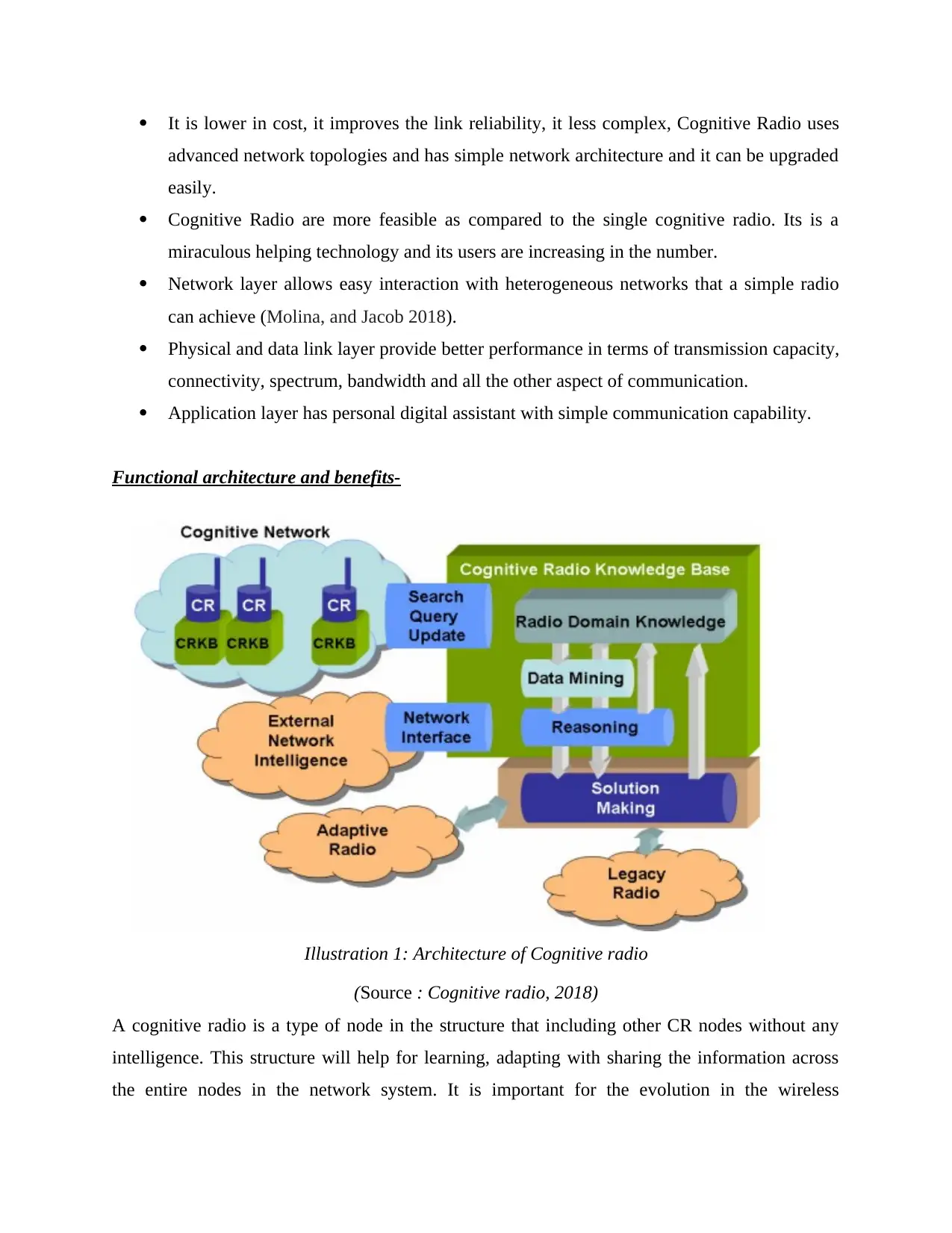
Functional architecture and benefits-
(Source : Cognitive radio, 2018)
A cognitive radio is a type of node in the structure that including other CR nodes without any
intelligence. This structure will help for learning, adapting with sharing the information across
the entire nodes in the network system. It is important for the evolution in the wireless
Illustration 1: Architecture of Cognitive radio
advanced network topologies and has simple network architecture and it can be upgraded
easily.
Cognitive Radio are more feasible as compared to the single cognitive radio. Its is a
miraculous helping technology and its users are increasing in the number.
Network layer allows easy interaction with heterogeneous networks that a simple radio
can achieve (Molina, and Jacob 2018).
Physical and data link layer provide better performance in terms of transmission capacity,
connectivity, spectrum, bandwidth and all the other aspect of communication.
Application layer has personal digital assistant with simple communication capability.
Functional architecture and benefits-
(Source : Cognitive radio, 2018)
A cognitive radio is a type of node in the structure that including other CR nodes without any
intelligence. This structure will help for learning, adapting with sharing the information across
the entire nodes in the network system. It is important for the evolution in the wireless
Illustration 1: Architecture of Cognitive radio

communication from the devices to their cognitive units. It has more capabilities and flexibilities
that support the network system according to the requirement of services. CR node is mainly
distributed the information in the form of processing chain and implemented across the entire
network system. Cognitive radio design is the highly multi disciplinary that combining with the
artificial intelligence, spectrum regulations, wireless communication for performing different
task in effective ways. Network based implementation is provided more comprehensive or
reliable information for the optimizing the performance. It always includes a group of nodes that
interactive behaviour and also distributed database for the purpose of information sharing.
Unlicensed Mobile Access(UMA)
UMA technology provide various alternative access to GPRS and GSM core network
issues through IP based broadband connections. To provide a seamless experience to users,
specifications define all the new network elements, associated protocols that provide secure
transport of GPRS/GSM signaling and user traffic over IP. It interfaces into core network
through existing 3GPP'S specified GB interfaces.
Benefits of UMA:
It has advanced the wireless devices section without worrying about the connectivity of
their own home network.
There is no need to input setting or operations in devices to avoid interference.
Certification procedure of user centric wireless home network is triggered by network
and has been made easy or simplified.
Better coverage area and relatively better quality and low cost service for subscriber.
It is used in home telephone internet which are available for free, also used in mobile terminals
that support both voice and data applications and at lat it is also used in various famous
applications such as Skype.
that support the network system according to the requirement of services. CR node is mainly
distributed the information in the form of processing chain and implemented across the entire
network system. Cognitive radio design is the highly multi disciplinary that combining with the
artificial intelligence, spectrum regulations, wireless communication for performing different
task in effective ways. Network based implementation is provided more comprehensive or
reliable information for the optimizing the performance. It always includes a group of nodes that
interactive behaviour and also distributed database for the purpose of information sharing.
Unlicensed Mobile Access(UMA)
UMA technology provide various alternative access to GPRS and GSM core network
issues through IP based broadband connections. To provide a seamless experience to users,
specifications define all the new network elements, associated protocols that provide secure
transport of GPRS/GSM signaling and user traffic over IP. It interfaces into core network
through existing 3GPP'S specified GB interfaces.
Benefits of UMA:
It has advanced the wireless devices section without worrying about the connectivity of
their own home network.
There is no need to input setting or operations in devices to avoid interference.
Certification procedure of user centric wireless home network is triggered by network
and has been made easy or simplified.
Better coverage area and relatively better quality and low cost service for subscriber.
It is used in home telephone internet which are available for free, also used in mobile terminals
that support both voice and data applications and at lat it is also used in various famous
applications such as Skype.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




