Optimal Linear Cyber-Attack on Remote State Estimation: An Analysis
VerifiedAdded on 2022/11/13
|10
|10940
|397
Report
AI Summary
This paper delves into the realm of cyber-physical systems security, specifically focusing on deception attacks within a remote state estimation application. It proposes a novel linear attack strategy where a malicious attacker can inject false data without being detected by a residue-based false data detector. The study presents the feasibility constraints of this attack and analyzes the resulting degradation in system performance, including the derivation of the estimation error covariance. Furthermore, the paper provides a closed-form expression for the optimal linear attack strategy, which maximizes the error covariance. The research contributes to the understanding of potential cyber threats and provides insights into developing effective countermeasures. The results are supported by simulated examples that illustrate the theoretical findings.

2325-5870 (c) 2016 IEEE. Personal use is permitted, but republication/redistribution requires IEEE permission. See http://www.ieee.org/publication
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publi
Transactions on Control of Network Systems
1
Optimal Linear Cyber-Attack on
Remote State Estimation
Ziyang Guo, Dawei Shi, Karl Henrik Johansson, Ling Shi
Abstract—Recent years have witnessed the surge of interest
of security issues in cyber-physical systems. In this paper, we
consider malicious cyber attacks in a remote state estimation
application where a smart sensor node transmits data to a remote
estimator equipped with a false data detector. It is assumed
that all the sensor data can be observed and modified by the
malicious attacker and a residue-based detection algorithm is
used at the remote side to detect data anomalies. We propose a
linear deception attack strategy and present the corresponding
feasibility constraint which guarantees that the attacker is able
to successfully inject false data without being detected. The
evolution of the estimation error covariance at the remote
estimator is derived and the degradation of system performance
under the proposed linear attack policy is analyzed. Furthermore,
we obtain a closed-form expression of the optimal attack strategy
among all linear attacks. Comparison of attack strategies through
simulated examples are provided to illustrate the theoretical
results.
Index Terms—Cyber-Physical Systems, Deception Attack, Se-
curity, Remote State Estimation.
I. INTRODUCTION
CYBER-Physical Systems (CPS) are systems that smooth-
ly integrate sensing, communication, control, computa-
tion and physical processes [1]. CPS applications range from
large-scale industrial applications to critical infrastructures
including chemical processes, smart grids, mine monitoring,
intelligent transportation, precision agriculture, civil engineer-
ing, aerospace, etc. [2]–[4].
The rapid growth of CPS and its safety-critical applications
have generated a surge of interest in CPS security in recent
years [5]. Since the measurement and control data in CPS are
commonly transmitted through unprotected communication
networks, such systems are vulnerable to cyber threats. Any
successful CPS attack may lead to a variety of severe con-
sequences, including customer information leakage, damages
to national economy, destruction of infrastructure, and even
endangering of human lives [6], [7].
Z. Guo and L. Shi are with Department of Electronic and Computer
Engineering, the Hong Kong University of Science and Technology, Clear
Water Bay, Kowloon, Hong Kong (e-mail: zguoae@ust.hk, eesling@ust.hk).
D. Shi is with State Key Laboratory of Intelligent Control and Decision
of Complex Systems, School of Automation, Beijing Institute of Technology,
Beijing, 100081, China (e-mail: dawei.shi@outlook.com).
K. H. Johansson is with ACCESS Linnaeus Centre and Department of
Automatic Control, School of Electrical Engineering, KTH Royal Institute of
Technology, Stockholm, Sweden (e-mail: kallej@kth.se).
The work by Z. Guo and L. Shi is supported by a Hong Kong RGC
GRF grant 16209114. The work by D. Shi is supported by Natural Science
Foundation of China (61503027). The work by K. H. Johansson is supported
by the Knut and Alice Wallenberg Foundation and the Swedish Research
Council.
The cyber-physical attack space can be divided according
to the adversary’s system knowledge, disclosure resources
and disruption resources. Attack models, such as Denial-of-
Service (DoS), replay, false data injection and zero dynamic
attacks were analyzed in [8]. Cardenas et al. [9] studied cyber
attacks compromising measurement and actuator data integrity
and availability. They considered two types of CPS attacks:
DoS and deception attacks. The DoS attack, which jams
the communication channels and prevents the exchange of
information containing both sensor measurements and control
inputs, was further analyzed for a resource-constrained attack-
er in [10], [11]. Moreover, a game-theoretic approach was
utilized to provide an effective framework to handle security
and privacy issues in communication networks in [12]. With
energy constraints on both the sensor and the attacker, Li
et al. [13] studied the interactive decision-making process of
when to send and when to attack using a zero-sum game. They
proved that the optimal strategies for both sides constitute a
Nash equilibrium. Agah et al. [14] formulated a repeated game
between the intrusion detector and the sensor nodes to study
the prevention of DoS attack in wireless sensor networks. A
framework to enforce cooperation among sensor nodes and
punishment for non-cooperative behavior was proposed.
The deception attacks, which affect the integrity of data by
modifying its content, have recently received attention. The
replay attack is a special type of deception attack where the
attacker does not have any system knowledge but is able to
access, record, and replay the sensor data. Mo et al. [15],
[16] studied the feasibility of the replay attack on a control
system equipped with a bad-data detector and proposed a
countermeasure to detect the existence of such an attack. Miao
et al. [17] proposed a zero-sum stochastic game framework
to balance the tradeoff between the control performance and
the system security. Another type of deception attack with
perfect system knowledge, false-data injection attack, was
initially proposed for power networks [18]. Sandberg et al. [19]
analyzed the minimum number of sensors required for a
stealthy attack and proposed the concept of measurement
security metric. A more general framework for security indices
was provided in [20]. Furthermore, the consequence of the
false-data injection attack and the reachable state estimation
error have been analyzed in [21]. Besides the aforementioned
studies where the models used are static, data injection attacks
on dynamic control systems have also been considered. A
covert data attack, which misleads the control center to remove
useful measurements, was proposed and analyzed in [22].
Pasqualetti et al. [23] studied the set of undetectable false-data
injection attacks for omniscient attackers who have full system
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publi
Transactions on Control of Network Systems
1
Optimal Linear Cyber-Attack on
Remote State Estimation
Ziyang Guo, Dawei Shi, Karl Henrik Johansson, Ling Shi
Abstract—Recent years have witnessed the surge of interest
of security issues in cyber-physical systems. In this paper, we
consider malicious cyber attacks in a remote state estimation
application where a smart sensor node transmits data to a remote
estimator equipped with a false data detector. It is assumed
that all the sensor data can be observed and modified by the
malicious attacker and a residue-based detection algorithm is
used at the remote side to detect data anomalies. We propose a
linear deception attack strategy and present the corresponding
feasibility constraint which guarantees that the attacker is able
to successfully inject false data without being detected. The
evolution of the estimation error covariance at the remote
estimator is derived and the degradation of system performance
under the proposed linear attack policy is analyzed. Furthermore,
we obtain a closed-form expression of the optimal attack strategy
among all linear attacks. Comparison of attack strategies through
simulated examples are provided to illustrate the theoretical
results.
Index Terms—Cyber-Physical Systems, Deception Attack, Se-
curity, Remote State Estimation.
I. INTRODUCTION
CYBER-Physical Systems (CPS) are systems that smooth-
ly integrate sensing, communication, control, computa-
tion and physical processes [1]. CPS applications range from
large-scale industrial applications to critical infrastructures
including chemical processes, smart grids, mine monitoring,
intelligent transportation, precision agriculture, civil engineer-
ing, aerospace, etc. [2]–[4].
The rapid growth of CPS and its safety-critical applications
have generated a surge of interest in CPS security in recent
years [5]. Since the measurement and control data in CPS are
commonly transmitted through unprotected communication
networks, such systems are vulnerable to cyber threats. Any
successful CPS attack may lead to a variety of severe con-
sequences, including customer information leakage, damages
to national economy, destruction of infrastructure, and even
endangering of human lives [6], [7].
Z. Guo and L. Shi are with Department of Electronic and Computer
Engineering, the Hong Kong University of Science and Technology, Clear
Water Bay, Kowloon, Hong Kong (e-mail: zguoae@ust.hk, eesling@ust.hk).
D. Shi is with State Key Laboratory of Intelligent Control and Decision
of Complex Systems, School of Automation, Beijing Institute of Technology,
Beijing, 100081, China (e-mail: dawei.shi@outlook.com).
K. H. Johansson is with ACCESS Linnaeus Centre and Department of
Automatic Control, School of Electrical Engineering, KTH Royal Institute of
Technology, Stockholm, Sweden (e-mail: kallej@kth.se).
The work by Z. Guo and L. Shi is supported by a Hong Kong RGC
GRF grant 16209114. The work by D. Shi is supported by Natural Science
Foundation of China (61503027). The work by K. H. Johansson is supported
by the Knut and Alice Wallenberg Foundation and the Swedish Research
Council.
The cyber-physical attack space can be divided according
to the adversary’s system knowledge, disclosure resources
and disruption resources. Attack models, such as Denial-of-
Service (DoS), replay, false data injection and zero dynamic
attacks were analyzed in [8]. Cardenas et al. [9] studied cyber
attacks compromising measurement and actuator data integrity
and availability. They considered two types of CPS attacks:
DoS and deception attacks. The DoS attack, which jams
the communication channels and prevents the exchange of
information containing both sensor measurements and control
inputs, was further analyzed for a resource-constrained attack-
er in [10], [11]. Moreover, a game-theoretic approach was
utilized to provide an effective framework to handle security
and privacy issues in communication networks in [12]. With
energy constraints on both the sensor and the attacker, Li
et al. [13] studied the interactive decision-making process of
when to send and when to attack using a zero-sum game. They
proved that the optimal strategies for both sides constitute a
Nash equilibrium. Agah et al. [14] formulated a repeated game
between the intrusion detector and the sensor nodes to study
the prevention of DoS attack in wireless sensor networks. A
framework to enforce cooperation among sensor nodes and
punishment for non-cooperative behavior was proposed.
The deception attacks, which affect the integrity of data by
modifying its content, have recently received attention. The
replay attack is a special type of deception attack where the
attacker does not have any system knowledge but is able to
access, record, and replay the sensor data. Mo et al. [15],
[16] studied the feasibility of the replay attack on a control
system equipped with a bad-data detector and proposed a
countermeasure to detect the existence of such an attack. Miao
et al. [17] proposed a zero-sum stochastic game framework
to balance the tradeoff between the control performance and
the system security. Another type of deception attack with
perfect system knowledge, false-data injection attack, was
initially proposed for power networks [18]. Sandberg et al. [19]
analyzed the minimum number of sensors required for a
stealthy attack and proposed the concept of measurement
security metric. A more general framework for security indices
was provided in [20]. Furthermore, the consequence of the
false-data injection attack and the reachable state estimation
error have been analyzed in [21]. Besides the aforementioned
studies where the models used are static, data injection attacks
on dynamic control systems have also been considered. A
covert data attack, which misleads the control center to remove
useful measurements, was proposed and analyzed in [22].
Pasqualetti et al. [23] studied the set of undetectable false-data
injection attacks for omniscient attackers who have full system
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2325-5870 (c) 2016 IEEE. Personal use is permitted, but republication/redistribution requires IEEE permission. See http://www.ieee.org/publication
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publi
Transactions on Control of Network Systems
2
information but only compromise a part of existing sensors
and actuators. A unified framework and advanced monitoring
procedures to detect components malfunction or measurements
corruption were also proposed. Further results on different for-
mulations of integrity attack and secure estimation problems
were investigated in [24], [25].
In this paper, we consider deception attacks in a remote state
estimation scenario. We study the optimal linear deception
attack on the sensor data without being detected by a false
data detector at the remote state estimator. The motivation of
the current work is three-fold:
1) A deception attack is subtler and may cause more severe
consequences compared with many other attacks.
2) Existing models of deception attack are quite simple,
many focusing on static parameter estimation [18]–[21].
The need for analyzing potential consequences of attacks
on a dynamic system is important.
3) To propose effective countermeasures, one needs to un-
derstand what the worst attack might be.
The main contributions of this paper are summarized as
follows:
1) We propose a novel type of linear attack strategy and
present the corresponding feasibility constraint, which
guarantees the attacker to successfully inject false data
and remain undetected by the false data detector at the
same time.
2) We compute the evolution of the estimation error covari-
ance at the remote estimator and analyze the degradation
of system performance under various linear attack strate-
gies (Theorem 1).
3) We derive a closed-form expression of the optimal linear
attack strategy which yields the largest error covariance
(Theorem 2).
The remainder of the paper is organized as follows. Sec-
tion II presents the problem formulation and revisits some
preliminaries of the Kalman filter and the false data detector.
Section III proposes a new type of deception attack strategy
and states the feasibility constraint. Section IV illustrates the
degradation of system performance and derives the optimal
strategy among all linear attacks. Simulation results are pro-
vided in Section V. Some concluding remarks are given in the
end.
Notations: N and R denote the sets of natural numbers and
real numbers, respectively. Rn is the n-dimensional Euclidean
space. Sn
+ and Sn
++ are the sets of n × n positive semi-
definite and positive definite matrices. When X ∈ S n
+ , we
simply write X ≥ 0 (or X > 0 if X ∈ S n
++ ). X ≥ Y
if X − Y ∈ S n
+ . N (μ, Σ) denotes Gaussian distribution
with mean μ and covariance matrix Σ. The superscript T
stands for transposition. tr(·) refers to the trace of a matrix.
E[·] denotes the expectation of a random variable. Pr{·}
denotes the probability of an event. For functions f, f 1, f2
with appropriate domain, f 1 ◦ f2(x) stands for the function
composition f 1(f 2(x)), and f n (x) , f (f n−1 (x)).
II. PROBLEM SETUP
The system architecture of cyber attacks in a remote state
estimation application considered in this paper is shown in
Fig. 1. System architecture. The attacker is able to intercept and modify sensor
data, which affects the remote estimation performance despite the false data
detector.
Fig. 1. It consists of six main components, namely the process,
smart sensor, attacker, remote estimator, false data detector,
and wireless network. The smart sensor performs local esti-
mation based on the process measurements and transmits data
packet to the remote estimator through a wireless network
where a malicious attacker may intercept and modify the
transmitted data. A false data detector at remote side monitors
the system behavior and identifies the existence of the attacker.
The detailed models are described in the following.
A. Process Model
Consider a discrete-time linear time-invariant process:
xk+1 = Axk + wk , (1)
yk = Cxk + vk , (2)
where k ∈ Nis the time index, xk ∈ Rn the vector of system
states, yk ∈ Rm the vector of sensor measurements, wk ∈
Rn and vk ∈ Rm are zero-mean i.i.d. Gaussian noises with
covariances Q ≥ 0 and R > 0, respectively. The initial state
x0 is zero-mean Gaussian with covariance matrix Π0 ≥ 0, and
is independent of wk and vk for all k ≥ 0. The pair (A, C) is
detectable and (A, √ Q) is stabilizable.
B. Smart Sensor and Remote Estimator
The concept of smart sensors refers to sensors that provide
extra functions beyond those necessary for generating the
measured quantity. The functions included might be signal
processing, decision-making and alarm functions, which can
be used to improve system performance [26], [27]. Thus,
we assume that the smart sensor first locally processes the
raw measurement data and transmits its innovation to the
remote estimator in this work. To estimate the system state,
the following standard Kalman filter is adopted by the remote
estimator:
ˆx−
k = Aˆxk−1 , (3)
P −
k = APk−1 AT + Q, (4)
K k = P−
k CT (CP −
k CT + R)−1, (5)
ˆxk = ˆx−
k + Kk zk , (6)
Pk = (I − Kk C)P −
k , (7)
where zk is the local innovation transmitted to the remote
estimator with
zk = yk − C ˆx−
k , (8)
ˆx−
k and ˆxk are the a priori and the a posteriori Minimum
Mean Squared Error (MMSE) estimates of the state xk at the
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publi
Transactions on Control of Network Systems
2
information but only compromise a part of existing sensors
and actuators. A unified framework and advanced monitoring
procedures to detect components malfunction or measurements
corruption were also proposed. Further results on different for-
mulations of integrity attack and secure estimation problems
were investigated in [24], [25].
In this paper, we consider deception attacks in a remote state
estimation scenario. We study the optimal linear deception
attack on the sensor data without being detected by a false
data detector at the remote state estimator. The motivation of
the current work is three-fold:
1) A deception attack is subtler and may cause more severe
consequences compared with many other attacks.
2) Existing models of deception attack are quite simple,
many focusing on static parameter estimation [18]–[21].
The need for analyzing potential consequences of attacks
on a dynamic system is important.
3) To propose effective countermeasures, one needs to un-
derstand what the worst attack might be.
The main contributions of this paper are summarized as
follows:
1) We propose a novel type of linear attack strategy and
present the corresponding feasibility constraint, which
guarantees the attacker to successfully inject false data
and remain undetected by the false data detector at the
same time.
2) We compute the evolution of the estimation error covari-
ance at the remote estimator and analyze the degradation
of system performance under various linear attack strate-
gies (Theorem 1).
3) We derive a closed-form expression of the optimal linear
attack strategy which yields the largest error covariance
(Theorem 2).
The remainder of the paper is organized as follows. Sec-
tion II presents the problem formulation and revisits some
preliminaries of the Kalman filter and the false data detector.
Section III proposes a new type of deception attack strategy
and states the feasibility constraint. Section IV illustrates the
degradation of system performance and derives the optimal
strategy among all linear attacks. Simulation results are pro-
vided in Section V. Some concluding remarks are given in the
end.
Notations: N and R denote the sets of natural numbers and
real numbers, respectively. Rn is the n-dimensional Euclidean
space. Sn
+ and Sn
++ are the sets of n × n positive semi-
definite and positive definite matrices. When X ∈ S n
+ , we
simply write X ≥ 0 (or X > 0 if X ∈ S n
++ ). X ≥ Y
if X − Y ∈ S n
+ . N (μ, Σ) denotes Gaussian distribution
with mean μ and covariance matrix Σ. The superscript T
stands for transposition. tr(·) refers to the trace of a matrix.
E[·] denotes the expectation of a random variable. Pr{·}
denotes the probability of an event. For functions f, f 1, f2
with appropriate domain, f 1 ◦ f2(x) stands for the function
composition f 1(f 2(x)), and f n (x) , f (f n−1 (x)).
II. PROBLEM SETUP
The system architecture of cyber attacks in a remote state
estimation application considered in this paper is shown in
Fig. 1. System architecture. The attacker is able to intercept and modify sensor
data, which affects the remote estimation performance despite the false data
detector.
Fig. 1. It consists of six main components, namely the process,
smart sensor, attacker, remote estimator, false data detector,
and wireless network. The smart sensor performs local esti-
mation based on the process measurements and transmits data
packet to the remote estimator through a wireless network
where a malicious attacker may intercept and modify the
transmitted data. A false data detector at remote side monitors
the system behavior and identifies the existence of the attacker.
The detailed models are described in the following.
A. Process Model
Consider a discrete-time linear time-invariant process:
xk+1 = Axk + wk , (1)
yk = Cxk + vk , (2)
where k ∈ Nis the time index, xk ∈ Rn the vector of system
states, yk ∈ Rm the vector of sensor measurements, wk ∈
Rn and vk ∈ Rm are zero-mean i.i.d. Gaussian noises with
covariances Q ≥ 0 and R > 0, respectively. The initial state
x0 is zero-mean Gaussian with covariance matrix Π0 ≥ 0, and
is independent of wk and vk for all k ≥ 0. The pair (A, C) is
detectable and (A, √ Q) is stabilizable.
B. Smart Sensor and Remote Estimator
The concept of smart sensors refers to sensors that provide
extra functions beyond those necessary for generating the
measured quantity. The functions included might be signal
processing, decision-making and alarm functions, which can
be used to improve system performance [26], [27]. Thus,
we assume that the smart sensor first locally processes the
raw measurement data and transmits its innovation to the
remote estimator in this work. To estimate the system state,
the following standard Kalman filter is adopted by the remote
estimator:
ˆx−
k = Aˆxk−1 , (3)
P −
k = APk−1 AT + Q, (4)
K k = P−
k CT (CP −
k CT + R)−1, (5)
ˆxk = ˆx−
k + Kk zk , (6)
Pk = (I − Kk C)P −
k , (7)
where zk is the local innovation transmitted to the remote
estimator with
zk = yk − C ˆx−
k , (8)
ˆx−
k and ˆxk are the a priori and the a posteriori Minimum
Mean Squared Error (MMSE) estimates of the state xk at the

2325-5870 (c) 2016 IEEE. Personal use is permitted, but republication/redistribution requires IEEE permission. See http://www.ieee.org/publication
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publi
Transactions on Control of Network Systems
3
remote estimator, and P −
k and Pk are the corresponding error
covariances. The recursion starts from ˆx−
0 = 0 and P −
0 =
Π0 ≥ 0.
For notational brevity, we also define the Lyapunov and
Riccati operators h, ˜g : Sn
+ → Sn
+ as:
h(X) , AXA T + Q, (9)
˜g(X) , X − XC T (CXC T + R)−1CX. (10)
It is well known that the gain and the error covariance of the
Kalman filter converge from any initial condition [28]. Hence,
we denote the steady-state value of the a priori estimation
error covariance as
P = lim
k→∞ P −
k ,
where P is the unique positive semi-definite solution of h ◦
˜g(X) = X .
To simplify our subsequent discussions, we assume that the
Kalman filter at the remote estimator starts from the steady
state, i.e., Π0 = P , which results in a steady-state Kalman
filter with fixed gain
K = PC T (CP CT + R)−1. (11)
Remark 1 Using the smart sensor instead of the conventional
sensor not only improves measurement accuracy, but also
reduces the computations at the remote estimator and improve
communication efficiency [29]. Another reason why sending
the innovation zk rather than the measurement yk or the
local estimate ˆxk is that the innovation zk will approach a
steady-state distribution that can be easily checked by a false
data detector. If yk or ˆxk is sent instead, it is difficult to find
an appropriate detector which can detect potential malicious
attacks.
C. False Data Detector
The innovation sequence zk sent by the smart sensor is a
white Gaussian process with zero mean and covariance P ,
where P = CPC T + R [28]. The false data detector at
the remote estimator side monitors the system behavior and
detects cyber attacks by checking the statistical characteristic
of the arriving innovation sequence. The mean and covariance
of the innovations are used to diagnose the existence of
potential cyber attacks.
The χ2 detector is a residue-based detector widely used
to reveal system anomalies [30], [31]. The detector makes a
decision based on the sum of squared residues zk which is
normalized by the steady-state innovation covariance matrix
P . At time slot k, we suppose the detection criterion is given
in the following form:
gk =
kX
i=k−J+1
zT
i P −1zi
H 0
≶
H 1
δ, (12)
where J is the window size of detection, δ is the threshold,
the null hypotheses H0 means that the system is operating
normally, while the alternative hypotheses H1 means that the
system is under attack. The left hand side of (12) satisfies the
χ2 distribution with mJ degrees of freedom. Thus, it is easy
to calculate the false alarm rate from the χ2 distribution. If gk
is greater than the threshold, the detector triggers an alarm.
D. Problems of Interest
Based on the model of the process, the smart sensor, and
the false data detector, the main problems we are interested in
consist of the following:
1) What are the possible attack strategies under which the
attacker remains undetectable to the false data detector?
2) What is the corresponding estimation error at the remote
estimator under such an attack?
3) Does there exist an optimal attack strategy that renders
maximum estimation error?
The detailed mathematical formulations and solutions to
these problems will be introduced in the following two sec-
tions.
III. LINEAR ATTACK STRATEGY
In this section, we consider the existence of a malicious
agent who intentionally launches cyber attacks to degrade the
system performance. We will first define the attack policy and
then analyze the feasibility constraint needed for such attack
from being detected by the false data detector.
A. Linear Deception Attack
Similar to the attack models in existing works [32], [33]
and the man-in-the-middle attack where the attacker has
knowledge of all relevant messages passing between the two
victims and can inject new ones [34], [35], we suppose that
the attacker is able to intercept and modify the transmitted
data. At each time k, the attack strategy is defined as
˜zk = fk (zk ) + bk ,
where zk is the currently intercepted innovation, ˜zk the in-
novation modified by the attacker, f k an arbitrary function,
bk ∼ N (0, L ) an i.i.d. Gaussian random variable which is
independent of zk .
In this paper, we focus on the subset of all linear attack
strategies where f k is a linear transformation of the innovation
zk . We shall consider the general nonlinear attack strategies in
the future work. The proposed linear attack strategy is defined
as
˜zk = Tk zk + bk , (13)
where Tk ∈ R m×m is an arbitrary matrix. Since zk ∼
N (0, P), where P = CPC T + R, it is easy to see that
˜zk is also an i.i.d. Gaussian random variable with zero mean
and variance Tk PT T
k + L .
According to the detection criterion (12) of the false data
detector, the detection rate of the proposed linear attack (13)
is the same as without attack if the modified innovation ˜zk
preserves the same statistical characteristic as zk . In other
words, to bypass the false data detector, ˜zk is supposed to
satisfy the Gaussian distribution N (0, P), i.e., have zero mean
and covariance P . Hence,
Tk PT T
k + L = P.
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publi
Transactions on Control of Network Systems
3
remote estimator, and P −
k and Pk are the corresponding error
covariances. The recursion starts from ˆx−
0 = 0 and P −
0 =
Π0 ≥ 0.
For notational brevity, we also define the Lyapunov and
Riccati operators h, ˜g : Sn
+ → Sn
+ as:
h(X) , AXA T + Q, (9)
˜g(X) , X − XC T (CXC T + R)−1CX. (10)
It is well known that the gain and the error covariance of the
Kalman filter converge from any initial condition [28]. Hence,
we denote the steady-state value of the a priori estimation
error covariance as
P = lim
k→∞ P −
k ,
where P is the unique positive semi-definite solution of h ◦
˜g(X) = X .
To simplify our subsequent discussions, we assume that the
Kalman filter at the remote estimator starts from the steady
state, i.e., Π0 = P , which results in a steady-state Kalman
filter with fixed gain
K = PC T (CP CT + R)−1. (11)
Remark 1 Using the smart sensor instead of the conventional
sensor not only improves measurement accuracy, but also
reduces the computations at the remote estimator and improve
communication efficiency [29]. Another reason why sending
the innovation zk rather than the measurement yk or the
local estimate ˆxk is that the innovation zk will approach a
steady-state distribution that can be easily checked by a false
data detector. If yk or ˆxk is sent instead, it is difficult to find
an appropriate detector which can detect potential malicious
attacks.
C. False Data Detector
The innovation sequence zk sent by the smart sensor is a
white Gaussian process with zero mean and covariance P ,
where P = CPC T + R [28]. The false data detector at
the remote estimator side monitors the system behavior and
detects cyber attacks by checking the statistical characteristic
of the arriving innovation sequence. The mean and covariance
of the innovations are used to diagnose the existence of
potential cyber attacks.
The χ2 detector is a residue-based detector widely used
to reveal system anomalies [30], [31]. The detector makes a
decision based on the sum of squared residues zk which is
normalized by the steady-state innovation covariance matrix
P . At time slot k, we suppose the detection criterion is given
in the following form:
gk =
kX
i=k−J+1
zT
i P −1zi
H 0
≶
H 1
δ, (12)
where J is the window size of detection, δ is the threshold,
the null hypotheses H0 means that the system is operating
normally, while the alternative hypotheses H1 means that the
system is under attack. The left hand side of (12) satisfies the
χ2 distribution with mJ degrees of freedom. Thus, it is easy
to calculate the false alarm rate from the χ2 distribution. If gk
is greater than the threshold, the detector triggers an alarm.
D. Problems of Interest
Based on the model of the process, the smart sensor, and
the false data detector, the main problems we are interested in
consist of the following:
1) What are the possible attack strategies under which the
attacker remains undetectable to the false data detector?
2) What is the corresponding estimation error at the remote
estimator under such an attack?
3) Does there exist an optimal attack strategy that renders
maximum estimation error?
The detailed mathematical formulations and solutions to
these problems will be introduced in the following two sec-
tions.
III. LINEAR ATTACK STRATEGY
In this section, we consider the existence of a malicious
agent who intentionally launches cyber attacks to degrade the
system performance. We will first define the attack policy and
then analyze the feasibility constraint needed for such attack
from being detected by the false data detector.
A. Linear Deception Attack
Similar to the attack models in existing works [32], [33]
and the man-in-the-middle attack where the attacker has
knowledge of all relevant messages passing between the two
victims and can inject new ones [34], [35], we suppose that
the attacker is able to intercept and modify the transmitted
data. At each time k, the attack strategy is defined as
˜zk = fk (zk ) + bk ,
where zk is the currently intercepted innovation, ˜zk the in-
novation modified by the attacker, f k an arbitrary function,
bk ∼ N (0, L ) an i.i.d. Gaussian random variable which is
independent of zk .
In this paper, we focus on the subset of all linear attack
strategies where f k is a linear transformation of the innovation
zk . We shall consider the general nonlinear attack strategies in
the future work. The proposed linear attack strategy is defined
as
˜zk = Tk zk + bk , (13)
where Tk ∈ R m×m is an arbitrary matrix. Since zk ∼
N (0, P), where P = CPC T + R, it is easy to see that
˜zk is also an i.i.d. Gaussian random variable with zero mean
and variance Tk PT T
k + L .
According to the detection criterion (12) of the false data
detector, the detection rate of the proposed linear attack (13)
is the same as without attack if the modified innovation ˜zk
preserves the same statistical characteristic as zk . In other
words, to bypass the false data detector, ˜zk is supposed to
satisfy the Gaussian distribution N (0, P), i.e., have zero mean
and covariance P . Hence,
Tk PT T
k + L = P.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2325-5870 (c) 2016 IEEE. Personal use is permitted, but republication/redistribution requires IEEE permission. See http://www.ieee.org/publication
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publi
Transactions on Control of Network Systems
4
Consequently, it must hold that
P − T k PT T
k = L ≥ 0. (14)
Remark 2 In principle, the attacker has knowledge of all the
past innovations such that it can design the linear attack
strategy in the form of ˜zk = f (z 0, z1, . . . , zk ) + bk =P k
i=0 Ti zi + bk . However, in order to bypass the false data
detector, the modified innovation ˜zk needs to preserve the
same Gaussian distribution N (0, P) as zk . The zero mean
condition forces T0 = T1 = · · · = Tk−1 = 0 when choosing
˜zk . Hence, it is reasonable that the proposed linear attack
strategy ˜zk only depends on current innovation zk .
B. Attacker with Perfect System Information
In the case that the attacker has perfect system information,
it can accurately calculate P by solving the Riccati equation
h ◦ ˜g(X) = X based on the system parameters A, C, Q, R.
Then for each time slot k, the attack strategy that remains
undetected by the false data detector can be easily generated
by firstly selecting any matrix Tk ∈ Rm×m which satisfies
P−T k PT T
k ≥ 0, and then selecting L = P−T k PT T
k ≥ 0.
C. Attacker with No System Information
In the case that the attacker does not have any system
information, it needs to estimate the mean and the variance
of the innovation zk before launching the attack. In statistics,
interval estimation is the use of sample data to calculate
an interval of probable values of an unknown population
parameter [36]. Suppose {X1, X2, . . . , Xn } is an independent
sample from a normally distributed population with mean μ
and variance σ2. Let
¯X = 1
n
nX
i=1
X i ,
S2 = 1
n − 1
nX
i=1
(X i − ¯X) 2,
where ¯X is the sample mean, and S2 the sample variance. In
order to estimate the mean of the population, one has
T = ¯X − μ
S/ √ n ∼ t(n − 1),
where t(n−1) represents a Student’s t−distribution with n−1
degrees of freedom. For a given confidence level 1 − α, we
obtain
Pr ¯X − tα
2 (n − 1)S
√ n < μ < ¯X + tα
2 (n − 1)S
√ n
= 1 − α, (15)
which means that the value of the estimated parameter μ falls
into the confidence interval with probability 1 − α.
Similarly, to estimate the variance of the population, we
have
χ2 = (n − 1)S2
σ2 ∼ χ2(n − 1),
where χ2(n−1)represents a chi-squared distribution withn−1
degrees of freedom. For a given confidence level 1 − β, the
probability that the estimated value is between two stochastic
endpoints is shown as follows:
Pr
(
(n − 1)S2
χ2
β
2
(n − 1)< σ2 < (n − 1)S2
χ2
1− β
2
(n − 1)
)
= 1 − β. (16)
From (15) and (16), it is not difficult to see when n is
sufficiently large, a small confidence interval with a high
confidence level can be obtained. Therefore, even though the
attacker may not know anything about the system parameters,
it can still launch the proposed linear attack without being
detected after a certain period of time, during which it can
successfully estimate the mean and the variance of the inno-
vation zk .
Based on the attack strategy, the problem we are interested
in is to find the largest degradation of the system performance
at the remote estimator under the proposed linear attack. To
quantify the estimation performance, we define ˜x−
k and ˜xk as
the a priori and the a posteriori MMSE estimates of the state
xk at the remote estimator when the system is under attack,
and ˜P −
k and ˜Pk as the corresponding error covariances. Note
that the linear attack is able to start at any time k ∈ N. Without
loss of generality, we assume that the attack starts at k = 1
and investigate the error covariance iteration at the remote side.
Due to the assumption that the remote estimator starts from
the steady state, we obtain the initial conditions ˜x−
0 = ˆx−
0 and
E[(x0 − ˜x−
0 )(x0 − ˜x−
0 )0
] = E[(x0 − ˆx−
0 )(x0 − ˆx−
0 )0
] = P.
IV. PERFORMANCE ANALYSIS
We consider the system under the linear attack (13) with
the feasibility constraint (14) in this section. First, we derive
the evolution of the estimation error covariance at the remote
estimator during an attack, which quantifies the system per-
formance degradation. Second, we derive the error covariance
iteration and optimal attack strategy for scalar systems. Then,
we formulate the problem of finding the optimal attacker
as a convex optimization problem and apply semi-definite
programming (SDP) to find a numerical solution. Finally,
we prove that the optimal attack strategy is obtained when
Tk = −I , i.e., when the attacker flips the sign of all the
innovation.
A. Error Covariance Evolution
Consider the process (1)–(2) under the proposed linear
attack ˜zk = T k zk + bk . The state estimate of the remote
estimator follows
˜x−
k = A˜xk−1 , (17)
˜xk = ˜x−
k + K˜zk , (18)
where the fixed gain K is given in (11).
Since the false data detector cannot detect any anomaly if
the linear attack strategy (13) satisfies the feasibility constrain-
t (14), the state estimate ˜xk produced by the remote estimator
will deviate from the true system state. The following theorem
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publi
Transactions on Control of Network Systems
4
Consequently, it must hold that
P − T k PT T
k = L ≥ 0. (14)
Remark 2 In principle, the attacker has knowledge of all the
past innovations such that it can design the linear attack
strategy in the form of ˜zk = f (z 0, z1, . . . , zk ) + bk =P k
i=0 Ti zi + bk . However, in order to bypass the false data
detector, the modified innovation ˜zk needs to preserve the
same Gaussian distribution N (0, P) as zk . The zero mean
condition forces T0 = T1 = · · · = Tk−1 = 0 when choosing
˜zk . Hence, it is reasonable that the proposed linear attack
strategy ˜zk only depends on current innovation zk .
B. Attacker with Perfect System Information
In the case that the attacker has perfect system information,
it can accurately calculate P by solving the Riccati equation
h ◦ ˜g(X) = X based on the system parameters A, C, Q, R.
Then for each time slot k, the attack strategy that remains
undetected by the false data detector can be easily generated
by firstly selecting any matrix Tk ∈ Rm×m which satisfies
P−T k PT T
k ≥ 0, and then selecting L = P−T k PT T
k ≥ 0.
C. Attacker with No System Information
In the case that the attacker does not have any system
information, it needs to estimate the mean and the variance
of the innovation zk before launching the attack. In statistics,
interval estimation is the use of sample data to calculate
an interval of probable values of an unknown population
parameter [36]. Suppose {X1, X2, . . . , Xn } is an independent
sample from a normally distributed population with mean μ
and variance σ2. Let
¯X = 1
n
nX
i=1
X i ,
S2 = 1
n − 1
nX
i=1
(X i − ¯X) 2,
where ¯X is the sample mean, and S2 the sample variance. In
order to estimate the mean of the population, one has
T = ¯X − μ
S/ √ n ∼ t(n − 1),
where t(n−1) represents a Student’s t−distribution with n−1
degrees of freedom. For a given confidence level 1 − α, we
obtain
Pr ¯X − tα
2 (n − 1)S
√ n < μ < ¯X + tα
2 (n − 1)S
√ n
= 1 − α, (15)
which means that the value of the estimated parameter μ falls
into the confidence interval with probability 1 − α.
Similarly, to estimate the variance of the population, we
have
χ2 = (n − 1)S2
σ2 ∼ χ2(n − 1),
where χ2(n−1)represents a chi-squared distribution withn−1
degrees of freedom. For a given confidence level 1 − β, the
probability that the estimated value is between two stochastic
endpoints is shown as follows:
Pr
(
(n − 1)S2
χ2
β
2
(n − 1)< σ2 < (n − 1)S2
χ2
1− β
2
(n − 1)
)
= 1 − β. (16)
From (15) and (16), it is not difficult to see when n is
sufficiently large, a small confidence interval with a high
confidence level can be obtained. Therefore, even though the
attacker may not know anything about the system parameters,
it can still launch the proposed linear attack without being
detected after a certain period of time, during which it can
successfully estimate the mean and the variance of the inno-
vation zk .
Based on the attack strategy, the problem we are interested
in is to find the largest degradation of the system performance
at the remote estimator under the proposed linear attack. To
quantify the estimation performance, we define ˜x−
k and ˜xk as
the a priori and the a posteriori MMSE estimates of the state
xk at the remote estimator when the system is under attack,
and ˜P −
k and ˜Pk as the corresponding error covariances. Note
that the linear attack is able to start at any time k ∈ N. Without
loss of generality, we assume that the attack starts at k = 1
and investigate the error covariance iteration at the remote side.
Due to the assumption that the remote estimator starts from
the steady state, we obtain the initial conditions ˜x−
0 = ˆx−
0 and
E[(x0 − ˜x−
0 )(x0 − ˜x−
0 )0
] = E[(x0 − ˆx−
0 )(x0 − ˆx−
0 )0
] = P.
IV. PERFORMANCE ANALYSIS
We consider the system under the linear attack (13) with
the feasibility constraint (14) in this section. First, we derive
the evolution of the estimation error covariance at the remote
estimator during an attack, which quantifies the system per-
formance degradation. Second, we derive the error covariance
iteration and optimal attack strategy for scalar systems. Then,
we formulate the problem of finding the optimal attacker
as a convex optimization problem and apply semi-definite
programming (SDP) to find a numerical solution. Finally,
we prove that the optimal attack strategy is obtained when
Tk = −I , i.e., when the attacker flips the sign of all the
innovation.
A. Error Covariance Evolution
Consider the process (1)–(2) under the proposed linear
attack ˜zk = T k zk + bk . The state estimate of the remote
estimator follows
˜x−
k = A˜xk−1 , (17)
˜xk = ˜x−
k + K˜zk , (18)
where the fixed gain K is given in (11).
Since the false data detector cannot detect any anomaly if
the linear attack strategy (13) satisfies the feasibility constrain-
t (14), the state estimate ˜xk produced by the remote estimator
will deviate from the true system state. The following theorem
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2325-5870 (c) 2016 IEEE. Personal use is permitted, but republication/redistribution requires IEEE permission. See http://www.ieee.org/publication
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publi
Transactions on Control of Network Systems
5
summarizes the evolution of the estimation error covariance
under such an attack.
Theorem 1 For the system in Fig. 1, the linear attack (13)
satisfying the feasibility constraint (14) remains undetected
by the false data detector. Moreover, the estimation error
covariance at the remote estimator follows the recursion
˜Pk = A ˜Pk−1 A0+ Q + PCT (Σ − TT
k Σ − ΣTk )CP , (19)
where Σ = (CP CT + R)−1.
Proof: The stealthiness of the proposed linear attack
strategy follows from the previous reasoning.
According to the process model (1)–(2) and the iteration of
state estimate (17)–(18), one has
xk − ˜x−
k = A(xk−1 − ˜xk−1 ) + wk−1 ,
xk − ˜xk = xk − ˜x−
k − K˜zk ,
from which the error covariance at the remote estimator side
can be obtained as
˜P −
k = E[(xk − ˜x−
k )(xk − ˜x−
k )T ]
= A ˜Pk−1 AT + Q,
˜Pk = E[(xk − ˜xk )(xk − ˜xk )T ]
= ˜P −
k + K(CP C T + R)K T
− E[(xk − ˜x−
k )˜zT
k K T ] − E[K ˜zk (xk − ˜x−
k )T ]. (20)
To calculate the last two terms of (20), we first evaluate
xk − ˜x−
k
= Axk−1 + wk−1 − A(˜x−
k−1 + K˜zk−1 )
= Ak x0 +
k−1X
i=0
Ai wk−1−i − Ak ˜x−
0 −
k−1X
i=0
Ai+1 K˜zk−1−i
= Ak (x0 − ˆx−
0 ) +
k−1X
i=0
Ai wk−1−i −
k−1X
i=0
Ai+1 K˜zk−1−i ,
(21)
where the last equality follows from the steady-state assump-
tion ˜x−
0 = ˆx−
0 . Since ˜zk is an i.i.d. Gaussian random variable,
we obtain that E[˜zi ˜zT
j ] = 0, ∀i 6= j. Thus, we are only
concerned of the correlation between the first two terms of (21)
and ˜zk . Then, based on
xk − ˆx−
k
= Axk−1 + wk−1 − A(ˆx−
k−1 + Kzk−1 )
= Axk−1 + wk−1 − A[ˆx−
k−1 + K(C(x k−1 − ˆx−
k−1 ) + vk−1 ))]
= A(I − KC)(x k−1 − ˆx−
k−1 ) + wk−1 − AKvk−1 , (22)
we can further represent ˜zk in the form of
˜zk = Tk zk + bk
= Tk C(xk − ˆx−
k ) + Tk vk + bk
= Tk CA(I − KC)(x k−1 − ˆx−
k−1 ) + Tk Cwk−1
− Tk CAKv k−1 + Tk vk + bk
= Tk C[A(I − KC)] k (x0 − ˆx−
0 )
+
k−1X
i=0
Tk C[A(I − KC)] i wk−1−i + V, (23)
where V = Tk vk + bk − P k−1
i=0 Tk C[A(I − KC)] i AKv k−1−i
is independent of the first two terms of (21). It now follows
that the second last term of (20) can be written as
E (xk − ˜x−
k )˜zT
k K T
= E
"
Ak (x0 − ˆx−
0 ) +
k−1X
i=0
Ai wk−1−i Tk C [A(I − KC)] k
(x0 − ˆx−
0 ) +
k−1X
i=0
Tk C [A(I − KC)] i wk−1−i
T
K T
#
= Ak E (x0 − ˆx−
0 )(x0 − ˆx−
0 )T (I − KC) T AT k
+
k−1X
i=0
Ai E wk−1−i wT
k−1−i (I − KC) T AT i CT T T
k K T
= Ak P (I − KC) T AT k
+
k−1X
i=0
Ai Q (I − KC) T AT i CT T T
k K T
= PC T T T
k K T , (24)
where the last equality is due to the fact that P is the unique
positive semi-definite fixed point of h ◦ ˜g, i.e.,
P = (h ◦ ˜g)n (P )
= [A(I − KC)] n P (AT )n +
n−1X
i=0
[A(I − KC)] i Q(AT )i
= An P [(I − KC) T AT ]n +
n−1X
i=0
Ai Q[(I − KC) T AT ]i .
Similarly, we obtain
E K˜zk (xk − ˜x−
k )T = KT k CP . (25)
Substituting (24) and (25) into (20), the error covariance at
the remote estimator is given by
˜Pk = ˜P −
k + PC T (CP CT + R)−1CP
− PC T T T
k (CP CT + R)−1CP
− PC T (CP CT + R)−1Tk C
= A ˜Pk−1 AT + Q + PCT (Σ − TT
k Σ − ΣTk )CP ,
where Σ = (CP CT + R)−1 > 0.
Remark 3 The obtained iteration of the remote estimation
error covariance (19) when the system is under linear attack
is based on the steady-state assumption, i.e., ˜x−
0 = ˆx−
0
and ˜P −
0 = E[(x0 − ˆx−
0 )(x0 − ˆx−
0 )0
] = P . Otherwise, the
error covariance recursion at the remote estimator depends
on system initial state when the attack begins. However, the
analytical method and the obtained result are the same.
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publi
Transactions on Control of Network Systems
5
summarizes the evolution of the estimation error covariance
under such an attack.
Theorem 1 For the system in Fig. 1, the linear attack (13)
satisfying the feasibility constraint (14) remains undetected
by the false data detector. Moreover, the estimation error
covariance at the remote estimator follows the recursion
˜Pk = A ˜Pk−1 A0+ Q + PCT (Σ − TT
k Σ − ΣTk )CP , (19)
where Σ = (CP CT + R)−1.
Proof: The stealthiness of the proposed linear attack
strategy follows from the previous reasoning.
According to the process model (1)–(2) and the iteration of
state estimate (17)–(18), one has
xk − ˜x−
k = A(xk−1 − ˜xk−1 ) + wk−1 ,
xk − ˜xk = xk − ˜x−
k − K˜zk ,
from which the error covariance at the remote estimator side
can be obtained as
˜P −
k = E[(xk − ˜x−
k )(xk − ˜x−
k )T ]
= A ˜Pk−1 AT + Q,
˜Pk = E[(xk − ˜xk )(xk − ˜xk )T ]
= ˜P −
k + K(CP C T + R)K T
− E[(xk − ˜x−
k )˜zT
k K T ] − E[K ˜zk (xk − ˜x−
k )T ]. (20)
To calculate the last two terms of (20), we first evaluate
xk − ˜x−
k
= Axk−1 + wk−1 − A(˜x−
k−1 + K˜zk−1 )
= Ak x0 +
k−1X
i=0
Ai wk−1−i − Ak ˜x−
0 −
k−1X
i=0
Ai+1 K˜zk−1−i
= Ak (x0 − ˆx−
0 ) +
k−1X
i=0
Ai wk−1−i −
k−1X
i=0
Ai+1 K˜zk−1−i ,
(21)
where the last equality follows from the steady-state assump-
tion ˜x−
0 = ˆx−
0 . Since ˜zk is an i.i.d. Gaussian random variable,
we obtain that E[˜zi ˜zT
j ] = 0, ∀i 6= j. Thus, we are only
concerned of the correlation between the first two terms of (21)
and ˜zk . Then, based on
xk − ˆx−
k
= Axk−1 + wk−1 − A(ˆx−
k−1 + Kzk−1 )
= Axk−1 + wk−1 − A[ˆx−
k−1 + K(C(x k−1 − ˆx−
k−1 ) + vk−1 ))]
= A(I − KC)(x k−1 − ˆx−
k−1 ) + wk−1 − AKvk−1 , (22)
we can further represent ˜zk in the form of
˜zk = Tk zk + bk
= Tk C(xk − ˆx−
k ) + Tk vk + bk
= Tk CA(I − KC)(x k−1 − ˆx−
k−1 ) + Tk Cwk−1
− Tk CAKv k−1 + Tk vk + bk
= Tk C[A(I − KC)] k (x0 − ˆx−
0 )
+
k−1X
i=0
Tk C[A(I − KC)] i wk−1−i + V, (23)
where V = Tk vk + bk − P k−1
i=0 Tk C[A(I − KC)] i AKv k−1−i
is independent of the first two terms of (21). It now follows
that the second last term of (20) can be written as
E (xk − ˜x−
k )˜zT
k K T
= E
"
Ak (x0 − ˆx−
0 ) +
k−1X
i=0
Ai wk−1−i Tk C [A(I − KC)] k
(x0 − ˆx−
0 ) +
k−1X
i=0
Tk C [A(I − KC)] i wk−1−i
T
K T
#
= Ak E (x0 − ˆx−
0 )(x0 − ˆx−
0 )T (I − KC) T AT k
+
k−1X
i=0
Ai E wk−1−i wT
k−1−i (I − KC) T AT i CT T T
k K T
= Ak P (I − KC) T AT k
+
k−1X
i=0
Ai Q (I − KC) T AT i CT T T
k K T
= PC T T T
k K T , (24)
where the last equality is due to the fact that P is the unique
positive semi-definite fixed point of h ◦ ˜g, i.e.,
P = (h ◦ ˜g)n (P )
= [A(I − KC)] n P (AT )n +
n−1X
i=0
[A(I − KC)] i Q(AT )i
= An P [(I − KC) T AT ]n +
n−1X
i=0
Ai Q[(I − KC) T AT ]i .
Similarly, we obtain
E K˜zk (xk − ˜x−
k )T = KT k CP . (25)
Substituting (24) and (25) into (20), the error covariance at
the remote estimator is given by
˜Pk = ˜P −
k + PC T (CP CT + R)−1CP
− PC T T T
k (CP CT + R)−1CP
− PC T (CP CT + R)−1Tk C
= A ˜Pk−1 AT + Q + PCT (Σ − TT
k Σ − ΣTk )CP ,
where Σ = (CP CT + R)−1 > 0.
Remark 3 The obtained iteration of the remote estimation
error covariance (19) when the system is under linear attack
is based on the steady-state assumption, i.e., ˜x−
0 = ˆx−
0
and ˜P −
0 = E[(x0 − ˆx−
0 )(x0 − ˆx−
0 )0
] = P . Otherwise, the
error covariance recursion at the remote estimator depends
on system initial state when the attack begins. However, the
analytical method and the obtained result are the same.

2325-5870 (c) 2016 IEEE. Personal use is permitted, but republication/redistribution requires IEEE permission. See http://www.ieee.org/publication
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publi
Transactions on Control of Network Systems
6
B. Scalar Systems
For processes with scalar outputs ( m = 1), Tk is a scalar,
so the linear attack strategy and the corresponding feasibility
constraint become
˜zk = Tk zk + bk , (26)
L = P − T 2
k P ≥ 0. (27)
Hence, the parameters of the linear attack strategy should be
chosen as Tk ∈ [−1, 1]and L ∈ [0, P] . According to (19),
the error covariance at the remote estimator is
˜Pk = A ˜Pk−1 AT + Q + (1 − 2Tk )4, (28)
where 4 = PC T (CP CT +R)−1CP . Then the optimal linear
attack strategy which yields the largest error covariance is
obtained when Tk = −1and L = 0 , i.e., when ˜zk = −zk .
It is worth noticing that there are some interesting special
cases for the attack strategy (26):
1) ˜zk = zk : When Tk = 1, bk = 0, the error covariance is
recursively given as
˜Pk = A ˜Pk−1 AT + Q − 4
with the initial state ˜P0 = (I − KC)P = P − ∆ . It pro-
duces the same result with the steady-state Kalman filter,
which can be represented as Pk = (I−KC)(AP k−1 AT +
Q) = (I − KC)P = P − ∆ .
2) ˜zk = −z k : When Tk = −1 , bk = 0 , the attacker
launches the attack ˜zk = −zk and the corresponding error
covariance is
˜Pk = A ˜Pk−1AT + Q + 34.
3) ˜zk ∼ N (0, CP C T + R) : When Tk = 0 , bk ∼
N (0, CP CT + R), the attacker generates i.i.d. Gaussian
noise as an attack and the error covariance is
˜Pk = A ˜Pk−1 AT + Q + 4.
All the estimation error covariance iterates above converge if
the system is stable.
In the case that the remote estimator uses no data to update
its estimate, the error covariance is
˜Pk = A ˜Pk−1 AT + Q.
Hence, the optimal attack strategy Tk = −1 degrades the
system performance by adding 34 to the iteration of the error
covariance.
The optimal attack strategy for the multiple-output case
(m > 1) is more difficult to derive. The scalar case suggests
the conjecture Tk = −I. This motivates our investigations in
the following two subsections, where we show that it is indeed
true.
C. Numerical Solution of the Optimal Attack Strategy
The remote estimation error covariance under the linear
attack ˜zk = Tk zk +bk can be represented as Pk (Tk ) according
to (19), based on which we define the optimal attack strategy
T ∗
k as the one that yields the largest estimation error covari-
ance, i.e., for any other Tk , ˜Pk (T ∗
k )− ˜Pk (Tk ) is positive semi-
definite. Then the following proposition uses the trace of the
error covariance matrix as a metric to quantify the attack effect
formulates the problem of finding an optimal attack strategy
as a convex optimization problem, from which a numerical
solution can be easily obtained.
Proposition 1 The optimal attack strategy is given by the
solution of the convex optimization problem
min
Tk ∈Rm×m
tr(CP P CT ΣTk )
s.t. P Tk
T T
k P −1 ≥ 0. (29)
Proof: According to the iteration of the error covari-
ance (19) under linear deception attack, we obtain that
tr( ˜Pk ) = tr(A ˜Pk−1 AT + Q + PCT (Σ − TT
k Σ − ΣTk )CP )
= tr(Ak P [AT ]k ) +
k−1X
i=0
tr(Ai Q[AT ]i )
+
kX
i=0
tr(Ai (P CT (Σ − TT
i Σ − ΣTi )CP )[AT ]i ).
It can be observed that at time k, for any given system,
maximizing the trace of the error covariance matrix is equiv-
alent to maximizing the trace of the last term of (19). Since
tr(A + B) = tr(A) + tr(B), tr(ABCD) = tr(DABC) and
tr(X T Y ) = tr(XY T ), one has
tr(P CT [Σ − TT
k Σ − ΣTk ]CP )
= tr(P CT ΣCP ) − tr(P CT T T
k ΣCP ) − tr(P CT ΣTk CP )
= tr(P CT ΣCP ) − tr(ΣCP P CT T T
k ) − tr(CP P CT ΣTk )
= tr(P CT ΣCP ) − 2 tr(CP P CT ΣTk ), (30)
where Σ and P are semi-definite matrices.
Ignoring the constant term of (30), the problem of finding
the optimal attack strategy is equivalent to solving the opti-
mization problem
max
Tk ∈Rm×m
− tr(CP P CT ΣTk )
s.t. Tk PT T
k − P ≤ 0.
To solve this optimization problem, we use Schur comple-
ment to change the constraint to a linear matrix inequality:
min
Tk ∈Rm×m
tr(CP P CT ΣTk )
s.t. P Tk
T T
k P −1 ≥ 0.
Remark 4 Using the CVX toolbox [37] in MATLAB to solve
the optimization problem given in (29), we can find a numer-
ical solution based on SDP.
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publi
Transactions on Control of Network Systems
6
B. Scalar Systems
For processes with scalar outputs ( m = 1), Tk is a scalar,
so the linear attack strategy and the corresponding feasibility
constraint become
˜zk = Tk zk + bk , (26)
L = P − T 2
k P ≥ 0. (27)
Hence, the parameters of the linear attack strategy should be
chosen as Tk ∈ [−1, 1]and L ∈ [0, P] . According to (19),
the error covariance at the remote estimator is
˜Pk = A ˜Pk−1 AT + Q + (1 − 2Tk )4, (28)
where 4 = PC T (CP CT +R)−1CP . Then the optimal linear
attack strategy which yields the largest error covariance is
obtained when Tk = −1and L = 0 , i.e., when ˜zk = −zk .
It is worth noticing that there are some interesting special
cases for the attack strategy (26):
1) ˜zk = zk : When Tk = 1, bk = 0, the error covariance is
recursively given as
˜Pk = A ˜Pk−1 AT + Q − 4
with the initial state ˜P0 = (I − KC)P = P − ∆ . It pro-
duces the same result with the steady-state Kalman filter,
which can be represented as Pk = (I−KC)(AP k−1 AT +
Q) = (I − KC)P = P − ∆ .
2) ˜zk = −z k : When Tk = −1 , bk = 0 , the attacker
launches the attack ˜zk = −zk and the corresponding error
covariance is
˜Pk = A ˜Pk−1AT + Q + 34.
3) ˜zk ∼ N (0, CP C T + R) : When Tk = 0 , bk ∼
N (0, CP CT + R), the attacker generates i.i.d. Gaussian
noise as an attack and the error covariance is
˜Pk = A ˜Pk−1 AT + Q + 4.
All the estimation error covariance iterates above converge if
the system is stable.
In the case that the remote estimator uses no data to update
its estimate, the error covariance is
˜Pk = A ˜Pk−1 AT + Q.
Hence, the optimal attack strategy Tk = −1 degrades the
system performance by adding 34 to the iteration of the error
covariance.
The optimal attack strategy for the multiple-output case
(m > 1) is more difficult to derive. The scalar case suggests
the conjecture Tk = −I. This motivates our investigations in
the following two subsections, where we show that it is indeed
true.
C. Numerical Solution of the Optimal Attack Strategy
The remote estimation error covariance under the linear
attack ˜zk = Tk zk +bk can be represented as Pk (Tk ) according
to (19), based on which we define the optimal attack strategy
T ∗
k as the one that yields the largest estimation error covari-
ance, i.e., for any other Tk , ˜Pk (T ∗
k )− ˜Pk (Tk ) is positive semi-
definite. Then the following proposition uses the trace of the
error covariance matrix as a metric to quantify the attack effect
formulates the problem of finding an optimal attack strategy
as a convex optimization problem, from which a numerical
solution can be easily obtained.
Proposition 1 The optimal attack strategy is given by the
solution of the convex optimization problem
min
Tk ∈Rm×m
tr(CP P CT ΣTk )
s.t. P Tk
T T
k P −1 ≥ 0. (29)
Proof: According to the iteration of the error covari-
ance (19) under linear deception attack, we obtain that
tr( ˜Pk ) = tr(A ˜Pk−1 AT + Q + PCT (Σ − TT
k Σ − ΣTk )CP )
= tr(Ak P [AT ]k ) +
k−1X
i=0
tr(Ai Q[AT ]i )
+
kX
i=0
tr(Ai (P CT (Σ − TT
i Σ − ΣTi )CP )[AT ]i ).
It can be observed that at time k, for any given system,
maximizing the trace of the error covariance matrix is equiv-
alent to maximizing the trace of the last term of (19). Since
tr(A + B) = tr(A) + tr(B), tr(ABCD) = tr(DABC) and
tr(X T Y ) = tr(XY T ), one has
tr(P CT [Σ − TT
k Σ − ΣTk ]CP )
= tr(P CT ΣCP ) − tr(P CT T T
k ΣCP ) − tr(P CT ΣTk CP )
= tr(P CT ΣCP ) − tr(ΣCP P CT T T
k ) − tr(CP P CT ΣTk )
= tr(P CT ΣCP ) − 2 tr(CP P CT ΣTk ), (30)
where Σ and P are semi-definite matrices.
Ignoring the constant term of (30), the problem of finding
the optimal attack strategy is equivalent to solving the opti-
mization problem
max
Tk ∈Rm×m
− tr(CP P CT ΣTk )
s.t. Tk PT T
k − P ≤ 0.
To solve this optimization problem, we use Schur comple-
ment to change the constraint to a linear matrix inequality:
min
Tk ∈Rm×m
tr(CP P CT ΣTk )
s.t. P Tk
T T
k P −1 ≥ 0.
Remark 4 Using the CVX toolbox [37] in MATLAB to solve
the optimization problem given in (29), we can find a numer-
ical solution based on SDP.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2325-5870 (c) 2016 IEEE. Personal use is permitted, but republication/redistribution requires IEEE permission. See http://www.ieee.org/publication
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publi
Transactions on Control of Network Systems
7
D. Optimal Attack Strategy
Based on the conjecture of the optimal attack strategy from
the scalar case and the numerical solutions, we aim to find out
a closed-loop expression of the optimal Tk . The main result
is summarized in the following theorem.
Theorem 2 For the system in Fig. 1 with the linear at-
tack (13), Tk = −I and bk = 0 is the optimal linear attack
strategy in the sense that it yields the largest estimation error
covariance.
Proof: The iteration of estimation error covariance at the
remote estimator under the linear attack ˜zk = Tk zk + bk is
given by (19). Obviously, the optimal attack strategy which
maximizes ˜Pk is equivalent to the strategy which maximizes
P CT (Σ−T T
k Σ−ΣT k )CP . We then derive the optimal attack
strategy based on the correspondence between the optimal
attack and the optimal estimate.
According to the attack strategy (13) and the iteration
equation 18, one has
˜xk = ˜x−
k + K˜zk
= ˜x−
k + K(Tk zk + bk )
= ˜x−
k + K[Tk + bk (zT
k zk )−1zT
k ]zk
= ˜x−
k + ˜K k zk , (31)
where ˜K k = K[T k + bk (zT
k zk )−1zT
k ]. Note that the state
estimate at time k is a linear combination of all the past
innovations zi , i ∈ {1, 2, . . . , k}. Due to the orthogonality
between zi and zj , i.e., E[zi zj ] = 0, ∀i 6= j, whether there
exists malicious attacks during the past time instants or not, the
optimal state estimate at time k which minimizes the remote
estimation error covariance is obtained when ˜K k = K . This
corresponds to the estimation error covariance when Tk = I
and bk = 0, i.e.,
˜Pk = A ˜Pk−1AT + Q − PCT ΣCP .
It other words, Tk = I yields the smallest error covariance at
time k among all attacks given by (13).
Hence, if we denote Tk1 = I and note that
Σ − TT
k1Σ − ΣTk1 = −Σ,
for any Tk2 = T k1 + M , where M is an arbitrary matrix
satisfying the constraint
Tk2PT T
k2 = (I + M)P(I + M) T ≤ P, (32)
the following inequality
P CT [Σ − TT
k2Σ − ΣTk2 − (Σ − TT
k1Σ − ΣTk1)]CP
= PC T [Σ − (I + M)T Σ − Σ(I + M) + Σ]CP
= PC T [−MT Σ − ΣM]CP
≥ 0 (33)
must be true since Tk = I is the optimal estimate which yields
the smallest error covariance.
Now we obtain a one-to-one correspondence in finding the
optimal attack strategy. Denote Tk3 = −I and note that
Σ − TT
k3Σ − ΣTk3 = 3Σ.
For any Tk4 = T k3 − M , where M is an arbitrary matrix
satisfying the constraint
Tk4PT T
k4 = (−I − M)P(−I − M) T
= (I + M)P(I + M) T ≤ P, (34)
we obtain that
P CT [Σ − TT
k3Σ − ΣTk3 − (Σ − TT
k4Σ − ΣTk4)]CP
= PC T [3Σ − Σ + (−I − M)T Σ + Σ(−I − M)]CP
= PC T [−MT Σ − ΣM]CP
≥ 0 (35)
from (33). This means that for any Tk matrix different from
−I , the difference between the two error covariances is always
positive semi-definite. Therefore, Tk = −I is the optimal
attack that yields the largest error covariance.
V. SIMULATION EXAMPLES
To demonstrate the analytical results, we present some
numerical simulations in this section. We compare the attack
strategies ˜zk = −zk and ˜zk ∼ N (0, CP CT + R) with the
extreme case where the remote estimator does not use any data
to update its state estimate. We consider a stable process with
parameters A = 0.8, C = 1.2, Q = 1, R = 1and an unstable
process with parameters A = 1.02, C = 1.2, Q = 1, R = 1.
A. Stable Process under Linear Attack
For the stable process, the simulation results of the remote
state estimate and estimation error covariance under different
attacks are shown in Fig. 2 and Fig. 3, respectively. Dur-
ing time periods [0, 20], [40, 60]and [80, 100], the remote
estimator runs a Kalman filter and enters the steady state.
The attacker uses the false data ˜zk = −zk during the time
period [60, 80]and randomly generates an i.i.d. Gaussian
innovation ˜zk ∼ N (0, CP CT + R) during the time period
[100, 120]to launch cyber attack. Since the false data detector
cannot successfully detect the existence of the attack, the
remote estimator still uses the Kalman filter to update its state
estimate and the corresponding error covariance, which are
the green dash-dot lines in Fig. 2 and Fig. 3. However, the
real state estimate deviates from the true state and leads to
large estimation error, which can be seen by the red dashed
lines in Fig. 2 and Fig. 3. To compare different attack effects,
the extreme case where the remote estimator uses no data
to update its state estimate is shown in Fig. 2 and Fig. 3
during the time period [20, 40]. It can be observed that the
error covariance under the ˜zk = −zk attack is larger than that
under the ˜zk ∼ N (0, CP CT +R) attack, and the latter is larger
than using no data. Hence, using bad data is worse than using
no data and Tk = −I is the optimal linear deception attack
strategy. Moreover, the error covariance converges when the
process is stable.
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publi
Transactions on Control of Network Systems
7
D. Optimal Attack Strategy
Based on the conjecture of the optimal attack strategy from
the scalar case and the numerical solutions, we aim to find out
a closed-loop expression of the optimal Tk . The main result
is summarized in the following theorem.
Theorem 2 For the system in Fig. 1 with the linear at-
tack (13), Tk = −I and bk = 0 is the optimal linear attack
strategy in the sense that it yields the largest estimation error
covariance.
Proof: The iteration of estimation error covariance at the
remote estimator under the linear attack ˜zk = Tk zk + bk is
given by (19). Obviously, the optimal attack strategy which
maximizes ˜Pk is equivalent to the strategy which maximizes
P CT (Σ−T T
k Σ−ΣT k )CP . We then derive the optimal attack
strategy based on the correspondence between the optimal
attack and the optimal estimate.
According to the attack strategy (13) and the iteration
equation 18, one has
˜xk = ˜x−
k + K˜zk
= ˜x−
k + K(Tk zk + bk )
= ˜x−
k + K[Tk + bk (zT
k zk )−1zT
k ]zk
= ˜x−
k + ˜K k zk , (31)
where ˜K k = K[T k + bk (zT
k zk )−1zT
k ]. Note that the state
estimate at time k is a linear combination of all the past
innovations zi , i ∈ {1, 2, . . . , k}. Due to the orthogonality
between zi and zj , i.e., E[zi zj ] = 0, ∀i 6= j, whether there
exists malicious attacks during the past time instants or not, the
optimal state estimate at time k which minimizes the remote
estimation error covariance is obtained when ˜K k = K . This
corresponds to the estimation error covariance when Tk = I
and bk = 0, i.e.,
˜Pk = A ˜Pk−1AT + Q − PCT ΣCP .
It other words, Tk = I yields the smallest error covariance at
time k among all attacks given by (13).
Hence, if we denote Tk1 = I and note that
Σ − TT
k1Σ − ΣTk1 = −Σ,
for any Tk2 = T k1 + M , where M is an arbitrary matrix
satisfying the constraint
Tk2PT T
k2 = (I + M)P(I + M) T ≤ P, (32)
the following inequality
P CT [Σ − TT
k2Σ − ΣTk2 − (Σ − TT
k1Σ − ΣTk1)]CP
= PC T [Σ − (I + M)T Σ − Σ(I + M) + Σ]CP
= PC T [−MT Σ − ΣM]CP
≥ 0 (33)
must be true since Tk = I is the optimal estimate which yields
the smallest error covariance.
Now we obtain a one-to-one correspondence in finding the
optimal attack strategy. Denote Tk3 = −I and note that
Σ − TT
k3Σ − ΣTk3 = 3Σ.
For any Tk4 = T k3 − M , where M is an arbitrary matrix
satisfying the constraint
Tk4PT T
k4 = (−I − M)P(−I − M) T
= (I + M)P(I + M) T ≤ P, (34)
we obtain that
P CT [Σ − TT
k3Σ − ΣTk3 − (Σ − TT
k4Σ − ΣTk4)]CP
= PC T [3Σ − Σ + (−I − M)T Σ + Σ(−I − M)]CP
= PC T [−MT Σ − ΣM]CP
≥ 0 (35)
from (33). This means that for any Tk matrix different from
−I , the difference between the two error covariances is always
positive semi-definite. Therefore, Tk = −I is the optimal
attack that yields the largest error covariance.
V. SIMULATION EXAMPLES
To demonstrate the analytical results, we present some
numerical simulations in this section. We compare the attack
strategies ˜zk = −zk and ˜zk ∼ N (0, CP CT + R) with the
extreme case where the remote estimator does not use any data
to update its state estimate. We consider a stable process with
parameters A = 0.8, C = 1.2, Q = 1, R = 1and an unstable
process with parameters A = 1.02, C = 1.2, Q = 1, R = 1.
A. Stable Process under Linear Attack
For the stable process, the simulation results of the remote
state estimate and estimation error covariance under different
attacks are shown in Fig. 2 and Fig. 3, respectively. Dur-
ing time periods [0, 20], [40, 60]and [80, 100], the remote
estimator runs a Kalman filter and enters the steady state.
The attacker uses the false data ˜zk = −zk during the time
period [60, 80]and randomly generates an i.i.d. Gaussian
innovation ˜zk ∼ N (0, CP CT + R) during the time period
[100, 120]to launch cyber attack. Since the false data detector
cannot successfully detect the existence of the attack, the
remote estimator still uses the Kalman filter to update its state
estimate and the corresponding error covariance, which are
the green dash-dot lines in Fig. 2 and Fig. 3. However, the
real state estimate deviates from the true state and leads to
large estimation error, which can be seen by the red dashed
lines in Fig. 2 and Fig. 3. To compare different attack effects,
the extreme case where the remote estimator uses no data
to update its state estimate is shown in Fig. 2 and Fig. 3
during the time period [20, 40]. It can be observed that the
error covariance under the ˜zk = −zk attack is larger than that
under the ˜zk ∼ N (0, CP CT +R) attack, and the latter is larger
than using no data. Hence, using bad data is worse than using
no data and Tk = −I is the optimal linear deception attack
strategy. Moreover, the error covariance converges when the
process is stable.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
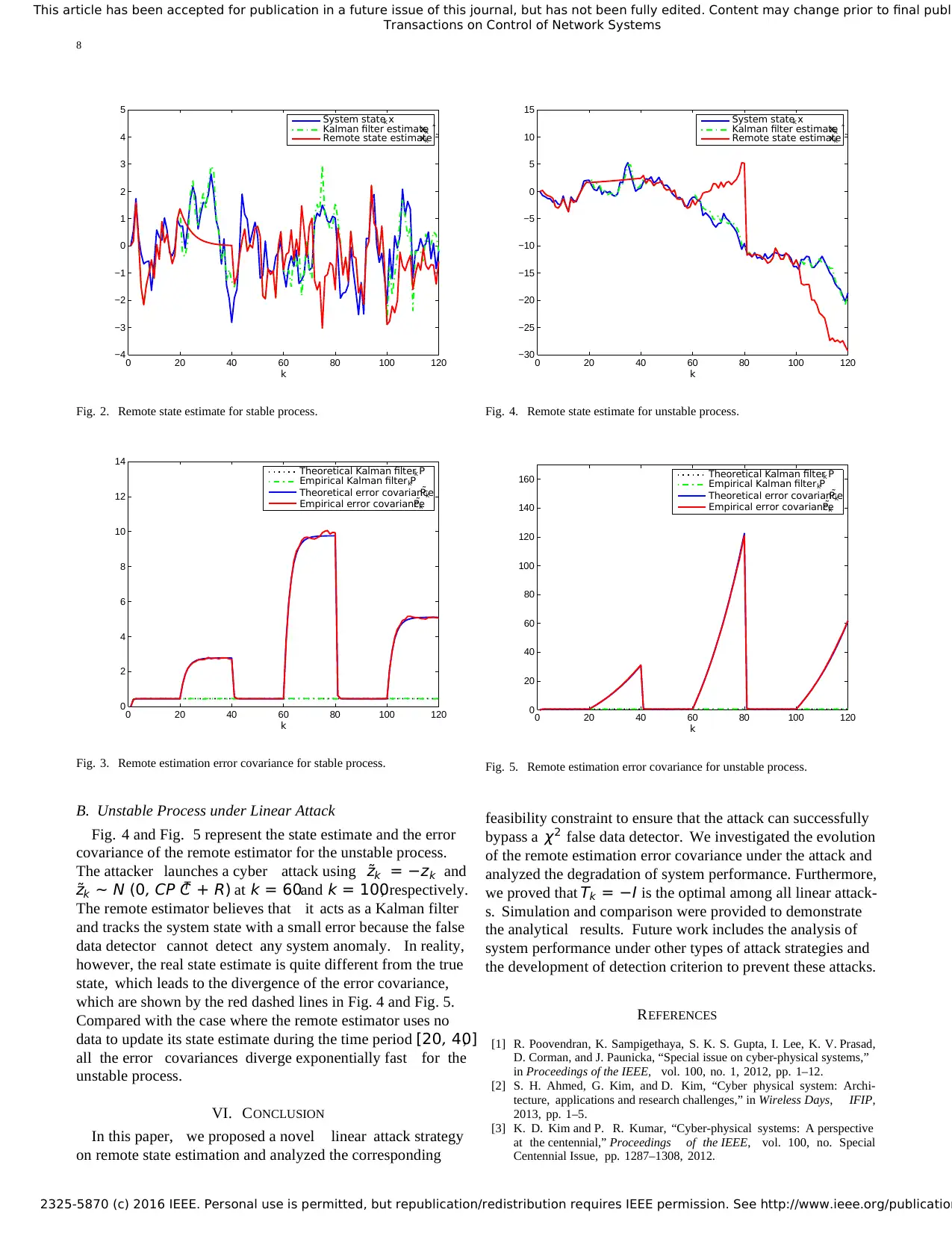
2325-5870 (c) 2016 IEEE. Personal use is permitted, but republication/redistribution requires IEEE permission. See http://www.ieee.org/publication
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publi
Transactions on Control of Network Systems
8
0 20 40 60 80 100 120
−4
−3
−2
−1
0
1
2
3
4
5
k
System state xk
Kalman filter estimate ˆxk
Remote state estimate ˜xk
Fig. 2. Remote state estimate for stable process.
0 20 40 60 80 100 120
0
2
4
6
8
10
12
14
k
Theoretical Kalman filter Pk
Empirical Kalman filter Pk
Theoretical error covariance˜Pk
Empirical error covariance˜Pk
Fig. 3. Remote estimation error covariance for stable process.
B. Unstable Process under Linear Attack
Fig. 4 and Fig. 5 represent the state estimate and the error
covariance of the remote estimator for the unstable process.
The attacker launches a cyber attack using ˜zk = −zk and
˜zk ∼ N (0, CP CT + R) at k = 60and k = 100, respectively.
The remote estimator believes that it acts as a Kalman filter
and tracks the system state with a small error because the false
data detector cannot detect any system anomaly. In reality,
however, the real state estimate is quite different from the true
state, which leads to the divergence of the error covariance,
which are shown by the red dashed lines in Fig. 4 and Fig. 5.
Compared with the case where the remote estimator uses no
data to update its state estimate during the time period [20, 40],
all the error covariances diverge exponentially fast for the
unstable process.
VI. CONCLUSION
In this paper, we proposed a novel linear attack strategy
on remote state estimation and analyzed the corresponding
0 20 40 60 80 100 120
−30
−25
−20
−15
−10
−5
0
5
10
15
k
System state xk
Kalman filter estimate ˆxk
Remote state estimate ˜xk
Fig. 4. Remote state estimate for unstable process.
0 20 40 60 80 100 120
0
20
40
60
80
100
120
140
160
k
Theoretical Kalman filter Pk
Empirical Kalman filter Pk
Theoretical error covariance˜Pk
Empirical error covariance˜Pk
Fig. 5. Remote estimation error covariance for unstable process.
feasibility constraint to ensure that the attack can successfully
bypass a χ2 false data detector. We investigated the evolution
of the remote estimation error covariance under the attack and
analyzed the degradation of system performance. Furthermore,
we proved that Tk = −I is the optimal among all linear attack-
s. Simulation and comparison were provided to demonstrate
the analytical results. Future work includes the analysis of
system performance under other types of attack strategies and
the development of detection criterion to prevent these attacks.
REFERENCES
[1] R. Poovendran, K. Sampigethaya, S. K. S. Gupta, I. Lee, K. V. Prasad,
D. Corman, and J. Paunicka, “Special issue on cyber-physical systems,”
in Proceedings of the IEEE, vol. 100, no. 1, 2012, pp. 1–12.
[2] S. H. Ahmed, G. Kim, and D. Kim, “Cyber physical system: Archi-
tecture, applications and research challenges,” in Wireless Days, IFIP,
2013, pp. 1–5.
[3] K. D. Kim and P. R. Kumar, “Cyber-physical systems: A perspective
at the centennial,” Proceedings of the IEEE, vol. 100, no. Special
Centennial Issue, pp. 1287–1308, 2012.
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publi
Transactions on Control of Network Systems
8
0 20 40 60 80 100 120
−4
−3
−2
−1
0
1
2
3
4
5
k
System state xk
Kalman filter estimate ˆxk
Remote state estimate ˜xk
Fig. 2. Remote state estimate for stable process.
0 20 40 60 80 100 120
0
2
4
6
8
10
12
14
k
Theoretical Kalman filter Pk
Empirical Kalman filter Pk
Theoretical error covariance˜Pk
Empirical error covariance˜Pk
Fig. 3. Remote estimation error covariance for stable process.
B. Unstable Process under Linear Attack
Fig. 4 and Fig. 5 represent the state estimate and the error
covariance of the remote estimator for the unstable process.
The attacker launches a cyber attack using ˜zk = −zk and
˜zk ∼ N (0, CP CT + R) at k = 60and k = 100, respectively.
The remote estimator believes that it acts as a Kalman filter
and tracks the system state with a small error because the false
data detector cannot detect any system anomaly. In reality,
however, the real state estimate is quite different from the true
state, which leads to the divergence of the error covariance,
which are shown by the red dashed lines in Fig. 4 and Fig. 5.
Compared with the case where the remote estimator uses no
data to update its state estimate during the time period [20, 40],
all the error covariances diverge exponentially fast for the
unstable process.
VI. CONCLUSION
In this paper, we proposed a novel linear attack strategy
on remote state estimation and analyzed the corresponding
0 20 40 60 80 100 120
−30
−25
−20
−15
−10
−5
0
5
10
15
k
System state xk
Kalman filter estimate ˆxk
Remote state estimate ˜xk
Fig. 4. Remote state estimate for unstable process.
0 20 40 60 80 100 120
0
20
40
60
80
100
120
140
160
k
Theoretical Kalman filter Pk
Empirical Kalman filter Pk
Theoretical error covariance˜Pk
Empirical error covariance˜Pk
Fig. 5. Remote estimation error covariance for unstable process.
feasibility constraint to ensure that the attack can successfully
bypass a χ2 false data detector. We investigated the evolution
of the remote estimation error covariance under the attack and
analyzed the degradation of system performance. Furthermore,
we proved that Tk = −I is the optimal among all linear attack-
s. Simulation and comparison were provided to demonstrate
the analytical results. Future work includes the analysis of
system performance under other types of attack strategies and
the development of detection criterion to prevent these attacks.
REFERENCES
[1] R. Poovendran, K. Sampigethaya, S. K. S. Gupta, I. Lee, K. V. Prasad,
D. Corman, and J. Paunicka, “Special issue on cyber-physical systems,”
in Proceedings of the IEEE, vol. 100, no. 1, 2012, pp. 1–12.
[2] S. H. Ahmed, G. Kim, and D. Kim, “Cyber physical system: Archi-
tecture, applications and research challenges,” in Wireless Days, IFIP,
2013, pp. 1–5.
[3] K. D. Kim and P. R. Kumar, “Cyber-physical systems: A perspective
at the centennial,” Proceedings of the IEEE, vol. 100, no. Special
Centennial Issue, pp. 1287–1308, 2012.

2325-5870 (c) 2016 IEEE. Personal use is permitted, but republication/redistribution requires IEEE permission. See http://www.ieee.org/publication
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publi
Transactions on Control of Network Systems
9
[4] E. A. Lee, “Cyber physical systems: Design challenges,” in 11th IEEE
International Symposium on Object Oriented Real-Time Distributed
Computing, 2008, pp. 363–369.
[5] H. Sandberg, S. Amin, and K. H. Johansson, “Cyberphysical security in
networked control systems: An introduction to the issue,” IEEE Control
Systems Magazine, vol. 35, no. 1, pp. 20–23, 2015.
[6] Y. Mo, T. H. Kim, K. Brancik, D. Dickinson, H. Lee, A. Perrig, and
B. Sinopoli, “Cyber-physical security of a smart grid infrastructure,”
Proceedings of the IEEE, vol. 100, no. 1, pp. 195–209, 2012.
[7] A. A. Cardenas, S. Amin, and S. Sastry, “Research challenges for the
security of control systems.” in HotSec: Procceedings of 3rd Conference
in Hot Toptics in Secuity. Berkeley, CA, USA, 2008, pp. 1–6.
[8] A. Teixeira, D. P´erez, H. Sandberg, and K. H. Johansson, “Attack models
and scenarios for networked control systems,” in Proceedings of the
1st International Conference on High Confidence Networked Systems.
ACM, 2012, pp. 55–64.
[9] A. A. Cardenas, S. Amin, and S. Sastry, “Secure control: Towards
survivable cyber-physical systems,” 28th International Conference on
Distributed Computing Workshops, pp. 495–500, 2008.
[10] S. Amin, A. A. C ´ardenas, and S. S. Sastry, “Safe and secure networked
control systems under denial-of-service attacks,” in Hybrid Systems:
Computation and Control. Springer, 2009, pp. 31–45.
[11] A. Gupta, C. Langbort, and T. Basar, “Optimal control in the presence
of an intelligent jammer with limited actions,” in 49th IEEE Conference
on Decision and Control, 2010, pp. 1096–1101.
[12] M. H. Manshaei, Q. Zhu, T. Alpcan, T. Bacs¸ar, and J. P. Hubaux, “Game
theory meets network security and privacy,” ACM Computing Surveys,
vol. 45, no. 3, pp. 25:1–39, 2013.
[13] Y. Li, L. Shi, P. Cheng, J. Chen, and D. E. Quevedo, “Jamming attacks
on remote state estimation in cyber-physical systems: A game-theoretic
approach,” IEEE Transactions on Automatic Control, vol. 60, no. 10,
pp. 2831–2836, 2015.
[14] A. Agah and S. K. Das, “Preventing dos attacks in wireless sensor
networks: A repeated game theory approach,” International Journal of
Network Security, vol. 5, no. 2, pp. 145–153, 2007.
[15] Y. Mo and B. Sinopoli, “Secure control against replay attacks,” in
47th Annual Allerton Conference on Communication, Control, and
Computing, 2009, pp. 911–918.
[16] ——, “Integrity attacks on cyber-physical systems,” in Proceedings
of the 1st International Conference on High Confidence Networked
Systems. ACM, 2012, pp. 47–54.
[17] F. Miao, M. Pajic, and G. J. Pappas, “Stochastic game approach for
replay attack detection,” in 52nd Annual Conference on Decision and
Control, 2013, pp. 1854–1859.
[18] Y. Liu, P. Ning, and M. K. Reiter, “False data injection attacks against
state estimation in electric power grids,” ACM Transactions on Informa-
tion and System Security, vol. 14, no. 1, pp. 13–24, 2011.
[19] H. Sandberg, A. Teixeira, and K. H. Johansson, “On security indices
for state estimators in power networks,” in First Workshop on Secure
Control Systems, Stockholm, Sweden, 2010.
[20] A. Teixeira, K. C. Sou, H. Sandberg, and K. H. Johansson, “Secure
control systems: A quantitative risk management approach,” IEEE
Control Systems Magazine, vol. 35, no. 1, pp. 24–45, 2015.
[21] L. Xie, Y. Mo, and B. Sinopoli, “Integrity data attacks in power market
operations,” IEEE Transactions on Smart Grid, vol. 2, no. 4, pp. 659–
666, 2011.
[22] J. Kim, L. Tong, and R. J. Thomas, “Subspace methods for data attack on
state estimation: A data driven approach,” IEEE Transactions on Signal
Processing, vol. 63, no. 5, pp. 1102–1114, 2014.
[23] F. Pasqualetti, F. Dorfler, and F. Bullo, “Cyber-physical attacks in power
networks: Models, fundamental limitations and monitor design,” in
50th IEEE Conference on Decision and Control and European Control
Conference, 2011, pp. 2195–2201.
[24] D. Shi, T. Chen, and M. Darouach, “Event-based state estimation of
linear dynamic systems with unknown exogenous inputs,” Automatica,
vol. 69, pp. 275–288, 2016.
[25] D. Shi, R. J. Elliott, and T. Chen, “On finite-state stochastic modeling
and secure estimation of cyber-physical systems,” IEEE Transactions on
Automatic Control, vol. PP, no. 99, p. 1, 2016.
[26] F. L. Lewis et al., “Wireless sensor networks,” Smart environments:
technologies, protocols, and applications, pp. 11–46, 2004.
[27] R. Frank, Understanding smart sensors. Artech House, 2013.
[28] B. D. O. Anderson and J. B. Moore, Optimal filtering. Dover
Publications, Mineola, N.Y, 2005.
[29] J. Favenne, “Smart sensors in industry,” Journal of Physics E: Scientific
Instruments, vol. 20, no. 9, pp. 1087–1090, 1987.
[30] R. K. Mehra and J. Peschon, “An innovations approach to fault detection
and diagnosis in dynamic systems,” Automatica, vol. 7, no. 5, pp. 637–
640, 1971.
[31] A. S. Willsky, “A survey of design methods for failure detection in
dynamic systems,” Automatica, vol. 12, no. 6, pp. 601–611, 1976.
[32] Y. Mo, S. Weerakkody, and B. Sinopoli, “Physical authentication of con-
trol systems: designing watermarked control inputs to detect counterfeit
sensor outputs,” IEEE Control Systems Magazine, vol. 35, no. 1, pp.
93–109, 2015.
[33] R. S. Smith, “Covert misappropriation of networked control systems:
Presenting a feedback structure,” IEEE Control Systems Magazine,
vol. 35, no. 1, pp. 82–92, 2015.
[34] U. Meyer and S. Wetzel, “A man-in-the-middle attack on UMTS,” in
Proceedings of the 3rd ACM workshop on Wireless security, 2004, pp.
90–97.
[35] F. Callegati, W. Cerroni, and M. Ramilli, “Man-in-the-middle attack to
the HTTPS protocol,” IEEE Security and Privacy Magazine, no. 1, pp.
78–81, 2009.
[36] D. Cox and D. Hinkley, Theoretical statistics. New York: Chapman
and Hall, distributed in U.S. by Halsted Press, 1979.
[37] M. Grant, S. Boyd, V. Blondel, and H. Kimura, CVX: Matlab Software
for Disciplined Convex Programming, version 2.0, 2011.
Ziyang Guo was born in Henan, China, in 1992. She
received the B.Eng. degree (Honors) in College of
Control Science and Engineering from Zhejiang U-
niversity, Hangzhou, China, in 2014. She is currently
pursuing the Ph.D. degree in Electronic and Com-
puter Engineering at the Hong Kong University of
Science and Technology, Hong Kong. Her research
interests include cyber-physical system security, s-
tate estimation and wireless sensor network.
Dawei Shi received his B.Eng. degree in Electrical
Engineering and Automation from the Beijing Insti-
tute of Technology in 2008. He received his Ph.D.
degree in Control Systems from the University of
Alberta in 2014. Since December 2014, he has been
appointed as an Associate Professor at the School of
Automation, Beijing Institute of Technology, China.
His research interests include event-based control
and estimation, robust model predictive control and
tuning, and wireless sensor networks. He is a review-
er for a number of international journals, including
IEEE Transactions on Automatic Control, Automatica, and Systems & Con-
trol Letters. In 2009, he received the Best Student Paper Award in IEEE
International Conference on Automation and Logistics.
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publi
Transactions on Control of Network Systems
9
[4] E. A. Lee, “Cyber physical systems: Design challenges,” in 11th IEEE
International Symposium on Object Oriented Real-Time Distributed
Computing, 2008, pp. 363–369.
[5] H. Sandberg, S. Amin, and K. H. Johansson, “Cyberphysical security in
networked control systems: An introduction to the issue,” IEEE Control
Systems Magazine, vol. 35, no. 1, pp. 20–23, 2015.
[6] Y. Mo, T. H. Kim, K. Brancik, D. Dickinson, H. Lee, A. Perrig, and
B. Sinopoli, “Cyber-physical security of a smart grid infrastructure,”
Proceedings of the IEEE, vol. 100, no. 1, pp. 195–209, 2012.
[7] A. A. Cardenas, S. Amin, and S. Sastry, “Research challenges for the
security of control systems.” in HotSec: Procceedings of 3rd Conference
in Hot Toptics in Secuity. Berkeley, CA, USA, 2008, pp. 1–6.
[8] A. Teixeira, D. P´erez, H. Sandberg, and K. H. Johansson, “Attack models
and scenarios for networked control systems,” in Proceedings of the
1st International Conference on High Confidence Networked Systems.
ACM, 2012, pp. 55–64.
[9] A. A. Cardenas, S. Amin, and S. Sastry, “Secure control: Towards
survivable cyber-physical systems,” 28th International Conference on
Distributed Computing Workshops, pp. 495–500, 2008.
[10] S. Amin, A. A. C ´ardenas, and S. S. Sastry, “Safe and secure networked
control systems under denial-of-service attacks,” in Hybrid Systems:
Computation and Control. Springer, 2009, pp. 31–45.
[11] A. Gupta, C. Langbort, and T. Basar, “Optimal control in the presence
of an intelligent jammer with limited actions,” in 49th IEEE Conference
on Decision and Control, 2010, pp. 1096–1101.
[12] M. H. Manshaei, Q. Zhu, T. Alpcan, T. Bacs¸ar, and J. P. Hubaux, “Game
theory meets network security and privacy,” ACM Computing Surveys,
vol. 45, no. 3, pp. 25:1–39, 2013.
[13] Y. Li, L. Shi, P. Cheng, J. Chen, and D. E. Quevedo, “Jamming attacks
on remote state estimation in cyber-physical systems: A game-theoretic
approach,” IEEE Transactions on Automatic Control, vol. 60, no. 10,
pp. 2831–2836, 2015.
[14] A. Agah and S. K. Das, “Preventing dos attacks in wireless sensor
networks: A repeated game theory approach,” International Journal of
Network Security, vol. 5, no. 2, pp. 145–153, 2007.
[15] Y. Mo and B. Sinopoli, “Secure control against replay attacks,” in
47th Annual Allerton Conference on Communication, Control, and
Computing, 2009, pp. 911–918.
[16] ——, “Integrity attacks on cyber-physical systems,” in Proceedings
of the 1st International Conference on High Confidence Networked
Systems. ACM, 2012, pp. 47–54.
[17] F. Miao, M. Pajic, and G. J. Pappas, “Stochastic game approach for
replay attack detection,” in 52nd Annual Conference on Decision and
Control, 2013, pp. 1854–1859.
[18] Y. Liu, P. Ning, and M. K. Reiter, “False data injection attacks against
state estimation in electric power grids,” ACM Transactions on Informa-
tion and System Security, vol. 14, no. 1, pp. 13–24, 2011.
[19] H. Sandberg, A. Teixeira, and K. H. Johansson, “On security indices
for state estimators in power networks,” in First Workshop on Secure
Control Systems, Stockholm, Sweden, 2010.
[20] A. Teixeira, K. C. Sou, H. Sandberg, and K. H. Johansson, “Secure
control systems: A quantitative risk management approach,” IEEE
Control Systems Magazine, vol. 35, no. 1, pp. 24–45, 2015.
[21] L. Xie, Y. Mo, and B. Sinopoli, “Integrity data attacks in power market
operations,” IEEE Transactions on Smart Grid, vol. 2, no. 4, pp. 659–
666, 2011.
[22] J. Kim, L. Tong, and R. J. Thomas, “Subspace methods for data attack on
state estimation: A data driven approach,” IEEE Transactions on Signal
Processing, vol. 63, no. 5, pp. 1102–1114, 2014.
[23] F. Pasqualetti, F. Dorfler, and F. Bullo, “Cyber-physical attacks in power
networks: Models, fundamental limitations and monitor design,” in
50th IEEE Conference on Decision and Control and European Control
Conference, 2011, pp. 2195–2201.
[24] D. Shi, T. Chen, and M. Darouach, “Event-based state estimation of
linear dynamic systems with unknown exogenous inputs,” Automatica,
vol. 69, pp. 275–288, 2016.
[25] D. Shi, R. J. Elliott, and T. Chen, “On finite-state stochastic modeling
and secure estimation of cyber-physical systems,” IEEE Transactions on
Automatic Control, vol. PP, no. 99, p. 1, 2016.
[26] F. L. Lewis et al., “Wireless sensor networks,” Smart environments:
technologies, protocols, and applications, pp. 11–46, 2004.
[27] R. Frank, Understanding smart sensors. Artech House, 2013.
[28] B. D. O. Anderson and J. B. Moore, Optimal filtering. Dover
Publications, Mineola, N.Y, 2005.
[29] J. Favenne, “Smart sensors in industry,” Journal of Physics E: Scientific
Instruments, vol. 20, no. 9, pp. 1087–1090, 1987.
[30] R. K. Mehra and J. Peschon, “An innovations approach to fault detection
and diagnosis in dynamic systems,” Automatica, vol. 7, no. 5, pp. 637–
640, 1971.
[31] A. S. Willsky, “A survey of design methods for failure detection in
dynamic systems,” Automatica, vol. 12, no. 6, pp. 601–611, 1976.
[32] Y. Mo, S. Weerakkody, and B. Sinopoli, “Physical authentication of con-
trol systems: designing watermarked control inputs to detect counterfeit
sensor outputs,” IEEE Control Systems Magazine, vol. 35, no. 1, pp.
93–109, 2015.
[33] R. S. Smith, “Covert misappropriation of networked control systems:
Presenting a feedback structure,” IEEE Control Systems Magazine,
vol. 35, no. 1, pp. 82–92, 2015.
[34] U. Meyer and S. Wetzel, “A man-in-the-middle attack on UMTS,” in
Proceedings of the 3rd ACM workshop on Wireless security, 2004, pp.
90–97.
[35] F. Callegati, W. Cerroni, and M. Ramilli, “Man-in-the-middle attack to
the HTTPS protocol,” IEEE Security and Privacy Magazine, no. 1, pp.
78–81, 2009.
[36] D. Cox and D. Hinkley, Theoretical statistics. New York: Chapman
and Hall, distributed in U.S. by Halsted Press, 1979.
[37] M. Grant, S. Boyd, V. Blondel, and H. Kimura, CVX: Matlab Software
for Disciplined Convex Programming, version 2.0, 2011.
Ziyang Guo was born in Henan, China, in 1992. She
received the B.Eng. degree (Honors) in College of
Control Science and Engineering from Zhejiang U-
niversity, Hangzhou, China, in 2014. She is currently
pursuing the Ph.D. degree in Electronic and Com-
puter Engineering at the Hong Kong University of
Science and Technology, Hong Kong. Her research
interests include cyber-physical system security, s-
tate estimation and wireless sensor network.
Dawei Shi received his B.Eng. degree in Electrical
Engineering and Automation from the Beijing Insti-
tute of Technology in 2008. He received his Ph.D.
degree in Control Systems from the University of
Alberta in 2014. Since December 2014, he has been
appointed as an Associate Professor at the School of
Automation, Beijing Institute of Technology, China.
His research interests include event-based control
and estimation, robust model predictive control and
tuning, and wireless sensor networks. He is a review-
er for a number of international journals, including
IEEE Transactions on Automatic Control, Automatica, and Systems & Con-
trol Letters. In 2009, he received the Best Student Paper Award in IEEE
International Conference on Automation and Logistics.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2325-5870 (c) 2016 IEEE. Personal use is permitted, but republication/redistribution requires IEEE permission. See http://www.ieee.org/publication
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publi
Transactions on Control of Network Systems
10
Karl H. Johansson n is Director of the ACCESS
Linnaeus Centre and Professor at the School of
Electrical Engineering, KTH Royal Institute of Tech-
nology, Sweden. He is a Wallenberg Scholar and has
held a Senior Researcher Position with the Swedish
Research Council. He also heads the Stockholm
Strategic Research Area ICT The Next Generation.
He received M.Sc. and Ph.D. degrees in Electrical
Engineering from Lund University. He has held vis-
iting positions at UC Berkeley, California Institute
of Technology, Nanyang Technological University,
and Institute of Advanced Studies, Hong Kong University of Science and
Technology. His research interests are in networked control systems, cyber-
physical systems, and applications in transportation, energy, and automation
systems. He has been a member of the IEEE Control Systems Society Board
of Governors and the Chair of the IFAC Technical Committee on Networked
Systems. He has been on the Editorial Boards of several journals, including
Automatica, IEEE Transactions on Automatic Control, and IET Control
Theory and Applications. He is currently a Senior Editor of IEEE Transactions
on Control of Network Systems and Associate Editor of European Journal of
Control. He has been Guest Editor for a special issue of IEEE Transactions
on Automatic Control on cyberphysical systems and one of IEEE Control
Systems Magazine on cyberphysical security. He was the General Chair of the
ACM/IEEE CyberPhysical Systems Week 2010 in Stockholm and IPC Chair
of many conferences. He has served on the Executive Committees of several
European research projects in the area of networked embedded systems. He
received the Best Paper Award of the IEEE International Conference on
Mobile Ad-hoc and Sensor Systems in 2009 and the Best Theory Paper Award
of the World Congress on Intelligent Control and Automation in 2014. In 2009
he was awarded Wallenberg Scholar, as one of the first ten scholars from all
sciences, by the Knut and Alice Wallenberg Foundation. He was awarded
Future Research Leader from the Swedish Foundation for Strategic Research
in 2005. He received the triennial Young Author Prize from IFAC in 1996
and the Peccei Award from the International Institute of System Analysis,
Austria, in 1993. He received Young Researcher Awards from Scania in 1996
and from Ericsson in 1998 and 1999. He is a Fellow of the IEEE.
Ling Shi received the B.S. degree in electrical and
electronic engineering from Hong Kong University
of Science and Technology, Kowloon, Hong Kong,
in 2002 and the Ph.D. degree in control and dynami-
cal systems from California Institute of Technology,
Pasadena, CA, USA, in 2008. He is currently an
associate professor at the Department of Electronic
and Computer Engineering, Hong Kong University
of Science and Technology. His research interests
include networked control systems, wireless sensor
networks, event-based state estimation and sensor
scheduling, and smart energy systems. He has been serving as a subject editor
for International Journal of Robust and Nonlinear Control from 2015. He also
served as an associate editor for a special issue on Secure Control of Cyber
Physical Systems in the IEEE Transactions on Control of Network Systems
in 2015-2016.
This article has been accepted for publication in a future issue of this journal, but has not been fully edited. Content may change prior to final publi
Transactions on Control of Network Systems
10
Karl H. Johansson n is Director of the ACCESS
Linnaeus Centre and Professor at the School of
Electrical Engineering, KTH Royal Institute of Tech-
nology, Sweden. He is a Wallenberg Scholar and has
held a Senior Researcher Position with the Swedish
Research Council. He also heads the Stockholm
Strategic Research Area ICT The Next Generation.
He received M.Sc. and Ph.D. degrees in Electrical
Engineering from Lund University. He has held vis-
iting positions at UC Berkeley, California Institute
of Technology, Nanyang Technological University,
and Institute of Advanced Studies, Hong Kong University of Science and
Technology. His research interests are in networked control systems, cyber-
physical systems, and applications in transportation, energy, and automation
systems. He has been a member of the IEEE Control Systems Society Board
of Governors and the Chair of the IFAC Technical Committee on Networked
Systems. He has been on the Editorial Boards of several journals, including
Automatica, IEEE Transactions on Automatic Control, and IET Control
Theory and Applications. He is currently a Senior Editor of IEEE Transactions
on Control of Network Systems and Associate Editor of European Journal of
Control. He has been Guest Editor for a special issue of IEEE Transactions
on Automatic Control on cyberphysical systems and one of IEEE Control
Systems Magazine on cyberphysical security. He was the General Chair of the
ACM/IEEE CyberPhysical Systems Week 2010 in Stockholm and IPC Chair
of many conferences. He has served on the Executive Committees of several
European research projects in the area of networked embedded systems. He
received the Best Paper Award of the IEEE International Conference on
Mobile Ad-hoc and Sensor Systems in 2009 and the Best Theory Paper Award
of the World Congress on Intelligent Control and Automation in 2014. In 2009
he was awarded Wallenberg Scholar, as one of the first ten scholars from all
sciences, by the Knut and Alice Wallenberg Foundation. He was awarded
Future Research Leader from the Swedish Foundation for Strategic Research
in 2005. He received the triennial Young Author Prize from IFAC in 1996
and the Peccei Award from the International Institute of System Analysis,
Austria, in 1993. He received Young Researcher Awards from Scania in 1996
and from Ericsson in 1998 and 1999. He is a Fellow of the IEEE.
Ling Shi received the B.S. degree in electrical and
electronic engineering from Hong Kong University
of Science and Technology, Kowloon, Hong Kong,
in 2002 and the Ph.D. degree in control and dynami-
cal systems from California Institute of Technology,
Pasadena, CA, USA, in 2008. He is currently an
associate professor at the Department of Electronic
and Computer Engineering, Hong Kong University
of Science and Technology. His research interests
include networked control systems, wireless sensor
networks, event-based state estimation and sensor
scheduling, and smart energy systems. He has been serving as a subject editor
for International Journal of Robust and Nonlinear Control from 2015. He also
served as an associate editor for a special issue on Secure Control of Cyber
Physical Systems in the IEEE Transactions on Control of Network Systems
in 2015-2016.
1 out of 10
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.