Standard Ethics and Compliance: Cyber Crime at Maroochy Water Services
VerifiedAdded on 2020/05/01
|14
|3407
|130
Report
AI Summary
This report analyzes the cyber crime incident at Maroochy Water Services, focusing on the theft of the SCADA system by an employee. The introduction defines cyber crime and cyber security, highlighting the growing threats and financial impacts of cyber attacks, particularly in Australia. The discussion section details the various types of cyber security, including application, information, disaster recovery, and network security. The Maroochy Water Services case is then examined, describing the SCADA system, its components, and the incident where an employee caused a major sewage release. The report identifies the causes of the adversity, including insecure systems and insider threats, along with the problem of inadequate security policies. Finally, the report outlines the solutions implemented, such as the use of firewalls and security programs to enhance the SCADA system's security. The conclusion summarizes the key findings and the significance of the incident in the context of Australian cyber security.

Running head: STANDARD ETHICS AND COMPLIANCE
Standard Ethics and Compliance
Name of the Student
Name of the University
Author Note
Standard Ethics and Compliance
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1STANDARD ETHICS AND COMPLIANCE
Table of Contents
1.0 Introduction................................................................................................................................2
2.0 Discussion..................................................................................................................................2
2.1 Approaches for causing cyber crime.....................................................................................4
2.2 The Maroochy Water Services Case......................................................................................4
2.3 Cause of the adversity............................................................................................................5
2.4 The identified problem..........................................................................................................6
2.5 The proposed solution implemented by Maroochy Water Services......................................7
3.0 Conclusion.................................................................................................................................9
4.0 Reference List..........................................................................................................................10
Table of Contents
1.0 Introduction................................................................................................................................2
2.0 Discussion..................................................................................................................................2
2.1 Approaches for causing cyber crime.....................................................................................4
2.2 The Maroochy Water Services Case......................................................................................4
2.3 Cause of the adversity............................................................................................................5
2.4 The identified problem..........................................................................................................6
2.5 The proposed solution implemented by Maroochy Water Services......................................7
3.0 Conclusion.................................................................................................................................9
4.0 Reference List..........................................................................................................................10

2STANDARD ETHICS AND COMPLIANCE
1.0 Introduction
The illegal activity that involves a computer and network is termed as cyber crime.
Moreover, the protection approaches taken for avoiding threats, disruption, misdirection and
theft from computer system referred to cyber security. Amin et al. (2013) stated that controlling
physical access where hardware of the computer system can be accessed for protection against
harm is a common method for implementing cyber security. There are many methods for
implementing cyber security- taking security measures, implementing secured architecture,
designing vulnerability management, obtaining secured operating systems, formulating hardware
protection mechanisms and implementing secure coding (Australia, C.E.R.T 2012).
According to the new Telstra study 2016, it is found that almost 60% of the Australian
company suffered from security incident (Aic.gov.au 2017). According to another research it is
also estimated that cyber security spending will exceed to $1 trillion from 2017 to 2021 (Zhang
et al. 2012). Each business have to incur a loss of $276,323 through a cyber attack in which on
detection up to 53% can be recovered (Acsc.gov.au 2017). In this business assessment, the
Maroochy Water Services is taken into consideration. One of the employees of the concerned
organization stole the SCADA control system and radio equipments and control the entire
system for taking revenge from the company. Thus, issues of cybercrime and the solution that is
taken by the organization will be illustrates in the business report.
2.0 Discussion
In Australia, the threat for cyber security raises significantly and between the month of
2015, July to 2016, June, CERT Australia has found that total of 14,804 cyber crime cases has
1.0 Introduction
The illegal activity that involves a computer and network is termed as cyber crime.
Moreover, the protection approaches taken for avoiding threats, disruption, misdirection and
theft from computer system referred to cyber security. Amin et al. (2013) stated that controlling
physical access where hardware of the computer system can be accessed for protection against
harm is a common method for implementing cyber security. There are many methods for
implementing cyber security- taking security measures, implementing secured architecture,
designing vulnerability management, obtaining secured operating systems, formulating hardware
protection mechanisms and implementing secure coding (Australia, C.E.R.T 2012).
According to the new Telstra study 2016, it is found that almost 60% of the Australian
company suffered from security incident (Aic.gov.au 2017). According to another research it is
also estimated that cyber security spending will exceed to $1 trillion from 2017 to 2021 (Zhang
et al. 2012). Each business have to incur a loss of $276,323 through a cyber attack in which on
detection up to 53% can be recovered (Acsc.gov.au 2017). In this business assessment, the
Maroochy Water Services is taken into consideration. One of the employees of the concerned
organization stole the SCADA control system and radio equipments and control the entire
system for taking revenge from the company. Thus, issues of cybercrime and the solution that is
taken by the organization will be illustrates in the business report.
2.0 Discussion
In Australia, the threat for cyber security raises significantly and between the month of
2015, July to 2016, June, CERT Australia has found that total of 14,804 cyber crime cases has
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
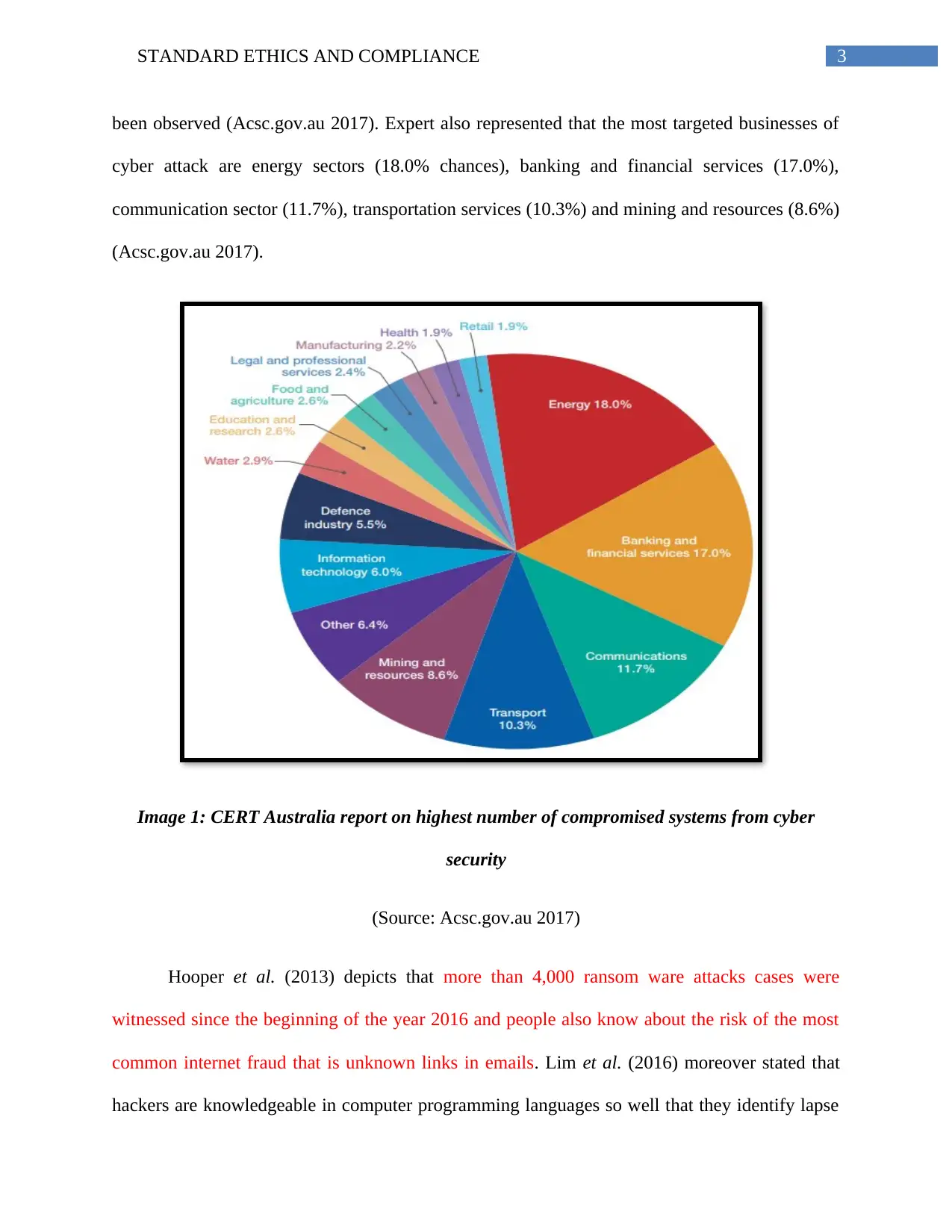
3STANDARD ETHICS AND COMPLIANCE
been observed (Acsc.gov.au 2017). Expert also represented that the most targeted businesses of
cyber attack are energy sectors (18.0% chances), banking and financial services (17.0%),
communication sector (11.7%), transportation services (10.3%) and mining and resources (8.6%)
(Acsc.gov.au 2017).
Image 1: CERT Australia report on highest number of compromised systems from cyber
security
(Source: Acsc.gov.au 2017)
Hooper et al. (2013) depicts that more than 4,000 ransom ware attacks cases were
witnessed since the beginning of the year 2016 and people also know about the risk of the most
common internet fraud that is unknown links in emails. Lim et al. (2016) moreover stated that
hackers are knowledgeable in computer programming languages so well that they identify lapse
been observed (Acsc.gov.au 2017). Expert also represented that the most targeted businesses of
cyber attack are energy sectors (18.0% chances), banking and financial services (17.0%),
communication sector (11.7%), transportation services (10.3%) and mining and resources (8.6%)
(Acsc.gov.au 2017).
Image 1: CERT Australia report on highest number of compromised systems from cyber
security
(Source: Acsc.gov.au 2017)
Hooper et al. (2013) depicts that more than 4,000 ransom ware attacks cases were
witnessed since the beginning of the year 2016 and people also know about the risk of the most
common internet fraud that is unknown links in emails. Lim et al. (2016) moreover stated that
hackers are knowledgeable in computer programming languages so well that they identify lapse
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4STANDARD ETHICS AND COMPLIANCE
and lacunas of the existing system and steal important data. According to a survey it is also
found that in previously, mobile devices had less than a 1% infection rate but in recent times
organization suffered a breach because of mobile devices (Australia, C.E.R.T 2012). Thus,
companies in recent times, adjust their security plans among which 31% of the organization are
making changes to their security plan; while, 52% of the company have not taken any steps yet.
2.1 Different types of cyber security
Protecting computer from virtual virus and computer adversity referred to as cyber
security. The major area that is considered in cyber securities are application security,
information security, disaster recovery and network security. Mariani (2014) also stated that the
most common way to hack the system is blockage of communication channel so that no
members of the organization able to control the server for protecting the data of the organization.
In some cases, hackers install a malicious program in the existing program or delete the actual
program that controls the operational functionalities of an organization. Application security
encompasses to protection of applications from threats that highlights the aspects of application
design, development, deployment, upgrade or maintenance. Companies uses techniques like
input parameter validation, session management, auditing and logging, parameter manipulation
& exception management and user/role authentication & authorization. Cunningham (2016) on
the other hand depicted that cyber criminals exploit unauthorized products with exploit
unauthorized products. In order to overcome the information breaches, company focuses on
cryptography and authentication & authorization of user. Some company also use the platform of
corporate cloud, where huge data are stored related to company’s crucial information. Moreover,
the disaster recovery planning refers to a process that includes performing risk assessment,
developing recovery strategies and establishing priorities in case when some cyber crime occurs.
and lacunas of the existing system and steal important data. According to a survey it is also
found that in previously, mobile devices had less than a 1% infection rate but in recent times
organization suffered a breach because of mobile devices (Australia, C.E.R.T 2012). Thus,
companies in recent times, adjust their security plans among which 31% of the organization are
making changes to their security plan; while, 52% of the company have not taken any steps yet.
2.1 Different types of cyber security
Protecting computer from virtual virus and computer adversity referred to as cyber
security. The major area that is considered in cyber securities are application security,
information security, disaster recovery and network security. Mariani (2014) also stated that the
most common way to hack the system is blockage of communication channel so that no
members of the organization able to control the server for protecting the data of the organization.
In some cases, hackers install a malicious program in the existing program or delete the actual
program that controls the operational functionalities of an organization. Application security
encompasses to protection of applications from threats that highlights the aspects of application
design, development, deployment, upgrade or maintenance. Companies uses techniques like
input parameter validation, session management, auditing and logging, parameter manipulation
& exception management and user/role authentication & authorization. Cunningham (2016) on
the other hand depicted that cyber criminals exploit unauthorized products with exploit
unauthorized products. In order to overcome the information breaches, company focuses on
cryptography and authentication & authorization of user. Some company also use the platform of
corporate cloud, where huge data are stored related to company’s crucial information. Moreover,
the disaster recovery planning refers to a process that includes performing risk assessment,
developing recovery strategies and establishing priorities in case when some cyber crime occurs.

5STANDARD ETHICS AND COMPLIANCE
Lastly, company also value on network security that can be obtained through anti-virus and anti-
spyware, intrusion prevention systems (IPS), intrusion prevention systems (IPS) and identify
fast-spreading threats (Hooper et al. 2013).
2.2 The Maroochy Water Services Case
One such case that is considered in this study is Maroochy Water Services in Queensland,
Australia, where an employee stole the SCADA system and radio system. Amin et al. (2013)
stated that Supervisory control and data acquisition (SCADA) systems are utilized by
organization to monitor and control operations for the purpose of power distribution facilities,
water distribution systems and sewage treatment plants. SCADA systems are utilized by
Maroochy Water Services for gathering real-time data, monitoring the pipelines and control the
entire process. Warren and Streeter (2013) also portrays that SCADA system is also used for
public utilities along with the oil and gas pipelines, electrical power generation and transmission,
chemical plants and refineries and water and sewage treatment plants. The concerned system is
used for handling large geographical location and in this context also SCADA is used for such
case of public utilities. It has three components- field devices, servers, and clients. Nicholson et
al. (2012) illustrates that the field device includes include sensors and controllers that collect
data from various sources regarding the water movements. The controllers used are
programmable logic controllers (PLCs) and remote telemetry units (RTUs) and are interfaced
with serial connections or Ethernet. Asghari et al. (2016) on the other hand depict that servers
and clients refers for collecting and analyzing various field inputs and interacting with servers
via terminals respectively. In case of Australia, due to remoteness of many of the utility plants
and vastness of the country, Australian SCADA systems are complex in nature. The system is
liable to control the water and sewage system by maintaining the temperature, current, power
Lastly, company also value on network security that can be obtained through anti-virus and anti-
spyware, intrusion prevention systems (IPS), intrusion prevention systems (IPS) and identify
fast-spreading threats (Hooper et al. 2013).
2.2 The Maroochy Water Services Case
One such case that is considered in this study is Maroochy Water Services in Queensland,
Australia, where an employee stole the SCADA system and radio system. Amin et al. (2013)
stated that Supervisory control and data acquisition (SCADA) systems are utilized by
organization to monitor and control operations for the purpose of power distribution facilities,
water distribution systems and sewage treatment plants. SCADA systems are utilized by
Maroochy Water Services for gathering real-time data, monitoring the pipelines and control the
entire process. Warren and Streeter (2013) also portrays that SCADA system is also used for
public utilities along with the oil and gas pipelines, electrical power generation and transmission,
chemical plants and refineries and water and sewage treatment plants. The concerned system is
used for handling large geographical location and in this context also SCADA is used for such
case of public utilities. It has three components- field devices, servers, and clients. Nicholson et
al. (2012) illustrates that the field device includes include sensors and controllers that collect
data from various sources regarding the water movements. The controllers used are
programmable logic controllers (PLCs) and remote telemetry units (RTUs) and are interfaced
with serial connections or Ethernet. Asghari et al. (2016) on the other hand depict that servers
and clients refers for collecting and analyzing various field inputs and interacting with servers
via terminals respectively. In case of Australia, due to remoteness of many of the utility plants
and vastness of the country, Australian SCADA systems are complex in nature. The system is
liable to control the water and sewage system by maintaining the temperature, current, power
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6STANDARD ETHICS AND COMPLIANCE
variables, fire alarms and load shedding systems Rjaibi et al. (2016.). In Maroochy Water
Services Case, due to insecure SCADA system, the staffs of the organization lost their control
over the system and more than 1million liter of untreated sewage was released to the local parks
and waterways.
2.3 Cause of the adversity
It is a general believe of the staffs that there might be some problems in their newly
implemented system. The communication with the wastewater pumping stations link with their
radio system was lost and the alarms that were implemented there for identification of any
adversity in the initial stages were also not working. Beasley et al. (2014) highlighted that the
person actually liable for the cases is Vitek Boden staff of Maroochy Water Services. The person
used a laptop and a radio transmitter and he also stole the SCADA system and controlled 150
sewage pumping stations. The system disabled the alarm fitted at four pumping stations. Some
staffs of the concerned organization then noticed that the system is controlled by some intruder,
who hacked the entire system. The reason was personal antagonism with the company for not
securing the job in that organization. Mr. Boden has released one million liters of untreated
sewage in a stormwater drain that flowed in the local parks, rivers and grounds of a Hyatt
Regency hotel (Rid and Buchanan 2015). The adversity caused through this action was death in
marine bodies, turning of creek water into black and unbearable stench for the community
people. The evidence that found was the laptop had been reloaded with most of the waterline
security software operating programs- PDS software file. The software is used by the officials to
access the sewage system. Moreover, the two-way radio that was used for council’s
communication system was also tuned into the frequencies of the repeater stations. These radio
numbers were matched with the radios that was supplied to the company’s supplier named
variables, fire alarms and load shedding systems Rjaibi et al. (2016.). In Maroochy Water
Services Case, due to insecure SCADA system, the staffs of the organization lost their control
over the system and more than 1million liter of untreated sewage was released to the local parks
and waterways.
2.3 Cause of the adversity
It is a general believe of the staffs that there might be some problems in their newly
implemented system. The communication with the wastewater pumping stations link with their
radio system was lost and the alarms that were implemented there for identification of any
adversity in the initial stages were also not working. Beasley et al. (2014) highlighted that the
person actually liable for the cases is Vitek Boden staff of Maroochy Water Services. The person
used a laptop and a radio transmitter and he also stole the SCADA system and controlled 150
sewage pumping stations. The system disabled the alarm fitted at four pumping stations. Some
staffs of the concerned organization then noticed that the system is controlled by some intruder,
who hacked the entire system. The reason was personal antagonism with the company for not
securing the job in that organization. Mr. Boden has released one million liters of untreated
sewage in a stormwater drain that flowed in the local parks, rivers and grounds of a Hyatt
Regency hotel (Rid and Buchanan 2015). The adversity caused through this action was death in
marine bodies, turning of creek water into black and unbearable stench for the community
people. The evidence that found was the laptop had been reloaded with most of the waterline
security software operating programs- PDS software file. The software is used by the officials to
access the sewage system. Moreover, the two-way radio that was used for council’s
communication system was also tuned into the frequencies of the repeater stations. These radio
numbers were matched with the radios that was supplied to the company’s supplier named
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7STANDARD ETHICS AND COMPLIANCE
Hunter Watertech (Slay and Miller 2007). Lastly, the address of PDS Compact 500 was set to
004 that set off the alarm present at that water pipeline (Slay and Miller 2007).
2.4 The identified problem
Robert Stringfellow, responsible civil engineer during the time of adversity believed that
the SCADA installation may cause some flaws through which the problem arise. The pump
setting kept changing even after re-installing all the software and checking the system and thus it
can be said that there was an external malicious entity that was entered through wireless
equipment and infected he SCADA system. Abrams and Weiss (2008) also depict that even after
high security system; it is very difficult to protect the system from insider attacks. The radio
systems are not properly configured and also insecure and this gap was identified by the intruder.
The security system was also not assessed properly in the SCADA system and this is the reason
that the security staffs also overlook the small malicious changes that occurred. Lastly, the
SCADA system also comprises of sophisticated logging mechanisms that contain thousands of
codes and hence is impossible to evaluate on a daily basis. The staffs from the company also
identified some of the Boden’s malicious activities which were addressed later and not the time
of the incident was thrugh SP 800-53 controls (Amin et al. 2013). Mr. Boden created problem in
the policy and procedures, personnel security, hardware and software. The problem is also
presented in awareness and training, auditing, contingency planning, incidence response and
information protection system (Rid and McBurney 2012). The organization does not have proper
cyber security policies or procedures in place like “AC-18 Wireless Access Restrictions” that
authorizes monitors, controls wireless access and establishes usage implementation and
restrictions guidance.
Hunter Watertech (Slay and Miller 2007). Lastly, the address of PDS Compact 500 was set to
004 that set off the alarm present at that water pipeline (Slay and Miller 2007).
2.4 The identified problem
Robert Stringfellow, responsible civil engineer during the time of adversity believed that
the SCADA installation may cause some flaws through which the problem arise. The pump
setting kept changing even after re-installing all the software and checking the system and thus it
can be said that there was an external malicious entity that was entered through wireless
equipment and infected he SCADA system. Abrams and Weiss (2008) also depict that even after
high security system; it is very difficult to protect the system from insider attacks. The radio
systems are not properly configured and also insecure and this gap was identified by the intruder.
The security system was also not assessed properly in the SCADA system and this is the reason
that the security staffs also overlook the small malicious changes that occurred. Lastly, the
SCADA system also comprises of sophisticated logging mechanisms that contain thousands of
codes and hence is impossible to evaluate on a daily basis. The staffs from the company also
identified some of the Boden’s malicious activities which were addressed later and not the time
of the incident was thrugh SP 800-53 controls (Amin et al. 2013). Mr. Boden created problem in
the policy and procedures, personnel security, hardware and software. The problem is also
presented in awareness and training, auditing, contingency planning, incidence response and
information protection system (Rid and McBurney 2012). The organization does not have proper
cyber security policies or procedures in place like “AC-18 Wireless Access Restrictions” that
authorizes monitors, controls wireless access and establishes usage implementation and
restrictions guidance.
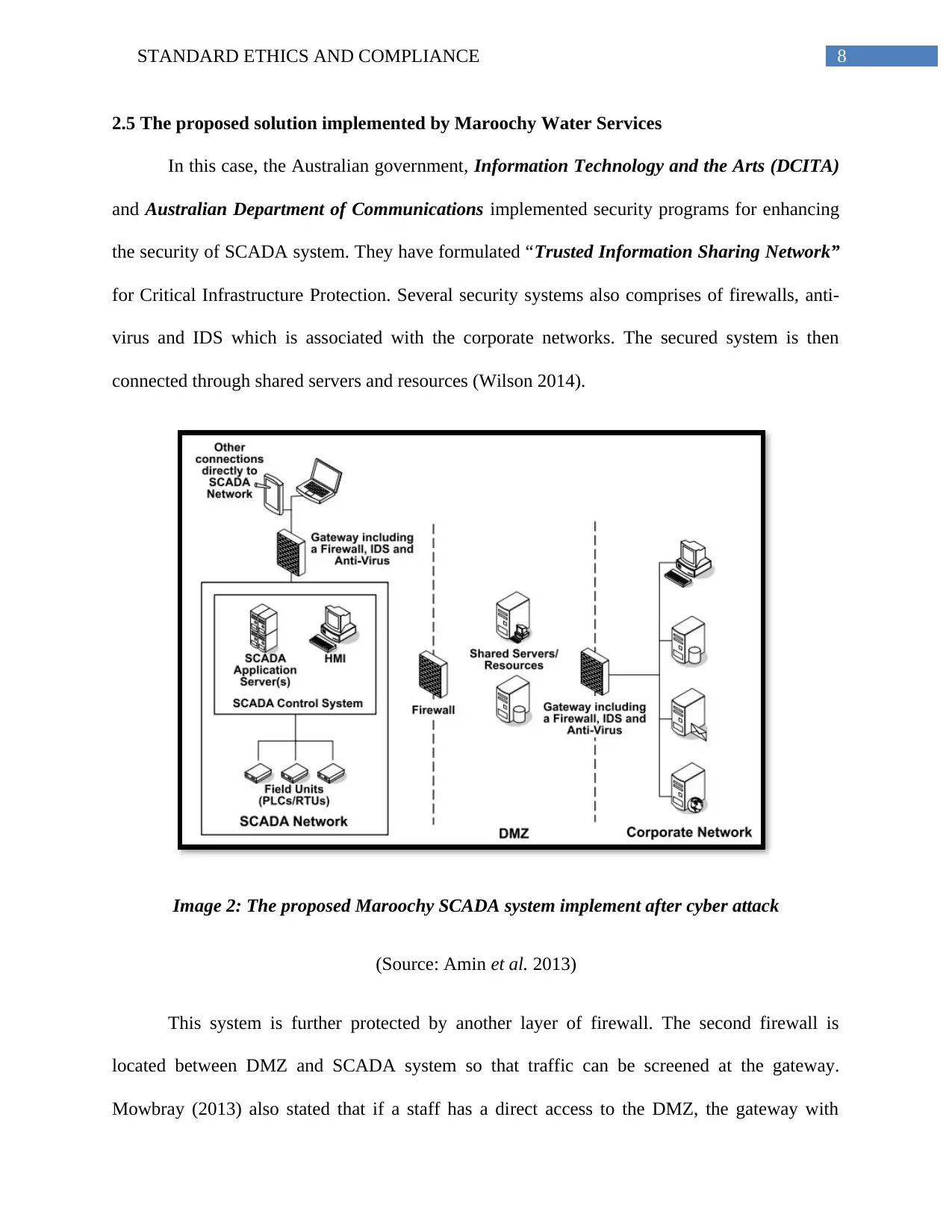
8STANDARD ETHICS AND COMPLIANCE
2.5 The proposed solution implemented by Maroochy Water Services
In this case, the Australian government, Information Technology and the Arts (DCITA)
and Australian Department of Communications implemented security programs for enhancing
the security of SCADA system. They have formulated “Trusted Information Sharing Network”
for Critical Infrastructure Protection. Several security systems also comprises of firewalls, anti-
virus and IDS which is associated with the corporate networks. The secured system is then
connected through shared servers and resources (Wilson 2014).
Image 2: The proposed Maroochy SCADA system implement after cyber attack
(Source: Amin et al. 2013)
This system is further protected by another layer of firewall. The second firewall is
located between DMZ and SCADA system so that traffic can be screened at the gateway.
Mowbray (2013) also stated that if a staff has a direct access to the DMZ, the gateway with
2.5 The proposed solution implemented by Maroochy Water Services
In this case, the Australian government, Information Technology and the Arts (DCITA)
and Australian Department of Communications implemented security programs for enhancing
the security of SCADA system. They have formulated “Trusted Information Sharing Network”
for Critical Infrastructure Protection. Several security systems also comprises of firewalls, anti-
virus and IDS which is associated with the corporate networks. The secured system is then
connected through shared servers and resources (Wilson 2014).
Image 2: The proposed Maroochy SCADA system implement after cyber attack
(Source: Amin et al. 2013)
This system is further protected by another layer of firewall. The second firewall is
located between DMZ and SCADA system so that traffic can be screened at the gateway.
Mowbray (2013) also stated that if a staff has a direct access to the DMZ, the gateway with
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9STANDARD ETHICS AND COMPLIANCE
substantial security functionality should be implemented. This security functionality is activated
in the boundary of SCADA system and DMZ. The prime reason for implementing the firewall
system is that firewall eliminates direct connections from the Internet, controls traffic entering
and restrict access from the corporate network. There were some other solutions also that were
suggested by the personals like addressing protocol-level vulnerabilities, network management
and administration.
3.0 Conclusion
Thus, it can be stated that Maroochy SCADA scam was one of the biggest cyber crime in
Australian industry of the year 2000. It is also concluded that the SCADA system comprised of
three radio frequencies and two monitoring stations. These systems comprises of operations of
142 sewage pumping stations. The fault that was found after the adversity were unexplained
pump station alarms, unnecessary configuration settings, increased radio traffic, turning of
alarms without pump station lockups, unexpected turning of pumps and no monitoring of the
alarm in computer communication. It can also be said from the assessment that the civil engineer
of the organization recommended the use of anti-virus and firewall protection for using
appropriate use of encryption. Moreover, proper staff training, implementation of upgradeable
SCADA systems, incorporation of security auditing and control. Thus, all organizations should
also prepare a mitigation plan so that they can avoid cyber crime.
substantial security functionality should be implemented. This security functionality is activated
in the boundary of SCADA system and DMZ. The prime reason for implementing the firewall
system is that firewall eliminates direct connections from the Internet, controls traffic entering
and restrict access from the corporate network. There were some other solutions also that were
suggested by the personals like addressing protocol-level vulnerabilities, network management
and administration.
3.0 Conclusion
Thus, it can be stated that Maroochy SCADA scam was one of the biggest cyber crime in
Australian industry of the year 2000. It is also concluded that the SCADA system comprised of
three radio frequencies and two monitoring stations. These systems comprises of operations of
142 sewage pumping stations. The fault that was found after the adversity were unexplained
pump station alarms, unnecessary configuration settings, increased radio traffic, turning of
alarms without pump station lockups, unexpected turning of pumps and no monitoring of the
alarm in computer communication. It can also be said from the assessment that the civil engineer
of the organization recommended the use of anti-virus and firewall protection for using
appropriate use of encryption. Moreover, proper staff training, implementation of upgradeable
SCADA systems, incorporation of security auditing and control. Thus, all organizations should
also prepare a mitigation plan so that they can avoid cyber crime.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10STANDARD ETHICS AND COMPLIANCE
4.0 Reference List
Abrams, M. and Weiss, J., 2008. Malicious control system cyber security attack case study–
Maroochy Water Services, Australia. McLean, VA: The MITRE Corporation.
Acsc.gov.au., 2017. ACSC Threat Report 2016. [online] Available at:
https://www.acsc.gov.au/publications/ACSC_Threat_Report_2016 [Accessed 30 Oct. 2017].
Ahmad, R. and Yunos, Z., 2012. A dynamic cyber terrorism framework. International Journal of
Computer Science and Information Security, 10(2), p.149.
Aic.gov.au., 2017. Australian Institute of Criminology - Cybercrime. [online] Available at:
http://www.aic.gov.au/crime_types/in_focus/cybercrime.html [Accessed 30 Oct. 2017].
Amin, S., Litrico, X., Sastry, S. and Bayen, A.M., 2013. Cyber security of water SCADA
systems—Part I: Analysis and experimentation of stealthy deception attacks. IEEE Transactions
on Control Systems Technology, 21(5), pp.1963-1970.
Amin, S., Litrico, X., Sastry, S. and Bayen, A.M., 2013. Cyber security of water SCADA
systems—Part I: Analysis and experimentation of stealthy deception attacks. IEEE Transactions
on Control Systems Technology, 21(5), pp.1963-1970.
Australia, C.E.R.T., 2012. Cyber crime and security survey report. 2013-09-19)[2014-07-20].
http:∥ www. canberra. edu. au/cis/storage/Cyber% 20Crime% 20and% 20Security% 20Survey%
20Report% 202012.
4.0 Reference List
Abrams, M. and Weiss, J., 2008. Malicious control system cyber security attack case study–
Maroochy Water Services, Australia. McLean, VA: The MITRE Corporation.
Acsc.gov.au., 2017. ACSC Threat Report 2016. [online] Available at:
https://www.acsc.gov.au/publications/ACSC_Threat_Report_2016 [Accessed 30 Oct. 2017].
Ahmad, R. and Yunos, Z., 2012. A dynamic cyber terrorism framework. International Journal of
Computer Science and Information Security, 10(2), p.149.
Aic.gov.au., 2017. Australian Institute of Criminology - Cybercrime. [online] Available at:
http://www.aic.gov.au/crime_types/in_focus/cybercrime.html [Accessed 30 Oct. 2017].
Amin, S., Litrico, X., Sastry, S. and Bayen, A.M., 2013. Cyber security of water SCADA
systems—Part I: Analysis and experimentation of stealthy deception attacks. IEEE Transactions
on Control Systems Technology, 21(5), pp.1963-1970.
Amin, S., Litrico, X., Sastry, S. and Bayen, A.M., 2013. Cyber security of water SCADA
systems—Part I: Analysis and experimentation of stealthy deception attacks. IEEE Transactions
on Control Systems Technology, 21(5), pp.1963-1970.
Australia, C.E.R.T., 2012. Cyber crime and security survey report. 2013-09-19)[2014-07-20].
http:∥ www. canberra. edu. au/cis/storage/Cyber% 20Crime% 20and% 20Security% 20Survey%
20Report% 202012.

11STANDARD ETHICS AND COMPLIANCE
Beasley, C., Zhong, X., Deng, J., Brooks, R. and Venayagamoorthy, G.K., 2014, October. A
survey of electric power synchrophasor network cyber security. In Innovative Smart Grid
Technologies Conference Europe (ISGT-Europe), 2014 IEEE PES (pp. 1-5). IEEE.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H. and Stoddart, K., 2016.
A review of cyber security risk assessment methods for SCADA systems. computers & security,
56, pp.1-27.
Clarke, R.A. and Knake, R.K., 2014. Cyber war. Tantor Media, Incorporated.
Collins, S. and McCombie, S., 2012. Stuxnet: the emergence of a new cyber weapon and its
implications. Journal of Policing, Intelligence and Counter Terrorism, 7(1), pp.80-91.
Cunningham, D., 2016. Developing a Core List of Journals at the National Institute of Standards
and Technology Research Library. Information Outlook.
Daryabar, F., Dehghantanha, A., Udzir, N.I. and bin Shamsuddin, S., 2012, June. Towards secure
model for SCADA systems. In Cyber Security, Cyber Warfare and Digital Forensic (CyberSec),
2012 International Conference on (pp. 60-64). IEEE.
Dunn Cavelty, M., 2012. The militarisation of cyber security as a source of global tension.
Henrie, M., 2013. Cyber security risk management in the SCADA critical infrastructure
environment. Engineering Management Journal, 25(2), pp.38-45.
Hooper, C., Martini, B. and Choo, K.K.R., 2013. Cloud computing and its implications for
cybercrime investigations in Australia. Computer Law & Security Review, 29(2), pp.152-163.
Beasley, C., Zhong, X., Deng, J., Brooks, R. and Venayagamoorthy, G.K., 2014, October. A
survey of electric power synchrophasor network cyber security. In Innovative Smart Grid
Technologies Conference Europe (ISGT-Europe), 2014 IEEE PES (pp. 1-5). IEEE.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H. and Stoddart, K., 2016.
A review of cyber security risk assessment methods for SCADA systems. computers & security,
56, pp.1-27.
Clarke, R.A. and Knake, R.K., 2014. Cyber war. Tantor Media, Incorporated.
Collins, S. and McCombie, S., 2012. Stuxnet: the emergence of a new cyber weapon and its
implications. Journal of Policing, Intelligence and Counter Terrorism, 7(1), pp.80-91.
Cunningham, D., 2016. Developing a Core List of Journals at the National Institute of Standards
and Technology Research Library. Information Outlook.
Daryabar, F., Dehghantanha, A., Udzir, N.I. and bin Shamsuddin, S., 2012, June. Towards secure
model for SCADA systems. In Cyber Security, Cyber Warfare and Digital Forensic (CyberSec),
2012 International Conference on (pp. 60-64). IEEE.
Dunn Cavelty, M., 2012. The militarisation of cyber security as a source of global tension.
Henrie, M., 2013. Cyber security risk management in the SCADA critical infrastructure
environment. Engineering Management Journal, 25(2), pp.38-45.
Hooper, C., Martini, B. and Choo, K.K.R., 2013. Cloud computing and its implications for
cybercrime investigations in Australia. Computer Law & Security Review, 29(2), pp.152-163.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





