Literature Review: Cyber Crime Risks and Responsibilities for Business
VerifiedAdded on 2020/03/02
|12
|2835
|165
Literature Review
AI Summary
This literature review examines the escalating cyber crime risks faced by businesses in today's technologically advanced world, with a specific focus on data security and the responsibilities of organizations in mitigating these threats. The review highlights the increasing sophistication of cyber attacks, the importance of data protection, and the need for robust security measures. It uses BHP Billiton as a case study, analyzing their approach to cyber security, including their organizational structure, incident response teams, and proactive measures to protect against various cyber threats. The review also provides a comparative analysis of cyber security initiatives worldwide, examining critical sectors, organizational overviews, early warning approaches, and legal frameworks. It emphasizes the importance of skilled responders, audit trails, and user awareness in reducing cyber crime and concludes with recommendations for comprehensive approaches to protect sensitive data. The document underscores the importance of continuous improvement and adaptation in the face of evolving cyber threats.
Cyber crime risk and responsibilities for business 1
Business research
Cyber crime risks and responsibilities for business
Business research
Cyber crime risks and responsibilities for business
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber crime risk and responsibilities for business 2
Literature review
World has become more technological, there are so many changes done in the business
due to developments in technology. Internet has become more advanced in today’s world.
However, the emerging technologies of internet have been challenged by pornographic. It
enhances the chance of developing international terrorism. Internet is being used by many
criminals to share the information in all over the world. In the context of negative aspect of
internet, various kind of terrorist such as nationalist, revolutionaries, fascist, separatists and
anarchists are able to share the propaganda to their supporter by using internet to overall execute
their information. Apart from that there can be other issues arise such as data lose, security
corrupt and cyber crime (Tonge, Kasture and Chaudhari, 2013).
Franke and Brynielsson, (2014) argued that cyber security is the cover of technologies,
practices and process which is designed to prevent networks, programs, computer and relevant
data from unnecessary attack and unauthorized access. BHP Billiton is the Australian company
which mainly deals in the mining, metals and petroleum dual listed public. The Headquarter of
this company is located in Melbourne, Australia. It is the trading entity. It was the fourth largest
company by revenues measured by market values of 2015. The business of BHP Billiton is
higher, so it is required to keep the data securely (Franke and Brynielsson, 2014). All shapes of
organization are living in online environment and use the device of mobile for automation to
improve the interaction with customers. There are billions of customers who use online services
with business and organization have obligation to prevent relevant information that could
personally recognize their customers. Unfortunately, the setup of the internet is extremely
Literature review
World has become more technological, there are so many changes done in the business
due to developments in technology. Internet has become more advanced in today’s world.
However, the emerging technologies of internet have been challenged by pornographic. It
enhances the chance of developing international terrorism. Internet is being used by many
criminals to share the information in all over the world. In the context of negative aspect of
internet, various kind of terrorist such as nationalist, revolutionaries, fascist, separatists and
anarchists are able to share the propaganda to their supporter by using internet to overall execute
their information. Apart from that there can be other issues arise such as data lose, security
corrupt and cyber crime (Tonge, Kasture and Chaudhari, 2013).
Franke and Brynielsson, (2014) argued that cyber security is the cover of technologies,
practices and process which is designed to prevent networks, programs, computer and relevant
data from unnecessary attack and unauthorized access. BHP Billiton is the Australian company
which mainly deals in the mining, metals and petroleum dual listed public. The Headquarter of
this company is located in Melbourne, Australia. It is the trading entity. It was the fourth largest
company by revenues measured by market values of 2015. The business of BHP Billiton is
higher, so it is required to keep the data securely (Franke and Brynielsson, 2014). All shapes of
organization are living in online environment and use the device of mobile for automation to
improve the interaction with customers. There are billions of customers who use online services
with business and organization have obligation to prevent relevant information that could
personally recognize their customers. Unfortunately, the setup of the internet is extremely

Cyber crime risk and responsibilities for business 3
familiar with cyber criminal (Yan, Zhang and Vasilakos, 2014). It is considered as decentralized
and therefore lack of controlling on subject, it cannot be censored, allow anyone to use it.
BHP Billiton is concern about its data and that is why it is set to house which has major
capability of cyber security in Melbourne. It is the part of its plan to enhance the size of its stable
workforce of IT globally. There are transactional data which might involve system identifiers
such as machine identifiers and internet protocol. Business should be more active to take action
against the hacked data (Jacobs, 2016). However, it is seen many times that the best interest of
organization and customers for a loss or breach to be informed, it must be known in the point of
necessity that there is no law in Australia regarding this process. To being as giant mining
organization, BHP Billiton recruit nine security architecture and the professional of cyber
security to revealed the major IT expansion. It is done by company to protect the data of
company secured. It has branches in Singapore and Houston and it is also placing same quality
of resources there. As per the article of Crozier, (2017), company stated that there is technology
and cyber unit separately in BHP Billiton, and at least six Australians sit, inside the company’s
wider security governance, risk and compliance group. In BHP Billiton, groups are categorized
that is having the specialization in security. It is the plan of company to employ cyber incident
response that should be specialized in proactively detect and immediate respond to incidents,
able to conduct post-mortems and bring changes in technology of operation. It is the initiate of
BHP Billiton to protect from cyber crimes, this role which is the part of it plan will be liable for
defending against the incidents of technology incidents along with that they should be capable to
recognize, analyze, communicate and contain these incidents in the time of occurrence (Crozier,
2017).
familiar with cyber criminal (Yan, Zhang and Vasilakos, 2014). It is considered as decentralized
and therefore lack of controlling on subject, it cannot be censored, allow anyone to use it.
BHP Billiton is concern about its data and that is why it is set to house which has major
capability of cyber security in Melbourne. It is the part of its plan to enhance the size of its stable
workforce of IT globally. There are transactional data which might involve system identifiers
such as machine identifiers and internet protocol. Business should be more active to take action
against the hacked data (Jacobs, 2016). However, it is seen many times that the best interest of
organization and customers for a loss or breach to be informed, it must be known in the point of
necessity that there is no law in Australia regarding this process. To being as giant mining
organization, BHP Billiton recruit nine security architecture and the professional of cyber
security to revealed the major IT expansion. It is done by company to protect the data of
company secured. It has branches in Singapore and Houston and it is also placing same quality
of resources there. As per the article of Crozier, (2017), company stated that there is technology
and cyber unit separately in BHP Billiton, and at least six Australians sit, inside the company’s
wider security governance, risk and compliance group. In BHP Billiton, groups are categorized
that is having the specialization in security. It is the plan of company to employ cyber incident
response that should be specialized in proactively detect and immediate respond to incidents,
able to conduct post-mortems and bring changes in technology of operation. It is the initiate of
BHP Billiton to protect from cyber crimes, this role which is the part of it plan will be liable for
defending against the incidents of technology incidents along with that they should be capable to
recognize, analyze, communicate and contain these incidents in the time of occurrence (Crozier,
2017).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cyber crime risk and responsibilities for business 4
Comparative analysis
It has been analyzed with the support of article “A Comparative Analysis Of Cyber
security Initiatives Worldwide”, that many policy makers have been showing their concerns
regarding the insecure information and wanted to share at highest level that it would be threaten
for economic growth and national security. As consequences of these concerns, the emerged has
been developed of web of regional, national and multilateral initiatives. It has been evaluated that
recent publications offers a collection and evaluation of the efforts of cyber security in 14
countries. The overview of issues has been provided by the international CIIP Handbook, in the
ground of information infrastructure information. There are five focal points which have higher
importance that has been emerged in the cross comparison company surveys. That is critical
sectors, organizational overview, early warning approaches, current topics in laws and legislation
and research and development (Rahman and Choo, 2015).
In the context of critical sectors, there are two interrelated but differ concept of
perceptions of critically. That is critically as systematic approach and critically as a symbolic
approach. However the organizations of Australia are found under critical sectors and sub
sectors. In the comparison of two concepts, the most observing similarity is the focus on
essential goods or services (Xie & Ou, 2010). It defines that the actual object of protection is not
the part of static infrastructure as that much, but focus on services, in the flow of physical and
electronic. This is far level of abstract of understanding essential assets. In the term of
organizational overview, several organizations in Australia are responsible for CIP. For instance,
Australia’s infrastructure such as virtual and physical structures, terrorism is found there. Cyber
security has been observed as a component of the effort of counter-terrorism of overall country.
Therefore, defense signals directorate, Australian Federal Police and the Australian Security
Comparative analysis
It has been analyzed with the support of article “A Comparative Analysis Of Cyber
security Initiatives Worldwide”, that many policy makers have been showing their concerns
regarding the insecure information and wanted to share at highest level that it would be threaten
for economic growth and national security. As consequences of these concerns, the emerged has
been developed of web of regional, national and multilateral initiatives. It has been evaluated that
recent publications offers a collection and evaluation of the efforts of cyber security in 14
countries. The overview of issues has been provided by the international CIIP Handbook, in the
ground of information infrastructure information. There are five focal points which have higher
importance that has been emerged in the cross comparison company surveys. That is critical
sectors, organizational overview, early warning approaches, current topics in laws and legislation
and research and development (Rahman and Choo, 2015).
In the context of critical sectors, there are two interrelated but differ concept of
perceptions of critically. That is critically as systematic approach and critically as a symbolic
approach. However the organizations of Australia are found under critical sectors and sub
sectors. In the comparison of two concepts, the most observing similarity is the focus on
essential goods or services (Xie & Ou, 2010). It defines that the actual object of protection is not
the part of static infrastructure as that much, but focus on services, in the flow of physical and
electronic. This is far level of abstract of understanding essential assets. In the term of
organizational overview, several organizations in Australia are responsible for CIP. For instance,
Australia’s infrastructure such as virtual and physical structures, terrorism is found there. Cyber
security has been observed as a component of the effort of counter-terrorism of overall country.
Therefore, defense signals directorate, Australian Federal Police and the Australian Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber crime risk and responsibilities for business 5
Intelligence Organization are the part of Critical Infrastructure Protection Group members. In the
order of early warning approaches, the Australian company BHP Billiton has cross-border Co-
operation (Pepper, McIntosh, Fitzsimmons, Gebhardt and Dillenbeck, 2015). This co-operation
is made internationally and it is more sensible when one observes the inherently cross-boundary
nature of threats CERT has been developed which have been set up mainly at national and
international level, and these kinds of organizations get incident response of any cyber crime.
There are legal issues because national laws are developed autonomously. In the company of
BHP Billiton, there should be data protection and security in electronic communications,
protection of personal data, international harmonization of cybercrime law and identifications
and digital signature (Lebek, Uffen, Neumann, Hohler and Breitner, 2014).
It has been evaluated in the comparison of Australia, USA and EU had well efficient
team of research and development in the field of cyber security. The US has a crucial role in
recognizing and promoting essential research topics. The EU plays a leading role in helping
cross-rational R&D in the field of cyber security of Europe. There is no objection that R&D will
face the challenge of cyber security in the future.
Intelligence Organization are the part of Critical Infrastructure Protection Group members. In the
order of early warning approaches, the Australian company BHP Billiton has cross-border Co-
operation (Pepper, McIntosh, Fitzsimmons, Gebhardt and Dillenbeck, 2015). This co-operation
is made internationally and it is more sensible when one observes the inherently cross-boundary
nature of threats CERT has been developed which have been set up mainly at national and
international level, and these kinds of organizations get incident response of any cyber crime.
There are legal issues because national laws are developed autonomously. In the company of
BHP Billiton, there should be data protection and security in electronic communications,
protection of personal data, international harmonization of cybercrime law and identifications
and digital signature (Lebek, Uffen, Neumann, Hohler and Breitner, 2014).
It has been evaluated in the comparison of Australia, USA and EU had well efficient
team of research and development in the field of cyber security. The US has a crucial role in
recognizing and promoting essential research topics. The EU plays a leading role in helping
cross-rational R&D in the field of cyber security of Europe. There is no objection that R&D will
face the challenge of cyber security in the future.
Cyber crime risk and responsibilities for business 6
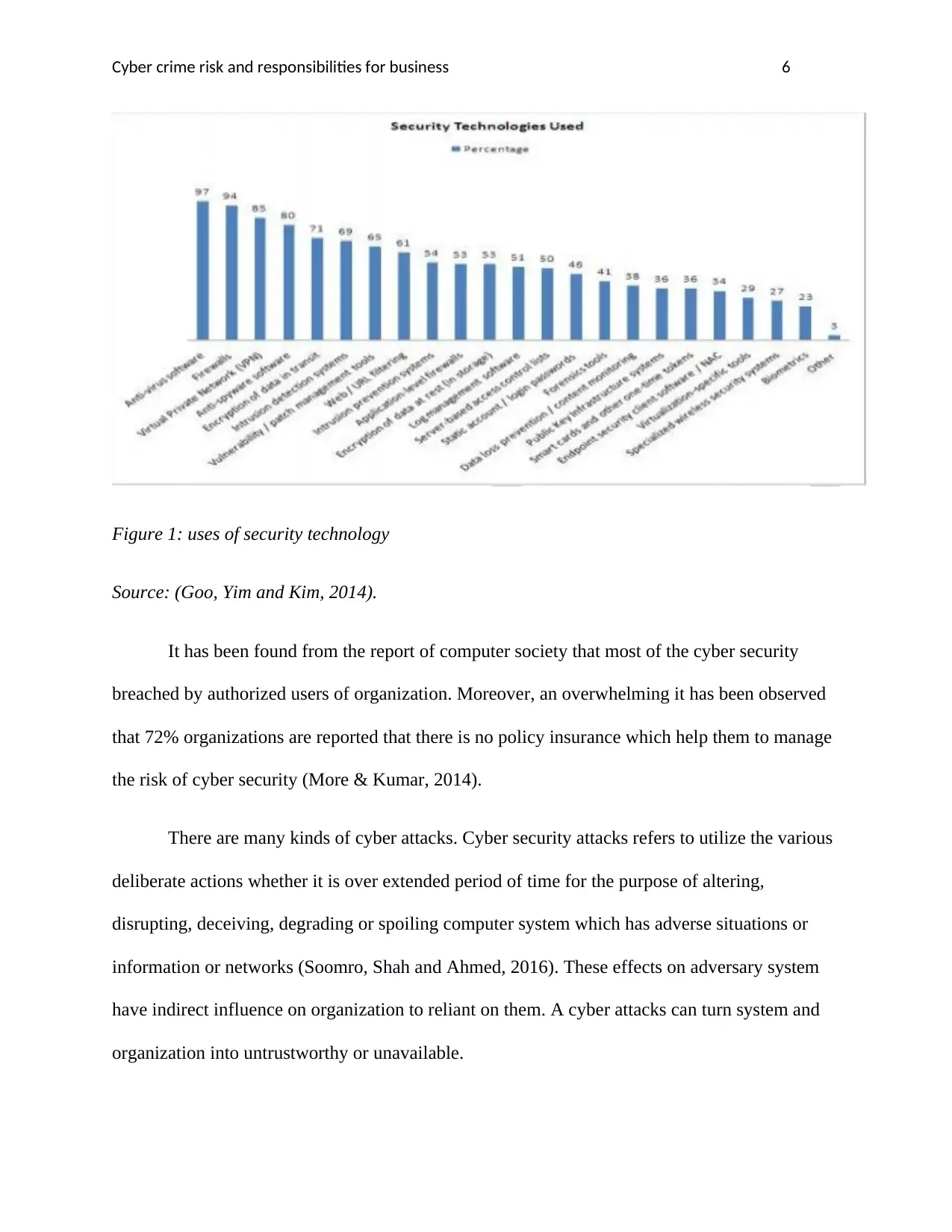
Figure 1: uses of security technology
Source: (Goo, Yim and Kim, 2014).
It has been found from the report of computer society that most of the cyber security
breached by authorized users of organization. Moreover, an overwhelming it has been observed
that 72% organizations are reported that there is no policy insurance which help them to manage
the risk of cyber security (More & Kumar, 2014).
There are many kinds of cyber attacks. Cyber security attacks refers to utilize the various
deliberate actions whether it is over extended period of time for the purpose of altering,
disrupting, deceiving, degrading or spoiling computer system which has adverse situations or
information or networks (Soomro, Shah and Ahmed, 2016). These effects on adversary system
have indirect influence on organization to reliant on them. A cyber attacks can turn system and
organization into untrustworthy or unavailable.
Figure 1: uses of security technology
Source: (Goo, Yim and Kim, 2014).
It has been found from the report of computer society that most of the cyber security
breached by authorized users of organization. Moreover, an overwhelming it has been observed
that 72% organizations are reported that there is no policy insurance which help them to manage
the risk of cyber security (More & Kumar, 2014).
There are many kinds of cyber attacks. Cyber security attacks refers to utilize the various
deliberate actions whether it is over extended period of time for the purpose of altering,
disrupting, deceiving, degrading or spoiling computer system which has adverse situations or
information or networks (Soomro, Shah and Ahmed, 2016). These effects on adversary system
have indirect influence on organization to reliant on them. A cyber attacks can turn system and
organization into untrustworthy or unavailable.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Cyber crime risk and responsibilities for business 7
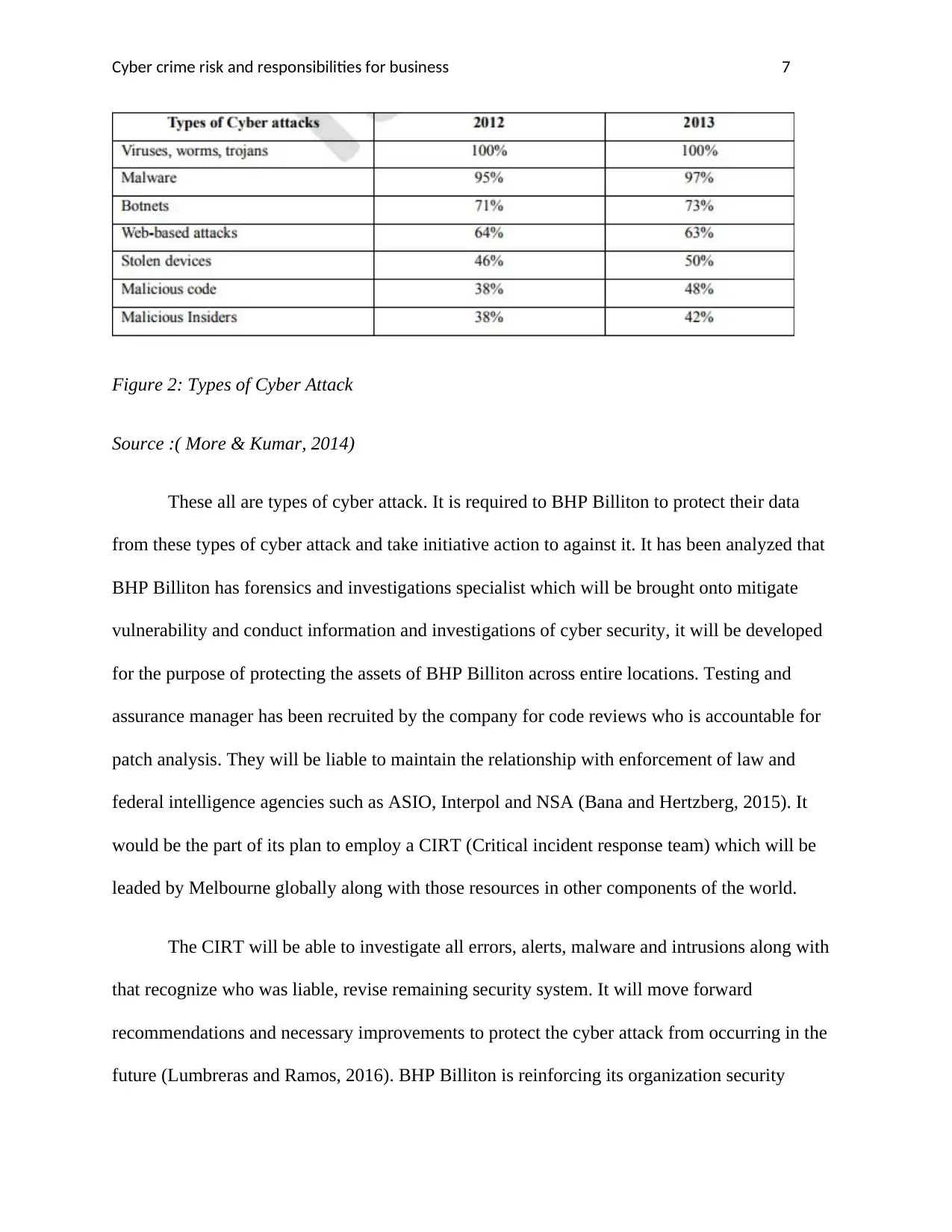
Figure 2: Types of Cyber Attack
Source :( More & Kumar, 2014)
These all are types of cyber attack. It is required to BHP Billiton to protect their data
from these types of cyber attack and take initiative action to against it. It has been analyzed that
BHP Billiton has forensics and investigations specialist which will be brought onto mitigate
vulnerability and conduct information and investigations of cyber security, it will be developed
for the purpose of protecting the assets of BHP Billiton across entire locations. Testing and
assurance manager has been recruited by the company for code reviews who is accountable for
patch analysis. They will be liable to maintain the relationship with enforcement of law and
federal intelligence agencies such as ASIO, Interpol and NSA (Bana and Hertzberg, 2015). It
would be the part of its plan to employ a CIRT (Critical incident response team) which will be
leaded by Melbourne globally along with those resources in other components of the world.
The CIRT will be able to investigate all errors, alerts, malware and intrusions along with
that recognize who was liable, revise remaining security system. It will move forward
recommendations and necessary improvements to protect the cyber attack from occurring in the
future (Lumbreras and Ramos, 2016). BHP Billiton is reinforcing its organization security
Figure 2: Types of Cyber Attack
Source :( More & Kumar, 2014)
These all are types of cyber attack. It is required to BHP Billiton to protect their data
from these types of cyber attack and take initiative action to against it. It has been analyzed that
BHP Billiton has forensics and investigations specialist which will be brought onto mitigate
vulnerability and conduct information and investigations of cyber security, it will be developed
for the purpose of protecting the assets of BHP Billiton across entire locations. Testing and
assurance manager has been recruited by the company for code reviews who is accountable for
patch analysis. They will be liable to maintain the relationship with enforcement of law and
federal intelligence agencies such as ASIO, Interpol and NSA (Bana and Hertzberg, 2015). It
would be the part of its plan to employ a CIRT (Critical incident response team) which will be
leaded by Melbourne globally along with those resources in other components of the world.
The CIRT will be able to investigate all errors, alerts, malware and intrusions along with
that recognize who was liable, revise remaining security system. It will move forward
recommendations and necessary improvements to protect the cyber attack from occurring in the
future (Lumbreras and Ramos, 2016). BHP Billiton is reinforcing its organization security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Cyber crime risk and responsibilities for business 8
architecture resources in outside the domain of specific security domain. The organization
security architecture team of BHP Billiton will be leading globally based out of Melbourne. This
team will provide the overall direction along with leadership for entire security architecture of
technology and design activities inside the organization of BHP. Moreover, BHP expects to
recruit principal security architects in number of locations for the purpose of designing,
implementing, documenting and supporting of architecture of security and the commodities of
infrastructure.
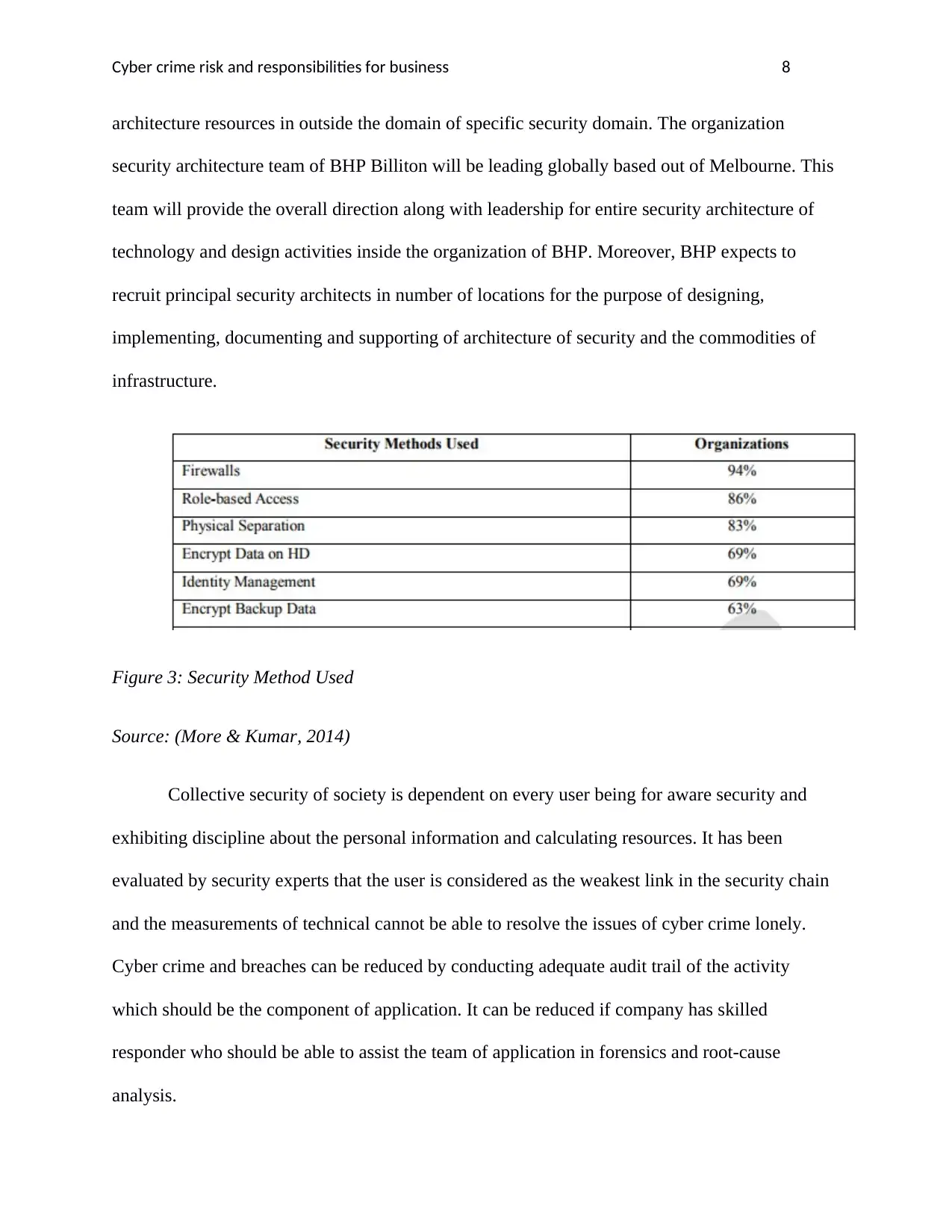
Figure 3: Security Method Used
Source: (More & Kumar, 2014)
Collective security of society is dependent on every user being for aware security and
exhibiting discipline about the personal information and calculating resources. It has been
evaluated by security experts that the user is considered as the weakest link in the security chain
and the measurements of technical cannot be able to resolve the issues of cyber crime lonely.
Cyber crime and breaches can be reduced by conducting adequate audit trail of the activity
which should be the component of application. It can be reduced if company has skilled
responder who should be able to assist the team of application in forensics and root-cause
analysis.
architecture resources in outside the domain of specific security domain. The organization
security architecture team of BHP Billiton will be leading globally based out of Melbourne. This
team will provide the overall direction along with leadership for entire security architecture of
technology and design activities inside the organization of BHP. Moreover, BHP expects to
recruit principal security architects in number of locations for the purpose of designing,
implementing, documenting and supporting of architecture of security and the commodities of
infrastructure.
Figure 3: Security Method Used
Source: (More & Kumar, 2014)
Collective security of society is dependent on every user being for aware security and
exhibiting discipline about the personal information and calculating resources. It has been
evaluated by security experts that the user is considered as the weakest link in the security chain
and the measurements of technical cannot be able to resolve the issues of cyber crime lonely.
Cyber crime and breaches can be reduced by conducting adequate audit trail of the activity
which should be the component of application. It can be reduced if company has skilled
responder who should be able to assist the team of application in forensics and root-cause
analysis.

Cyber crime risk and responsibilities for business 9
BHP Billiton has a cyber security team which is recognized by globally. It is highly
technical and innovative. To prevent the cyber attack the security system of BHP Billiton is
included in to its core functions. The core functions of this organization are scheduling work
based which should be basis on business priorities and perform administrative task for the head
of Global Cyber Security. To prevent the data, meeting should be managed while building the
agenda for each year with all information from fellow members of team. WebEx capability
should be there in the time of critical team meetings. Coordination is in the organization which is
helpful to assist the sub functions of wide goals, policies and objectives. It has the team of
tracking the objectives and actions of leaders to ensure the time frames that are able to meet the
cyber security function initiatives in partnership with higher level of authority.
It has been included that a cyber crime has increased day by day, there is need to protect
data of an individual as well as company. In this literature review BHP Billiton Company has
been take which is leading its business in the field of mining, petroleum and metals. It is the
fourth largest company in all over Australia. Throughout the literature review it has been found
that there is requirement to conduct the research to analyze a comprehensive approach for the
aim to protect sensitive data. It will be worth to take appropriate action. The security system of
BHP Billiton is secured and company is trying to develop approachable substance to protect its
data appropriately and in its mission, it has become successful almost because it is the company
which has efficient cyber security team. There are so many kind of cyber attacks which has been
elaborated in this literature review, it has been recommended that company should be aware
about that kind of attacks time to time and take initiative action to develop software which
should be able to recognize attack and inform immediately.
BHP Billiton has a cyber security team which is recognized by globally. It is highly
technical and innovative. To prevent the cyber attack the security system of BHP Billiton is
included in to its core functions. The core functions of this organization are scheduling work
based which should be basis on business priorities and perform administrative task for the head
of Global Cyber Security. To prevent the data, meeting should be managed while building the
agenda for each year with all information from fellow members of team. WebEx capability
should be there in the time of critical team meetings. Coordination is in the organization which is
helpful to assist the sub functions of wide goals, policies and objectives. It has the team of
tracking the objectives and actions of leaders to ensure the time frames that are able to meet the
cyber security function initiatives in partnership with higher level of authority.
It has been included that a cyber crime has increased day by day, there is need to protect
data of an individual as well as company. In this literature review BHP Billiton Company has
been take which is leading its business in the field of mining, petroleum and metals. It is the
fourth largest company in all over Australia. Throughout the literature review it has been found
that there is requirement to conduct the research to analyze a comprehensive approach for the
aim to protect sensitive data. It will be worth to take appropriate action. The security system of
BHP Billiton is secured and company is trying to develop approachable substance to protect its
data appropriately and in its mission, it has become successful almost because it is the company
which has efficient cyber security team. There are so many kind of cyber attacks which has been
elaborated in this literature review, it has been recommended that company should be aware
about that kind of attacks time to time and take initiative action to develop software which
should be able to recognize attack and inform immediately.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cyber crime risk and responsibilities for business 10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber crime risk and responsibilities for business 11
References
Rahman, N.H. and Choo, K.K.R., 2015, A survey of information security incident handling in
the cloud. Computers & Security, 49, pp.45-69.
Bana, A. and Hertzberg, D., 2015, Data Security and the Legal Profession: Risks, Unique
Challenges and Practical Considerations. Bus. L. Int'l, 16, p.247.
Choucri, N., Madnick, S. and Ferwerda, J., 2014, Institutions for cyber security: International
responses and global imperatives, Information Technology for Development, 20(2), pp.96-121.
Crozier, R, 2017, BHP Billiton to create big Aussie infosec unit, retrived on 19th August 2017
from: https://www.itnews.com.au/news/bhp-billiton-to-create-big-aussie-infosec-unit-450875.
Franke, U. and Brynielsson, J., 2014, Cyber situational awareness–a systematic review of the
literature, Computers & Security, 46, pp.18-31.
Goo, J., Yim, M.S. and Kim, D.J., 2014, A path to successful management of employee security
compliance: An empirical study of information security climate, IEEE Transactions on
Professional Communication, 57(4), pp.286-308.
Jacobs, T., 2016, Industrial-sized Cyber Attacks Threaten the Upstream Sector, Journal of
Petroleum Technology, 68(03), pp.42-50.
Lebek, B., Uffen, J., Neumann, M., Hohler, B. and H. Breitner, M., 2014, Information security
awareness and behavior: a theory-based literature review, Management Research Review,
37(12), pp.1049-1092.
References
Rahman, N.H. and Choo, K.K.R., 2015, A survey of information security incident handling in
the cloud. Computers & Security, 49, pp.45-69.
Bana, A. and Hertzberg, D., 2015, Data Security and the Legal Profession: Risks, Unique
Challenges and Practical Considerations. Bus. L. Int'l, 16, p.247.
Choucri, N., Madnick, S. and Ferwerda, J., 2014, Institutions for cyber security: International
responses and global imperatives, Information Technology for Development, 20(2), pp.96-121.
Crozier, R, 2017, BHP Billiton to create big Aussie infosec unit, retrived on 19th August 2017
from: https://www.itnews.com.au/news/bhp-billiton-to-create-big-aussie-infosec-unit-450875.
Franke, U. and Brynielsson, J., 2014, Cyber situational awareness–a systematic review of the
literature, Computers & Security, 46, pp.18-31.
Goo, J., Yim, M.S. and Kim, D.J., 2014, A path to successful management of employee security
compliance: An empirical study of information security climate, IEEE Transactions on
Professional Communication, 57(4), pp.286-308.
Jacobs, T., 2016, Industrial-sized Cyber Attacks Threaten the Upstream Sector, Journal of
Petroleum Technology, 68(03), pp.42-50.
Lebek, B., Uffen, J., Neumann, M., Hohler, B. and H. Breitner, M., 2014, Information security
awareness and behavior: a theory-based literature review, Management Research Review,
37(12), pp.1049-1092.

Cyber crime risk and responsibilities for business 12
Lumbreras, S. and Ramos, A., 2016, The new challenges to transmission expansion planning,
Survey of recent practice and literature review. Electric Power Systems Research, 134, pp.19-29.
More,R, M & Kumar, A, 2014, A Study of Current Scenario of Cyber Security Practices and
Measures: Literature Review, International Journal of Engineering Research and General
Science Volume 2, Issue 5, August-September, 2014 ISSN 2091-2730.
Xie, P. J. Li, X. Ou, 2010, Using Bayesian Networks for Cyber Security Analysis, Proc.40th
IEEE/IFIP Int’l Conf. Dependable Systems and Networks.
Pepper, A., McIntosh, P., Fitzsimmons, R., Gebhardt, T. and Dillenbeck, E., 2015, The
Unconventional Global Endowment: Results of BHP Billiton's Global Assessment. In
International Conference and Exhibition, Melbourne, Australia 13-16 September 2015 (pp. 283-
283). Society of Exploration Geophysicists and American Association of Petroleum Geologists.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016, Information security management needs more
holistic approach: A literature review, International Journal of Information Management, 36(2),
pp.215-225.
Tonge, A.M., Kasture, S.S. and Chaudhari, S.R., 2013, Cyber security: challenges for society-
literature review, IOSR Journal of Computer Engineering, 2(12), pp.67-75.
Yan, Z., Zhang, P. and Vasilakos, A.V., 2014, A survey on trust management for Internet of
Things, Journal of network and computer applications, 42, pp.120-134.
Lumbreras, S. and Ramos, A., 2016, The new challenges to transmission expansion planning,
Survey of recent practice and literature review. Electric Power Systems Research, 134, pp.19-29.
More,R, M & Kumar, A, 2014, A Study of Current Scenario of Cyber Security Practices and
Measures: Literature Review, International Journal of Engineering Research and General
Science Volume 2, Issue 5, August-September, 2014 ISSN 2091-2730.
Xie, P. J. Li, X. Ou, 2010, Using Bayesian Networks for Cyber Security Analysis, Proc.40th
IEEE/IFIP Int’l Conf. Dependable Systems and Networks.
Pepper, A., McIntosh, P., Fitzsimmons, R., Gebhardt, T. and Dillenbeck, E., 2015, The
Unconventional Global Endowment: Results of BHP Billiton's Global Assessment. In
International Conference and Exhibition, Melbourne, Australia 13-16 September 2015 (pp. 283-
283). Society of Exploration Geophysicists and American Association of Petroleum Geologists.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016, Information security management needs more
holistic approach: A literature review, International Journal of Information Management, 36(2),
pp.215-225.
Tonge, A.M., Kasture, S.S. and Chaudhari, S.R., 2013, Cyber security: challenges for society-
literature review, IOSR Journal of Computer Engineering, 2(12), pp.67-75.
Yan, Z., Zhang, P. and Vasilakos, A.V., 2014, A survey on trust management for Internet of
Things, Journal of network and computer applications, 42, pp.120-134.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





