Cyber Defence Project in ANZ Bank: Risk Assessment and Mitigation Plan
VerifiedAdded on 2023/06/03
|6
|841
|438
Report
AI Summary
This report provides a comprehensive analysis of the risks associated with implementing a cyber security mechanism for ANZ Bank. It identifies potential threats, including data breaches and occupational safety hazards, and proposes mitigation strategies. The analysis emphasizes the importance of a multi-dimensional approach to cyber security, considering technical, legal, regulatory, and organizational aspects. The report also highlights the significance of regulatory compliance, skill development, and expert consultation in ensuring the project's success. A risk management plan is included to identify root causes and outline mitigation measures, emphasizing the role of risk registers and treatment options in achieving project objectives. This document is available on Desklib, a platform offering a wide range of study resources for students.

CYBER DEFENCE PROJECT IN ANZ BANK
1
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Part 2. Analysis of Project Risks.....................................................................................................3
Reference List..................................................................................................................................6
2
Part 2. Analysis of Project Risks.....................................................................................................3
Reference List..................................................................................................................................6
2

Part 2. Analysis of Project Risks
In this segment, multiple risks that can affect the implementation of cyber security mechanism of
ANZ Bank has been analyzed critically. From the project description, it is observed that the
demonstration of cyber security solutions will ensure a productive environment in the
organization. It is further addressed that the implication of Cybersecurity solutions will provide
long-term protection from vulnerable attacks. According to Skopik, Settanni, and Fiedler (2016),
multiple dimensions of information sharing plays a crucial role in cybersecurity mechanism of
any organization. Furthermore, the authors have addressed that organisations often make
mistakes by focusing more on the technical aspects of cybersecurity. Instead, business
enterprises should adhere to multiple dimensions, such are:
Technical
Legal
Regulatory and
Organisational means
Besides this, Amin, Schwartz, and Hussain (2013), identified that Cyber-Physical Systems
(CPSs) help to clarify the layers that help business enterprises to maintain a better security
system. These layers are:
1. Regulatory Control
2. Supervisory Control and
3. Management level control
Therefore, it is pivotal for ANZ Bank to isolate multiple risks that can be evidenced during or
before applying ‘Cybersecurity solutions' for this organization. A risk management plan has been
embedded below to identify root causes of possible risks in a project, followed by a mitigation
plan that will determine the success of this project.
3
In this segment, multiple risks that can affect the implementation of cyber security mechanism of
ANZ Bank has been analyzed critically. From the project description, it is observed that the
demonstration of cyber security solutions will ensure a productive environment in the
organization. It is further addressed that the implication of Cybersecurity solutions will provide
long-term protection from vulnerable attacks. According to Skopik, Settanni, and Fiedler (2016),
multiple dimensions of information sharing plays a crucial role in cybersecurity mechanism of
any organization. Furthermore, the authors have addressed that organisations often make
mistakes by focusing more on the technical aspects of cybersecurity. Instead, business
enterprises should adhere to multiple dimensions, such are:
Technical
Legal
Regulatory and
Organisational means
Besides this, Amin, Schwartz, and Hussain (2013), identified that Cyber-Physical Systems
(CPSs) help to clarify the layers that help business enterprises to maintain a better security
system. These layers are:
1. Regulatory Control
2. Supervisory Control and
3. Management level control
Therefore, it is pivotal for ANZ Bank to isolate multiple risks that can be evidenced during or
before applying ‘Cybersecurity solutions' for this organization. A risk management plan has been
embedded below to identify root causes of possible risks in a project, followed by a mitigation
plan that will determine the success of this project.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
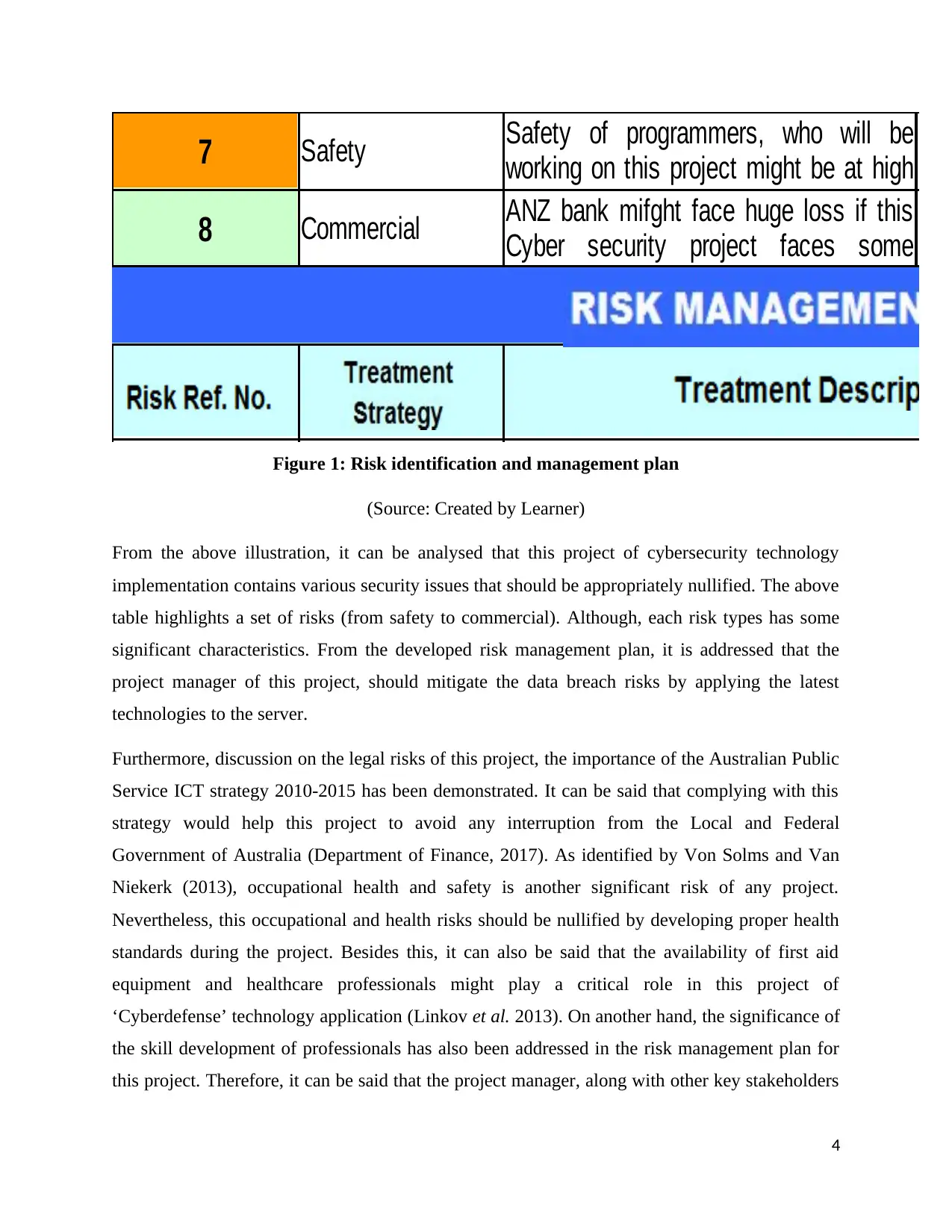
7 Safety
8 Commercial
Safety of programmers, who will be
working on this project might be at high
riskANZ bank mifght face huge loss if this
Cyber security project faces some
issues
Figure 1: Risk identification and management plan
(Source: Created by Learner)
From the above illustration, it can be analysed that this project of cybersecurity technology
implementation contains various security issues that should be appropriately nullified. The above
table highlights a set of risks (from safety to commercial). Although, each risk types has some
significant characteristics. From the developed risk management plan, it is addressed that the
project manager of this project, should mitigate the data breach risks by applying the latest
technologies to the server.
Furthermore, discussion on the legal risks of this project, the importance of the Australian Public
Service ICT strategy 2010-2015 has been demonstrated. It can be said that complying with this
strategy would help this project to avoid any interruption from the Local and Federal
Government of Australia (Department of Finance, 2017). As identified by Von Solms and Van
Niekerk (2013), occupational health and safety is another significant risk of any project.
Nevertheless, this occupational and health risks should be nullified by developing proper health
standards during the project. Besides this, it can also be said that the availability of first aid
equipment and healthcare professionals might play a critical role in this project of
‘Cyberdefense’ technology application (Linkov et al. 2013). On another hand, the significance of
the skill development of professionals has also been addressed in the risk management plan for
this project. Therefore, it can be said that the project manager, along with other key stakeholders
4
8 Commercial
Safety of programmers, who will be
working on this project might be at high
riskANZ bank mifght face huge loss if this
Cyber security project faces some
issues
Figure 1: Risk identification and management plan
(Source: Created by Learner)
From the above illustration, it can be analysed that this project of cybersecurity technology
implementation contains various security issues that should be appropriately nullified. The above
table highlights a set of risks (from safety to commercial). Although, each risk types has some
significant characteristics. From the developed risk management plan, it is addressed that the
project manager of this project, should mitigate the data breach risks by applying the latest
technologies to the server.
Furthermore, discussion on the legal risks of this project, the importance of the Australian Public
Service ICT strategy 2010-2015 has been demonstrated. It can be said that complying with this
strategy would help this project to avoid any interruption from the Local and Federal
Government of Australia (Department of Finance, 2017). As identified by Von Solms and Van
Niekerk (2013), occupational health and safety is another significant risk of any project.
Nevertheless, this occupational and health risks should be nullified by developing proper health
standards during the project. Besides this, it can also be said that the availability of first aid
equipment and healthcare professionals might play a critical role in this project of
‘Cyberdefense’ technology application (Linkov et al. 2013). On another hand, the significance of
the skill development of professionals has also been addressed in the risk management plan for
this project. Therefore, it can be said that the project manager, along with other key stakeholders
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

of this project will conduct proper training for skill development of employees. Finally, it can
also be mentioned that the hiring of professional experts should avoid the organization to
mitigate this in a significant manner. In the end, it can be concluded that risk register and risk
treatment options will play a pivotal role in completing this project successfully.
5
also be mentioned that the hiring of professional experts should avoid the organization to
mitigate this in a significant manner. In the end, it can be concluded that risk register and risk
treatment options will play a pivotal role in completing this project successfully.
5

Reference List
Amin, S., Schwartz, G.A. and Hussain, A., 2013. In quest of benchmarking security risks to
cyber-physical systems. IEEE Network, 27(1), pp.19-24.
Department of Finance (2017). Australian Public Service ICT strategy. Available from
https://www.finance.gov.au/archive/policy-guides-procurement/ict_strategy_2012_2015/.
[Accessed 25/07/2018]
Linkov, I., Eisenberg, D.A., Plourde, K., Seager, T.P., Allen, J. and Kott, A., 2013. Resilience
metrics for cyber systems. Environment Systems and Decisions, 33(4), pp.471-476.
Skopik, F., Settanni, G. and Fiedler, R., 2016. A problem shared is a problem halved: A survey
on the dimensions of collective cyber defense through security information sharing. Computers
& Security, 60, pp.154-176.
Von Solms, R. and Van Niekerk, J., 2013. From information security to cyber
security. computers & security, 38, pp.97-102.
6
Amin, S., Schwartz, G.A. and Hussain, A., 2013. In quest of benchmarking security risks to
cyber-physical systems. IEEE Network, 27(1), pp.19-24.
Department of Finance (2017). Australian Public Service ICT strategy. Available from
https://www.finance.gov.au/archive/policy-guides-procurement/ict_strategy_2012_2015/.
[Accessed 25/07/2018]
Linkov, I., Eisenberg, D.A., Plourde, K., Seager, T.P., Allen, J. and Kott, A., 2013. Resilience
metrics for cyber systems. Environment Systems and Decisions, 33(4), pp.471-476.
Skopik, F., Settanni, G. and Fiedler, R., 2016. A problem shared is a problem halved: A survey
on the dimensions of collective cyber defense through security information sharing. Computers
& Security, 60, pp.154-176.
Von Solms, R. and Van Niekerk, J., 2013. From information security to cyber
security. computers & security, 38, pp.97-102.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





