Cyber Forensics Report: Drug Trafficking and Evidence Analysis
VerifiedAdded on 2020/04/01
|33
|5596
|52
Report
AI Summary
This cyber forensics report details an investigation into a case involving potential drug trafficking (amphetamine and methamphetamine) and evidence tampering. The investigation involved analyzing a computer hard drive, examining downloaded videos, and searching for incriminating files. The report highlights the investigation procedure, including the use of software like FTK Imager, ProDiscover, and OSForensics. The findings reveal suspicions of drug dealing and production, as well as potential tampering with digital evidence by the police. The report provides a timeline of events, character profiles, and a case summary, concluding with an analysis of the evidence and the implications of the tampering. The report aims to either prove or disprove the charges set against the suspects involved. The report also includes details about the M57 organization, the police department's involvement, and the various steps taken to preserve the integrity of the evidence during the investigation, including the use of hash sets and hex viewers to analyze the data.

CYBER FORENSICS REPORT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
Abstract
The following case file documents the investigation that was done on the machine that was owned
by Aaron Greene who bought it from the second hand market. The machine originally belonged to
Jo, a M57 employee, and the machine was a workstation in the M57 organization. Aaron Greene, the
current owner of the machine, found suspicious elements in the machine and surrendered the
machine to the police for investigation. On investigation, certain files were found in the machine
that could suggest that Jo was involved in dealing and production of amphetamine and
methamphetamine. Two hard drive images of the machine were made of two different dates and
investigators analysed, examined and used with various software to look into the digital copies of
the hard drive without tampering the original machine. The investigation shows the recording of an
excel sheet which suggests that the suspect may have been involved in the negotiation of a
transaction regarding the sale of the drugs. The suspect may have also been involved in the
production of methamphetamine and amphetamine. Further investigation has lighted on a certain
amount of tampering that has occurred on the digital copy of the hard drive made on the second day
that could indicate ‘foul play’ on the part of the police, negligence done either intentionally or
accidental, and the involvement of suspect in an attempt to destroy digital evidence. Information
has been extracted for the second hard drive that could suggest that the suspect was trying to
destroy physical evidence as well by the use of certain chemicals. The investigation procedure is
followed in the way to either prove or disprove the charges set against the suspects involved in this
case.
Abstract
The following case file documents the investigation that was done on the machine that was owned
by Aaron Greene who bought it from the second hand market. The machine originally belonged to
Jo, a M57 employee, and the machine was a workstation in the M57 organization. Aaron Greene, the
current owner of the machine, found suspicious elements in the machine and surrendered the
machine to the police for investigation. On investigation, certain files were found in the machine
that could suggest that Jo was involved in dealing and production of amphetamine and
methamphetamine. Two hard drive images of the machine were made of two different dates and
investigators analysed, examined and used with various software to look into the digital copies of
the hard drive without tampering the original machine. The investigation shows the recording of an
excel sheet which suggests that the suspect may have been involved in the negotiation of a
transaction regarding the sale of the drugs. The suspect may have also been involved in the
production of methamphetamine and amphetamine. Further investigation has lighted on a certain
amount of tampering that has occurred on the digital copy of the hard drive made on the second day
that could indicate ‘foul play’ on the part of the police, negligence done either intentionally or
accidental, and the involvement of suspect in an attempt to destroy digital evidence. Information
has been extracted for the second hard drive that could suggest that the suspect was trying to
destroy physical evidence as well by the use of certain chemicals. The investigation procedure is
followed in the way to either prove or disprove the charges set against the suspects involved in this
case.

3
Table of Contents
1. Abstract 2
2. Body of Report 4
a. Character Profile 4
i. Main Character Profile 4
1. Profile – Jo 4
ii. Minor Character Profile 4
1. Company Profile – M57 4
2. Public Department Profile – Police Department 4
3. Public Department Profile – Police Department 4
b. Case Background 5
c. The Investigation Procedure 6
d. Investigation Findings – Inculpatory Evidence 9
i. Suspicion in dealing with Amphetamine and Methamphetamine
ii. Production of Amphetamine and Methamphetamine 12
iii. Suspicion in Selling of Amphetamine and Methamphetamine
14
iv. Tampering of Physical Evidence 17
e. Time Line of Events 27
f. Case Summary 28
3. Conclusion 29
4. References 30
5. Appendices 31
1. Body of Report
a. Character Profile
Table of Contents
1. Abstract 2
2. Body of Report 4
a. Character Profile 4
i. Main Character Profile 4
1. Profile – Jo 4
ii. Minor Character Profile 4
1. Company Profile – M57 4
2. Public Department Profile – Police Department 4
3. Public Department Profile – Police Department 4
b. Case Background 5
c. The Investigation Procedure 6
d. Investigation Findings – Inculpatory Evidence 9
i. Suspicion in dealing with Amphetamine and Methamphetamine
ii. Production of Amphetamine and Methamphetamine 12
iii. Suspicion in Selling of Amphetamine and Methamphetamine
14
iv. Tampering of Physical Evidence 17
e. Time Line of Events 27
f. Case Summary 28
3. Conclusion 29
4. References 30
5. Appendices 31
1. Body of Report
a. Character Profile
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
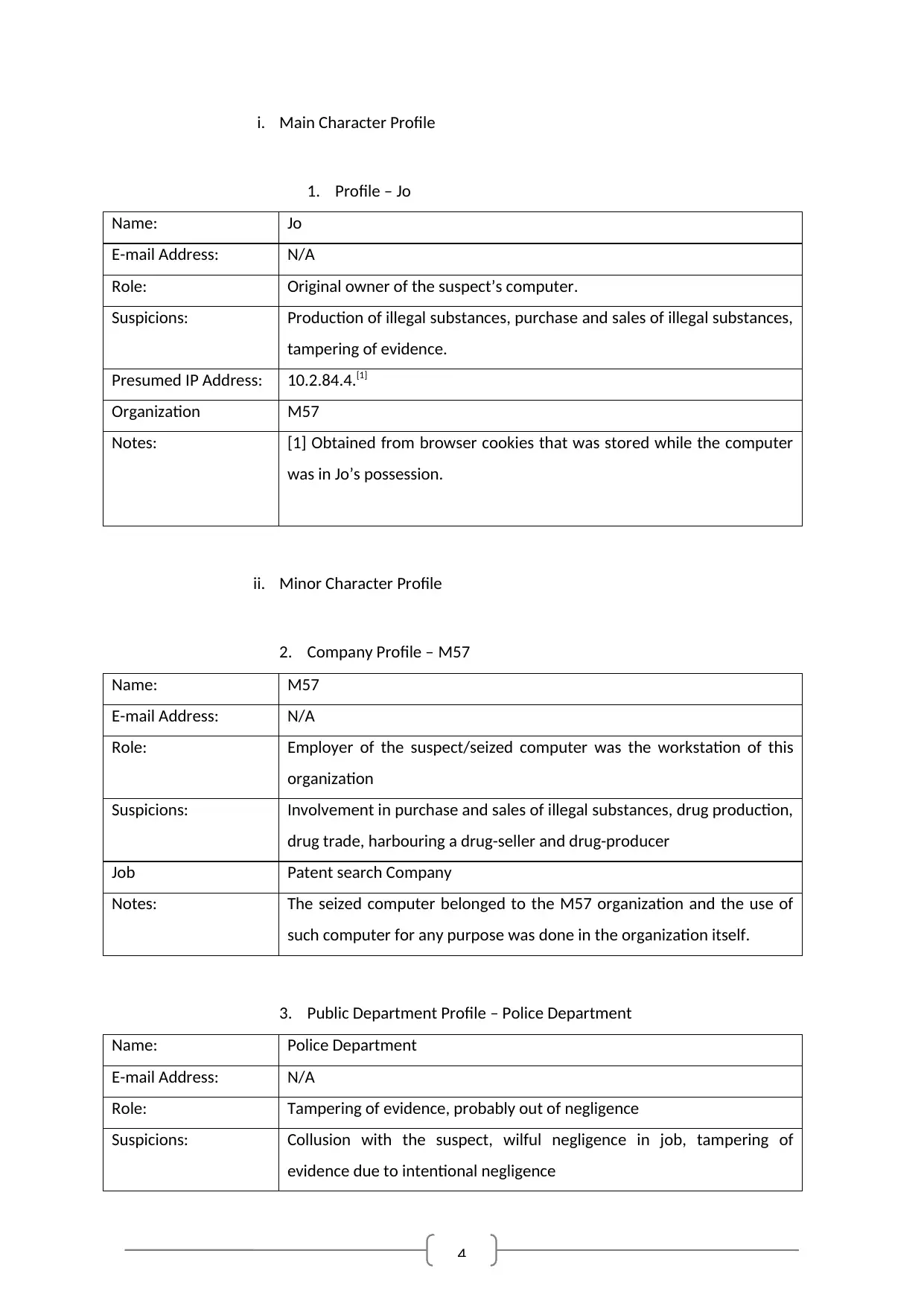
4
i. Main Character Profile
1. Profile – Jo
Name: Jo
E-mail Address: N/A
Role: Original owner of the suspect’s computer.
Suspicions: Production of illegal substances, purchase and sales of illegal substances,
tampering of evidence.
Presumed IP Address: 10.2.84.4.[1]
Organization M57
Notes: [1] Obtained from browser cookies that was stored while the computer
was in Jo’s possession.
ii. Minor Character Profile
2. Company Profile – M57
Name: M57
E-mail Address: N/A
Role: Employer of the suspect/seized computer was the workstation of this
organization
Suspicions: Involvement in purchase and sales of illegal substances, drug production,
drug trade, harbouring a drug-seller and drug-producer
Job Patent search Company
Notes: The seized computer belonged to the M57 organization and the use of
such computer for any purpose was done in the organization itself.
3. Public Department Profile – Police Department
Name: Police Department
E-mail Address: N/A
Role: Tampering of evidence, probably out of negligence
Suspicions: Collusion with the suspect, wilful negligence in job, tampering of
evidence due to intentional negligence
i. Main Character Profile
1. Profile – Jo
Name: Jo
E-mail Address: N/A
Role: Original owner of the suspect’s computer.
Suspicions: Production of illegal substances, purchase and sales of illegal substances,
tampering of evidence.
Presumed IP Address: 10.2.84.4.[1]
Organization M57
Notes: [1] Obtained from browser cookies that was stored while the computer
was in Jo’s possession.
ii. Minor Character Profile
2. Company Profile – M57
Name: M57
E-mail Address: N/A
Role: Employer of the suspect/seized computer was the workstation of this
organization
Suspicions: Involvement in purchase and sales of illegal substances, drug production,
drug trade, harbouring a drug-seller and drug-producer
Job Patent search Company
Notes: The seized computer belonged to the M57 organization and the use of
such computer for any purpose was done in the organization itself.
3. Public Department Profile – Police Department
Name: Police Department
E-mail Address: N/A
Role: Tampering of evidence, probably out of negligence
Suspicions: Collusion with the suspect, wilful negligence in job, tampering of
evidence due to intentional negligence
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
Job Law-enforcement
Notes: The two hard drive images extracted from the seized computer has been
compared to be different with the second image being tampered with.
Such tampering has been noted to be done due to the negligence of the
police, but that suggests a ‘foul-play’ involved on the police’s part and
needs to be investigated further to arrive at a proper conclusion.
b. Case Background
The machine that has been possessed and investigated is lately owned by Aaron Greene who had
bought the device in question from a second-hand market. After the transference of ownership of
the device, the current owner of the machine, Aaron Greene, discovers that the previous data of the
computer has not been erased. On analysis of the said data, Aaron Greene finds out suspicious
documents and videos on the drive that could be related to the buying, creating, possessing and
selling of methamphetamines, an illegal drug that is slowly becoming a bane to the society. Aaron
reports his findings to the police and the machine in question is handed over for further
investigation into the matter.
From the analysis of the machine, it has been found out that the computer can be traced back to be
used as a former workstation by Jo, a M57 employee, as a work machine. The machine was thus
originally belonged to the m57.biz, a new patent search company that researches patent
information of its clients. After such a major discovery, the CEO of M57, Pat McGoo was contacted
by the police who granted the permission for the imaging of all the computers that was being used
or has been used before by the M57 organization to support additional investigation.
However, there are evidences that suggest that the evidence extraction has not been flawless. There
are certain evidences such as the differences between the images of the hard drive that points out
that the police assigned to collect the evidence have somehow tampered with the evidence.
However, the forensics experts have tried to document such differences in the evidence, retraced
back some of the tampered evidence to bring about a more genuine case that might follow the real
events that might have been transpired through the machine in question (Berger & Heath , 2007).
Such a foul-play has also been taken into account as a negligible act on the part of the police, but it is
yet to be seen whether the negligence committed by the police was unintentional or not. The
investigators had tried to use hex editing and other software functions to try and find out how the
‘foul-play’ has occurred, the lost information and whether the tampering of the said information was
Job Law-enforcement
Notes: The two hard drive images extracted from the seized computer has been
compared to be different with the second image being tampered with.
Such tampering has been noted to be done due to the negligence of the
police, but that suggests a ‘foul-play’ involved on the police’s part and
needs to be investigated further to arrive at a proper conclusion.
b. Case Background
The machine that has been possessed and investigated is lately owned by Aaron Greene who had
bought the device in question from a second-hand market. After the transference of ownership of
the device, the current owner of the machine, Aaron Greene, discovers that the previous data of the
computer has not been erased. On analysis of the said data, Aaron Greene finds out suspicious
documents and videos on the drive that could be related to the buying, creating, possessing and
selling of methamphetamines, an illegal drug that is slowly becoming a bane to the society. Aaron
reports his findings to the police and the machine in question is handed over for further
investigation into the matter.
From the analysis of the machine, it has been found out that the computer can be traced back to be
used as a former workstation by Jo, a M57 employee, as a work machine. The machine was thus
originally belonged to the m57.biz, a new patent search company that researches patent
information of its clients. After such a major discovery, the CEO of M57, Pat McGoo was contacted
by the police who granted the permission for the imaging of all the computers that was being used
or has been used before by the M57 organization to support additional investigation.
However, there are evidences that suggest that the evidence extraction has not been flawless. There
are certain evidences such as the differences between the images of the hard drive that points out
that the police assigned to collect the evidence have somehow tampered with the evidence.
However, the forensics experts have tried to document such differences in the evidence, retraced
back some of the tampered evidence to bring about a more genuine case that might follow the real
events that might have been transpired through the machine in question (Berger & Heath , 2007).
Such a foul-play has also been taken into account as a negligible act on the part of the police, but it is
yet to be seen whether the negligence committed by the police was unintentional or not. The
investigators had tried to use hex editing and other software functions to try and find out how the
‘foul-play’ has occurred, the lost information and whether the tampering of the said information was

6
intentional or not. Hence, the contamination of the evidence and the comparison of the two image
files of the original machine extracted from the device in question is also an important part of the
case.
The police as in pursuit of the thumb drive of the suspect, Jo, who is an employee of the
organization, M57. After the permission granted by the CEO of the organization, the police shall be
imaging the remaining workstation of the said organization and in the process, try to find out how
the specific organization or the workstation of that specific organization, or the employee employed
in the organization had come about to become involved in this specific case regarding the exchange
and use of drugs.
c. The Investigation Procedure
After creating a digital copy of the machine, all the investigation procedure has been conducted on
the copy of the ‘live’ data or the original machine, thereby preventing any accidental tampering of
evidence in the process so as to preserve the integrity of the evidence as it is.
The investigation on the machine was conducted by the use of various software which are as
follows:
- Access Data® FTK® Imager Version 4.1.1.1
- ProDiscover Version 7.0.0.3
- OSForensics
These software has been used to investigate the materials extracted from the device in question.
The materials found are
Hard drive image 2009-11-19.E01 (of the original sold computer) – E01
Second drive image purporting to be of the same computer – AD1, AD2
Hard drive image 2009-12-01.E01 (of the suspect’s replacement computer seize from M57) –
E01
Second drive image purporting to be of the same computer – AD1, AD2, AD3
The hard drive images were extracted by using FTK Imager by the use of Forensic Acquisition feature,
thereby creating a physical image of the drive in question.
The investigation process is mainly comprised sifting through the files of the computer and making
sure to gather inculpatory evidences that could be used as a base to set up an argument for or
against the owner of the computer, Jo, the employee of M57 organization. The sifting procedure has
intentional or not. Hence, the contamination of the evidence and the comparison of the two image
files of the original machine extracted from the device in question is also an important part of the
case.
The police as in pursuit of the thumb drive of the suspect, Jo, who is an employee of the
organization, M57. After the permission granted by the CEO of the organization, the police shall be
imaging the remaining workstation of the said organization and in the process, try to find out how
the specific organization or the workstation of that specific organization, or the employee employed
in the organization had come about to become involved in this specific case regarding the exchange
and use of drugs.
c. The Investigation Procedure
After creating a digital copy of the machine, all the investigation procedure has been conducted on
the copy of the ‘live’ data or the original machine, thereby preventing any accidental tampering of
evidence in the process so as to preserve the integrity of the evidence as it is.
The investigation on the machine was conducted by the use of various software which are as
follows:
- Access Data® FTK® Imager Version 4.1.1.1
- ProDiscover Version 7.0.0.3
- OSForensics
These software has been used to investigate the materials extracted from the device in question.
The materials found are
Hard drive image 2009-11-19.E01 (of the original sold computer) – E01
Second drive image purporting to be of the same computer – AD1, AD2
Hard drive image 2009-12-01.E01 (of the suspect’s replacement computer seize from M57) –
E01
Second drive image purporting to be of the same computer – AD1, AD2, AD3
The hard drive images were extracted by using FTK Imager by the use of Forensic Acquisition feature,
thereby creating a physical image of the drive in question.
The investigation process is mainly comprised sifting through the files of the computer and making
sure to gather inculpatory evidences that could be used as a base to set up an argument for or
against the owner of the computer, Jo, the employee of M57 organization. The sifting procedure has
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
been done using the FTK Imager software to mount and read the hard drive images that have been
extracted from the device and the use of ProDiscover to sift through the files of the suspect
computer and make a timeline out of it. The OSForensics software has been used to create a hash
lookup and make the system files in the hard drive image invisible so that it would be possible for
the investigators to concentration on the specific files that has been presented in the drive image.
The Windows 7 hash set has been used to hide the system files of windows and provide the normal
documents for the work to be done. Fig 1 shows the use of the hash set to bring out the necessary
files downloaded by the user of or related to methamphetamine of amphetamine. There has been
only one encrypted file process in the drive that could inculpate the suspect as a seller of the drugs
that has been searched for using the device in question (Duan, Gu & Whinston, 2008).
Additionally, file slack tools and file slack analysis tools from the OSForensics software has been used
to locate files whose extensions have been changed to conceal the file from the eyes of the
investigators. Other tools to reveal concealed hidden folders and files, encrypted data and protected
documents have been used during the investigation procedure so as to go through a thorough
analysis of the drive image and make sure that none of the evidence is overlooked during the
investigation process.
The use of these software and method have allowed the investigator to go through the device and
form a proper narrative that could be assumed to be closer to the reality of the past events and so
that the investigation could be performed in a swift and accurate manner with the least amount of
contamination creeping into the drive images that have been extracted from the device in question.
Such methods have also been used to make comparison between the two separate file images that
have been collected by the investigators and to try and point out the changes that has taken place
between the two imaged due or the ‘tampering’ of the evidence by the ‘foul play’ of the police. The
investigators have also tried by these methods to restore the conditions of the files that has been
tampered with to the best of their ability and to document the tampering and try to set up a proper
investigative narrative to discuss the nature of the tampering that has taken place.
been done using the FTK Imager software to mount and read the hard drive images that have been
extracted from the device and the use of ProDiscover to sift through the files of the suspect
computer and make a timeline out of it. The OSForensics software has been used to create a hash
lookup and make the system files in the hard drive image invisible so that it would be possible for
the investigators to concentration on the specific files that has been presented in the drive image.
The Windows 7 hash set has been used to hide the system files of windows and provide the normal
documents for the work to be done. Fig 1 shows the use of the hash set to bring out the necessary
files downloaded by the user of or related to methamphetamine of amphetamine. There has been
only one encrypted file process in the drive that could inculpate the suspect as a seller of the drugs
that has been searched for using the device in question (Duan, Gu & Whinston, 2008).
Additionally, file slack tools and file slack analysis tools from the OSForensics software has been used
to locate files whose extensions have been changed to conceal the file from the eyes of the
investigators. Other tools to reveal concealed hidden folders and files, encrypted data and protected
documents have been used during the investigation procedure so as to go through a thorough
analysis of the drive image and make sure that none of the evidence is overlooked during the
investigation process.
The use of these software and method have allowed the investigator to go through the device and
form a proper narrative that could be assumed to be closer to the reality of the past events and so
that the investigation could be performed in a swift and accurate manner with the least amount of
contamination creeping into the drive images that have been extracted from the device in question.
Such methods have also been used to make comparison between the two separate file images that
have been collected by the investigators and to try and point out the changes that has taken place
between the two imaged due or the ‘tampering’ of the evidence by the ‘foul play’ of the police. The
investigators have also tried by these methods to restore the conditions of the files that has been
tampered with to the best of their ability and to document the tampering and try to set up a proper
investigative narrative to discuss the nature of the tampering that has taken place.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
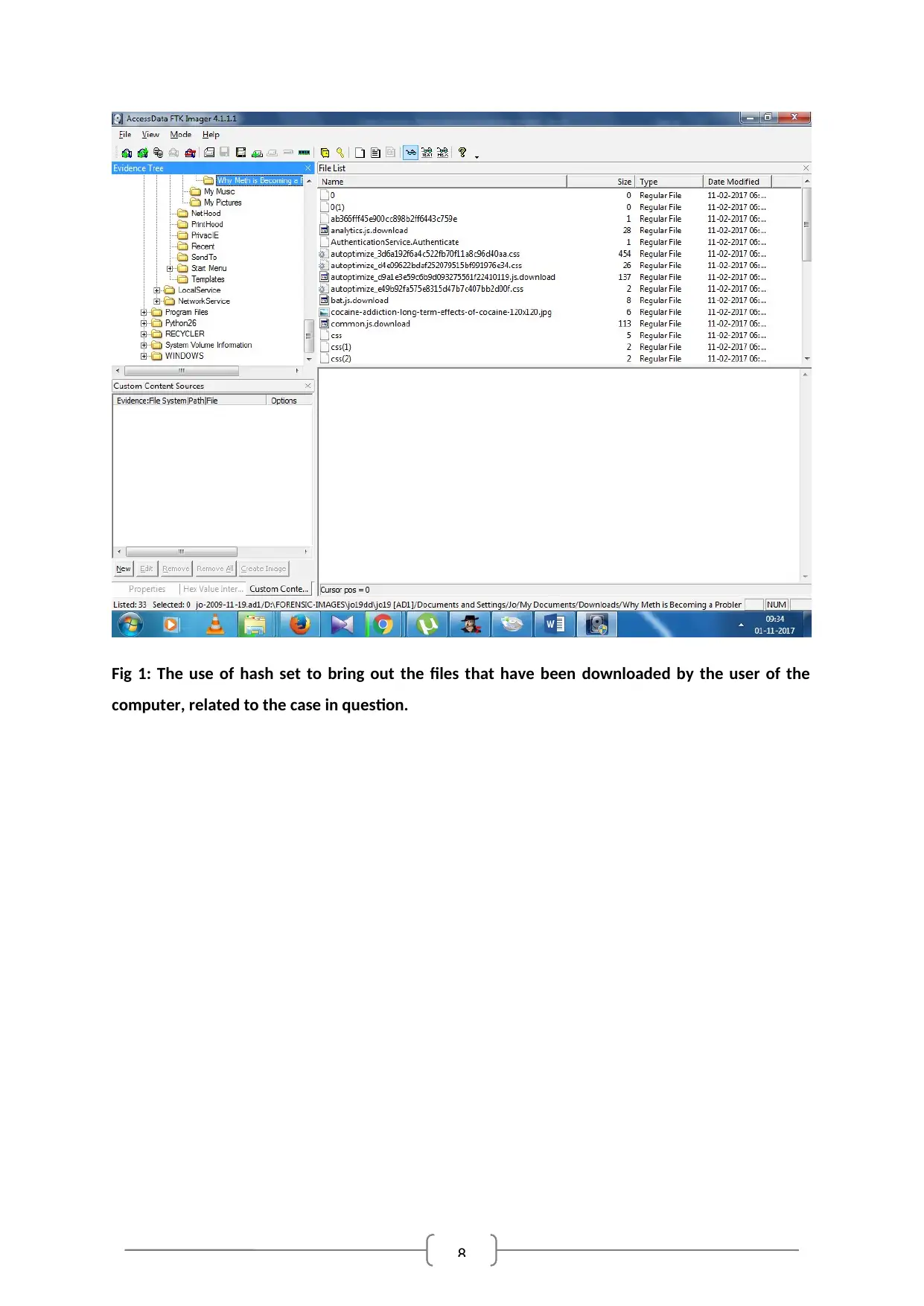
8
Fig 1: The use of hash set to bring out the files that have been downloaded by the user of the
computer, related to the case in question.
Fig 1: The use of hash set to bring out the files that have been downloaded by the user of the
computer, related to the case in question.
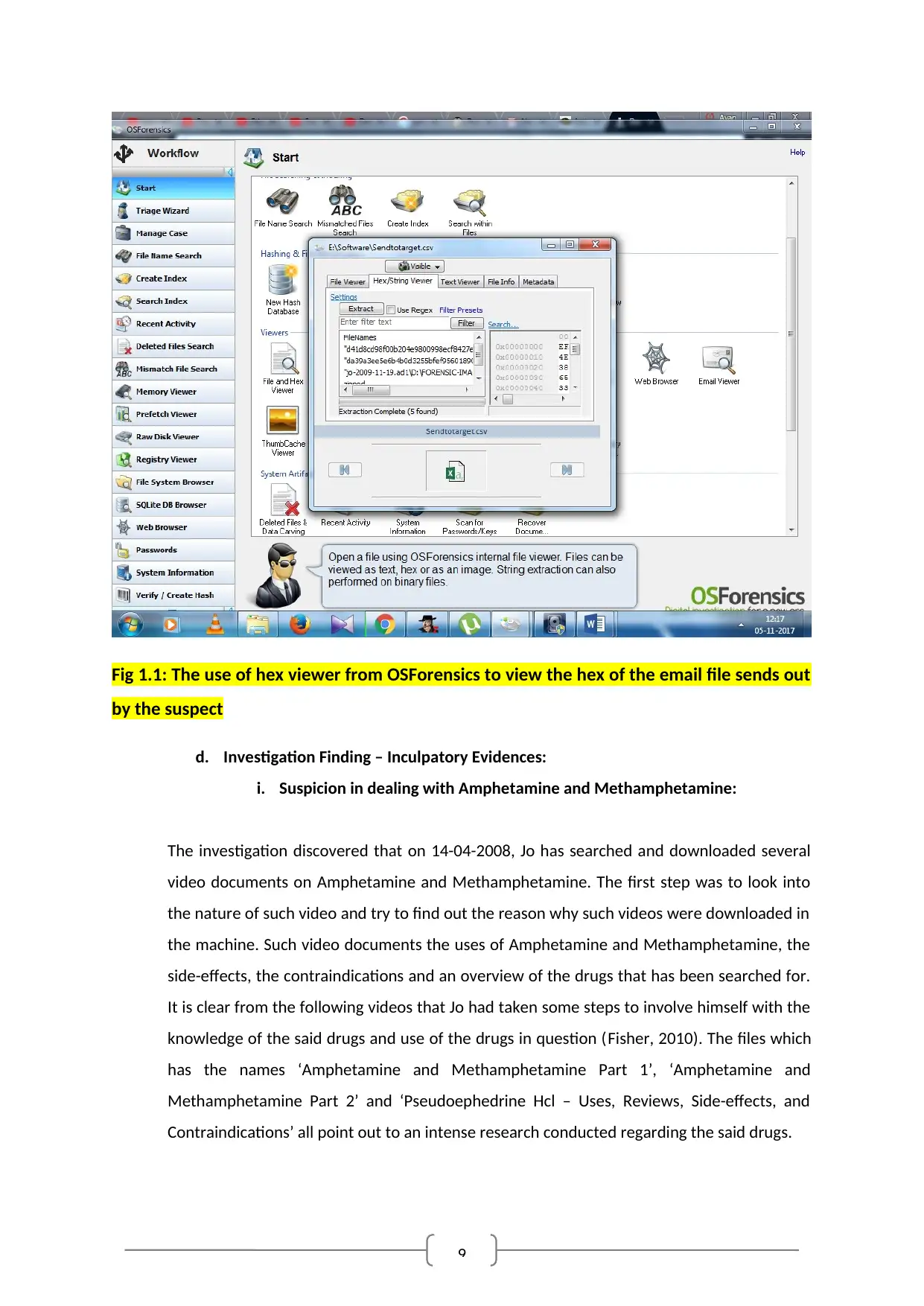
9
Fig 1.1: The use of hex viewer from OSForensics to view the hex of the email file sends out
by the suspect
d. Investigation Finding – Inculpatory Evidences:
i. Suspicion in dealing with Amphetamine and Methamphetamine:
The investigation discovered that on 14-04-2008, Jo has searched and downloaded several
video documents on Amphetamine and Methamphetamine. The first step was to look into
the nature of such video and try to find out the reason why such videos were downloaded in
the machine. Such video documents the uses of Amphetamine and Methamphetamine, the
side-effects, the contraindications and an overview of the drugs that has been searched for.
It is clear from the following videos that Jo had taken some steps to involve himself with the
knowledge of the said drugs and use of the drugs in question (Fisher, 2010). The files which
has the names ‘Amphetamine and Methamphetamine Part 1’, ‘Amphetamine and
Methamphetamine Part 2’ and ‘Pseudoephedrine Hcl – Uses, Reviews, Side-effects, and
Contraindications’ all point out to an intense research conducted regarding the said drugs.
Fig 1.1: The use of hex viewer from OSForensics to view the hex of the email file sends out
by the suspect
d. Investigation Finding – Inculpatory Evidences:
i. Suspicion in dealing with Amphetamine and Methamphetamine:
The investigation discovered that on 14-04-2008, Jo has searched and downloaded several
video documents on Amphetamine and Methamphetamine. The first step was to look into
the nature of such video and try to find out the reason why such videos were downloaded in
the machine. Such video documents the uses of Amphetamine and Methamphetamine, the
side-effects, the contraindications and an overview of the drugs that has been searched for.
It is clear from the following videos that Jo had taken some steps to involve himself with the
knowledge of the said drugs and use of the drugs in question (Fisher, 2010). The files which
has the names ‘Amphetamine and Methamphetamine Part 1’, ‘Amphetamine and
Methamphetamine Part 2’ and ‘Pseudoephedrine Hcl – Uses, Reviews, Side-effects, and
Contraindications’ all point out to an intense research conducted regarding the said drugs.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
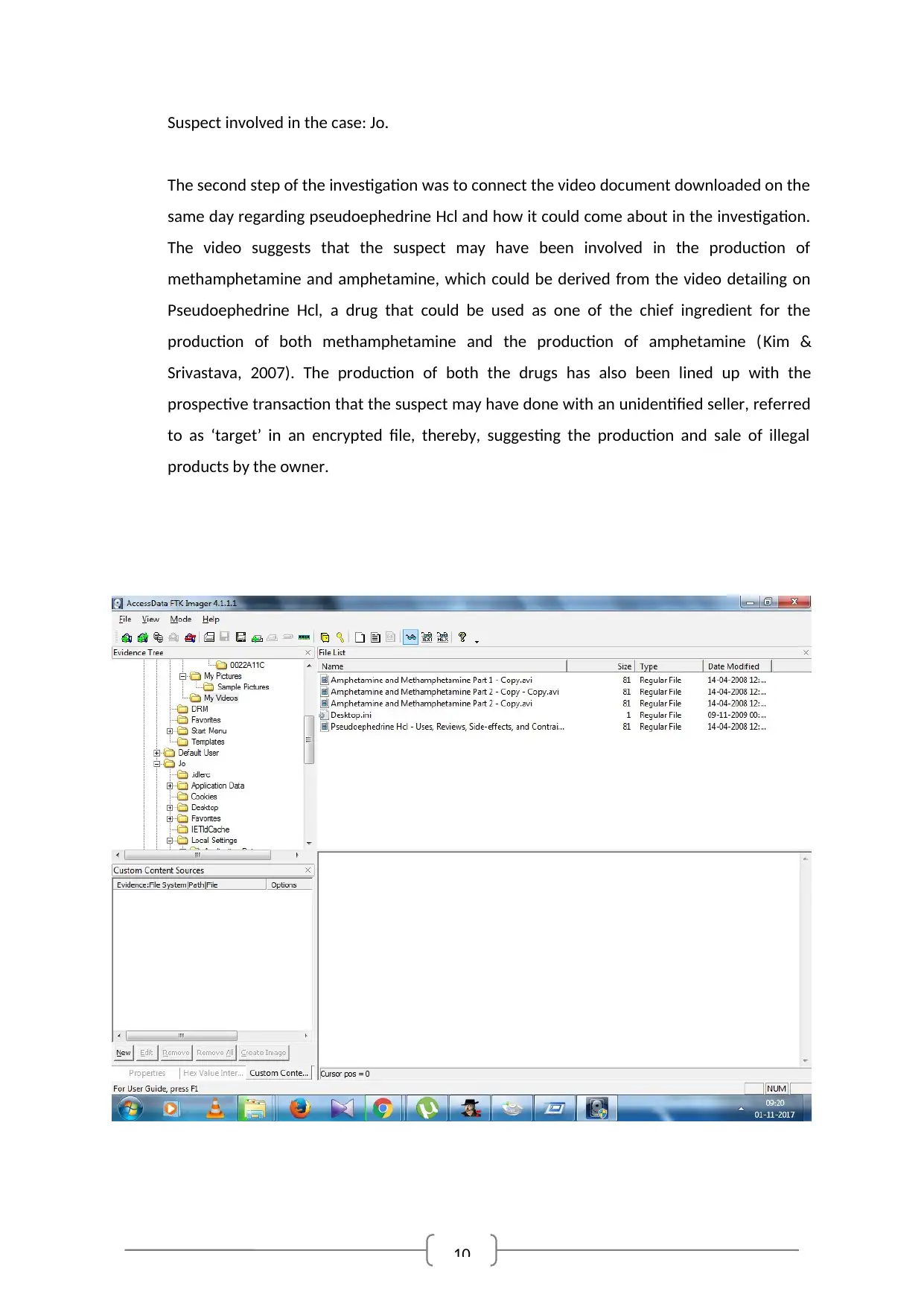
10
Suspect involved in the case: Jo.
The second step of the investigation was to connect the video document downloaded on the
same day regarding pseudoephedrine Hcl and how it could come about in the investigation.
The video suggests that the suspect may have been involved in the production of
methamphetamine and amphetamine, which could be derived from the video detailing on
Pseudoephedrine Hcl, a drug that could be used as one of the chief ingredient for the
production of both methamphetamine and the production of amphetamine (Kim &
Srivastava, 2007). The production of both the drugs has also been lined up with the
prospective transaction that the suspect may have done with an unidentified seller, referred
to as ‘target’ in an encrypted file, thereby, suggesting the production and sale of illegal
products by the owner.
Suspect involved in the case: Jo.
The second step of the investigation was to connect the video document downloaded on the
same day regarding pseudoephedrine Hcl and how it could come about in the investigation.
The video suggests that the suspect may have been involved in the production of
methamphetamine and amphetamine, which could be derived from the video detailing on
Pseudoephedrine Hcl, a drug that could be used as one of the chief ingredient for the
production of both methamphetamine and the production of amphetamine (Kim &
Srivastava, 2007). The production of both the drugs has also been lined up with the
prospective transaction that the suspect may have done with an unidentified seller, referred
to as ‘target’ in an encrypted file, thereby, suggesting the production and sale of illegal
products by the owner.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
11
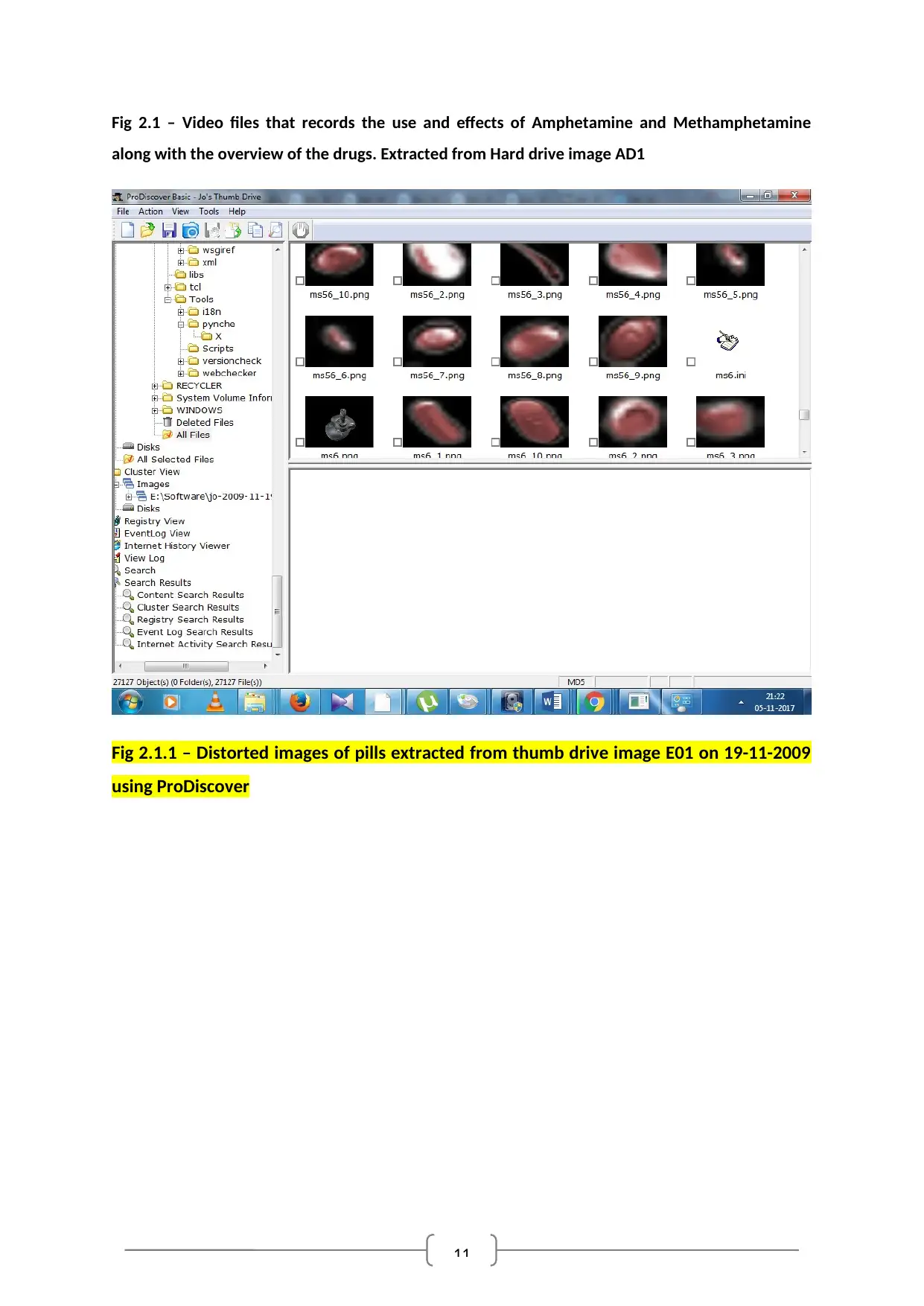
Fig 2.1 – Video files that records the use and effects of Amphetamine and Methamphetamine
along with the overview of the drugs. Extracted from Hard drive image AD1
Fig 2.1.1 – Distorted images of pills extracted from thumb drive image E01 on 19-11-2009
using ProDiscover
Fig 2.1 – Video files that records the use and effects of Amphetamine and Methamphetamine
along with the overview of the drugs. Extracted from Hard drive image AD1
Fig 2.1.1 – Distorted images of pills extracted from thumb drive image E01 on 19-11-2009
using ProDiscover
12
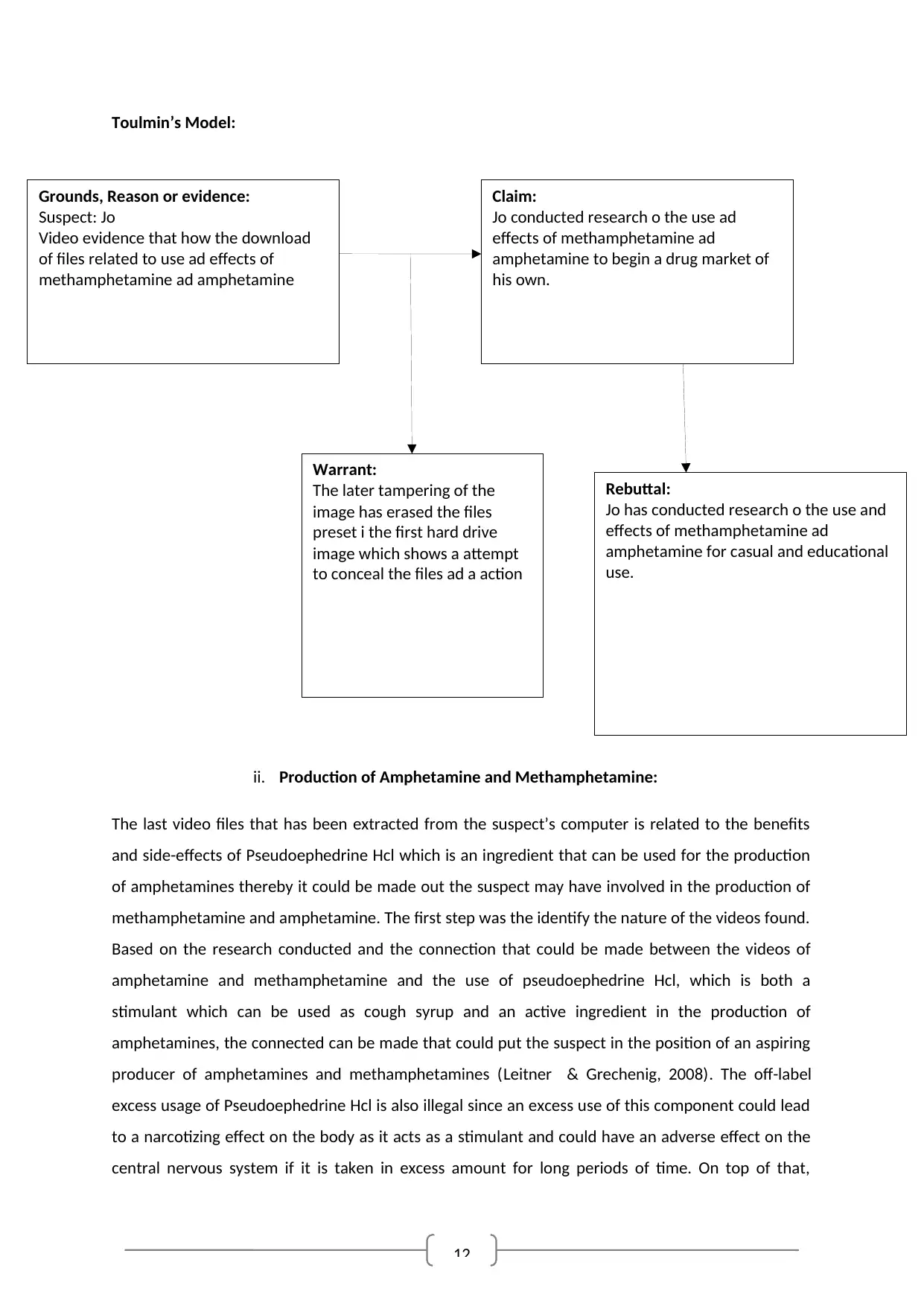
Grounds, Reason or evidence:
Suspect: Jo
Video evidence that how the download
of files related to use ad effects of
methamphetamine ad amphetamine
Claim:
Jo conducted research o the use ad
effects of methamphetamine ad
amphetamine to begin a drug market of
his own.
Rebuttal:
Jo has conducted research o the use and
effects of methamphetamine ad
amphetamine for casual and educational
use.
Warrant:
The later tampering of the
image has erased the files
preset i the first hard drive
image which shows a attempt
to conceal the files ad a action
Toulmin’s Model:
ii. Production of Amphetamine and Methamphetamine:
The last video files that has been extracted from the suspect’s computer is related to the benefits
and side-effects of Pseudoephedrine Hcl which is an ingredient that can be used for the production
of amphetamines thereby it could be made out the suspect may have involved in the production of
methamphetamine and amphetamine. The first step was the identify the nature of the videos found.
Based on the research conducted and the connection that could be made between the videos of
amphetamine and methamphetamine and the use of pseudoephedrine Hcl, which is both a
stimulant which can be used as cough syrup and an active ingredient in the production of
amphetamines, the connected can be made that could put the suspect in the position of an aspiring
producer of amphetamines and methamphetamines (Leitner & Grechenig, 2008). The off-label
excess usage of Pseudoephedrine Hcl is also illegal since an excess use of this component could lead
to a narcotizing effect on the body as it acts as a stimulant and could have an adverse effect on the
central nervous system if it is taken in excess amount for long periods of time. On top of that,
Grounds, Reason or evidence:
Suspect: Jo
Video evidence that how the download
of files related to use ad effects of
methamphetamine ad amphetamine
Claim:
Jo conducted research o the use ad
effects of methamphetamine ad
amphetamine to begin a drug market of
his own.
Rebuttal:
Jo has conducted research o the use and
effects of methamphetamine ad
amphetamine for casual and educational
use.
Warrant:
The later tampering of the
image has erased the files
preset i the first hard drive
image which shows a attempt
to conceal the files ad a action
Toulmin’s Model:
ii. Production of Amphetamine and Methamphetamine:
The last video files that has been extracted from the suspect’s computer is related to the benefits
and side-effects of Pseudoephedrine Hcl which is an ingredient that can be used for the production
of amphetamines thereby it could be made out the suspect may have involved in the production of
methamphetamine and amphetamine. The first step was the identify the nature of the videos found.
Based on the research conducted and the connection that could be made between the videos of
amphetamine and methamphetamine and the use of pseudoephedrine Hcl, which is both a
stimulant which can be used as cough syrup and an active ingredient in the production of
amphetamines, the connected can be made that could put the suspect in the position of an aspiring
producer of amphetamines and methamphetamines (Leitner & Grechenig, 2008). The off-label
excess usage of Pseudoephedrine Hcl is also illegal since an excess use of this component could lead
to a narcotizing effect on the body as it acts as a stimulant and could have an adverse effect on the
central nervous system if it is taken in excess amount for long periods of time. On top of that,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 33
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
