Comparative Analysis of Cyber Intrusion Detection Research Papers
VerifiedAdded on 2022/09/18
|8
|1581
|19
Report
AI Summary
This report analyzes two research papers focused on cyber intrusion detection, a critical aspect of modern infrastructure. The first paper, "A whale optimization algorithm-trained artificial neural network for smart grid cyber intrusion detection," introduces a novel model utilizing a whale optimization algorithm (WOA) to train an artificial neural network (ANN) for identifying cyber-attacks in smart grids. The model classifies binary, triple, and multi-class cyber-attacks and power-system incidents. The second paper, "Network Intrusion Detection Framework Based on Whale Swarm Algorithm and Artificial Neural Network in Cloud Computing," proposes a framework based on the Whale Swarm Algorithm and ANN to detect and prevent denial-of-service attacks in cloud computing environments. Both papers highlight the use of AI techniques to address vulnerabilities and enhance security in critical systems. The report summarizes the research problems, proposed solutions, results, conclusions, and future work outlined in each paper. The research emphasizes the importance of timely and accurate threat detection in evolving technological landscapes.

Running head: ANALYSIS OF RESEARCH PAPER
ANALYSIS OF RESEARCH PAPER
Name of the Student
Name of the university
Author note
ANALYSIS OF RESEARCH PAPER
Name of the Student
Name of the university
Author note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1ANALYSIS OF RESEARCH PAPER
A whale optimization algorithm-trained artificial neural network for smart grid cyber
intrusion detection
Research Problem
As per the study Haghnegahdar and Wang (2019) smart grid can be considered as an
emerging as well as evolving next-generation power system. Smart grid falls under the
purview of cyber infrastructure and thus this system needs to detect and deal with the cyber
attacks in time so that loss can be prevented. It is a complex system and is a combination of
different computation technologies, advanced communications as well as recognition in the
current stage of power systems. High-quality and error-free data is required by the system.
The problem is that smart grids are critical infrastructures and thus subjected to various risks
of misoperations.
Proposed solution
The authors have proposed a new model that can detect intrusion and this particular
model can also classify binary-class, multi-class as well as triple-class cyber attacks along
with the power-system incidents as well. The model relies on whale optimization algorithm
(WOA)-trained artificial neural network (ANN). The proposed model is expected to address
the various challenges related to cyber attacks. The ANN is one of the classification tools and
this is inspired by activities related to biological neurons in the human brain (Haghnegahdar
& Wang, 2019). It is different from the other classification methods as relationships in this
are generated dynamically from the training inputs contrary to which the traditional methods
rely on predefined relations.
WOA is nature-inspired population-based novel stochastic optimization technique and
it has not been many days that this has been developed. This makes use of a set of search
agents thus providing a solution that best suits the optimization problem. This technique
imitates behavior of the humpback whales like in situation they hunt through the bubble net
A whale optimization algorithm-trained artificial neural network for smart grid cyber
intrusion detection
Research Problem
As per the study Haghnegahdar and Wang (2019) smart grid can be considered as an
emerging as well as evolving next-generation power system. Smart grid falls under the
purview of cyber infrastructure and thus this system needs to detect and deal with the cyber
attacks in time so that loss can be prevented. It is a complex system and is a combination of
different computation technologies, advanced communications as well as recognition in the
current stage of power systems. High-quality and error-free data is required by the system.
The problem is that smart grids are critical infrastructures and thus subjected to various risks
of misoperations.
Proposed solution
The authors have proposed a new model that can detect intrusion and this particular
model can also classify binary-class, multi-class as well as triple-class cyber attacks along
with the power-system incidents as well. The model relies on whale optimization algorithm
(WOA)-trained artificial neural network (ANN). The proposed model is expected to address
the various challenges related to cyber attacks. The ANN is one of the classification tools and
this is inspired by activities related to biological neurons in the human brain (Haghnegahdar
& Wang, 2019). It is different from the other classification methods as relationships in this
are generated dynamically from the training inputs contrary to which the traditional methods
rely on predefined relations.
WOA is nature-inspired population-based novel stochastic optimization technique and
it has not been many days that this has been developed. This makes use of a set of search
agents thus providing a solution that best suits the optimization problem. This technique
imitates behavior of the humpback whales like in situation they hunt through the bubble net
2ANALYSIS OF RESEARCH PAPER
hunting. The mechanism used by the humpback whales is to circle around the prey and hunt
on them.
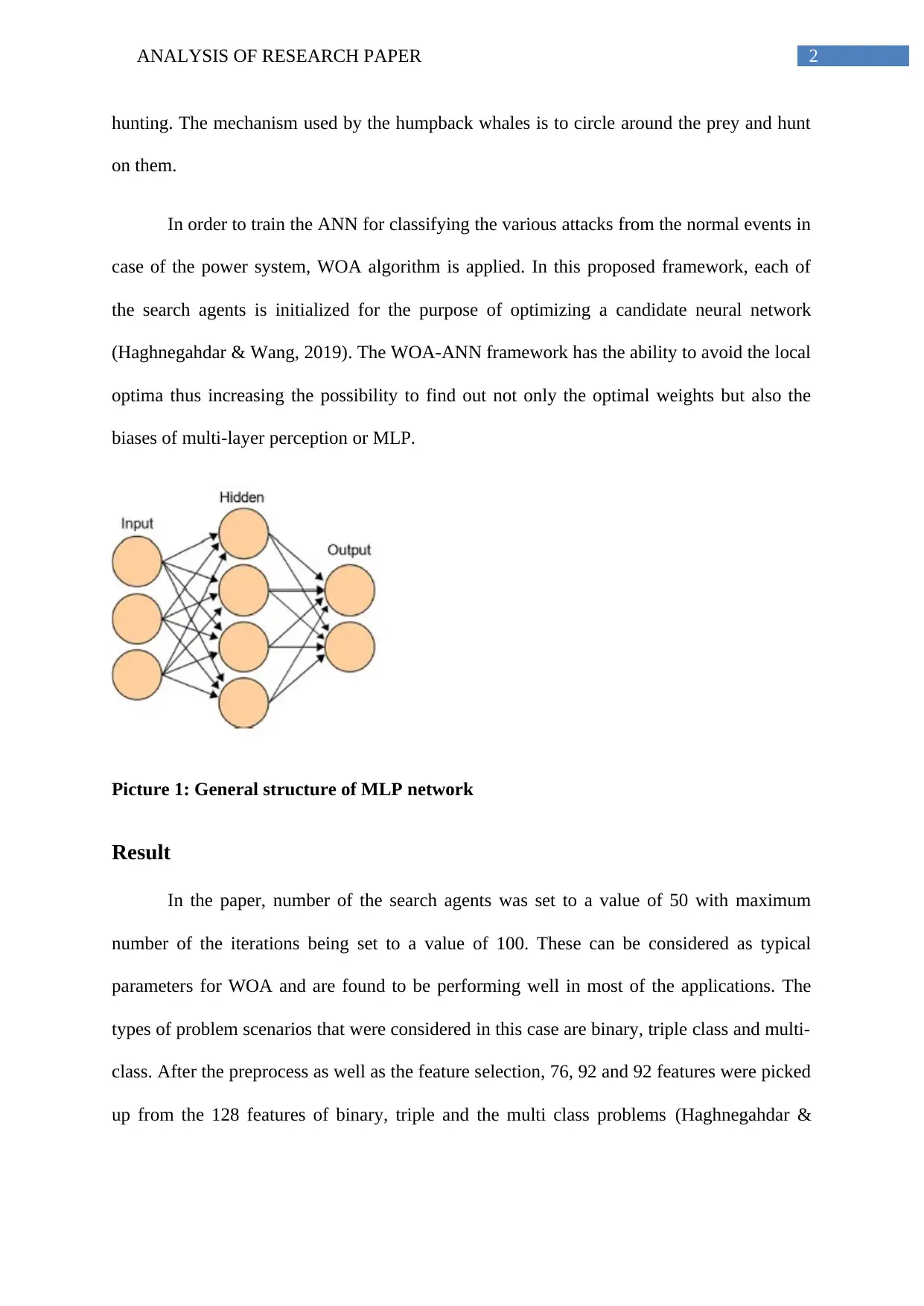
In order to train the ANN for classifying the various attacks from the normal events in
case of the power system, WOA algorithm is applied. In this proposed framework, each of
the search agents is initialized for the purpose of optimizing a candidate neural network
(Haghnegahdar & Wang, 2019). The WOA-ANN framework has the ability to avoid the local
optima thus increasing the possibility to find out not only the optimal weights but also the
biases of multi-layer perception or MLP.
Picture 1: General structure of MLP network
Result
In the paper, number of the search agents was set to a value of 50 with maximum
number of the iterations being set to a value of 100. These can be considered as typical
parameters for WOA and are found to be performing well in most of the applications. The
types of problem scenarios that were considered in this case are binary, triple class and multi-
class. After the preprocess as well as the feature selection, 76, 92 and 92 features were picked
up from the 128 features of binary, triple and the multi class problems (Haghnegahdar &
hunting. The mechanism used by the humpback whales is to circle around the prey and hunt
on them.
In order to train the ANN for classifying the various attacks from the normal events in
case of the power system, WOA algorithm is applied. In this proposed framework, each of
the search agents is initialized for the purpose of optimizing a candidate neural network
(Haghnegahdar & Wang, 2019). The WOA-ANN framework has the ability to avoid the local
optima thus increasing the possibility to find out not only the optimal weights but also the
biases of multi-layer perception or MLP.
Picture 1: General structure of MLP network
Result
In the paper, number of the search agents was set to a value of 50 with maximum
number of the iterations being set to a value of 100. These can be considered as typical
parameters for WOA and are found to be performing well in most of the applications. The
types of problem scenarios that were considered in this case are binary, triple class and multi-
class. After the preprocess as well as the feature selection, 76, 92 and 92 features were picked
up from the 128 features of binary, triple and the multi class problems (Haghnegahdar &
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3ANALYSIS OF RESEARCH PAPER
Wang, 2019). The results suggested that accuracy increases gradually with the increase in the
number of iterations.
Conclusion
The main characteristic feature of a reliable smart grid is being able to detect threats
and that too on time. The high dependence of these on cyber infrastructures makes them
vulnerable to threats and thus comes the play of cyber security. In this research some of the
problems such as trapping in case of local minima have been overcome. The proposed
framework was made to detect failures in the power system that make use of datasets
associated with different levels of difficulty as well.
Future Work and comparison
The proposed framework can be modified in certain cases such as if any unknown
event gets verified by the human user of this model as being a real attack, it must be tagged a
verified label and should be added to the training library. This in turn should be made use of
for detection of various tasks in the future.
Network Intrusion Detection Framework Based on Whale Swarm Algorithm and
Artificial Neural Network in Cloud Computing
Research problem
As per research done by Fahad, Ahmed, and Kahar (2018) one of the rapidly
developing technology is the cloud computing technology. The business giants like the
Amazon, Microsoft and the others makes use of the technology for their business and
benefits. The cloud computing technology makes use of the flexible information technology
architecture which is easily accessible with the help of the internet all over. However, there
are certain drawbacks of the technology as well. There are numerous malicious attacks which
Wang, 2019). The results suggested that accuracy increases gradually with the increase in the
number of iterations.
Conclusion
The main characteristic feature of a reliable smart grid is being able to detect threats
and that too on time. The high dependence of these on cyber infrastructures makes them
vulnerable to threats and thus comes the play of cyber security. In this research some of the
problems such as trapping in case of local minima have been overcome. The proposed
framework was made to detect failures in the power system that make use of datasets
associated with different levels of difficulty as well.
Future Work and comparison
The proposed framework can be modified in certain cases such as if any unknown
event gets verified by the human user of this model as being a real attack, it must be tagged a
verified label and should be added to the training library. This in turn should be made use of
for detection of various tasks in the future.
Network Intrusion Detection Framework Based on Whale Swarm Algorithm and
Artificial Neural Network in Cloud Computing
Research problem
As per research done by Fahad, Ahmed, and Kahar (2018) one of the rapidly
developing technology is the cloud computing technology. The business giants like the
Amazon, Microsoft and the others makes use of the technology for their business and
benefits. The cloud computing technology makes use of the flexible information technology
architecture which is easily accessible with the help of the internet all over. However, there
are certain drawbacks of the technology as well. There are numerous malicious attacks which
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4ANALYSIS OF RESEARCH PAPER
are prevalent in the in the cloud services. Starting from the Denial of Services, Distributed
Denial of Services, Mann-in-the-Middle and many others. One of the serious threats to the
cloud services is obtained from the Denial of Services attack. The major focus of the research
is to determine the ways in which the attacks can be detected and prevented in the system.
Proposed solution
Whale Optimizing Algorithm: The Whale optimizing algorithm is one of the latest
techniques of optimizing problems. There are three operators associated with the algorithm,
which includes prey searching, prey encircling and the behavior of eating of the humpback
whales by using the method of bubble net foraging. The mathematical model of WOA was
prepared and it was found out that this algorithm can be implemented for solving a large
number of challenging problems and issues and has a lot of other applications as well (Fahad
et al., 2018). It was also tested and the performance was analysed on several functions and
also implemented for case study of Photonic crystal filter.
The behavior of the optimal search agent can be determined with the help of the following
equations:
X(t+1)= X* (t)- B.S
S=|K.X*(t)-X(t)|
(Where t is the current iteration, and are the coefficient vectors, is the position vector of the
current best solution obtained and is the position vector.)
Exploitation phase: the mechanism of bubble net foraging is deployed by the humpback
whales so that multiple whales can feed at the same time.
The formula for the spiral updating position mechanism is given by:
are prevalent in the in the cloud services. Starting from the Denial of Services, Distributed
Denial of Services, Mann-in-the-Middle and many others. One of the serious threats to the
cloud services is obtained from the Denial of Services attack. The major focus of the research
is to determine the ways in which the attacks can be detected and prevented in the system.
Proposed solution
Whale Optimizing Algorithm: The Whale optimizing algorithm is one of the latest
techniques of optimizing problems. There are three operators associated with the algorithm,
which includes prey searching, prey encircling and the behavior of eating of the humpback
whales by using the method of bubble net foraging. The mathematical model of WOA was
prepared and it was found out that this algorithm can be implemented for solving a large
number of challenging problems and issues and has a lot of other applications as well (Fahad
et al., 2018). It was also tested and the performance was analysed on several functions and
also implemented for case study of Photonic crystal filter.
The behavior of the optimal search agent can be determined with the help of the following
equations:
X(t+1)= X* (t)- B.S
S=|K.X*(t)-X(t)|
(Where t is the current iteration, and are the coefficient vectors, is the position vector of the
current best solution obtained and is the position vector.)
Exploitation phase: the mechanism of bubble net foraging is deployed by the humpback
whales so that multiple whales can feed at the same time.
The formula for the spiral updating position mechanism is given by:

5ANALYSIS OF RESEARCH PAPER
X(t+1)=S.eml. cos(2πl)+X*(t)
Exploration phase: This phase is also known as the search for prey phase. It is the phase
where humpback whales which can be regarded as the search agents search for their prey or
the best solution in random direction and communicate and change the position of one whale
according to the other (Fahad et al., 2018).
S=|K.Xrand(t)-X(t)|
X(t+1)=Xrand-B.S
Where, Xrand is a random position vector which is chosen from the current population.
Result
With the help of this algorithm, the denial of the services attack can be detected. Once
the attack is detected, the cloud computing technology can eliminate any possible chances of
the attack from the entire system.
Conclusions
The main purpose of this project is to provide a new design which is classified on the
basis of Whale Swarm Algorithm and Hybridised artificial neural network that could feed
into the biases and weight of ANN. But without any derivative dataset this model is useless.
Thus this dataset has been prepared based on a design belonging to our test bed which is
developed by the network topology named TUIDS over Eucalyptus Cloud Computing. Using
MATLAB we can analyse the log output from this data set.
Future work and comparison
This design and model can be improved further in the future in order to enhance the
process of detection of the attacks in the cloud computing services. However, the services can
X(t+1)=S.eml. cos(2πl)+X*(t)
Exploration phase: This phase is also known as the search for prey phase. It is the phase
where humpback whales which can be regarded as the search agents search for their prey or
the best solution in random direction and communicate and change the position of one whale
according to the other (Fahad et al., 2018).
S=|K.Xrand(t)-X(t)|
X(t+1)=Xrand-B.S
Where, Xrand is a random position vector which is chosen from the current population.
Result
With the help of this algorithm, the denial of the services attack can be detected. Once
the attack is detected, the cloud computing technology can eliminate any possible chances of
the attack from the entire system.
Conclusions
The main purpose of this project is to provide a new design which is classified on the
basis of Whale Swarm Algorithm and Hybridised artificial neural network that could feed
into the biases and weight of ANN. But without any derivative dataset this model is useless.
Thus this dataset has been prepared based on a design belonging to our test bed which is
developed by the network topology named TUIDS over Eucalyptus Cloud Computing. Using
MATLAB we can analyse the log output from this data set.
Future work and comparison
This design and model can be improved further in the future in order to enhance the
process of detection of the attacks in the cloud computing services. However, the services can
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6ANALYSIS OF RESEARCH PAPER
be improved with the help of the encryption algorithm which is extremely important and
essential when one is dealing with the cloud computing services and technologies (Fahad et
al., 2018). This is much simpler that WOA and can be used for encrypting all the data
available over the cloud. The private cloud technology allows the security of the data better
than the others.
be improved with the help of the encryption algorithm which is extremely important and
essential when one is dealing with the cloud computing services and technologies (Fahad et
al., 2018). This is much simpler that WOA and can be used for encrypting all the data
available over the cloud. The private cloud technology allows the security of the data better
than the others.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7ANALYSIS OF RESEARCH PAPER
References
Fahad, A. M., Ahmed, A. A., & Kahar, M. N. M. (2018). Network intrusion detection
framework based on whale swarm algorithm and artificial neural network in cloud
computing. Paper presented at the International Conference on Intelligent Computing
& Optimization.
Haghnegahdar, L., & Wang, Y. (2019). A whale optimization algorithm-trained artificial
neural network for smart grid cyber intrusion detection. Neural Computing and
Applications, 1-15.
References
Fahad, A. M., Ahmed, A. A., & Kahar, M. N. M. (2018). Network intrusion detection
framework based on whale swarm algorithm and artificial neural network in cloud
computing. Paper presented at the International Conference on Intelligent Computing
& Optimization.
Haghnegahdar, L., & Wang, Y. (2019). A whale optimization algorithm-trained artificial
neural network for smart grid cyber intrusion detection. Neural Computing and
Applications, 1-15.
1 out of 8
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

