Cyber Law: Analysis of Telstra Security Report 2018
VerifiedAdded on 2020/10/22
|16
|5193
|369
Report
AI Summary
This report provides a comprehensive analysis of cyber law, specifically focusing on the security challenges and their impact on businesses, referencing the Telstra Security Report 2018. It explores the evolutionary trends in security, including the increasing attention given to security in business, the challenges in detecting and responding to security incidents, and the impact of new technologies. The report further examines the implications of these trends on the current world, including the impact of security breaches on productivity, data integrity, intellectual property, reputation, and customer relationships. It also covers the application of legal and legislative considerations, such as the Data Privacy Act of 1988, and their role in securing data and mitigating cybercrime. Finally, the report predicts future trends, such as the evolution of ransomware, the expansion of artificial intelligence, IoT threats, and blockchain revolution, and the need for businesses to adapt to these evolving challenges. The report underscores the importance of public disclosure of breaches, data classification, and the need for companies to invest in research and development to stay ahead of cyber threats.

Cyber law 2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................1
Main Body.......................................................................................................................................1
A) The evolutionary view of the trend.........................................................................................1
B) Implication of the trend to the world that we live...................................................................3
C) Application of legal and legislative considerations in relation to the trend............................5
D) Prediction for the future .........................................................................................................7
CONCLUSION..............................................................................................................................10
REFERENCES..............................................................................................................................11
INTRODUCTION...........................................................................................................................1
Main Body.......................................................................................................................................1
A) The evolutionary view of the trend.........................................................................................1
B) Implication of the trend to the world that we live...................................................................3
C) Application of legal and legislative considerations in relation to the trend............................5
D) Prediction for the future .........................................................................................................7
CONCLUSION..............................................................................................................................10
REFERENCES..............................................................................................................................11

INTRODUCTION
Cyber law is an entire legal system that incorporates with the internet crimes, cyberspace
and relevant legal issues. It covers a broad area which encompassed in few areas like freedom of
expression, usage of and access to internet as well as entitled with covering online
confidentiality. The cyber law is preventing to reduce wide amount of damages imposed by
cybercrime such as protecting the information access, intellectual property and communications.
The project report is based on Telstra Security report 2018 on topic number 5 which creates
barriers in security challenge and Business impact. The Telstra Security report 2018 underpins
everything from customer experience to employee engagement. The project report is focuses to
stay prepared in the face of constantly evolving threats to cyber. The project report will outline
the evolutionary view of trends based on current, past and future in Security challenges and
business impact. The project report will further outline the implication of the trend to the world.
The project report will outline the application of laws with considerations in relation to the trend.
Lastly the project report will predict what is yet to happen and what to look out for in the future.
Main Body
Security challenges and business impact
A) The evolutionary view of the trend
Security is getting more attention in today's business culture. The Business and IT leaders
are concern about security due to difficulty in managing the Information technology environment
and while protecting in against the security threats (Werbach, 2017). There are top two
challenges regarding the Security challenges that are the ability to timely detect and effectively
responds the security incidents. There is impact of new technology namely, cloud mobile and
software defining the SDN. The new cyber security solutions and the methodologies are adopted
in Australia (Woods, 2018). 32% of the respondents indicates that the training of staff in security
was a major challenge. The challenges are regarding the ability to detect and respond to security
incidents. The another challenge is emerging the new technologies.
There is challenge of internal awareness and formal training. The business are facing
challenge for giving their employees training about the security. There is challenge of cost of
compliance. The business are facing the challenges of Vendor interoperability. There is shortage
of skill labour in order to overcome the Security challenge in Business (Ohlin, 2016). The
business are facing the challenge of communication with their executive team there is lack of
1
Cyber law is an entire legal system that incorporates with the internet crimes, cyberspace
and relevant legal issues. It covers a broad area which encompassed in few areas like freedom of
expression, usage of and access to internet as well as entitled with covering online
confidentiality. The cyber law is preventing to reduce wide amount of damages imposed by
cybercrime such as protecting the information access, intellectual property and communications.
The project report is based on Telstra Security report 2018 on topic number 5 which creates
barriers in security challenge and Business impact. The Telstra Security report 2018 underpins
everything from customer experience to employee engagement. The project report is focuses to
stay prepared in the face of constantly evolving threats to cyber. The project report will outline
the evolutionary view of trends based on current, past and future in Security challenges and
business impact. The project report will further outline the implication of the trend to the world.
The project report will outline the application of laws with considerations in relation to the trend.
Lastly the project report will predict what is yet to happen and what to look out for in the future.
Main Body
Security challenges and business impact
A) The evolutionary view of the trend
Security is getting more attention in today's business culture. The Business and IT leaders
are concern about security due to difficulty in managing the Information technology environment
and while protecting in against the security threats (Werbach, 2017). There are top two
challenges regarding the Security challenges that are the ability to timely detect and effectively
responds the security incidents. There is impact of new technology namely, cloud mobile and
software defining the SDN. The new cyber security solutions and the methodologies are adopted
in Australia (Woods, 2018). 32% of the respondents indicates that the training of staff in security
was a major challenge. The challenges are regarding the ability to detect and respond to security
incidents. The another challenge is emerging the new technologies.
There is challenge of internal awareness and formal training. The business are facing
challenge for giving their employees training about the security. There is challenge of cost of
compliance. The business are facing the challenges of Vendor interoperability. There is shortage
of skill labour in order to overcome the Security challenge in Business (Ohlin, 2016). The
business are facing the challenge of communication with their executive team there is lack of
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

understanding among them. According to the study of Carbon Black highlights there is
emergence of creative and non-malware attacks like portray the Chief Information Security
Officer (CISO) while attempting to access the corporate IP and the spoofing login systems to
appear authenticity and asking employees for their personal details and also utilising the
automation and configuration management frameworks like PowerShell. There is lack of
visibility with the legacy anti virus solutions. The online collaboration tools are sharing files with
the co-workers and with external shareholders. This is against the privacy policy of the
companies (Watts, 2016). The greatest risks can be defined that the Information Technology
security practitioners are associating with the use of social media at the workplace. The many
incidents and the security breaches are reported in the year 2017 (Tryfonas and Li, 2016). The
security breach is higher in Asia. Pacific and Europe. The most common virus and malware
outbreaks the employee error in Europe. There is need of Employees awareness in the security
risks and the there is need of training.
The Security challenges are impacting the Business
Loss of productivity in business – There is loss of productivity due to the Security
challenge in Singapore, Australia and Europe. The serious impact is on APAC. The loss
of the productivity is expensive for the organisation they need to bear costs like wages,
rents and utilities. The business are facing the potential loss of the revenue when the
operations have been disrupted. In case when consumer are unable to complete purchase
transactions online due to the major security challenges (Calo, 2015). The Australia has
faced major lost productivity and has rated fourth in the Telstra Security 2016 survey that
is showing increasing concerns based on the possible impact as the cyberattacks become
more prevalent in today's world.
Corrupted business data – The organizations are becoming more data driven. The
organization sees the data as the critical asset in order to drive differentiation. The
detection of corruption usually takes long time. The alteration of data during the security
breach that can be harder to detect. The companies are working to forward the
increasingly big data analytics and securing the business insights. The corrupted data was
the majorly influencing the organisation that are serving the APAC and third Europe.
Loss of intellectual property – The business are impacting the major loss of intellectual
property. There is loss of IP that continues to major impact. This might be results in the
2
emergence of creative and non-malware attacks like portray the Chief Information Security
Officer (CISO) while attempting to access the corporate IP and the spoofing login systems to
appear authenticity and asking employees for their personal details and also utilising the
automation and configuration management frameworks like PowerShell. There is lack of
visibility with the legacy anti virus solutions. The online collaboration tools are sharing files with
the co-workers and with external shareholders. This is against the privacy policy of the
companies (Watts, 2016). The greatest risks can be defined that the Information Technology
security practitioners are associating with the use of social media at the workplace. The many
incidents and the security breaches are reported in the year 2017 (Tryfonas and Li, 2016). The
security breach is higher in Asia. Pacific and Europe. The most common virus and malware
outbreaks the employee error in Europe. There is need of Employees awareness in the security
risks and the there is need of training.
The Security challenges are impacting the Business
Loss of productivity in business – There is loss of productivity due to the Security
challenge in Singapore, Australia and Europe. The serious impact is on APAC. The loss
of the productivity is expensive for the organisation they need to bear costs like wages,
rents and utilities. The business are facing the potential loss of the revenue when the
operations have been disrupted. In case when consumer are unable to complete purchase
transactions online due to the major security challenges (Calo, 2015). The Australia has
faced major lost productivity and has rated fourth in the Telstra Security 2016 survey that
is showing increasing concerns based on the possible impact as the cyberattacks become
more prevalent in today's world.
Corrupted business data – The organizations are becoming more data driven. The
organization sees the data as the critical asset in order to drive differentiation. The
detection of corruption usually takes long time. The alteration of data during the security
breach that can be harder to detect. The companies are working to forward the
increasingly big data analytics and securing the business insights. The corrupted data was
the majorly influencing the organisation that are serving the APAC and third Europe.
Loss of intellectual property – The business are impacting the major loss of intellectual
property. There is loss of IP that continues to major impact. This might be results in the
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

loss of competitive advantage to rivals. The company's are relaying on the innovation that
stay ahead and are costing highly for research and development in order to built IP (Alur,
Berger and Rexford, 2016.). The ACSC Threat Report 2017 indicates that financial losses
in financial year 2016 and 2017 was amounted to A$20 million that is increment of over
230 percent from A$8.6 million in financial year 2015 and 2016.
Loss of reputation – The businesses are facing the loss of reputation in Australia, APAC
and Europe. In order to rebuilt the reputation it requires the time and huge amount of
resources. The There is financial impact on the business due to the loss of reputation and
this puts negative impact to the brand.
Loss of customers – There is loss of customers and companies have distrust customers
and partners (Medwed, 2016). The Companies are facing the raising costs due to cyber
security breaches. There is psychological stress to workers due the increasing security
challenges among the companies.
The major Cybersecurity challenges and trends are as follows -
Ransomware evolution – The cybersecurity bane is Ransomware. The spreading virus
latches the customers and the businesses. The Ransomware attacks are the fastest
growing cybercrime (Cybersecurity Challenges and Trends, 2018).
Artificial intelligence expansion – The robots can be helping hand to defeat against the
cyber attacks. The robots do not have to pay by hourly work which is beneficial for the
companies. The timing is everything with malware and other vicious data manipulations.
3
stay ahead and are costing highly for research and development in order to built IP (Alur,
Berger and Rexford, 2016.). The ACSC Threat Report 2017 indicates that financial losses
in financial year 2016 and 2017 was amounted to A$20 million that is increment of over
230 percent from A$8.6 million in financial year 2015 and 2016.
Loss of reputation – The businesses are facing the loss of reputation in Australia, APAC
and Europe. In order to rebuilt the reputation it requires the time and huge amount of
resources. The There is financial impact on the business due to the loss of reputation and
this puts negative impact to the brand.
Loss of customers – There is loss of customers and companies have distrust customers
and partners (Medwed, 2016). The Companies are facing the raising costs due to cyber
security breaches. There is psychological stress to workers due the increasing security
challenges among the companies.
The major Cybersecurity challenges and trends are as follows -
Ransomware evolution – The cybersecurity bane is Ransomware. The spreading virus
latches the customers and the businesses. The Ransomware attacks are the fastest
growing cybercrime (Cybersecurity Challenges and Trends, 2018).
Artificial intelligence expansion – The robots can be helping hand to defeat against the
cyber attacks. The robots do not have to pay by hourly work which is beneficial for the
companies. The timing is everything with malware and other vicious data manipulations.
3
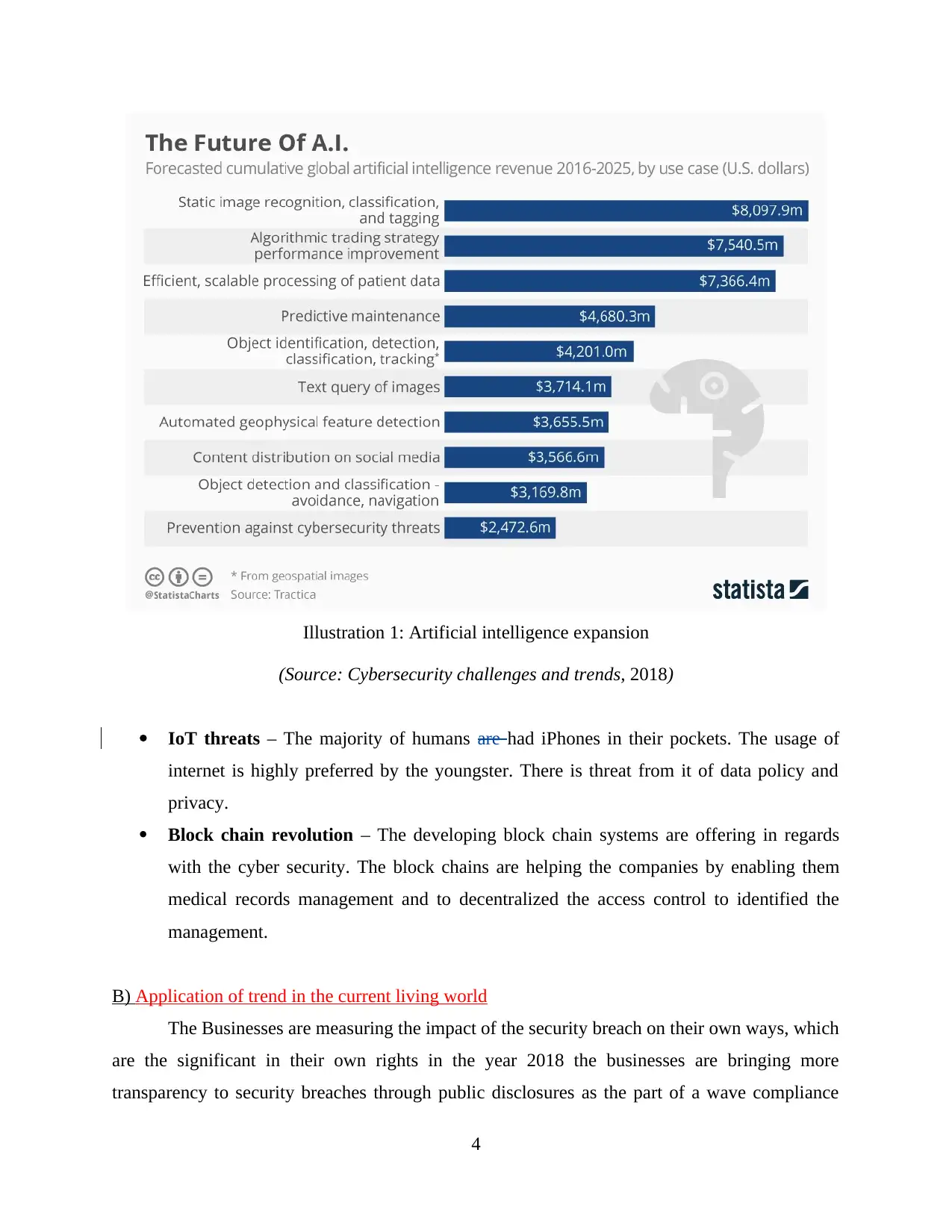
IoT threats – The majority of humans are had iPhones in their pockets. The usage of
internet is highly preferred by the youngster. There is threat from it of data policy and
privacy.
Block chain revolution – The developing block chain systems are offering in regards
with the cyber security. The block chains are helping the companies by enabling them
medical records management and to decentralized the access control to identified the
management.
B) Application of trend in the current living world
The Businesses are measuring the impact of the security breach on their own ways, which
are the significant in their own rights in the year 2018 the businesses are bringing more
transparency to security breaches through public disclosures as the part of a wave compliance
4
Illustration 1: Artificial intelligence expansion
(Source: Cybersecurity challenges and trends, 2018)
internet is highly preferred by the youngster. There is threat from it of data policy and
privacy.
Block chain revolution – The developing block chain systems are offering in regards
with the cyber security. The block chains are helping the companies by enabling them
medical records management and to decentralized the access control to identified the
management.
B) Application of trend in the current living world
The Businesses are measuring the impact of the security breach on their own ways, which
are the significant in their own rights in the year 2018 the businesses are bringing more
transparency to security breaches through public disclosures as the part of a wave compliance
4
Illustration 1: Artificial intelligence expansion
(Source: Cybersecurity challenges and trends, 2018)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

that has being measured and being introduced at global level. This is adding on considerable
pressure on the businesses. The public disclosure of the breaches might impacting the customer's
confidence and in an era where the businesses are trying to differentiate on the basis of customer
experiences and public embarrassment in having to attest before lawmakers (McLaughlin, and
Gogan, 2018). By the happening of cyber and electronic security the impact of a breach will
further extend to physical damage to the property and infrastructure and the assets. The
Companies are now obtaining the sources to reduce the large scale damages from the
cyberattacks by protecting the information access, privacy and communications and intellectual
property. The increasing internet traffic lead to higher proportion of the legal issues.
The organisations are now at the path of digital reforms and are taking several initiatives
around for using big database. The vast majority of businesses does not have the centralised
strategy around their data privacy (He and Johnson, 2017). The data collection and analysis in
project specific and can be over seen at various departments level. To bring better protect digital
assets and abjuratory for the organisations in order to assign the ownership and responsibility of
data. The marketing is leading the charge for the big data and can be a strong partner with
Information technology. The security breaches are adversely impacting the bottom line and
businesses are turned to assess their digital capacity in order to determine their worth.
The businesses are looking to provide the higher level of security coextensive with the
true value of these digital assets. The Data classification in companies helps to identify the most
captious digital assets. The businesses are conducted such an assessment and are founding this
process very challenging. The businesses are impacting from the public disclosure and it is
impacting the customer's confidence in an era where the businesses are trying to make
differences between the customers experience and the public embarrassment that is being
testified by lawmakers (Haldorai and Ramu, 2018). The happening of the cyber crime and
electronic security are impacted by a breach and will extend to the physical damage of the
property and infrastructure. The companies are relying on the innovation in order to overcome
the security challenges by doing research and development. There is evidence of rising costs in
the companies due to the cyber breaches in the ACSC threat report 2017.
5
pressure on the businesses. The public disclosure of the breaches might impacting the customer's
confidence and in an era where the businesses are trying to differentiate on the basis of customer
experiences and public embarrassment in having to attest before lawmakers (McLaughlin, and
Gogan, 2018). By the happening of cyber and electronic security the impact of a breach will
further extend to physical damage to the property and infrastructure and the assets. The
Companies are now obtaining the sources to reduce the large scale damages from the
cyberattacks by protecting the information access, privacy and communications and intellectual
property. The increasing internet traffic lead to higher proportion of the legal issues.
The organisations are now at the path of digital reforms and are taking several initiatives
around for using big database. The vast majority of businesses does not have the centralised
strategy around their data privacy (He and Johnson, 2017). The data collection and analysis in
project specific and can be over seen at various departments level. To bring better protect digital
assets and abjuratory for the organisations in order to assign the ownership and responsibility of
data. The marketing is leading the charge for the big data and can be a strong partner with
Information technology. The security breaches are adversely impacting the bottom line and
businesses are turned to assess their digital capacity in order to determine their worth.
The businesses are looking to provide the higher level of security coextensive with the
true value of these digital assets. The Data classification in companies helps to identify the most
captious digital assets. The businesses are conducted such an assessment and are founding this
process very challenging. The businesses are impacting from the public disclosure and it is
impacting the customer's confidence in an era where the businesses are trying to make
differences between the customers experience and the public embarrassment that is being
testified by lawmakers (Haldorai and Ramu, 2018). The happening of the cyber crime and
electronic security are impacted by a breach and will extend to the physical damage of the
property and infrastructure. The companies are relying on the innovation in order to overcome
the security challenges by doing research and development. There is evidence of rising costs in
the companies due to the cyber breaches in the ACSC threat report 2017.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
C) Ascertainment of regulatory impacts in accordance with current trends
According to the Data Privacy Act, 1988, it regulated with various framework to the
companies to secure their data from hacking and infringement of their information from that
available data. As in context to Telstra Security report, they improving their security system and
cyber crime for the new trends. As due to changes in technology and electronic usage in new
trend and to develop such changes in company much crime areis committed and also the security
system are also upgraded which secure the security system. As compare to the security report of
2018 it is more comprehensive than which was indicating before (Keogh, Gordon and
Marinovic, 2018). Due to more fraud committed in the data and information the security is also
less which results in easily hacking of company website. As company usually deal with the email
facility and they can connect through their customers and investors to share any important
information. To protect the email facility in the company, they have to upgrade their
technologies and also provide more security passwords which is not easily disclosed to any
employees.
6
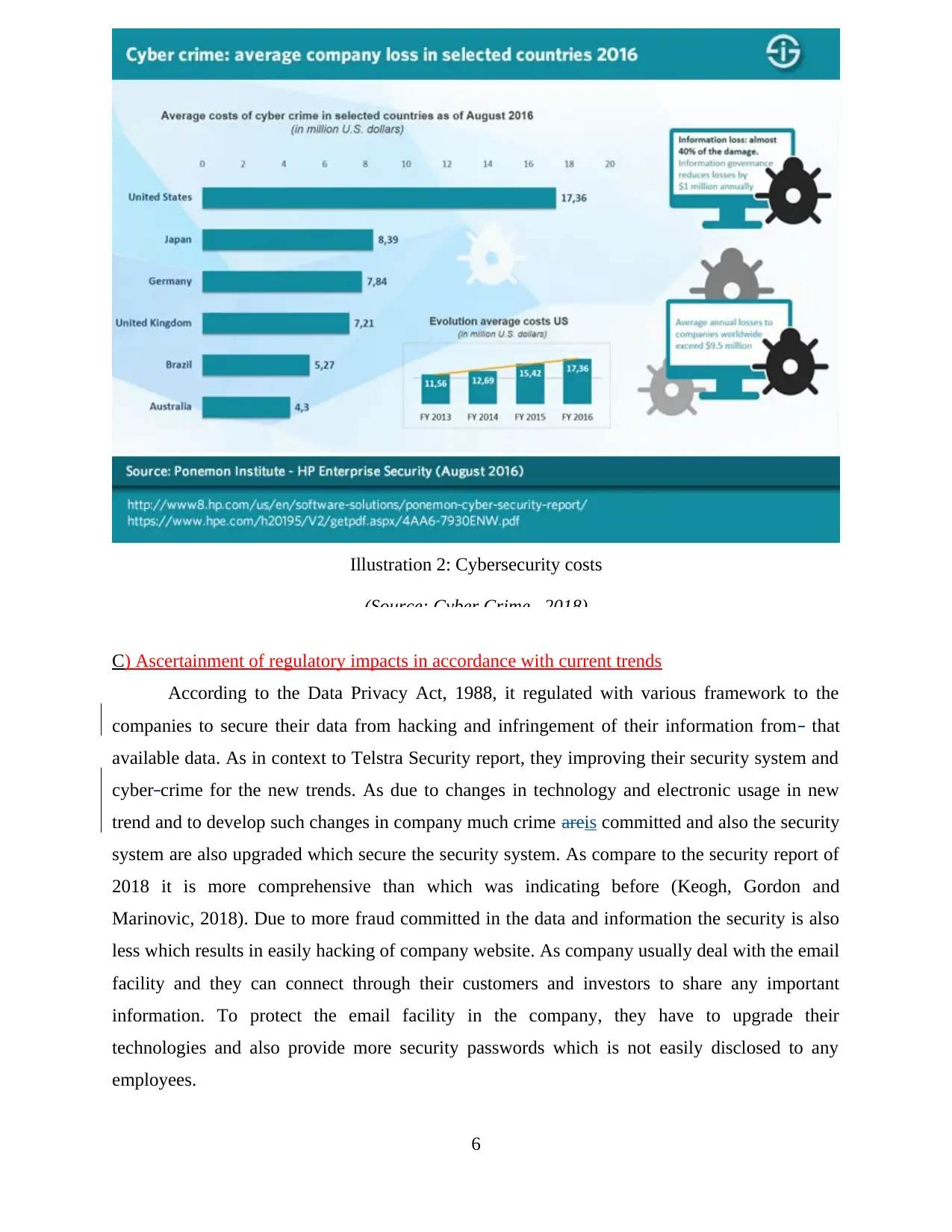
Illustration 2: Cybersecurity costs
(Source: Cyber Crime , 2018)
According to the Data Privacy Act, 1988, it regulated with various framework to the
companies to secure their data from hacking and infringement of their information from that
available data. As in context to Telstra Security report, they improving their security system and
cyber crime for the new trends. As due to changes in technology and electronic usage in new
trend and to develop such changes in company much crime areis committed and also the security
system are also upgraded which secure the security system. As compare to the security report of
2018 it is more comprehensive than which was indicating before (Keogh, Gordon and
Marinovic, 2018). Due to more fraud committed in the data and information the security is also
less which results in easily hacking of company website. As company usually deal with the email
facility and they can connect through their customers and investors to share any important
information. To protect the email facility in the company, they have to upgrade their
technologies and also provide more security passwords which is not easily disclosed to any
employees.
6
Illustration 2: Cybersecurity costs
(Source: Cyber Crime , 2018)

As the report says that few data infringement cases occurs due to more trust in employees
and giving them power to handle the company information. This results in fraud committed
which is not easily traced. As company can easily trust their loyalty and dignity through their
hard work. This attract them to give more powers regarding to handle company issues and
matters which can be solved through technologies and providing security to the data which is the
major priority to attain certain business (Mann and et.al., 2018). Due to viewing this condition in
the emerging counties and company, government imposed certain strict norms regarding the data
protection under the Data privacy act, 1988. To establish a company or the country, data plays a
major role for the fulfillmentfulfilment of the needs of the Country people and the company tin
respect to their employee and the customers which are attached to them. The security is needed
in various electronic gadgets such as in mobiles, computers, business projects and the transaction
which can be deal through email.
In Today generation, electronic and cyber security are the major aspects to run a
successful business or country. As if any important discussion which is related to welfare of the
country than in that case the matter arises between the parties. There are two types of parties one
which agree with all the changes which benefits to the country and one which is against such
changes. In that case more case of hacking arises which affect the security system of the country.
The mostly challenges which is faced under security threat is related to business and It
department (Weber and Studer, 2016). As due to their coding ideas and experts, they have to
develop new technologies to protect their electronic system and security of the employees and
the people living iIn the society. As it is right of every person to live freely and their information
are secured or even they have the right to secure their data but that are under the government
norms.
To understand the impact of security it is effective to know the time management
techniques and the incidents which are happened at that time. The data are securely when this
both things happen with the same time which these incidents happens which affect the society
and company. As due to more cases are register it is tough to identify the attachers who attaches
on the data of the county and company (Anwar, Gill and Beydoun, 2018). Sometimes the
infringement of data areis committed with the internal management team only which does not
want the company to grow or expand their business activities. This results in managing the data
or fraudulently enter their transaction. As CCTV cameras are implemented in the companies so
7
and giving them power to handle the company information. This results in fraud committed
which is not easily traced. As company can easily trust their loyalty and dignity through their
hard work. This attract them to give more powers regarding to handle company issues and
matters which can be solved through technologies and providing security to the data which is the
major priority to attain certain business (Mann and et.al., 2018). Due to viewing this condition in
the emerging counties and company, government imposed certain strict norms regarding the data
protection under the Data privacy act, 1988. To establish a company or the country, data plays a
major role for the fulfillmentfulfilment of the needs of the Country people and the company tin
respect to their employee and the customers which are attached to them. The security is needed
in various electronic gadgets such as in mobiles, computers, business projects and the transaction
which can be deal through email.
In Today generation, electronic and cyber security are the major aspects to run a
successful business or country. As if any important discussion which is related to welfare of the
country than in that case the matter arises between the parties. There are two types of parties one
which agree with all the changes which benefits to the country and one which is against such
changes. In that case more case of hacking arises which affect the security system of the country.
The mostly challenges which is faced under security threat is related to business and It
department (Weber and Studer, 2016). As due to their coding ideas and experts, they have to
develop new technologies to protect their electronic system and security of the employees and
the people living iIn the society. As it is right of every person to live freely and their information
are secured or even they have the right to secure their data but that are under the government
norms.
To understand the impact of security it is effective to know the time management
techniques and the incidents which are happened at that time. The data are securely when this
both things happen with the same time which these incidents happens which affect the society
and company. As due to more cases are register it is tough to identify the attachers who attaches
on the data of the county and company (Anwar, Gill and Beydoun, 2018). Sometimes the
infringement of data areis committed with the internal management team only which does not
want the company to grow or expand their business activities. This results in managing the data
or fraudulently enter their transaction. As CCTV cameras are implemented in the companies so
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

that they can track the employees records and their activities in the organisation.
But many employees commit such fraud regarding their activities committed at the time
of working or hack the system through which their working is not clear. To protect such system,
government imposed certain rules which every companies have to follow. Electronic system can
be considered as the evidence which helps companies to solve the cases if any crime committed
during the work premises. As many employees just to earn more profits make false comment
against the company structure and file a case relating to crime committed during work hours
(Foody and et.al., 2017). This system helps companies to trace the record of their employees and
also crack the working criteria of employees they are committed at the time they file suit. This
helps them to easily know the employeesemployee’s interests towards the work and if they
commit false case they are punishable under the following laws imposed buyby the judges of the
courts.
As per new trend many new laws are imposed according to the privacy and security of
the data. They are actively adhering to the American Privacy Act which helps the companies and
country to secure their data and information which helps them to face the challenges which can
be occurs at any time. This results in controlling the breach of data and informatininformation
are secured with the company profile. Usually companies establish a whole IT teams to just
protect the data and track the person in case of infringement of data. By looking such strict
policies of companies and spending lot of saving on securing the information. Government also
made strict punishment in case of any breach of company information by any way (Jia and
Huaisheng, 2017). As mostly the cases related to transferring of data in inbound and outbound of
messages which results in more breaching of data. But to emerging market and companies had
mostly expanded their business into large scale, they have to also upgrade their technologies and
system. Government imposed various rules and laws against the data protection acts and it is the
duties of the company to follow such rules and also they are liable to the employees who are
engages with their business activities.
8
But many employees commit such fraud regarding their activities committed at the time
of working or hack the system through which their working is not clear. To protect such system,
government imposed certain rules which every companies have to follow. Electronic system can
be considered as the evidence which helps companies to solve the cases if any crime committed
during the work premises. As many employees just to earn more profits make false comment
against the company structure and file a case relating to crime committed during work hours
(Foody and et.al., 2017). This system helps companies to trace the record of their employees and
also crack the working criteria of employees they are committed at the time they file suit. This
helps them to easily know the employeesemployee’s interests towards the work and if they
commit false case they are punishable under the following laws imposed buyby the judges of the
courts.
As per new trend many new laws are imposed according to the privacy and security of
the data. They are actively adhering to the American Privacy Act which helps the companies and
country to secure their data and information which helps them to face the challenges which can
be occurs at any time. This results in controlling the breach of data and informatininformation
are secured with the company profile. Usually companies establish a whole IT teams to just
protect the data and track the person in case of infringement of data. By looking such strict
policies of companies and spending lot of saving on securing the information. Government also
made strict punishment in case of any breach of company information by any way (Jia and
Huaisheng, 2017). As mostly the cases related to transferring of data in inbound and outbound of
messages which results in more breaching of data. But to emerging market and companies had
mostly expanded their business into large scale, they have to also upgrade their technologies and
system. Government imposed various rules and laws against the data protection acts and it is the
duties of the company to follow such rules and also they are liable to the employees who are
engages with their business activities.
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
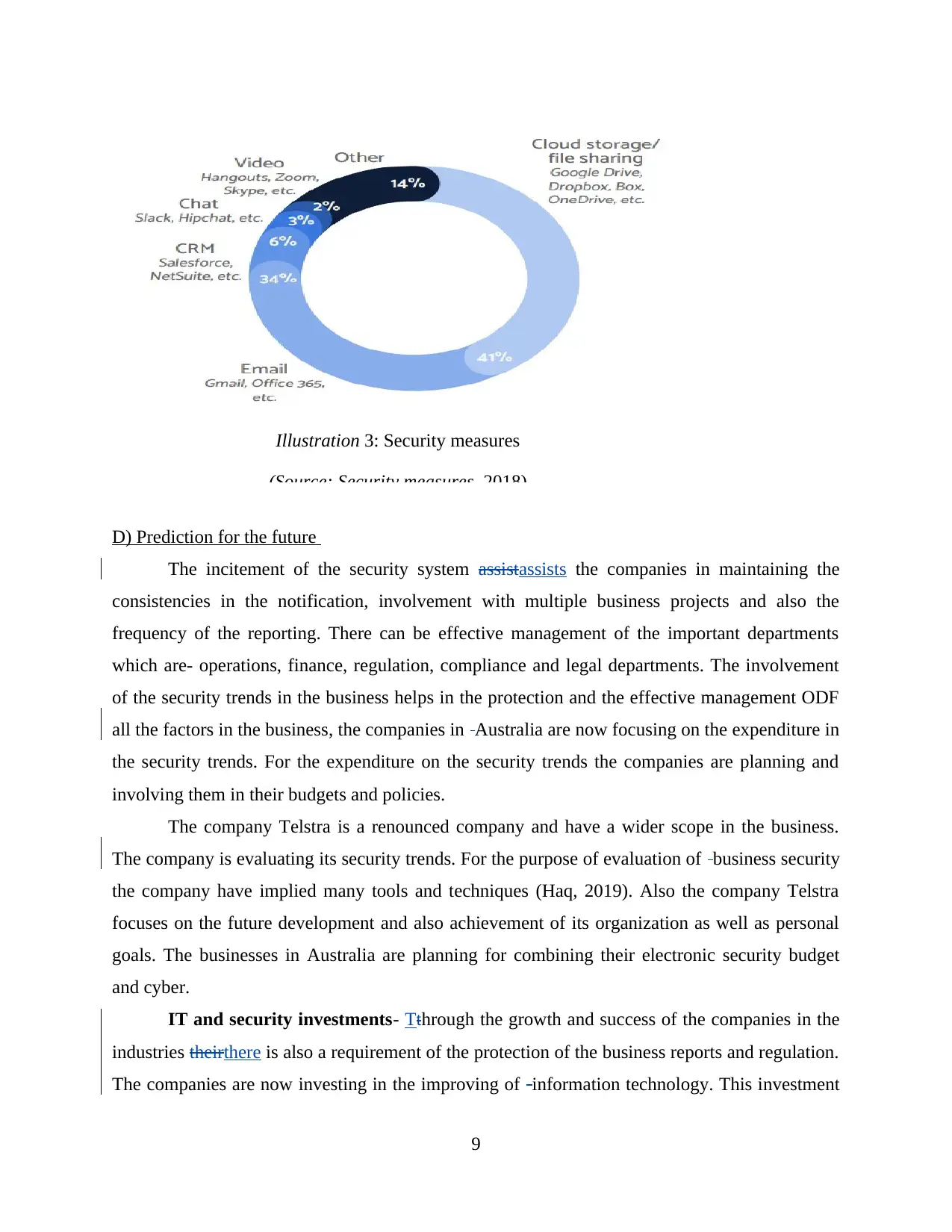
Illustration 3: Security measures
(Source: Security measures, 2018)
D) Prediction for the future
The incitement of the security system assistassists the companies in maintaining the
consistencies in the notification, involvement with multiple business projects and also the
frequency of the reporting. There can be effective management of the important departments
which are- operations, finance, regulation, compliance and legal departments. The involvement
of the security trends in the business helps in the protection and the effective management ODF
all the factors in the business, the companies in Australia are now focusing on the expenditure in
the security trends. For the expenditure on the security trends the companies are planning and
involving them in their budgets and policies.
The company Telstra is a renounced company and have a wider scope in the business.
The company is evaluating its security trends. For the purpose of evaluation of business security
the company have implied many tools and techniques (Haq, 2019). Also the company Telstra
focuses on the future development and also achievement of its organization as well as personal
goals. The businesses in Australia are planning for combining their electronic security budget
and cyber.
IT and security investments- Tthrough the growth and success of the companies in the
industries theirthere is also a requirement of the protection of the business reports and regulation.
The companies are now investing in the improving of information technology. This investment
9
(Source: Security measures, 2018)
D) Prediction for the future
The incitement of the security system assistassists the companies in maintaining the
consistencies in the notification, involvement with multiple business projects and also the
frequency of the reporting. There can be effective management of the important departments
which are- operations, finance, regulation, compliance and legal departments. The involvement
of the security trends in the business helps in the protection and the effective management ODF
all the factors in the business, the companies in Australia are now focusing on the expenditure in
the security trends. For the expenditure on the security trends the companies are planning and
involving them in their budgets and policies.
The company Telstra is a renounced company and have a wider scope in the business.
The company is evaluating its security trends. For the purpose of evaluation of business security
the company have implied many tools and techniques (Haq, 2019). Also the company Telstra
focuses on the future development and also achievement of its organization as well as personal
goals. The businesses in Australia are planning for combining their electronic security budget
and cyber.
IT and security investments- Tthrough the growth and success of the companies in the
industries theirthere is also a requirement of the protection of the business reports and regulation.
The companies are now investing in the improving of information technology. This investment
9

by the companies in many countries is done to achieve more advanced technologies to compete
the developing organizations. Also there have been a vast investment in the security of their
accounts and reports through from the outsiders. In the country like Australia the companies are
investing more in the overall security budget which is cyber and security budget in the company.
Also the companies in Australia states that theirthere will be increase in the relative security
budget by 58% (Narula and Jindal,2015).
C level involvements- it has been reported that theirthere will be increase in the C-level
security of the business which involves a tight security on the operations of the business and
secure the business from any risk involved by the companies.
Spending priorities- with the involvement of the security trends in the functioning ODF
the companies. The companies are more aware towards theretheir responsibilities and duties. The
result of this is companies in the countries Australia, Asia, Pacific and Europe are focusing on
the fulfilling of compliance in the companies (Mussington and et.al., 2018). Therefore, there is a
widespread scope by the companies spending more according to the priorities in the
organizations.
Technologies being trialed or considered- the companies are focusing on the
advancement of the companies. The companies are more inclined towards the development and
advancement of their old used methods and policies. The companies only trialedtrailed but also
considered the technological advancement seriously. With the increment in the technological
advancement in the field of security cyber the companies can achieve its organization goals and
objectives. As per the future perspective the companies in the countries like Australia, Asia and
Europe there is wide scope of future advancement in the companies.
Cyber in hands of many stakeholders- Aas the stakeholders are indirectly the owners
of the company there can be tight control on the companies' action by the stakeholders,. In the
future the most companies are indirectly under control of stakeholders. In the near future
countries like Australia, Asia and Europe will include the more involvement of the stakeholders
in the companies' action (Mikolic-Torreira And et.al., 2017). This involvement of stakeholders in
the company will increase the security trends in the cyber and its uses. The companies will
provide a transparent and clear image of the security techniques used by the companies in in
countries like Australia. There will be greater impact if the involvement of stakeholders on the
growth of companies.
10
the developing organizations. Also there have been a vast investment in the security of their
accounts and reports through from the outsiders. In the country like Australia the companies are
investing more in the overall security budget which is cyber and security budget in the company.
Also the companies in Australia states that theirthere will be increase in the relative security
budget by 58% (Narula and Jindal,2015).
C level involvements- it has been reported that theirthere will be increase in the C-level
security of the business which involves a tight security on the operations of the business and
secure the business from any risk involved by the companies.
Spending priorities- with the involvement of the security trends in the functioning ODF
the companies. The companies are more aware towards theretheir responsibilities and duties. The
result of this is companies in the countries Australia, Asia, Pacific and Europe are focusing on
the fulfilling of compliance in the companies (Mussington and et.al., 2018). Therefore, there is a
widespread scope by the companies spending more according to the priorities in the
organizations.
Technologies being trialed or considered- the companies are focusing on the
advancement of the companies. The companies are more inclined towards the development and
advancement of their old used methods and policies. The companies only trialedtrailed but also
considered the technological advancement seriously. With the increment in the technological
advancement in the field of security cyber the companies can achieve its organization goals and
objectives. As per the future perspective the companies in the countries like Australia, Asia and
Europe there is wide scope of future advancement in the companies.
Cyber in hands of many stakeholders- Aas the stakeholders are indirectly the owners
of the company there can be tight control on the companies' action by the stakeholders,. In the
future the most companies are indirectly under control of stakeholders. In the near future
countries like Australia, Asia and Europe will include the more involvement of the stakeholders
in the companies' action (Mikolic-Torreira And et.al., 2017). This involvement of stakeholders in
the company will increase the security trends in the cyber and its uses. The companies will
provide a transparent and clear image of the security techniques used by the companies in in
countries like Australia. There will be greater impact if the involvement of stakeholders on the
growth of companies.
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




