Cyber Operations: Endpoint Vulnerabilities and Attacks Research Report
VerifiedAdded on 2022/09/01
|24
|4105
|19
Report
AI Summary
This report, prepared by a student for Desklib, examines cyber operations with a specific focus on endpoint vulnerabilities and attacks. The research delves into the implementation of security measures by organizations and the challenges faced in preventing costly data breaches. The literature review explores various aspects of cybersecurity, including the assessment of risks, the impact of malware and phishing attacks, and the importance of user behavior analysis. The report highlights the significance of IT infrastructure vulnerability, user facilitation, and the probabilities associated with potential cyber threats. It also discusses the need for integrated methods to assess vulnerabilities, particularly concerning malware attacks and the role of user behavior in the exploitation of vulnerabilities. The report further examines the impact of localized attacks on infrastructure systems and the use of honeypots for tracking attackers and protecting real-time assets. Recommendations and conclusions are provided based on the findings, contributing to a better understanding of cybersecurity operations and mitigation strategies.

Running head: CYBER OPERATIONS
CYBER OPERATIONS
Name of the student:
Name of the university:
Author Note:
CYBER OPERATIONS
Name of the student:
Name of the university:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBER OPERATIONS
Table of Contents
Part-A.........................................................................................................................................2
Introduction............................................................................................................................2
Literature Review...................................................................................................................2
Conclusion..............................................................................................................................8
Recommendations..................................................................................................................8
Part-B.........................................................................................................................................9
Steps for Analysis..................................................................................................................9
Analysis of Wireshark file...................................................................................................10
References................................................................................................................................19
Table of Contents
Part-A.........................................................................................................................................2
Introduction............................................................................................................................2
Literature Review...................................................................................................................2
Conclusion..............................................................................................................................8
Recommendations..................................................................................................................8
Part-B.........................................................................................................................................9
Steps for Analysis..................................................................................................................9
Analysis of Wireshark file...................................................................................................10
References................................................................................................................................19

2CYBER OPERATIONS
Part-A
Introduction
Transformation with the help of digitalized methods have been provisioned by the
companies with a number of operational as well as financial benefits along with the
management of a large fleet of computational devices, mobile phones as well as smart
appliances is in dire need of a cybersecurity posture (Mladenov, Mainka and Schwenk 2015).
Every individual digitalized device in connection to a private network puts forward
representations having the inclusion of an access point for the exploitation of potential
hackers. As a reason, most of the organizations within the field of business has deployed rigid
security measures for such data along with the credential guidelines for the users in
particular. Hence, this report highlights the various endpoint security that has been
implemented by the various organizations to provision all the individual users with the
assurance that the data they use to communicate with other individuals are secure with
necessary protocols (Goyal et al. 2018). Despite the particular implementation of these
security measures within the organizations, many of the enterprise have been facing struggles
regarding the same to ward off such costly data breaches that have been leading to a better
safeguarding of the business devices that are being utilized properly by the employees of the
organization.
Literature Review
As stated by Leitold, Arrott and Hadarics (2016), measure of security that has been
integrated as a reason of vulnerability related to cyber security that has been present forward
as a reason of disparate but at the same time interrelated sources belonging to endpoint
vulnerability. This has a primary inclusion of attacker ingenuity, weakness in infrastructure as
well as adverse behaviour belonging to the users of such systems. In general, analytical
Part-A
Introduction
Transformation with the help of digitalized methods have been provisioned by the
companies with a number of operational as well as financial benefits along with the
management of a large fleet of computational devices, mobile phones as well as smart
appliances is in dire need of a cybersecurity posture (Mladenov, Mainka and Schwenk 2015).
Every individual digitalized device in connection to a private network puts forward
representations having the inclusion of an access point for the exploitation of potential
hackers. As a reason, most of the organizations within the field of business has deployed rigid
security measures for such data along with the credential guidelines for the users in
particular. Hence, this report highlights the various endpoint security that has been
implemented by the various organizations to provision all the individual users with the
assurance that the data they use to communicate with other individuals are secure with
necessary protocols (Goyal et al. 2018). Despite the particular implementation of these
security measures within the organizations, many of the enterprise have been facing struggles
regarding the same to ward off such costly data breaches that have been leading to a better
safeguarding of the business devices that are being utilized properly by the employees of the
organization.
Literature Review
As stated by Leitold, Arrott and Hadarics (2016), measure of security that has been
integrated as a reason of vulnerability related to cyber security that has been present forward
as a reason of disparate but at the same time interrelated sources belonging to endpoint
vulnerability. This has a primary inclusion of attacker ingenuity, weakness in infrastructure as
well as adverse behaviour belonging to the users of such systems. In general, analytical
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CYBER OPERATIONS
formulas meant for the assessment of risk having a complete dependency upon the three
related variables have been applied to that of the endpoint within the field of cybersecurity
and problems related to its protection (Finlayson et al. 2018). Narrowing down, the primary
focus is upon the vulnerability in a broader spectrum such as the like of malware as well as
phishing attacks. For a specific cyber threat or an aggregated class of such threats, there is a
specific requirement of an IT infrastructure that belongs to the vulnerability and also has the
inclusion of user facilitation that is completely know. Estimations have been placed forward
that are,
Probability of a potential attacker to make use of a particular threat or a class of
threats against a business organization.
Probability that the existing infrastructure of the respective organization will
provision the attack with the allowance to cause an effect to that of the same.
Probability that the employees working within an organization will put forward
sufficient facilitation for the attack to be carried out and effect the organization as a
whole (Liu et al. 2018).
The above-mentioned three probabilities can be particularly combined in order to
obtain a general probability of the malicious success and make way for the potential hackers
existing online. Probabilities ion relation to malicious success can be separately measured
along with combined, prioritized as well as compared. In addition to this, identification of
high priority of the mentioned vulnerabilities can be specifically decomposed with the help of
constituent sources belonging to vulnerability provisioning with the allowance of remedial
actions that need to be directed as a greater measure of improvement that can be made
(Polivka, Oujezsky and Skorpil 2015). To have success with a malware attack by the
potential hackers present online, successful execution of the malicious code is needed for
posing an attack towards the enterprises within the world of business. Metrics of
formulas meant for the assessment of risk having a complete dependency upon the three
related variables have been applied to that of the endpoint within the field of cybersecurity
and problems related to its protection (Finlayson et al. 2018). Narrowing down, the primary
focus is upon the vulnerability in a broader spectrum such as the like of malware as well as
phishing attacks. For a specific cyber threat or an aggregated class of such threats, there is a
specific requirement of an IT infrastructure that belongs to the vulnerability and also has the
inclusion of user facilitation that is completely know. Estimations have been placed forward
that are,
Probability of a potential attacker to make use of a particular threat or a class of
threats against a business organization.
Probability that the existing infrastructure of the respective organization will
provision the attack with the allowance to cause an effect to that of the same.
Probability that the employees working within an organization will put forward
sufficient facilitation for the attack to be carried out and effect the organization as a
whole (Liu et al. 2018).
The above-mentioned three probabilities can be particularly combined in order to
obtain a general probability of the malicious success and make way for the potential hackers
existing online. Probabilities ion relation to malicious success can be separately measured
along with combined, prioritized as well as compared. In addition to this, identification of
high priority of the mentioned vulnerabilities can be specifically decomposed with the help of
constituent sources belonging to vulnerability provisioning with the allowance of remedial
actions that need to be directed as a greater measure of improvement that can be made
(Polivka, Oujezsky and Skorpil 2015). To have success with a malware attack by the
potential hackers present online, successful execution of the malicious code is needed for
posing an attack towards the enterprises within the world of business. Metrics of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CYBER OPERATIONS
cybersecurity have tended to primarily focus upon the protection of an existing IT
infrastructure within an organization. Behaviour of users utilizing measures of cybersecurity
are very less developed having the inclusion of network traffic having to monitor over the
richer opportunities required for the process of development (Mansfield-Devine 2017). Along
with this, passive monitoring using the methods of interactive metrics can also be deployed
with the help of proper and effective measures of security that is specifically needed within
organizations.
According to Leitold et al. (2016), an integrated method for the assessment of
vulnerability related to organizations for the purpose of malware attacks that is in dire need of
urgent attention for the measurement as well as correlation of three primary aspects. These
are namely,
Vulnerability of IT infrastructure that is protected as well as processes related to such
attacks.
Global prevalence as well as local incident in relation to the malware threats on a
specific instance puts forward relevance to the targeted organization.
Vulnerability in regards to the authorized users for the malicious manipulation such as
the like of social engineering.
However, advanced tools are existing for all of the three aspects that have been
mentioned above; having the primary inclusion of affordability as well as practicality in
relation to the high-quality vulnerability assessment for smaller sized organizations is at
minimum level for the third aspect above (Levomaki, Niemi and Jalio 2017). This refers to an
effective analysis that has been carried out in relation to the user behaviour. This particular
problem is severe for the protection of unstructured data belonging to the users as well as the
ad hoc user practices that are unregulated. This particular problem that has been highlighted
cybersecurity have tended to primarily focus upon the protection of an existing IT
infrastructure within an organization. Behaviour of users utilizing measures of cybersecurity
are very less developed having the inclusion of network traffic having to monitor over the
richer opportunities required for the process of development (Mansfield-Devine 2017). Along
with this, passive monitoring using the methods of interactive metrics can also be deployed
with the help of proper and effective measures of security that is specifically needed within
organizations.
According to Leitold et al. (2016), an integrated method for the assessment of
vulnerability related to organizations for the purpose of malware attacks that is in dire need of
urgent attention for the measurement as well as correlation of three primary aspects. These
are namely,
Vulnerability of IT infrastructure that is protected as well as processes related to such
attacks.
Global prevalence as well as local incident in relation to the malware threats on a
specific instance puts forward relevance to the targeted organization.
Vulnerability in regards to the authorized users for the malicious manipulation such as
the like of social engineering.
However, advanced tools are existing for all of the three aspects that have been
mentioned above; having the primary inclusion of affordability as well as practicality in
relation to the high-quality vulnerability assessment for smaller sized organizations is at
minimum level for the third aspect above (Levomaki, Niemi and Jalio 2017). This refers to an
effective analysis that has been carried out in relation to the user behaviour. This particular
problem is severe for the protection of unstructured data belonging to the users as well as the
ad hoc user practices that are unregulated. This particular problem that has been highlighted

5CYBER OPERATIONS
can be potentially mitigated with the proper usage of actionable measures such as the like of
risks associated with user behaviour having a more focus upon the automated behaviours of
user belonging to an organization as an employee. This paper puts forward all the related
information in regards to the framework meant for the development of automated
measurements belonging to the behaviour of the user and the relative interactions that is
particularly required for the threats (Bhuiyan et al. 2018). Measurements of user behaviour
are completely based upon the passive monitoring as well as the active interaction that is
carried out the users working within the IT organizations. As a reason, this paper puts
forward and highlights a practical method in accordance to the results that have been obtained
from automated procedure of pen testing, intelligence feeds of threats as well as having a
prime focus upon the vulnerabilities associated with the user behaviour. An example that has
been stated by the author is the existence of a correlation spectrum in relation to the malware
attacks in the presence or the particular absence of an anti-virus protection along with the
user maintaining a diligence within the procedure of securing protection with the help of
antivirus programs (Vanhoef and Piessens 2017). For succeeding with an attack posed
towards a business organization, specifically requires a successful execution of the potential
malicious code with the help of protected IT along with appropriate user facilitation for the
subverting of the network security. Metrics of cybersecurity have specifically tended to have
the prime focus upon the protected IT as well as the malicious activity. Metrics of cyber
security in terms of user behaviour are very less developed. However, the monitoring of
network traffic provisions with richer opportunities for the required amount of development
(Brewer 2016). In addition to this, passive monitoring of along with the interactive metrics
can also lead to deployment.
As placed forward by Ouyang (2016), infrastructure systems present within the
organizations within the field of business have been usually distributed within the wide area
can be potentially mitigated with the proper usage of actionable measures such as the like of
risks associated with user behaviour having a more focus upon the automated behaviours of
user belonging to an organization as an employee. This paper puts forward all the related
information in regards to the framework meant for the development of automated
measurements belonging to the behaviour of the user and the relative interactions that is
particularly required for the threats (Bhuiyan et al. 2018). Measurements of user behaviour
are completely based upon the passive monitoring as well as the active interaction that is
carried out the users working within the IT organizations. As a reason, this paper puts
forward and highlights a practical method in accordance to the results that have been obtained
from automated procedure of pen testing, intelligence feeds of threats as well as having a
prime focus upon the vulnerabilities associated with the user behaviour. An example that has
been stated by the author is the existence of a correlation spectrum in relation to the malware
attacks in the presence or the particular absence of an anti-virus protection along with the
user maintaining a diligence within the procedure of securing protection with the help of
antivirus programs (Vanhoef and Piessens 2017). For succeeding with an attack posed
towards a business organization, specifically requires a successful execution of the potential
malicious code with the help of protected IT along with appropriate user facilitation for the
subverting of the network security. Metrics of cybersecurity have specifically tended to have
the prime focus upon the protected IT as well as the malicious activity. Metrics of cyber
security in terms of user behaviour are very less developed. However, the monitoring of
network traffic provisions with richer opportunities for the required amount of development
(Brewer 2016). In addition to this, passive monitoring of along with the interactive metrics
can also lead to deployment.
As placed forward by Ouyang (2016), infrastructure systems present within the
organizations within the field of business have been usually distributed within the wide area
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CYBER OPERATIONS
as well as the subject to many of the hazards. For each of the individual types of hazards
having a direct impact upon the components belonging to the infrastructure as well as
analysing the induced level of system vulnerability that is considered to be important for the
identification of the variously existing strategies for mitigation (Shah and Farik 2017). This
paper has a prime focus upon the studies of localized attacks that have been modelled with
the help of a collective set of infrastructure components present within or might as well be
crossing the circle shaped localized area that is subjected to damage, while on the other hand
the components do not undergo direct failure. Specifically for these attacks, taking into
consideration the interdependent power along with the gas systems in various of the countries
worldwide. This paper particularly puts forward the procedure of localized attacks that takes
place in the endpoint transfer of messages located at the critical situations having the
complete dependency upon the infrastructure systems making the possibility of vulnerability
attacks at the business organizations due to the fact of such systems being irritably vulnerable
to attacks such as malware and phishing (Kumar and Xu 2017). Researches have been
conducted to which results have been placed forward that show,
(a) Interdependency of infrastructure as well as radius of attack having a direct effect upon
the largely affected positions of critically existing locations.
(b) Spatial localized attacks that specifically causes less of vulnerability than randomly
occurring failures.
(c) Identification of vulnerabilities at the critical locations by considering the node failures
having no change at both the node as well as the edge failures within the area of attack.
Infrastructure systems existing within the business organizations such as the like of
electric power, telecommunication, water supply as well as the emergence systems of service
particularly form the backbone of the functioning within a community belonging to any
as well as the subject to many of the hazards. For each of the individual types of hazards
having a direct impact upon the components belonging to the infrastructure as well as
analysing the induced level of system vulnerability that is considered to be important for the
identification of the variously existing strategies for mitigation (Shah and Farik 2017). This
paper has a prime focus upon the studies of localized attacks that have been modelled with
the help of a collective set of infrastructure components present within or might as well be
crossing the circle shaped localized area that is subjected to damage, while on the other hand
the components do not undergo direct failure. Specifically for these attacks, taking into
consideration the interdependent power along with the gas systems in various of the countries
worldwide. This paper particularly puts forward the procedure of localized attacks that takes
place in the endpoint transfer of messages located at the critical situations having the
complete dependency upon the infrastructure systems making the possibility of vulnerability
attacks at the business organizations due to the fact of such systems being irritably vulnerable
to attacks such as malware and phishing (Kumar and Xu 2017). Researches have been
conducted to which results have been placed forward that show,
(a) Interdependency of infrastructure as well as radius of attack having a direct effect upon
the largely affected positions of critically existing locations.
(b) Spatial localized attacks that specifically causes less of vulnerability than randomly
occurring failures.
(c) Identification of vulnerabilities at the critical locations by considering the node failures
having no change at both the node as well as the edge failures within the area of attack.
Infrastructure systems existing within the business organizations such as the like of
electric power, telecommunication, water supply as well as the emergence systems of service
particularly form the backbone of the functioning within a community belonging to any
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBER OPERATIONS
respective nation (Knapp 2017). This is carried out for provisioning the citizens of the
respective nation with the support towards the wellbeing of the same. However, all of these
mentioned systems currently are subjected towards multiply existing hazards such as the like
of unavoidable naturally existing hazards, sharp increase in demand, component aging as well
as changes in climate. This brings an increase within the failure of probability as well as
vulnerability (Hofbauer, Beckers and Quirchmayr 2015). In addition to this, the infrastructure
systems belonging to the business organizations are not kept isolated but having a high
interconnection towards the mutually interdependent behaviour. These interdependencies can
specifically improve the operational efficiency within the organizations however, may also
bring a specific increase within the vulnerability of the systems. Minor failures within the
systems can specifically lead towards cascading failures within the mentioned systems as
well as across the other existing systems. Hence, for a better protection of the interdependent
infrastructures for each of the specific type of hazards is in requirement of modelling the
direct impact upon the components belonging to the systems of infrastructure
(Neugschwandtner, Beitler and Kurmus 2016). This is followed by the proper analysis of the
vulnerability in reference to the level of system for the identification of the required amount
of mitigation strategies that have been termed as Vulnerability within the paper taken into
consideration.
As argued by Stoecklin et al. (2018), honeypots have been necessarily employed for
the tracking of attackers and their activities along with the diversion of potential threats
against the real time assets. A critically existing challenge belonging to the honeypot and the
related research is how to integrate the better existing honeypots forming a component of the
total network related to production (Mistry, Lalwani and Potdar 2018). Conventional
honeypots have been typically deployed as a part of separate assets near those of the
components that have been provisioning with the required amount of protection. However,
respective nation (Knapp 2017). This is carried out for provisioning the citizens of the
respective nation with the support towards the wellbeing of the same. However, all of these
mentioned systems currently are subjected towards multiply existing hazards such as the like
of unavoidable naturally existing hazards, sharp increase in demand, component aging as well
as changes in climate. This brings an increase within the failure of probability as well as
vulnerability (Hofbauer, Beckers and Quirchmayr 2015). In addition to this, the infrastructure
systems belonging to the business organizations are not kept isolated but having a high
interconnection towards the mutually interdependent behaviour. These interdependencies can
specifically improve the operational efficiency within the organizations however, may also
bring a specific increase within the vulnerability of the systems. Minor failures within the
systems can specifically lead towards cascading failures within the mentioned systems as
well as across the other existing systems. Hence, for a better protection of the interdependent
infrastructures for each of the specific type of hazards is in requirement of modelling the
direct impact upon the components belonging to the systems of infrastructure
(Neugschwandtner, Beitler and Kurmus 2016). This is followed by the proper analysis of the
vulnerability in reference to the level of system for the identification of the required amount
of mitigation strategies that have been termed as Vulnerability within the paper taken into
consideration.
As argued by Stoecklin et al. (2018), honeypots have been necessarily employed for
the tracking of attackers and their activities along with the diversion of potential threats
against the real time assets. A critically existing challenge belonging to the honeypot and the
related research is how to integrate the better existing honeypots forming a component of the
total network related to production (Mistry, Lalwani and Potdar 2018). Conventional
honeypots have been typically deployed as a part of separate assets near those of the
components that have been provisioning with the required amount of protection. However,

8CYBER OPERATIONS
these mentioned components do not belong to the directly existing line of fire. Such a
mentioned setup does not have an effective protection upon the real time assets for a reason
that the attackers are not in requirement of the fully advanced network for the purpose of
scanning the identify meant for the hosts of production (Slate 2018). This paper also puts
forward the presentation of a novel framework in regards to the transparently existing project
that is vulnerable in the sense of honey services for the real production systems without
entertaining the interference into the production system installed within the organizations in
the field of business. Traffic that is specifically intended for the workloads in reference to the
production as well as decoy of servers. Decoy servers carry out vulnerable services that are
particularly monitored for the reasons mentioned above (Hollis and Zahn 2017). From the
potential attackers and their carried perspective, all of the mentioned vulnerabilities run upon
the production systems, having a traffic instead of the replayed configuration in related to the
honeypot.
Conclusion
Majority of the business organizations have been upgrading themselves with the help
of digitalized systems and making them a part of the infrastructure as a primary component of
the organizations. This has been visibly identified that such digital transformations within the
business organizations have led to specific cause of attacks by potential hackers as a reason
of which various effects have been visible upon the respective organizations. Digital
transformations and the related upgradation of online services have made the organizations
vulnerable to potential hackers present online and have led to cause of potential attacks such
as malware and phishing leading to unavoidable consequences in the end.
these mentioned components do not belong to the directly existing line of fire. Such a
mentioned setup does not have an effective protection upon the real time assets for a reason
that the attackers are not in requirement of the fully advanced network for the purpose of
scanning the identify meant for the hosts of production (Slate 2018). This paper also puts
forward the presentation of a novel framework in regards to the transparently existing project
that is vulnerable in the sense of honey services for the real production systems without
entertaining the interference into the production system installed within the organizations in
the field of business. Traffic that is specifically intended for the workloads in reference to the
production as well as decoy of servers. Decoy servers carry out vulnerable services that are
particularly monitored for the reasons mentioned above (Hollis and Zahn 2017). From the
potential attackers and their carried perspective, all of the mentioned vulnerabilities run upon
the production systems, having a traffic instead of the replayed configuration in related to the
honeypot.
Conclusion
Majority of the business organizations have been upgrading themselves with the help
of digitalized systems and making them a part of the infrastructure as a primary component of
the organizations. This has been visibly identified that such digital transformations within the
business organizations have led to specific cause of attacks by potential hackers as a reason
of which various effects have been visible upon the respective organizations. Digital
transformations and the related upgradation of online services have made the organizations
vulnerable to potential hackers present online and have led to cause of potential attacks such
as malware and phishing leading to unavoidable consequences in the end.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CYBER OPERATIONS
Recommendations
Digitalized transformations and upgradation of the existing infrastructure of IT within
the business organizations have led to various consequences and situations such as loss of
potential and sensitive data belonging to the organization along with the employees in
particular. Hence, it is recommended that the organizations should consider the
vulnerabilities existing within the endpoint conversations having a direct impact upon the
same to implement security measures for protection and securing of data. As a reason, this
will lead to proper mitigation of such potential attacks by hackers and leading to a better
process of communication.
Part-B
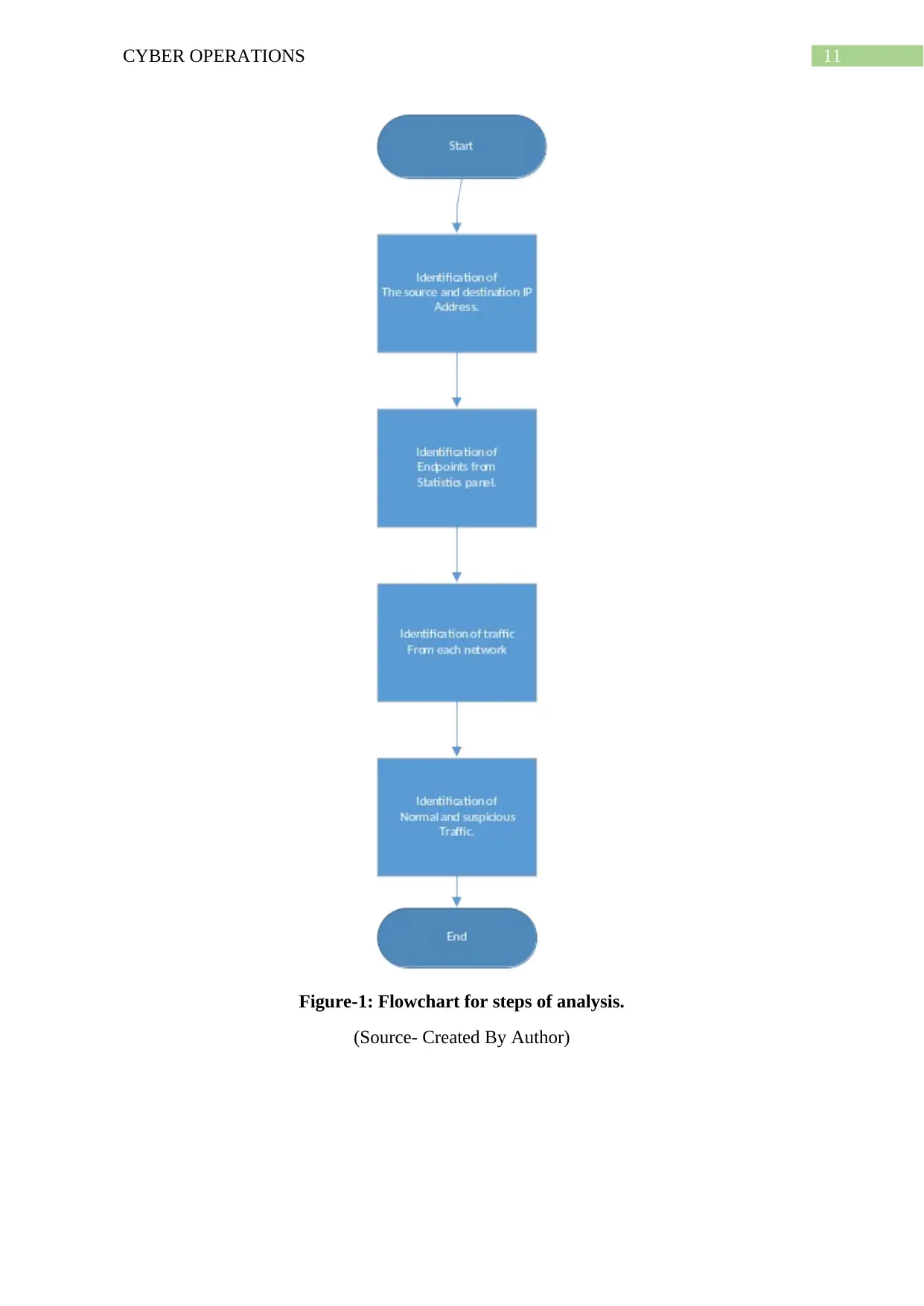
Steps for Analysis
Wireshark has been used for the purpose of capturing the network belonging to the
organization and with the help of this application, the packets that have been travelling from
one packet to that of other along with the traffic that enter as well as leaves the network. The
application also analyses and puts forward the traffic that is normal and the ones that is
considered to be a suspicious activity online (Choi et al. 2019). The steps that have been
followed for analysing the capture file with the help of Wireshark are,
The network that consists of a different source and a different destination IP address is
identified and noted down for carrying out the network packets that is communicated
from one network to another network.
Next, the endpoints of the destination network is identified from the statistics panel
present within the interface of the Wireshark application.
Recommendations
Digitalized transformations and upgradation of the existing infrastructure of IT within
the business organizations have led to various consequences and situations such as loss of
potential and sensitive data belonging to the organization along with the employees in
particular. Hence, it is recommended that the organizations should consider the
vulnerabilities existing within the endpoint conversations having a direct impact upon the
same to implement security measures for protection and securing of data. As a reason, this
will lead to proper mitigation of such potential attacks by hackers and leading to a better
process of communication.
Part-B
Steps for Analysis
Wireshark has been used for the purpose of capturing the network belonging to the
organization and with the help of this application, the packets that have been travelling from
one packet to that of other along with the traffic that enter as well as leaves the network. The
application also analyses and puts forward the traffic that is normal and the ones that is
considered to be a suspicious activity online (Choi et al. 2019). The steps that have been
followed for analysing the capture file with the help of Wireshark are,
The network that consists of a different source and a different destination IP address is
identified and noted down for carrying out the network packets that is communicated
from one network to another network.
Next, the endpoints of the destination network is identified from the statistics panel
present within the interface of the Wireshark application.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CYBER OPERATIONS
Following this, the traffic that comes out and enter each individual network is
identified from the flow graph option again present within the Wireshark interface
(Choi et al. 2019).
Lastly, the traffic that has been coming out or entering the respective network along
with the traffic that is normal as well as the suspicious ones have been identified.
Following this, the traffic that comes out and enter each individual network is
identified from the flow graph option again present within the Wireshark interface
(Choi et al. 2019).
Lastly, the traffic that has been coming out or entering the respective network along
with the traffic that is normal as well as the suspicious ones have been identified.
11CYBER OPERATIONS
Figure-1: Flowchart for steps of analysis.
(Source- Created By Author)
Figure-1: Flowchart for steps of analysis.
(Source- Created By Author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 24
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





