M&S Cyber Resilience: Data Breach and Cyber-Attack Strategies
VerifiedAdded on 2023/01/19
|10
|2187
|41
Report
AI Summary
This report examines the implementation of an information security management strategy to mitigate data breaches and cyber-attacks, with a specific focus on Marks and Spencer (M&S) within the UK retail sector. The research delves into the background of cyber threats in the context of globalization and technological advancements, highlighting the challenges faced by companies in securing consumer data. The report outlines the aims and objectives, including understanding information security, addressing challenges, and recommending solutions to enhance customer confidence. The literature review explores concepts of cyber resilience and its importance in maintaining data integrity. The methodology section details the use of qualitative research, an inductive approach, and a combination of primary and secondary data collection methods, including questionnaires and literature reviews. The report also addresses ethical considerations and includes a timeline for the research process. The appendix provides a sample questionnaire used for data collection. The report's findings and recommendations aim to improve M&S's cyber resilience, reduce data breach risks, and ultimately enhance customer trust in the company's online and offline operations.

CORPORATE STRATEGY
AND GOVERNANCE
RESEARCH
AND GOVERNANCE
RESEARCH
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
TABLE OF CONTENTS..............................................................................................................2
INTRODUCTION...........................................................................................................................4
Aim.........................................................................................................................................4
Objectives...............................................................................................................................4
LITERATURE REVIEW................................................................................................................5
RESEARCH METHODOLOGY.....................................................................................................6
TIMELINE.......................................................................................................................................7
REFERENCES................................................................................................................................9
APPENDIX....................................................................................................................................10
Questionnaire........................................................................................................................10
TABLE OF CONTENTS..............................................................................................................2
INTRODUCTION...........................................................................................................................4
Aim.........................................................................................................................................4
Objectives...............................................................................................................................4
LITERATURE REVIEW................................................................................................................5
RESEARCH METHODOLOGY.....................................................................................................6
TIMELINE.......................................................................................................................................7
REFERENCES................................................................................................................................9
APPENDIX....................................................................................................................................10
Questionnaire........................................................................................................................10

TOPIC- “Implementing information security management strategy to reduce the threats of
data breaches and cyber-attacks to improve customer confidence in the UK retail sector- A
case study of Marks and Spencer”
INTRODUCTION
Research background
With the help of globalization and modernisation there is much interaction between
different companies of different countries. And because of this many new advancements in
technologies have taken place as some of the countries have good technology and the other
country can use these technologies when they do business with each other (Peltier, 2016). These
advancement in technology leads the business to way of success. But these technologies
sometime possess problem in working and may lead to breach of data of even cyber- attacks or
crime.
For dealing with this topic the company selected is Marks and Spencer. This is a
company is a multinational retailer which was founded in the year 1884 by Michael Marks and
Thomas Spencer which is headquartered in London. The present research will focus on different
strategies which the company use to implement different information security management
system to control the data breach and cyber- attacks. The company as well as the retail sector of
the country are facing many issues relating to the technology and the consumers are not trusting
the techniques and technologies used by the company for recoding and saving the data of the
consumers. This is the main reason for the accomplishment of this research.
Aims and objectives
Aim
“To examine how M&S can improve the cyber resilience to enhance customer confidence in
company to decrease the risk of threat of breach of data and cyber-attacks.
Objectives
To understand the concept of information security management and cyber- attacks and
data breach
To discuss the challenges which company faces in managing the information security
To recommend some ways in order to overcome the challenges and identification of the
future research areas
data breaches and cyber-attacks to improve customer confidence in the UK retail sector- A
case study of Marks and Spencer”
INTRODUCTION
Research background
With the help of globalization and modernisation there is much interaction between
different companies of different countries. And because of this many new advancements in
technologies have taken place as some of the countries have good technology and the other
country can use these technologies when they do business with each other (Peltier, 2016). These
advancement in technology leads the business to way of success. But these technologies
sometime possess problem in working and may lead to breach of data of even cyber- attacks or
crime.
For dealing with this topic the company selected is Marks and Spencer. This is a
company is a multinational retailer which was founded in the year 1884 by Michael Marks and
Thomas Spencer which is headquartered in London. The present research will focus on different
strategies which the company use to implement different information security management
system to control the data breach and cyber- attacks. The company as well as the retail sector of
the country are facing many issues relating to the technology and the consumers are not trusting
the techniques and technologies used by the company for recoding and saving the data of the
consumers. This is the main reason for the accomplishment of this research.
Aims and objectives
Aim
“To examine how M&S can improve the cyber resilience to enhance customer confidence in
company to decrease the risk of threat of breach of data and cyber-attacks.
Objectives
To understand the concept of information security management and cyber- attacks and
data breach
To discuss the challenges which company faces in managing the information security
To recommend some ways in order to overcome the challenges and identification of the
future research areas
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Research questions
What is the concept of cyber resilience for improving the customer confidence?
How company can improve cyber resilience to improve customer confidence?
What are the different challenges which company faces in managing the information
security? What is some recommendation for improvement of strategies and future research?
Rationale
The present topic is being selected by the researcher because of the reason that this is the
latest topic going on in the business environment. The cyber resilience is the ability of the
company to deliver the expected outcome of the adverse cyber events. This is the major issues in
the business environment because there is much technological advancement in the business
environment. With the help of the report of the company it was outlined that the online sales of
the company decreased and this was pertaining to the fact that the consumers are having the
threat of losing their data to someone else.
LITERATURE REVIEW
In accordance with the AlKalbani, Deng and Kam, (2015) cyber resilience means the
ability of the company to withstand and the way of responding to the cyber-attacks which may
take place in the company system of networking. The main aim of the using the cyber resilience
is only to maintian the confidentiality and integrity of the data of the business as well as the
consumers data. In accordance to Susanto and Almunawar, (2018) both the cyvber security and
cyber resilience are interconnected with one another and both are equally important for the
company to maintain.
As per the view of Ahmad, Maynard and Shanks, (2015), Get management on board is
the best cyber resilience. This despite published evidence that cyber more risks because that
increasing this is not taken seriously enough. In this IT manager often have trouble
communicating with the business leaders about the security problems are facing the business.
This helps to describe a need for the further security which are measures to business leaders in
the organization. That is very important and effective for the business and for its growth factors.
This strategy is higher costly which defines the risk and scope of the problem to the board. This
will more effective and valuable for business.
What is the concept of cyber resilience for improving the customer confidence?
How company can improve cyber resilience to improve customer confidence?
What are the different challenges which company faces in managing the information
security? What is some recommendation for improvement of strategies and future research?
Rationale
The present topic is being selected by the researcher because of the reason that this is the
latest topic going on in the business environment. The cyber resilience is the ability of the
company to deliver the expected outcome of the adverse cyber events. This is the major issues in
the business environment because there is much technological advancement in the business
environment. With the help of the report of the company it was outlined that the online sales of
the company decreased and this was pertaining to the fact that the consumers are having the
threat of losing their data to someone else.
LITERATURE REVIEW
In accordance with the AlKalbani, Deng and Kam, (2015) cyber resilience means the
ability of the company to withstand and the way of responding to the cyber-attacks which may
take place in the company system of networking. The main aim of the using the cyber resilience
is only to maintian the confidentiality and integrity of the data of the business as well as the
consumers data. In accordance to Susanto and Almunawar, (2018) both the cyvber security and
cyber resilience are interconnected with one another and both are equally important for the
company to maintain.
As per the view of Ahmad, Maynard and Shanks, (2015), Get management on board is
the best cyber resilience. This despite published evidence that cyber more risks because that
increasing this is not taken seriously enough. In this IT manager often have trouble
communicating with the business leaders about the security problems are facing the business.
This helps to describe a need for the further security which are measures to business leaders in
the organization. That is very important and effective for the business and for its growth factors.
This strategy is higher costly which defines the risk and scope of the problem to the board. This
will more effective and valuable for business.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

AlHogail, (2015) stated that in respect of adapting the strategy relating to providing
training to all the employees of the company, it is examined that it is not necessary that every
employee must be expertise in security codes or carrying the wider Knowledge of the cyber
protection crime. Thus, in such aspects they must carry the basic Knowledge in respect of
finding the appropriate solution in respect of facing any such issues.
Soomro, Shah and Ahmed, (2016) argued that they are not agree with this fact that as
every employee had their own capability of learning and also grabbing knowledge on this
perspective. This is not necessary that employees must carry the learning skills to secure the
company from these aspects.
RESEARCH METHODOLOGY
Research type- the research type are the methods through which the whole research can
be carried on (Bryman, 2016). These are of two different types that is qualitative and
quantitative. For the present research on different strategies of information management system
the researcher will use the qualitative research. The qualitative research is the one which is based
on the study of theories and concept relating to the research. The quantitative research is the one
which is used when the numbers are used in order to carry on the research. The qualitative
research will be used by the researcher as they want to develop the concept of cyber resilience.
Research approach- this refers to as the different steps or process which are taken in
process to complete the research. The two different types of approach are inductive and
deductive. The approach that will be selected for the present research is inductive because this
approach compliments the qualitative research. The deductive approach is the one which
involves the making of hypothesis and then directing the whole research in the direction of
fulfilment of the research and testing the research hypothesis.
Data collection- for the research the most important thing is the data. If data will not be
there then no research can reach to any conclusion. The data can be collected from primary
sources and secondary sources. For completing present study researcher will use a combination
of the sources. In the primary source the help of questionnaire is taken and for the secondary
source the help of literature review that is views of different authors will be used.
Sampling- it is not possible to test the research on all the population therefore, from the
population some of the samples are selected and then research is done on these samples. For the
present research 30 managers of the company have been selected. For the selection of sample
training to all the employees of the company, it is examined that it is not necessary that every
employee must be expertise in security codes or carrying the wider Knowledge of the cyber
protection crime. Thus, in such aspects they must carry the basic Knowledge in respect of
finding the appropriate solution in respect of facing any such issues.
Soomro, Shah and Ahmed, (2016) argued that they are not agree with this fact that as
every employee had their own capability of learning and also grabbing knowledge on this
perspective. This is not necessary that employees must carry the learning skills to secure the
company from these aspects.
RESEARCH METHODOLOGY
Research type- the research type are the methods through which the whole research can
be carried on (Bryman, 2016). These are of two different types that is qualitative and
quantitative. For the present research on different strategies of information management system
the researcher will use the qualitative research. The qualitative research is the one which is based
on the study of theories and concept relating to the research. The quantitative research is the one
which is used when the numbers are used in order to carry on the research. The qualitative
research will be used by the researcher as they want to develop the concept of cyber resilience.
Research approach- this refers to as the different steps or process which are taken in
process to complete the research. The two different types of approach are inductive and
deductive. The approach that will be selected for the present research is inductive because this
approach compliments the qualitative research. The deductive approach is the one which
involves the making of hypothesis and then directing the whole research in the direction of
fulfilment of the research and testing the research hypothesis.
Data collection- for the research the most important thing is the data. If data will not be
there then no research can reach to any conclusion. The data can be collected from primary
sources and secondary sources. For completing present study researcher will use a combination
of the sources. In the primary source the help of questionnaire is taken and for the secondary
source the help of literature review that is views of different authors will be used.
Sampling- it is not possible to test the research on all the population therefore, from the
population some of the samples are selected and then research is done on these samples. For the
present research 30 managers of the company have been selected. For the selection of sample
random sampling will be chosen because under this method every person among population has
equal chance of being selected.
Data analysis- just assimilating the data is not enough also it needs to be analysed. This
analysis is of two types thematic and non- thematic (Murshed and Zhang, 2016). For current
study thematic analysis will be done. For the analysis of data firstly the questionnaire relating to
cyber resilience will be created and there after this will be distributed among the respondent and
they will answer the questions. Further with help of chart and graphs the data collected will be
analysed.
Ethical consideration- this is the most important part in the completion of the research.
This is because of the reason that whole research needs to be in ethical and correct manner. For
this the researcher will use the ethical approval form before asking any question to the
respondent. Also, in carrying on with this research all the norms and regulation will be followed
and all the work will be done in accordance with these regulations. Also, the data will be stored
in accordance with the data protection act.
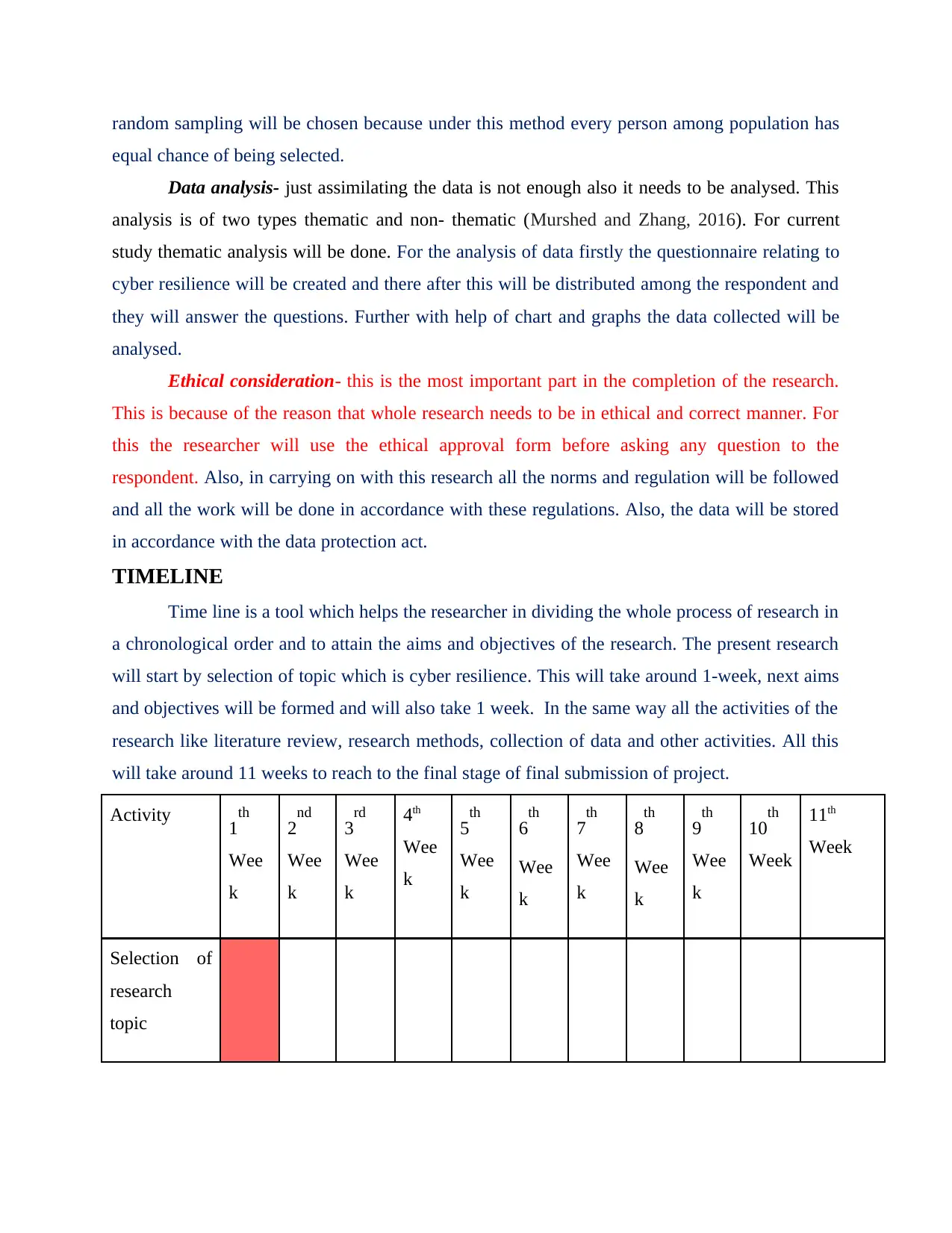
TIMELINE
Time line is a tool which helps the researcher in dividing the whole process of research in
a chronological order and to attain the aims and objectives of the research. The present research
will start by selection of topic which is cyber resilience. This will take around 1-week, next aims
and objectives will be formed and will also take 1 week. In the same way all the activities of the
research like literature review, research methods, collection of data and other activities. All this
will take around 11 weeks to reach to the final stage of final submission of project.
Activity 1th
Wee
k
2nd
Wee
k
3rd
Wee
k
4th
Wee
k
5th
Wee
k
6th
Wee
k
7th
Wee
k
8th
Wee
k
9th
Wee
k
10th
Week
11th
Week
Selection of
research
topic
equal chance of being selected.
Data analysis- just assimilating the data is not enough also it needs to be analysed. This
analysis is of two types thematic and non- thematic (Murshed and Zhang, 2016). For current
study thematic analysis will be done. For the analysis of data firstly the questionnaire relating to
cyber resilience will be created and there after this will be distributed among the respondent and
they will answer the questions. Further with help of chart and graphs the data collected will be
analysed.
Ethical consideration- this is the most important part in the completion of the research.
This is because of the reason that whole research needs to be in ethical and correct manner. For
this the researcher will use the ethical approval form before asking any question to the
respondent. Also, in carrying on with this research all the norms and regulation will be followed
and all the work will be done in accordance with these regulations. Also, the data will be stored
in accordance with the data protection act.
TIMELINE
Time line is a tool which helps the researcher in dividing the whole process of research in
a chronological order and to attain the aims and objectives of the research. The present research
will start by selection of topic which is cyber resilience. This will take around 1-week, next aims
and objectives will be formed and will also take 1 week. In the same way all the activities of the
research like literature review, research methods, collection of data and other activities. All this
will take around 11 weeks to reach to the final stage of final submission of project.
Activity 1th
Wee
k
2nd
Wee
k
3rd
Wee
k
4th
Wee
k
5th
Wee
k
6th
Wee
k
7th
Wee
k
8th
Wee
k
9th
Wee
k
10th
Week
11th
Week
Selection of
research
topic
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
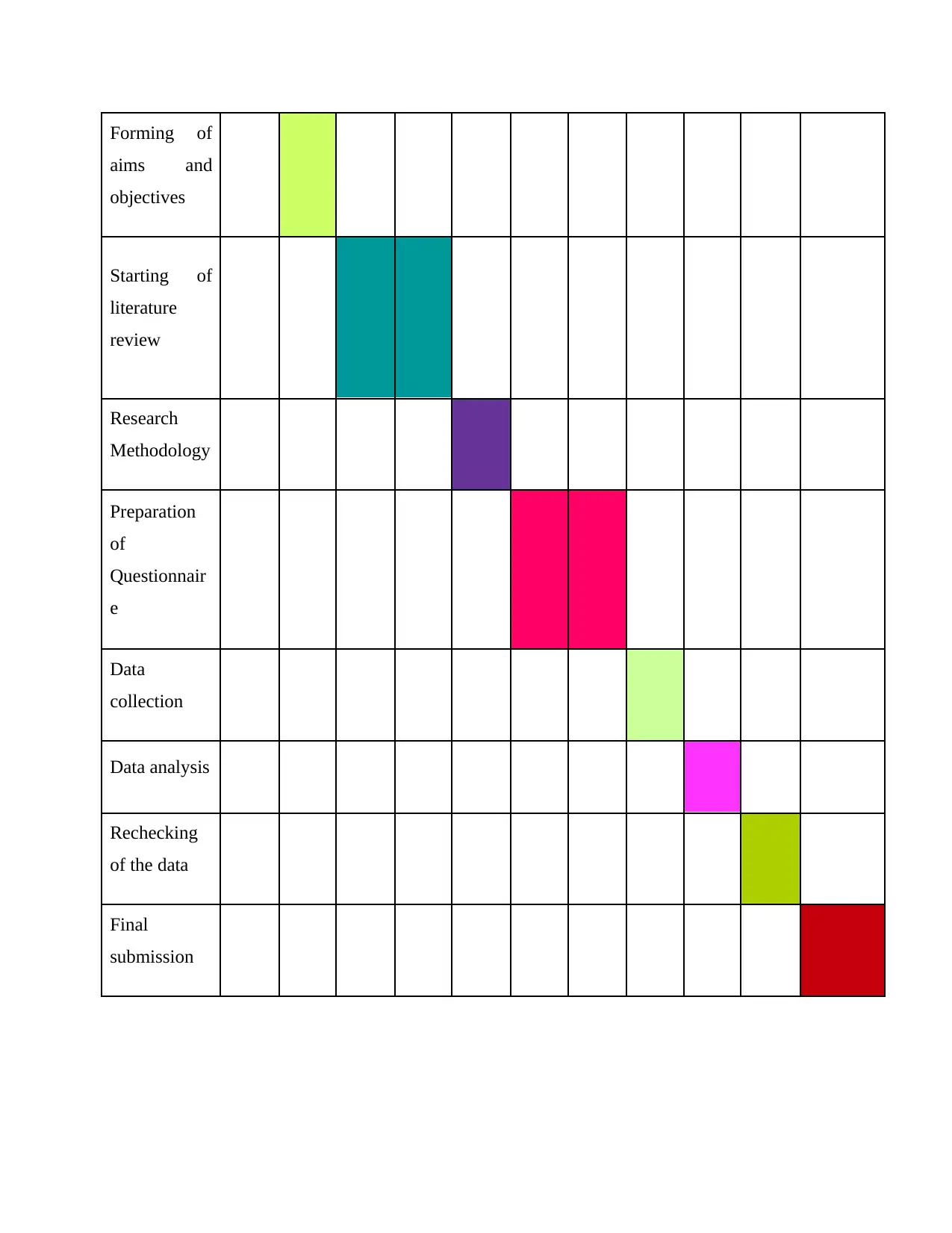
Forming of
aims and
objectives
Starting of
literature
review
Research
Methodology
Preparation
of
Questionnair
e
Data
collection
Data analysis
Rechecking
of the data
Final
submission
aims and
objectives
Starting of
literature
review
Research
Methodology
Preparation
of
Questionnair
e
Data
collection
Data analysis
Rechecking
of the data
Final
submission
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCES
Books and Journals
Ahmad, A., Maynard, S.B. and Shanks, G., 2015. A case analysis of information systems and
security incident responses. International Journal of Information Management. 35(6).
pp.717-723.
AlHogail, A., 2015. Design and validation of information security culture framework. Computers
in Human Behavior. 49. pp.567-575.
AlKalbani, A., Deng, H. and Kam, B., 2015, July. Organisational Security Culture and
Information Security Compliance for E-Government Development: The Moderating
Effect of Social Pressure. In PACIS (p. 65).
Bryman, A., 2016. Social research methods. Oxford university press.
Murshed, F. and Zhang, Y., 2016. Thinking orientation and preference for research
methodology. Journal of Consumer Marketing. 33(6). pp.437-446.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. Auerbach Publications.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs more
holistic approach: A literature review. International Journal of Information
Management. 36(2). pp.215-225.
Susanto, H. and Almunawar, M.N., 2018. Information Security Management Systems: A Novel
Framework and Software as a Tool for Compliance with Information Security Standard.
Apple Academic Press.
Books and Journals
Ahmad, A., Maynard, S.B. and Shanks, G., 2015. A case analysis of information systems and
security incident responses. International Journal of Information Management. 35(6).
pp.717-723.
AlHogail, A., 2015. Design and validation of information security culture framework. Computers
in Human Behavior. 49. pp.567-575.
AlKalbani, A., Deng, H. and Kam, B., 2015, July. Organisational Security Culture and
Information Security Compliance for E-Government Development: The Moderating
Effect of Social Pressure. In PACIS (p. 65).
Bryman, A., 2016. Social research methods. Oxford university press.
Murshed, F. and Zhang, Y., 2016. Thinking orientation and preference for research
methodology. Journal of Consumer Marketing. 33(6). pp.437-446.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. Auerbach Publications.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs more
holistic approach: A literature review. International Journal of Information
Management. 36(2). pp.215-225.
Susanto, H. and Almunawar, M.N., 2018. Information Security Management Systems: A Novel
Framework and Software as a Tool for Compliance with Information Security Standard.
Apple Academic Press.

APPENDIX
Questionnaire
Demographic information
Name:
Age:
Gender:
Q.1 According to you, how frequently situation pertaining to data security breach or theft
occurs?
Frequently ()
Less frequently ()
More frequently ()
One in a while ()
Q.2 Do you agree that information security system helps in avoiding cyber-attacks?
Agree ()
Strongly agree ()
Neutral ()
Disagree ()
Strongly disagree ()
Q.3 Do you think that aspect of data security breach negatively impacts productivity and
profitability of M&S?
Yes ()
No ()
Maybe ()
Q.4 Do you find adoption of advanced technology, for ensuring high information security, as
highly expensive?
Yes ()
No ()
Maybe ()
Q.5 Which kind of difficulty do you face while adopting IT tool for the purpose of
Lack of research & development ()
Having incompetent personnel ()
Questionnaire
Demographic information
Name:
Age:
Gender:
Q.1 According to you, how frequently situation pertaining to data security breach or theft
occurs?
Frequently ()
Less frequently ()
More frequently ()
One in a while ()
Q.2 Do you agree that information security system helps in avoiding cyber-attacks?
Agree ()
Strongly agree ()
Neutral ()
Disagree ()
Strongly disagree ()
Q.3 Do you think that aspect of data security breach negatively impacts productivity and
profitability of M&S?
Yes ()
No ()
Maybe ()
Q.4 Do you find adoption of advanced technology, for ensuring high information security, as
highly expensive?
Yes ()
No ()
Maybe ()
Q.5 Which kind of difficulty do you face while adopting IT tool for the purpose of
Lack of research & development ()
Having incompetent personnel ()
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

High investment ()
Q.6 Do you agree that modelling and simulation technologies contributes in avoiding security
vulnerabilities?
Agree ()
Strongly agree ()
Neutral ()
Disagree ()
Strongly disagree ()
Q.7 Do you agree that due to rise in information security breaches customers not prefer to
purchase via online?
Agree ()
Strongly agree ()
Neutral ()
Disagree ()
Strongly disagree ()
Q.8 Do you think that customer confidence can be built and enhanced by ensuring data security
system?
Yes ()
No ()
Maybe ()
Q.9 Please recommend strategies that can be undertaken for avoiding issues related to security
vulnerabilities and data theft……………………………………………………………………..
Q.6 Do you agree that modelling and simulation technologies contributes in avoiding security
vulnerabilities?
Agree ()
Strongly agree ()
Neutral ()
Disagree ()
Strongly disagree ()
Q.7 Do you agree that due to rise in information security breaches customers not prefer to
purchase via online?
Agree ()
Strongly agree ()
Neutral ()
Disagree ()
Strongly disagree ()
Q.8 Do you think that customer confidence can be built and enhanced by ensuring data security
system?
Yes ()
No ()
Maybe ()
Q.9 Please recommend strategies that can be undertaken for avoiding issues related to security
vulnerabilities and data theft……………………………………………………………………..
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





