Cyber Security Risk Assessment Report: SCU Educational Institute
VerifiedAdded on 2022/09/17
|9
|1516
|15
Report
AI Summary
This report provides a comprehensive cyber security risk assessment for the educational institute SCU. It begins by emphasizing the importance of risk assessment in developing and managing cyber security, identifying limitations in current methods. The report then details the identification of critical information assets through a series of questions and a WFA template. It highlights the top five threats, including external and internal cyber attacks, social engineering, emerging mobile computing threats, funding issues, and the value of information. Each threat is analyzed for its potential impact on information assets, ranked by severity. The conclusion underscores the importance of developing a robust risk assessment to mitigate potential vulnerabilities and strengthen the organization's security posture. References to relevant literature are also included.

Running head: CYBER SECURITY RISK ASSESSMENT
Cyber Security Risk Assessment
Name of the student:
Name of the university:
Author note:
Cyber Security Risk Assessment
Name of the student:
Name of the university:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBER SECURITY RISK ASSESSMENT
Table of Contents
Introduction:....................................................................................................................................3
Discussion:.......................................................................................................................................3
Task1:..........................................................................................................................................3
Task 2:.........................................................................................................................................4
Task 3:.........................................................................................................................................5
Task 4:.........................................................................................................................................7
Conclusion:......................................................................................................................................8
Table of Contents
Introduction:....................................................................................................................................3
Discussion:.......................................................................................................................................3
Task1:..........................................................................................................................................3
Task 2:.........................................................................................................................................4
Task 3:.........................................................................................................................................5
Task 4:.........................................................................................................................................7
Conclusion:......................................................................................................................................8

2CYBER SECURITY RISK ASSESSMENT
Introduction:
Current business organizations are becoming more and more intertwined with the use of
online technology and hence there arises a risk of cyber security within organizations for which
standard ways needs to be implemented within the organizational structure. The implementation
of cyber security program within organization helps in mitigating the existing issues that are
present within organization while implementing proper cyber security framework. This part of
the report reflects on the importance of cyber security program within the educational institute of
SCU while focusing on the major cyber security program that needs to be carried out within the
organization.
Discussion:
Task1:
Cyber Security Risk Assessment is one of the important parts while developing and
managing the cyber security within organizations. It helps in determining the possible threats that
may occur to a business based on system related information; business related information as
well as natural related information (Fielder et al. 2016). Implementing a proper cyber security
risk assessment within organization helps in identifying the possible threats that can take place
while helping the institute of SCU to manage the issues effectively using various mitigating
methods.
Limitations of the current risk assessment methods:
Introduction:
Current business organizations are becoming more and more intertwined with the use of
online technology and hence there arises a risk of cyber security within organizations for which
standard ways needs to be implemented within the organizational structure. The implementation
of cyber security program within organization helps in mitigating the existing issues that are
present within organization while implementing proper cyber security framework. This part of
the report reflects on the importance of cyber security program within the educational institute of
SCU while focusing on the major cyber security program that needs to be carried out within the
organization.
Discussion:
Task1:
Cyber Security Risk Assessment is one of the important parts while developing and
managing the cyber security within organizations. It helps in determining the possible threats that
may occur to a business based on system related information; business related information as
well as natural related information (Fielder et al. 2016). Implementing a proper cyber security
risk assessment within organization helps in identifying the possible threats that can take place
while helping the institute of SCU to manage the issues effectively using various mitigating
methods.
Limitations of the current risk assessment methods:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CYBER SECURITY RISK ASSESSMENT
Currently the limitations that exist within the risk assessment method of the organization
are as follows:
1. The traditional way of cyber risk assessment method consists of certain risks that cannot be
applied to the modern designing of the software.
2. The current risk assessment method has the issues with the effective inhibiting management
and lacks processes of efficient risk management.
3. The current risk assessment method of the organization lacks having sufficient expertise on
doing the risk analysis based on time.
Task 2:
Information assets:
Information assets are defined as a set of knowledge within an organization that is
managed within a single entity. The information assets of any organization consists of the
financial value of an organization and helps in increasing the direct relationship between the
number of people that are making use of the information asset within the organization.
Questionnaires to allow methods to identify the most critical information assets of the
organization:
1. What are the information assets of the institute of SCU ?
2. What are the possible risks that are related to the information assets of the organization?
3. What are costs of corrective versus for implementing preventive measures for the maintenance
of the critical assets?
Currently the limitations that exist within the risk assessment method of the organization
are as follows:
1. The traditional way of cyber risk assessment method consists of certain risks that cannot be
applied to the modern designing of the software.
2. The current risk assessment method has the issues with the effective inhibiting management
and lacks processes of efficient risk management.
3. The current risk assessment method of the organization lacks having sufficient expertise on
doing the risk analysis based on time.
Task 2:
Information assets:
Information assets are defined as a set of knowledge within an organization that is
managed within a single entity. The information assets of any organization consists of the
financial value of an organization and helps in increasing the direct relationship between the
number of people that are making use of the information asset within the organization.
Questionnaires to allow methods to identify the most critical information assets of the
organization:
1. What are the information assets of the institute of SCU ?
2. What are the possible risks that are related to the information assets of the organization?
3. What are costs of corrective versus for implementing preventive measures for the maintenance
of the critical assets?
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4CYBER SECURITY RISK ASSESSMENT
4. What are the currents conditions of the critical assets of the organization?
5. Does the assets need to be replaced or repaired?
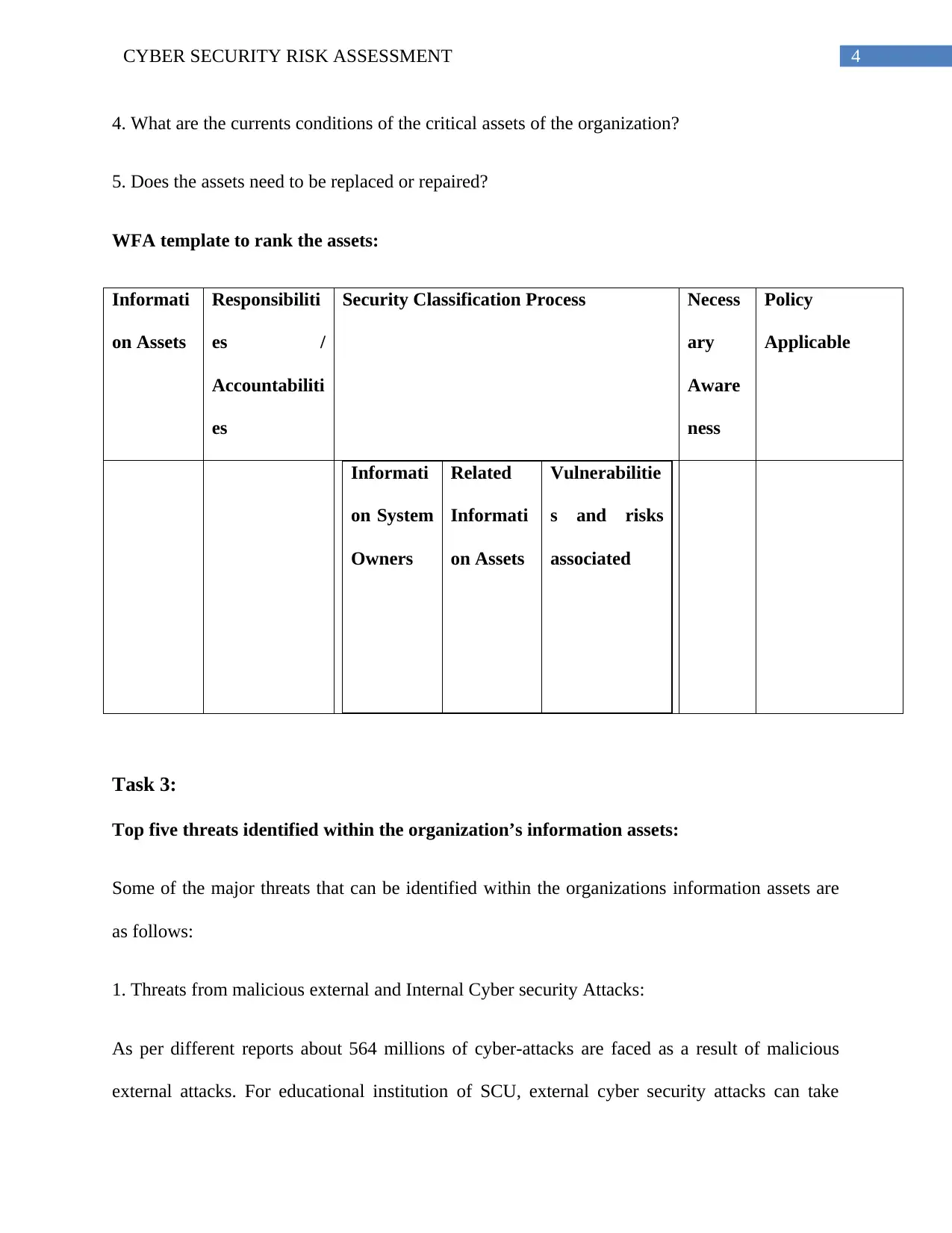
WFA template to rank the assets:
Informati
on Assets
Responsibiliti
es /
Accountabiliti
es
Security Classification Process Necess
ary
Aware
ness
Policy
Applicable
Informati
on System
Owners
Related
Informati
on Assets
Vulnerabilitie
s and risks
associated
Task 3:
Top five threats identified within the organization’s information assets:
Some of the major threats that can be identified within the organizations information assets are
as follows:
1. Threats from malicious external and Internal Cyber security Attacks:
As per different reports about 564 millions of cyber-attacks are faced as a result of malicious
external attacks. For educational institution of SCU, external cyber security attacks can take
4. What are the currents conditions of the critical assets of the organization?
5. Does the assets need to be replaced or repaired?
WFA template to rank the assets:
Informati
on Assets
Responsibiliti
es /
Accountabiliti
es
Security Classification Process Necess
ary
Aware
ness
Policy
Applicable
Informati
on System
Owners
Related
Informati
on Assets
Vulnerabilitie
s and risks
associated
Task 3:
Top five threats identified within the organization’s information assets:
Some of the major threats that can be identified within the organizations information assets are
as follows:
1. Threats from malicious external and Internal Cyber security Attacks:
As per different reports about 564 millions of cyber-attacks are faced as a result of malicious
external attacks. For educational institution of SCU, external cyber security attacks can take

5CYBER SECURITY RISK ASSESSMENT
place in different ways such as students clicking on to malicious hyperlinks that might contain
virus in it while enabling access to unprotected internet connections (Cherdantseva et al. 2016).
2. Social Engineering and Phishing Attacks:
Social Engineering and Phishing attacks are one of the most vulnerable threats that are related to
the information assets of the organisation of SCU (Krombholz et al. 2015). This type of threats
include gaining unauthorized access too the private information of the students, or memebers of
the institution including access to their passwords and other credential information (Anwar et al.
2015).
3. Threats with emerging mobile computing:
As the institution of SCU is taking full advantage of the use of mobile devices while making
classrooms more effective and interactive for educatrional purpose, hence it is more vulnerable
towards threats that may arise due to mobile computing (Karim et al. 2015) . This allows hacking
and accessing of mobile equipments that are used by students as wella s other memebers ogf the
sinstitution and exploiting the information assets contained in them.
4. Funding issues and Prioritization:
Funding issues is an important operational cost that is beared by almost all memebers of the
institutional organisation. Sometimes the organisation faces risks related to maintaining of the
constant evaluation of the costs while tremoving the vulnerabilities fro ttheir IT systems (Wang
and Rao 2015). The institution lacks to keep pace with the new types of risks that are faced
within the system and hence most of the information assets gets critically suffered.
5. Value of information:
place in different ways such as students clicking on to malicious hyperlinks that might contain
virus in it while enabling access to unprotected internet connections (Cherdantseva et al. 2016).
2. Social Engineering and Phishing Attacks:
Social Engineering and Phishing attacks are one of the most vulnerable threats that are related to
the information assets of the organisation of SCU (Krombholz et al. 2015). This type of threats
include gaining unauthorized access too the private information of the students, or memebers of
the institution including access to their passwords and other credential information (Anwar et al.
2015).
3. Threats with emerging mobile computing:
As the institution of SCU is taking full advantage of the use of mobile devices while making
classrooms more effective and interactive for educatrional purpose, hence it is more vulnerable
towards threats that may arise due to mobile computing (Karim et al. 2015) . This allows hacking
and accessing of mobile equipments that are used by students as wella s other memebers ogf the
sinstitution and exploiting the information assets contained in them.
4. Funding issues and Prioritization:
Funding issues is an important operational cost that is beared by almost all memebers of the
institutional organisation. Sometimes the organisation faces risks related to maintaining of the
constant evaluation of the costs while tremoving the vulnerabilities fro ttheir IT systems (Wang
and Rao 2015). The institution lacks to keep pace with the new types of risks that are faced
within the system and hence most of the information assets gets critically suffered.
5. Value of information:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6CYBER SECURITY RISK ASSESSMENT
Maintaining the value of information is an important aspect that needs to be maintained within
organization and the educational institutions need to follow measures to maintain most of their
financial information. As this type of information are related with other information assets like
addresses, social security numbers and other bank credential information of the students hence
threats may arise if these types of data gets threatened (Soomro, Shah and Ahmed 2016).
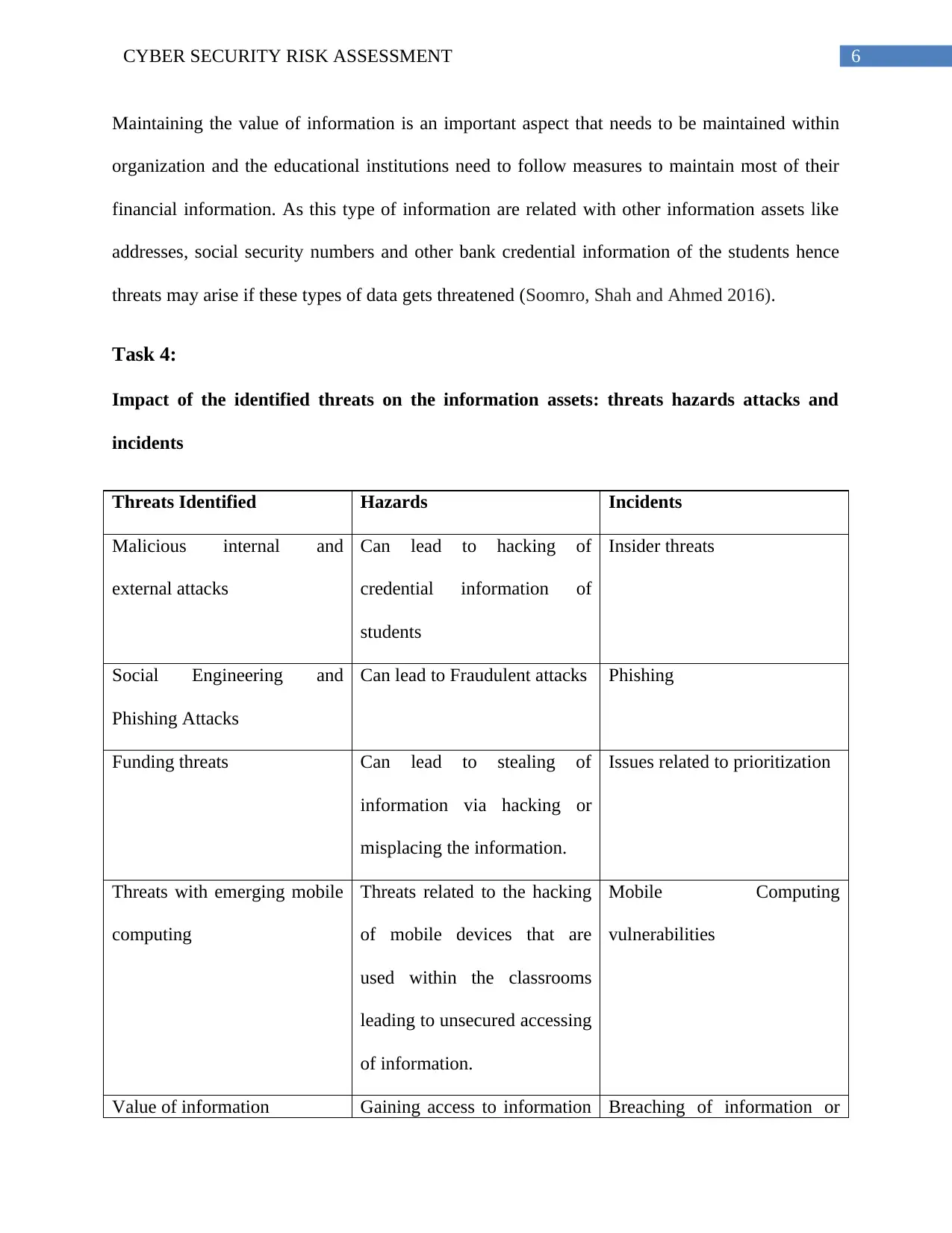
Task 4:
Impact of the identified threats on the information assets: threats hazards attacks and
incidents
Threats Identified Hazards Incidents
Malicious internal and
external attacks
Can lead to hacking of
credential information of
students
Insider threats
Social Engineering and
Phishing Attacks
Can lead to Fraudulent attacks Phishing
Funding threats Can lead to stealing of
information via hacking or
misplacing the information.
Issues related to prioritization
Threats with emerging mobile
computing
Threats related to the hacking
of mobile devices that are
used within the classrooms
leading to unsecured accessing
of information.
Mobile Computing
vulnerabilities
Value of information Gaining access to information Breaching of information or
Maintaining the value of information is an important aspect that needs to be maintained within
organization and the educational institutions need to follow measures to maintain most of their
financial information. As this type of information are related with other information assets like
addresses, social security numbers and other bank credential information of the students hence
threats may arise if these types of data gets threatened (Soomro, Shah and Ahmed 2016).
Task 4:
Impact of the identified threats on the information assets: threats hazards attacks and
incidents
Threats Identified Hazards Incidents
Malicious internal and
external attacks
Can lead to hacking of
credential information of
students
Insider threats
Social Engineering and
Phishing Attacks
Can lead to Fraudulent attacks Phishing
Funding threats Can lead to stealing of
information via hacking or
misplacing the information.
Issues related to prioritization
Threats with emerging mobile
computing
Threats related to the hacking
of mobile devices that are
used within the classrooms
leading to unsecured accessing
of information.
Mobile Computing
vulnerabilities
Value of information Gaining access to information Breaching of information or
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7CYBER SECURITY RISK ASSESSMENT
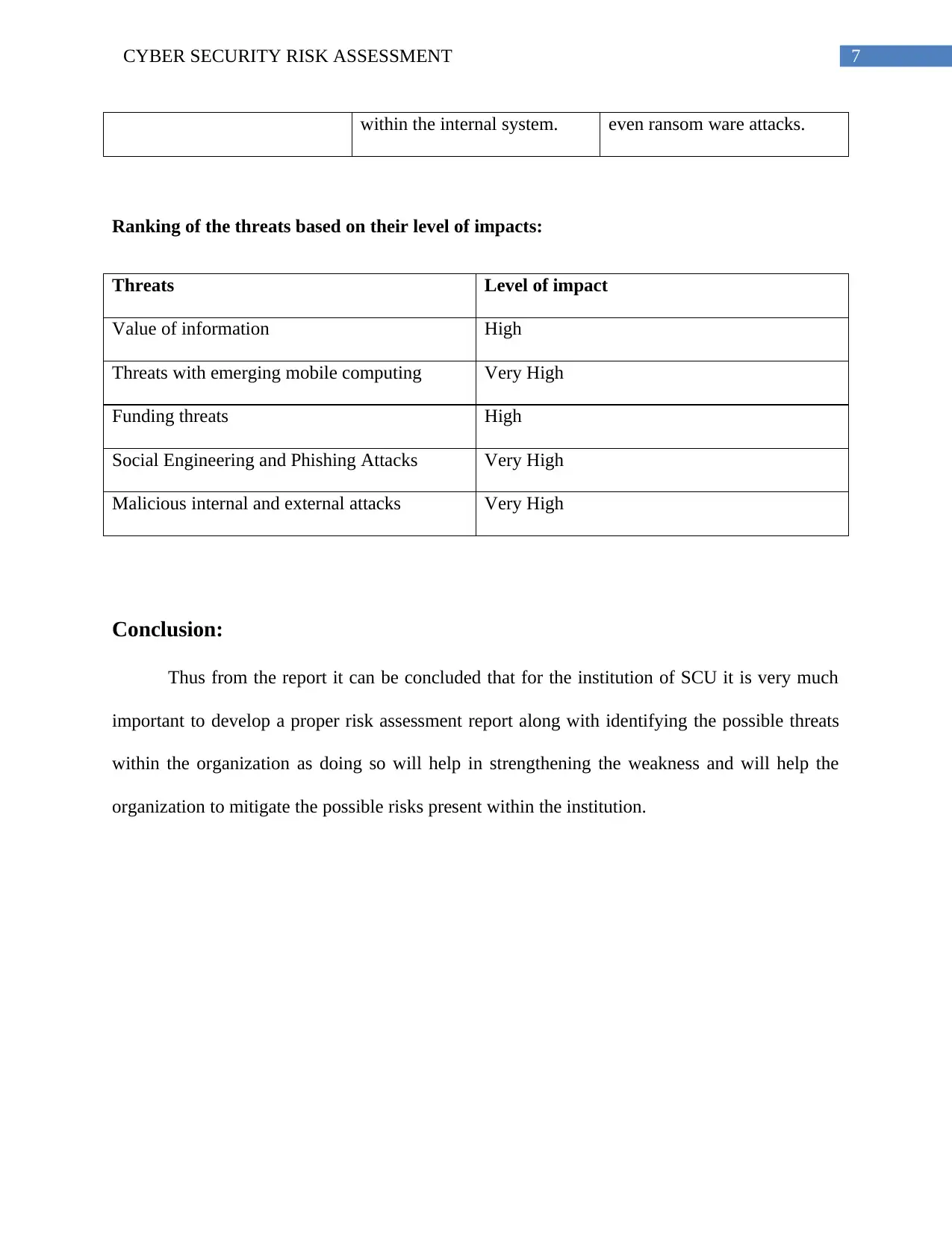
within the internal system. even ransom ware attacks.
Ranking of the threats based on their level of impacts:
Threats Level of impact
Value of information High
Threats with emerging mobile computing Very High
Funding threats High
Social Engineering and Phishing Attacks Very High
Malicious internal and external attacks Very High
Conclusion:
Thus from the report it can be concluded that for the institution of SCU it is very much
important to develop a proper risk assessment report along with identifying the possible threats
within the organization as doing so will help in strengthening the weakness and will help the
organization to mitigate the possible risks present within the institution.
within the internal system. even ransom ware attacks.
Ranking of the threats based on their level of impacts:
Threats Level of impact
Value of information High
Threats with emerging mobile computing Very High
Funding threats High
Social Engineering and Phishing Attacks Very High
Malicious internal and external attacks Very High
Conclusion:
Thus from the report it can be concluded that for the institution of SCU it is very much
important to develop a proper risk assessment report along with identifying the possible threats
within the organization as doing so will help in strengthening the weakness and will help the
organization to mitigate the possible risks present within the institution.

8CYBER SECURITY RISK ASSESSMENT
References:
Anwar, R.W., Bakhtiari, M., Zainal, A., Abdullah, A.H. and Qureshi, K.N., 2015, May.
Enhanced trust aware routing against wormhole attacks in wireless sensor networks. In 2015
International Conference on Smart Sensors and Application (ICSSA) (pp. 56-59). IEEE.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H. and Stoddart, K., 2016.
A review of cyber security risk assessment methods for SCADA systems. Computers &
security, 56, pp.1-27.
Fielder, A., Panaousis, E., Malacaria, P., Hankin, C. and Smeraldi, F., 2016. Decision support
approaches for cyber security investment. Decision Support Systems, 86, pp.13-23.
Karim, A., Shah, S.A.A., Salleh, R.B., Arif, M. and Noor, R.M., 2015. Mobile botnet attacks–An
emerging threat: Classification, review and open issues. KSII Transactions on Internet and
Information Systems (TIIS), 9(4), pp.1471-1492.
Krombholz, K., Hobel, H., Huber, M. and Weippl, E., 2015. Advanced social engineering
attacks. Journal of Information Security and applications, 22, pp.113-122.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs more
holistic approach: A literature review. International Journal of Information Management, 36(2),
pp.215-225.
Wang, J., Gupta, M. and Rao, H.R., 2015. Insider threats in a financial institution: Analysis of
attack-proneness of information systems applications. MIS quarterly, 39(1).
References:
Anwar, R.W., Bakhtiari, M., Zainal, A., Abdullah, A.H. and Qureshi, K.N., 2015, May.
Enhanced trust aware routing against wormhole attacks in wireless sensor networks. In 2015
International Conference on Smart Sensors and Application (ICSSA) (pp. 56-59). IEEE.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H. and Stoddart, K., 2016.
A review of cyber security risk assessment methods for SCADA systems. Computers &
security, 56, pp.1-27.
Fielder, A., Panaousis, E., Malacaria, P., Hankin, C. and Smeraldi, F., 2016. Decision support
approaches for cyber security investment. Decision Support Systems, 86, pp.13-23.
Karim, A., Shah, S.A.A., Salleh, R.B., Arif, M. and Noor, R.M., 2015. Mobile botnet attacks–An
emerging threat: Classification, review and open issues. KSII Transactions on Internet and
Information Systems (TIIS), 9(4), pp.1471-1492.
Krombholz, K., Hobel, H., Huber, M. and Weippl, E., 2015. Advanced social engineering
attacks. Journal of Information Security and applications, 22, pp.113-122.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs more
holistic approach: A literature review. International Journal of Information Management, 36(2),
pp.215-225.
Wang, J., Gupta, M. and Rao, H.R., 2015. Insider threats in a financial institution: Analysis of
attack-proneness of information systems applications. MIS quarterly, 39(1).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





