Cyber Operations Report: Wireshark Analysis and Security Principles
VerifiedAdded on 2023/01/18
|15
|2960
|74
Report
AI Summary
This report provides an in-depth analysis of cyber operations, focusing on the principles of cyber maneuver and the application of computer security principles within a modern environment. The report examines the technical aspects of cyberspace, emphasizing the need for adaptability and rapid response in a dynamic landscape. It delves into the classification of cyber operations, differentiating between offensive and defensive strategies, and highlights the importance of situational awareness. Furthermore, the report utilizes Wireshark to perform packet capture analysis, detailing the identification of network traffic, the interpretation of packet data, and the analysis of potential security threats. The analysis includes the identification of network congestion, packet loss, and undesirable network behavior, with a focus on TCP and UDP traffic. The report concludes by emphasizing the importance of confidentiality, integrity, and availability in maintaining a secure network system.

Cyber Operations
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................3
TASK 2............................................................................................................................................3
Principles of Cyber Maneuver................................................................................................3
Cyber Operations in the modern environment.......................................................................4
TASK 3............................................................................................................................................5
Describe about the advanced principles of computer security from the system....................5
Packet Capture analysis..........................................................................................................6
CONCLUSION..............................................................................................................................13
REFERENCES..............................................................................................................................14
INTRODUCTION...........................................................................................................................3
TASK 2............................................................................................................................................3
Principles of Cyber Maneuver................................................................................................3
Cyber Operations in the modern environment.......................................................................4
TASK 3............................................................................................................................................5
Describe about the advanced principles of computer security from the system....................5
Packet Capture analysis..........................................................................................................6
CONCLUSION..............................................................................................................................13
REFERENCES..............................................................................................................................14

INTRODUCTION
The Cyber Operations Mission Area is shaping the future of warfare through cyber operations,
focusing on assuring critical Department of Defense missions, delivering key solutions to enable
intelligence and military operations, and developing the systems that underpin novel operational
capabilities in cyberspace and across the electromagnetic spectrum. This documentation will
demonstrate about the packet capture analysis by using Wireshark. It will identify the suitable
security principle and practices that must require to adopt in the data transmission from one place
to another. Furthermore, it will discuss about principle of Cyber Maneuver which will capable
for identifying technical aspects.
TASK 2
Principles of Cyber Maneuver
Maneuver of cyberspace depend on the capabilities of technical aspects in an environment
which is rapidly changing and developing in this industry. The domain of cyberspace gives the
introduction of series with considerations that are distinct and which applies to warfare in
traditional approach which helps to analyze the operations of cyberspace. (Saner and et.al.,
2016.) Actions are occurred according to the speed of the machine and it vary according to the
distance which may be enormous and can be affected or done by many attackers who set a
parallel series of targets. It is impossible to give an attribute to an entity even after discovering
them and even if it is concerned with defending them. Range of operations of cyberspace and
their targets can be reach from a single station to hundreds or thousands of servers which already
stores the information of millions of people. By leveraging the domain any single person can
influence the data in a misappropriate manner with the technology that cannot be discovered
which increases the vulnerability of this sector under a nation, state or corporation. This domain
of cyberspace has some unique aspects which helps in creating a battle space which is
fundamentally different. Also, the considerations which are necessary are branch of this
maneuver theory distinctly. Warfare of this approach is traditional and it involves big decisions
and information such as movement of forces of military which also gives the advantage to the
The Cyber Operations Mission Area is shaping the future of warfare through cyber operations,
focusing on assuring critical Department of Defense missions, delivering key solutions to enable
intelligence and military operations, and developing the systems that underpin novel operational
capabilities in cyberspace and across the electromagnetic spectrum. This documentation will
demonstrate about the packet capture analysis by using Wireshark. It will identify the suitable
security principle and practices that must require to adopt in the data transmission from one place
to another. Furthermore, it will discuss about principle of Cyber Maneuver which will capable
for identifying technical aspects.
TASK 2
Principles of Cyber Maneuver
Maneuver of cyberspace depend on the capabilities of technical aspects in an environment
which is rapidly changing and developing in this industry. The domain of cyberspace gives the
introduction of series with considerations that are distinct and which applies to warfare in
traditional approach which helps to analyze the operations of cyberspace. (Saner and et.al.,
2016.) Actions are occurred according to the speed of the machine and it vary according to the
distance which may be enormous and can be affected or done by many attackers who set a
parallel series of targets. It is impossible to give an attribute to an entity even after discovering
them and even if it is concerned with defending them. Range of operations of cyberspace and
their targets can be reach from a single station to hundreds or thousands of servers which already
stores the information of millions of people. By leveraging the domain any single person can
influence the data in a misappropriate manner with the technology that cannot be discovered
which increases the vulnerability of this sector under a nation, state or corporation. This domain
of cyberspace has some unique aspects which helps in creating a battle space which is
fundamentally different. Also, the considerations which are necessary are branch of this
maneuver theory distinctly. Warfare of this approach is traditional and it involves big decisions
and information such as movement of forces of military which also gives the advantage to the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

forces of military when the issues are concerned with attack and defense. In this area military
uses this software, hardware, operators in a way which is offensive or defensive in the operation
of cyberspace. The concept of this method is to support the fire which are elements of non-
proximate substances and the movement of the forces does not help it describing it in a accurate
manner which is in relation with the action of these operations linked with cyberspace. Maneuver
forces must have advantage because the reason is the environment gets manipulated with the
help of operations of cyberspace. This approach and method is consists of a series of firewalls on
a network. It is required and enabled so that it can be used to defense the operations of
cyberspace. Operations which are related to cyberspace can be classified in two ways and that is
either the actions done by them can be offensive or defensive. (Power, 2017) It is often seen that
actions which are related to offensive cyberspace are used for the aspects which are concerned
with degradation, denial, destruction or disruption so that the target which is set can be
manipulated with the help of employing cyberspace capabilities. The effects which are the results
of the offensive classification are generally comes under positioning, exploitative or actions
which can be influenced. Actions which are kinetic sometimes they can also be used for the same
actions as offensive. The manner in which these effects are made in this domain are not linked
directly to the approach or method of this theory of Maneuver. On the other hand, actions which
are classified as defensive cyberspace. This classification is extent with a slightly more degree of
operations. It helps in stating the maneuver that secure, rebuild, protect or recover the survey of
networks which are friendly. To accomplish these effects, first step is to categorize the operation
as deceptive defense, perimeter defense or the target that moves the action of defense. Moving
the target even when it is not evolved from single force of this maneuver domain that is also the
least similar to the actions which are traditional. (Lewis, 2015)
Cyber Operations in the modern environment
These types of operations are concerned with defending the attack on the computer and
networks. It also includes real attacks and techniques which are classified as offensive and
defensive. It is supported by resources which are rich in nature. (Steiner, 2017) To enable this
process DNS and directory which is active is required through the services and network which is
common. The whole program involves web servers and database and it ends with a web
application that is complex. By this infrastructure of defensive classification can be made which
includes system which can detect intrusion, application of firewalls, log servers. The concept of
uses this software, hardware, operators in a way which is offensive or defensive in the operation
of cyberspace. The concept of this method is to support the fire which are elements of non-
proximate substances and the movement of the forces does not help it describing it in a accurate
manner which is in relation with the action of these operations linked with cyberspace. Maneuver
forces must have advantage because the reason is the environment gets manipulated with the
help of operations of cyberspace. This approach and method is consists of a series of firewalls on
a network. It is required and enabled so that it can be used to defense the operations of
cyberspace. Operations which are related to cyberspace can be classified in two ways and that is
either the actions done by them can be offensive or defensive. (Power, 2017) It is often seen that
actions which are related to offensive cyberspace are used for the aspects which are concerned
with degradation, denial, destruction or disruption so that the target which is set can be
manipulated with the help of employing cyberspace capabilities. The effects which are the results
of the offensive classification are generally comes under positioning, exploitative or actions
which can be influenced. Actions which are kinetic sometimes they can also be used for the same
actions as offensive. The manner in which these effects are made in this domain are not linked
directly to the approach or method of this theory of Maneuver. On the other hand, actions which
are classified as defensive cyberspace. This classification is extent with a slightly more degree of
operations. It helps in stating the maneuver that secure, rebuild, protect or recover the survey of
networks which are friendly. To accomplish these effects, first step is to categorize the operation
as deceptive defense, perimeter defense or the target that moves the action of defense. Moving
the target even when it is not evolved from single force of this maneuver domain that is also the
least similar to the actions which are traditional. (Lewis, 2015)
Cyber Operations in the modern environment
These types of operations are concerned with defending the attack on the computer and
networks. It also includes real attacks and techniques which are classified as offensive and
defensive. It is supported by resources which are rich in nature. (Steiner, 2017) To enable this
process DNS and directory which is active is required through the services and network which is
common. The whole program involves web servers and database and it ends with a web
application that is complex. By this infrastructure of defensive classification can be made which
includes system which can detect intrusion, application of firewalls, log servers. The concept of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

this approach is that anyone can defend the network if they know how to attempt an attack. For
starters attacks such as elementary attacks are done against web browsers so that defense cannot
be compromised of the sites of e-commerce. Techniques of these which are used in key areas for
defense through integration of services and exposition. Situational awareness is also needed to
develop the network. These operations in modern era are crucial in the cases of contemporary
conflict that too in the area which are limited to intelligence. These operations are also a part of
information of the states and operations related to warfare and helps in controlling these factors.
(Schmitt, 2017) In this era the concept and abilities of cyber operations will evolve with time as
demand of this approach will increase. Due to the hindrances of technological aspect
development in this operation take longer than it should. It has been proved that there is a
relationship between dawn of armor warfare and cyber warfare all because of culture which is
dependent on path favor.
TASK 3
Describe about the advanced principles of computer security from the system.
Security is basically constant term when it comes to information technology which protect
data through malware, hacking and data theft. These are different type of threat that directly
affects on the overall process of network system. At that time when it will send a data from
source to destination (Sanders, 2017). It increases the different types of risk issues and problem.
In this way, it will require to follows common principles for managing and controlling overall
network system.
Confidentiality: It is important principle that should protect the information by
unauthorised person. Only authorised person will access the information through network
system.
Integrity: Data integrity is a part of security concept which maintained the assurance,
consistency and accuracy of consistent data or information. It is a critical aspect of
design, implementation and usage of any system which are stored, processes and retrieves
data or information.
Availability: it is an accessible for information when its authorised users need it. Data
availability is an ability to ensure that require for accessible authorised (Bagyalakshmi
and et.al., 2018). It needed for managing the overall information or data at the time of
sending from one place to another.
starters attacks such as elementary attacks are done against web browsers so that defense cannot
be compromised of the sites of e-commerce. Techniques of these which are used in key areas for
defense through integration of services and exposition. Situational awareness is also needed to
develop the network. These operations in modern era are crucial in the cases of contemporary
conflict that too in the area which are limited to intelligence. These operations are also a part of
information of the states and operations related to warfare and helps in controlling these factors.
(Schmitt, 2017) In this era the concept and abilities of cyber operations will evolve with time as
demand of this approach will increase. Due to the hindrances of technological aspect
development in this operation take longer than it should. It has been proved that there is a
relationship between dawn of armor warfare and cyber warfare all because of culture which is
dependent on path favor.
TASK 3
Describe about the advanced principles of computer security from the system.
Security is basically constant term when it comes to information technology which protect
data through malware, hacking and data theft. These are different type of threat that directly
affects on the overall process of network system. At that time when it will send a data from
source to destination (Sanders, 2017). It increases the different types of risk issues and problem.
In this way, it will require to follows common principles for managing and controlling overall
network system.
Confidentiality: It is important principle that should protect the information by
unauthorised person. Only authorised person will access the information through network
system.
Integrity: Data integrity is a part of security concept which maintained the assurance,
consistency and accuracy of consistent data or information. It is a critical aspect of
design, implementation and usage of any system which are stored, processes and retrieves
data or information.
Availability: it is an accessible for information when its authorised users need it. Data
availability is an ability to ensure that require for accessible authorised (Bagyalakshmi
and et.al., 2018). It needed for managing the overall information or data at the time of
sending from one place to another.
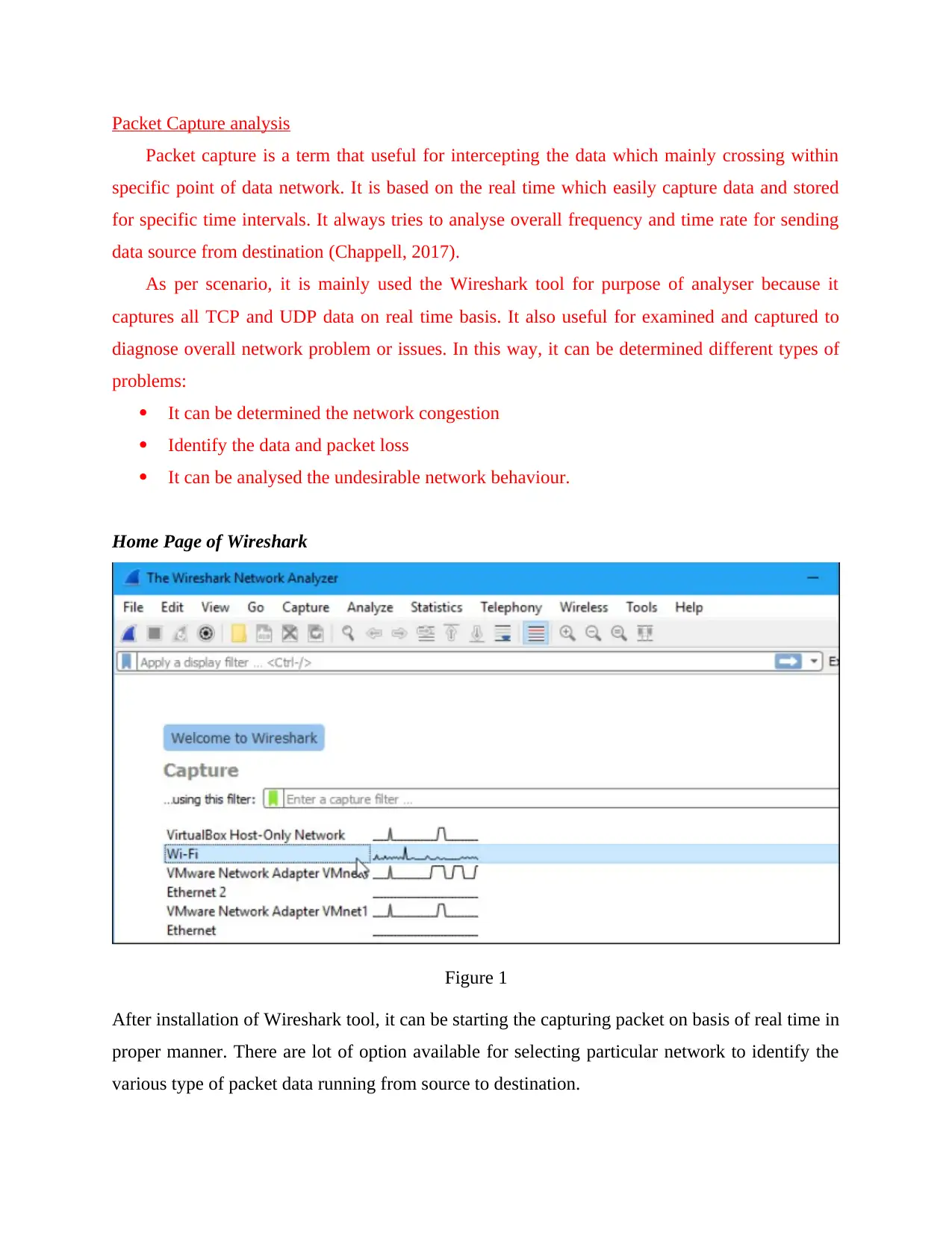
Packet Capture analysis
Packet capture is a term that useful for intercepting the data which mainly crossing within
specific point of data network. It is based on the real time which easily capture data and stored
for specific time intervals. It always tries to analyse overall frequency and time rate for sending
data source from destination (Chappell, 2017).
As per scenario, it is mainly used the Wireshark tool for purpose of analyser because it
captures all TCP and UDP data on real time basis. It also useful for examined and captured to
diagnose overall network problem or issues. In this way, it can be determined different types of
problems:
It can be determined the network congestion
Identify the data and packet loss
It can be analysed the undesirable network behaviour.
Home Page of Wireshark
Figure 1
After installation of Wireshark tool, it can be starting the capturing packet on basis of real time in
proper manner. There are lot of option available for selecting particular network to identify the
various type of packet data running from source to destination.
Packet capture is a term that useful for intercepting the data which mainly crossing within
specific point of data network. It is based on the real time which easily capture data and stored
for specific time intervals. It always tries to analyse overall frequency and time rate for sending
data source from destination (Chappell, 2017).
As per scenario, it is mainly used the Wireshark tool for purpose of analyser because it
captures all TCP and UDP data on real time basis. It also useful for examined and captured to
diagnose overall network problem or issues. In this way, it can be determined different types of
problems:
It can be determined the network congestion
Identify the data and packet loss
It can be analysed the undesirable network behaviour.
Home Page of Wireshark
Figure 1
After installation of Wireshark tool, it can be starting the capturing packet on basis of real time in
proper manner. There are lot of option available for selecting particular network to identify the
various type of packet data running from source to destination.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
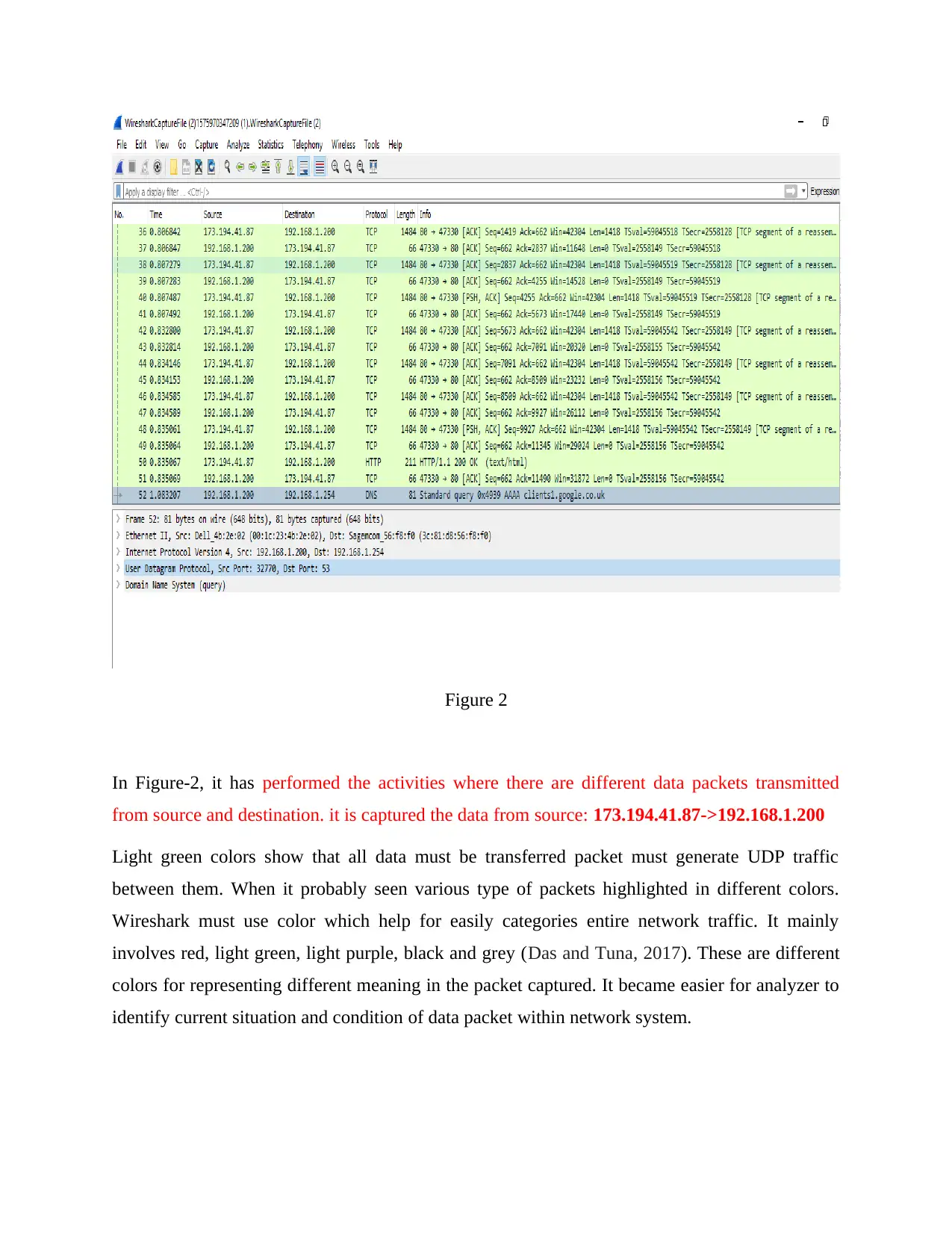
Figure 2
In Figure-2, it has performed the activities where there are different data packets transmitted
from source and destination. it is captured the data from source: 173.194.41.87->192.168.1.200
Light green colors show that all data must be transferred packet must generate UDP traffic
between them. When it probably seen various type of packets highlighted in different colors.
Wireshark must use color which help for easily categories entire network traffic. It mainly
involves red, light green, light purple, black and grey (Das and Tuna, 2017). These are different
colors for representing different meaning in the packet captured. It became easier for analyzer to
identify current situation and condition of data packet within network system.
In Figure-2, it has performed the activities where there are different data packets transmitted
from source and destination. it is captured the data from source: 173.194.41.87->192.168.1.200
Light green colors show that all data must be transferred packet must generate UDP traffic
between them. When it probably seen various type of packets highlighted in different colors.
Wireshark must use color which help for easily categories entire network traffic. It mainly
involves red, light green, light purple, black and grey (Das and Tuna, 2017). These are different
colors for representing different meaning in the packet captured. It became easier for analyzer to
identify current situation and condition of data packet within network system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
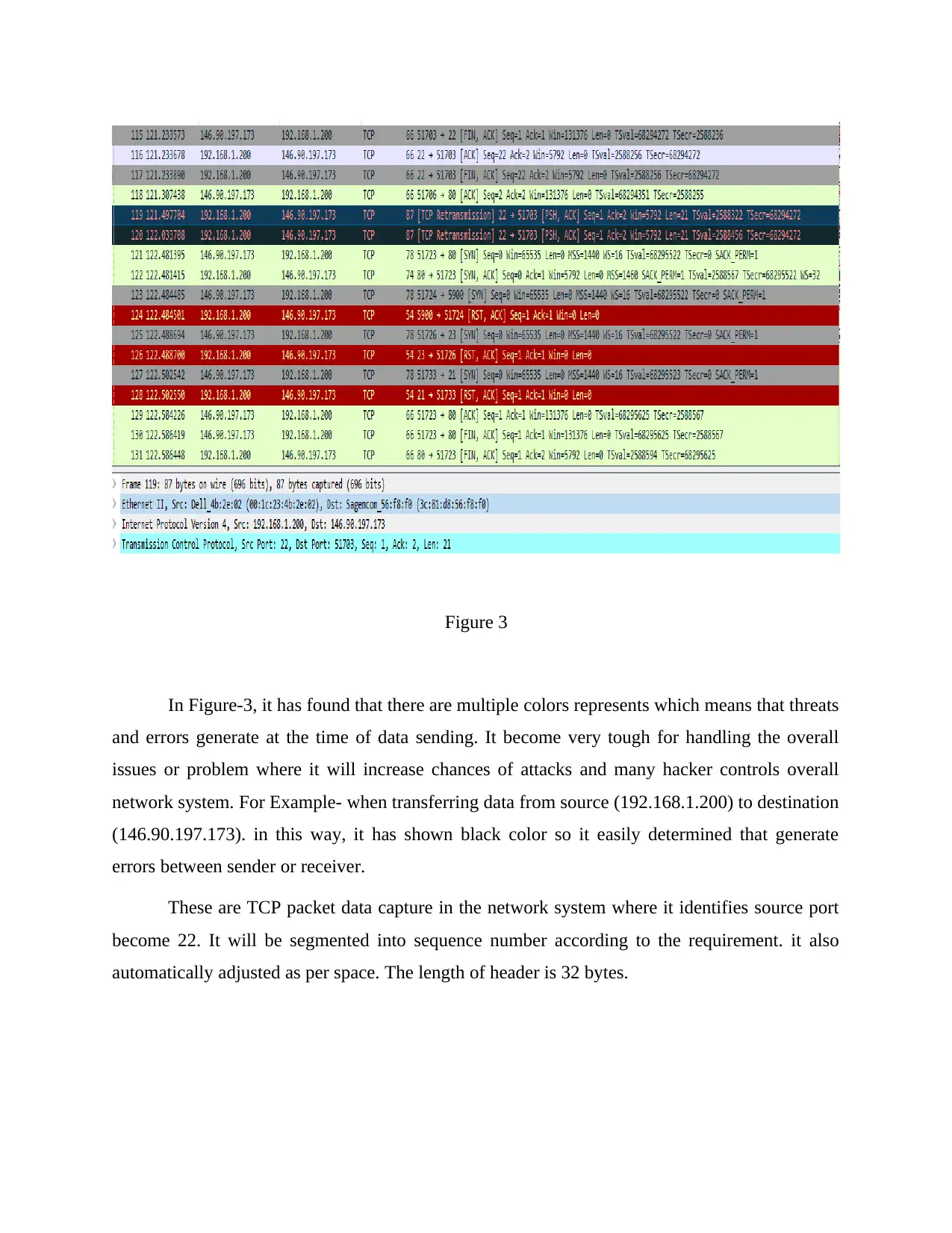
Figure 3
In Figure-3, it has found that there are multiple colors represents which means that threats
and errors generate at the time of data sending. It become very tough for handling the overall
issues or problem where it will increase chances of attacks and many hacker controls overall
network system. For Example- when transferring data from source (192.168.1.200) to destination
(146.90.197.173). in this way, it has shown black color so it easily determined that generate
errors between sender or receiver.
These are TCP packet data capture in the network system where it identifies source port
become 22. It will be segmented into sequence number according to the requirement. it also
automatically adjusted as per space. The length of header is 32 bytes.
In Figure-3, it has found that there are multiple colors represents which means that threats
and errors generate at the time of data sending. It become very tough for handling the overall
issues or problem where it will increase chances of attacks and many hacker controls overall
network system. For Example- when transferring data from source (192.168.1.200) to destination
(146.90.197.173). in this way, it has shown black color so it easily determined that generate
errors between sender or receiver.
These are TCP packet data capture in the network system where it identifies source port
become 22. It will be segmented into sequence number according to the requirement. it also
automatically adjusted as per space. The length of header is 32 bytes.
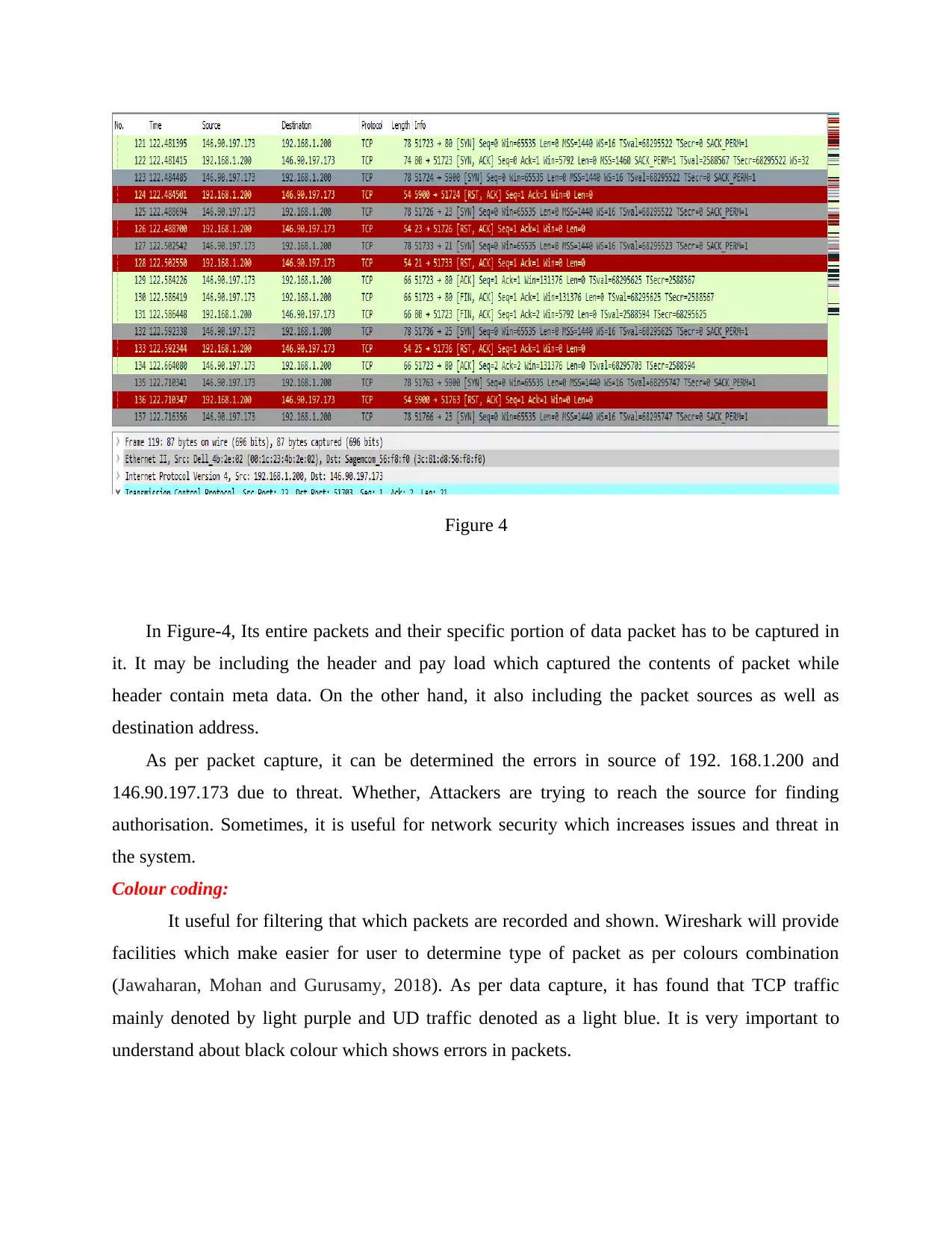
Figure 4
In Figure-4, Its entire packets and their specific portion of data packet has to be captured in
it. It may be including the header and pay load which captured the contents of packet while
header contain meta data. On the other hand, it also including the packet sources as well as
destination address.
As per packet capture, it can be determined the errors in source of 192. 168.1.200 and
146.90.197.173 due to threat. Whether, Attackers are trying to reach the source for finding
authorisation. Sometimes, it is useful for network security which increases issues and threat in
the system.
Colour coding:
It useful for filtering that which packets are recorded and shown. Wireshark will provide
facilities which make easier for user to determine type of packet as per colours combination
(Jawaharan, Mohan and Gurusamy, 2018). As per data capture, it has found that TCP traffic
mainly denoted by light purple and UD traffic denoted as a light blue. It is very important to
understand about black colour which shows errors in packets.
In Figure-4, Its entire packets and their specific portion of data packet has to be captured in
it. It may be including the header and pay load which captured the contents of packet while
header contain meta data. On the other hand, it also including the packet sources as well as
destination address.
As per packet capture, it can be determined the errors in source of 192. 168.1.200 and
146.90.197.173 due to threat. Whether, Attackers are trying to reach the source for finding
authorisation. Sometimes, it is useful for network security which increases issues and threat in
the system.
Colour coding:
It useful for filtering that which packets are recorded and shown. Wireshark will provide
facilities which make easier for user to determine type of packet as per colours combination
(Jawaharan, Mohan and Gurusamy, 2018). As per data capture, it has found that TCP traffic
mainly denoted by light purple and UD traffic denoted as a light blue. It is very important to
understand about black colour which shows errors in packets.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Wireshark is mainly representing the various combination of colours for providing different
meaning in data transmission within network system.
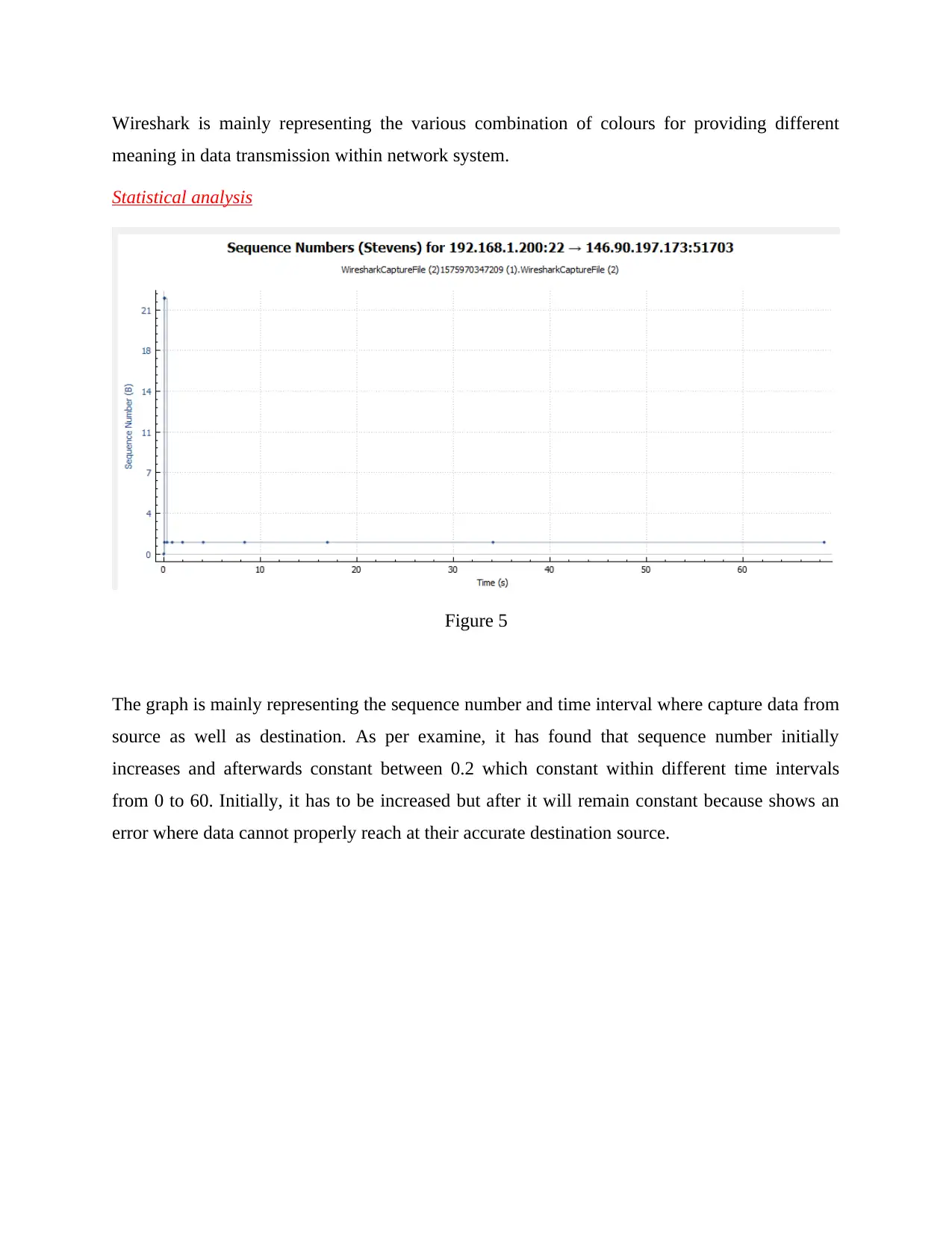
Statistical analysis
Figure 5
The graph is mainly representing the sequence number and time interval where capture data from
source as well as destination. As per examine, it has found that sequence number initially
increases and afterwards constant between 0.2 which constant within different time intervals
from 0 to 60. Initially, it has to be increased but after it will remain constant because shows an
error where data cannot properly reach at their accurate destination source.
meaning in data transmission within network system.
Statistical analysis
Figure 5
The graph is mainly representing the sequence number and time interval where capture data from
source as well as destination. As per examine, it has found that sequence number initially
increases and afterwards constant between 0.2 which constant within different time intervals
from 0 to 60. Initially, it has to be increased but after it will remain constant because shows an
error where data cannot properly reach at their accurate destination source.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
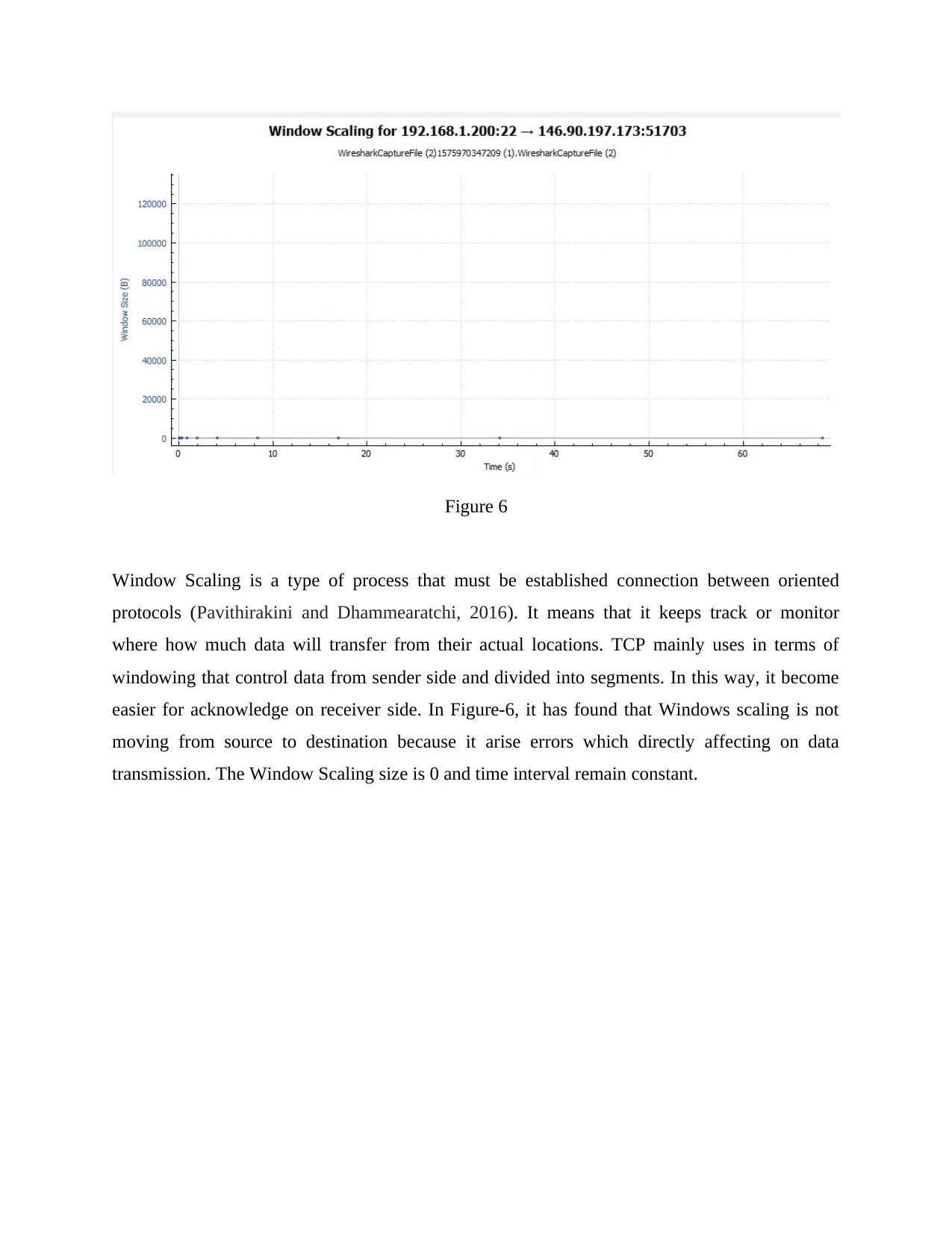
Figure 6
Window Scaling is a type of process that must be established connection between oriented
protocols (Pavithirakini and Dhammearatchi, 2016). It means that it keeps track or monitor
where how much data will transfer from their actual locations. TCP mainly uses in terms of
windowing that control data from sender side and divided into segments. In this way, it become
easier for acknowledge on receiver side. In Figure-6, it has found that Windows scaling is not
moving from source to destination because it arise errors which directly affecting on data
transmission. The Window Scaling size is 0 and time interval remain constant.
Window Scaling is a type of process that must be established connection between oriented
protocols (Pavithirakini and Dhammearatchi, 2016). It means that it keeps track or monitor
where how much data will transfer from their actual locations. TCP mainly uses in terms of
windowing that control data from sender side and divided into segments. In this way, it become
easier for acknowledge on receiver side. In Figure-6, it has found that Windows scaling is not
moving from source to destination because it arise errors which directly affecting on data
transmission. The Window Scaling size is 0 and time interval remain constant.
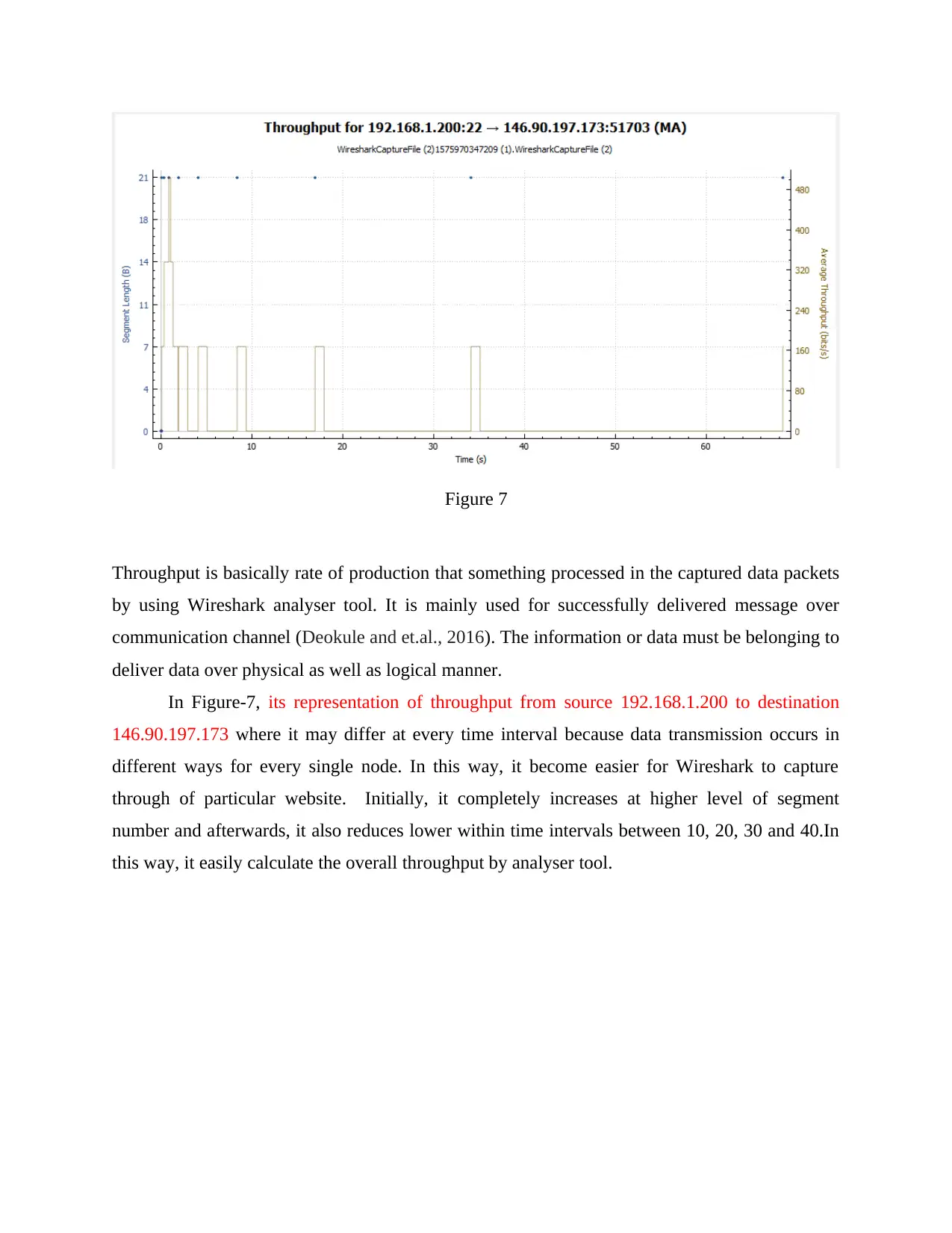
Figure 7
Throughput is basically rate of production that something processed in the captured data packets
by using Wireshark analyser tool. It is mainly used for successfully delivered message over
communication channel (Deokule and et.al., 2016). The information or data must be belonging to
deliver data over physical as well as logical manner.
In Figure-7, its representation of throughput from source 192.168.1.200 to destination
146.90.197.173 where it may differ at every time interval because data transmission occurs in
different ways for every single node. In this way, it become easier for Wireshark to capture
through of particular website. Initially, it completely increases at higher level of segment
number and afterwards, it also reduces lower within time intervals between 10, 20, 30 and 40.In
this way, it easily calculate the overall throughput by analyser tool.
Throughput is basically rate of production that something processed in the captured data packets
by using Wireshark analyser tool. It is mainly used for successfully delivered message over
communication channel (Deokule and et.al., 2016). The information or data must be belonging to
deliver data over physical as well as logical manner.
In Figure-7, its representation of throughput from source 192.168.1.200 to destination
146.90.197.173 where it may differ at every time interval because data transmission occurs in
different ways for every single node. In this way, it become easier for Wireshark to capture
through of particular website. Initially, it completely increases at higher level of segment
number and afterwards, it also reduces lower within time intervals between 10, 20, 30 and 40.In
this way, it easily calculate the overall throughput by analyser tool.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
