Cyber Security: Attacks, Threats, and Mitigation Strategies
VerifiedAdded on 2022/07/28
|1
|274
|55
Homework Assignment
AI Summary
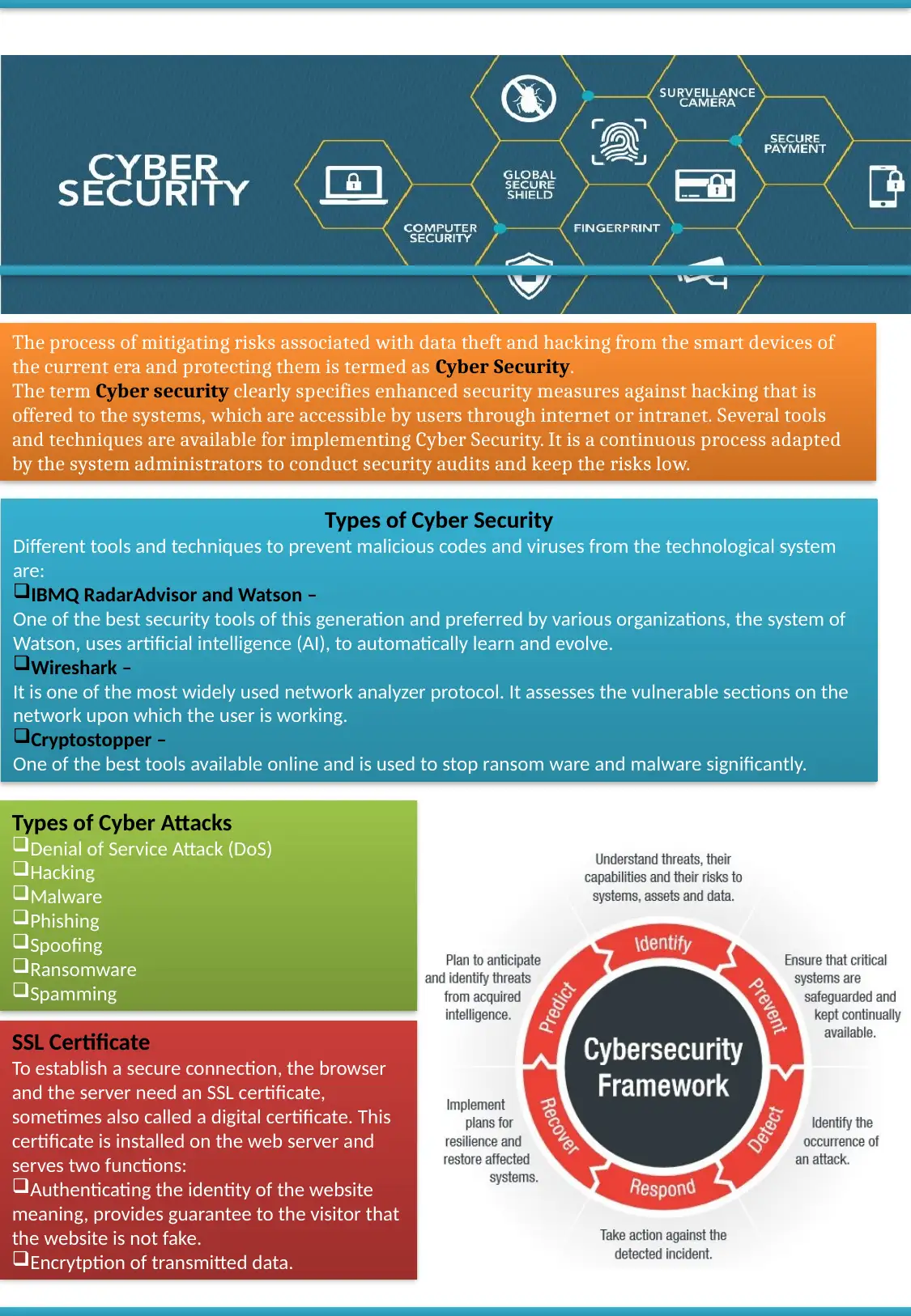
This assignment delves into the realm of cyber security, focusing on the various threats, attacks, and mitigation strategies employed to safeguard digital systems. It begins by defining cyber security and highlighting its importance in protecting against hacking and data breaches. The assignment then explores different types of cyber attacks, including Denial of Service (DoS) attacks, hacking, malware, phishing, spoofing, ransomware, and spamming. It also discusses the role of SSL certificates in establishing secure connections. Furthermore, the assignment introduces several tools and techniques used to enhance cyber security, such as IBMQ RadarAdvisor, Watson (AI-based security), and Wireshark (network analyzer), along with Cryptostoppper, a tool used to stop ransom ware and malware. The content provides a comprehensive overview of the current cyber security landscape, offering insights into both the threats and the defenses used to protect valuable data and systems. This assignment provides a good foundation for understanding key concepts and challenges in the field of cyber security.






![[object Object]](/_next/static/media/star-bottom.7253800d.svg)