Analyzing Challenges of Cyber Security in Modern Business Context
VerifiedAdded on 2020/04/01
|15
|3304
|174
Report
AI Summary
This report provides a comprehensive overview of the challenges of cyber security in the business environment. It begins by outlining the importance of cyber security and the increasing threats posed by digital advancements, including phishing, malware, and data breaches. The project objectives are to analyze these challenges and propose effective mitigation strategies. The scope encompasses both internal and external security threats, with a focus on e-commerce organizations. A literature review highlights the evolving nature of cyber threats and the need for robust security measures. The research employs both qualitative and quantitative data analysis methods, including case studies and numerical data analysis. The report examines the impact of cyber security breaches on businesses and suggests strategies for enhancing security, addressing research questions about the nature of these challenges, their effects, and recommended solutions. The limitations of the research are also acknowledged, focusing on the scope of the case studies used in the report.

Running head: CHALLENGES OF CYBER SECURITY IN BUSINESS
CHALLENGES OF CYBER SECURITY IN BUSINESS
Name of the Student:
Name of the University:
Author note:
CHALLENGES OF CYBER SECURITY IN BUSINESS
Name of the Student:
Name of the University:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1Introduction
CHALLENGES OF CYBER SECURITY IN BUSINESS
Table of Contents
Introduction......................................................................................................................................2
Project Objective.............................................................................................................................2
Project Scope...................................................................................................................................2
Literature review..............................................................................................................................3
Research Questions..........................................................................................................................6
Research Design and Methodology:................................................................................................7
Data Collection Method...............................................................................................................7
Data Analysis Method.................................................................................................................7
Research limitation..........................................................................................................................8
Time Schedule.................................................................................................................................8
Conclusion.......................................................................................................................................8
Reference.......................................................................................................................................10
Appendix........................................................................................................................................13
CHALLENGES OF CYBER SECURITY IN BUSINESS
Table of Contents
Introduction......................................................................................................................................2
Project Objective.............................................................................................................................2
Project Scope...................................................................................................................................2
Literature review..............................................................................................................................3
Research Questions..........................................................................................................................6
Research Design and Methodology:................................................................................................7
Data Collection Method...............................................................................................................7
Data Analysis Method.................................................................................................................7
Research limitation..........................................................................................................................8
Time Schedule.................................................................................................................................8
Conclusion.......................................................................................................................................8
Reference.......................................................................................................................................10
Appendix........................................................................................................................................13

2Introduction
CHALLENGES OF CYBER SECURITY IN BUSINESS
Introduction
Cyber security has become a major issue in the present day business situations. The
advancement of the technology helps to give various solutions that can solve the problems in the
business within a short time span and in a cost effective way. Most of the business organizations
are going for the digital disruptions nowadays which leads to the increased amount of using the
smart phones and other advanced digital devices. This trend is enhancing the threats from the
cyber crime. In order to mitigate the risks from the cyber security threats, the business
organizations are needed to follow some steps. The solution should be effective in nature and
will give the sustainable solutions to the business organization so that they can compete in the
business in the competitive market. The aim of this research proposal is to develop a concept
about the challenges regarding the cyber security in the business field. The paper discusses about
the various aspects of the challenges and the way to overcome those challenges so that the
organizations can hold a good position the highly competitive market.
Project Objective
The main objective of this article is to discuss about the challenges regarding the cyber
security in the business which can be applicable in the highly competitive business
environment.
Apart from that the paper also addresses the way to face those challenges .
This paper delivers the knowledge about the cyber security from the different perspective
and the ways to deal with that challenges so that the security in the business organizations
can be maintained.
CHALLENGES OF CYBER SECURITY IN BUSINESS
Introduction
Cyber security has become a major issue in the present day business situations. The
advancement of the technology helps to give various solutions that can solve the problems in the
business within a short time span and in a cost effective way. Most of the business organizations
are going for the digital disruptions nowadays which leads to the increased amount of using the
smart phones and other advanced digital devices. This trend is enhancing the threats from the
cyber crime. In order to mitigate the risks from the cyber security threats, the business
organizations are needed to follow some steps. The solution should be effective in nature and
will give the sustainable solutions to the business organization so that they can compete in the
business in the competitive market. The aim of this research proposal is to develop a concept
about the challenges regarding the cyber security in the business field. The paper discusses about
the various aspects of the challenges and the way to overcome those challenges so that the
organizations can hold a good position the highly competitive market.
Project Objective
The main objective of this article is to discuss about the challenges regarding the cyber
security in the business which can be applicable in the highly competitive business
environment.
Apart from that the paper also addresses the way to face those challenges .
This paper delivers the knowledge about the cyber security from the different perspective
and the ways to deal with that challenges so that the security in the business organizations
can be maintained.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3Introduction
CHALLENGES OF CYBER SECURITY IN BUSINESS
Project Scope
The scope of this project has great concern in today’s digital world. The security
challenges faced in the organization can be both internal and the external. The business
organizations have to handle the large amount of data in daily basis. Most of the digital
organization supports the digital disruption and this make sthe use of the technology as the
integral part of the business organization. The use of the technologies in the organizations makes
the scope of the discussing the challenges in the protection of the security and the data within the
organization.
The main objective of the project is to address the challenges regarding the cyber security
in the business organizations. The objective of this paper has a good scope to be researched as
there are many opportunities that can be evaluated in this course. The paper can contribute in the
implementation of the right security standards in the organizations as it evaluates the different
security challenges in different organizations. This evaluation will indicate the nature of the
security challenges and will specify the different ways of mitigation. The ways of evaluation of
the security challenges and the mitigation techniques are derived from the comparative studies of
the cyber security challenges in different organizations those are conducting their business
online.
Literature review
The issues regarding the cyber security has become a major concern nowadays. The
business organizations are conducting the business in both the online and offline modes. In this
case, the business organizations are concerned about the security threats in the conduction of the
online business. In order to deal with the various security threats in the online business
CHALLENGES OF CYBER SECURITY IN BUSINESS
Project Scope
The scope of this project has great concern in today’s digital world. The security
challenges faced in the organization can be both internal and the external. The business
organizations have to handle the large amount of data in daily basis. Most of the digital
organization supports the digital disruption and this make sthe use of the technology as the
integral part of the business organization. The use of the technologies in the organizations makes
the scope of the discussing the challenges in the protection of the security and the data within the
organization.
The main objective of the project is to address the challenges regarding the cyber security
in the business organizations. The objective of this paper has a good scope to be researched as
there are many opportunities that can be evaluated in this course. The paper can contribute in the
implementation of the right security standards in the organizations as it evaluates the different
security challenges in different organizations. This evaluation will indicate the nature of the
security challenges and will specify the different ways of mitigation. The ways of evaluation of
the security challenges and the mitigation techniques are derived from the comparative studies of
the cyber security challenges in different organizations those are conducting their business
online.
Literature review
The issues regarding the cyber security has become a major concern nowadays. The
business organizations are conducting the business in both the online and offline modes. In this
case, the business organizations are concerned about the security threats in the conduction of the
online business. In order to deal with the various security threats in the online business
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4Introduction
CHALLENGES OF CYBER SECURITY IN BUSINESS
organizations, the management of the organizations are hiring the cyber security experts to keep
their systems safe from the internal and external threats. This helps the companies to do business
in an cost effective way.
According to the report generated by the ACS, the threats can be of different types. The
business organizations can face the threats such as Phishing and scamming (ACS 2016). Major
security threats can also come from the activities like key logger and attacks from malware and
ransom wares. It can be said with the advancement of the technology conduction of the business
has become easier along with that it also increases the security issues in the organizations
(Herrera, Ron and Rabadão 2017). The use of the cloud computing architecture and the use of
IoT in the business organizations have increased the productivity and the creativity of the
technological and business companies (Li et al.2012). However, the use of these advanced
technologies has increased the threats for the cyber security. The advancement of the technology
has enhanced complexity of the threats in the security (Sadeghi, Wachsmann and Waidner 2015).
The business organizations are responsible for the maintaining the security of the data. In case, if
the system security in the organization get breached , the whole situation will turn against the
business organizations.
The working of the various types of the cyber security threats is different. The control of
the system can be done by the cyber criminals through the use of Bonets. The keys which are
pressed can be recorded using the key loggers and the key logging information can be used by
the criminals to enter in to the system (Babate et al. 2015). Malwares are the malicious programs
which acts as a normal application in the system but secretly collects the user data from the
system and the information can be accessed by the cyber criminals through a specific link
(Bradley 2017). The most common threats faced by the business organizations are the virus and
CHALLENGES OF CYBER SECURITY IN BUSINESS
organizations, the management of the organizations are hiring the cyber security experts to keep
their systems safe from the internal and external threats. This helps the companies to do business
in an cost effective way.
According to the report generated by the ACS, the threats can be of different types. The
business organizations can face the threats such as Phishing and scamming (ACS 2016). Major
security threats can also come from the activities like key logger and attacks from malware and
ransom wares. It can be said with the advancement of the technology conduction of the business
has become easier along with that it also increases the security issues in the organizations
(Herrera, Ron and Rabadão 2017). The use of the cloud computing architecture and the use of
IoT in the business organizations have increased the productivity and the creativity of the
technological and business companies (Li et al.2012). However, the use of these advanced
technologies has increased the threats for the cyber security. The advancement of the technology
has enhanced complexity of the threats in the security (Sadeghi, Wachsmann and Waidner 2015).
The business organizations are responsible for the maintaining the security of the data. In case, if
the system security in the organization get breached , the whole situation will turn against the
business organizations.
The working of the various types of the cyber security threats is different. The control of
the system can be done by the cyber criminals through the use of Bonets. The keys which are
pressed can be recorded using the key loggers and the key logging information can be used by
the criminals to enter in to the system (Babate et al. 2015). Malwares are the malicious programs
which acts as a normal application in the system but secretly collects the user data from the
system and the information can be accessed by the cyber criminals through a specific link
(Bradley 2017). The most common threats faced by the business organizations are the virus and

5Introduction
CHALLENGES OF CYBER SECURITY IN BUSINESS
Trojans. The main specification of these kinds of threats is that they can spread from one system
through another through the programs and the links (Goutam 2015). These types of threats can
destroy the system and make the loss of the data in a significant way.
The main problem in the cyber security is that it causes the negative effect on the
business organizations. The threat regarding the cyber security has become o e of the major
problem nowadays according to the government of the United States ( Amit and Zott 2012).. The
importance of the cyber security lies on the ability to protect information and the raw data of the
organizations from the unauthorized access (Fischer 2016). Almost all the organizations in the
world have been affected negatively from the violation of the cyber security by the unauthorized
entity (Tisdale 2015). The importance of the cyber security has increased as almost all the
sectors of the business are dependent on the digital technology and internet in order to do the
business.
Literature gap:
Various studies has discussed about the different threats that can be encountered by the
online organizations during doing the business online (Harris and Patten 2014). The introduction
of different security threats has been discussed by some papers. Apart from that the impact of the
violation of the cyber security has been well explained and importance of the cyber security
experts and the need for the cyber security has been well explained in the journals and reports
maintained in the literature review. However, there is a gap in those research as no discussion
has been conducted about the challenges the organizations can face from the cyber security and
the ways to mitigate those threats (Jeschke et al. 2017). The nature of the previous papers are
CHALLENGES OF CYBER SECURITY IN BUSINESS
Trojans. The main specification of these kinds of threats is that they can spread from one system
through another through the programs and the links (Goutam 2015). These types of threats can
destroy the system and make the loss of the data in a significant way.
The main problem in the cyber security is that it causes the negative effect on the
business organizations. The threat regarding the cyber security has become o e of the major
problem nowadays according to the government of the United States ( Amit and Zott 2012).. The
importance of the cyber security lies on the ability to protect information and the raw data of the
organizations from the unauthorized access (Fischer 2016). Almost all the organizations in the
world have been affected negatively from the violation of the cyber security by the unauthorized
entity (Tisdale 2015). The importance of the cyber security has increased as almost all the
sectors of the business are dependent on the digital technology and internet in order to do the
business.
Literature gap:
Various studies has discussed about the different threats that can be encountered by the
online organizations during doing the business online (Harris and Patten 2014). The introduction
of different security threats has been discussed by some papers. Apart from that the impact of the
violation of the cyber security has been well explained and importance of the cyber security
experts and the need for the cyber security has been well explained in the journals and reports
maintained in the literature review. However, there is a gap in those research as no discussion
has been conducted about the challenges the organizations can face from the cyber security and
the ways to mitigate those threats (Jeschke et al. 2017). The nature of the previous papers are
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6Introduction
CHALLENGES OF CYBER SECURITY IN BUSINESS
explicit. The objective of the current paper is to present a knowledgeable discussion about the
challenges of the cyber security in the business filed and the ways to mitigate those challenges.
Opportunities:
The papers has helped in finding the different aspects of the security threats applicable
for the various technologies (Fonseca and Rosen 2017). These information has made an
opportunity to research further regarding the challenges caused by the security threats in the
organization conducting the business online (Arabo 2015). Apart from that the problems faced
by the various organizations have made a way to find out the problems and the possible loss the
organization can face due to the violation of the cyber security. This leads to the way for finding
the ways to dissolve the challenges and the possible ways for mitigation of the damage.
Hypothesis:
H1: There are many potential threats regarding the cyber security and the ways for the mitigation
of those threats are affecting the business of the organizations.
H2: There are no potential threats of the regarding the cyber security and it is not affecting the
business of the organizations.
Research Questions
Primary Question:
What are the challenges in maintaining the cyber security in the organizations?
Secondary Questions:
Question 1:What are the different aspects of these challenges?
CHALLENGES OF CYBER SECURITY IN BUSINESS
explicit. The objective of the current paper is to present a knowledgeable discussion about the
challenges of the cyber security in the business filed and the ways to mitigate those challenges.
Opportunities:
The papers has helped in finding the different aspects of the security threats applicable
for the various technologies (Fonseca and Rosen 2017). These information has made an
opportunity to research further regarding the challenges caused by the security threats in the
organization conducting the business online (Arabo 2015). Apart from that the problems faced
by the various organizations have made a way to find out the problems and the possible loss the
organization can face due to the violation of the cyber security. This leads to the way for finding
the ways to dissolve the challenges and the possible ways for mitigation of the damage.
Hypothesis:
H1: There are many potential threats regarding the cyber security and the ways for the mitigation
of those threats are affecting the business of the organizations.
H2: There are no potential threats of the regarding the cyber security and it is not affecting the
business of the organizations.
Research Questions
Primary Question:
What are the challenges in maintaining the cyber security in the organizations?
Secondary Questions:
Question 1:What are the different aspects of these challenges?
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7Introduction
CHALLENGES OF CYBER SECURITY IN BUSINESS
Question 2: How do these challenges effect then business organizations?
Question 3: What are recommended ways to address these challenges and mitigate the negative
effect on the business organizations?
Research Design and Methodology:
Data Collection Method
There are two types of data collection method –primary data collection and secondary
data collection. The secondary data collection includes the evaluation of the data those are
already published. In this article secondary data will be used in order to determine the challenges
of the cyber security and the impacts of the threats from the cyber security in the organization.
Data Analysis Method
The data analysis method can be of two types- qualitative and quantitative. Qualitative
data analysis includes the examination of the information from the well researched articles and
the discussion (Shaik, Abdullah and Klein 2017). On the other hand the quantitative approach of
data analysis indicates the systematic approach towards the research question through the
analysis of the numerical and statistical data. In this paper the combination of these two analysis
will be used to address the research questions.
Under the qualitative analysis section the comparison of the three e-commerce
organizations is done. The analysis of the threats the three companies has been faced and the
impact of those threats for those companies are examined in a detailed process (Sajid, Abbas
and Saleem 2016). It has been seen that one common thing between the three organizations is
that , they has been attacked by the malware. Due to this attack all the three companies has faced
CHALLENGES OF CYBER SECURITY IN BUSINESS
Question 2: How do these challenges effect then business organizations?
Question 3: What are recommended ways to address these challenges and mitigate the negative
effect on the business organizations?
Research Design and Methodology:
Data Collection Method
There are two types of data collection method –primary data collection and secondary
data collection. The secondary data collection includes the evaluation of the data those are
already published. In this article secondary data will be used in order to determine the challenges
of the cyber security and the impacts of the threats from the cyber security in the organization.
Data Analysis Method
The data analysis method can be of two types- qualitative and quantitative. Qualitative
data analysis includes the examination of the information from the well researched articles and
the discussion (Shaik, Abdullah and Klein 2017). On the other hand the quantitative approach of
data analysis indicates the systematic approach towards the research question through the
analysis of the numerical and statistical data. In this paper the combination of these two analysis
will be used to address the research questions.
Under the qualitative analysis section the comparison of the three e-commerce
organizations is done. The analysis of the threats the three companies has been faced and the
impact of those threats for those companies are examined in a detailed process (Sajid, Abbas
and Saleem 2016). It has been seen that one common thing between the three organizations is
that , they has been attacked by the malware. Due to this attack all the three companies has faced

8Introduction
CHALLENGES OF CYBER SECURITY IN BUSINESS
a loss of great revenue. The occurrence of this attack has been found out due to the lack of cyber
awareness among the employees of the organization and unintentional use of the malicious links.
It has been seen that one of the companies has become the victim of the key logging. In this case
the possible culprit may be the someone inside the organization.
Under the quantitative analysis section the charts are use and the percentage of the loss
due to the different cyber security challenges has been mentioned through the use of numerical
data.
Research limitation
The research is limited between the comparison of the three e-commerce organizations.
The security challenge discussed in this paper is limited to the attacks of different malicious
entities in the websites of the organizations. However, the data breaches and the damage of the
system can be happen to any organization of different fields like banking and marketing
organizations. The threats and the effects of the cyber attack may have a different impacts on
those organizations. The limit of this research is that the research has not done on the diverse
company profiles. The findings are restricted to the e-commerce websites and denotes the
challenges in the business regarding cyber security along with the possible way of mitigation.
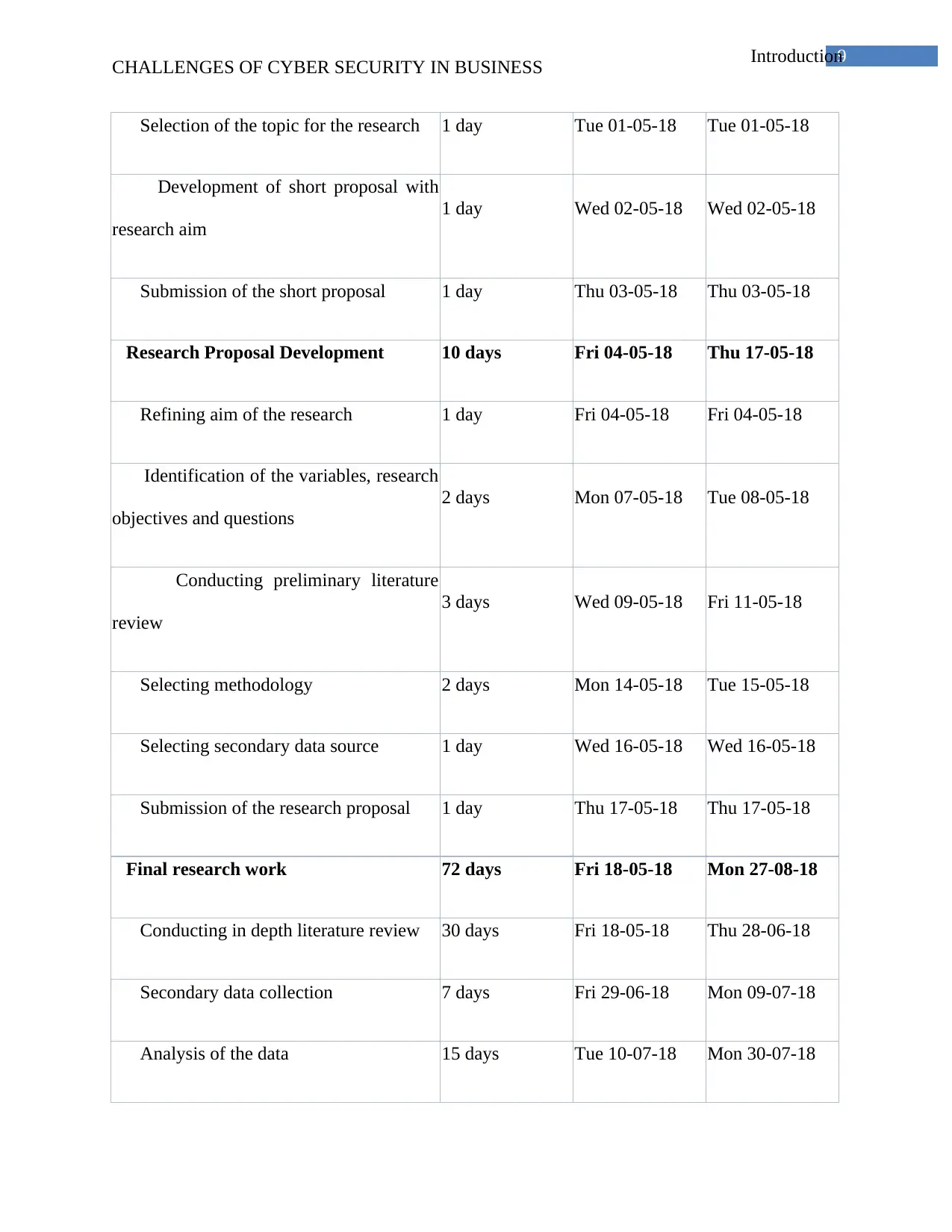
Time Schedule
Task Name Duration Start Finish
Research Project 85 days Tue 01-05-18 Mon 27-08-18
Topic selection 3 days Tue 01-05-18 Thu 03-05-18
CHALLENGES OF CYBER SECURITY IN BUSINESS
a loss of great revenue. The occurrence of this attack has been found out due to the lack of cyber
awareness among the employees of the organization and unintentional use of the malicious links.
It has been seen that one of the companies has become the victim of the key logging. In this case
the possible culprit may be the someone inside the organization.
Under the quantitative analysis section the charts are use and the percentage of the loss
due to the different cyber security challenges has been mentioned through the use of numerical
data.
Research limitation
The research is limited between the comparison of the three e-commerce organizations.
The security challenge discussed in this paper is limited to the attacks of different malicious
entities in the websites of the organizations. However, the data breaches and the damage of the
system can be happen to any organization of different fields like banking and marketing
organizations. The threats and the effects of the cyber attack may have a different impacts on
those organizations. The limit of this research is that the research has not done on the diverse
company profiles. The findings are restricted to the e-commerce websites and denotes the
challenges in the business regarding cyber security along with the possible way of mitigation.
Time Schedule
Task Name Duration Start Finish
Research Project 85 days Tue 01-05-18 Mon 27-08-18
Topic selection 3 days Tue 01-05-18 Thu 03-05-18
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9Introduction
CHALLENGES OF CYBER SECURITY IN BUSINESS
Selection of the topic for the research 1 day Tue 01-05-18 Tue 01-05-18
Development of short proposal with
research aim
1 day Wed 02-05-18 Wed 02-05-18
Submission of the short proposal 1 day Thu 03-05-18 Thu 03-05-18
Research Proposal Development 10 days Fri 04-05-18 Thu 17-05-18
Refining aim of the research 1 day Fri 04-05-18 Fri 04-05-18
Identification of the variables, research
objectives and questions
2 days Mon 07-05-18 Tue 08-05-18
Conducting preliminary literature
review
3 days Wed 09-05-18 Fri 11-05-18
Selecting methodology 2 days Mon 14-05-18 Tue 15-05-18
Selecting secondary data source 1 day Wed 16-05-18 Wed 16-05-18
Submission of the research proposal 1 day Thu 17-05-18 Thu 17-05-18
Final research work 72 days Fri 18-05-18 Mon 27-08-18
Conducting in depth literature review 30 days Fri 18-05-18 Thu 28-06-18
Secondary data collection 7 days Fri 29-06-18 Mon 09-07-18
Analysis of the data 15 days Tue 10-07-18 Mon 30-07-18
CHALLENGES OF CYBER SECURITY IN BUSINESS
Selection of the topic for the research 1 day Tue 01-05-18 Tue 01-05-18
Development of short proposal with
research aim
1 day Wed 02-05-18 Wed 02-05-18
Submission of the short proposal 1 day Thu 03-05-18 Thu 03-05-18
Research Proposal Development 10 days Fri 04-05-18 Thu 17-05-18
Refining aim of the research 1 day Fri 04-05-18 Fri 04-05-18
Identification of the variables, research
objectives and questions
2 days Mon 07-05-18 Tue 08-05-18
Conducting preliminary literature
review
3 days Wed 09-05-18 Fri 11-05-18
Selecting methodology 2 days Mon 14-05-18 Tue 15-05-18
Selecting secondary data source 1 day Wed 16-05-18 Wed 16-05-18
Submission of the research proposal 1 day Thu 17-05-18 Thu 17-05-18
Final research work 72 days Fri 18-05-18 Mon 27-08-18
Conducting in depth literature review 30 days Fri 18-05-18 Thu 28-06-18
Secondary data collection 7 days Fri 29-06-18 Mon 09-07-18
Analysis of the data 15 days Tue 10-07-18 Mon 30-07-18
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10Introduction
CHALLENGES OF CYBER SECURITY IN BUSINESS
Drawing conclusion from the data
analysis
7 days Tue 31-07-18 Wed 08-08-18
Providing recommendations 2 days Thu 09-08-18 Fri 10-08-18
Preparing the final report 10 days Mon 13-08-18 Fri 24-08-18
Submission of the research project 1 day Mon 27-08-18 Mon 27-08-18
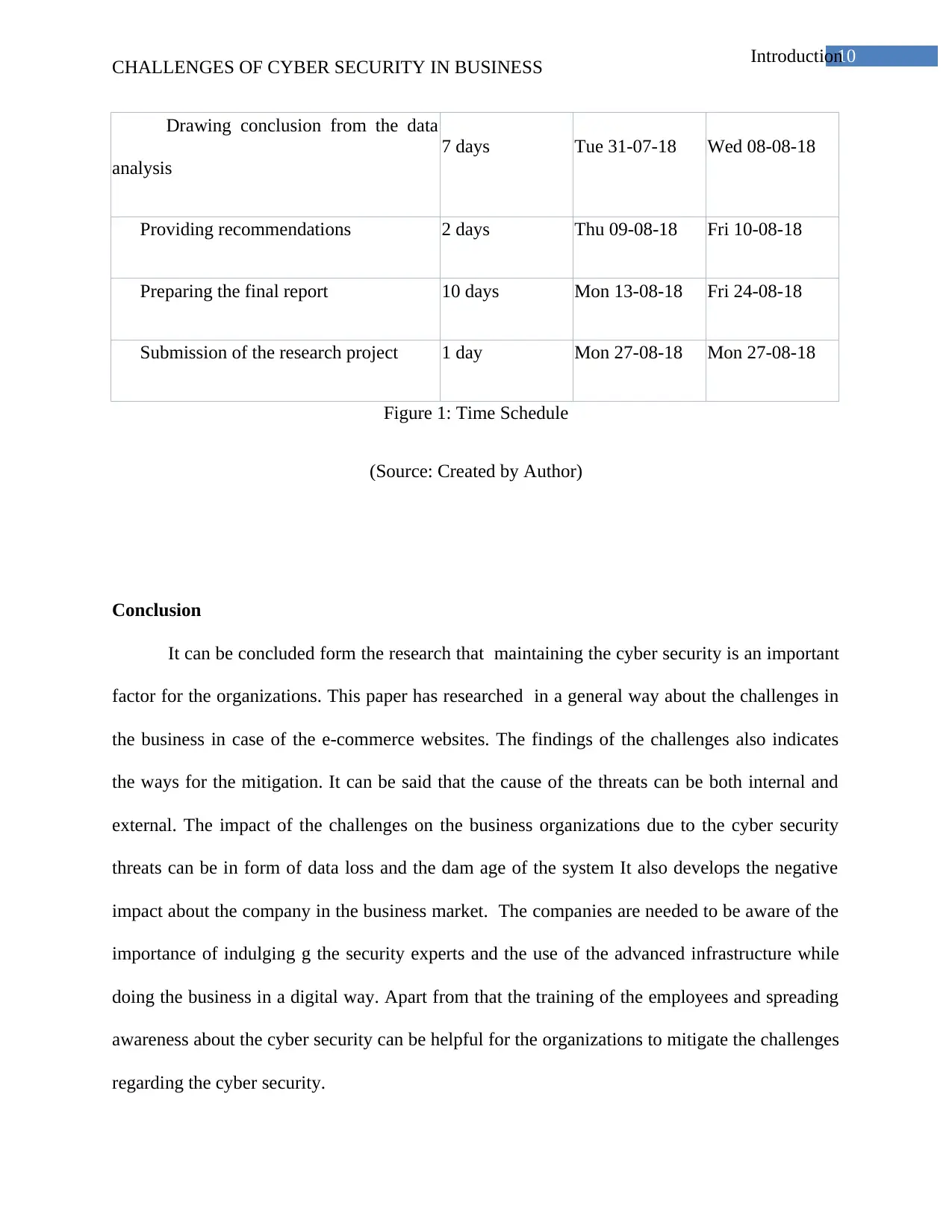
Figure 1: Time Schedule
(Source: Created by Author)
Conclusion
It can be concluded form the research that maintaining the cyber security is an important
factor for the organizations. This paper has researched in a general way about the challenges in
the business in case of the e-commerce websites. The findings of the challenges also indicates
the ways for the mitigation. It can be said that the cause of the threats can be both internal and
external. The impact of the challenges on the business organizations due to the cyber security
threats can be in form of data loss and the dam age of the system It also develops the negative
impact about the company in the business market. The companies are needed to be aware of the
importance of indulging g the security experts and the use of the advanced infrastructure while
doing the business in a digital way. Apart from that the training of the employees and spreading
awareness about the cyber security can be helpful for the organizations to mitigate the challenges
regarding the cyber security.
CHALLENGES OF CYBER SECURITY IN BUSINESS
Drawing conclusion from the data
analysis
7 days Tue 31-07-18 Wed 08-08-18
Providing recommendations 2 days Thu 09-08-18 Fri 10-08-18
Preparing the final report 10 days Mon 13-08-18 Fri 24-08-18
Submission of the research project 1 day Mon 27-08-18 Mon 27-08-18
Figure 1: Time Schedule
(Source: Created by Author)
Conclusion
It can be concluded form the research that maintaining the cyber security is an important
factor for the organizations. This paper has researched in a general way about the challenges in
the business in case of the e-commerce websites. The findings of the challenges also indicates
the ways for the mitigation. It can be said that the cause of the threats can be both internal and
external. The impact of the challenges on the business organizations due to the cyber security
threats can be in form of data loss and the dam age of the system It also develops the negative
impact about the company in the business market. The companies are needed to be aware of the
importance of indulging g the security experts and the use of the advanced infrastructure while
doing the business in a digital way. Apart from that the training of the employees and spreading
awareness about the cyber security can be helpful for the organizations to mitigate the challenges
regarding the cyber security.

11Introduction
CHALLENGES OF CYBER SECURITY IN BUSINESS
Reference
Arabo, A., 2015. Cyber security challenges within the connected home ecosystem
futures. Procedia Computer Science, 61, pp.227-232.
Sajid, A., Abbas, H. and Saleem, K., 2016. Cloud-assisted iot-based scada systems security: A
review of the state of the art and future challenges. IEEE Access, 4, pp.1375-1384.
Tisdale, S.M., 2015. Cybersecurity: Challenges from a Systems, Complexity, Knowledge
Management and Business Intelligence Perspective. Issues in Information Systems, 16(3).
Jeschke, S., Brecher, C., Meisen, T., Özdemir, D. and Eschert, T., 2017. Industrial internet of
things and cyber manufacturing systems. In Industrial Internet of Things (pp. 3-19). Springer,
Cham.
Abomhara, M., 2015. Cyber security and the internet of things: vulnerabilities, threats, intruders
and attacks. Journal of Cyber Security and Mobility, 4(1), pp.65-88.
Fonseca, B. and Rosen, J.D., 2017. Cybersecurity in the US: Major Trends and Challenges.
In The New US Security Agenda (pp. 87-106). Palgrave Macmillan, Cham.
ACS (2016). Cybersecurity – Threats Challenges Opportunities [Online]. Available at:
https://www.acs.org.au/content/dam/acs/acs-publications/ACS_Cybersecurity_Guide.pdf
[Accessed on 25 April 2018].
CHALLENGES OF CYBER SECURITY IN BUSINESS
Reference
Arabo, A., 2015. Cyber security challenges within the connected home ecosystem
futures. Procedia Computer Science, 61, pp.227-232.
Sajid, A., Abbas, H. and Saleem, K., 2016. Cloud-assisted iot-based scada systems security: A
review of the state of the art and future challenges. IEEE Access, 4, pp.1375-1384.
Tisdale, S.M., 2015. Cybersecurity: Challenges from a Systems, Complexity, Knowledge
Management and Business Intelligence Perspective. Issues in Information Systems, 16(3).
Jeschke, S., Brecher, C., Meisen, T., Özdemir, D. and Eschert, T., 2017. Industrial internet of
things and cyber manufacturing systems. In Industrial Internet of Things (pp. 3-19). Springer,
Cham.
Abomhara, M., 2015. Cyber security and the internet of things: vulnerabilities, threats, intruders
and attacks. Journal of Cyber Security and Mobility, 4(1), pp.65-88.
Fonseca, B. and Rosen, J.D., 2017. Cybersecurity in the US: Major Trends and Challenges.
In The New US Security Agenda (pp. 87-106). Palgrave Macmillan, Cham.
ACS (2016). Cybersecurity – Threats Challenges Opportunities [Online]. Available at:
https://www.acs.org.au/content/dam/acs/acs-publications/ACS_Cybersecurity_Guide.pdf
[Accessed on 25 April 2018].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





