Cyber Security Analysis: NIST Framework and Infrastructure Assessment
VerifiedAdded on 2022/12/22
|11
|1515
|26
Homework Assignment
AI Summary
This cyber security assignment comprehensively addresses key concepts and practical applications within the field. The solution begins by defining the National Institute of Standards and Technology (NIST) cybersecurity framework, explaining its functions, and illustrating how it aids organizations in mitigating cyber threats. It then provides detailed definitions of essential cyber security terminologies, including information security, incident response standards, threat actors, threat vectors, threat goals, access controls, firewall, gateway, botnets, the cyber kill chain, IAM, and IoT devices. The assignment continues with an analysis of password strength and an evaluation of an office infrastructure, identifying vulnerabilities and proposing solutions such as installing antivirus software. Finally, it emphasizes the importance of a professional cyber security officer for managing and securing IT infrastructure, protecting data, and establishing robust security policies. The document is a student-contributed solution to the assignment published on Desklib, a platform for AI-based study tools.

Cyber security
1
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
TASK 1............................................................................................................................................3
TASK 2............................................................................................................................................3
TASK 3............................................................................................................................................3
REFERENCES................................................................................................................................5
2
TASK 1............................................................................................................................................3
TASK 2............................................................................................................................................3
TASK 3............................................................................................................................................3
REFERENCES................................................................................................................................5
2

TASK 1
1.1 What is the National Institute of Standards and Technology (NIST) cyber security framework and
what are its functions? How can it assist organisations to protect themselves from cyber threats?
(max 150 words)
It is a framework of policy of computer security which consists of guidelines that how private
companies in US can enhance security. Also, it enables organisation to detected, prevent and
respond to cyber attacks (El Mrabet and et.al., 2018). They are set of practices, standards and
recommendations which help companies to improve its cyber security measures. Its 5 functions
are defined as below ;
Identify – this enable companies to manage their cyber security risk to people, data, etc.
Protect- it outline safeguard to ensure delivery of infrastructure services.
Detect- it lay down activities to find out risk of cyber security event.
Respond- in this relevant measures are taken to detect cyber security incident.
Recover – the activities by which services that are impaired during event is restored.
It assist organisation to follow framework and guidelines to protect their network from
attacks and take relevant measures to improve it.
1.2 Define/explain each of the following terminologies in your own words: (max 50 words each)
Information Security- it refers to practice in order to prevent, access, use, record, info that is
being shared. Basically, it means to prevent data and info from unauthorized access and maintain
its confidentiality.
Incident Response Standards- This is process which through which incident is detected and
responded by organizations in cyber security. There are 4 stages in it that are preparation,
detection, containment and recovery. The NIST has set this framework.
Threat Actors- they are group, individual, states, etc. whose main purpose is to take advantage of
security or technology in order to gain access of confidential data or info from network, device,
etc. for example- hackers, cyber criminals, state actor, etc. (Gunduz and Das 2020)
3
1.1 What is the National Institute of Standards and Technology (NIST) cyber security framework and
what are its functions? How can it assist organisations to protect themselves from cyber threats?
(max 150 words)
It is a framework of policy of computer security which consists of guidelines that how private
companies in US can enhance security. Also, it enables organisation to detected, prevent and
respond to cyber attacks (El Mrabet and et.al., 2018). They are set of practices, standards and
recommendations which help companies to improve its cyber security measures. Its 5 functions
are defined as below ;
Identify – this enable companies to manage their cyber security risk to people, data, etc.
Protect- it outline safeguard to ensure delivery of infrastructure services.
Detect- it lay down activities to find out risk of cyber security event.
Respond- in this relevant measures are taken to detect cyber security incident.
Recover – the activities by which services that are impaired during event is restored.
It assist organisation to follow framework and guidelines to protect their network from
attacks and take relevant measures to improve it.
1.2 Define/explain each of the following terminologies in your own words: (max 50 words each)
Information Security- it refers to practice in order to prevent, access, use, record, info that is
being shared. Basically, it means to prevent data and info from unauthorized access and maintain
its confidentiality.
Incident Response Standards- This is process which through which incident is detected and
responded by organizations in cyber security. There are 4 stages in it that are preparation,
detection, containment and recovery. The NIST has set this framework.
Threat Actors- they are group, individual, states, etc. whose main purpose is to take advantage of
security or technology in order to gain access of confidential data or info from network, device,
etc. for example- hackers, cyber criminals, state actor, etc. (Gunduz and Das 2020)
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Threat Vectors- It defines a path or way by which cyber criminals gain access from 1 or 6 routes
into computer system. This is done by exploiting route vulnerability. Here, 6 main routes are e
mail, user, network, mobile, remote access and web application.
Threat Goals- It is goal of attacker which want to be accomplished by compromising with
system. The goal can be access info, obtain user id and password, etc. the threat goals depends
on need of attacker.
Logical access control- They are those controls that either prevent or allow access to resources
once a user's identity already has been established. It only allow user to gain access of control to
perform their duties (Lallie and et.al., 2021)
Physical access control- It is the restriction of access to a physical space within organization. The
access can be either in room, building, IT asset, etc. Also, it keeps track record of who has
entered or exit in it.
Firewall- It is a network security device that monitors and filters incoming and outgoing network
traffic based on an organization's security policies. Basically, it is barrier between internet and
private network. Also, it blocks unnecessary traffic to be entered into network.
Gateway- It is network node which connect two network that are having different transmission
protocols. They are entry and exit points in network through which data is passed and as per
gateway route. It simplify network connection into one device.
Botnets- A botnet is internet connected devices that runs on one or more bots. Botnets perform
distributed denial of service attacks, steal data, send spam, and allow the attacker to access the
device and its connection.
Cyber Kill chain- they are series of steps that trace stages of a cyberattack from the early
reconnaissance stages to the exfiltration of data. It helps us understand and combat ransomware,
security breaches, and advanced persistent attacks (Srinivas and et.al., 2019).
IAM- It defines and manage the roles and access privileges of individual network users and the
circumstances in which users are granted privileges. It provide digital identity to one individual
one time.
4
into computer system. This is done by exploiting route vulnerability. Here, 6 main routes are e
mail, user, network, mobile, remote access and web application.
Threat Goals- It is goal of attacker which want to be accomplished by compromising with
system. The goal can be access info, obtain user id and password, etc. the threat goals depends
on need of attacker.
Logical access control- They are those controls that either prevent or allow access to resources
once a user's identity already has been established. It only allow user to gain access of control to
perform their duties (Lallie and et.al., 2021)
Physical access control- It is the restriction of access to a physical space within organization. The
access can be either in room, building, IT asset, etc. Also, it keeps track record of who has
entered or exit in it.
Firewall- It is a network security device that monitors and filters incoming and outgoing network
traffic based on an organization's security policies. Basically, it is barrier between internet and
private network. Also, it blocks unnecessary traffic to be entered into network.
Gateway- It is network node which connect two network that are having different transmission
protocols. They are entry and exit points in network through which data is passed and as per
gateway route. It simplify network connection into one device.
Botnets- A botnet is internet connected devices that runs on one or more bots. Botnets perform
distributed denial of service attacks, steal data, send spam, and allow the attacker to access the
device and its connection.
Cyber Kill chain- they are series of steps that trace stages of a cyberattack from the early
reconnaissance stages to the exfiltration of data. It helps us understand and combat ransomware,
security breaches, and advanced persistent attacks (Srinivas and et.al., 2019).
IAM- It defines and manage the roles and access privileges of individual network users and the
circumstances in which users are granted privileges. It provide digital identity to one individual
one time.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
IoT Devices- They are wireless sensors, software, etc. that is attached to particular object which
operate through internet. This allow in transfer of data via internet from object without any
human intervention. The entire device works on remote access.
One IoT Example- Home security is IOT device that is completely based on smart secure home.
It include security alarm CCTV camera, etc. which is connected to mobile.
TASK 2
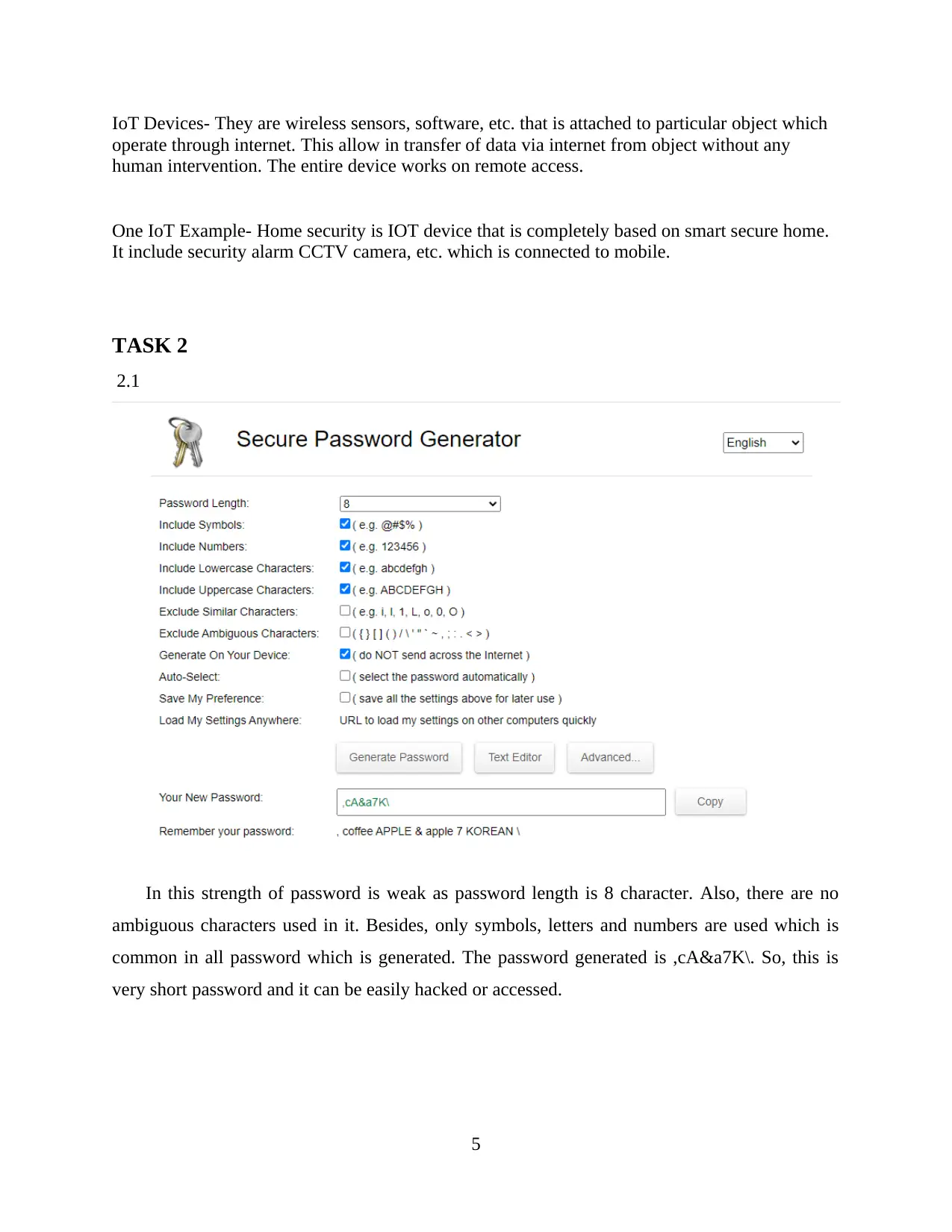
2.1
In this strength of password is weak as password length is 8 character. Also, there are no
ambiguous characters used in it. Besides, only symbols, letters and numbers are used which is
common in all password which is generated. The password generated is ,cA&a7K\. So, this is
very short password and it can be easily hacked or accessed.
5
operate through internet. This allow in transfer of data via internet from object without any
human intervention. The entire device works on remote access.
One IoT Example- Home security is IOT device that is completely based on smart secure home.
It include security alarm CCTV camera, etc. which is connected to mobile.
TASK 2
2.1
In this strength of password is weak as password length is 8 character. Also, there are no
ambiguous characters used in it. Besides, only symbols, letters and numbers are used which is
common in all password which is generated. The password generated is ,cA&a7K\. So, this is
very short password and it can be easily hacked or accessed.
5
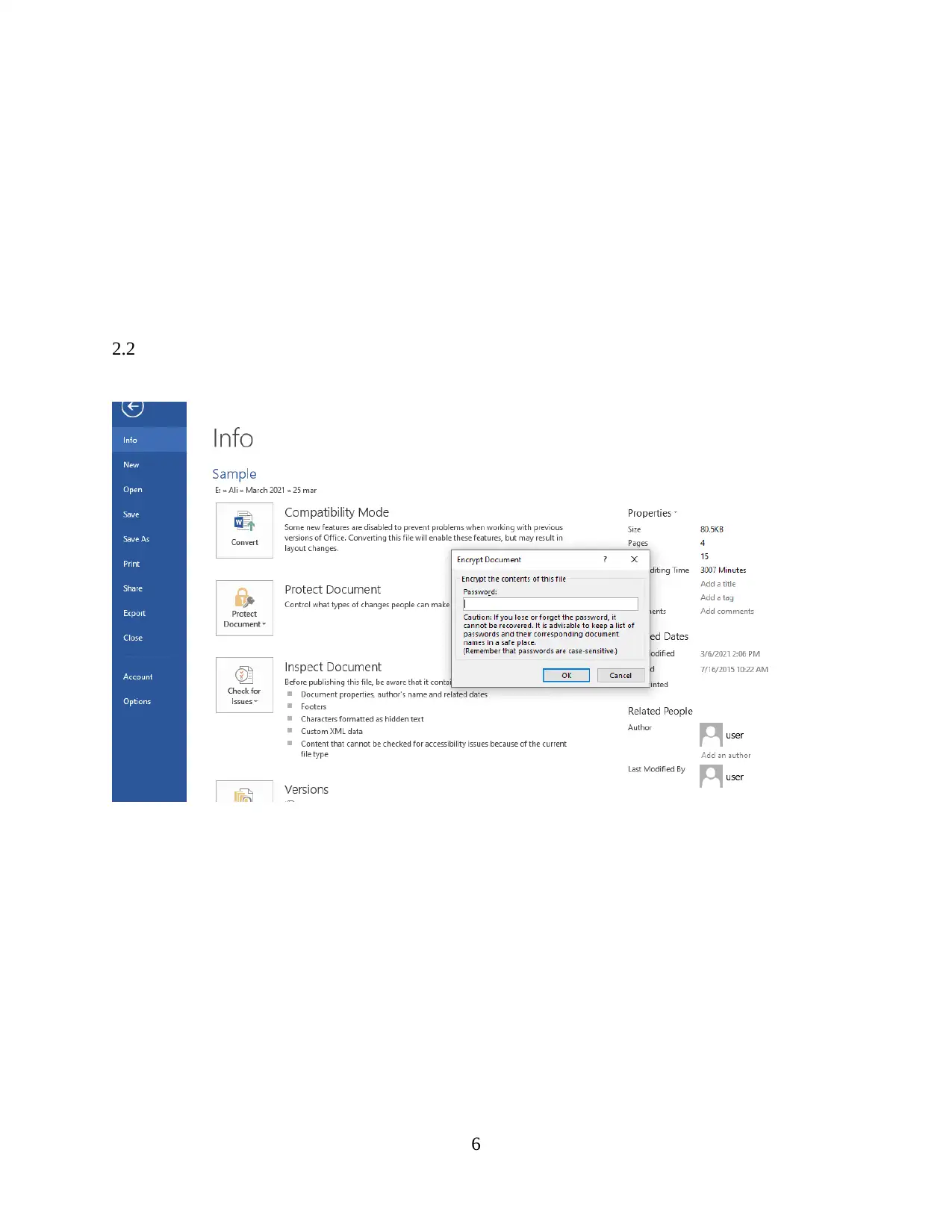
2.2
6
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
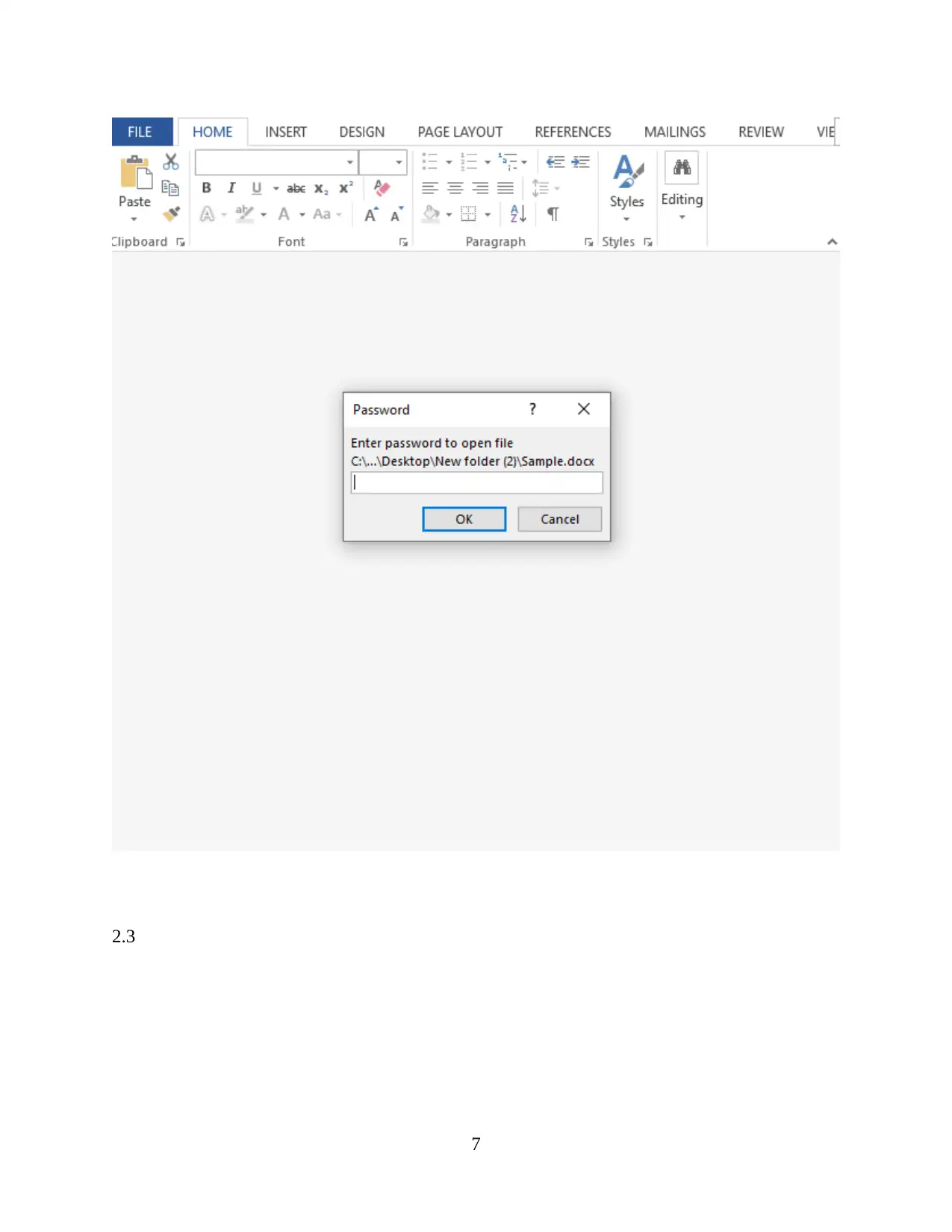
2.3
7
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TASK 3
3.1 A) Define how the components of WIDGET’S infrastructure in relation to data, networks,
machines, users and applications are interconnected with each other.
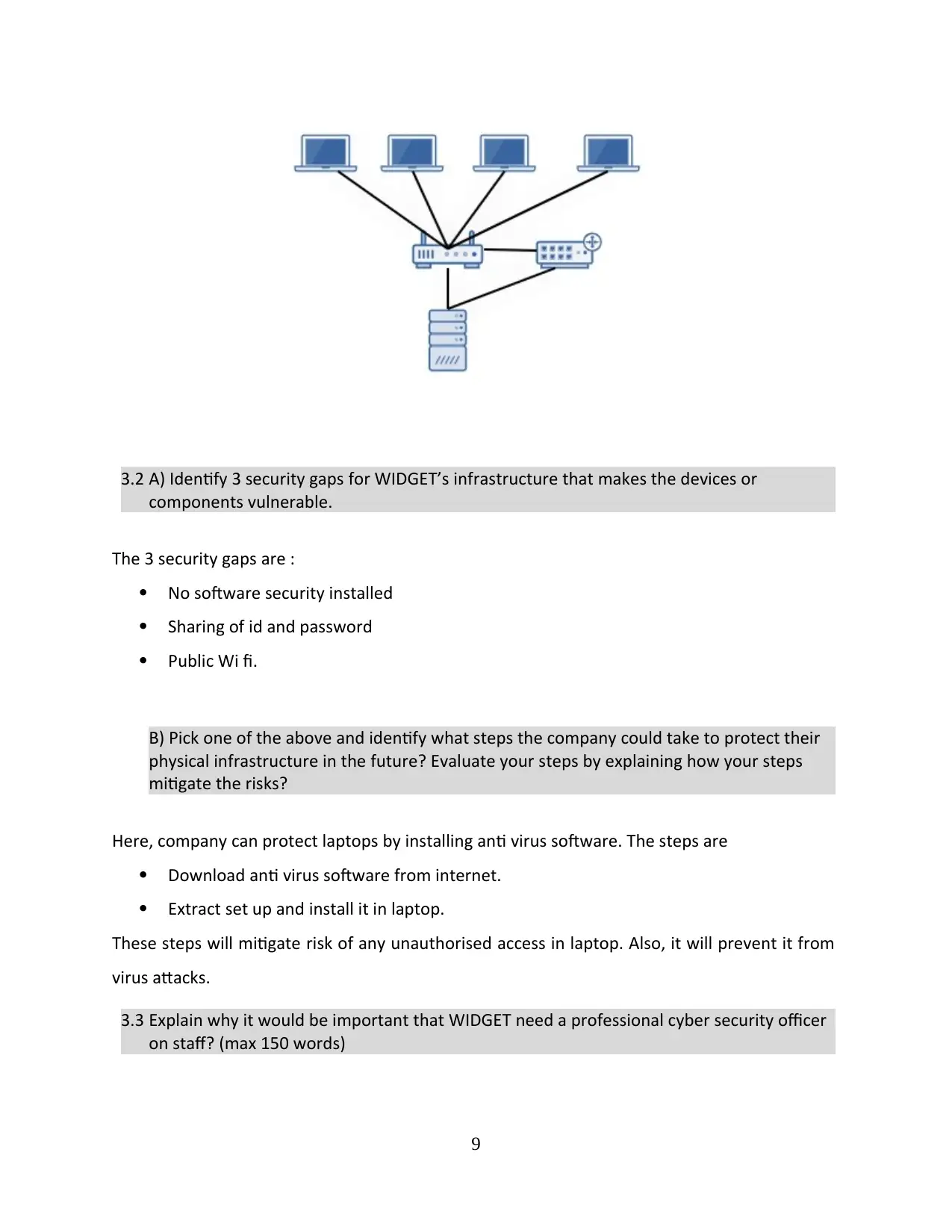
Here, it is identified that company staff use laptops which are connected through Wi fi. Also,
they are provided access from Netgear 24 port gigabit switch installed. So, data is easily shared
by staff through internet.
B) Please draw a simple diagram to demonstrate how the components are
interconnected with each other.
8
3.1 A) Define how the components of WIDGET’S infrastructure in relation to data, networks,
machines, users and applications are interconnected with each other.
Here, it is identified that company staff use laptops which are connected through Wi fi. Also,
they are provided access from Netgear 24 port gigabit switch installed. So, data is easily shared
by staff through internet.
B) Please draw a simple diagram to demonstrate how the components are
interconnected with each other.
8
3.2 A) Identify 3 security gaps for WIDGET’s infrastructure that makes the devices or
components vulnerable.
The 3 security gaps are :
No software security installed
Sharing of id and password
Public Wi fi.
B) Pick one of the above and identify what steps the company could take to protect their
physical infrastructure in the future? Evaluate your steps by explaining how your steps
mitigate the risks?
Here, company can protect laptops by installing anti virus software. The steps are
Download anti virus software from internet.
Extract set up and install it in laptop.
These steps will mitigate risk of any unauthorised access in laptop. Also, it will prevent it from
virus attacks.
3.3 Explain why it would be important that WIDGET need a professional cyber security officer
on staff? (max 150 words)
9
components vulnerable.
The 3 security gaps are :
No software security installed
Sharing of id and password
Public Wi fi.
B) Pick one of the above and identify what steps the company could take to protect their
physical infrastructure in the future? Evaluate your steps by explaining how your steps
mitigate the risks?
Here, company can protect laptops by installing anti virus software. The steps are
Download anti virus software from internet.
Extract set up and install it in laptop.
These steps will mitigate risk of any unauthorised access in laptop. Also, it will prevent it from
virus attacks.
3.3 Explain why it would be important that WIDGET need a professional cyber security officer
on staff? (max 150 words)
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

It is important for WIDGET to hire cyber security officer so that he will be able to manage and
ensure entire IT infrastructure security. Besides, officer will ensure that all physical devices are
secured and there is no risk of cyber attacks. Moreover, officer will be responsible for all
protecting confidential and sensitive data, IP, etc. of company (Sun, Hahn and Liu 2018). In
addition, the person will frame guidelines and policies regarding how to use data and info, how
to maintain security, giving access to data, etc. Thus, with that company will work as per set
policies and it will not result in any breach of data and info. He will set and implement user
access control and monitor network to find out irregular activity in it, do regular audits to ensure
security practices are implemented, etc.
10
ensure entire IT infrastructure security. Besides, officer will ensure that all physical devices are
secured and there is no risk of cyber attacks. Moreover, officer will be responsible for all
protecting confidential and sensitive data, IP, etc. of company (Sun, Hahn and Liu 2018). In
addition, the person will frame guidelines and policies regarding how to use data and info, how
to maintain security, giving access to data, etc. Thus, with that company will work as per set
policies and it will not result in any breach of data and info. He will set and implement user
access control and monitor network to find out irregular activity in it, do regular audits to ensure
security practices are implemented, etc.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCES
Books and journals
El Mrabet, Z. and et.al., 2018. Cyber-security in smart grid: Survey and challenges. Computers
& Electrical Engineering, 67, pp.469-482.
Gunduz, M.Z. and Das, R., 2020. Cyber-security on smart grid: Threats and potential
solutions. Computer networks, 169, p.107094.
Lallie, H.S., and et.al., 2021. Cyber security in the age of covid-19: A timeline and analysis of
cyber-crime and cyber-attacks during the pandemic. Computers & Security, p.102248.
Srinivas, J., and et.al., 2019. Government regulations in cyber security: Framework, standards
and recommendations. Future Generation Computer Systems, 92, pp.178-188.
Sun, C.C., Hahn, A. and Liu, C.C., 2018. Cyber security of a power grid: State-of-the-
art. International Journal of Electrical Power & Energy Systems, 99, pp.45-56.
11
Books and journals
El Mrabet, Z. and et.al., 2018. Cyber-security in smart grid: Survey and challenges. Computers
& Electrical Engineering, 67, pp.469-482.
Gunduz, M.Z. and Das, R., 2020. Cyber-security on smart grid: Threats and potential
solutions. Computer networks, 169, p.107094.
Lallie, H.S., and et.al., 2021. Cyber security in the age of covid-19: A timeline and analysis of
cyber-crime and cyber-attacks during the pandemic. Computers & Security, p.102248.
Srinivas, J., and et.al., 2019. Government regulations in cyber security: Framework, standards
and recommendations. Future Generation Computer Systems, 92, pp.178-188.
Sun, C.C., Hahn, A. and Liu, C.C., 2018. Cyber security of a power grid: State-of-the-
art. International Journal of Electrical Power & Energy Systems, 99, pp.45-56.
11
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




