Cyber Security Issues and Cloud-Based Solutions Report for JL Company
VerifiedAdded on 2023/02/01
|14
|3207
|24
Report
AI Summary
This report provides a comprehensive analysis of cyber security issues facing JL Company, a small business transitioning to an online platform. The report identifies vulnerabilities such as outdated software, insecure routers, spam emails, and past ransomware attacks. It highlights the need for immediate action to address these risks. The core recommendation is to adopt cloud-based security solutions, emphasizing the benefits of perimeter firewalls, data encryption, identity and access management, and cloud directory services. The report compares traditional and cloud-based IT security approaches, concluding that cloud-based solutions are more cost-effective and provide superior security for small businesses. It also includes a cost breakdown for implementing the proposed cloud solutions, reinforcing the importance of proactive cyber security measures for JL Company's online business operations.

Running head: ISSUES IN CYBER SECURITY
Issues in Cyber Security
Name of the student:
Name of the university:
Author note:
Issues in Cyber Security
Name of the student:
Name of the university:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1ISSUES IN CYBER SECURITY
Abstract
The following report is prepared so as to reflect the issues that are identified within the
company of JL and in terms of addressing those issues, the necessary cyber security measures
are hence recommended. The report reflects the importance of cloud security services for
online business services and as measure to solve the issues in the company of JL, it is
recommended to use the cloud security platform to prevent its data from major data breach.
The last part of the report reflects the important comparison between using traditional way of
securing data and the cloud platform based securing data and hence concludes its importance
in using in the company of JL.
Abstract
The following report is prepared so as to reflect the issues that are identified within the
company of JL and in terms of addressing those issues, the necessary cyber security measures
are hence recommended. The report reflects the importance of cloud security services for
online business services and as measure to solve the issues in the company of JL, it is
recommended to use the cloud security platform to prevent its data from major data breach.
The last part of the report reflects the important comparison between using traditional way of
securing data and the cloud platform based securing data and hence concludes its importance
in using in the company of JL.

2ISSUES IN CYBER SECURITY
Table of Contents
Introduction:...............................................................................................................................3
Overview of the company:.....................................................................................................3
Cyber security issues of the organisation:..............................................................................4
Need to address the cyber security issues:.............................................................................5
Mitigation methods to address the identified cyber security issues within the organisation:....6
Cloud security as a method of solution:.................................................................................6
Comparison between different other approaches to address the security issues within the
organisation:...........................................................................................................................9
Cost breakdown structure to implement the solution for the identified issues:.......................10
Conclusion:..............................................................................................................................10
References:...............................................................................................................................11
Table of Contents
Introduction:...............................................................................................................................3
Overview of the company:.....................................................................................................3
Cyber security issues of the organisation:..............................................................................4
Need to address the cyber security issues:.............................................................................5
Mitigation methods to address the identified cyber security issues within the organisation:....6
Cloud security as a method of solution:.................................................................................6
Comparison between different other approaches to address the security issues within the
organisation:...........................................................................................................................9
Cost breakdown structure to implement the solution for the identified issues:.......................10
Conclusion:..............................................................................................................................10
References:...............................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3ISSUES IN CYBER SECURITY
Introduction:
As the era of digital technology progresses, the popularity of e-commerce platform is
also gaining its pace. As the whole online world is surrounded with different types of threats
and cyber activities, it is becoming extremely important for business organisations to ensure
proper security within their business process so as to secure their different data related to
financial information or trade secrets or data related to patents. Here in plays the role of
Cyber security. The term cyber security is defined as the method to protect the systems that
are used within an organisation in order to store important information, from unwanted or
unauthorized access causing destruction of the entire organisation (Ibrahim, Hamlyn-Harris
& Grundy, 2016). Thus, it is essentially important that companies who are planning to or
already have their business process on online platform, should ensure cyber security and take
necessary measures so as to protect the organisation from scams and data thefts. The
following report is prepared based on the threats that are identified within the organisation of
JL Company and thus based on the identified threats, a detailed risk assessment is made on
the organisation.
Overview of the company:
The company of JL is a small sized company mainly known for its accounts related
work. The is developed in Perth at Western Australia and currently employs about five
people within the organisation. The company is now planning to move its business towards
online platform in the marketing field. As reported, the company is now facing problems
related to slowing down of computers, failure issues in operating systems, random pop ups of
spam messages, emails and also automatic installation of malware in the systems. As all these
issues are gradually taking place in the company of JL hampering their daily business
process, hence this may lead to some major issues in the field of cyber safety for the business.
Introduction:
As the era of digital technology progresses, the popularity of e-commerce platform is
also gaining its pace. As the whole online world is surrounded with different types of threats
and cyber activities, it is becoming extremely important for business organisations to ensure
proper security within their business process so as to secure their different data related to
financial information or trade secrets or data related to patents. Here in plays the role of
Cyber security. The term cyber security is defined as the method to protect the systems that
are used within an organisation in order to store important information, from unwanted or
unauthorized access causing destruction of the entire organisation (Ibrahim, Hamlyn-Harris
& Grundy, 2016). Thus, it is essentially important that companies who are planning to or
already have their business process on online platform, should ensure cyber security and take
necessary measures so as to protect the organisation from scams and data thefts. The
following report is prepared based on the threats that are identified within the organisation of
JL Company and thus based on the identified threats, a detailed risk assessment is made on
the organisation.
Overview of the company:
The company of JL is a small sized company mainly known for its accounts related
work. The is developed in Perth at Western Australia and currently employs about five
people within the organisation. The company is now planning to move its business towards
online platform in the marketing field. As reported, the company is now facing problems
related to slowing down of computers, failure issues in operating systems, random pop ups of
spam messages, emails and also automatic installation of malware in the systems. As all these
issues are gradually taking place in the company of JL hampering their daily business
process, hence this may lead to some major issues in the field of cyber safety for the business.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4ISSUES IN CYBER SECURITY
Hence the following report is thus prepared to analyse the issues and to find out the
mitigating solutions with respect to the identified issues.
Cyber security issues of the organisation:
As reported, company of JL is facing risks in cyber security with every business
operation that it is processing with. The risks that are identified with the organisation are
analyzed as follows:
1. The operating environment of the company consists of laptops with windows 10 server
which are currently updated with the most recent update of the Microsoft: The recent
update of the Microsoft in windows 10 server is reported to have faced certain problems
related to its security (Alnatheer, 2014). The last update that came in the year 2019, has
some more serious security concerns. As the JL company is using this update in most of
the computer servers, so it is under verge of major security issues.
2. None of the software that are installed in the laptops of the organisation are secured: For
businesses which wants to move to an online field, must ensure security in the software
that are used in the business processes (Vaniea & Rashidi, 2016). But the company of JL
lacks major security issues with the software that are installed within their laptops.
3. The company accesses the internet via ADSL using the D-Link DSL-2740B wireless
router: According to some recent reports, a new type of malware is detected which
mainly targets the ADSL routers. As the company of JL uses the ADSL router to access
its internet services, there is a risk that the malware gets spread in to other computers as
well disrupting the whole system.
4. The company used windows 2000 server in its business process but due to some issues in
the power surge, the functioning of the windows server has stopped: Windows 2000
server is one of the most secured servers which offers security features to data that are
stored in computers (Wash et al., 2014). But the JL company though used it for its
Hence the following report is thus prepared to analyse the issues and to find out the
mitigating solutions with respect to the identified issues.
Cyber security issues of the organisation:
As reported, company of JL is facing risks in cyber security with every business
operation that it is processing with. The risks that are identified with the organisation are
analyzed as follows:
1. The operating environment of the company consists of laptops with windows 10 server
which are currently updated with the most recent update of the Microsoft: The recent
update of the Microsoft in windows 10 server is reported to have faced certain problems
related to its security (Alnatheer, 2014). The last update that came in the year 2019, has
some more serious security concerns. As the JL company is using this update in most of
the computer servers, so it is under verge of major security issues.
2. None of the software that are installed in the laptops of the organisation are secured: For
businesses which wants to move to an online field, must ensure security in the software
that are used in the business processes (Vaniea & Rashidi, 2016). But the company of JL
lacks major security issues with the software that are installed within their laptops.
3. The company accesses the internet via ADSL using the D-Link DSL-2740B wireless
router: According to some recent reports, a new type of malware is detected which
mainly targets the ADSL routers. As the company of JL uses the ADSL router to access
its internet services, there is a risk that the malware gets spread in to other computers as
well disrupting the whole system.
4. The company used windows 2000 server in its business process but due to some issues in
the power surge, the functioning of the windows server has stopped: Windows 2000
server is one of the most secured servers which offers security features to data that are
stored in computers (Wash et al., 2014). But the JL company though used it for its

5ISSUES IN CYBER SECURITY
business purpose. now lacks its absence due to some power problems and thus lacks
security issues in the data that are stored.
5. The employees of the organisation has been reported to receive about 40 spam messages
every day on their server: As reported the company receives near about 40 spam
messages every day which may give arise to situations like phishing attack, causing
major data loss within the organisation (Sandberg, Amin & Johansson, 2015).
6. According to previous record, the company is known to have faced a ransomware attack
before: In July 2017, the company faced a major cyber-attack by means of ransomware,
and without taking any security measure, the company paid the ransom as demanded by
the hackers (Richardson & North, 2017).
Identified issues that needs immediate attention:
1. Non-functioning of the windows 2000 server
2. Daily receiving of spam messages and email
3. Unauthorized access of other employees account without permission
4. Absence of any policy structure or rules in order to guide the employees about the usage
of the computer systems.
5. Lack of firewall securities in the software that are installed with in the laptops of the
company.
6. Use of D-Link DSL to access the internet through wireless router.
7. Lack of cryptographic techniques for authenticating the data access.
Need to address the cyber security issues:
As the entire business of JL company is planning to expand its business in the online
marketing platform, hence, ensuring advanced security features within its business process is
very much necessary (Chang, Kuo & Ramachandran, 2016). As with the recently identified
business purpose. now lacks its absence due to some power problems and thus lacks
security issues in the data that are stored.
5. The employees of the organisation has been reported to receive about 40 spam messages
every day on their server: As reported the company receives near about 40 spam
messages every day which may give arise to situations like phishing attack, causing
major data loss within the organisation (Sandberg, Amin & Johansson, 2015).
6. According to previous record, the company is known to have faced a ransomware attack
before: In July 2017, the company faced a major cyber-attack by means of ransomware,
and without taking any security measure, the company paid the ransom as demanded by
the hackers (Richardson & North, 2017).
Identified issues that needs immediate attention:
1. Non-functioning of the windows 2000 server
2. Daily receiving of spam messages and email
3. Unauthorized access of other employees account without permission
4. Absence of any policy structure or rules in order to guide the employees about the usage
of the computer systems.
5. Lack of firewall securities in the software that are installed with in the laptops of the
company.
6. Use of D-Link DSL to access the internet through wireless router.
7. Lack of cryptographic techniques for authenticating the data access.
Need to address the cyber security issues:
As the entire business of JL company is planning to expand its business in the online
marketing platform, hence, ensuring advanced security features within its business process is
very much necessary (Chang, Kuo & Ramachandran, 2016). As with the recently identified
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6ISSUES IN CYBER SECURITY
threats, there is still no mitigating solutions or steps that are taken by the organisation, hence
it is important for the company to take immediate actions on the identified risks before
moving its business to the online platform. Implementing a proper cyber security measure
has become very much essential for the company while working in the online platform.
Mitigation methods to address the identified cyber security issues within
the organisation:
As the company of JL is facing a whole lot of cyber security issues within their
business process hence it is recommended that they should opt for moving their business to
the cloud-based platform in order to ensure the business progress and also to provide
advanced security with their information assets (Rittinghouse & Ransome, 2017). Companies
under cloud-based platforms are well equipped to manage any situation be it under
unexpected peaks in traffic or in content delivery or in optimizing the speed of the loads
while providing services to the customers (Chang, Kuo & Ramachandran, 2016). The most
important feature that is provided in cloud-based environment to business organisations is a
well ensured data security which helps the business organisations to secure their data from
any kind of cyber-attacks.
Cloud security as a method of solution:
Cloud based solutions are beneficial to all companies of all sizes but it is more beneficial
to small startup companies like that of the company of JL. It helps companies to increase the
chance of gaining profit on the medium as well as provides high class cyber security features
to the companies (Ali, Khan & Vasilakos, 2015). All the problems that are faced in small
enterprises are taken care in the cloud environment. Though it can be a little expensive for the
startup companies to opt for a cloud environment but it will help them to reduce individual
costs on providing separate security features for each and every assets of the company. The
threats, there is still no mitigating solutions or steps that are taken by the organisation, hence
it is important for the company to take immediate actions on the identified risks before
moving its business to the online platform. Implementing a proper cyber security measure
has become very much essential for the company while working in the online platform.
Mitigation methods to address the identified cyber security issues within
the organisation:
As the company of JL is facing a whole lot of cyber security issues within their
business process hence it is recommended that they should opt for moving their business to
the cloud-based platform in order to ensure the business progress and also to provide
advanced security with their information assets (Rittinghouse & Ransome, 2017). Companies
under cloud-based platforms are well equipped to manage any situation be it under
unexpected peaks in traffic or in content delivery or in optimizing the speed of the loads
while providing services to the customers (Chang, Kuo & Ramachandran, 2016). The most
important feature that is provided in cloud-based environment to business organisations is a
well ensured data security which helps the business organisations to secure their data from
any kind of cyber-attacks.
Cloud security as a method of solution:
Cloud based solutions are beneficial to all companies of all sizes but it is more beneficial
to small startup companies like that of the company of JL. It helps companies to increase the
chance of gaining profit on the medium as well as provides high class cyber security features
to the companies (Ali, Khan & Vasilakos, 2015). All the problems that are faced in small
enterprises are taken care in the cloud environment. Though it can be a little expensive for the
startup companies to opt for a cloud environment but it will help them to reduce individual
costs on providing separate security features for each and every assets of the company. The
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7ISSUES IN CYBER SECURITY
basic and the first level of security that are provided in cloud-based environment are as
follows:
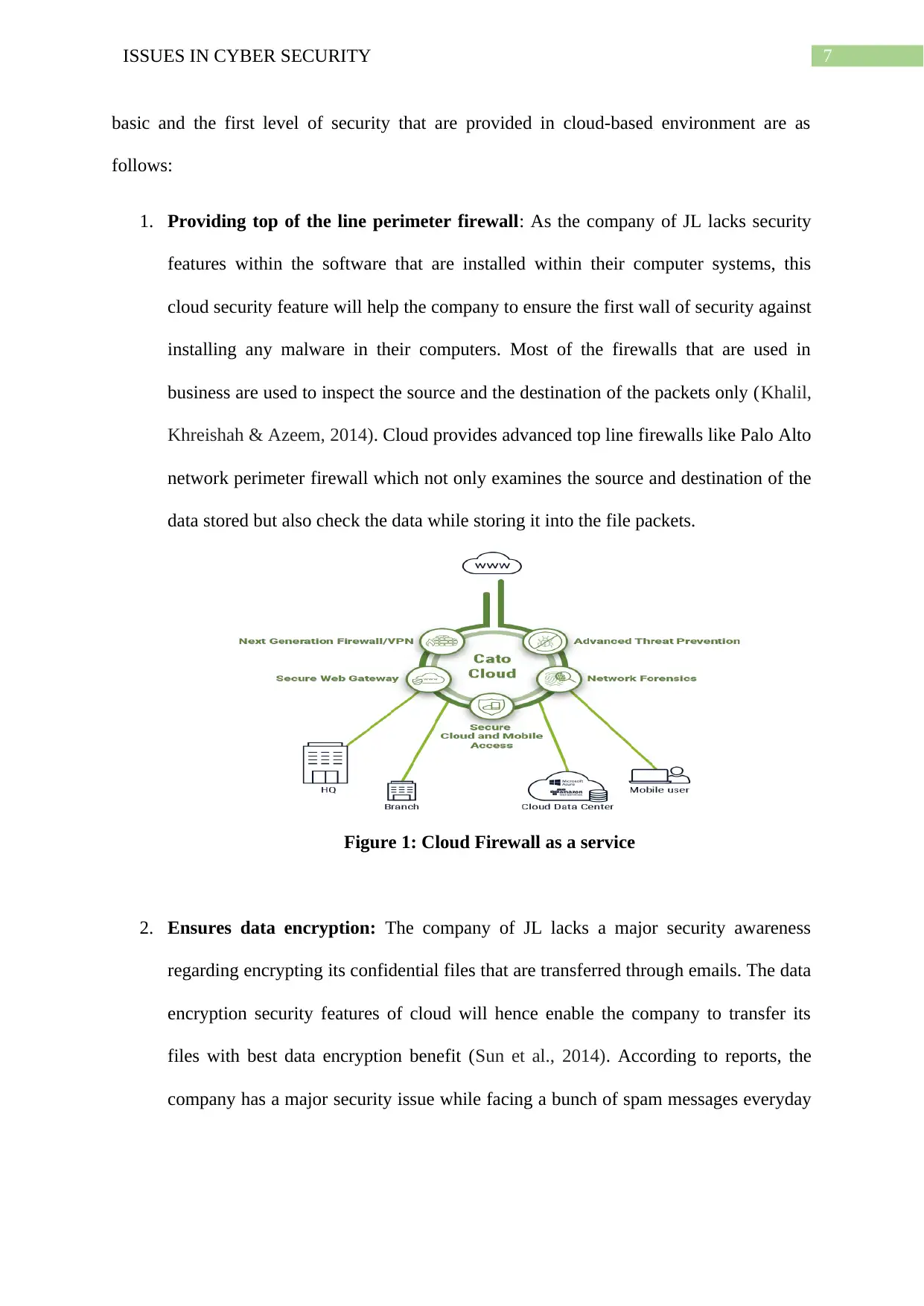
1. Providing top of the line perimeter firewall: As the company of JL lacks security
features within the software that are installed within their computer systems, this
cloud security feature will help the company to ensure the first wall of security against
installing any malware in their computers. Most of the firewalls that are used in
business are used to inspect the source and the destination of the packets only (Khalil,
Khreishah & Azeem, 2014). Cloud provides advanced top line firewalls like Palo Alto
network perimeter firewall which not only examines the source and destination of the
data stored but also check the data while storing it into the file packets.
Figure 1: Cloud Firewall as a service
2. Ensures data encryption: The company of JL lacks a major security awareness
regarding encrypting its confidential files that are transferred through emails. The data
encryption security features of cloud will hence enable the company to transfer its
files with best data encryption benefit (Sun et al., 2014). According to reports, the
company has a major security issue while facing a bunch of spam messages everyday
basic and the first level of security that are provided in cloud-based environment are as
follows:
1. Providing top of the line perimeter firewall: As the company of JL lacks security
features within the software that are installed within their computer systems, this
cloud security feature will help the company to ensure the first wall of security against
installing any malware in their computers. Most of the firewalls that are used in
business are used to inspect the source and the destination of the packets only (Khalil,
Khreishah & Azeem, 2014). Cloud provides advanced top line firewalls like Palo Alto
network perimeter firewall which not only examines the source and destination of the
data stored but also check the data while storing it into the file packets.
Figure 1: Cloud Firewall as a service
2. Ensures data encryption: The company of JL lacks a major security awareness
regarding encrypting its confidential files that are transferred through emails. The data
encryption security features of cloud will hence enable the company to transfer its
files with best data encryption benefit (Sun et al., 2014). According to reports, the
company has a major security issue while facing a bunch of spam messages everyday

8ISSUES IN CYBER SECURITY
within their system. This cloud sponsored data encryption method will hence help the
company to mitigate the issue while providing them the best encryption services.
Figure 2: Cloud Data Encryption service
3. Identity and access management: Unauthorized access to others account and lack of
security policies and rules about access management is a major concern that needs to
be addressed immediately within the organisation of JL (Kalaiprasath, Elankavi &
Udayakumar, 2017). The identification and access management feature of cloud is
somewhat related to the authentication feature but its has a separate operational
feature. With this security feature, business of JL company, will have a secured way
of accessing systems of the employees (Nikolai & Wang, 2014). It uses a multifactor
authentication method to validate the users who are accessing the account.
4. Provides cloud directory services: One of the major issues that the company is
facing is the absence of the use of the windows 2000 server. It is an important part for
online businesses as it provides a number of security features that would prevent the
company from cyber risks. But now as the company lacks this privilege, the cloud-
based service will come into handy in this respect providing a cloud directory services
that will in turn reduce the expenditure cost and also help the company in mitigating
the issues.
within their system. This cloud sponsored data encryption method will hence help the
company to mitigate the issue while providing them the best encryption services.
Figure 2: Cloud Data Encryption service
3. Identity and access management: Unauthorized access to others account and lack of
security policies and rules about access management is a major concern that needs to
be addressed immediately within the organisation of JL (Kalaiprasath, Elankavi &
Udayakumar, 2017). The identification and access management feature of cloud is
somewhat related to the authentication feature but its has a separate operational
feature. With this security feature, business of JL company, will have a secured way
of accessing systems of the employees (Nikolai & Wang, 2014). It uses a multifactor
authentication method to validate the users who are accessing the account.
4. Provides cloud directory services: One of the major issues that the company is
facing is the absence of the use of the windows 2000 server. It is an important part for
online businesses as it provides a number of security features that would prevent the
company from cyber risks. But now as the company lacks this privilege, the cloud-
based service will come into handy in this respect providing a cloud directory services
that will in turn reduce the expenditure cost and also help the company in mitigating
the issues.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9ISSUES IN CYBER SECURITY
Comparison between different other approaches to address the security issues
within the organisation:
In order to mitigate the identified cyber issues within the company of JL, two main
approaches can be used in terms of addressing the issues which includes traditional and
cloud-based information technology approaches.
Traditional approach for providing IT security:
For any information technology-based company, developing a proper IT infrastructure
of the company is a crucial element. The company needs to connect to different hardware
devices in order to store their data securely (Sutikno, Stiawan & Subroto, 2014). In
traditional way of information system approach, IT companies need to install a huge number
of hardware and software requirements and as a result, it causes huge expenditure. For small
startup-based companies, it will incur a great amount of expenditure in order to provide the
necessary security measures.
Cloud based approach towards IT security:
On the other hand, cloud service approach helps the companies to deploy their
business in cloud environment and hence allows the company to store important data within
the provided storage place and thus reduces the cost for buying individual storages. Cloud
environment are equipped with specific hardware and software requirements which are
needed for ensuring security of a company’s data assets. It also provides security measures
like implementation of firewall and other password-based protocols.
Comparison between different other approaches to address the security issues
within the organisation:
In order to mitigate the identified cyber issues within the company of JL, two main
approaches can be used in terms of addressing the issues which includes traditional and
cloud-based information technology approaches.
Traditional approach for providing IT security:
For any information technology-based company, developing a proper IT infrastructure
of the company is a crucial element. The company needs to connect to different hardware
devices in order to store their data securely (Sutikno, Stiawan & Subroto, 2014). In
traditional way of information system approach, IT companies need to install a huge number
of hardware and software requirements and as a result, it causes huge expenditure. For small
startup-based companies, it will incur a great amount of expenditure in order to provide the
necessary security measures.
Cloud based approach towards IT security:
On the other hand, cloud service approach helps the companies to deploy their
business in cloud environment and hence allows the company to store important data within
the provided storage place and thus reduces the cost for buying individual storages. Cloud
environment are equipped with specific hardware and software requirements which are
needed for ensuring security of a company’s data assets. It also provides security measures
like implementation of firewall and other password-based protocols.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10ISSUES IN CYBER SECURITY
Cost breakdown structure to implement the solution for the identified
issues:
There are various cloud service providers that are present in market which provides
security and other services to the organisations and the cost for implementing those ranges
from about $10/ month. The cost for implementing firewall in cloud environment ranges to
about $100 and to implement the IAM services in the cloud it costs to around $5000.
Conclusion:
Thus, from the above report it can be concluded that cloud security plays a vital role
while benefiting business organisations to secure their credential information over the cloud
environment. Cloud security allows additional security benefits to online businesses by
allowing backing up of files in the offsite so as to decrease the potential f the hackers from
hacking information and thus protects the entire organisation. Besides implementing cloud
security, the company of JL should also implement strategies to develop policies and rules to
make the employees aware of the use of computer systems within the organisation.
Cost breakdown structure to implement the solution for the identified
issues:
There are various cloud service providers that are present in market which provides
security and other services to the organisations and the cost for implementing those ranges
from about $10/ month. The cost for implementing firewall in cloud environment ranges to
about $100 and to implement the IAM services in the cloud it costs to around $5000.
Conclusion:
Thus, from the above report it can be concluded that cloud security plays a vital role
while benefiting business organisations to secure their credential information over the cloud
environment. Cloud security allows additional security benefits to online businesses by
allowing backing up of files in the offsite so as to decrease the potential f the hackers from
hacking information and thus protects the entire organisation. Besides implementing cloud
security, the company of JL should also implement strategies to develop policies and rules to
make the employees aware of the use of computer systems within the organisation.

11ISSUES IN CYBER SECURITY
References:
Ali, M., Khan, S. U., & Vasilakos, A. V. (2015). Security in cloud computing: Opportunities
and challenges. Information sciences, 305, 357-383.
Alnatheer, M. A. (2014). Secure Socket Layer (SSL) Impact on Web Server
Performance. Journal of Advances in Computer Networks, 2(3), 211-217.
Chang, V., Kuo, Y. H., & Ramachandran, M. (2016). Cloud computing adoption framework:
A security framework for business clouds. Future Generation Computer Systems, 57,
24-41.
Chang, V., Kuo, Y. H., & Ramachandran, M. (2016). Cloud computing adoption framework:
A security framework for business clouds. Future Generation Computer Systems, 57,
24-41.
Ibrahim, A. S., Hamlyn-Harris, J., & Grundy, J. (2016). Emerging security challenges of
cloud virtual infrastructure. arXiv preprint arXiv:1612.09059.
Kalaiprasath, R., Elankavi, R., & Udayakumar, D. R. (2017). Cloud. Security and
Compliance-A Semantic Approach in End to End Security. International Journal Of
Mechanical Engineering And Technology (Ijmet), 8(5), 987-994.
Khalil, I., Khreishah, A., & Azeem, M. (2014). Cloud computing security: A
survey. Computers, 3(1), 1-35.
Nikolai, J., & Wang, Y. (2014, February). Hypervisor-based cloud intrusion detection
system. In 2014 International Conference on Computing, Networking and
Communications (ICNC) (pp. 989-993). IEEE.
References:
Ali, M., Khan, S. U., & Vasilakos, A. V. (2015). Security in cloud computing: Opportunities
and challenges. Information sciences, 305, 357-383.
Alnatheer, M. A. (2014). Secure Socket Layer (SSL) Impact on Web Server
Performance. Journal of Advances in Computer Networks, 2(3), 211-217.
Chang, V., Kuo, Y. H., & Ramachandran, M. (2016). Cloud computing adoption framework:
A security framework for business clouds. Future Generation Computer Systems, 57,
24-41.
Chang, V., Kuo, Y. H., & Ramachandran, M. (2016). Cloud computing adoption framework:
A security framework for business clouds. Future Generation Computer Systems, 57,
24-41.
Ibrahim, A. S., Hamlyn-Harris, J., & Grundy, J. (2016). Emerging security challenges of
cloud virtual infrastructure. arXiv preprint arXiv:1612.09059.
Kalaiprasath, R., Elankavi, R., & Udayakumar, D. R. (2017). Cloud. Security and
Compliance-A Semantic Approach in End to End Security. International Journal Of
Mechanical Engineering And Technology (Ijmet), 8(5), 987-994.
Khalil, I., Khreishah, A., & Azeem, M. (2014). Cloud computing security: A
survey. Computers, 3(1), 1-35.
Nikolai, J., & Wang, Y. (2014, February). Hypervisor-based cloud intrusion detection
system. In 2014 International Conference on Computing, Networking and
Communications (ICNC) (pp. 989-993). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





