Comprehensive Cyber Security Report: Threats, Attacks, and Solutions
VerifiedAdded on 2021/06/14
|10
|1812
|84
Report
AI Summary
This report provides an overview of cyber security in the context of network security. It begins by defining cyber security and its importance in protecting online data, especially in today's technologically advanced world. The report then identifies various threats and attacks, categorizing them as active or passive, and details their potential damage, including financial losses, reputational harm, and legal fines. It explores the issues and challenges associated with cyber security, such as viruses, worms, and Trojan errors, and highlights the difficulty of preventing unauthorized access. Finally, the report outlines various countermeasures and mitigation strategies, including intrusion prevention systems, encryption, firewalls, VPNs, anti-virus software, and access control lists (ACLs), concluding with the importance of cyber security in protecting organizational data.
Cyber Security 1
Network Security
Network Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber Security 2
Executive summary
In this report the main focus is on the topic Cyber security. In today’s era, the change
in technology has provided various benefits to the business by allowing them to store their
huge amount of data online. The aim of this report is to figure out the challenges and issues
associated due to cyber security. It is important to maintain the security of data as
organisations completely rely on data stored online. In this report, limelight is on the possible
attacks that occur on the network and the security measures that could be taken to avoid the
chances of security attacks. Cyber security keeps track of data packets assure that information
remains integrated, confidential and available to valid end users.
Executive summary
In this report the main focus is on the topic Cyber security. In today’s era, the change
in technology has provided various benefits to the business by allowing them to store their
huge amount of data online. The aim of this report is to figure out the challenges and issues
associated due to cyber security. It is important to maintain the security of data as
organisations completely rely on data stored online. In this report, limelight is on the possible
attacks that occur on the network and the security measures that could be taken to avoid the
chances of security attacks. Cyber security keeps track of data packets assure that information
remains integrated, confidential and available to valid end users.

Cyber Security 3
Table of Contents
Cyber security.......................................................................................................................................3
Identification of threats and attacks.......................................................................................................3
Potential Damage..................................................................................................................................4
Issues and challenges of cyber security.................................................................................................4
Countermeasures and mitigation strategies............................................................................................4
Conclusion.........................................................................................................................................6
References.............................................................................................................................................7
Appendix...............................................................................................................................................8
Table of Contents
Cyber security.......................................................................................................................................3
Identification of threats and attacks.......................................................................................................3
Potential Damage..................................................................................................................................4
Issues and challenges of cyber security.................................................................................................4
Countermeasures and mitigation strategies............................................................................................4
Conclusion.........................................................................................................................................6
References.............................................................................................................................................7
Appendix...............................................................................................................................................8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cyber Security 4
Cyber security
Cyber security is a protection that is used to safeguard the data stored on wide
networks. Cyber security is used to ensure that the information is shielded from the hackers.
Cyber security shields the information from unauthorized user and make sure that secrecy is
maintained. Cyber security is fundamental for every organisation as it uses set of techniques
to keep up the protection of data [1]. It guarantees that private information which is stored on
the network is secure and integrity, confidentiality and availability of data is met. Cyber
security is very significant as it protects digital data from hackers and avoid that the data do
not get modifies by unauthorized user. It uses set of strategies to maintain the privacy of
information. Cyber is related to group of computers that are connected to form a network via
internet these computers store important data and files that need to be secured.
Identification of threats and attacks
There are various threats that are associated with cyber security and it is important to
identify the threats. Identification of threat helps in analysing the risk so that security
measures could be taken accordingly [2]. Identifying the threats helps in tracking which part
of the system is not working. Threats are increasing day by day and it has increased the
chances of information loss. Sometimes viruses hit the system or unauthorized users gain the
access to data.
Possible attacks that violet cyber security of a network are classified as active attack or
passive attack. Active attack is one where unauthorized user gets the chance to access the
data as well as modifies it [3]. Passive attack is difficult to identify as the user do not make
any modification of data but silently reads it.
Possible attacks are:
Data modification – In which attacker modifies the data unknowingly.
Replay- It is the attack in which data packets are sent to the receiver in an interruptive
manner either by delaying the data packets or sending them in a repeated manner.
Masquerade- It is an active attack as in this the false user tries to act like a valid user. The
invalid user captures the identity of valid user and act like an authorized user.
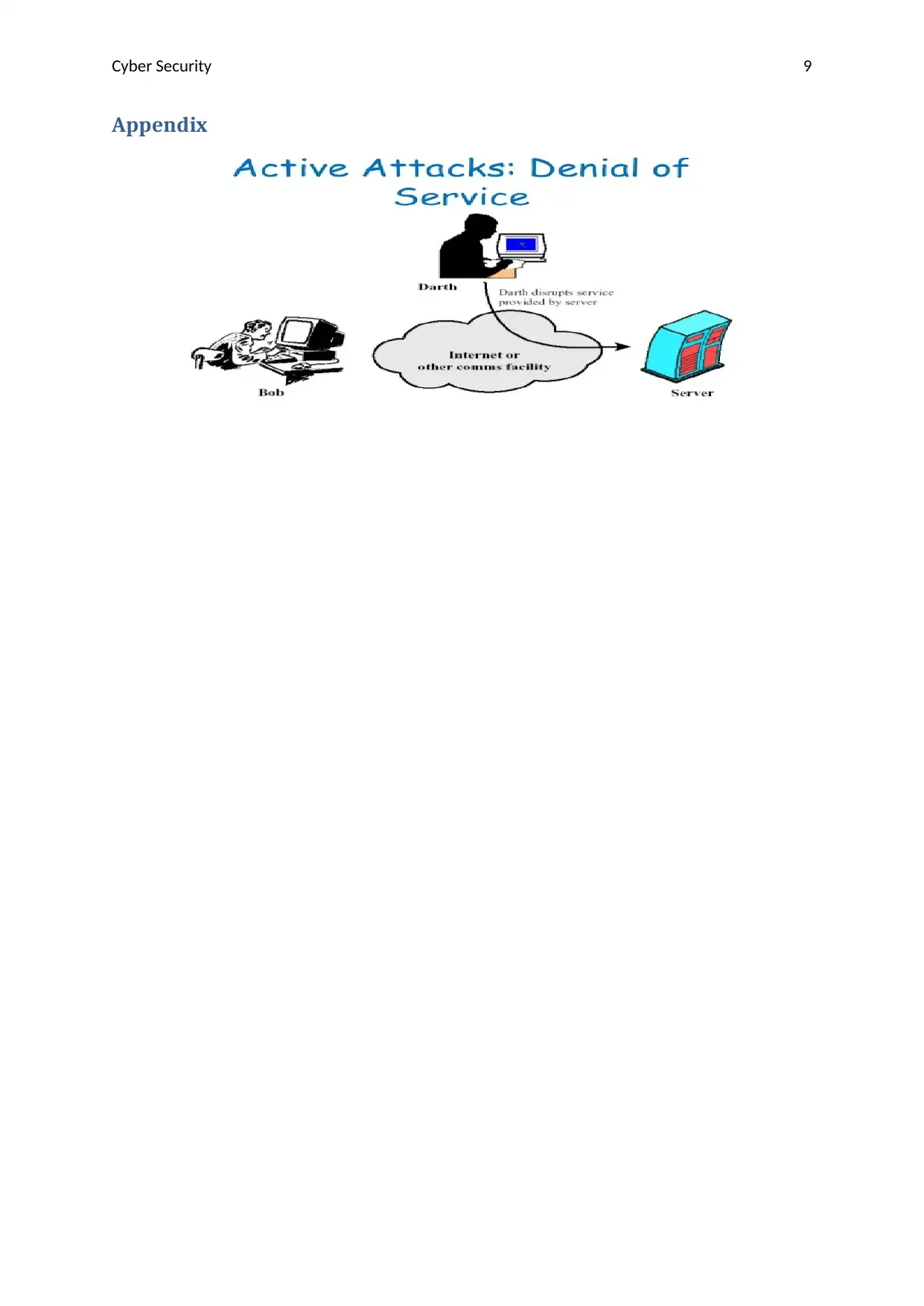
Denial of service- In this the unauthorized user tries to top the valid users to access the
information. This can be done by overloading the traffic of website or by making the server
inaccessible.
Man in the middle attack- In this third party user modifies the original communication route
and then accesses the data packets in between by breaking the direct connection.
Packet sniffing Attack- In this hackers design some programs and the silently monitor the
data over the network and capture data packets.
Cyber security
Cyber security is a protection that is used to safeguard the data stored on wide
networks. Cyber security is used to ensure that the information is shielded from the hackers.
Cyber security shields the information from unauthorized user and make sure that secrecy is
maintained. Cyber security is fundamental for every organisation as it uses set of techniques
to keep up the protection of data [1]. It guarantees that private information which is stored on
the network is secure and integrity, confidentiality and availability of data is met. Cyber
security is very significant as it protects digital data from hackers and avoid that the data do
not get modifies by unauthorized user. It uses set of strategies to maintain the privacy of
information. Cyber is related to group of computers that are connected to form a network via
internet these computers store important data and files that need to be secured.
Identification of threats and attacks
There are various threats that are associated with cyber security and it is important to
identify the threats. Identification of threat helps in analysing the risk so that security
measures could be taken accordingly [2]. Identifying the threats helps in tracking which part
of the system is not working. Threats are increasing day by day and it has increased the
chances of information loss. Sometimes viruses hit the system or unauthorized users gain the
access to data.
Possible attacks that violet cyber security of a network are classified as active attack or
passive attack. Active attack is one where unauthorized user gets the chance to access the
data as well as modifies it [3]. Passive attack is difficult to identify as the user do not make
any modification of data but silently reads it.
Possible attacks are:
Data modification – In which attacker modifies the data unknowingly.
Replay- It is the attack in which data packets are sent to the receiver in an interruptive
manner either by delaying the data packets or sending them in a repeated manner.
Masquerade- It is an active attack as in this the false user tries to act like a valid user. The
invalid user captures the identity of valid user and act like an authorized user.
Denial of service- In this the unauthorized user tries to top the valid users to access the
information. This can be done by overloading the traffic of website or by making the server
inaccessible.
Man in the middle attack- In this third party user modifies the original communication route
and then accesses the data packets in between by breaking the direct connection.
Packet sniffing Attack- In this hackers design some programs and the silently monitor the
data over the network and capture data packets.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber Security 5
Potential Damage
These attack leads to various potential damage to the business and organisation as
they are vulnerable and cause harm to the data stored on the network. Cyber -attacks often
result in financial loss, reputation damage and various legal fines. When corporate
information gets leaked it may cause to financial data loss as well as results in loss of
business contracts [4]. Cyber-attacks additionally damage the trust build with the customers
and results in loss of sale, profit and customers. Data stored over internet has some legal
regulations and if in some cases data leaks accidentally or deliberately it leads to security
violations that causes security fine on an organisation. These attacks cause a huge damage to
the network and affect the security of an organisation as digital data is common these days
[5]. Nowadays online transactions is adopted for money transfer and it is growing with time
thus it have opened doors for cybercriminals to read important information of the
organisation and miss-treat them.
Issues and challenges
There are many issues associated due to cyber security. Virus is one of the issues that
inject the system and erases some of the data without can prior knowledge. Worms are
similar as it enters the system without can intervention. Trojan error is software that is used to
increase the performance of the system that is speeding up the transaction. It claims to send
the confidential data to remote users [6]. Major challenge that occur due to cyber security is
that it allows access to hackers unknowingly which it turn gives righto hackers to simply
wipe out the important information and they read the precious data [7]. Cyber security uses
high technology to protect the data but it somewhere leaves the footprints on the network
which become easier for the hackers to access the information.
Countermeasures and mitigation strategies
To avoid the chances of cyber-attacks various precautions need to be followed so that
it mitigates the chances of risk [8].
Some of the solutions are:
Intrusion prevention System (IPS) – Intrusions are bugs in the system that allows access to
the information to an unauthorized user [9]. IPS takes proper steps to mitigate the risk and
prevent the attack to penetrate in the system.
Encryption- In this the actual text to data is kept in a form that is not readable by humans, so
that if the data gets leaked the third party is not able to access the information.
Firewall- It act like a gateway which allows only authorized user to enter the system and
block all the doors by which unauthorised user tries to enter the network.
Virtual Private Network- It makes sure that not only data but the communication path
through which data packets are transmitted are secure [10].
Potential Damage
These attack leads to various potential damage to the business and organisation as
they are vulnerable and cause harm to the data stored on the network. Cyber -attacks often
result in financial loss, reputation damage and various legal fines. When corporate
information gets leaked it may cause to financial data loss as well as results in loss of
business contracts [4]. Cyber-attacks additionally damage the trust build with the customers
and results in loss of sale, profit and customers. Data stored over internet has some legal
regulations and if in some cases data leaks accidentally or deliberately it leads to security
violations that causes security fine on an organisation. These attacks cause a huge damage to
the network and affect the security of an organisation as digital data is common these days
[5]. Nowadays online transactions is adopted for money transfer and it is growing with time
thus it have opened doors for cybercriminals to read important information of the
organisation and miss-treat them.
Issues and challenges
There are many issues associated due to cyber security. Virus is one of the issues that
inject the system and erases some of the data without can prior knowledge. Worms are
similar as it enters the system without can intervention. Trojan error is software that is used to
increase the performance of the system that is speeding up the transaction. It claims to send
the confidential data to remote users [6]. Major challenge that occur due to cyber security is
that it allows access to hackers unknowingly which it turn gives righto hackers to simply
wipe out the important information and they read the precious data [7]. Cyber security uses
high technology to protect the data but it somewhere leaves the footprints on the network
which become easier for the hackers to access the information.
Countermeasures and mitigation strategies
To avoid the chances of cyber-attacks various precautions need to be followed so that
it mitigates the chances of risk [8].
Some of the solutions are:
Intrusion prevention System (IPS) – Intrusions are bugs in the system that allows access to
the information to an unauthorized user [9]. IPS takes proper steps to mitigate the risk and
prevent the attack to penetrate in the system.
Encryption- In this the actual text to data is kept in a form that is not readable by humans, so
that if the data gets leaked the third party is not able to access the information.
Firewall- It act like a gateway which allows only authorized user to enter the system and
block all the doors by which unauthorised user tries to enter the network.
Virtual Private Network- It makes sure that not only data but the communication path
through which data packets are transmitted are secure [10].

Cyber Security 6
Use of Anti-Virus and anti-Spyware software’s-These are the software’s that protect the
system from viruses, worms, spyware and bugs so that they do not enter the system. It tries to
remove all the malicious programs that are injected in the network to perform vulnerabilities.
These software sae used to fix all the bugs.
ACL- It stands for access control list that is used to assign privileges to users like who can
read, write or modify the data [11]. This helps in controlling the traffic of the network and
enhances the performance.
Security Certification- These are the certificates that assure the network by reducing the risk
and managing the security of business.
Use of Anti-Virus and anti-Spyware software’s-These are the software’s that protect the
system from viruses, worms, spyware and bugs so that they do not enter the system. It tries to
remove all the malicious programs that are injected in the network to perform vulnerabilities.
These software sae used to fix all the bugs.
ACL- It stands for access control list that is used to assign privileges to users like who can
read, write or modify the data [11]. This helps in controlling the traffic of the network and
enhances the performance.
Security Certification- These are the certificates that assure the network by reducing the risk
and managing the security of business.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cyber Security 7
Conclusion
Cyber security is very important as most of the important data is stored online. The
data stored on the network as high chances of getting leaked. Thus it can be concluded that it
is necessary to protect the data packets from unauthorized access as they try to alter the data.
Security attacks are rising in today’s era attackers try to read the sensitive documents of
various organisations this has led to development of unique security measures. It can be
concluded from this research that cyber security allows the business to increase their
efficiency by storing their information online. This in turn have increased cyber-attacks as the
information can be read from anywhere.
Conclusion
Cyber security is very important as most of the important data is stored online. The
data stored on the network as high chances of getting leaked. Thus it can be concluded that it
is necessary to protect the data packets from unauthorized access as they try to alter the data.
Security attacks are rising in today’s era attackers try to read the sensitive documents of
various organisations this has led to development of unique security measures. It can be
concluded from this research that cyber security allows the business to increase their
efficiency by storing their information online. This in turn have increased cyber-attacks as the
information can be read from anywhere.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber Security 8
References
[1]D. Kovchegin, "Developing National Regulations to Support Nuclear Security: Lessons
Learned From the U.S. Support to Russia, Ukraine, and Belarus", Security Index: A Russian
Journal on International Security, vol. 20, no. 2, pp. 111-117, 2014.
[2]"UK launches new Cyber Security Strategy", Computer Fraud & Security, vol. 2011, no.
12, p. 3, 2011.
[3] Gupta B, Agrawal DP, Yamaguchi S, editors. Handbook of research on modern
cryptographic solutions for computer and cyber security”. IGI Global;, pp.56-90, 2016.
[4] Ben-Asher N, Gonzalez C. Effects of cyber security knowledge on attack detection.
Computers in Human Behavior”.pp- 51-61.2016.
[5] Rawat DB, Bajracharya C. Cyber security for smart grid systems: Status, challenges and
perspectives”.pp. 1-6, 2015.
[6] Kim DY. Cyber security issues imposed on nuclear power plants. Annals of Nuclear
Energy ;pp-141-3, 2014.
[7] Whitty M, Doodson J, Creese S, Hodges D. “Individual differences in cyber security
behaviors: an examination of who is sharing passwords”. Cyberpsychology, Behavior, and
Social Networking. 18(1), pp-3-7, 2015.
[8] Ellis A, McELwee T. “System and method for predicting impending cyber security events
using multi channel behavioral analysis in a distributed computing environment”. United
States patent US pp. 45-90, 2017.
[9] Drissi Y, Rick AH, Harrison CG, Kouloheris JL, Pattnaik PC, Rao JR, “International
Business Machines Corp, assignee. Systems, methods and computer programs providing
impact mitigation of cyber-security failures”. United States patent US 9,129,108. 2015
[10] Pour MM, Anzalchi A, Sarwat A. “A review on cyber security issues and mitigation
methods in smart grid systemspp. 1-4, 2017
[11] Farraj A, Hammad E, Al Daoud A, Kundur D.” A game-theoretic analysis of cyber
switching attacks and mitigation in smart grid systems”. 7(4):1846-55, 2016.
References
[1]D. Kovchegin, "Developing National Regulations to Support Nuclear Security: Lessons
Learned From the U.S. Support to Russia, Ukraine, and Belarus", Security Index: A Russian
Journal on International Security, vol. 20, no. 2, pp. 111-117, 2014.
[2]"UK launches new Cyber Security Strategy", Computer Fraud & Security, vol. 2011, no.
12, p. 3, 2011.
[3] Gupta B, Agrawal DP, Yamaguchi S, editors. Handbook of research on modern
cryptographic solutions for computer and cyber security”. IGI Global;, pp.56-90, 2016.
[4] Ben-Asher N, Gonzalez C. Effects of cyber security knowledge on attack detection.
Computers in Human Behavior”.pp- 51-61.2016.
[5] Rawat DB, Bajracharya C. Cyber security for smart grid systems: Status, challenges and
perspectives”.pp. 1-6, 2015.
[6] Kim DY. Cyber security issues imposed on nuclear power plants. Annals of Nuclear
Energy ;pp-141-3, 2014.
[7] Whitty M, Doodson J, Creese S, Hodges D. “Individual differences in cyber security
behaviors: an examination of who is sharing passwords”. Cyberpsychology, Behavior, and
Social Networking. 18(1), pp-3-7, 2015.
[8] Ellis A, McELwee T. “System and method for predicting impending cyber security events
using multi channel behavioral analysis in a distributed computing environment”. United
States patent US pp. 45-90, 2017.
[9] Drissi Y, Rick AH, Harrison CG, Kouloheris JL, Pattnaik PC, Rao JR, “International
Business Machines Corp, assignee. Systems, methods and computer programs providing
impact mitigation of cyber-security failures”. United States patent US 9,129,108. 2015
[10] Pour MM, Anzalchi A, Sarwat A. “A review on cyber security issues and mitigation
methods in smart grid systemspp. 1-4, 2017
[11] Farraj A, Hammad E, Al Daoud A, Kundur D.” A game-theoretic analysis of cyber
switching attacks and mitigation in smart grid systems”. 7(4):1846-55, 2016.
Cyber Security 9
Appendix
Appendix
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cyber Security 10
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





