CSCI 5742: Cyber Security Programming - Project Proposal Document
VerifiedAdded on 2023/06/03
|4
|702
|57
Homework Assignment
AI Summary
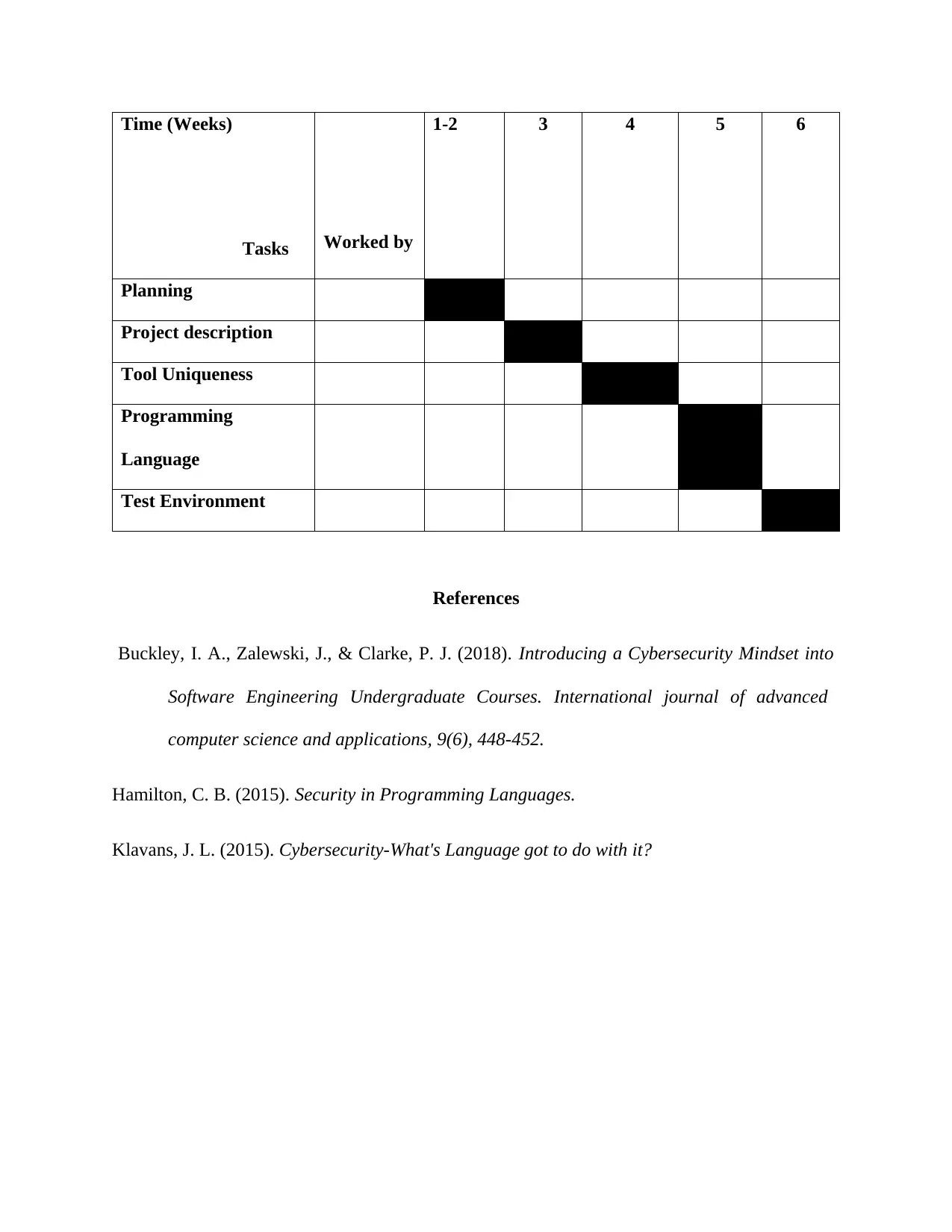
This document is a project proposal for a cyber security programming course, CSCI 5742. It outlines the design of a security tool, detailing its modules, functionality, and uniqueness. The proposed tool, an "eye lookup," monitors open ports to information systems, sending data packets to assess vulnerabilities and trigger alerts. The project emphasizes the use of Java and Python, along with testing environments and strategies. The proposal highlights the tool's uniqueness in providing a wide range of functionalities, including security and threat modeling, and details the programming language selection and testing methodologies. The project aims to create a tool that reduces operational costs and offers a user-friendly interface for both attacking and preventing interfaces, making it a valuable asset in the market.
1 out of 4





![[object Object]](/_next/static/media/star-bottom.7253800d.svg)