Cyber Operations Report: Decision Making in Modern Cyber Warfare
VerifiedAdded on 2022/09/10
|27
|3765
|22
Report
AI Summary
This report provides a comprehensive analysis of cyber operations, encompassing key concepts such as Clausewitz's "fog of war" and its relevance in the modern information environment. It examines decision-making processes in cybersecurity, addressing challenges like uncertainty and the need for risk assessment. The report also delves into practical aspects of computer security through deep packet analysis using Wireshark, including statistical analysis of network traffic, identification of active nodes, and protocol analysis. Furthermore, it identifies and explains potential cyberattacks, such as TCP SYN floods, providing a detailed understanding of offensive and defensive cyber operations. The report concludes with a discussion on the importance of effective cybersecurity strategies and the need for adaptability in a constantly evolving threat landscape.

Cyber Operations
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction......................................................................................................................................1
Task 1...............................................................................................................................................2
1.1 Fog of war.........................................................................................................................2
1.2 Information Environment..................................................................................................2
1.3 Decision making for cyber (friction issues?)....................................................................3
1.4 Critical Discussion............................................................................................................3
Task 3...............................................................................................................................................4
3.1 Statistical Analysis............................................................................................................4
3.2 Activity Narrative and Attack Identification..................................................................14
3.3 Attack Explanation..........................................................................................................16
Overall Conclusion........................................................................................................................21
References......................................................................................................................................22
Appendix........................................................................................................................................23
Introduction......................................................................................................................................1
Task 1...............................................................................................................................................2
1.1 Fog of war.........................................................................................................................2
1.2 Information Environment..................................................................................................2
1.3 Decision making for cyber (friction issues?)....................................................................3
1.4 Critical Discussion............................................................................................................3
Task 3...............................................................................................................................................4
3.1 Statistical Analysis............................................................................................................4
3.2 Activity Narrative and Attack Identification..................................................................14
3.3 Attack Explanation..........................................................................................................16
Overall Conclusion........................................................................................................................21
References......................................................................................................................................22
Appendix........................................................................................................................................23

Introduction
The main objective of this project is develop a deep and systematic understanding and
knowledge of information of cyber operations. This project is divided into three tasks, the task 1
is will assess the understanding of making decisions in the modern information environment. The
task 2 is will assess the understanding of theoretical and practical aspects of the computer
operations and security. The Task 3 is will assess the understanding pf advanced principles in
computer security from a system perceptive.
In Task 1, this report sheds light on the Clausewitz’s theory on the fog of war and its
implementation in today’s modern enterprise information environment, including its impact. This
is an interesting topic which is debated over the preparedness of the US military for dealing with
both fog and friction in the present day battlefield. Today, fog and friction are conflicts based on
information overload, real-time technology, and cyberspace threats. The debate starts with a few
suggestion on the promises of the modern technology and information dominance. But, some
feel that overloaded information and starvation of information both could result in fog and
friction. This report presents a discussion on the fog of war, decision making for cyber,
information environment, cyber security issues, and critical analysis will be presented by the end
of this report.
In Task 2, the main objective of this task is to provide the cyber manoeuvre principles
can underpin the offensive and defensive operations in the modern information environment.
In task 3, the main aim of this task is to do deep packet analysis of the provided file, by
using the Wireshark tool. The deep packet analysis includes the following aspects such as,
Statistics analysis - Network Boundaries, Active Node, Types of protocols and
Traffic and External sources.
Activity Narrative
Attack Identification and Explanation.
All the above aspects will be analyzed and discussed in detail.
1
The main objective of this project is develop a deep and systematic understanding and
knowledge of information of cyber operations. This project is divided into three tasks, the task 1
is will assess the understanding of making decisions in the modern information environment. The
task 2 is will assess the understanding of theoretical and practical aspects of the computer
operations and security. The Task 3 is will assess the understanding pf advanced principles in
computer security from a system perceptive.
In Task 1, this report sheds light on the Clausewitz’s theory on the fog of war and its
implementation in today’s modern enterprise information environment, including its impact. This
is an interesting topic which is debated over the preparedness of the US military for dealing with
both fog and friction in the present day battlefield. Today, fog and friction are conflicts based on
information overload, real-time technology, and cyberspace threats. The debate starts with a few
suggestion on the promises of the modern technology and information dominance. But, some
feel that overloaded information and starvation of information both could result in fog and
friction. This report presents a discussion on the fog of war, decision making for cyber,
information environment, cyber security issues, and critical analysis will be presented by the end
of this report.
In Task 2, the main objective of this task is to provide the cyber manoeuvre principles
can underpin the offensive and defensive operations in the modern information environment.
In task 3, the main aim of this task is to do deep packet analysis of the provided file, by
using the Wireshark tool. The deep packet analysis includes the following aspects such as,
Statistics analysis - Network Boundaries, Active Node, Types of protocols and
Traffic and External sources.
Activity Narrative
Attack Identification and Explanation.
All the above aspects will be analyzed and discussed in detail.
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Task 1
1.1 Fog of war
Fog of war was coined by Carl von Clausewitz. This term was used for ambiguities
related to war. When a battle starts, even the tactical and relevant information can be confusing
and misleading. This can be due to the difficulty to see the patterns in the midst of fog and noise.
A war is an art, which needs unplanned decision making. In war, there are practical situations
where the higher authority’s restricted commands need not be obeyed, instead based on the
situation the leaders should take the control on the situation and take advantage. The theory of
Colonel John Boyd, (Observe-Orient-Decide-Act) OODA loop are utilized in the business and
military. From his point of view, the fog of war can be beneficial (Strategic Thinking, 2019).
Initially, to gain advantage over the enemy, it is required to anticipate the ambiguity. The
next step is to understand the fog’s disorientations on the opponent, then continue the confusion
state by surprising tactics. More importantly, instantly analyze the opponent’s decision cycle,
with the help of OODA cycle. Here, the speed matters, so one must be quick than the opponent.
This can cause confusion, fear, and chaos. Today, the war is completely different, as the
technology has changed the combat, and the modern opponents rely on C4ISR systems
(Command, Control, Communications, Computers, Intelligence, Surveillance and
Reconnaissance). The tsunami of technology has resulted in cyber side of war (Reed, 2012).
1.2 Information Environment
In this technology-oriented world, people and organizations all rely on information and
communications technology (ICT) and this demands security policy regarding cyberspace. But it
can be a daunting task. The information environment in the present day overloads with
information, real-time technology, and cyberspace threats, which creates fog on the modern
battlefields. Today, the challenges in cybersecurity are regarding ransomware evolution,
blockchain revolution, AI expansion, increasing IoT threats, and vulnerability of serverless apps
(Mason, 2018). Despite the advantage of advanced technology and dominance of information,
the theory of Clausewitz about “fog and friction” remains in the modern combat and in all the
technological fields, which is more severe than before. Thus, it is necessary to come to terms
regarding modern ambiguities (Reed, 2012).
2
1.1 Fog of war
Fog of war was coined by Carl von Clausewitz. This term was used for ambiguities
related to war. When a battle starts, even the tactical and relevant information can be confusing
and misleading. This can be due to the difficulty to see the patterns in the midst of fog and noise.
A war is an art, which needs unplanned decision making. In war, there are practical situations
where the higher authority’s restricted commands need not be obeyed, instead based on the
situation the leaders should take the control on the situation and take advantage. The theory of
Colonel John Boyd, (Observe-Orient-Decide-Act) OODA loop are utilized in the business and
military. From his point of view, the fog of war can be beneficial (Strategic Thinking, 2019).
Initially, to gain advantage over the enemy, it is required to anticipate the ambiguity. The
next step is to understand the fog’s disorientations on the opponent, then continue the confusion
state by surprising tactics. More importantly, instantly analyze the opponent’s decision cycle,
with the help of OODA cycle. Here, the speed matters, so one must be quick than the opponent.
This can cause confusion, fear, and chaos. Today, the war is completely different, as the
technology has changed the combat, and the modern opponents rely on C4ISR systems
(Command, Control, Communications, Computers, Intelligence, Surveillance and
Reconnaissance). The tsunami of technology has resulted in cyber side of war (Reed, 2012).
1.2 Information Environment
In this technology-oriented world, people and organizations all rely on information and
communications technology (ICT) and this demands security policy regarding cyberspace. But it
can be a daunting task. The information environment in the present day overloads with
information, real-time technology, and cyberspace threats, which creates fog on the modern
battlefields. Today, the challenges in cybersecurity are regarding ransomware evolution,
blockchain revolution, AI expansion, increasing IoT threats, and vulnerability of serverless apps
(Mason, 2018). Despite the advantage of advanced technology and dominance of information,
the theory of Clausewitz about “fog and friction” remains in the modern combat and in all the
technological fields, which is more severe than before. Thus, it is necessary to come to terms
regarding modern ambiguities (Reed, 2012).
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1.3 Decision making for cyber (friction issues?)
The above sections provide an understanding that, it is important to take correct and
instant decisions based on the environmental and systemic uncertainty. There are various
challenges in formulating the cyber security policy that is effective. The decision makers are held
responsible for well-developed and a standard method. It is extremely difficult to make decision
in uncertain situation. Especially, in cyber- attacks the decision making worsens due to
uncertainty (Dean and McDermott, 2017).
The following reasons cause uncertainty in making decisions related to cyber security
(Jalali, Siegel and Madnick, 2019):
1) Lack of knowledge.
2) High complexity level
3) Poor capability of predicting future events.
4) Difficulty to calculate the impact of a hypothetical cyber incident.
5) Lack of experience.
To overcome uncertainty, one must invest on information security, because it helps to get
positive results. Then, the uncertainty can be solved by estimating risks and selecting risk-return
combinations (Jalali, Siegel and Madnick, 2019).
1.4 Critical Discussion
The discussion of this report determines that, in the data overload environment, educating
on how to ensure the leaders and users to fight unblocked based on the present technical
advantages is necessary.
The Internet is being increasingly exploited by the attackers, for various illegal purposes
and to develop new criminal methods to use the Internet. It is significant to stop such illegal
activities/cyber-crimes, which effects the internet’s growth and development due to security
issues. The security issues increases the fear of trust to perform any kind of personal or business
transactions (Canabarro and Borne, 2013). However, ensure risk assessment for cyber security
(Fielder et al., 2017). It is concluded that creation of effective policies and effective methods for
addressing the cyber threats and information technology is vital for defense. It is also worth to
have a comprehensive Cybersecurity Strategy, with effective measures for anticipating,
3
The above sections provide an understanding that, it is important to take correct and
instant decisions based on the environmental and systemic uncertainty. There are various
challenges in formulating the cyber security policy that is effective. The decision makers are held
responsible for well-developed and a standard method. It is extremely difficult to make decision
in uncertain situation. Especially, in cyber- attacks the decision making worsens due to
uncertainty (Dean and McDermott, 2017).
The following reasons cause uncertainty in making decisions related to cyber security
(Jalali, Siegel and Madnick, 2019):
1) Lack of knowledge.
2) High complexity level
3) Poor capability of predicting future events.
4) Difficulty to calculate the impact of a hypothetical cyber incident.
5) Lack of experience.
To overcome uncertainty, one must invest on information security, because it helps to get
positive results. Then, the uncertainty can be solved by estimating risks and selecting risk-return
combinations (Jalali, Siegel and Madnick, 2019).
1.4 Critical Discussion
The discussion of this report determines that, in the data overload environment, educating
on how to ensure the leaders and users to fight unblocked based on the present technical
advantages is necessary.
The Internet is being increasingly exploited by the attackers, for various illegal purposes
and to develop new criminal methods to use the Internet. It is significant to stop such illegal
activities/cyber-crimes, which effects the internet’s growth and development due to security
issues. The security issues increases the fear of trust to perform any kind of personal or business
transactions (Canabarro and Borne, 2013). However, ensure risk assessment for cyber security
(Fielder et al., 2017). It is concluded that creation of effective policies and effective methods for
addressing the cyber threats and information technology is vital for defense. It is also worth to
have a comprehensive Cybersecurity Strategy, with effective measures for anticipating,
3

addressing, and responding to the cyberattacks. The strategy must foster the development of
legal tools to combat all types of cyber-crime. Only such an initiative can help to distribute the
cybersecurity information and respond to the incidents, concerns, and computer security threats.
The sense of surging uncertainty shows a changing environment which can have impacts
on the choices that are made. Thus, it is necessary to identify and accommodate these changes
which helps to get an opportunity to increase the effectiveness of decision making (Decision-
making-solutions.com, 2019).
To be successful, it is necessary to revel in ambiguity. Because, it is the best option,
which helps to come to terms with what can and cannot be mastered. It is concluded that
investment on information security is essential to see positive results in cyber security.
It is not easy to develop a policy, which is flexible and adaptable by all, including state
actors, non-state actors, and businesses to engage in a World Wide Web, which is an established
form of government structure (Dean and McDermott, 2017).
Task 3
3.1 Statistical Analysis
In deep packet analysis, first do statistical analysis for the provided file. Thus, open the
provided file in the Wireshark tool as presented in the below screenshot (Insights.profitap.com,
2019).
4
legal tools to combat all types of cyber-crime. Only such an initiative can help to distribute the
cybersecurity information and respond to the incidents, concerns, and computer security threats.
The sense of surging uncertainty shows a changing environment which can have impacts
on the choices that are made. Thus, it is necessary to identify and accommodate these changes
which helps to get an opportunity to increase the effectiveness of decision making (Decision-
making-solutions.com, 2019).
To be successful, it is necessary to revel in ambiguity. Because, it is the best option,
which helps to come to terms with what can and cannot be mastered. It is concluded that
investment on information security is essential to see positive results in cyber security.
It is not easy to develop a policy, which is flexible and adaptable by all, including state
actors, non-state actors, and businesses to engage in a World Wide Web, which is an established
form of government structure (Dean and McDermott, 2017).
Task 3
3.1 Statistical Analysis
In deep packet analysis, first do statistical analysis for the provided file. Thus, open the
provided file in the Wireshark tool as presented in the below screenshot (Insights.profitap.com,
2019).
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
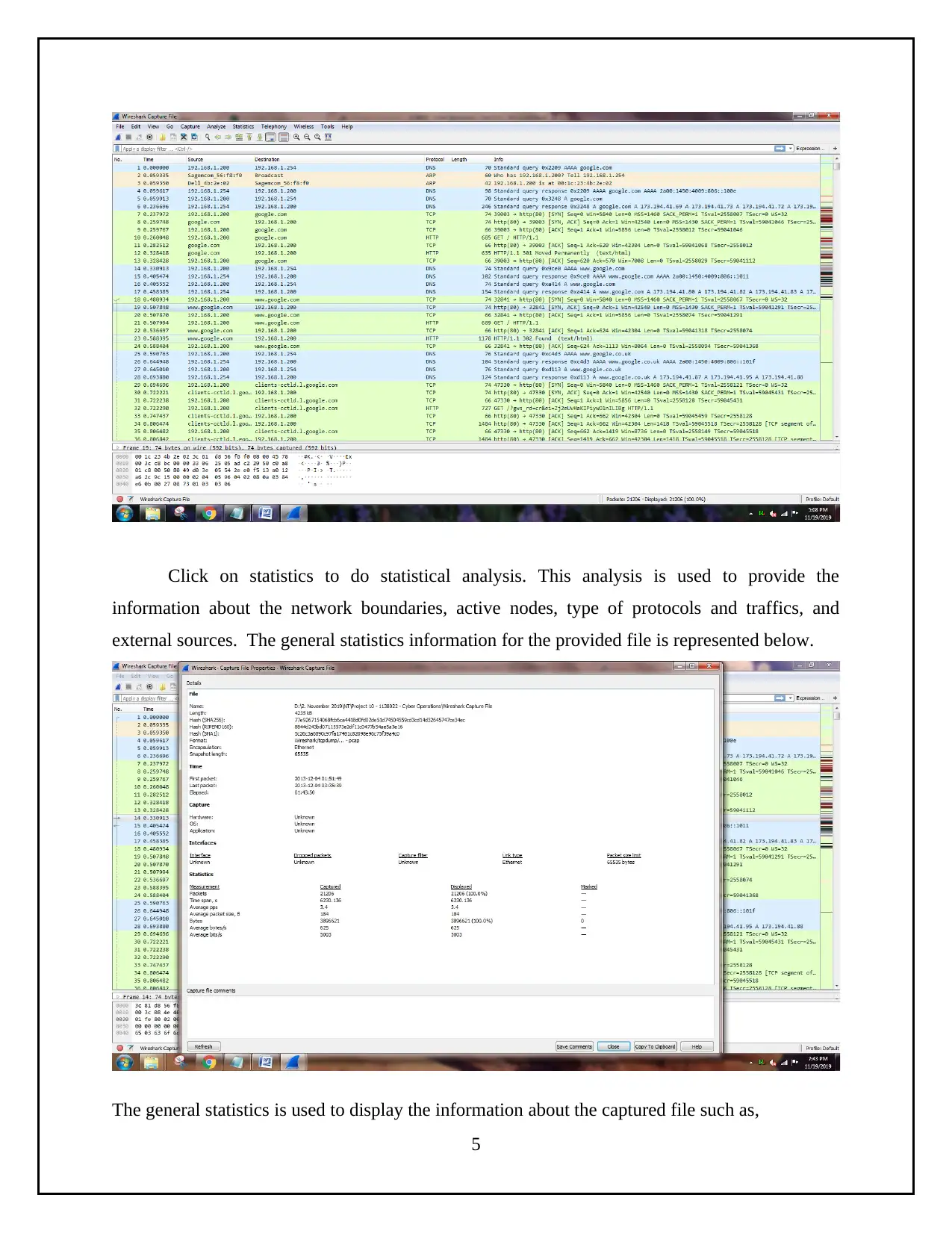
Click on statistics to do statistical analysis. This analysis is used to provide the
information about the network boundaries, active nodes, type of protocols and traffics, and
external sources. The general statistics information for the provided file is represented below.
The general statistics is used to display the information about the captured file such as,
5
information about the network boundaries, active nodes, type of protocols and traffics, and
external sources. The general statistics information for the provided file is represented below.
The general statistics is used to display the information about the captured file such as,
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
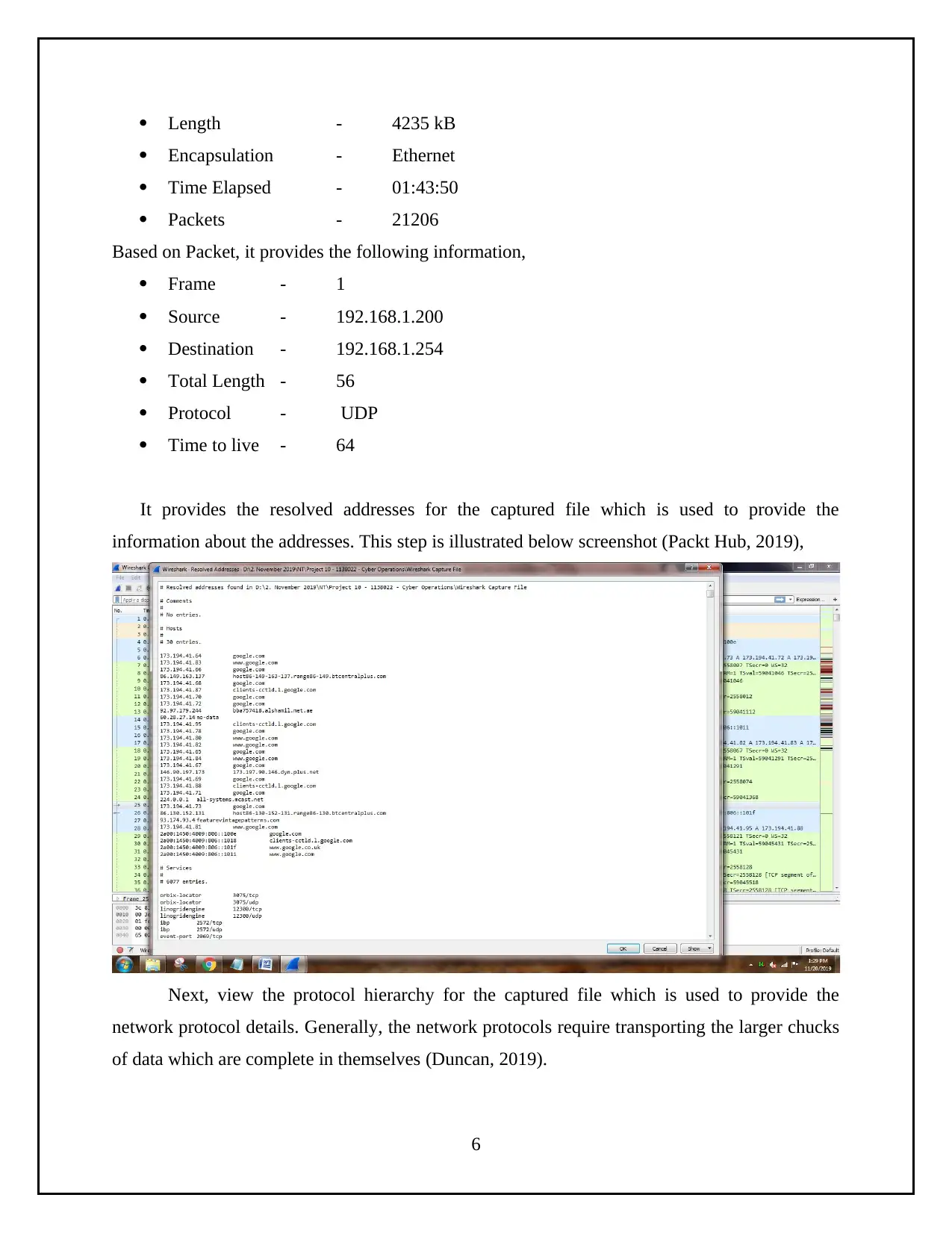
Length - 4235 kB
Encapsulation - Ethernet
Time Elapsed - 01:43:50
Packets - 21206
Based on Packet, it provides the following information,
Frame - 1
Source - 192.168.1.200
Destination - 192.168.1.254
Total Length - 56
Protocol - UDP
Time to live - 64
It provides the resolved addresses for the captured file which is used to provide the
information about the addresses. This step is illustrated below screenshot (Packt Hub, 2019),
Next, view the protocol hierarchy for the captured file which is used to provide the
network protocol details. Generally, the network protocols require transporting the larger chucks
of data which are complete in themselves (Duncan, 2019).
6
Encapsulation - Ethernet
Time Elapsed - 01:43:50
Packets - 21206
Based on Packet, it provides the following information,
Frame - 1
Source - 192.168.1.200
Destination - 192.168.1.254
Total Length - 56
Protocol - UDP
Time to live - 64
It provides the resolved addresses for the captured file which is used to provide the
information about the addresses. This step is illustrated below screenshot (Packt Hub, 2019),
Next, view the protocol hierarchy for the captured file which is used to provide the
network protocol details. Generally, the network protocols require transporting the larger chucks
of data which are complete in themselves (Duncan, 2019).
6
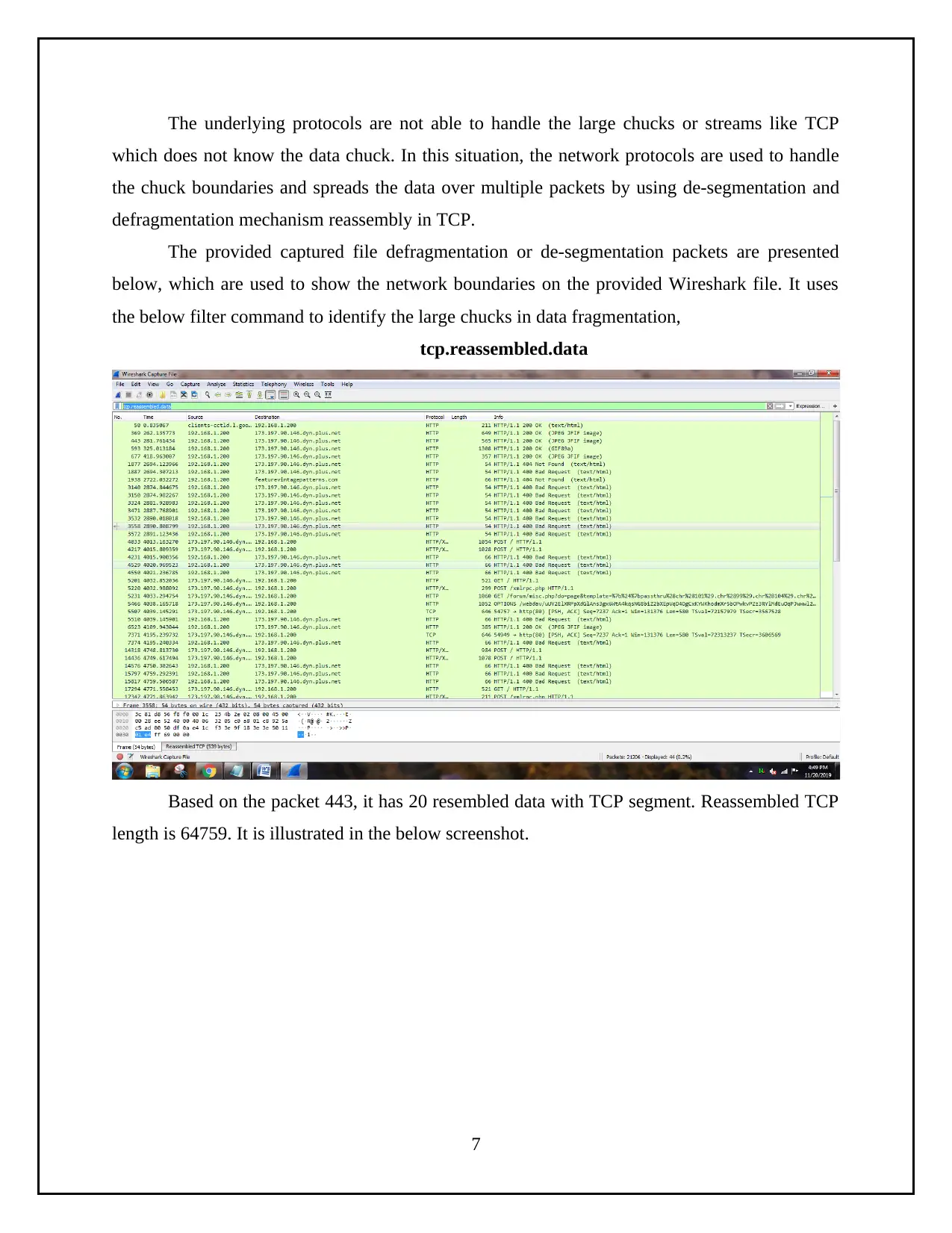
The underlying protocols are not able to handle the large chucks or streams like TCP
which does not know the data chuck. In this situation, the network protocols are used to handle
the chuck boundaries and spreads the data over multiple packets by using de-segmentation and
defragmentation mechanism reassembly in TCP.
The provided captured file defragmentation or de-segmentation packets are presented
below, which are used to show the network boundaries on the provided Wireshark file. It uses
the below filter command to identify the large chucks in data fragmentation,
tcp.reassembled.data
Based on the packet 443, it has 20 resembled data with TCP segment. Reassembled TCP
length is 64759. It is illustrated in the below screenshot.
7
which does not know the data chuck. In this situation, the network protocols are used to handle
the chuck boundaries and spreads the data over multiple packets by using de-segmentation and
defragmentation mechanism reassembly in TCP.
The provided captured file defragmentation or de-segmentation packets are presented
below, which are used to show the network boundaries on the provided Wireshark file. It uses
the below filter command to identify the large chucks in data fragmentation,
tcp.reassembled.data
Based on the packet 443, it has 20 resembled data with TCP segment. Reassembled TCP
length is 64759. It is illustrated in the below screenshot.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
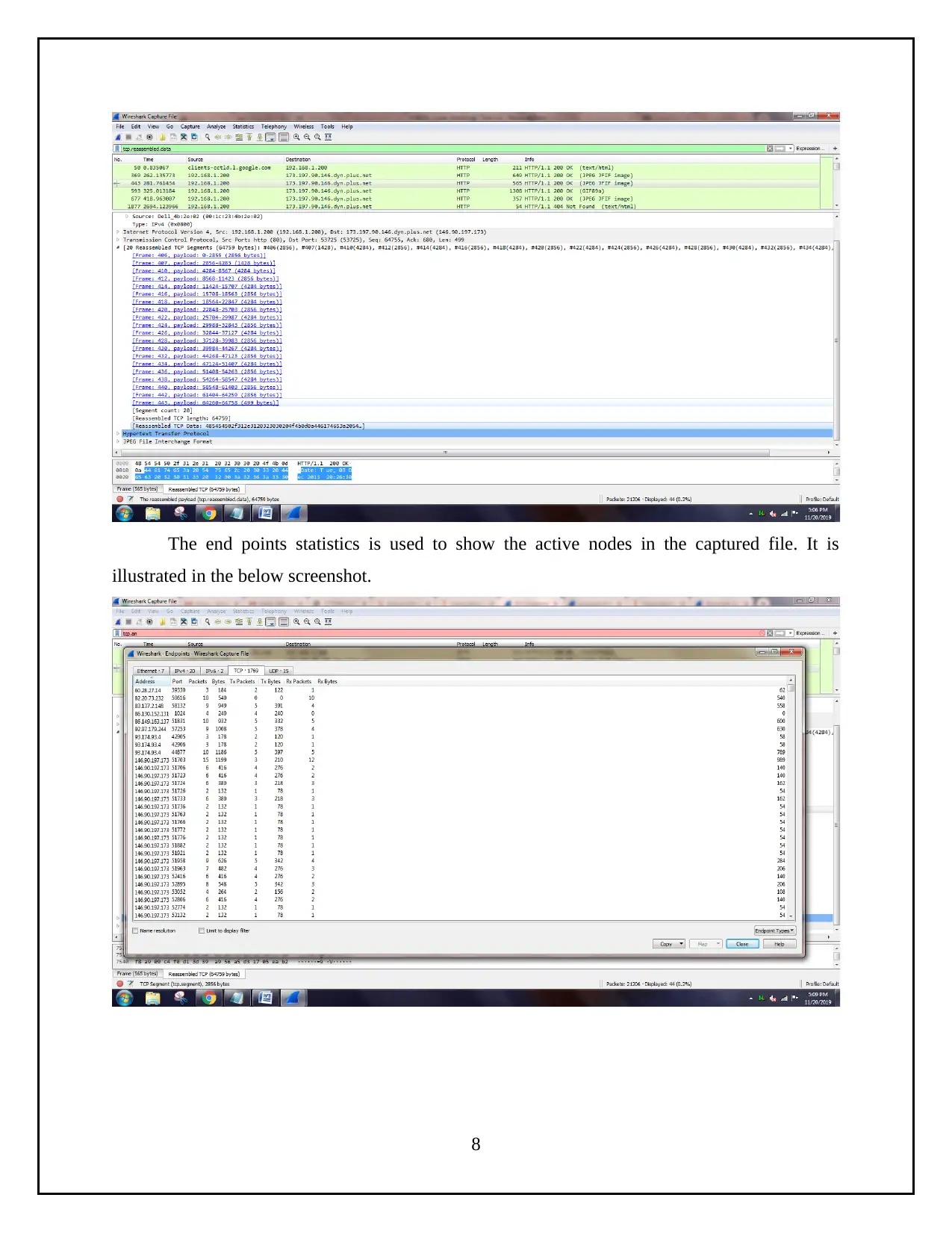
The end points statistics is used to show the active nodes in the captured file. It is
illustrated in the below screenshot.
8
illustrated in the below screenshot.
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
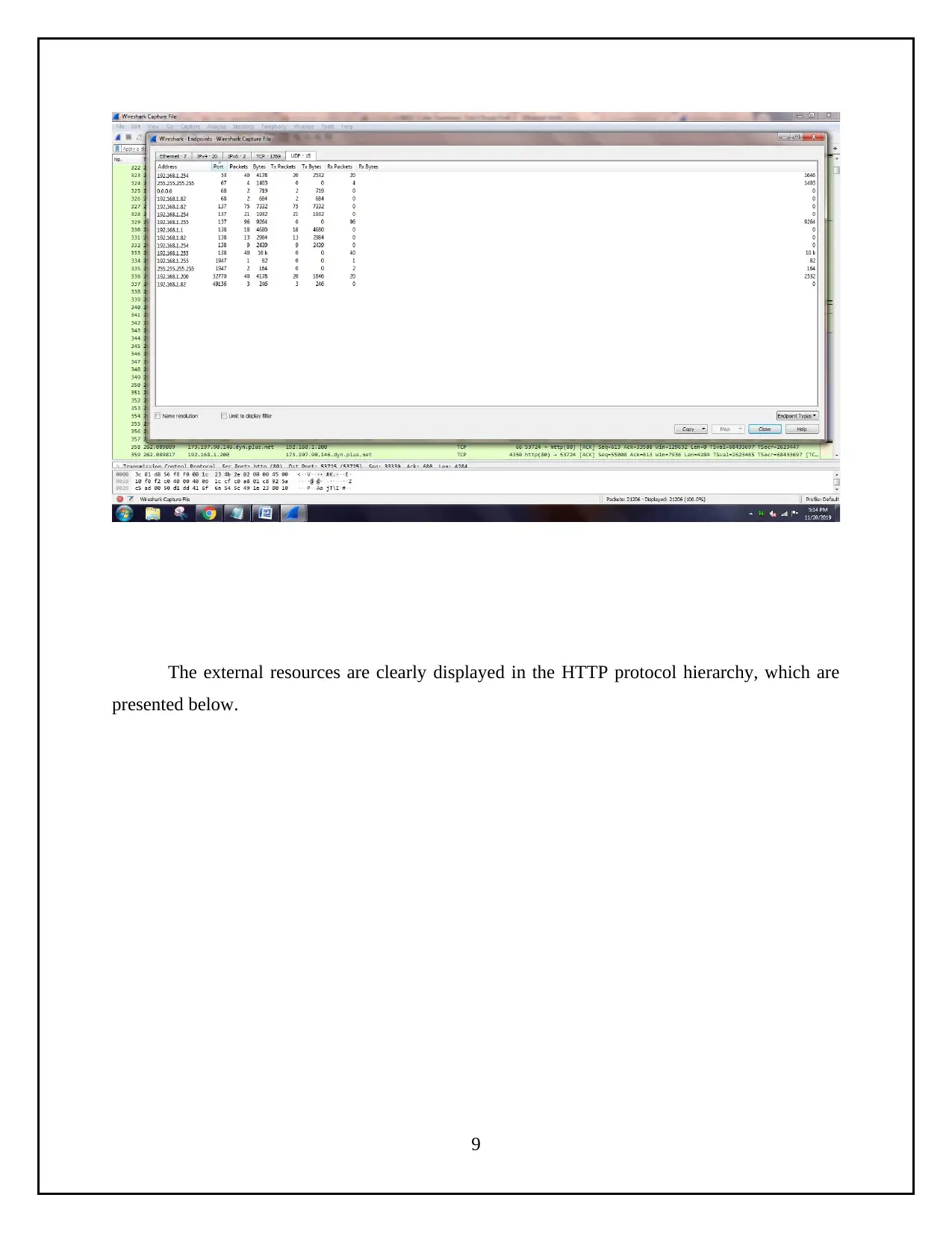
The external resources are clearly displayed in the HTTP protocol hierarchy, which are
presented below.
9
presented below.
9
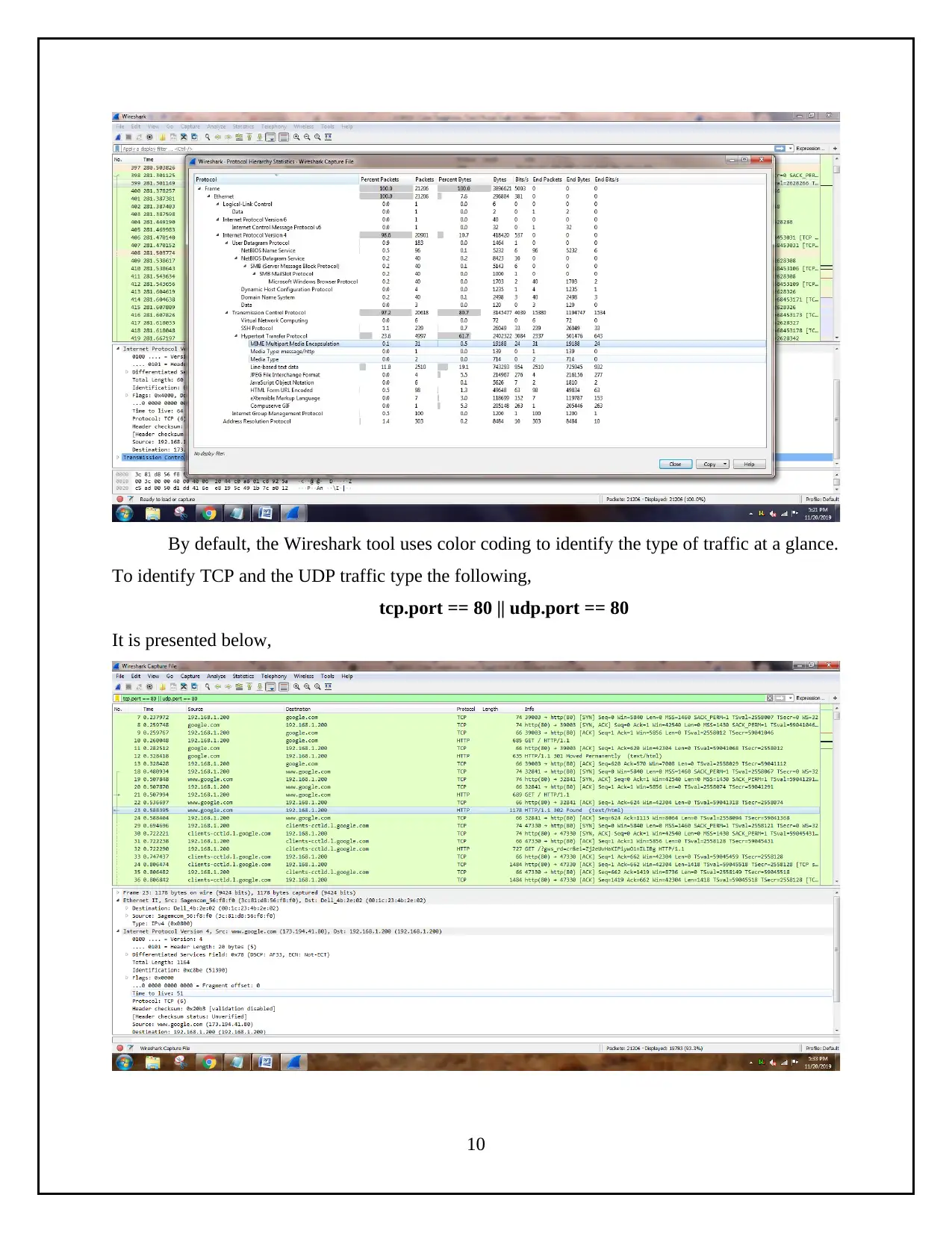
By default, the Wireshark tool uses color coding to identify the type of traffic at a glance.
To identify TCP and the UDP traffic type the following,
tcp.port == 80 || udp.port == 80
It is presented below,
10
To identify TCP and the UDP traffic type the following,
tcp.port == 80 || udp.port == 80
It is presented below,
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 27
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





