Research Report: Cyber Security Challenges for Businesses in Australia
VerifiedAdded on 2020/04/07
|12
|2263
|185
Report
AI Summary
This report provides a comprehensive overview of cyber security challenges facing businesses, particularly in Australia. It begins with an introduction to the concept of cyber security and its growing importance in the digital age, emphasizing the need for data protection. The project aims to understand public perceptions of cyber security and the precautions taken by individuals and businesses. The report outlines the project objectives, scope, and methodology, including qualitative and quantitative research approaches. A literature review explores existing research on cyber threats, including case studies of cyber-attacks and their impact on organizations. The research questions focus on factors influencing cyber security systems, protection strategies, and the handling of safety and privacy challenges. The methodology section details the use of qualitative research to uncover trends and opinions, and quantitative research to quantify issues. The report also acknowledges research limitations. The report concludes by highlighting the importance of cyber security in the current business environment, emphasizing the need for strong security cultures to protect data and maintain consumer confidence. References to relevant academic sources are included.

Report
Student Name
Institute Name
Student Name
Institute Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Introduction......................................................................................................................................3
Project Objective.............................................................................................................................3
Project Scope...................................................................................................................................4
Literature Review............................................................................................................................4
Research Questions/Hypothesis.......................................................................................................6
Primary Question.........................................................................................................................6
Secondary Questions....................................................................................................................6
Research Design and Methodology.................................................................................................7
Qualitative research......................................................................................................................7
Quantitative research....................................................................................................................7
Research Limitations.......................................................................................................................7
Time Schedule.................................................................................................................................8
Conclusion.......................................................................................................................................8
Reference.........................................................................................................................................9
Introduction......................................................................................................................................3
Project Objective.............................................................................................................................3
Project Scope...................................................................................................................................4
Literature Review............................................................................................................................4
Research Questions/Hypothesis.......................................................................................................6
Primary Question.........................................................................................................................6
Secondary Questions....................................................................................................................6
Research Design and Methodology.................................................................................................7
Qualitative research......................................................................................................................7
Quantitative research....................................................................................................................7
Research Limitations.......................................................................................................................7
Time Schedule.................................................................................................................................8
Conclusion.......................................................................................................................................8
Reference.........................................................................................................................................9

Introduction
The concept of cyber security is relatively new in business and since it is related to technological
development where companies are now clearly see and observe the importance of protecting the
data and how one can completely ignore any act based on security infringements (Bell et al.,
2015). Concept of cyber security can be defined as a wrong or unethical work to gain access to
the private information that an organization denies discussing with consumers.
The major significance of the topic is based on how technology continues to evolve with the
different opportunities and challenges. Our aim is to provide an informative primer on the
different relevant issues facing Australia. Along with this, the discussion is also to generate the
discussions about the debate and then raise awareness with regards to the fundamental block of
the technologically dependent society. In the current time, there are number of examples that are
eye-opening and have also struck the consumers to think again and consider the decision about
sharing sensitive resources of information on the internet (Von Solms et al., 2013).
The work is based on the research of how the cyber security has been proved to be the major
challenge for the different organizations with the focus on the different questionnaires and the
surveys from the people in Australia.
Project Objective
The focus of the project is to have a complete knowledge of what people think about the cyber
security and what precautions they have taken to secure their data. The challenge of cyber
security in companies like Apple, Microsoft and Google, is important to hover as many hackers
try to plunge into the system of the companies through phishing, hacking etc., and try to grab the
The concept of cyber security is relatively new in business and since it is related to technological
development where companies are now clearly see and observe the importance of protecting the
data and how one can completely ignore any act based on security infringements (Bell et al.,
2015). Concept of cyber security can be defined as a wrong or unethical work to gain access to
the private information that an organization denies discussing with consumers.
The major significance of the topic is based on how technology continues to evolve with the
different opportunities and challenges. Our aim is to provide an informative primer on the
different relevant issues facing Australia. Along with this, the discussion is also to generate the
discussions about the debate and then raise awareness with regards to the fundamental block of
the technologically dependent society. In the current time, there are number of examples that are
eye-opening and have also struck the consumers to think again and consider the decision about
sharing sensitive resources of information on the internet (Von Solms et al., 2013).
The work is based on the research of how the cyber security has been proved to be the major
challenge for the different organizations with the focus on the different questionnaires and the
surveys from the people in Australia.
Project Objective
The focus of the project is to have a complete knowledge of what people think about the cyber
security and what precautions they have taken to secure their data. The challenge of cyber
security in companies like Apple, Microsoft and Google, is important to hover as many hackers
try to plunge into the system of the companies through phishing, hacking etc., and try to grab the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

data of the system. My project objective is related to the research work that comes from
evaluating the different questions about the cyber security challenges for the business. The aim is
to understand the consequences of leakage of data and demands in the form of ransom.
Project Scope
To grasp various angles of the issues, it is important to refer different research paper and journals
on the internet. My project demonstrates the dimensions from the business perspectives where
the focus is based on achieving the deep knowledge about the cyber challenges. The data that I
have collected is from the various sources like the conducting surveys and interviewing
businessmen’s, books, research papers and from the internet. The literature review is also
included to depict about the cyber security and it answers the questions related to the challenges.
My project guides are mainly to understand the different risks of the cyber security and the issues
related to it. The work is mainly demonstrating the methods that could be used for preventing the
cyber threats in the organization.
Literature Review
Businesses these days are under constant assault from criminal working against them on internet
which is also known as cyber criminals resulting in the rise of overall cost for the companies. It
has been seen that for the big companies like Google, there is an increase in prevalence and the
severity of the malicious cyber enabled activities and other extraordinary threats that are done to
the national security, foreign policy and economy. One of the damaging targets are for the
society embroiled cyberwarfare infrastructure. Here, the focus is on the single points of failure
which is directed to the power stations, communication network, transport and the other utilities.
evaluating the different questions about the cyber security challenges for the business. The aim is
to understand the consequences of leakage of data and demands in the form of ransom.
Project Scope
To grasp various angles of the issues, it is important to refer different research paper and journals
on the internet. My project demonstrates the dimensions from the business perspectives where
the focus is based on achieving the deep knowledge about the cyber challenges. The data that I
have collected is from the various sources like the conducting surveys and interviewing
businessmen’s, books, research papers and from the internet. The literature review is also
included to depict about the cyber security and it answers the questions related to the challenges.
My project guides are mainly to understand the different risks of the cyber security and the issues
related to it. The work is mainly demonstrating the methods that could be used for preventing the
cyber threats in the organization.
Literature Review
Businesses these days are under constant assault from criminal working against them on internet
which is also known as cyber criminals resulting in the rise of overall cost for the companies. It
has been seen that for the big companies like Google, there is an increase in prevalence and the
severity of the malicious cyber enabled activities and other extraordinary threats that are done to
the national security, foreign policy and economy. One of the damaging targets are for the
society embroiled cyberwarfare infrastructure. Here, the focus is on the single points of failure
which is directed to the power stations, communication network, transport and the other utilities.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

In the year 2015, there were many corporate law firms in New York that were attack of
cybercrime (Born, 2015). There were three hackers from China that have got an opportunity to
enter into firm’s computer system by playing a trick n partners and revealing the passwords of
their emails. After entering the accounts, these criminals got their hands on very sensitive and
confidential information about some future mergers. These criminals than traded the information
and earned more than four million dollars. Like many other victims these firms preferred to stay
quiet about being part of victims (Cavelty, 2014). They also feared catching attention of other
thugs as well as also damaging the reputation since they were the keepers of the secrets of
clients. But some information leaked in media and then was later confirmed by the federal
prosecutors and those firms as well (Hong et al., 2014). The federal court publicly discussed the
discoveries and their efforts to bring the alleged criminals to justice. The case of cyber-attack
meets the security fraud must serve as wake – up call for much law based companies. It is
important to understand for such companies that they will be the target of cyber-attacks since the
information is valuable for the criminals (Overbye et al., 2017). The ransom ware like WannaCry
attack single handedly has crippled so many computers in more one hundred and fifty countries
in May and it can cost companies more than four billion dollars as per so many estimates. It is
slowly dawning on so many corporate level hackings based victims associated with some
vulnerable as well as completely defenseless situations (Wells et al., 2014). The case of
cybercrime is also metalizing for the similar face that are present on online services and have
become very popular with customers and businesses at the same time (Bates et al., 2015). The
internet network was established for the overall convenience and profit of the users is now
exposing the world new kinds of threats.
cybercrime (Born, 2015). There were three hackers from China that have got an opportunity to
enter into firm’s computer system by playing a trick n partners and revealing the passwords of
their emails. After entering the accounts, these criminals got their hands on very sensitive and
confidential information about some future mergers. These criminals than traded the information
and earned more than four million dollars. Like many other victims these firms preferred to stay
quiet about being part of victims (Cavelty, 2014). They also feared catching attention of other
thugs as well as also damaging the reputation since they were the keepers of the secrets of
clients. But some information leaked in media and then was later confirmed by the federal
prosecutors and those firms as well (Hong et al., 2014). The federal court publicly discussed the
discoveries and their efforts to bring the alleged criminals to justice. The case of cyber-attack
meets the security fraud must serve as wake – up call for much law based companies. It is
important to understand for such companies that they will be the target of cyber-attacks since the
information is valuable for the criminals (Overbye et al., 2017). The ransom ware like WannaCry
attack single handedly has crippled so many computers in more one hundred and fifty countries
in May and it can cost companies more than four billion dollars as per so many estimates. It is
slowly dawning on so many corporate level hackings based victims associated with some
vulnerable as well as completely defenseless situations (Wells et al., 2014). The case of
cybercrime is also metalizing for the similar face that are present on online services and have
become very popular with customers and businesses at the same time (Bates et al., 2015). The
internet network was established for the overall convenience and profit of the users is now
exposing the world new kinds of threats.

Research Questions/Hypothesis
Primary Question
1. What are some of the factors that influence the system of the cyber security with the
setup of the business organization?
Secondary Questions
1. What are some of the approaches which could be used for protecting the system of the
organizations from any kind of cyber-attacks?
2. How cyber security planning and the issues can handle the challenges of the safety and
privacy?
Research Gap
The research gaps are related to the business organization which are cyberspace and the cyber-
criminal activities that affect the business. The design faults are mainly in the web applications
which is the major issue of the cyber security. The design faults are due to the web applications,
with accessing the data and manipulating and misusing it. The issues are related to the internal
business process that affect the capacity to implement and sustain the cyber security. Moreover,
from surveys, cyber security software is too expensive for the small businesses so people usually
stop considering to buy them.
Research Design and Methodology
Qualitative research
Primary Question
1. What are some of the factors that influence the system of the cyber security with the
setup of the business organization?
Secondary Questions
1. What are some of the approaches which could be used for protecting the system of the
organizations from any kind of cyber-attacks?
2. How cyber security planning and the issues can handle the challenges of the safety and
privacy?
Research Gap
The research gaps are related to the business organization which are cyberspace and the cyber-
criminal activities that affect the business. The design faults are mainly in the web applications
which is the major issue of the cyber security. The design faults are due to the web applications,
with accessing the data and manipulating and misusing it. The issues are related to the internal
business process that affect the capacity to implement and sustain the cyber security. Moreover,
from surveys, cyber security software is too expensive for the small businesses so people usually
stop considering to buy them.
Research Design and Methodology
Qualitative research
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The qualitative research is mainly based on exploratory related research and used to gain
knowledge of so many underlying facts, views as well as motivations. It also provided various
kinds of insights into the issues that have helped to develop concepts as well as hypothesis for
number of quantitative research (Kwon et al., 2013). Here the project will use qualitative
research is uncover various trends through opinions of people and dive deeper in the issue. The
method will be used in a form of semi structured tools and techniques (Bates et al., 2015). Some
of most common methods also include the focus group discussion, interviews and observations.
The sample size for the research will be small and selected incidences which were highly
controversial by nature.
Quantitative research
Quantitative research has been done quantify the issue in a way of creating number of data that
can be modified into used statistics. I have worked on the elements which includes the secured
versions depending upon the views of the different elements. The research is mainly for the
classification of the features, construction of the statistical models to explain about what has
been observed. I have focused on the other tools like the questionnaires or the equipment for
collecting the numerical data. The data is more efficient that has been done with establishing the
facts depending upon the forms of surveys like questionnaire via email, face to face interview
from the support manager who has faced the cybersecurity challenges, mobile surveys and many
more.
Research Limitations
I have seen that there are some of the limitations:
knowledge of so many underlying facts, views as well as motivations. It also provided various
kinds of insights into the issues that have helped to develop concepts as well as hypothesis for
number of quantitative research (Kwon et al., 2013). Here the project will use qualitative
research is uncover various trends through opinions of people and dive deeper in the issue. The
method will be used in a form of semi structured tools and techniques (Bates et al., 2015). Some
of most common methods also include the focus group discussion, interviews and observations.
The sample size for the research will be small and selected incidences which were highly
controversial by nature.
Quantitative research
Quantitative research has been done quantify the issue in a way of creating number of data that
can be modified into used statistics. I have worked on the elements which includes the secured
versions depending upon the views of the different elements. The research is mainly for the
classification of the features, construction of the statistical models to explain about what has
been observed. I have focused on the other tools like the questionnaires or the equipment for
collecting the numerical data. The data is more efficient that has been done with establishing the
facts depending upon the forms of surveys like questionnaire via email, face to face interview
from the support manager who has faced the cybersecurity challenges, mobile surveys and many
more.
Research Limitations
I have seen that there are some of the limitations:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
a. The sample size is smaller with 6 participants, where the bigger sample would improve
the research reliability.
b. The research is not based on the measurements with the examination of the problems.
c. There are cases where some of the participants tend to refuse against the organization.
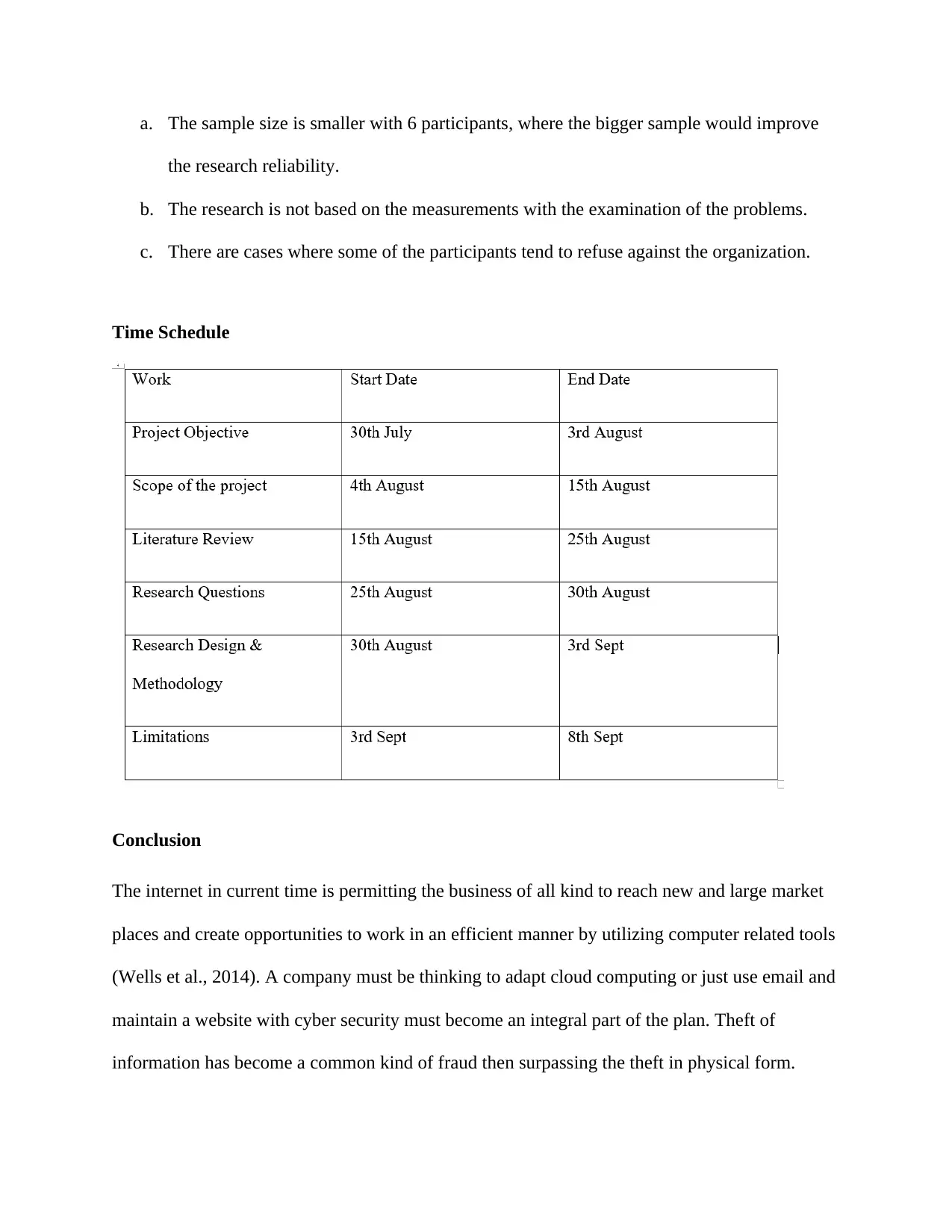
Time Schedule
Conclusion
The internet in current time is permitting the business of all kind to reach new and large market
places and create opportunities to work in an efficient manner by utilizing computer related tools
(Wells et al., 2014). A company must be thinking to adapt cloud computing or just use email and
maintain a website with cyber security must become an integral part of the plan. Theft of
information has become a common kind of fraud then surpassing the theft in physical form.
the research reliability.
b. The research is not based on the measurements with the examination of the problems.
c. There are cases where some of the participants tend to refuse against the organization.
Time Schedule
Conclusion
The internet in current time is permitting the business of all kind to reach new and large market
places and create opportunities to work in an efficient manner by utilizing computer related tools
(Wells et al., 2014). A company must be thinking to adapt cloud computing or just use email and
maintain a website with cyber security must become an integral part of the plan. Theft of
information has become a common kind of fraud then surpassing the theft in physical form.

Every business that uses internet for work is accountable for creating a strong base related to
culture of security that will increase the business as well as confidence of consumers.
culture of security that will increase the business as well as confidence of consumers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Reference
Bates, A.M., Tian, D., Butler, K.R. and Moyer, T., 2015, August. Trustworthy Whole-System
Provenance for the Linux Kernel. In USENIX Security Symposium (pp. 319-334).
Bell, G. and Ebert, M., 2015. Health Care and Cyber Security: Increasing Threats Require
Increased Capabilities. KPMG.
Born, J., 2015. An assessment of the cyber security legislation and its impact on the United
States electrical sector.
Buczak, A.L. and Guven, E., 2016. A survey of data mining and machine learning methods for
cyber security intrusion detection. IEEE Communications Surveys & Tutorials, 18(2), pp.1153-
1176.
Cavelty, M.D., 2014. Breaking the cyber-security dilemma: Aligning security needs and
removing vulnerabilities. Science and Engineering Ethics, 20(3), pp.701-715.
Elmaghraby, A.S. and Losavio, M.M., 2014. Cyber security challenges in Smart Cities: Safety,
security and privacy. Journal of advanced research, 5(4), pp.491-497.
Gordon, L.A., Loeb, M.P., Lucyshyn, W. and Zhou, L., 2015. Externalities and the magnitude of
cyber security underinvestment by private sector firms: a modification of the Gordon-Loeb
model. Journal of Information Security, 6(1), p.24.
Hong, J., Liu, C.C. and Govindarasu, M., 2014. Integrated anomaly detection for cyber security
of the substations. IEEE Transactions on Smart Grid, 5(4), pp.1643-1653.
Bates, A.M., Tian, D., Butler, K.R. and Moyer, T., 2015, August. Trustworthy Whole-System
Provenance for the Linux Kernel. In USENIX Security Symposium (pp. 319-334).
Bell, G. and Ebert, M., 2015. Health Care and Cyber Security: Increasing Threats Require
Increased Capabilities. KPMG.
Born, J., 2015. An assessment of the cyber security legislation and its impact on the United
States electrical sector.
Buczak, A.L. and Guven, E., 2016. A survey of data mining and machine learning methods for
cyber security intrusion detection. IEEE Communications Surveys & Tutorials, 18(2), pp.1153-
1176.
Cavelty, M.D., 2014. Breaking the cyber-security dilemma: Aligning security needs and
removing vulnerabilities. Science and Engineering Ethics, 20(3), pp.701-715.
Elmaghraby, A.S. and Losavio, M.M., 2014. Cyber security challenges in Smart Cities: Safety,
security and privacy. Journal of advanced research, 5(4), pp.491-497.
Gordon, L.A., Loeb, M.P., Lucyshyn, W. and Zhou, L., 2015. Externalities and the magnitude of
cyber security underinvestment by private sector firms: a modification of the Gordon-Loeb
model. Journal of Information Security, 6(1), p.24.
Hong, J., Liu, C.C. and Govindarasu, M., 2014. Integrated anomaly detection for cyber security
of the substations. IEEE Transactions on Smart Grid, 5(4), pp.1643-1653.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Kwon, C., Liu, W. and Hwang, I., 2013, June. Security analysis for cyber-physical systems
against stealthy deception attacks. In American Control Conference (ACC), 2013 (pp. 3344-
3349). IEEE.
Liu, Y., Sarabi, A., Zhang, J., Naghizadeh, P., Karir, M., Bailey, M. and Liu, M., 2015, August.
Cloudy with a Chance of Breach: Forecasting Cyber Security Incidents. In USENIX Security
Symposium (pp. 1009-1024).
Oltramari, A., Ben-Asher, N., Cranor, L., Bauer, L. and Christin, N., 2014, October. General
requirements of a hybrid-modeling framework for cyber security. In Military Communications
Conference (MILCOM), 2014 IEEE (pp. 129-135). IEEE.
Overbye, T.J., Mao, Z., Shetye, K.S. and Weber, J.D., 2017, February. An interactive, extensible
environment for power system simulation on the PMU time frame with a cyber security
application. In Power and Energy Conference (TPEC), IEEE Texas (pp. 1-6). IEEE.
Robert, M. and Directorate, I.C., 2015. ISR.
Von Solms, R. and Van Niekerk, J., 2013. From information security to cyber
security. computers & security, 38, pp.97-102.
Wang, W. and Lu, Z., 2013. Cyber security in the Smart Grid: Survey and challenges. Computer
Networks, 57(5), pp.1344-1371.
Wells, L.J., Camelio, J.A., Williams, C.B. and White, J., 2014. Cyber-physical security
challenges in manufacturing systems. Manufacturing Letters, 2(2), pp.74-77.
against stealthy deception attacks. In American Control Conference (ACC), 2013 (pp. 3344-
3349). IEEE.
Liu, Y., Sarabi, A., Zhang, J., Naghizadeh, P., Karir, M., Bailey, M. and Liu, M., 2015, August.
Cloudy with a Chance of Breach: Forecasting Cyber Security Incidents. In USENIX Security
Symposium (pp. 1009-1024).
Oltramari, A., Ben-Asher, N., Cranor, L., Bauer, L. and Christin, N., 2014, October. General
requirements of a hybrid-modeling framework for cyber security. In Military Communications
Conference (MILCOM), 2014 IEEE (pp. 129-135). IEEE.
Overbye, T.J., Mao, Z., Shetye, K.S. and Weber, J.D., 2017, February. An interactive, extensible
environment for power system simulation on the PMU time frame with a cyber security
application. In Power and Energy Conference (TPEC), IEEE Texas (pp. 1-6). IEEE.
Robert, M. and Directorate, I.C., 2015. ISR.
Von Solms, R. and Van Niekerk, J., 2013. From information security to cyber
security. computers & security, 38, pp.97-102.
Wang, W. and Lu, Z., 2013. Cyber security in the Smart Grid: Survey and challenges. Computer
Networks, 57(5), pp.1344-1371.
Wells, L.J., Camelio, J.A., Williams, C.B. and White, J., 2014. Cyber-physical security
challenges in manufacturing systems. Manufacturing Letters, 2(2), pp.74-77.

⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





