Cyber Security Management Report: Shipping Industry Challenges
VerifiedAdded on 2021/06/15
|18
|3911
|54
Report
AI Summary
This report delves into the critical aspects of cyber security management within the shipping industry, addressing the growing threats and challenges posed by digitalization and interconnected systems. It begins with an overview of the IT environment in modern shipping, highlighting the integration of technology and the resulting vulnerabilities. The report then explores the NIST framework for cyber security, emphasizing its role in managing and expressing cyber security risks. A significant portion is dedicated to cyber security management, including planning, risk assessment, and mitigation strategies. Key network security issues, such as cyber-attacks, DoS attacks, phishing, and cloud attacks, are examined in detail. The report proposes a seven-layer network security model to address these issues. Finally, the report concludes with recommendations for enhancing cyber security in the shipping industry, ensuring the protection of data, systems, and operations. The report also highlights the significance of proactive measures and continuous monitoring to safeguard against evolving threats.

Running head: CYBER SECURITY MANAGEMENT
Cyber Security management
Name of the Student
Name of the University
Author’s Note
Cyber Security management
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
CYBER SECURITY MANAGEMENT
Table of Contents
Introduction......................................................................................................................................3
Description of IT environment........................................................................................................3
NIST framework..........................................................................................................................4
Cyber Security Management...........................................................................................................4
Network Security issues..................................................................................................................7
Network Security Model................................................................................................................10
Conclusion.....................................................................................................................................14
Recommendations..........................................................................................................................14
References......................................................................................................................................16
CYBER SECURITY MANAGEMENT
Table of Contents
Introduction......................................................................................................................................3
Description of IT environment........................................................................................................3
NIST framework..........................................................................................................................4
Cyber Security Management...........................................................................................................4
Network Security issues..................................................................................................................7
Network Security Model................................................................................................................10
Conclusion.....................................................................................................................................14
Recommendations..........................................................................................................................14
References......................................................................................................................................16

3
CYBER SECURITY MANAGEMENT
Introduction
Cyber security has been an important for the application of information technology in
various fields. Different cyber rusks and threats are prevailing in the marmite with the
implementation of information technology. In the shipping industry, information technology has
played an important role in providing a quality transportation services. Modern technology have
helped in creating digitalized ships and increase in the exchange of data and information.
However, this have increased in cyber-attacks and variety of threats in the internet. The Cyprus
Shipping Chamber has been facing various IT security risks and threats due to the
implementation of the digitalization and information technology. This report has focused on the
cyber security issues in the shipping industry. This report outlines about the different strategy
for mitigating these issues related to the cyber issues in the shipping industry.
Description of IT environment
In the modern world, ships have been integrated with information technology and relying
in integration, digitalization and automation. These advancement in the shipping industry have
been helping in providing a keen approach towards the benefits and quality transportation
through water. However, this integration system has been increasing the accessibility of the ships
for transportation (Bonaci et al. 2015). The safety, environmental and commercial consequences
of the cyber security issues have been significantly affecting the shipping industry. The response
to increasing cyber threat have been supported with various group of stakeholders in the
companies. The stakeholders are responsible for maintaining the cyber threats included in
shipping industry. The use of various information technology at different parts of the ship have
been helping in different ways for providing a better (Bush et al. 2015). This case study has been
CYBER SECURITY MANAGEMENT
Introduction
Cyber security has been an important for the application of information technology in
various fields. Different cyber rusks and threats are prevailing in the marmite with the
implementation of information technology. In the shipping industry, information technology has
played an important role in providing a quality transportation services. Modern technology have
helped in creating digitalized ships and increase in the exchange of data and information.
However, this have increased in cyber-attacks and variety of threats in the internet. The Cyprus
Shipping Chamber has been facing various IT security risks and threats due to the
implementation of the digitalization and information technology. This report has focused on the
cyber security issues in the shipping industry. This report outlines about the different strategy
for mitigating these issues related to the cyber issues in the shipping industry.
Description of IT environment
In the modern world, ships have been integrated with information technology and relying
in integration, digitalization and automation. These advancement in the shipping industry have
been helping in providing a keen approach towards the benefits and quality transportation
through water. However, this integration system has been increasing the accessibility of the ships
for transportation (Bonaci et al. 2015). The safety, environmental and commercial consequences
of the cyber security issues have been significantly affecting the shipping industry. The response
to increasing cyber threat have been supported with various group of stakeholders in the
companies. The stakeholders are responsible for maintaining the cyber threats included in
shipping industry. The use of various information technology at different parts of the ship have
been helping in different ways for providing a better (Bush et al. 2015). This case study has been
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4
CYBER SECURITY MANAGEMENT
showing a real scenario of the implementation of information technology at various parts of the
shipping industry. With the implementation of the I technology in the shipping industry. The
cyber threats have been creating several issues in the shipping industry. Risks involved in the
shipping us dustsr have been identified in order to mitigate issues in the shipping industry.
The International Maritime Organization (IMO) has able to develop some policies in
order to provide strategies for the development of recommendation to mitigate maritime cyber
risks. The risks management to procedure in the maritime industry have been initiated by this
organization that have helped a lot to reduce cyber threats in the industry (Thakur et Al. 2015).
Cyber security has been a major threat to the shipping industry. The information technology
have helped in storing data and information of the persons on the shop and others staffs.
Therefore, this data an information is important for the shipping company as the ship will be in
the middle of the sea. The security of the ship and staffs on the ship have been dependent of the
data and information. The use of the information technology have helped in storing data and
information over the cloud and online database. Therefore, it creates a huge risks for the cyber
threats and risks in shipping industry.
NIST framework
The National Institute of Standards and Technology framework has been helping in
developing guidelines for providing security to data and information. The NIST focuses in the
understanding, managing and expressing cyber security of data and information both externally
and internally (Glantz et al. 2014). The stakeholders of the organization have been responsible
for the security of the data and information in the market. The use of the NIST help in providing
actions in reducing cyber security risks. Therefore, it helps in aligning policy and technological
approaches.
CYBER SECURITY MANAGEMENT
showing a real scenario of the implementation of information technology at various parts of the
shipping industry. With the implementation of the I technology in the shipping industry. The
cyber threats have been creating several issues in the shipping industry. Risks involved in the
shipping us dustsr have been identified in order to mitigate issues in the shipping industry.
The International Maritime Organization (IMO) has able to develop some policies in
order to provide strategies for the development of recommendation to mitigate maritime cyber
risks. The risks management to procedure in the maritime industry have been initiated by this
organization that have helped a lot to reduce cyber threats in the industry (Thakur et Al. 2015).
Cyber security has been a major threat to the shipping industry. The information technology
have helped in storing data and information of the persons on the shop and others staffs.
Therefore, this data an information is important for the shipping company as the ship will be in
the middle of the sea. The security of the ship and staffs on the ship have been dependent of the
data and information. The use of the information technology have helped in storing data and
information over the cloud and online database. Therefore, it creates a huge risks for the cyber
threats and risks in shipping industry.
NIST framework
The National Institute of Standards and Technology framework has been helping in
developing guidelines for providing security to data and information. The NIST focuses in the
understanding, managing and expressing cyber security of data and information both externally
and internally (Glantz et al. 2014). The stakeholders of the organization have been responsible
for the security of the data and information in the market. The use of the NIST help in providing
actions in reducing cyber security risks. Therefore, it helps in aligning policy and technological
approaches.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
CYBER SECURITY MANAGEMENT
Cyber Security Management
Cyber security is concerned with availability and integrity of the safety of data and
information in the shipping industry. The use of the cyber security management in the
maintaining and monitoring the security risks sin the shipping industry. The use of the cyber
security management include various steps and stages that have been discussed below:
Plans and procedure
Planning helps in creating and maintaining a different approach to the security
assessment of the company. The company operates 100 ships including that include tankers,
bulkers and container ships. The company directly employ over 3000 employees in seven offices
worldwide. Therefore, it becomes difficult for the company a huge amount of data and
information. The use of the online database helps in maintaining a proper record of information
of employees (Borders, Syrowik David 2015). The cyber security has been creating threat for the
owners, stakeholders and other board of directors of the company. Therefore, cyber security has
been an important topic for the company to secure their data and information from the hackers.
Company employees, port agents, service vendors, equipment manufacturers, and
crewing services do introduce a significant cyber security risk for a ship’s commercial operations
due to the large number of persons routinely visiting the ship or joining as crew (Amini et al.
2015). These ship visitors are often routine in nature and are left minimally monitored while they
complete their tasks onboard. There is no company cybersecurity policy in place for ship related
services that use the ships network. Therefore, there is a requirement to identify major risks
involved in the shipping industry related to the cyber security.
CYBER SECURITY MANAGEMENT
Cyber Security Management
Cyber security is concerned with availability and integrity of the safety of data and
information in the shipping industry. The use of the cyber security management in the
maintaining and monitoring the security risks sin the shipping industry. The use of the cyber
security management include various steps and stages that have been discussed below:
Plans and procedure
Planning helps in creating and maintaining a different approach to the security
assessment of the company. The company operates 100 ships including that include tankers,
bulkers and container ships. The company directly employ over 3000 employees in seven offices
worldwide. Therefore, it becomes difficult for the company a huge amount of data and
information. The use of the online database helps in maintaining a proper record of information
of employees (Borders, Syrowik David 2015). The cyber security has been creating threat for the
owners, stakeholders and other board of directors of the company. Therefore, cyber security has
been an important topic for the company to secure their data and information from the hackers.
Company employees, port agents, service vendors, equipment manufacturers, and
crewing services do introduce a significant cyber security risk for a ship’s commercial operations
due to the large number of persons routinely visiting the ship or joining as crew (Amini et al.
2015). These ship visitors are often routine in nature and are left minimally monitored while they
complete their tasks onboard. There is no company cybersecurity policy in place for ship related
services that use the ships network. Therefore, there is a requirement to identify major risks
involved in the shipping industry related to the cyber security.

6
CYBER SECURITY MANAGEMENT
The company is currently undergoing to through a transition from the current fleet broadband
communication systems to a higher broadband capable VSAT system. This change in the system
might help in maintaining and monitoring cyber security of the ship (Malhotra 2015). The rapid
development in the maritime industry have been depending in the satellite communication
coverage. Therefore, this might help in connecting directly to the receiver section of the ships.
Ships are no longer protected by an air-gap from external systems. Today, an estimated 30,000
vessels globally have equipment providing them with constant internet access, which is an
increase from only 6,000 in 2008. However, cyber security focuses on the security of the
networks and information stired in the ship database (Hong et al. 2015). The communication
process in the ship depends on the satellite communication. Therefore, there is a chanced of
tracking and intercepting the data and information during communication.
This might create an issue and loss to the company. The security of the ships in mid ocean
becomes difficult (Carr 2016). The VSAT broadband ability of different ships have been
maintaining internet connection in the ships. The use of internet connection in the shop might
help in providing a various tendency to improve communication in the ship. Various malwares
attacks are the main threat to the ship. The communication in the ship might get hampered by
the malware attack in the network (Conti, M., Dargahi and Dehghantanha 2018). However, the
Board of Directors has helped in maintaining the cyber security of the network. Therefore, cyber
risk management include following data and information:
It helps in identifying the roles and responsibilities of users, key personnel and managing
bith on shore and abroad.
It helps in identifying assets and systems with proper assets and capabilities that might
create risks for the operations of ships and safety.
CYBER SECURITY MANAGEMENT
The company is currently undergoing to through a transition from the current fleet broadband
communication systems to a higher broadband capable VSAT system. This change in the system
might help in maintaining and monitoring cyber security of the ship (Malhotra 2015). The rapid
development in the maritime industry have been depending in the satellite communication
coverage. Therefore, this might help in connecting directly to the receiver section of the ships.
Ships are no longer protected by an air-gap from external systems. Today, an estimated 30,000
vessels globally have equipment providing them with constant internet access, which is an
increase from only 6,000 in 2008. However, cyber security focuses on the security of the
networks and information stired in the ship database (Hong et al. 2015). The communication
process in the ship depends on the satellite communication. Therefore, there is a chanced of
tracking and intercepting the data and information during communication.
This might create an issue and loss to the company. The security of the ships in mid ocean
becomes difficult (Carr 2016). The VSAT broadband ability of different ships have been
maintaining internet connection in the ships. The use of internet connection in the shop might
help in providing a various tendency to improve communication in the ship. Various malwares
attacks are the main threat to the ship. The communication in the ship might get hampered by
the malware attack in the network (Conti, M., Dargahi and Dehghantanha 2018). However, the
Board of Directors has helped in maintaining the cyber security of the network. Therefore, cyber
risk management include following data and information:
It helps in identifying the roles and responsibilities of users, key personnel and managing
bith on shore and abroad.
It helps in identifying assets and systems with proper assets and capabilities that might
create risks for the operations of ships and safety.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
7
CYBER SECURITY MANAGEMENT
It helps in implementing technical measures for protecting against a cyber-incident for
ensuring continuity of operations. This may include training and awareness, software
maintenance, remote and local access, access privileges, use of removable media and
equipment disposal.
It helps in implementing activities for preparing and responding to the cyber problems.
Network Security issues
There are various network issues can be identified in the organization:
Cyber-attacks
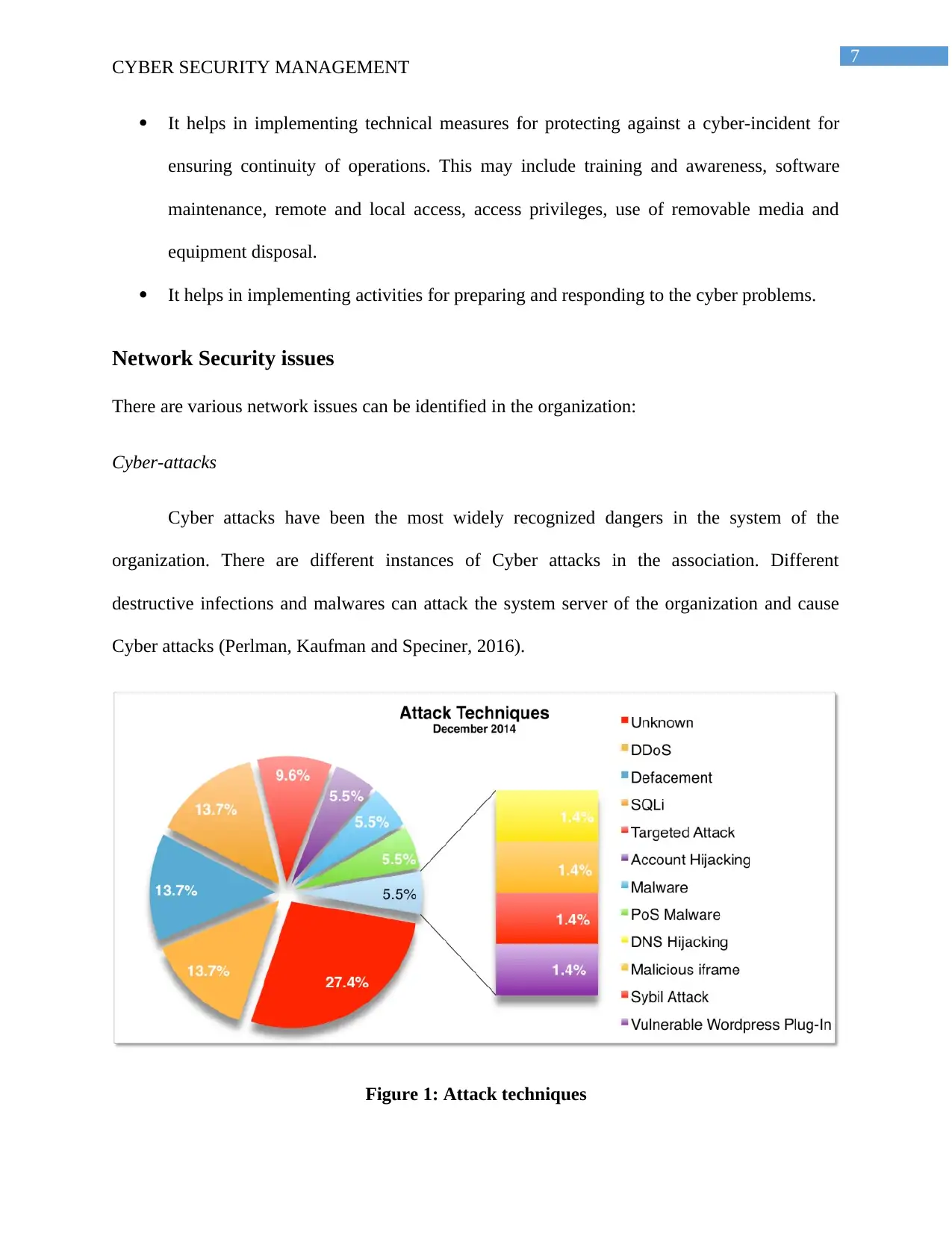
Cyber attacks have been the most widely recognized dangers in the system of the
organization. There are different instances of Cyber attacks in the association. Different
destructive infections and malwares can attack the system server of the organization and cause
Cyber attacks (Perlman, Kaufman and Speciner, 2016).
Figure 1: Attack techniques
CYBER SECURITY MANAGEMENT
It helps in implementing technical measures for protecting against a cyber-incident for
ensuring continuity of operations. This may include training and awareness, software
maintenance, remote and local access, access privileges, use of removable media and
equipment disposal.
It helps in implementing activities for preparing and responding to the cyber problems.
Network Security issues
There are various network issues can be identified in the organization:
Cyber-attacks
Cyber attacks have been the most widely recognized dangers in the system of the
organization. There are different instances of Cyber attacks in the association. Different
destructive infections and malwares can attack the system server of the organization and cause
Cyber attacks (Perlman, Kaufman and Speciner, 2016).
Figure 1: Attack techniques
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
CYBER SECURITY MANAGEMENT
(Source: Perlman, Kaufman and Speciner, 2016)
DoS attack
A denial of service attack is an attack that arrangements with closing down of system
server o the organization. This attack may shut down a machine or a server for all time by
harming the web design. It centers in the private information and data of the association in the
market. This may diminish mark estimation of the organization in the market (Kizza, 2017).
Figure 2: DoS attack
(Source: Kizza, 2017)
Phishing
This attack focuses on the individual data of the clients including the username,
passwords, managing an account data and other individual data. This attack is basically finished
with the assistance of spam messages that are sent to the clients. At the point when the clients
open that spam mail. All the login qualifications are sent to the programmers (Acemoglu,
CYBER SECURITY MANAGEMENT
(Source: Perlman, Kaufman and Speciner, 2016)
DoS attack
A denial of service attack is an attack that arrangements with closing down of system
server o the organization. This attack may shut down a machine or a server for all time by
harming the web design. It centers in the private information and data of the association in the
market. This may diminish mark estimation of the organization in the market (Kizza, 2017).
Figure 2: DoS attack
(Source: Kizza, 2017)
Phishing
This attack focuses on the individual data of the clients including the username,
passwords, managing an account data and other individual data. This attack is basically finished
with the assistance of spam messages that are sent to the clients. At the point when the clients
open that spam mail. All the login qualifications are sent to the programmers (Acemoglu,

9
CYBER SECURITY MANAGEMENT
Malekian and Ozdaglar, 2016). This can be a hazardous or the organization, as there are various
sends are gotten on their mail id.
Figure 3: Phishing attack
(Source: Acemoglu, Malekian and Ozdaglar, 2016)
Cloud attacks
Cloud computing have been a developing innovation everywhere throughout the world.
By and large, the greater part of the organization are keeping up and putting away their
information over the cloud. In this way, different programmers that have focusing on cloud for
breaking out information and data (Beberlein et al., 2017). The attacks in the cloud have been an
incredible effect in the advancement of the organization. Cloud attacks have been regular over
the web as the vast majority of the organizations are accessible in the cloud.
CYBER SECURITY MANAGEMENT
Malekian and Ozdaglar, 2016). This can be a hazardous or the organization, as there are various
sends are gotten on their mail id.
Figure 3: Phishing attack
(Source: Acemoglu, Malekian and Ozdaglar, 2016)
Cloud attacks
Cloud computing have been a developing innovation everywhere throughout the world.
By and large, the greater part of the organization are keeping up and putting away their
information over the cloud. In this way, different programmers that have focusing on cloud for
breaking out information and data (Beberlein et al., 2017). The attacks in the cloud have been an
incredible effect in the advancement of the organization. Cloud attacks have been regular over
the web as the vast majority of the organizations are accessible in the cloud.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
10
CYBER SECURITY MANAGEMENT
Figure 4: Cloud attacks
(Source: Beberlein et al., 2017)
Network Security Model
The proposed arrange security show is of seven layers that aides in partitioning the
assignment in the system framework. This model has been a nonspecific model and can be
pertinent to various security gadgets. The seven layers of the system security show incorporate
Physical, VLAN, ACL, Software, client, Administrative and IT Department.
Physical layer
The physical layer centers in the security of the system at physical level. It can be
actualized to the physical security for keeping them from getting to an office to pick up put away
on PCs and servers. Clients get associated with the frameworks through physical layer. Be that as
it may, physical layer has been the most effortless layer in the model (Frigault et al., 2017).
VLAN
The VLAN layer alludes to the support and making of the virtual neighborhood. The
VLAN help in keeping up the security of different frameworks associated together. These
CYBER SECURITY MANAGEMENT
Figure 4: Cloud attacks
(Source: Beberlein et al., 2017)
Network Security Model
The proposed arrange security show is of seven layers that aides in partitioning the
assignment in the system framework. This model has been a nonspecific model and can be
pertinent to various security gadgets. The seven layers of the system security show incorporate
Physical, VLAN, ACL, Software, client, Administrative and IT Department.
Physical layer
The physical layer centers in the security of the system at physical level. It can be
actualized to the physical security for keeping them from getting to an office to pick up put away
on PCs and servers. Clients get associated with the frameworks through physical layer. Be that as
it may, physical layer has been the most effortless layer in the model (Frigault et al., 2017).
VLAN
The VLAN layer alludes to the support and making of the virtual neighborhood. The
VLAN help in keeping up the security of different frameworks associated together. These
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11
CYBER SECURITY MANAGEMENT
associated PCs and different gadgets get attacked by various infections and interlopers for
rupturing out information and data from the system. The VLAN deals with general society and
private system (Knapp and Langill, 2014). VLAN helps in making an ensuring over the systems
that aides in shielding them from outer interlopers in the system.
ACL Layer
The Access Control Lists or ACL is security convention introduced in switches and
firewalls. This aides in permitting and denying a specific demand on various servers and hosts.
Client can put a solid access control records to confines a portion of the sites and servers to be
gotten to from the gadget. This aides in limiting the passage of hurtful components in the
systems (Larson et al., 2016). This layer helps in giving security of the product utilized as a part
of the framework. It ensures the area controller that aides in keeping up the security of the space
names of different server over the system.
Programming layer
The product layer has been concentrating on the refreshing programming introduced in
the gadget. Redesigned patches encourages in giving security to the new dangers over the web.
The utilization of the product layer helps in keeping up the propelled rendition of different
programming that expands productivity of the gadget utilized as a part of the system (Kizza,
2017). In the event that a host is legitimately refreshed and fixed accurately, a client layer attack
can be confined in the system.
Client Layer
The client layer have concentrated on the preparation and information of the client over
the security in the system. The client needs to comprehend the back idea of the system security
CYBER SECURITY MANAGEMENT
associated PCs and different gadgets get attacked by various infections and interlopers for
rupturing out information and data from the system. The VLAN deals with general society and
private system (Knapp and Langill, 2014). VLAN helps in making an ensuring over the systems
that aides in shielding them from outer interlopers in the system.
ACL Layer
The Access Control Lists or ACL is security convention introduced in switches and
firewalls. This aides in permitting and denying a specific demand on various servers and hosts.
Client can put a solid access control records to confines a portion of the sites and servers to be
gotten to from the gadget. This aides in limiting the passage of hurtful components in the
systems (Larson et al., 2016). This layer helps in giving security of the product utilized as a part
of the framework. It ensures the area controller that aides in keeping up the security of the space
names of different server over the system.
Programming layer
The product layer has been concentrating on the refreshing programming introduced in
the gadget. Redesigned patches encourages in giving security to the new dangers over the web.
The utilization of the product layer helps in keeping up the propelled rendition of different
programming that expands productivity of the gadget utilized as a part of the system (Kizza,
2017). In the event that a host is legitimately refreshed and fixed accurately, a client layer attack
can be confined in the system.
Client Layer
The client layer have concentrated on the preparation and information of the client over
the security in the system. The client needs to comprehend the back idea of the system security

12
CYBER SECURITY MANAGEMENT
over the web. The learning and preparing over the system security helps in limiting the dangers
and dangers over the system. The client has to think about the vulnerabilities that can be
executed on the system (Acemoglu, Malekian and Ozdaglar, 2016). A system security expert
may help in giving preparing and information about system security issues.
Managerial Layer
The managerial layer centers around the preparation and inspiration of the regulatory clients.
This layer incorporate every one of the individuals from administration. In this way, the
managerial clients should be taught with the learning of system security and attempt to
distinguish issue in the system of the association.
IT Department layer
The IT division layer contains all system security experts including professionals,
modelers and bolster authorities. The IT division layer have the entrance to peruse and compose
any information and data from organize (Knapp and Langill, 2014). This aides in getting to the
security conventions of the system. Its nonappearance office layer stick make chances in the
system identified with the money related loss of the organization in the market. These headway
in the delivery business have been helping in giving a sharp approach towards the advantages
and quality transportation through water. Nonetheless, this mix framework has been expanding
the openness of the boats for transportation. The wellbeing, ecological and business outcomes of
the digital security issues have been fundamentally influencing the delivery business. The
reaction to expanding digital danger have been upheld with different gathering of partners in the
organizations. The partners are in charge of keeping up the digital dangers incorporated into
transportation industry. The utilization of different data innovation at various parts of the ship
CYBER SECURITY MANAGEMENT
over the web. The learning and preparing over the system security helps in limiting the dangers
and dangers over the system. The client has to think about the vulnerabilities that can be
executed on the system (Acemoglu, Malekian and Ozdaglar, 2016). A system security expert
may help in giving preparing and information about system security issues.
Managerial Layer
The managerial layer centers around the preparation and inspiration of the regulatory clients.
This layer incorporate every one of the individuals from administration. In this way, the
managerial clients should be taught with the learning of system security and attempt to
distinguish issue in the system of the association.
IT Department layer
The IT division layer contains all system security experts including professionals,
modelers and bolster authorities. The IT division layer have the entrance to peruse and compose
any information and data from organize (Knapp and Langill, 2014). This aides in getting to the
security conventions of the system. Its nonappearance office layer stick make chances in the
system identified with the money related loss of the organization in the market. These headway
in the delivery business have been helping in giving a sharp approach towards the advantages
and quality transportation through water. Nonetheless, this mix framework has been expanding
the openness of the boats for transportation. The wellbeing, ecological and business outcomes of
the digital security issues have been fundamentally influencing the delivery business. The
reaction to expanding digital danger have been upheld with different gathering of partners in the
organizations. The partners are in charge of keeping up the digital dangers incorporated into
transportation industry. The utilization of different data innovation at various parts of the ship
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





