Wallington Trust Hospital: Cyber Security and Information Governance
VerifiedAdded on 2023/01/19
|16
|4128
|21
Report
AI Summary
This report examines cyber security threats, focusing on the need for information governance, particularly within the context of Wallington Trust Hospital. The report begins by critically assessing various cyber security threats, including the Dunkin' Donuts credential stuffing attack, Toyota's data breach, the Citrix breach, the NHS WannaCry attack, and the Phishy Wipro Breach, demonstrating the importance of proactive measures. It then justifies the approaches and purpose of an Information Security Management System (ISMS), highlighting the need for access controls, software updates, standardization, network protection, and employee training. The report further illustrates the significance of information governance, including the use of frameworks like COBIT and ISO 27001, along with risk assessment methodologies to ensure data integrity, availability, and confidentiality. The report concludes by emphasizing the critical role of information governance in mitigating cyber threats and ensuring a secure environment for organizations and their data.

Cyber Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction......................................................................................................................................3
Task 1...............................................................................................................................................4
Critically assess cyber security threats for demonstration of needs of information governance.
.....................................................................................................................................................4
Task 2...............................................................................................................................................6
Justify approaches and purpose of ISMS....................................................................................6
Task 3...............................................................................................................................................8
Illustrate significance of information governance along with risk assessment methodologies.. 8
Conclusion.....................................................................................................................................10
References .....................................................................................................................................11
Introduction......................................................................................................................................3
Task 1...............................................................................................................................................4
Critically assess cyber security threats for demonstration of needs of information governance.
.....................................................................................................................................................4
Task 2...............................................................................................................................................6
Justify approaches and purpose of ISMS....................................................................................6
Task 3...............................................................................................................................................8
Illustrate significance of information governance along with risk assessment methodologies.. 8
Conclusion.....................................................................................................................................10
References .....................................................................................................................................11

Introduction
Cyber security is defined as protecting computer system from any kind of damage or theft
to software, electronic data or hardware. It involves controls, processes and technologies which
are premeditated for protection of programs, networks, data and devices from any kind cyber
attacks (Abomhara, 2015). Efficacious cyber security eliminates the risk associated with cyber
attacks along with this; it is liable for protecting from unauthorised exploitation of technologies,
networks and systems. This report is based on Wallington Trust Hospital which is liable for
rendering secondary health services in London. It offers their patients with rehabilitation,
orthopaedics, gynaecology, neurosurgery and various other services. This report is based on
cyber security threats approaches along with information security management system.
Furthermore, significance of information governance will be illustrated.
Task 1
Critically assess cyber security threats for demonstration of needs of information governance.
The preventive techniques that are being utilised for protecting data, networks and
programs from any kind of unauthorised access, damage or attack is referred to as cyber security.
It involves protection of systems and information from cyberthreats which can be in any form
like exploit kits, phishing, ransomware and malware. The different real life case studies have
been illustrated beneath:
Dunkin's Donuts Credential Stuffing Attack: This attack took place in November 2018
but still now they are notifying their users with more number of account breaches. In this
attack, hackers got leverage into accounts of user’s credentials as they prompted them to
enter their details within DD Perks reward account. The purpose behind this was not
having personal information of users but instead they wanted to have account itself for
selling Dark Web Forums (Top 5 Cyber Security Breaches of 2019 So Far, 2019). This
attack tool place last year but still organisation has not taken any peculiar steps through
which it can be protected as same attack again occurred in the same firm. The
Cyber security is defined as protecting computer system from any kind of damage or theft
to software, electronic data or hardware. It involves controls, processes and technologies which
are premeditated for protection of programs, networks, data and devices from any kind cyber
attacks (Abomhara, 2015). Efficacious cyber security eliminates the risk associated with cyber
attacks along with this; it is liable for protecting from unauthorised exploitation of technologies,
networks and systems. This report is based on Wallington Trust Hospital which is liable for
rendering secondary health services in London. It offers their patients with rehabilitation,
orthopaedics, gynaecology, neurosurgery and various other services. This report is based on
cyber security threats approaches along with information security management system.
Furthermore, significance of information governance will be illustrated.
Task 1
Critically assess cyber security threats for demonstration of needs of information governance.
The preventive techniques that are being utilised for protecting data, networks and
programs from any kind of unauthorised access, damage or attack is referred to as cyber security.
It involves protection of systems and information from cyberthreats which can be in any form
like exploit kits, phishing, ransomware and malware. The different real life case studies have
been illustrated beneath:
Dunkin's Donuts Credential Stuffing Attack: This attack took place in November 2018
but still now they are notifying their users with more number of account breaches. In this
attack, hackers got leverage into accounts of user’s credentials as they prompted them to
enter their details within DD Perks reward account. The purpose behind this was not
having personal information of users but instead they wanted to have account itself for
selling Dark Web Forums (Top 5 Cyber Security Breaches of 2019 So Far, 2019). This
attack tool place last year but still organisation has not taken any peculiar steps through
which it can be protected as same attack again occurred in the same firm. The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

organisation must have taken appropriate countermeasures through which they can be
avoided.
Toyota's second data breach: The attack took place on 29th March, 2019 and has created
impact on 3.1 million individuals. Firm is identifying whether still the cybercriminals
possess access to their data or they are able to read data (Brown, Gommers and Serrano,
2015). Unauthorised access occurred to server which was connected with network of
Toyota. The server to which intruder was able to get in do not contained details of credit
card. When this attack came into notice, the systems were made offline to make sure that
more details do not get compromised. For this they have taken appropriate
countermeasures by interacting with experts from international cyber security so that they
can prevent such attacks in future.
Citrix breach:The firm believe that cyber criminals has acquired access to their internal
network. It was reported that Iranian-backed Iridium hacker group has attacked Citrix in
December, 2018 and on 6th March, 2019 again again the attack took place which lead to a
leak of sensitive internal files which were around of 6 terabytes. This information
contained blueprints, emails and other relevant documents. Same group of hackers have
attacked around 200 government agencies and for this they have been making use of
bypassing multi-factor authentications for having access to critical services and
application via SSO and VPN channels (Collins, 2016) .
NHS WannaCry attack: On May, 2017 this ransomware attack affected lots of
organisation in which third person infected computers as well as encrypted content on
hard disk. For this they made demand for payment in the form of bitcoin for decrypting it.
Cost of around £92m was declined as appointments were being cancelled. Due to the
cyber attack near about 2,00,000 computers of users were locked with an red-lettered
error message. Similarly, other firms were also impacted by this and lots of data was lost.
Phishy Wipro Breach: It was observed that the systems of Wipro (which is a consulting
and outsourcing giant) acted as a jumping-off points for digital phishing expeditions
which target various customer systems. The customers traced suspicious & malicious
network reconnaissance activities which were being carried back to their partner systems
which were then directly communicated within the network of Wipro. The breach was
restricted to only few employees and there systems were phished.
avoided.
Toyota's second data breach: The attack took place on 29th March, 2019 and has created
impact on 3.1 million individuals. Firm is identifying whether still the cybercriminals
possess access to their data or they are able to read data (Brown, Gommers and Serrano,
2015). Unauthorised access occurred to server which was connected with network of
Toyota. The server to which intruder was able to get in do not contained details of credit
card. When this attack came into notice, the systems were made offline to make sure that
more details do not get compromised. For this they have taken appropriate
countermeasures by interacting with experts from international cyber security so that they
can prevent such attacks in future.
Citrix breach:The firm believe that cyber criminals has acquired access to their internal
network. It was reported that Iranian-backed Iridium hacker group has attacked Citrix in
December, 2018 and on 6th March, 2019 again again the attack took place which lead to a
leak of sensitive internal files which were around of 6 terabytes. This information
contained blueprints, emails and other relevant documents. Same group of hackers have
attacked around 200 government agencies and for this they have been making use of
bypassing multi-factor authentications for having access to critical services and
application via SSO and VPN channels (Collins, 2016) .
NHS WannaCry attack: On May, 2017 this ransomware attack affected lots of
organisation in which third person infected computers as well as encrypted content on
hard disk. For this they made demand for payment in the form of bitcoin for decrypting it.
Cost of around £92m was declined as appointments were being cancelled. Due to the
cyber attack near about 2,00,000 computers of users were locked with an red-lettered
error message. Similarly, other firms were also impacted by this and lots of data was lost.
Phishy Wipro Breach: It was observed that the systems of Wipro (which is a consulting
and outsourcing giant) acted as a jumping-off points for digital phishing expeditions
which target various customer systems. The customers traced suspicious & malicious
network reconnaissance activities which were being carried back to their partner systems
which were then directly communicated within the network of Wipro. The breach was
restricted to only few employees and there systems were phished.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Some cyber security threats have been illustrated above and in some cases it is clear that
it was mistake of technical team of the firm like Dunkin' Donuts were not serious and they
avoided to take any relevant step. Breaches always creates a negative impact on either entire
organisation and even their customers (Graham, Olson and Howard, 2016). This implies that
there is need to opt for information governance which will ensure that appropriate measures are
being taken by which such kinds of things can be avoided by firms independently. Along with
this, organisations also need to ensure that systems they are being using are up to date as well as
are less vulnerable to threats. Furthermore, they must have monitored activities which are being
carried out on the network on regular basis so that they must be aware if any kind of illegal
activities occur (Gupta, Agrawal and Yamaguchi, 2016).
Information governance is defined as an holistic approach that is being used for
managing information of corporate through execution of metrics, controls, roles and processes
which treats data as a valuable asset of business. This will eliminate threats which might be
caused on data of Wallington Trust Hospital. An example can be taken to understand this
concept, information governance provides firm with ECM (Enterprise content management)
which acts like a strategy as well as practice for capturing, management, storage and delivery of
content & data by leveraging technology tools. ECM will render firms with an option to manage
their unstructured data.
Information security auditors are liable for analysing as well as accessing technological
infrastructure of organisation for making sure that systems and processes execute efficiently &
accurately (Hendrix, Al-Sherbaz and Bloom, 2016). Along with this, they identify IT issues
associated with risk & security management and in case if any problems are identified then they
are responsible for interacting with others as well as provide solutions for improvisation within
system or processes.
Task 2
Justify approaches and purpose of ISMS.
In context of cybersecurity, different instances have been provided above. This implies
that to have adequate results it is necessary that appropriate measures are being taken by firm for
ensuring that there systems are secured. For this different approaches can be utilised by
Wallington Trust Hospital. Cyber Security Approaches implies the way in which firm can
it was mistake of technical team of the firm like Dunkin' Donuts were not serious and they
avoided to take any relevant step. Breaches always creates a negative impact on either entire
organisation and even their customers (Graham, Olson and Howard, 2016). This implies that
there is need to opt for information governance which will ensure that appropriate measures are
being taken by which such kinds of things can be avoided by firms independently. Along with
this, organisations also need to ensure that systems they are being using are up to date as well as
are less vulnerable to threats. Furthermore, they must have monitored activities which are being
carried out on the network on regular basis so that they must be aware if any kind of illegal
activities occur (Gupta, Agrawal and Yamaguchi, 2016).
Information governance is defined as an holistic approach that is being used for
managing information of corporate through execution of metrics, controls, roles and processes
which treats data as a valuable asset of business. This will eliminate threats which might be
caused on data of Wallington Trust Hospital. An example can be taken to understand this
concept, information governance provides firm with ECM (Enterprise content management)
which acts like a strategy as well as practice for capturing, management, storage and delivery of
content & data by leveraging technology tools. ECM will render firms with an option to manage
their unstructured data.
Information security auditors are liable for analysing as well as accessing technological
infrastructure of organisation for making sure that systems and processes execute efficiently &
accurately (Hendrix, Al-Sherbaz and Bloom, 2016). Along with this, they identify IT issues
associated with risk & security management and in case if any problems are identified then they
are responsible for interacting with others as well as provide solutions for improvisation within
system or processes.
Task 2
Justify approaches and purpose of ISMS.
In context of cybersecurity, different instances have been provided above. This implies
that to have adequate results it is necessary that appropriate measures are being taken by firm for
ensuring that there systems are secured. For this different approaches can be utilised by
Wallington Trust Hospital. Cyber Security Approaches implies the way in which firm can

protect their systems from any kind of threats like malware, spyware, phishing and many others
(Johnson, 2015). The steps that can be taken by Wallington Trust Hospital to protect their
systems are illustrated beneath:
Bolster access control: The process of restricting access to virtual or physical resources
in context of what they can use as well as see is defined as access controls. Weaker
controls will leave systems and data hyper-sensitized for unauthorised access. It is
necessary for Wallington Trust Hospital that they boost up control measures through
utilisation of strong password and access control policies.
Update all software: The pop-up for software update must not be avoided as they are
crucial for health of network. It must vary from operating system to anti-virus when
newer versions of software are being released (Knowles and et. al, 2015). This needs to
be carried out by Wallington Trust Hospital as new versions comprises of fixes for
carrying out security vulnerabilities. Apart from this, manual software updates are time-
consuming therefore, it is recommended that automatic updates must be utilised for
maximum processes or programs.
Standardise software: Technical team of Wallington Trust Hospital needs to ensure that
the systems of firm are protected by making use of standardizing software. Along with
this, it is necessary that individuals must be restricted to install software within system
within prior approval. As, it is difficult to identify that which software is vulnerable on
the network (Liu and et. al, 2018). For this, all systems must have identical browser,
operating system, plugins and standardisation.
Use network protection measures: It is crucial to protect the network to ensure that third
person do not get access to it. For this effective criterion must be utilised by technical
team of Wallington Trust Hospital, they includes: installation of firewall, make sure that
proper controls are provided, IPS/IDS must be used for tracking probable packet floods,
network needs to be segmented, utilise VPN (virtual private network) and carry out
appropriate maintenance.
Employee training:It is usually observed that external threats takes place due insiders
which acts as the weaker link within the firm. For this it is mandatory for Wallington
Trust Hospital to make employees aware about network security so that they can identify
(Johnson, 2015). The steps that can be taken by Wallington Trust Hospital to protect their
systems are illustrated beneath:
Bolster access control: The process of restricting access to virtual or physical resources
in context of what they can use as well as see is defined as access controls. Weaker
controls will leave systems and data hyper-sensitized for unauthorised access. It is
necessary for Wallington Trust Hospital that they boost up control measures through
utilisation of strong password and access control policies.
Update all software: The pop-up for software update must not be avoided as they are
crucial for health of network. It must vary from operating system to anti-virus when
newer versions of software are being released (Knowles and et. al, 2015). This needs to
be carried out by Wallington Trust Hospital as new versions comprises of fixes for
carrying out security vulnerabilities. Apart from this, manual software updates are time-
consuming therefore, it is recommended that automatic updates must be utilised for
maximum processes or programs.
Standardise software: Technical team of Wallington Trust Hospital needs to ensure that
the systems of firm are protected by making use of standardizing software. Along with
this, it is necessary that individuals must be restricted to install software within system
within prior approval. As, it is difficult to identify that which software is vulnerable on
the network (Liu and et. al, 2018). For this, all systems must have identical browser,
operating system, plugins and standardisation.
Use network protection measures: It is crucial to protect the network to ensure that third
person do not get access to it. For this effective criterion must be utilised by technical
team of Wallington Trust Hospital, they includes: installation of firewall, make sure that
proper controls are provided, IPS/IDS must be used for tracking probable packet floods,
network needs to be segmented, utilise VPN (virtual private network) and carry out
appropriate maintenance.
Employee training:It is usually observed that external threats takes place due insiders
which acts as the weaker link within the firm. For this it is mandatory for Wallington
Trust Hospital to make employees aware about network security so that they can identify
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

threats id they have anything suspicious on their screen. Along with this, they must be
aware that if any kind of problem occurs then whom they should contact with.
The approach for prevention of cybersecurity has illustrated above which is necessary to
every firm that they acknowledge them for ensuring that they stay away from unwanted attacks
(Sayan, Hariri and Ball, 2017). The rationale behind this is to have a secured environment in
terms of data as well as systems. Information security management system refers to control
which firm must execute for ensuring that it is able to sensibly protect their integrity, availability
and confidentiality of assets from vulnerabilities and threats. This enables them within
assessment of risks and protecting their important assets. It implies that Wallington Trust
Hospital must make use of information governance frameworks for attaining this. This will
provide them with details related to defining, creating, usage, security, ownership as well as
permission for deleting all the data of organisation. It is liable for covering organisational roles
and models which are required for defining as well as managing processes & policies which will
affect the technical and business creation, usage and maintenance of data of enterprise (Sun,
Hahn and Liu, 2018). The rationale behind this is that it will render audit trails, ECM, access
governance, information lifecycle management and many others.
COBIT framework: A control objective for information and related technology is developed
for management as well as IT governance. This can be used by Wallington Trust Hospital like a
supportive tool that will bridge gap in between control requirements, technical issues and risks.
aware that if any kind of problem occurs then whom they should contact with.
The approach for prevention of cybersecurity has illustrated above which is necessary to
every firm that they acknowledge them for ensuring that they stay away from unwanted attacks
(Sayan, Hariri and Ball, 2017). The rationale behind this is to have a secured environment in
terms of data as well as systems. Information security management system refers to control
which firm must execute for ensuring that it is able to sensibly protect their integrity, availability
and confidentiality of assets from vulnerabilities and threats. This enables them within
assessment of risks and protecting their important assets. It implies that Wallington Trust
Hospital must make use of information governance frameworks for attaining this. This will
provide them with details related to defining, creating, usage, security, ownership as well as
permission for deleting all the data of organisation. It is liable for covering organisational roles
and models which are required for defining as well as managing processes & policies which will
affect the technical and business creation, usage and maintenance of data of enterprise (Sun,
Hahn and Liu, 2018). The rationale behind this is that it will render audit trails, ECM, access
governance, information lifecycle management and many others.
COBIT framework: A control objective for information and related technology is developed
for management as well as IT governance. This can be used by Wallington Trust Hospital like a
supportive tool that will bridge gap in between control requirements, technical issues and risks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Figure 1 COBIT Framework
(Source: COBIT 4.1: Framework for IT Governance and Control, 2019)
This is responsible for making sure that quality, reliability and control is attained with
respect to information system. By using this, hospital can develop plans, organise them, and
ensure delivery, support, monitoring and evaluating system by which enhanced level of security
can be attained. This framework involves description of processes, maturity models along with
management guidelines.
ISO27001 framework: It is an international standard that is being utilised for making sure
security in system of organisation. This entirely depends on ISMS which will allow Wallington
Trust Hospital in consistent management of information security risks, vulnerabilities and threats
associated with this. Along with this, it will assist in designing as well as execution of various
security controls for having coherent and comprehensive systems.
(Source: COBIT 4.1: Framework for IT Governance and Control, 2019)
This is responsible for making sure that quality, reliability and control is attained with
respect to information system. By using this, hospital can develop plans, organise them, and
ensure delivery, support, monitoring and evaluating system by which enhanced level of security
can be attained. This framework involves description of processes, maturity models along with
management guidelines.
ISO27001 framework: It is an international standard that is being utilised for making sure
security in system of organisation. This entirely depends on ISMS which will allow Wallington
Trust Hospital in consistent management of information security risks, vulnerabilities and threats
associated with this. Along with this, it will assist in designing as well as execution of various
security controls for having coherent and comprehensive systems.
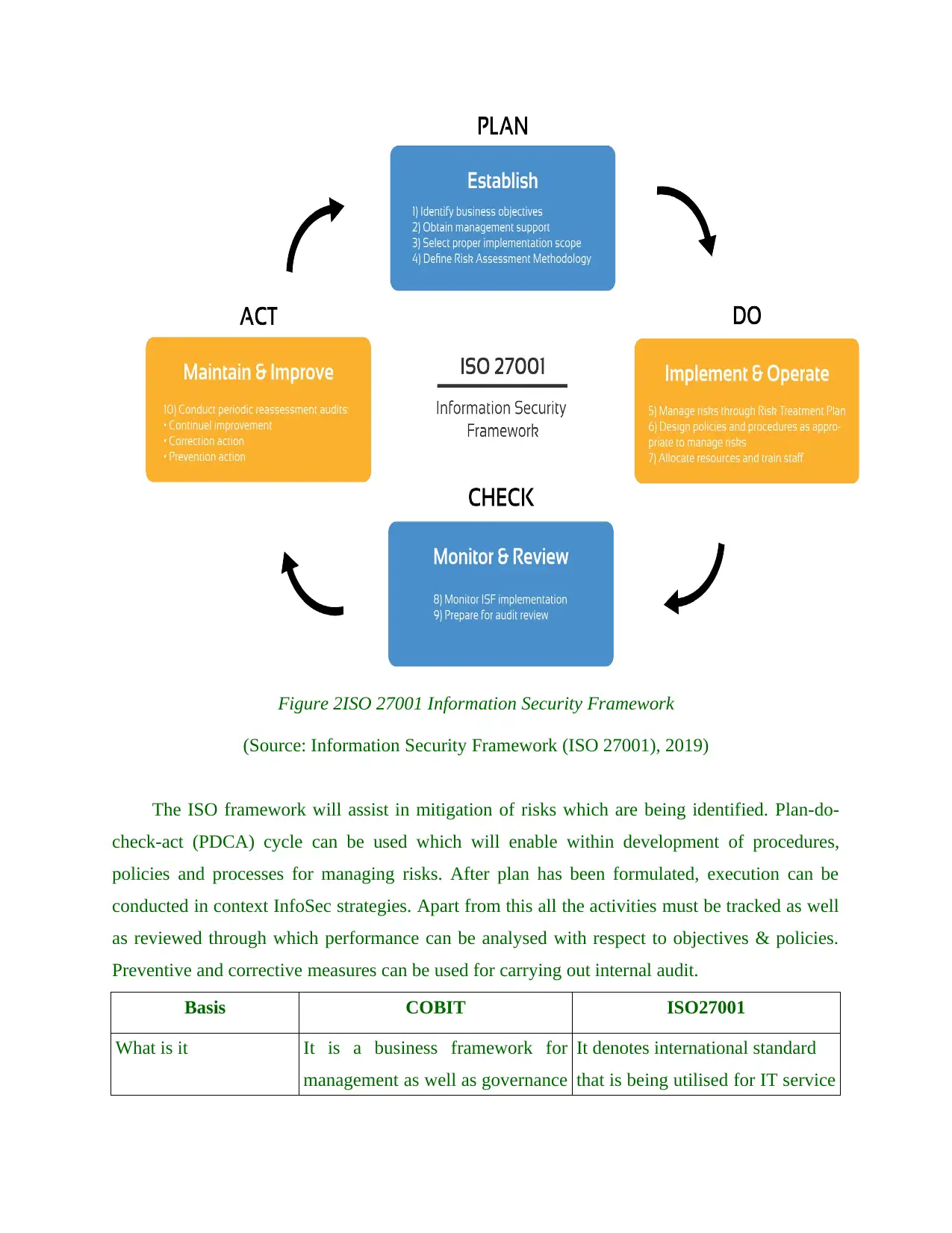
Figure 2ISO 27001 Information Security Framework
(Source: Information Security Framework (ISO 27001), 2019)
The ISO framework will assist in mitigation of risks which are being identified. Plan-do-
check-act (PDCA) cycle can be used which will enable within development of procedures,
policies and processes for managing risks. After plan has been formulated, execution can be
conducted in context InfoSec strategies. Apart from this all the activities must be tracked as well
as reviewed through which performance can be analysed with respect to objectives & policies.
Preventive and corrective measures can be used for carrying out internal audit.
Basis COBIT ISO27001
What is it It is a business framework for
management as well as governance
It denotes international standard
that is being utilised for IT service
(Source: Information Security Framework (ISO 27001), 2019)
The ISO framework will assist in mitigation of risks which are being identified. Plan-do-
check-act (PDCA) cycle can be used which will enable within development of procedures,
policies and processes for managing risks. After plan has been formulated, execution can be
conducted in context InfoSec strategies. Apart from this all the activities must be tracked as well
as reviewed through which performance can be analysed with respect to objectives & policies.
Preventive and corrective measures can be used for carrying out internal audit.
Basis COBIT ISO27001
What is it It is a business framework for
management as well as governance
It denotes international standard
that is being utilised for IT service
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

of IT enterprise. management system needs.
How it is seen within
market
This is attained from history of
compliance and audit.
It emphasise on attainment of
certification for demonstrating
compliance to standard.
Who use it Defining compliance as well as
audit needs for IT
Demonstration that IT firms
acknowledge recognised
standards.
Task 3
Illustrate significance of information governance along with risk assessment methodologies.
The process which is liable for illustrating ways in which firms handle or process data is
referred to as information governance. The relevance of this (IG) with respect to Wallington
Trust Hospital is illustrated beneath:
Know your customer (KYC): It denotes the process for identifying their customers or
clients as well as assessing risks related with criminal or legal business relationship
(THOMAS and et. al, 2019). It is crucial for Wallington Trust Hospital to ensure this to
stay away from legal troubles. This can be carried out through utilisation of information
governance.
Knowledge management: It implies discipline for creation, sharing, usage as well as
management of information and knowledge that is being held by firm for reaching
objectives of firm through optimum utilisation of knowledge. This will aid Wallington
Trust Hospital to have crucial information related with security aspects within a network.
Audit trails: They are the chronological records which render documentary evidences
related with sequence of activities that are concerned with operations, events, workflow
or any specified program (Abomhara, 2015). Through this, technical team of Wallington
Trust Hospital will be able to capture and preserve assets such as meeting records,
documents , etc.
Process/ Workflow automation: By utilising such kind of software Wallington Trust
Hospital can automate as well as digitize the repetitive and mundane aspects associated
How it is seen within
market
This is attained from history of
compliance and audit.
It emphasise on attainment of
certification for demonstrating
compliance to standard.
Who use it Defining compliance as well as
audit needs for IT
Demonstration that IT firms
acknowledge recognised
standards.
Task 3
Illustrate significance of information governance along with risk assessment methodologies.
The process which is liable for illustrating ways in which firms handle or process data is
referred to as information governance. The relevance of this (IG) with respect to Wallington
Trust Hospital is illustrated beneath:
Know your customer (KYC): It denotes the process for identifying their customers or
clients as well as assessing risks related with criminal or legal business relationship
(THOMAS and et. al, 2019). It is crucial for Wallington Trust Hospital to ensure this to
stay away from legal troubles. This can be carried out through utilisation of information
governance.
Knowledge management: It implies discipline for creation, sharing, usage as well as
management of information and knowledge that is being held by firm for reaching
objectives of firm through optimum utilisation of knowledge. This will aid Wallington
Trust Hospital to have crucial information related with security aspects within a network.
Audit trails: They are the chronological records which render documentary evidences
related with sequence of activities that are concerned with operations, events, workflow
or any specified program (Abomhara, 2015). Through this, technical team of Wallington
Trust Hospital will be able to capture and preserve assets such as meeting records,
documents , etc.
Process/ Workflow automation: By utilising such kind of software Wallington Trust
Hospital can automate as well as digitize the repetitive and mundane aspects associated
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

with information governance. This leads to enhancement within accuracy, speed as well
as security aspects of processes which leads to reduction within cost as well as errors.
Information governance software: Technical team of Wallington Trust Hospital must
make of information governance tools such as ECM (Enterprise Content Management)
solutions and data for addressing demands of data governance (Brown, Gommers and
Serrano, 2015). Along with this, employees must be provided with different tools to
render their services as per desired standard.
Figure 3 Information Governance
(Source: What is Information Governance and how does it differ from Data Governance?, 2019)
Through appropriate utilisation of information governance Wallington Trust Hospital can
ensure that relevant standards are being formulated which enables them to deliver their services
accordingly.
Risk assessment refers to systematic process for evaluation of potential risks which might
create pessimistic effect on assets, environment and individuals. For this Wallington Trust
Hospital can opt for either quantitative or qualitative methods. Some crucial aspects have been
illustrated beneath:
In context of cyber security, quantitative methods will denote formulation of algorithms
or models by which specified problem can be resolved. But since then there lies high
as security aspects of processes which leads to reduction within cost as well as errors.
Information governance software: Technical team of Wallington Trust Hospital must
make of information governance tools such as ECM (Enterprise Content Management)
solutions and data for addressing demands of data governance (Brown, Gommers and
Serrano, 2015). Along with this, employees must be provided with different tools to
render their services as per desired standard.
Figure 3 Information Governance
(Source: What is Information Governance and how does it differ from Data Governance?, 2019)
Through appropriate utilisation of information governance Wallington Trust Hospital can
ensure that relevant standards are being formulated which enables them to deliver their services
accordingly.
Risk assessment refers to systematic process for evaluation of potential risks which might
create pessimistic effect on assets, environment and individuals. For this Wallington Trust
Hospital can opt for either quantitative or qualitative methods. Some crucial aspects have been
illustrated beneath:
In context of cyber security, quantitative methods will denote formulation of algorithms
or models by which specified problem can be resolved. But since then there lies high

chances that model might not be that much effective and is also time consuming (Collins,
2016).
On the other hand, qualitative methods will assist within making use of existent models
by analysing benefits that are being provided by them. This method will be apt for
Wallington Trust Hospital on the basis of functionalities that are being rendered by
specified tool, firm can use it instead of bringing in something new. Along with this, it
will assist them within development of new policies and strategies to avoid security
threats.
(Source: MANAGING THIRD-PARTY CYBER RISK – NEXT LEVEL CHALLENGE, 2019)
The information assets with respect to Wallington Hospital comprises of the data of
patients, employees as well as other information related with the working structure.
The major threat is hacking through which third person can get access to their system for
misusing them or getting information from them. Vulnerabilities denote loopholes which exist within the system which might enable
intruder to get access into their system. In context of Wallington Hospital it can be
outdated systems.
Risk assessment
Illustration 1: Digital Transformation introduces Third Party Risk
2016).
On the other hand, qualitative methods will assist within making use of existent models
by analysing benefits that are being provided by them. This method will be apt for
Wallington Trust Hospital on the basis of functionalities that are being rendered by
specified tool, firm can use it instead of bringing in something new. Along with this, it
will assist them within development of new policies and strategies to avoid security
threats.
(Source: MANAGING THIRD-PARTY CYBER RISK – NEXT LEVEL CHALLENGE, 2019)
The information assets with respect to Wallington Hospital comprises of the data of
patients, employees as well as other information related with the working structure.
The major threat is hacking through which third person can get access to their system for
misusing them or getting information from them. Vulnerabilities denote loopholes which exist within the system which might enable
intruder to get access into their system. In context of Wallington Hospital it can be
outdated systems.
Risk assessment
Illustration 1: Digital Transformation introduces Third Party Risk
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





