ICTICT424/426 - Cyber Security Requirements & Emerging Technologies
VerifiedAdded on 2022/11/16
|13
|2618
|100
Report
AI Summary
This report addresses cyber security requirements and emerging technologies within an organizational context. It differentiates between threats and vulnerabilities, identifies factors influencing cyber security risk, and explores the STRIDE model for threat classification. The report also discusses the importance of Information Security Management Systems (ISMS) and principle-based approaches to IT security. It highlights the role of risk management in technology implementation projects and the benefits of cross-functional teams. Furthermore, it delves into researching emerging technologies that impact cyber security defenses and the importance of detailed planning and reviewing organizational practices for effective technology implementation. This document is available on Desklib, a platform offering a wealth of study resources, including past papers and solved assignments.

Running head: CYBER SECURITY
Cyber Security
Name of Student
Name of University
Author Note
Cyber Security
Name of Student
Name of University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
CYBER SECURITY
Table of Contents
Task 1: Threat and Vulnerability.........................................................................................2
Task 2: Cyber Security Risk................................................................................................2
Task 3: Nature of Threats and Control................................................................................3
Task 4...................................................................................................................................5
Task 5...................................................................................................................................6
Task 6...................................................................................................................................6
Task 7...................................................................................................................................6
Task 8...................................................................................................................................7
Task 9...................................................................................................................................7
Task 10.................................................................................................................................8
Task 11.................................................................................................................................8
Task 12.................................................................................................................................9
Task 13.................................................................................................................................9
Bibliography......................................................................................................................11
CYBER SECURITY
Table of Contents
Task 1: Threat and Vulnerability.........................................................................................2
Task 2: Cyber Security Risk................................................................................................2
Task 3: Nature of Threats and Control................................................................................3
Task 4...................................................................................................................................5
Task 5...................................................................................................................................6
Task 6...................................................................................................................................6
Task 7...................................................................................................................................6
Task 8...................................................................................................................................7
Task 9...................................................................................................................................7
Task 10.................................................................................................................................8
Task 11.................................................................................................................................8
Task 12.................................................................................................................................9
Task 13.................................................................................................................................9
Bibliography......................................................................................................................11

2
CYBER SECURITY
Assessment 1 – Knowledge
Task 1: Threat and Vulnerability
There are certain significant differences between a threat and a vulnerability. Threat can
be described as a possible danger that is capable of exploiting a vulnerability (Scholz 2017).
Threat is therefore, a possible danger that has the power of damaging or destroying a particular
asset.
Vulnerability can further be described as a gap in the implemented security program,
which is mainly exploited by the present threats to get an unauthorized admittance to a particular
asset.
Task 2: Cyber Security Risk
There are certain factors that affect and influences the cyber security landscape within an
organization. Identification of the main factors that determine the cyber security risk to an
organization is critically essential to understand the various risk factors penetrating in the
organization.
One key factor that determine the cyber security risk to an organization involves the
extent to which the threat can affect internal functionality of an organization. Along with that
identification of the potential consequences of a threat is another factor that determines the cyber
security risk to an organization (Burger et al. 2014). The identification of the impact of any
particular risk helps in defining the possible cyber security in the organization. The significant
factors that determines the occurrence of cyber security risk in any particular organization is
indicated as follows.
CYBER SECURITY
Assessment 1 – Knowledge
Task 1: Threat and Vulnerability
There are certain significant differences between a threat and a vulnerability. Threat can
be described as a possible danger that is capable of exploiting a vulnerability (Scholz 2017).
Threat is therefore, a possible danger that has the power of damaging or destroying a particular
asset.
Vulnerability can further be described as a gap in the implemented security program,
which is mainly exploited by the present threats to get an unauthorized admittance to a particular
asset.
Task 2: Cyber Security Risk
There are certain factors that affect and influences the cyber security landscape within an
organization. Identification of the main factors that determine the cyber security risk to an
organization is critically essential to understand the various risk factors penetrating in the
organization.
One key factor that determine the cyber security risk to an organization involves the
extent to which the threat can affect internal functionality of an organization. Along with that
identification of the potential consequences of a threat is another factor that determines the cyber
security risk to an organization (Burger et al. 2014). The identification of the impact of any
particular risk helps in defining the possible cyber security in the organization. The significant
factors that determines the occurrence of cyber security risk in any particular organization is
indicated as follows.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
CYBER SECURITY
1. The risk management process or frameworks that has been adapted in the organization.
2. The knowledge of the staffs and employees of the organization regarding the risk
management and disaster recovery
3. The availability of cyber security expert for detecting and managing the cybersecurity
risks
4. The efficiency of the risk management plan in detecting and management of the risk
and issues.
The above factors are responsible for determining the cyber security risk to an
organization. These factors are significantly related to each other. These factors indicate the
efficiency of an organization in managing and eliminating any type of cyber security risks. The
cyber security risks are manageable and the extent to which an organization is able to manage the
cyber security risks determine the cyber security risk to an organization. If an organization takes
proper measures in determination and management of the cyber security risks, the similar risks in
the organization can be reduced.
Task 3: Nature of Threats and Control
The STRIDE model of threat was established by Praerit Garg and Loren Kohnfelder at
Microsoft. The acronym STRID stands for six types of security risks, which comprise spoofing,
information disclosure, repudiation, denial of service, tampering and elevation of the privileges.
The STRIDE model indicates that the mentioned six categories of security risks are needed to be
controlled for reducing the threats and issues in an organization.
CYBER SECURITY
1. The risk management process or frameworks that has been adapted in the organization.
2. The knowledge of the staffs and employees of the organization regarding the risk
management and disaster recovery
3. The availability of cyber security expert for detecting and managing the cybersecurity
risks
4. The efficiency of the risk management plan in detecting and management of the risk
and issues.
The above factors are responsible for determining the cyber security risk to an
organization. These factors are significantly related to each other. These factors indicate the
efficiency of an organization in managing and eliminating any type of cyber security risks. The
cyber security risks are manageable and the extent to which an organization is able to manage the
cyber security risks determine the cyber security risk to an organization. If an organization takes
proper measures in determination and management of the cyber security risks, the similar risks in
the organization can be reduced.
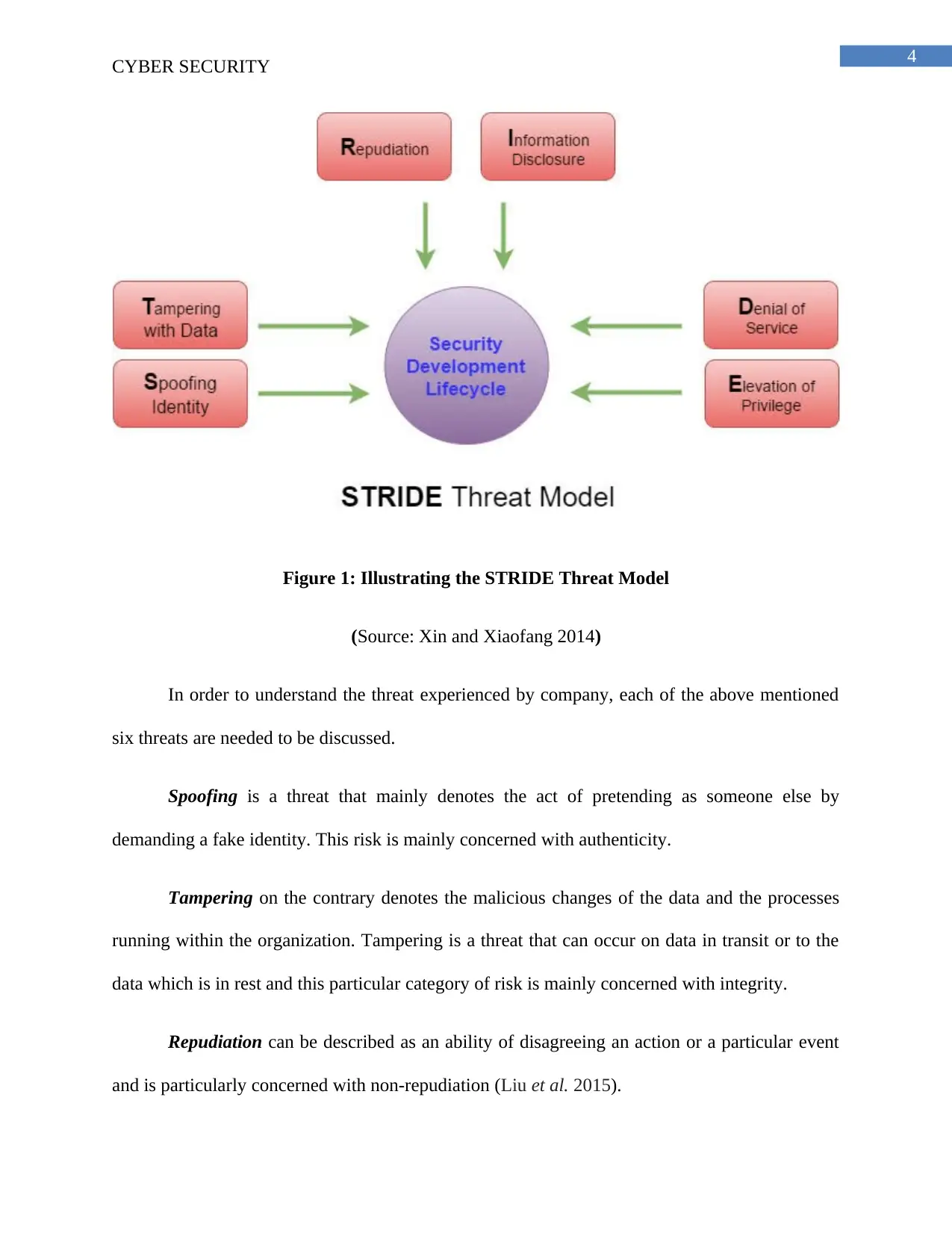
Task 3: Nature of Threats and Control
The STRIDE model of threat was established by Praerit Garg and Loren Kohnfelder at
Microsoft. The acronym STRID stands for six types of security risks, which comprise spoofing,
information disclosure, repudiation, denial of service, tampering and elevation of the privileges.
The STRIDE model indicates that the mentioned six categories of security risks are needed to be
controlled for reducing the threats and issues in an organization.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
CYBER SECURITY
Figure 1: Illustrating the STRIDE Threat Model
(Source: Xin and Xiaofang 2014)
In order to understand the threat experienced by company, each of the above mentioned
six threats are needed to be discussed.
Spoofing is a threat that mainly denotes the act of pretending as someone else by
demanding a fake identity. This risk is mainly concerned with authenticity.
Tampering on the contrary denotes the malicious changes of the data and the processes
running within the organization. Tampering is a threat that can occur on data in transit or to the
data which is in rest and this particular category of risk is mainly concerned with integrity.
Repudiation can be described as an ability of disagreeing an action or a particular event
and is particularly concerned with non-repudiation (Liu et al. 2015).
CYBER SECURITY
Figure 1: Illustrating the STRIDE Threat Model
(Source: Xin and Xiaofang 2014)
In order to understand the threat experienced by company, each of the above mentioned
six threats are needed to be discussed.
Spoofing is a threat that mainly denotes the act of pretending as someone else by
demanding a fake identity. This risk is mainly concerned with authenticity.
Tampering on the contrary denotes the malicious changes of the data and the processes
running within the organization. Tampering is a threat that can occur on data in transit or to the
data which is in rest and this particular category of risk is mainly concerned with integrity.
Repudiation can be described as an ability of disagreeing an action or a particular event
and is particularly concerned with non-repudiation (Liu et al. 2015).

5
CYBER SECURITY
Information disclosure mainly relates to the data leaks or the data breaches that is done
deliberately and is mainly concerned with data confidentiality.
Denial of Service causes an unavailability of the resources to a particular user and is
mainly concerned with data availability.
Elevation of Privileges refer to getting an access of the components that one should not
have and is mainly related to authorization.
The present situation is concerned with information disclosure that affects the
confidentiality of the data within an organization.
The controls or the mitigation approach that should have been in place for mitigating this
particular risk involves implementation of proper encryption so that the important data are not
accessed by the unauthorized personnel. If the data would have been stored in an encrypted form,
the member of the design team would not been able to disclose the information to the key
competitor of Company X.
Task 4
ISMS stands for Information Security Management System. A proper and robust security
within an organization requires installation of an ISMS and implementation of ISMS can help in
securing the information and can further increase the resilience of a company or an organization
to cyber-attacks.
ISMS 27001 defines the specification and the process in which the information security
management system should be contained within the information security policy of an
CYBER SECURITY
Information disclosure mainly relates to the data leaks or the data breaches that is done
deliberately and is mainly concerned with data confidentiality.
Denial of Service causes an unavailability of the resources to a particular user and is
mainly concerned with data availability.
Elevation of Privileges refer to getting an access of the components that one should not
have and is mainly related to authorization.
The present situation is concerned with information disclosure that affects the
confidentiality of the data within an organization.
The controls or the mitigation approach that should have been in place for mitigating this
particular risk involves implementation of proper encryption so that the important data are not
accessed by the unauthorized personnel. If the data would have been stored in an encrypted form,
the member of the design team would not been able to disclose the information to the key
competitor of Company X.
Task 4
ISMS stands for Information Security Management System. A proper and robust security
within an organization requires installation of an ISMS and implementation of ISMS can help in
securing the information and can further increase the resilience of a company or an organization
to cyber-attacks.
ISMS 27001 defines the specification and the process in which the information security
management system should be contained within the information security policy of an
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
CYBER SECURITY
organization (Candra, Briliyant and Tamba 2017). This mainly include the physical, legal and
technical controls involved with the information risk management process of an organization.
Task 5
Use of password protection for authentication may not be an effective process as it has
several vulnerability issues (Craigen, Diakun-Thibault and Purse 2014). An IT auditor can audit
a lack of password policies for enforcing a lack of security awareness on the part of users
regarding password protection. This can help in addressing the vulnerabilities of password
protection authentication.
Task 6
Implementation of a principle based approach requires a planned process of setting up the
goal and identification of the process in which the goal can be achieved. The principle based
approach is a rules based approach that is associated with the issues of fundamental safety. This
approach is therefore needed to be implemented in a workplace as an approach to IT security
(Knowles et al. 2015). A structured approach can help in management of the security risks
within an organization. This approach can be implemented by training and educating the
employees about the importance of implementation of a principles based approach in regulation
of work in practice.
Task 7
Risk management is important in an organization as it helps in organization to manage
and eliminate the main risks that can hamper the normal functionality of an organization.
CYBER SECURITY
organization (Candra, Briliyant and Tamba 2017). This mainly include the physical, legal and
technical controls involved with the information risk management process of an organization.
Task 5
Use of password protection for authentication may not be an effective process as it has
several vulnerability issues (Craigen, Diakun-Thibault and Purse 2014). An IT auditor can audit
a lack of password policies for enforcing a lack of security awareness on the part of users
regarding password protection. This can help in addressing the vulnerabilities of password
protection authentication.
Task 6
Implementation of a principle based approach requires a planned process of setting up the
goal and identification of the process in which the goal can be achieved. The principle based
approach is a rules based approach that is associated with the issues of fundamental safety. This
approach is therefore needed to be implemented in a workplace as an approach to IT security
(Knowles et al. 2015). A structured approach can help in management of the security risks
within an organization. This approach can be implemented by training and educating the
employees about the importance of implementation of a principles based approach in regulation
of work in practice.
Task 7
Risk management is important in an organization as it helps in organization to manage
and eliminate the main risks that can hamper the normal functionality of an organization.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
CYBER SECURITY
Appropriate risk management in an organization is further necessary to define and fulfil the
objectives of an organization for future (Aven 2016).
The scope of cyber security risk assessment involves identification of the various risks
that can affect the information assets of an organization (Tupa, Simota and Steiner 2017). The
cyber security risk assessment further includes the identification and authentication mechanism
for the identified risk. Therefore, the scope of cyber security risk assessment is to identify the
extent to which a risk can have an effect on an organization.
Task 8
There are certain advantages of making use of Google Scholar for research. The benefits
of using Google Scholar for research is that, it is quite familiar and relatively simple to use,
similar to Google and it allows the users to search from a variety of materials that is related to
the research topic. Apart from that, the use of google scholar is beneficial for any research as
Google Scholar is capable of displaying the links of the books that are held through ECU
libraries. It further helps in saving the citations and the articles as well.
However, there are certain issues that are linked with the use of Google Scholar. One key
issue is that even if the coverage of google scholar is wide ranging, it is not comprehensive and
therefore it cannot be the only source to be used in the research. Furthermore, this database does
not allow its users to limit the research results to either peer reviewed or to only full text
materials. The citation tracker of Google scholar is often inaccurate and can be difficult to use.
Task 9
CYBER SECURITY
Appropriate risk management in an organization is further necessary to define and fulfil the
objectives of an organization for future (Aven 2016).
The scope of cyber security risk assessment involves identification of the various risks
that can affect the information assets of an organization (Tupa, Simota and Steiner 2017). The
cyber security risk assessment further includes the identification and authentication mechanism
for the identified risk. Therefore, the scope of cyber security risk assessment is to identify the
extent to which a risk can have an effect on an organization.
Task 8
There are certain advantages of making use of Google Scholar for research. The benefits
of using Google Scholar for research is that, it is quite familiar and relatively simple to use,
similar to Google and it allows the users to search from a variety of materials that is related to
the research topic. Apart from that, the use of google scholar is beneficial for any research as
Google Scholar is capable of displaying the links of the books that are held through ECU
libraries. It further helps in saving the citations and the articles as well.
However, there are certain issues that are linked with the use of Google Scholar. One key
issue is that even if the coverage of google scholar is wide ranging, it is not comprehensive and
therefore it cannot be the only source to be used in the research. Furthermore, this database does
not allow its users to limit the research results to either peer reviewed or to only full text
materials. The citation tracker of Google scholar is often inaccurate and can be difficult to use.
Task 9

8
CYBER SECURITY
Risk management is an important tool for technology implementation projects. There are
several reasons behind the same. Risk management is described as a significant tool mainly
because it helps in identification of the several issues that can affect the implementation of the
undertaken project. Risk assessment is further important for identifying the impact of a particular
risk on the project that is being implemented. It further helps in identification of the mitigation
approaches that can reduce the negative effect of the risks in a particular technology project. Risk
assessment is important as it forms an integral part of determining a control program against a
particular hazard.
Task 10
Cross functional teams have turn out to be popular in the recent years mainly because of
three primary reasons which encompasses improving the coordination and integration, spanning
boundaries of an organization and reduction in the production cycle of the new products
developed. Furthermore, the presence of cross functional teams helps in gaining a better insight
to the problems within the project and further helps in exercising better communication skills
(Aime et al. 2014). The use of cross functional teams in implementing new technologies is
beneficial as a cross-functional team generally helps in developing effective management skills.
The improvement in coordination and integration helps in reducing the time needed for a
complete product life cycle mainly because a number of problems get easily solved when people
with various expertise and cultural background come together to deliver a successful project.
Cross-functional team is furthermore important for building up team spirit, which makes the
implementation process of a project much easier.
Task 11
CYBER SECURITY
Risk management is an important tool for technology implementation projects. There are
several reasons behind the same. Risk management is described as a significant tool mainly
because it helps in identification of the several issues that can affect the implementation of the
undertaken project. Risk assessment is further important for identifying the impact of a particular
risk on the project that is being implemented. It further helps in identification of the mitigation
approaches that can reduce the negative effect of the risks in a particular technology project. Risk
assessment is important as it forms an integral part of determining a control program against a
particular hazard.
Task 10
Cross functional teams have turn out to be popular in the recent years mainly because of
three primary reasons which encompasses improving the coordination and integration, spanning
boundaries of an organization and reduction in the production cycle of the new products
developed. Furthermore, the presence of cross functional teams helps in gaining a better insight
to the problems within the project and further helps in exercising better communication skills
(Aime et al. 2014). The use of cross functional teams in implementing new technologies is
beneficial as a cross-functional team generally helps in developing effective management skills.
The improvement in coordination and integration helps in reducing the time needed for a
complete product life cycle mainly because a number of problems get easily solved when people
with various expertise and cultural background come together to deliver a successful project.
Cross-functional team is furthermore important for building up team spirit, which makes the
implementation process of a project much easier.
Task 11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
CYBER SECURITY
a) The aim of the research to be conducted relates to identification of any emerging
technology that can impact the cyber security defences and for that I will research on the recent
breaches that has occurred and its impact on different organizations. Along with that, I will
research about the emerging technologies that are in practise or might be included as a part of the
organizational projects. The research will be conducted in a planned manner that involve
extensive research on the emerging technologies and the cyber security issues that can be a cause
of those emerging technologies.
b) The extensive research to be performed might have a significant impact on the
emerging technologies. Adoption of certain emerging technologies can get hampered if that
particular technology is found to be a cause of a major cyber security issue in an organization.
Therefore, it can be said that the research that will be performed will be a key decision maker of
the implementation process of any new technology in an organization. A lot of importance is
therefore needed to be given to the accuracy to which the research is performed so that it yields
correct results.
Task 12
After the cross-functional teams accepts the cyber security method, a detailed planning
process is needed to be enforced so that the new technology can be implemented in a proper way.
The detailed planning process includes the process in which the new technology will be
implemented along with the detailed understanding of the issues that will be a part of the
implementation of new technology. If the new technology to be implemented is associated with
any cyber security risk, the process in which those risks will be mitigated will be included in
CYBER SECURITY
a) The aim of the research to be conducted relates to identification of any emerging
technology that can impact the cyber security defences and for that I will research on the recent
breaches that has occurred and its impact on different organizations. Along with that, I will
research about the emerging technologies that are in practise or might be included as a part of the
organizational projects. The research will be conducted in a planned manner that involve
extensive research on the emerging technologies and the cyber security issues that can be a cause
of those emerging technologies.
b) The extensive research to be performed might have a significant impact on the
emerging technologies. Adoption of certain emerging technologies can get hampered if that
particular technology is found to be a cause of a major cyber security issue in an organization.
Therefore, it can be said that the research that will be performed will be a key decision maker of
the implementation process of any new technology in an organization. A lot of importance is
therefore needed to be given to the accuracy to which the research is performed so that it yields
correct results.
Task 12
After the cross-functional teams accepts the cyber security method, a detailed planning
process is needed to be enforced so that the new technology can be implemented in a proper way.
The detailed planning process includes the process in which the new technology will be
implemented along with the detailed understanding of the issues that will be a part of the
implementation of new technology. If the new technology to be implemented is associated with
any cyber security risk, the process in which those risks will be mitigated will be included in
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
CYBER SECURITY
project plan so that majority of the risks related to the implementation of the new technology can
be reduced.
Task 13
Implementation of new technology requires reviewing certain organizational practises so
that the proposed technology can be implemented in an effective manner. The implementation of
any new technology requires effective cyber resilience and reviewing the existing cyber security
and governance strategy so that the negative effects of any risks related to the proposed new
cyber security technology can be eliminated. The risk mitigation and the governance strategy
involve the organizational practises that are needed to be reviewed prior to the implementation of
any proposed new cyber security technologies.
CYBER SECURITY
project plan so that majority of the risks related to the implementation of the new technology can
be reduced.
Task 13
Implementation of new technology requires reviewing certain organizational practises so
that the proposed technology can be implemented in an effective manner. The implementation of
any new technology requires effective cyber resilience and reviewing the existing cyber security
and governance strategy so that the negative effects of any risks related to the proposed new
cyber security technology can be eliminated. The risk mitigation and the governance strategy
involve the organizational practises that are needed to be reviewed prior to the implementation of
any proposed new cyber security technologies.

11
CYBER SECURITY
Bibliography
Aime, F., Humphrey, S., DeRue, D.S. and Paul, J.B., 2014. The riddle of heterarchy: Power
transitions in cross-functional teams. Academy of Management Journal, 57(2), pp.327-352.
Aven, T., 2016. Risk assessment and risk management: Review of recent advances on their
foundation. European Journal of Operational Research, 253(1), pp.1-13.
Burger, E.W., Goodman, M.D., Kampanakis, P. and Zhu, K.A., 2014, November. Taxonomy
model for cyber threat intelligence information exchange technologies. In Proceedings of the
2014 ACM Workshop on Information Sharing & Collaborative Security (pp. 51-60). ACM.
Candra, J.W., Briliyant, O.C. and Tamba, S.R., 2017, October. ISMS planning based on ISO/IEC
27001: 2013 using analytical hierarchy process at gap analysis phase (Case study: XYZ
institute). In 2017 11th International Conference on Telecommunication Systems Services and
Applications (TSSA) (pp. 1-6). IEEE.
Craigen, D., Diakun-Thibault, N. and Purse, R., 2014. Defining cybersecurity. Technology
Innovation Management Review, 4(10).
Knowles, W., Prince, D., Hutchison, D., Disso, J.F.P. and Jones, K., 2015. A survey of cyber
security management in industrial control systems. International journal of critical
infrastructure protection, 9, pp.52-80.
Liu, Y., Sarabi, A., Zhang, J., Naghizadeh, P., Karir, M., Bailey, M. and Liu, M., 2015. Cloudy
with a chance of breach: Forecasting cyber security incidents. In 24th {USENIX} Security
Symposium ({USENIX} Security 15) (pp. 1009-1024).
Rodal Castro, P., Implementation Plan for an ISMS according to ISO/IEC 27001: 2013.
CYBER SECURITY
Bibliography
Aime, F., Humphrey, S., DeRue, D.S. and Paul, J.B., 2014. The riddle of heterarchy: Power
transitions in cross-functional teams. Academy of Management Journal, 57(2), pp.327-352.
Aven, T., 2016. Risk assessment and risk management: Review of recent advances on their
foundation. European Journal of Operational Research, 253(1), pp.1-13.
Burger, E.W., Goodman, M.D., Kampanakis, P. and Zhu, K.A., 2014, November. Taxonomy
model for cyber threat intelligence information exchange technologies. In Proceedings of the
2014 ACM Workshop on Information Sharing & Collaborative Security (pp. 51-60). ACM.
Candra, J.W., Briliyant, O.C. and Tamba, S.R., 2017, October. ISMS planning based on ISO/IEC
27001: 2013 using analytical hierarchy process at gap analysis phase (Case study: XYZ
institute). In 2017 11th International Conference on Telecommunication Systems Services and
Applications (TSSA) (pp. 1-6). IEEE.
Craigen, D., Diakun-Thibault, N. and Purse, R., 2014. Defining cybersecurity. Technology
Innovation Management Review, 4(10).
Knowles, W., Prince, D., Hutchison, D., Disso, J.F.P. and Jones, K., 2015. A survey of cyber
security management in industrial control systems. International journal of critical
infrastructure protection, 9, pp.52-80.
Liu, Y., Sarabi, A., Zhang, J., Naghizadeh, P., Karir, M., Bailey, M. and Liu, M., 2015. Cloudy
with a chance of breach: Forecasting cyber security incidents. In 24th {USENIX} Security
Symposium ({USENIX} Security 15) (pp. 1009-1024).
Rodal Castro, P., Implementation Plan for an ISMS according to ISO/IEC 27001: 2013.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





