Business Research Proposal: Analyzing Cyber Security Challenges
VerifiedAdded on 2020/03/04
|13
|2803
|140
Project
AI Summary
This research proposal investigates the challenges of cyber security in modern business environments. It begins with an introduction highlighting the increasing reliance on technology and the associated risks of cyber attacks, emphasizing the need for robust security measures. The proposal outlines the background of the research, noting the growing concern among IT experts and policymakers regarding the protection of businesses. It defines the project scope, focusing on a primary analysis using the Australian National Bank as a case study, and explains the project's objectives, including examining the impact of cyber security challenges and developing strategies to mitigate these threats. The research questions and hypotheses are presented, followed by a literature review summarizing existing studies on cyber security challenges. The methodology section details the data collection methods, including surveys and interviews, as well as the sampling methods, reliability, and validity of the research. Finally, the proposal acknowledges research limitations and provides a timeline for the project's completion.

Running head: RESEARCH PROPOSAL
Business Research Method Research Proposal
Name of the Student
Name of the University
Author Note
Business Research Method Research Proposal
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1RESEARCH PROPOSAL
Table of Content
1.1 Introduction................................................................................................................................3
1.2 Background to research.............................................................................................................4
1.3 Project Scope.............................................................................................................................4
1.4 Project Objectives and aim........................................................................................................5
1.5 Research Question and Hypotheses...........................................................................................5
1.6 Literature Review......................................................................................................................6
1.7 Research Methodology..............................................................................................................7
1.8 Research Limitation.................................................................................................................10
1.9 Research Timeline...................................................................................................................10
1.10 Conclusion.............................................................................................................................11
References and Bibliography.........................................................................................................12
Table of Content
1.1 Introduction................................................................................................................................3
1.2 Background to research.............................................................................................................4
1.3 Project Scope.............................................................................................................................4
1.4 Project Objectives and aim........................................................................................................5
1.5 Research Question and Hypotheses...........................................................................................5
1.6 Literature Review......................................................................................................................6
1.7 Research Methodology..............................................................................................................7
1.8 Research Limitation.................................................................................................................10
1.9 Research Timeline...................................................................................................................10
1.10 Conclusion.............................................................................................................................11
References and Bibliography.........................................................................................................12

2RESEARCH PROPOSAL
Topic - Challenges in Cyber Security for Business
1.1 Introduction
The proposed research is based on the challenges and issues observed in cyber security
for the business in the recent time. It has been observed that businesses are now fully
depended on the technology, which means that due to the technological advancement, the
ways of leading the business in a dynamic environment has become quite easy for the
marketers. However, even though, the technology plays a big role in today’s modern
business, due to the loophole in the technologies, the businesses often face external threats –
such as stealing valuable information, anonymous access to bank accounts or organization’s
official sites and other cyber attacks. According to Aloul et al., (2012) ICT devices as well as
elements are largely interdependent and disrupt of one could affect many others. The
Information Technology experts and the policy makers have expressed their concern
regarding the protection of businesses from the cyber attacks. Here, the acts of protecting the
ICT system as well as their contents are considered as cyber security.
In this report, a detail about the proposed research has been discussed elaborately. The
report presents the idea how the research is going to be conducted. The report provides the
project scope, which includes the determining and documenting a list of particular project
goals, features, tasks, deadline and other significant factors. Likewise, the report also
includes the key objectives of the proposed research. Considering the background to the
research, the research questions and objectives have been provided in this report.
Furthermore, the research report also includes a set of research techniques that will be
applied to the proposed study.
Topic - Challenges in Cyber Security for Business
1.1 Introduction
The proposed research is based on the challenges and issues observed in cyber security
for the business in the recent time. It has been observed that businesses are now fully
depended on the technology, which means that due to the technological advancement, the
ways of leading the business in a dynamic environment has become quite easy for the
marketers. However, even though, the technology plays a big role in today’s modern
business, due to the loophole in the technologies, the businesses often face external threats –
such as stealing valuable information, anonymous access to bank accounts or organization’s
official sites and other cyber attacks. According to Aloul et al., (2012) ICT devices as well as
elements are largely interdependent and disrupt of one could affect many others. The
Information Technology experts and the policy makers have expressed their concern
regarding the protection of businesses from the cyber attacks. Here, the acts of protecting the
ICT system as well as their contents are considered as cyber security.
In this report, a detail about the proposed research has been discussed elaborately. The
report presents the idea how the research is going to be conducted. The report provides the
project scope, which includes the determining and documenting a list of particular project
goals, features, tasks, deadline and other significant factors. Likewise, the report also
includes the key objectives of the proposed research. Considering the background to the
research, the research questions and objectives have been provided in this report.
Furthermore, the research report also includes a set of research techniques that will be
applied to the proposed study.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3RESEARCH PROPOSAL
1.2 Background to research
Several studies have been conducted to learn the impact of the issues related to cyber-
security on businesses. The current scenario indicates that the marketers rush to implement
all policies related to cyber security to protect their business from the external threats. It is
observed that the federal role in cyber security includes both securing federal system as well
as assisting in preserving the non-federal systems. A study conducted by Busch and Givens
(2012) mentioned that protecting the valuable intellectual property as well as the business
information in the digital form against the theft as well as misuse remains as the critical
management issue. Dunn Cavelty (2013) indicated in their study that organization must have
to fend off the regular cyber-attacks and the threats of cyber criminal. Dumitras and Neamtiu,
(2011) mentioned that sophisticated organizations have recently endured the public breaches
to their technological environment and many incidents went unreported but the marketers are
not eager to advertise or describe the vulnerabilities. On the other side, the study conducted
by Liu et al. (2012), mentioned that most large organizations have gradually reinforced their
cyber security capabilities over the past few years. Nonetheless, due to this argumentative
outcome, the present study observes the importance of conducting an investigation on cyber
security challenge and its impact on the businesses.
1.3 Project Scope
Understanding the importance of examining the impact of cyber-security on business, the
proposed research has been framed with a primary analysis. This will help to conduct the
analysis with the practical evidences. The proposed study abandons the secondary analysis
because the research might not provide an authentic outcome that is related to the real-world
context. In order to conduct a primary analysis, an organization- Australian National Bank
1.2 Background to research
Several studies have been conducted to learn the impact of the issues related to cyber-
security on businesses. The current scenario indicates that the marketers rush to implement
all policies related to cyber security to protect their business from the external threats. It is
observed that the federal role in cyber security includes both securing federal system as well
as assisting in preserving the non-federal systems. A study conducted by Busch and Givens
(2012) mentioned that protecting the valuable intellectual property as well as the business
information in the digital form against the theft as well as misuse remains as the critical
management issue. Dunn Cavelty (2013) indicated in their study that organization must have
to fend off the regular cyber-attacks and the threats of cyber criminal. Dumitras and Neamtiu,
(2011) mentioned that sophisticated organizations have recently endured the public breaches
to their technological environment and many incidents went unreported but the marketers are
not eager to advertise or describe the vulnerabilities. On the other side, the study conducted
by Liu et al. (2012), mentioned that most large organizations have gradually reinforced their
cyber security capabilities over the past few years. Nonetheless, due to this argumentative
outcome, the present study observes the importance of conducting an investigation on cyber
security challenge and its impact on the businesses.
1.3 Project Scope
Understanding the importance of examining the impact of cyber-security on business, the
proposed research has been framed with a primary analysis. This will help to conduct the
analysis with the practical evidences. The proposed study abandons the secondary analysis
because the research might not provide an authentic outcome that is related to the real-world
context. In order to conduct a primary analysis, an organization- Australian National Bank
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4RESEARCH PROPOSAL
will be considered as the case study organization in the proposed study. Moreover, the
proposed study also focuses on the existing studies conducted on the same topic. In order to
conduct the literature review, 20 journals have been considered and hence, the analysis will
help to find out the gaps in the previous studies. In addition to this, to collect the primary
data, a survey and interview will be conducted among the employees and senior executives
of Australian National Bank. However, the research is restricted to primary analysis only,
any sort thematic and comparative analysis will not be included in the proposed study.
Eventually, a research time line has been provided in the following, which shows how the
research has been scheduled to be conducted.
1.4 Project Objectives and aim
The major aim of the study is to examine the impact of cyber-security challenges and issues
on the business organizations. The following are the key objectives of the research:
To critically investigate the impact of cyber security challenges on the business
To critically understand the importance of protecting the business information from
the cyber attacks
To develop suitable strategies to resolve the cyber-security issues
1.5 Research Question and Hypotheses
What is the impact of cyber-security challenges on the business?
What strategies can be developed to deal with cyber-attacks?
Research Hypotheses
H0-Cyber security challenges have no impact on the businesses
will be considered as the case study organization in the proposed study. Moreover, the
proposed study also focuses on the existing studies conducted on the same topic. In order to
conduct the literature review, 20 journals have been considered and hence, the analysis will
help to find out the gaps in the previous studies. In addition to this, to collect the primary
data, a survey and interview will be conducted among the employees and senior executives
of Australian National Bank. However, the research is restricted to primary analysis only,
any sort thematic and comparative analysis will not be included in the proposed study.
Eventually, a research time line has been provided in the following, which shows how the
research has been scheduled to be conducted.
1.4 Project Objectives and aim
The major aim of the study is to examine the impact of cyber-security challenges and issues
on the business organizations. The following are the key objectives of the research:
To critically investigate the impact of cyber security challenges on the business
To critically understand the importance of protecting the business information from
the cyber attacks
To develop suitable strategies to resolve the cyber-security issues
1.5 Research Question and Hypotheses
What is the impact of cyber-security challenges on the business?
What strategies can be developed to deal with cyber-attacks?
Research Hypotheses
H0-Cyber security challenges have no impact on the businesses

5RESEARCH PROPOSAL
H1- Cyber security challenges have impact on the businesses
1.6 Literature Review
Many studies have been conducted on cyber security challenges and their impact on the
businesses. Each study has been framed with variety of requirements and techniques;
thereby, the outcome of the study came out to be different. The study conducted by Bonaci
et al., (2015) mentioned that as the technology is continuously growing to develop, the
opportunities and challenges also come out. However, as the society that runs widely on the
technology, the business, as the consequences are dependent on it. The technology also
brings the greater threats. According to Wang and Lu (2013), by the very nature of the
opportunities, the technology presents, the technology becomes a focal point for the cyber –
attacks and threats. Sridhar, Hahn and Govindarasu (2012) particularly focused on the threats
of data manipulation, identify theft and cyber-warfare that have a strong impact on the
businesses.
Moreover, the studies claim that as the world environment transitions large amount of
products and service online, the people in turn depend on them. Protecting this technology
infrastructure has now become a fundamental building block for the information system
internationally. It is understood that existing studies have focused on the type of threats and
attacks occurred in the businesses through the technological adoption but the studies have
hardly provided any relevant outcome in terms of the strategies. However, an in-depth
literature review will be conducted considering 20 different journals conducted on the present
topic.
H1- Cyber security challenges have impact on the businesses
1.6 Literature Review
Many studies have been conducted on cyber security challenges and their impact on the
businesses. Each study has been framed with variety of requirements and techniques;
thereby, the outcome of the study came out to be different. The study conducted by Bonaci
et al., (2015) mentioned that as the technology is continuously growing to develop, the
opportunities and challenges also come out. However, as the society that runs widely on the
technology, the business, as the consequences are dependent on it. The technology also
brings the greater threats. According to Wang and Lu (2013), by the very nature of the
opportunities, the technology presents, the technology becomes a focal point for the cyber –
attacks and threats. Sridhar, Hahn and Govindarasu (2012) particularly focused on the threats
of data manipulation, identify theft and cyber-warfare that have a strong impact on the
businesses.
Moreover, the studies claim that as the world environment transitions large amount of
products and service online, the people in turn depend on them. Protecting this technology
infrastructure has now become a fundamental building block for the information system
internationally. It is understood that existing studies have focused on the type of threats and
attacks occurred in the businesses through the technological adoption but the studies have
hardly provided any relevant outcome in terms of the strategies. However, an in-depth
literature review will be conducted considering 20 different journals conducted on the present
topic.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6RESEARCH PROPOSAL
1.7 Research Methodology
Research methodology determines the outcome of the study, which means the
implementation of the techniques determine the result of the study. In order to conduct the
proposed study, appropriate primary research techniques will be applied to the study. The
type of methods will be applied to the study has been discussed in the following.
Data collection methods
The data collection is usually divided into two different categories primary and secondary
data collection.
Primary data collection- The primary data collection method is categorized into two
different groups such quantitative and qualitative data collection. It is observed that
quantitative data collection techniques are based in mathematical calculation in different
formats. In the proposed study, the primary data collection techniques include the
questionnaire with the close-ended questions such as the method of correlation, mean, mode,
median and others. On the contrary, the qualitative research method does not consist of
number and mathematical calculation and this method is rather related to emotion, sounds,
voices and other relevant elements. This research methodology focuses on the level of depth
of understanding. In the proposed study, the quantitative data collection involves the survey
method, which will be conducted among the employees of Australian National Bank.
Conversely, for collecting qualitative data, interview method will be applied to the proposed
study. However, for conducting the survey and interview, a particular sampling method will
be applied, which is discussed in the following.
1.7 Research Methodology
Research methodology determines the outcome of the study, which means the
implementation of the techniques determine the result of the study. In order to conduct the
proposed study, appropriate primary research techniques will be applied to the study. The
type of methods will be applied to the study has been discussed in the following.
Data collection methods
The data collection is usually divided into two different categories primary and secondary
data collection.
Primary data collection- The primary data collection method is categorized into two
different groups such quantitative and qualitative data collection. It is observed that
quantitative data collection techniques are based in mathematical calculation in different
formats. In the proposed study, the primary data collection techniques include the
questionnaire with the close-ended questions such as the method of correlation, mean, mode,
median and others. On the contrary, the qualitative research method does not consist of
number and mathematical calculation and this method is rather related to emotion, sounds,
voices and other relevant elements. This research methodology focuses on the level of depth
of understanding. In the proposed study, the quantitative data collection involves the survey
method, which will be conducted among the employees of Australian National Bank.
Conversely, for collecting qualitative data, interview method will be applied to the proposed
study. However, for conducting the survey and interview, a particular sampling method will
be applied, which is discussed in the following.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7RESEARCH PROPOSAL
Secondary data- The secondary data will be used for conducting the literature review in
the proposed study. Almost 20 journals have been selected for conducting the literature
review. The secondary data will be collected from the journals, books, blogs, newsletter,
annual report and other reliable secondary sources. Apart from the collection of data,
reliability and validity of the papers will also be checked.
Sampling method
As put forward by Babbie (2010), sampling can be described as the particular principle
applied to make the choices of members of population to be included in the research. It is
also appropriately noted that as many population interest are very large to work directly. It
can be mentioned that because of the brad size of target population, the studies do not have
any choices besides to research a number of case elements in the population to present the
population and reach the population. For the proposed study, the sampling has been
categorized into two different categories such as probability and non-probability sampling.
In probability sampling, every individual of the population has less or zero chance of being
involved in the study. On the other side, non-probability samplings are chosen on a non-
random manner; thereby, not each population member has a chance to take part in the study.
However, in the present study, both probability and non-probability sampling method
will be applied. The probability sampling method will include the general employees of
Australian National Bank. Hence, the employees are eligible for the survey because they do
not need much knowledge about the occurrence of cyber threats and challenges and their
impact on the businesses. Conversely, the non-probability sampling method will include IT
executives and managers of Australian National Bank; certainly, they have much knowledge
Secondary data- The secondary data will be used for conducting the literature review in
the proposed study. Almost 20 journals have been selected for conducting the literature
review. The secondary data will be collected from the journals, books, blogs, newsletter,
annual report and other reliable secondary sources. Apart from the collection of data,
reliability and validity of the papers will also be checked.
Sampling method
As put forward by Babbie (2010), sampling can be described as the particular principle
applied to make the choices of members of population to be included in the research. It is
also appropriately noted that as many population interest are very large to work directly. It
can be mentioned that because of the brad size of target population, the studies do not have
any choices besides to research a number of case elements in the population to present the
population and reach the population. For the proposed study, the sampling has been
categorized into two different categories such as probability and non-probability sampling.
In probability sampling, every individual of the population has less or zero chance of being
involved in the study. On the other side, non-probability samplings are chosen on a non-
random manner; thereby, not each population member has a chance to take part in the study.
However, in the present study, both probability and non-probability sampling method
will be applied. The probability sampling method will include the general employees of
Australian National Bank. Hence, the employees are eligible for the survey because they do
not need much knowledge about the occurrence of cyber threats and challenges and their
impact on the businesses. Conversely, the non-probability sampling method will include IT
executives and managers of Australian National Bank; certainly, they have much knowledge

8RESEARCH PROPOSAL
about the type of threats, attacks, thefts and other relevant technological attacks. Thereby,
the managers and the executives are the perfect the suitable individuals among all type of
population. This means, the proposed study will include a mixed sampling method. The
sample size for the proposed survey and interview is 100 employees and 5 managers
respectively. It is identified that reliability and validity should be tested and clarified before
applying the methods to the study.
Research reliability and validity
As put forward by Wilson (2010) the reliability is referred to the extent to which the same
response can be derived with the help of the same instruments many a time. The outcome of
the proposed study will be reliable because if the analysis is made using the same interview
and survey method. Therefore, in future when other researchers will conduct the research on
the same topic, they could derive the same result with interview and survey methods. In this
context, Babbie (2010) mentioned that reliability revolves around the source and it is mostly
associated with the subjectivity. On the contrary, the data that will be collected for analysis is
validity because to conduct the research, appropriate time scale of the research along with
appropriate research method will be selected. In addition, to conduct the study, the most
suitable method for the research will be selected. Whenever, the study will be conducted with
such similar methods, the same response will come out. Moreover, it is not possible to
eliminate the threats to study’s reliability and validity but it is ensured that much effort will
be put to minimize as much risk as possible.
about the type of threats, attacks, thefts and other relevant technological attacks. Thereby,
the managers and the executives are the perfect the suitable individuals among all type of
population. This means, the proposed study will include a mixed sampling method. The
sample size for the proposed survey and interview is 100 employees and 5 managers
respectively. It is identified that reliability and validity should be tested and clarified before
applying the methods to the study.
Research reliability and validity
As put forward by Wilson (2010) the reliability is referred to the extent to which the same
response can be derived with the help of the same instruments many a time. The outcome of
the proposed study will be reliable because if the analysis is made using the same interview
and survey method. Therefore, in future when other researchers will conduct the research on
the same topic, they could derive the same result with interview and survey methods. In this
context, Babbie (2010) mentioned that reliability revolves around the source and it is mostly
associated with the subjectivity. On the contrary, the data that will be collected for analysis is
validity because to conduct the research, appropriate time scale of the research along with
appropriate research method will be selected. In addition, to conduct the study, the most
suitable method for the research will be selected. Whenever, the study will be conducted with
such similar methods, the same response will come out. Moreover, it is not possible to
eliminate the threats to study’s reliability and validity but it is ensured that much effort will
be put to minimize as much risk as possible.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9RESEARCH PROPOSAL
1.8 Research Limitation
The proposed study is limited to primary analysis only; this means that no thematic and
comparative analysis will be conducted in the proposed study. In addition to this, sample size
for the proposed study is very constrained. The study will be conducted considering one
single organization only, but the study would be more intensive, if a comparative is
conducted.
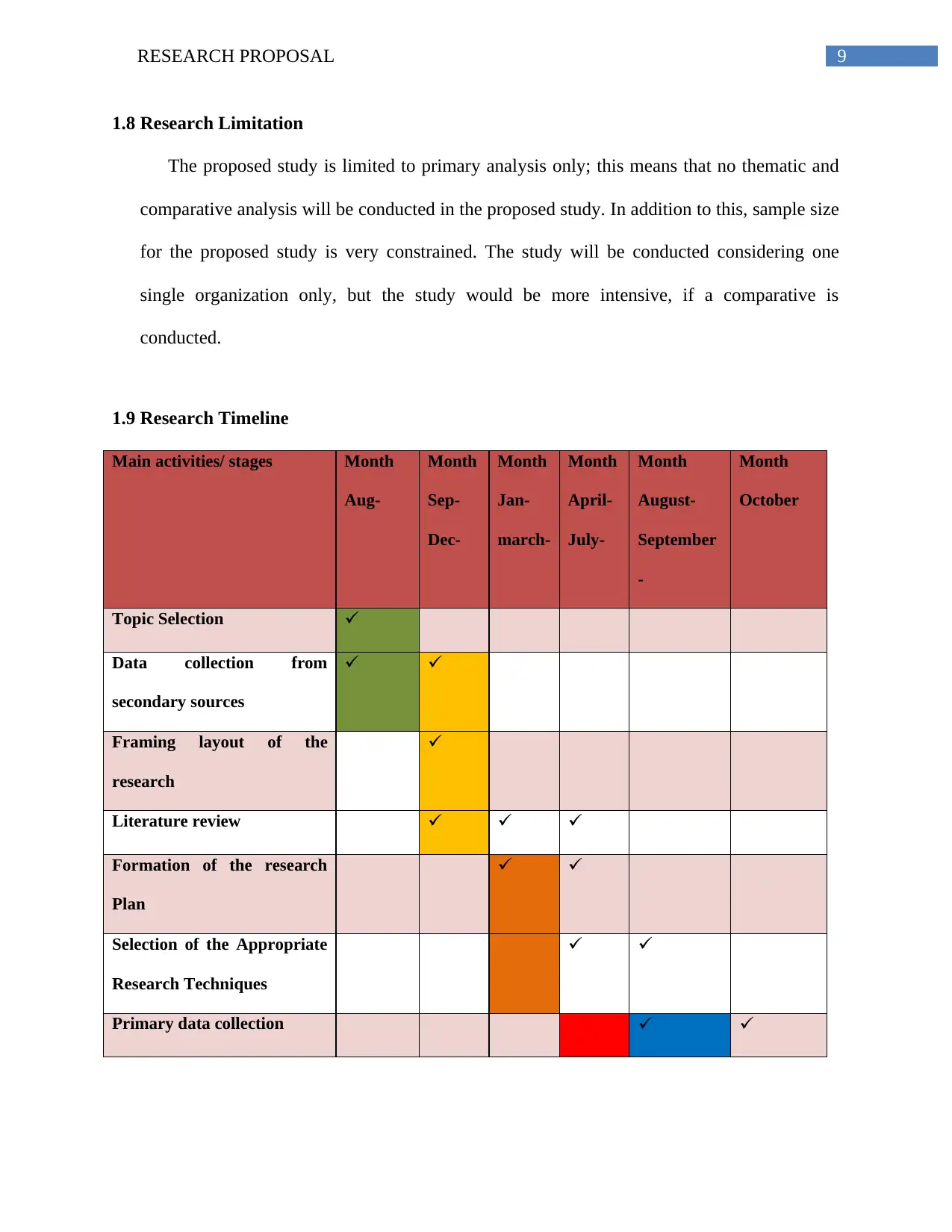
1.9 Research Timeline
Main activities/ stages Month
Aug-
Month
Sep-
Dec-
Month
Jan-
march-
Month
April-
July-
Month
August-
September
-
Month
October
Topic Selection
Data collection from
secondary sources
Framing layout of the
research
Literature review
Formation of the research
Plan
Selection of the Appropriate
Research Techniques
Primary data collection
1.8 Research Limitation
The proposed study is limited to primary analysis only; this means that no thematic and
comparative analysis will be conducted in the proposed study. In addition to this, sample size
for the proposed study is very constrained. The study will be conducted considering one
single organization only, but the study would be more intensive, if a comparative is
conducted.
1.9 Research Timeline
Main activities/ stages Month
Aug-
Month
Sep-
Dec-
Month
Jan-
march-
Month
April-
July-
Month
August-
September
-
Month
October
Topic Selection
Data collection from
secondary sources
Framing layout of the
research
Literature review
Formation of the research
Plan
Selection of the Appropriate
Research Techniques
Primary data collection
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10RESEARCH PROPOSAL
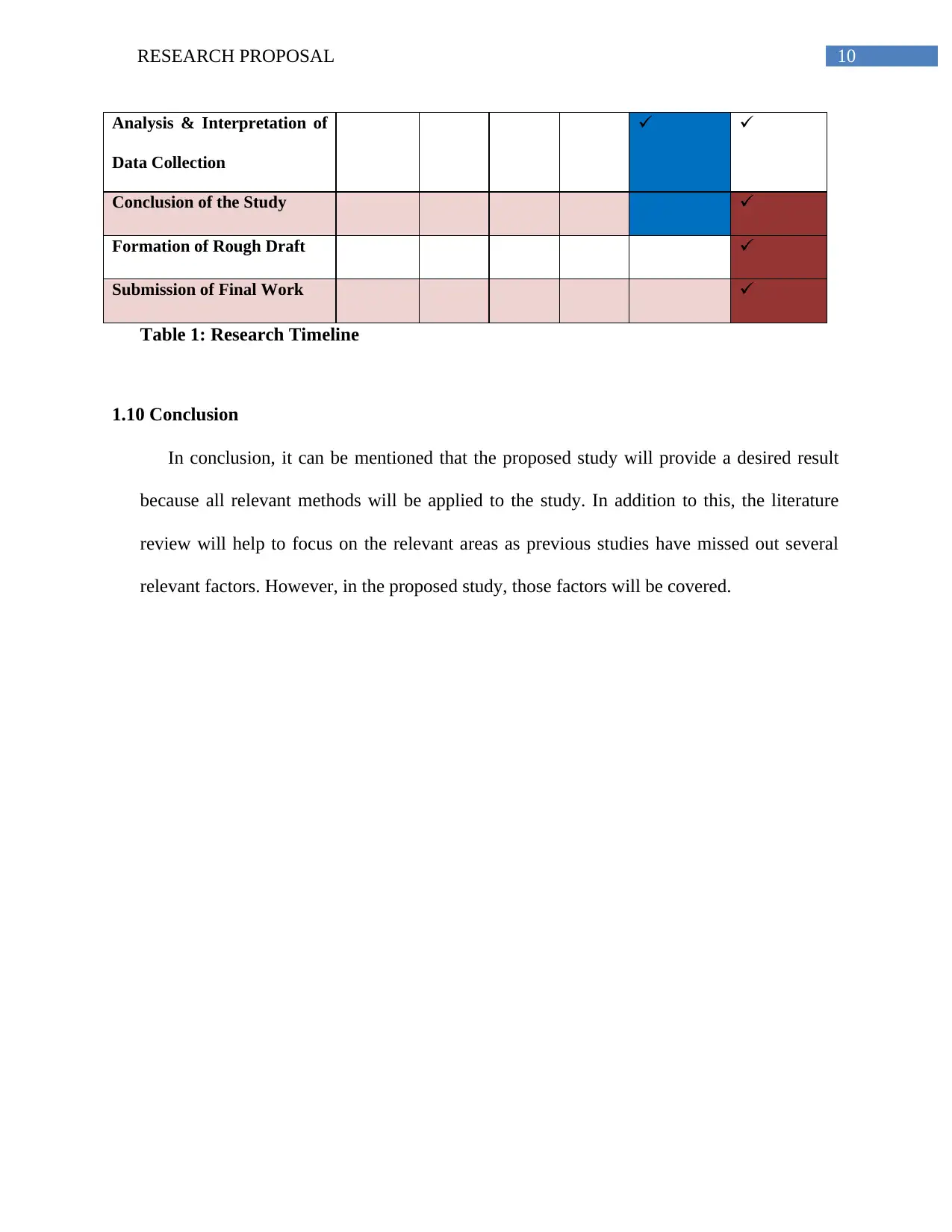
Analysis & Interpretation of
Data Collection
Conclusion of the Study
Formation of Rough Draft
Submission of Final Work
Table 1: Research Timeline
1.10 Conclusion
In conclusion, it can be mentioned that the proposed study will provide a desired result
because all relevant methods will be applied to the study. In addition to this, the literature
review will help to focus on the relevant areas as previous studies have missed out several
relevant factors. However, in the proposed study, those factors will be covered.
Analysis & Interpretation of
Data Collection
Conclusion of the Study
Formation of Rough Draft
Submission of Final Work
Table 1: Research Timeline
1.10 Conclusion
In conclusion, it can be mentioned that the proposed study will provide a desired result
because all relevant methods will be applied to the study. In addition to this, the literature
review will help to focus on the relevant areas as previous studies have missed out several
relevant factors. However, in the proposed study, those factors will be covered.

11RESEARCH PROPOSAL
References and Bibliography
Aloul, F., Al-Ali, A. R., Al-Dalky, R., Al-Mardini, M., & El-Hajj, W. (2012). Smart grid
security: Threats, vulnerabilities and solutions. International Journal of Smart Grid and
Clean Energy, 1(1), 1-6.
Babbie, E. R. (2010) The Practice of Social Research, Cengage Learning
Bonaci, T., Herron, J., Yusuf, T., Yan, J., Kohno, T., & Chizeck, H. J. (2015). To make a robot
secure: An experimental analysis of cyber security threats against teleoperated surgical
robots. arXiv preprint arXiv:1504.04339.
Busch, N. E., & Givens, A. D. (2012). Public-private partnerships in homeland security:
Opportunities and challenges. Homeland Security Affairs, 8(1).
Choo, K. K. R. (2011). The cyber threat landscape: Challenges and future research
directions. Computers & Security, 30(8), 719-731.
Dumitras, T., & Neamtiu, I. (2011). Experimental Challenges in Cyber Security: A Story of
Provenance and Lineage for Malware. CSET, 11, 2011-9.
Dunn Cavelty, M. (2013). From cyber-bombs to political fallout: Threat representations with an
impact in the cyber-security discourse. International Studies Review, 15(1), 105-122.
Line, M. B., Tøndel, I. A., & Jaatun, M. G. (2011, December). Cyber security challenges in
Smart Grids. In Innovative Smart Grid Technologies (ISGT Europe), 2011 2nd IEEE PES
International Conference and Exhibition on (pp. 1-8). IEEE.
References and Bibliography
Aloul, F., Al-Ali, A. R., Al-Dalky, R., Al-Mardini, M., & El-Hajj, W. (2012). Smart grid
security: Threats, vulnerabilities and solutions. International Journal of Smart Grid and
Clean Energy, 1(1), 1-6.
Babbie, E. R. (2010) The Practice of Social Research, Cengage Learning
Bonaci, T., Herron, J., Yusuf, T., Yan, J., Kohno, T., & Chizeck, H. J. (2015). To make a robot
secure: An experimental analysis of cyber security threats against teleoperated surgical
robots. arXiv preprint arXiv:1504.04339.
Busch, N. E., & Givens, A. D. (2012). Public-private partnerships in homeland security:
Opportunities and challenges. Homeland Security Affairs, 8(1).
Choo, K. K. R. (2011). The cyber threat landscape: Challenges and future research
directions. Computers & Security, 30(8), 719-731.
Dumitras, T., & Neamtiu, I. (2011). Experimental Challenges in Cyber Security: A Story of
Provenance and Lineage for Malware. CSET, 11, 2011-9.
Dunn Cavelty, M. (2013). From cyber-bombs to political fallout: Threat representations with an
impact in the cyber-security discourse. International Studies Review, 15(1), 105-122.
Line, M. B., Tøndel, I. A., & Jaatun, M. G. (2011, December). Cyber security challenges in
Smart Grids. In Innovative Smart Grid Technologies (ISGT Europe), 2011 2nd IEEE PES
International Conference and Exhibition on (pp. 1-8). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





