Comprehensive Report: Cyber Security and Risk Management Strategies
VerifiedAdded on 2022/07/28
|11
|2332
|89
Report
AI Summary
This report delves into the critical domain of cyber security and risk management, emphasizing its importance for organizations of all sizes. It outlines key principles, including risk identification, analysis, and treatment, alongside continuous monitoring and review. The report categorizes risks based on impact and likelihood, offering insights into data breaches, malware attacks, and threats targeting Internet of Things (IoT) devices. It underscores the significance of proactive measures like password hygiene, firewalls, and user training to mitigate risks from various sources, including hackers, insiders, and competitors. The report concludes by highlighting the evolving nature of cyber threats and the necessity for adaptable and updated security strategies. It also discusses the importance of encryption and cloud computing in protecting sensitive information, and emphasizes the constant need for vigilance and adaptation in the face of emerging technologies.

Running head: CYBER SEURITY AND RISK MANAGEMENT 1
Cyber security and risk management
Institutional affiliation
Date
Cyber security and risk management
Institutional affiliation
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CYBER SEURITY AND RISK MANAGEMENT 2
Table of Contents
Introduction.................................................................................................................................................2
Risk management principles........................................................................................................................2
Risk identifying............................................................................................................................................2
Risk analysis.................................................................................................................................................3
Risk treatment.............................................................................................................................................4
Risks categories...........................................................................................................................................4
Data breach.................................................................................................................................................5
Malware......................................................................................................................................................6
Internet of things attacks.............................................................................................................................7
Sources of data threats...............................................................................................................................7
Conclusion...................................................................................................................................................7
References...................................................................................................................................................8
Table of Contents
Introduction.................................................................................................................................................2
Risk management principles........................................................................................................................2
Risk identifying............................................................................................................................................2
Risk analysis.................................................................................................................................................3
Risk treatment.............................................................................................................................................4
Risks categories...........................................................................................................................................4
Data breach.................................................................................................................................................5
Malware......................................................................................................................................................6
Internet of things attacks.............................................................................................................................7
Sources of data threats...............................................................................................................................7
Conclusion...................................................................................................................................................7
References...................................................................................................................................................8

CYBER SEURITY AND RISK MANAGEMENT 3
Introduction
Security is vital in every organization regardless of its size. The impact of the occurrence
of risk is subject to percentage loss, and therefore the effect of the risk does not only profoundly
affect big organizations but also the small ones. Security is one of the foremost things any
organization cannot afford to gamble with. While physical organization security involves hiring
a guard, electrical fence installation, and fixing strong doors, cyber and information security
dwells on security software and firewalls: this document details cyber security and risk
management.
Cyber security is a term that encompasses the technologies, processes, and designs
adopted and used in the protection of data in networks, devices, or files from malicious attacks
and access by unauthorized persons or programs (Alali, Almogren, Hassan, Rassan, & Bhuiyan,
2018). Cyber security has exponential importance in the protection of not only intellectual but
also financial or any other important piece of information owned by the military, government, or
any private corporate. It is crucial to appreciate every piece of information on a subject is a threat
if accessed by unauthorized persons since it can be used maliciously.
Risk management principles
Risk identifying
Risk management is a process, not an event; hence a strategy with robust principals is
used to effectively manage the risks that are likely to occur in as long as computing is concerned.
The first principle of effective cyber security risk management is the identification of the risk
(Bakar, Ramli, & Hassan, 2019). It is challenging to fight or defend oneself from unknown
enemies. The risks that are likely to be listed under this principle include but not limited to the
Introduction
Security is vital in every organization regardless of its size. The impact of the occurrence
of risk is subject to percentage loss, and therefore the effect of the risk does not only profoundly
affect big organizations but also the small ones. Security is one of the foremost things any
organization cannot afford to gamble with. While physical organization security involves hiring
a guard, electrical fence installation, and fixing strong doors, cyber and information security
dwells on security software and firewalls: this document details cyber security and risk
management.
Cyber security is a term that encompasses the technologies, processes, and designs
adopted and used in the protection of data in networks, devices, or files from malicious attacks
and access by unauthorized persons or programs (Alali, Almogren, Hassan, Rassan, & Bhuiyan,
2018). Cyber security has exponential importance in the protection of not only intellectual but
also financial or any other important piece of information owned by the military, government, or
any private corporate. It is crucial to appreciate every piece of information on a subject is a threat
if accessed by unauthorized persons since it can be used maliciously.
Risk management principles
Risk identifying
Risk management is a process, not an event; hence a strategy with robust principals is
used to effectively manage the risks that are likely to occur in as long as computing is concerned.
The first principle of effective cyber security risk management is the identification of the risk
(Bakar, Ramli, & Hassan, 2019). It is challenging to fight or defend oneself from unknown
enemies. The risks that are likely to be listed under this principle include but not limited to the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CYBER SEURITY AND RISK MANAGEMENT 4
data breach, insecure application user, cloud abuse, malware attacks, data loss, single-factor
password, and shadow IT systems.
Risk analysis
Identifying these possible risks is followed by an evaluation and analysis of the impact of
the risk. The occurrence of some risks has moderate risks. In contrast, others have high impact;
hence this classification is critical, and it helps in giving priority on the risks that have high
chances of occurrence, and those have high impact when they occur. Analysis of these risks
leads to the third principle of risk management, that is, the formulation of the techniques to
control and prevent the risks as well as developing mechanisms of recovery in case the risk has
already occurred (Hemilä, Mikkola, & Salonen, 2019). It is essential to acknowledge that the
occurrence of cyber security risks is a subject with little control since the technologies in the
threats are evolving daily.
(Peterson, Adams, Sanders, & Sanford, 2018).
data breach, insecure application user, cloud abuse, malware attacks, data loss, single-factor
password, and shadow IT systems.
Risk analysis
Identifying these possible risks is followed by an evaluation and analysis of the impact of
the risk. The occurrence of some risks has moderate risks. In contrast, others have high impact;
hence this classification is critical, and it helps in giving priority on the risks that have high
chances of occurrence, and those have high impact when they occur. Analysis of these risks
leads to the third principle of risk management, that is, the formulation of the techniques to
control and prevent the risks as well as developing mechanisms of recovery in case the risk has
already occurred (Hemilä, Mikkola, & Salonen, 2019). It is essential to acknowledge that the
occurrence of cyber security risks is a subject with little control since the technologies in the
threats are evolving daily.
(Peterson, Adams, Sanders, & Sanford, 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CYBER SEURITY AND RISK MANAGEMENT 5
Risk treatment
If the risks have not occurred, mitigation strategies such as observing passwords hygiene,
firewalls, and anti-virus software can be used. However, if the risk has already occurred,
treatment efforts must come into play to recover the lost data. The principal of treatment assures
continuity of the organization's operations even after the occurrence of the given threat. The last
principle involves monitoring and reviewing the effects on the performance of the laid strategies.
If the approach seems to work well, they are improved to make them foolproof (Kruse,
Frederick, Jacobson, & Monticone, 2017). They are also substituted if they don’t function as
expected, or there exists a more feasible alternative after review.
Risks categories
It is outright that cyber security risks are broadly classified in two broad categories, that
is impact category and likelihood of occurrence. The impacts associated with the occurrence of
risk are further classified in categories of severe, major, medium, low, and insignificant (Lamba,
Singh, Balvinder, Dutta, & Rela, 2017). On the other hand, as long as the chances of occurrence
are concerned, the risks are categorized into almost certain, likely, and possible. These
classifications are then merged hence providing a blueprint of priority in management efforts.
Malicious cyber-attack associated with ex-workers attacks with the use of system password they
had been previously using in the organization is almost certain, and the impact is severe. The
severe examples of such risks may include interference with financial and procurement details of
the organization, which is detrimental. The most appropriate management in managing the
occurrence of such a risk is exercising regular and continued password changing.
Risk treatment
If the risks have not occurred, mitigation strategies such as observing passwords hygiene,
firewalls, and anti-virus software can be used. However, if the risk has already occurred,
treatment efforts must come into play to recover the lost data. The principal of treatment assures
continuity of the organization's operations even after the occurrence of the given threat. The last
principle involves monitoring and reviewing the effects on the performance of the laid strategies.
If the approach seems to work well, they are improved to make them foolproof (Kruse,
Frederick, Jacobson, & Monticone, 2017). They are also substituted if they don’t function as
expected, or there exists a more feasible alternative after review.
Risks categories
It is outright that cyber security risks are broadly classified in two broad categories, that
is impact category and likelihood of occurrence. The impacts associated with the occurrence of
risk are further classified in categories of severe, major, medium, low, and insignificant (Lamba,
Singh, Balvinder, Dutta, & Rela, 2017). On the other hand, as long as the chances of occurrence
are concerned, the risks are categorized into almost certain, likely, and possible. These
classifications are then merged hence providing a blueprint of priority in management efforts.
Malicious cyber-attack associated with ex-workers attacks with the use of system password they
had been previously using in the organization is almost certain, and the impact is severe. The
severe examples of such risks may include interference with financial and procurement details of
the organization, which is detrimental. The most appropriate management in managing the
occurrence of such a risk is exercising regular and continued password changing.

CYBER SEURITY AND RISK MANAGEMENT 6
(Sun, Hahn, & Liu, 2018).
Data breach
To effectively understand in detail the strategy to assume in the management of cyber
security risks, it is crucial to give an insight on several common risks of variant impacts after the
occurrence. Perhaps, a data breach is one of the most common cyber security risks according to
the findings of various researches on cyber security. Data is often breached on transit or the
storage space of the computing device. The impact associated with this risk is severe, and the
occurrence is almost certainly where brute force attacks and tapping data on transit or passwords
to some pieces of information are at the hands of malicious unauthorized hands (Kure, Islam, &
Razzaque, 2018). To manage the risk of data breach deserves a priority since the organization
may even halt due to data compromise on such occasions. The management in this context
involves employing the scientific techniques of data security, such as scrambling the files such
that no third party can unscramble it. This technology is known as encryption, and when
effectively used along with strong passwords that are regularly changed, the risk is effectively
managed. The use of cloud computing is also appropriate to decentralize the data hence reducing
the impact of the risk if it occurs on the data in the storage devices.
(Sun, Hahn, & Liu, 2018).
Data breach
To effectively understand in detail the strategy to assume in the management of cyber
security risks, it is crucial to give an insight on several common risks of variant impacts after the
occurrence. Perhaps, a data breach is one of the most common cyber security risks according to
the findings of various researches on cyber security. Data is often breached on transit or the
storage space of the computing device. The impact associated with this risk is severe, and the
occurrence is almost certainly where brute force attacks and tapping data on transit or passwords
to some pieces of information are at the hands of malicious unauthorized hands (Kure, Islam, &
Razzaque, 2018). To manage the risk of data breach deserves a priority since the organization
may even halt due to data compromise on such occasions. The management in this context
involves employing the scientific techniques of data security, such as scrambling the files such
that no third party can unscramble it. This technology is known as encryption, and when
effectively used along with strong passwords that are regularly changed, the risk is effectively
managed. The use of cloud computing is also appropriate to decentralize the data hence reducing
the impact of the risk if it occurs on the data in the storage devices.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
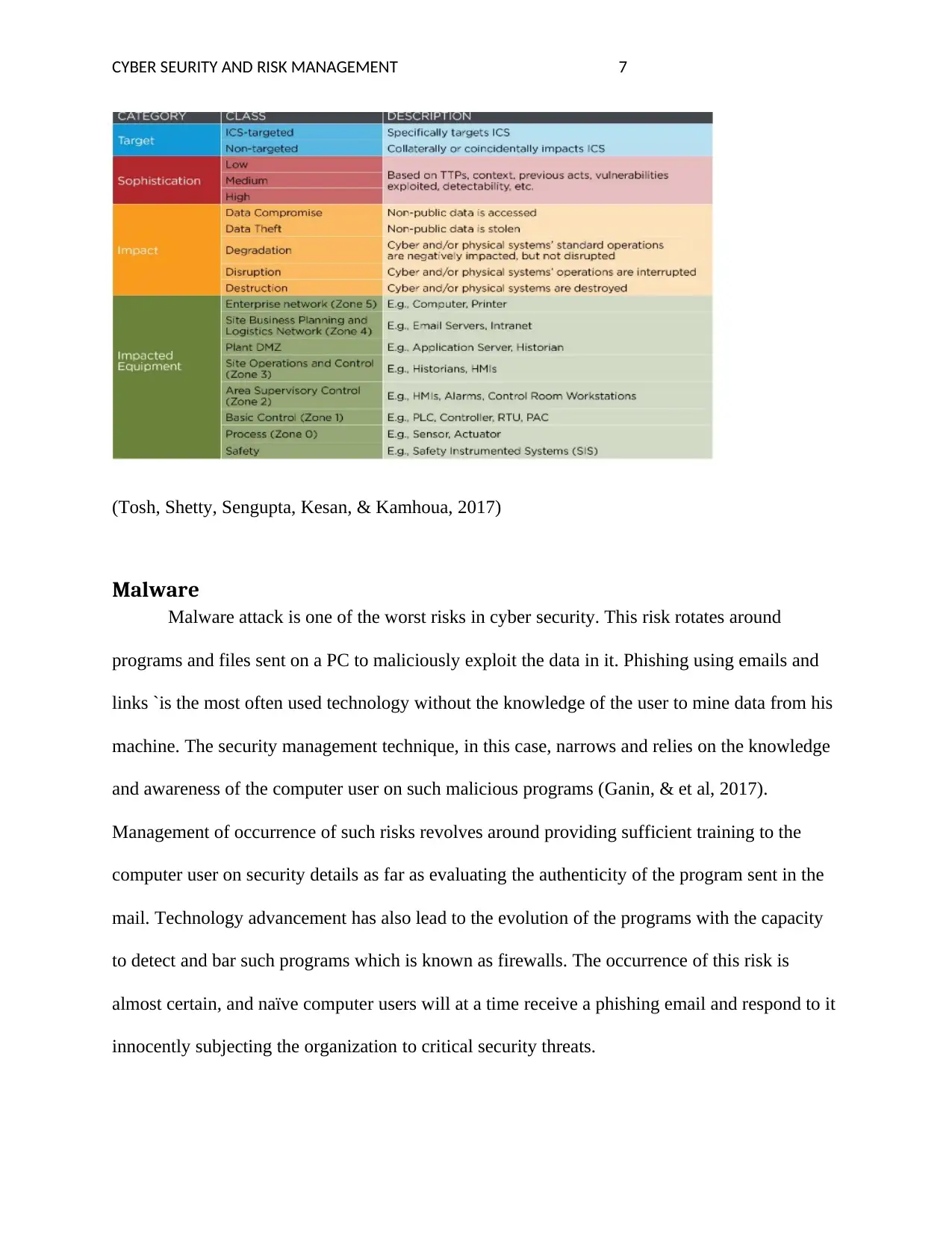
CYBER SEURITY AND RISK MANAGEMENT 7
(Tosh, Shetty, Sengupta, Kesan, & Kamhoua, 2017)
Malware
Malware attack is one of the worst risks in cyber security. This risk rotates around
programs and files sent on a PC to maliciously exploit the data in it. Phishing using emails and
links `is the most often used technology without the knowledge of the user to mine data from his
machine. The security management technique, in this case, narrows and relies on the knowledge
and awareness of the computer user on such malicious programs (Ganin, & et al, 2017).
Management of occurrence of such risks revolves around providing sufficient training to the
computer user on security details as far as evaluating the authenticity of the program sent in the
mail. Technology advancement has also lead to the evolution of the programs with the capacity
to detect and bar such programs which is known as firewalls. The occurrence of this risk is
almost certain, and naïve computer users will at a time receive a phishing email and respond to it
innocently subjecting the organization to critical security threats.
(Tosh, Shetty, Sengupta, Kesan, & Kamhoua, 2017)
Malware
Malware attack is one of the worst risks in cyber security. This risk rotates around
programs and files sent on a PC to maliciously exploit the data in it. Phishing using emails and
links `is the most often used technology without the knowledge of the user to mine data from his
machine. The security management technique, in this case, narrows and relies on the knowledge
and awareness of the computer user on such malicious programs (Ganin, & et al, 2017).
Management of occurrence of such risks revolves around providing sufficient training to the
computer user on security details as far as evaluating the authenticity of the program sent in the
mail. Technology advancement has also lead to the evolution of the programs with the capacity
to detect and bar such programs which is known as firewalls. The occurrence of this risk is
almost certain, and naïve computer users will at a time receive a phishing email and respond to it
innocently subjecting the organization to critical security threats.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CYBER SEURITY AND RISK MANAGEMENT 8
Internet of things attacks
Attacks on the internet of things devices are also roaming among the cyber security risks
in the computing world today. With their numbers, structure, functionality, and architecture are
known, tampering with their actuators; hence functionality is easy with attackers (Joshi, & Singh,
2017). The attackers target sensors and tap the data from the device, subjecting the organization
to critical security threats that could even result in the most unexpected thing, such as power
outage. Management and treatment of this security threat remain a critical challenge on the
account that the technology is still new. However, having a detailed and vast knowledge base of
the device could mitigate the occurrence of such risks.
Sources of data threats
Hackers, unhappy insiders, competitors, industrial terrorists, and nations are just a few of
the sources of cyber security risks and threats. This proves that the number and location of the
attacker are not a subject to easily predict hence a need for precaution such as practicing
passwords hygiene. This involves avoiding the use of passwords that can easily be guessed in
simple brute force attacks such as the user name and sequential numbers such as 1234 or leaving
the passwords printed or written in any manner near the device (Longley, 2019). Training
against phishing attacks is also critical to make the user aware of attacks from mails. The user are
sensitized that they should not open any email unless they are 100% sure of their sources. Since
human management to the threats is limited, the use of anti-virus software and firewall serves the
best hence commendable to use.
Conclusion
The future of cyber security threats and risks is not predictable; this implies that at n time
would a security risk management strategy or mechanism would be developed targeting to solve
Internet of things attacks
Attacks on the internet of things devices are also roaming among the cyber security risks
in the computing world today. With their numbers, structure, functionality, and architecture are
known, tampering with their actuators; hence functionality is easy with attackers (Joshi, & Singh,
2017). The attackers target sensors and tap the data from the device, subjecting the organization
to critical security threats that could even result in the most unexpected thing, such as power
outage. Management and treatment of this security threat remain a critical challenge on the
account that the technology is still new. However, having a detailed and vast knowledge base of
the device could mitigate the occurrence of such risks.
Sources of data threats
Hackers, unhappy insiders, competitors, industrial terrorists, and nations are just a few of
the sources of cyber security risks and threats. This proves that the number and location of the
attacker are not a subject to easily predict hence a need for precaution such as practicing
passwords hygiene. This involves avoiding the use of passwords that can easily be guessed in
simple brute force attacks such as the user name and sequential numbers such as 1234 or leaving
the passwords printed or written in any manner near the device (Longley, 2019). Training
against phishing attacks is also critical to make the user aware of attacks from mails. The user are
sensitized that they should not open any email unless they are 100% sure of their sources. Since
human management to the threats is limited, the use of anti-virus software and firewall serves the
best hence commendable to use.
Conclusion
The future of cyber security threats and risks is not predictable; this implies that at n time
would a security risk management strategy or mechanism would be developed targeting to solve

CYBER SEURITY AND RISK MANAGEMENT 9
the security challenges of the future. Security risks emerge with the advancement in technology;
hence the more the technology advances, the security risks also advance hence a need to
maintain updated security measures. This document details the security management strategies
that can be implemented to mitigate and treat cyber security risks and threats. The document
details the principals of a good management strategy to the risks as wells as giving an insight
into the classification of the risks and threats on the basis of occurrence and impact. The article
also details some of the common cyber security threats and how they can be mitigated or treated
if they had already occurred.
References
Alali, M., Almogren, A., Hassan, M. M., Rassan, I. A., & Bhuiyan, M. Z. A. (2018). Improving
risk assessment model of cyber security using fuzzy logic inference system. Computers &
Security, 74, 323-339.
Bakar, N. A., Ramli, W. M. W., & Hassan, N. H. (2019). The internet of things in healthcare: an
overview, challenges and model plan for security risks management process. Indonesian
Journal of Electrical Engineering and Computer Science (IJEECS), 15(1), 414-420.
the security challenges of the future. Security risks emerge with the advancement in technology;
hence the more the technology advances, the security risks also advance hence a need to
maintain updated security measures. This document details the security management strategies
that can be implemented to mitigate and treat cyber security risks and threats. The document
details the principals of a good management strategy to the risks as wells as giving an insight
into the classification of the risks and threats on the basis of occurrence and impact. The article
also details some of the common cyber security threats and how they can be mitigated or treated
if they had already occurred.
References
Alali, M., Almogren, A., Hassan, M. M., Rassan, I. A., & Bhuiyan, M. Z. A. (2018). Improving
risk assessment model of cyber security using fuzzy logic inference system. Computers &
Security, 74, 323-339.
Bakar, N. A., Ramli, W. M. W., & Hassan, N. H. (2019). The internet of things in healthcare: an
overview, challenges and model plan for security risks management process. Indonesian
Journal of Electrical Engineering and Computer Science (IJEECS), 15(1), 414-420.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CYBER SEURITY AND RISK MANAGEMENT 10
Ganin, A. A., Quach, P., Panwar, M., Collier, Z. A., Keisler, J. M., Marchese, D., & Linkov, I.
(2017). Multicriteria decision framework for cybersecurity risk assessment and
management. Risk Analysis.
Hemilä, J., Mikkola, M., & Salonen, J. (2019, December). Management of Cyber Security
Threats in the Factories of the Future Supply Chains. In 9th International Conference on
Operations and Supply Chain Management, OSCM 2019.
Joshi, C., & Singh, U. K. (2017). Information security risks management framework–A step
towards mitigating security risks in university network. Journal of Information Security
and Applications, 35, 128-137.
Kruse, C. S., Frederick, B., Jacobson, T., & Monticone, D. K. (2017). Cybersecurity in
healthcare: A systematic review of modern threats and trends. Technology and Health
Care, 25(1), 1-10.
Kure, H. I., Islam, S., & Razzaque, M. A. (2018). An integrated cyber security risk management
approach for a cyber-physical system. Applied Sciences, 8(6), 898.
Lamba, A., Singh, S., Balvinder, S., Dutta, N., & Rela, S. (2017). Mitigating Cyber Security
Threats of Industrial Control Systems (Scada & Dcs). In 3rd International Conference on
Emerging Technologies in Engineering, Biomedical, Medical and Science (ETEBMS–
July 2017).
Longley, A. (2019). Understanding and managing cyber security threats and countermeasures in
the process industries. Loss Prevention Bulletin, (268).
Ganin, A. A., Quach, P., Panwar, M., Collier, Z. A., Keisler, J. M., Marchese, D., & Linkov, I.
(2017). Multicriteria decision framework for cybersecurity risk assessment and
management. Risk Analysis.
Hemilä, J., Mikkola, M., & Salonen, J. (2019, December). Management of Cyber Security
Threats in the Factories of the Future Supply Chains. In 9th International Conference on
Operations and Supply Chain Management, OSCM 2019.
Joshi, C., & Singh, U. K. (2017). Information security risks management framework–A step
towards mitigating security risks in university network. Journal of Information Security
and Applications, 35, 128-137.
Kruse, C. S., Frederick, B., Jacobson, T., & Monticone, D. K. (2017). Cybersecurity in
healthcare: A systematic review of modern threats and trends. Technology and Health
Care, 25(1), 1-10.
Kure, H. I., Islam, S., & Razzaque, M. A. (2018). An integrated cyber security risk management
approach for a cyber-physical system. Applied Sciences, 8(6), 898.
Lamba, A., Singh, S., Balvinder, S., Dutta, N., & Rela, S. (2017). Mitigating Cyber Security
Threats of Industrial Control Systems (Scada & Dcs). In 3rd International Conference on
Emerging Technologies in Engineering, Biomedical, Medical and Science (ETEBMS–
July 2017).
Longley, A. (2019). Understanding and managing cyber security threats and countermeasures in
the process industries. Loss Prevention Bulletin, (268).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CYBER SEURITY AND RISK MANAGEMENT 11
Peterson, D. C., Adams, A., Sanders, S., & Sanford, B. (2018). Assessing and addressing threats
and risks to cybersecurity. Frontiers of health services management, 35(1), 23-29.
Sun, C. C., Hahn, A., & Liu, C. C. (2018). Cyber security of a power grid: State-of-the-
art. International Journal of Electrical Power & Energy Systems, 99, 45-56.
Tosh, D. K., Shetty, S., Sengupta, S., Kesan, J. P., & Kamhoua, C. A. (2017, May). Risk
management using cyber-threat information sharing and cyber-insurance. In International
Conference on Game Theory for Networks (pp. 154-164). Springer, Cham.
Peterson, D. C., Adams, A., Sanders, S., & Sanford, B. (2018). Assessing and addressing threats
and risks to cybersecurity. Frontiers of health services management, 35(1), 23-29.
Sun, C. C., Hahn, A., & Liu, C. C. (2018). Cyber security of a power grid: State-of-the-
art. International Journal of Electrical Power & Energy Systems, 99, 45-56.
Tosh, D. K., Shetty, S., Sengupta, S., Kesan, J. P., & Kamhoua, C. A. (2017, May). Risk
management using cyber-threat information sharing and cyber-insurance. In International
Conference on Game Theory for Networks (pp. 154-164). Springer, Cham.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





