BSc (Hons) Cyber Security: CO404 Secure Systems Risk Management Report
VerifiedAdded on 2022/09/05
|11
|2302
|15
Report
AI Summary
This report, prepared for a BSc (Hons) Cyber Security course, delves into the principles and practices of risk management within the context of cyber security. It begins with an introduction to risk management, defining its role in identifying and mitigating potential threats to organizational assets. The discussion section explores various risk management techniques, categorizing them into qualitative and quantitative approaches, and outlining the steps involved in risk analysis. The report then examines the seven domains of a typical IT infrastructure, identifying potential risks and vulnerabilities within each domain. Furthermore, it addresses the critical security goals of confidentiality, integrity, and availability, emphasizing their importance in IT systems. The report concludes by summarizing the key concepts and emphasizing the role of risk management in securing IT systems and protecting valuable organizational assets.
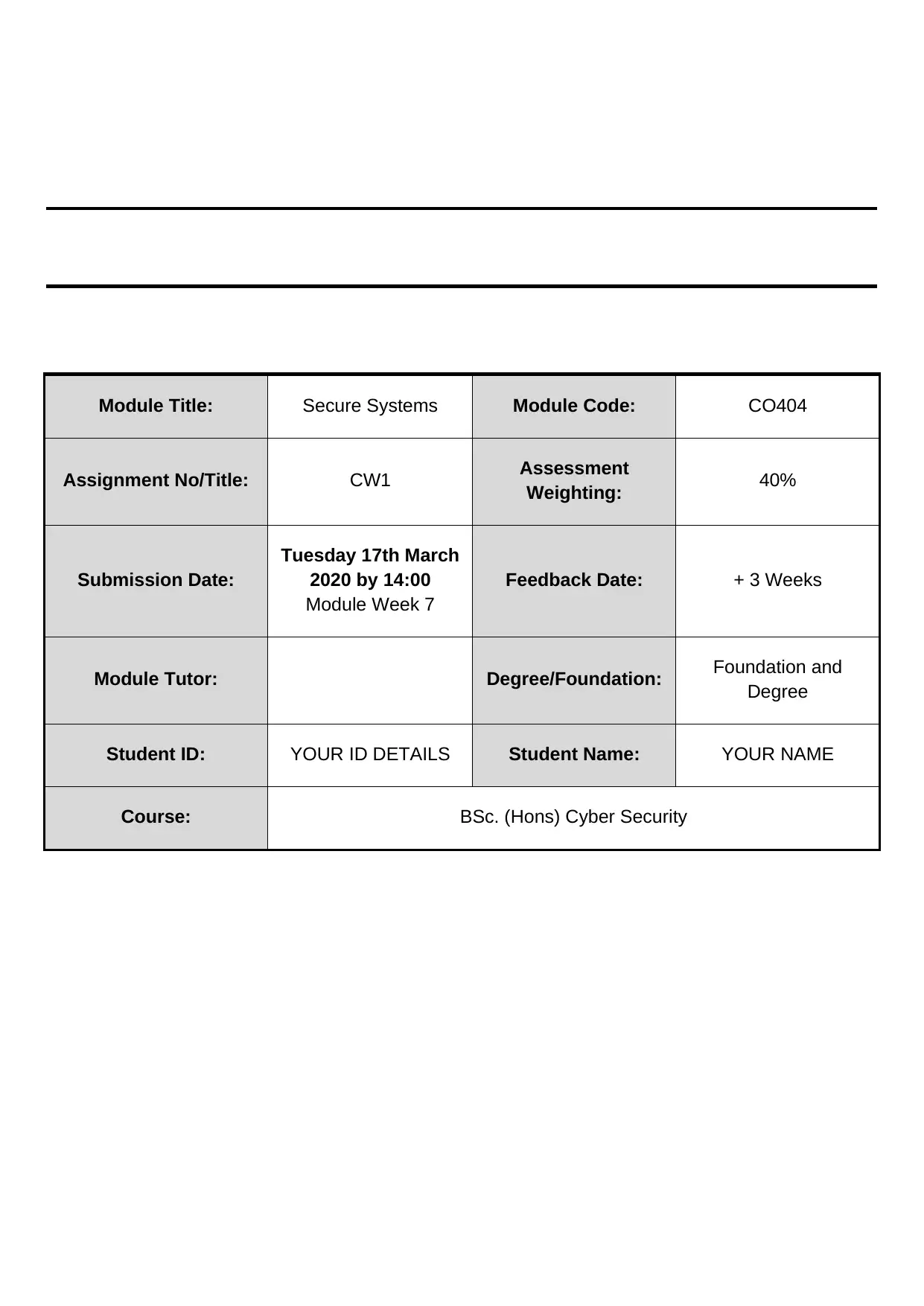
Module Title: Secure Systems Module Code: CO404
Assignment No/Title: CW1 Assessment
Weighting: 40%
Submission Date:
Tuesday 17th March
2020 by 14:00
Module Week 7
Feedback Date: + 3 Weeks
Module Tutor: Degree/Foundation: Foundation and
Degree
Student ID: YOUR ID DETAILS Student Name: YOUR NAME
Course: BSc. (Hons) Cyber Security
Assignment No/Title: CW1 Assessment
Weighting: 40%
Submission Date:
Tuesday 17th March
2020 by 14:00
Module Week 7
Feedback Date: + 3 Weeks
Module Tutor: Degree/Foundation: Foundation and
Degree
Student ID: YOUR ID DETAILS Student Name: YOUR NAME
Course: BSc. (Hons) Cyber Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The principals and practices of risk
management in relation to cyber security
Researched by ENTER FULL NAME & STUDENT ID
management in relation to cyber security
Researched by ENTER FULL NAME & STUDENT ID

ENTER YOUR FULL NAME AND YOUR STUDENT ID NUMBER HERE Tuesday 10th March 2020 by 14:00
Table of Contents
Introduction..........................................................................................................................................4
Discussion...........................................................................................................................................5
Conclusions.........................................................................................................................................9
References........................................................................................................................................10
CO404 Cyber Threat and Risk Management CW1 Page 3 of 11
Table of Contents
Introduction..........................................................................................................................................4
Discussion...........................................................................................................................................5
Conclusions.........................................................................................................................................9
References........................................................................................................................................10
CO404 Cyber Threat and Risk Management CW1 Page 3 of 11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ENTER YOUR FULL NAME AND YOUR STUDENT ID NUMBER HERE Tuesday 10th March 2020 by 14:00
Introduction
Risk management is a technique to recognize the potential risks, measure the effect of these
risks also plan for responding is these risks turn into actuality (McNeil, Frey and Embrechts 2015).
This technique is present as long as the organizations have their assets to secure. The departments
of IT depend on the combination of the technologies, strategies and the education of the user for
protecting the organization against the attacks which can be compromised the systems, steal the
information and another valuable information of the company also damage the reputation of the
organization (Hopkin 2018). The cybersecurity risk management proceeds the thought of the real
world management of risk also applies this to cyber world. This implicates the recognizing the risks
also the susceptibilities also applying the actions of administration and the inclusive solutions to
confirm that the company is effectively secured. There are many methods of risk management
present to identify the probable risks in relation to the cyber security.
CO404 Cyber Threat and Risk Management CW1 Page 4 of 11
Introduction
Risk management is a technique to recognize the potential risks, measure the effect of these
risks also plan for responding is these risks turn into actuality (McNeil, Frey and Embrechts 2015).
This technique is present as long as the organizations have their assets to secure. The departments
of IT depend on the combination of the technologies, strategies and the education of the user for
protecting the organization against the attacks which can be compromised the systems, steal the
information and another valuable information of the company also damage the reputation of the
organization (Hopkin 2018). The cybersecurity risk management proceeds the thought of the real
world management of risk also applies this to cyber world. This implicates the recognizing the risks
also the susceptibilities also applying the actions of administration and the inclusive solutions to
confirm that the company is effectively secured. There are many methods of risk management
present to identify the probable risks in relation to the cyber security.
CO404 Cyber Threat and Risk Management CW1 Page 4 of 11
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ENTER YOUR FULL NAME AND YOUR STUDENT ID NUMBER HERE Tuesday 10th March 2020 by 14:00
Discussion
The cybersecurity risk management is the technologies, policies and practices which address
the vulnerabilities or the threats in the computers, data, programs and network, and enabled by the
connection to the information systems, industrial systems of control, the digital infrastructure,
containing but not limited to the assurance of the supply chain, assurance of software also hardware,
assurance of the information and the security of the information (Pritchard and PMP 2014).
There are many techniques are available in the risk management which are used for
recognizing, evaluating also the planning of the responses to the specific risk also the entire risks
(Aven 2016). Though several techniques are there for the risk management, but it is very important to
select the appropriate techniques to use. For evaluating the risks in the risk management, the
techniques that are present are divided into two categories, one is the qualitative and another is the
quantitative.
i) Qualitative technique:
This technique is focused on the specific risk also it is centered in the judgement by the expert
and the opinion from the educated people. It contains the possibility also effect the assessment,
influence the diagrams and expected the calculations of the value (Meszaros and Buchalcevova
2017). It is the method of project management which highlights the risk on the proposed project by
conveying the possibility and also the number of effect. This technique of examination is for
assessing and also evaluating all the characteristics of exclusively recognized risk and after that
arrange them in the basis of agreed upon characteristics. So multiplication of the possibility and the
effect can be used to determine the qualitative examination.
ii) Quantitative technique:
This technique is focused on the entire risk also it is based on the more approaches of the
numeric. It contains the analysis of the Monte Carlo, analysis of the sensitivity and the decision trees
(Sumra, Hasbullah and AbManan 2015). It is mainly used for evaluating the possibility of the
achievement in the objectives of the proposed project also for estimating the contingency reserve that
is mainly applicable for the coat and the time. This technique is not compulsory mainly for the
projects of smaller size. This technique of examination is mainly helped to calculate the estimates of
the entire risks of the project.
The steps which are followed by the procedure of risk analysis are as follows:
a) Perform the survey of risk assessment
b) Recognize the risks
CO404 Cyber Threat and Risk Management CW1 Page 5 of 11
Discussion
The cybersecurity risk management is the technologies, policies and practices which address
the vulnerabilities or the threats in the computers, data, programs and network, and enabled by the
connection to the information systems, industrial systems of control, the digital infrastructure,
containing but not limited to the assurance of the supply chain, assurance of software also hardware,
assurance of the information and the security of the information (Pritchard and PMP 2014).
There are many techniques are available in the risk management which are used for
recognizing, evaluating also the planning of the responses to the specific risk also the entire risks
(Aven 2016). Though several techniques are there for the risk management, but it is very important to
select the appropriate techniques to use. For evaluating the risks in the risk management, the
techniques that are present are divided into two categories, one is the qualitative and another is the
quantitative.
i) Qualitative technique:
This technique is focused on the specific risk also it is centered in the judgement by the expert
and the opinion from the educated people. It contains the possibility also effect the assessment,
influence the diagrams and expected the calculations of the value (Meszaros and Buchalcevova
2017). It is the method of project management which highlights the risk on the proposed project by
conveying the possibility and also the number of effect. This technique of examination is for
assessing and also evaluating all the characteristics of exclusively recognized risk and after that
arrange them in the basis of agreed upon characteristics. So multiplication of the possibility and the
effect can be used to determine the qualitative examination.
ii) Quantitative technique:
This technique is focused on the entire risk also it is based on the more approaches of the
numeric. It contains the analysis of the Monte Carlo, analysis of the sensitivity and the decision trees
(Sumra, Hasbullah and AbManan 2015). It is mainly used for evaluating the possibility of the
achievement in the objectives of the proposed project also for estimating the contingency reserve that
is mainly applicable for the coat and the time. This technique is not compulsory mainly for the
projects of smaller size. This technique of examination is mainly helped to calculate the estimates of
the entire risks of the project.
The steps which are followed by the procedure of risk analysis are as follows:
a) Perform the survey of risk assessment
b) Recognize the risks
CO404 Cyber Threat and Risk Management CW1 Page 5 of 11
ENTER YOUR FULL NAME AND YOUR STUDENT ID NUMBER HERE Tuesday 10th March 2020 by 14:00
c) Examine the risks
d) Develop the plan of risk management
e) Execute the plan of risk management
f) Monitor this risks
There are seven domains of the typical infrastructure of IT which are Workstation domain,
User domain, Remote Access Domain, System/Application Domain, LAN Domain, WAN Domain and
LAN-to-WAN Domain (Tchernykh et al. 2019). Each domain is noticed as the entries for the attackers
if the countermeasures are failed.
Workstation Domain: The computer of any specific user wherever the production proceeds.
Risks:
i) OS of workstation can have the identified vulnerability of software which permits the hacker for
connecting remotely also steal the information.
ii) The browser of workstation can have the vulnerability of software that permits the unsigned scripts
for installing silently the malicious software (Kumar et al. 2015).
iii) The hard drive of workstation can fail by losing the data.
User Domain: It is for all users who have the entrance to the remaining six domains.
Risks:
i) The user can abolish the data in the application also delete all the data.
ii) User can introduce an infested CD or the USB flash drive into their work computer.
Remote Access Domain: In this domain any mobile user can access remotely the local
network generally via a VPN.
Risks:
i) The circuit outage of communication can reject the connection.
ii) The remote statement from the office can unsecure.
iii) The VPN tunnelling in the middle of remote computer also the access router can hack.
Application/ System Storage Domain: It is pretended of the servers of user accessed like database
and email.
CO404 Cyber Threat and Risk Management CW1 Page 6 of 11
c) Examine the risks
d) Develop the plan of risk management
e) Execute the plan of risk management
f) Monitor this risks
There are seven domains of the typical infrastructure of IT which are Workstation domain,
User domain, Remote Access Domain, System/Application Domain, LAN Domain, WAN Domain and
LAN-to-WAN Domain (Tchernykh et al. 2019). Each domain is noticed as the entries for the attackers
if the countermeasures are failed.
Workstation Domain: The computer of any specific user wherever the production proceeds.
Risks:
i) OS of workstation can have the identified vulnerability of software which permits the hacker for
connecting remotely also steal the information.
ii) The browser of workstation can have the vulnerability of software that permits the unsigned scripts
for installing silently the malicious software (Kumar et al. 2015).
iii) The hard drive of workstation can fail by losing the data.
User Domain: It is for all users who have the entrance to the remaining six domains.
Risks:
i) The user can abolish the data in the application also delete all the data.
ii) User can introduce an infested CD or the USB flash drive into their work computer.
Remote Access Domain: In this domain any mobile user can access remotely the local
network generally via a VPN.
Risks:
i) The circuit outage of communication can reject the connection.
ii) The remote statement from the office can unsecure.
iii) The VPN tunnelling in the middle of remote computer also the access router can hack.
Application/ System Storage Domain: It is pretended of the servers of user accessed like database
and email.
CO404 Cyber Threat and Risk Management CW1 Page 6 of 11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ENTER YOUR FULL NAME AND YOUR STUDENT ID NUMBER HERE Tuesday 10th March 2020 by 14:00
Risks:
i) The fire can finish the primary data.
ii) The attack of DOS can cripple email of the organization.
iii) The server of database can attack by the SQL injection for corrupting data.
LAN Domain: It comprises all the workstations, switches, routers also hubs. This LAN is reliable
zone.
Risks:
i) The worm can blowout over this LAN also pollute all the computers.
ii) The server OS of LAN can have the identified vulnerability of software (Rodrigues-da-Silva and
Crispim 2014).
iii) Any unauthorized user can be accessed workstations in the LAN of any organization.
WAN Domain: It stances for the Wide Area Network. It contains Internet and the semi-private lines.
Risks:
i) The service provider can consume the main network outage.
ii) The server can collect the attack of DOS or DDOS.
iii) The FTP server can permit to upload any unlawful software secretly.
LAN / WAN Domain: The border in the middle of the reliable and the un-trusted regions. This
regions are filtered with the firewall.
Risks:
i) The hacker can breach the IT infrastructure also achieve the access to the internal network.
ii) Weak access of traffic filtering can damage the performance.
iii) The firewall with needless ports open can permit the access from Internet.
The risk management addresses the confidentiality, integrity, and availability in IT systems
which are discussed below:
a) Confidentiality: It is the condition whose determination to for keeping the sensitive data from
disclosing to the unauthorized recipients. This secret may be significant for the reasons of the
CO404 Cyber Threat and Risk Management CW1 Page 7 of 11
Risks:
i) The fire can finish the primary data.
ii) The attack of DOS can cripple email of the organization.
iii) The server of database can attack by the SQL injection for corrupting data.
LAN Domain: It comprises all the workstations, switches, routers also hubs. This LAN is reliable
zone.
Risks:
i) The worm can blowout over this LAN also pollute all the computers.
ii) The server OS of LAN can have the identified vulnerability of software (Rodrigues-da-Silva and
Crispim 2014).
iii) Any unauthorized user can be accessed workstations in the LAN of any organization.
WAN Domain: It stances for the Wide Area Network. It contains Internet and the semi-private lines.
Risks:
i) The service provider can consume the main network outage.
ii) The server can collect the attack of DOS or DDOS.
iii) The FTP server can permit to upload any unlawful software secretly.
LAN / WAN Domain: The border in the middle of the reliable and the un-trusted regions. This
regions are filtered with the firewall.
Risks:
i) The hacker can breach the IT infrastructure also achieve the access to the internal network.
ii) Weak access of traffic filtering can damage the performance.
iii) The firewall with needless ports open can permit the access from Internet.
The risk management addresses the confidentiality, integrity, and availability in IT systems
which are discussed below:
a) Confidentiality: It is the condition whose determination to for keeping the sensitive data from
disclosing to the unauthorized recipients. This secret may be significant for the reasons of the
CO404 Cyber Threat and Risk Management CW1 Page 7 of 11
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ENTER YOUR FULL NAME AND YOUR STUDENT ID NUMBER HERE Tuesday 10th March 2020 by 14:00
national security, competitive advantage or the personal privacy (Irimia Diéguez, Sánchez Cazorla
and Alfalla Luque 2014). The confidentiality of the system also the data states to guard of the data
from the illegal revelation. The effect of this illegal revelation of personal data can range from
exposing of national security to the revelation of the Act data of Privacy. Illegal, unexpected, or
accidental revelation could outcome in loss of the public assurance, discomfiture, or any lawful action
in contradiction of the organization.
b) Integrity: The integrity of the system also data states to the condition that the data need to be
secured from inappropriate variation. Integrity is vanished if the illegal changes are prepared to data
or the system of IT by either the acts of intentional or accidental (Fakis et al. 2014). If this loss of
system or the data integrity is not modified, continual use of tainted system or the corrupted data
could effect in incorrectness, erroneous decisions and fraud. Correspondingly, the violation of
integrity may be first step in the effective attack in contradiction of the availability or privacy of
system. For all of these causes, the loss of integrity decreases the guarantee of the IT system.
c) Availability: If the mission critical system of IT is unreachable to the end users of it, then the
mission of the organization may affect (Bowers and Khorakian 2014). The loss of the functionality
also operational effectiveness of the system, for instance, may consequence in loss of the productive
time, therefore hindering the performance of the end users and their purposes in supportive the
mission of this organization.
CO404 Cyber Threat and Risk Management CW1 Page 8 of 11
national security, competitive advantage or the personal privacy (Irimia Diéguez, Sánchez Cazorla
and Alfalla Luque 2014). The confidentiality of the system also the data states to guard of the data
from the illegal revelation. The effect of this illegal revelation of personal data can range from
exposing of national security to the revelation of the Act data of Privacy. Illegal, unexpected, or
accidental revelation could outcome in loss of the public assurance, discomfiture, or any lawful action
in contradiction of the organization.
b) Integrity: The integrity of the system also data states to the condition that the data need to be
secured from inappropriate variation. Integrity is vanished if the illegal changes are prepared to data
or the system of IT by either the acts of intentional or accidental (Fakis et al. 2014). If this loss of
system or the data integrity is not modified, continual use of tainted system or the corrupted data
could effect in incorrectness, erroneous decisions and fraud. Correspondingly, the violation of
integrity may be first step in the effective attack in contradiction of the availability or privacy of
system. For all of these causes, the loss of integrity decreases the guarantee of the IT system.
c) Availability: If the mission critical system of IT is unreachable to the end users of it, then the
mission of the organization may affect (Bowers and Khorakian 2014). The loss of the functionality
also operational effectiveness of the system, for instance, may consequence in loss of the productive
time, therefore hindering the performance of the end users and their purposes in supportive the
mission of this organization.
CO404 Cyber Threat and Risk Management CW1 Page 8 of 11

ENTER YOUR FULL NAME AND YOUR STUDENT ID NUMBER HERE Tuesday 10th March 2020 by 14:00
Conclusions
So, from the beyond discussed project, it can conclude that Risk management is the method
for identifying the potential risks, measure effect of these risks also strategy for the responding is
these risks turn into reality. Also the cybersecurity risk management ensues the assumed of the real
world management of the risk also put on this to the cyber world. In the cyber security, the five
security goals are present in which three most important goals are integrity, availability and
confidentiality. The risk management is also addressed these three goals of security. Also risk
management alters in the relation to the seven domains of the classic infrastructure of IT, these
seven domains are Workstation domain, User domain, Remote Access Domain, System/Application
Domain, LAN Domain, WAN Domain and LAN-to-WAN Domain. All the risks which can noticed in
these seven domain are discussed above. This risk management are two types, one is Qualitative
analysis and another is Quantitative analysis which are also discussed above. This risk management
have some steps by these it can proceed which are Perform the survey of risk assessment,
Recognize the risks, Examine the risks, Develop the plan of the risk management, Execute the plan
of the risk management and Monitor this risks.
CO404 Cyber Threat and Risk Management CW1 Page 9 of 11
Conclusions
So, from the beyond discussed project, it can conclude that Risk management is the method
for identifying the potential risks, measure effect of these risks also strategy for the responding is
these risks turn into reality. Also the cybersecurity risk management ensues the assumed of the real
world management of the risk also put on this to the cyber world. In the cyber security, the five
security goals are present in which three most important goals are integrity, availability and
confidentiality. The risk management is also addressed these three goals of security. Also risk
management alters in the relation to the seven domains of the classic infrastructure of IT, these
seven domains are Workstation domain, User domain, Remote Access Domain, System/Application
Domain, LAN Domain, WAN Domain and LAN-to-WAN Domain. All the risks which can noticed in
these seven domain are discussed above. This risk management are two types, one is Qualitative
analysis and another is Quantitative analysis which are also discussed above. This risk management
have some steps by these it can proceed which are Perform the survey of risk assessment,
Recognize the risks, Examine the risks, Develop the plan of the risk management, Execute the plan
of the risk management and Monitor this risks.
CO404 Cyber Threat and Risk Management CW1 Page 9 of 11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ENTER YOUR FULL NAME AND YOUR STUDENT ID NUMBER HERE Tuesday 10th March 2020 by 14:00
References
McNeil, A.J., Frey, R. and Embrechts, P., 2015. Quantitative risk management: concepts, techniques
and tools-revised edition. Princeton university press.
Hopkin, P., 2018. Fundamentals of risk management: understanding, evaluating and implementing
effective risk management. Kogan Page Publishers.
Pritchard, C.L. and PMP, P.R., 2014. Risk management: concepts and guidance. CRC Press.
Aven, T., 2016. Risk assessment and risk management: Review of recent advances on their
foundation. European Journal of Operational Research, 253(1), pp.1-13.
Meszaros, J. and Buchalcevova, A., 2017. Introducing OSSF: A framework for online service
cybersecurity risk management. computers & security, 65, pp.300-313.
Sumra, I.A., Hasbullah, H.B. and AbManan, J.L.B., 2015. Attacks on security goals (confidentiality,
integrity, availability) in VANET: a survey. In Vehicular Ad-Hoc Networks for Smart Cities (pp. 51-61).
Springer, Singapore.
Tchernykh, A., Schwiegelsohn, U., Talbi, E.G. and Babenko, M., 2019. Towards understanding
uncertainty in cloud computing with risks of confidentiality, integrity, and availability. Journal of
Computational Science, 36, p.100581.
Kumar, M., Meena, J., Singh, R. and Vardhan, M., 2015, October. Data outsourcing: A threat to
confidentiality, integrity, and availability. In 2015 International Conference on Green Computing and
Internet of Things (ICGCIoT) (pp. 1496-1501). IEEE.
Rodrigues-da-Silva, L.H. and Crispim, J.A., 2014. The project risk management process, a
preliminary study. Procedia technology, 16, pp.943-949.
Irimia Diéguez, A.I., Sánchez Cazorla, Á. and Alfalla Luque, R., 2014. Risk management in
megaprojects. Procedia: Social and Behavioral Sciences, 119, 407-416.
Fakis, A., Hilliam, R., Stoneley, H. and Townend, M., 2014. Quantitative analysis of qualitative
information from interviews: A systematic literature review. Journal of Mixed Methods Research, 8(2),
pp.139-161.
Bowers, J. and Khorakian, A., 2014. Integrating risk management in the innovation project. European
Journal of innovation management.
CO404 Cyber Threat and Risk Management CW1 Page 10 of 11
References
McNeil, A.J., Frey, R. and Embrechts, P., 2015. Quantitative risk management: concepts, techniques
and tools-revised edition. Princeton university press.
Hopkin, P., 2018. Fundamentals of risk management: understanding, evaluating and implementing
effective risk management. Kogan Page Publishers.
Pritchard, C.L. and PMP, P.R., 2014. Risk management: concepts and guidance. CRC Press.
Aven, T., 2016. Risk assessment and risk management: Review of recent advances on their
foundation. European Journal of Operational Research, 253(1), pp.1-13.
Meszaros, J. and Buchalcevova, A., 2017. Introducing OSSF: A framework for online service
cybersecurity risk management. computers & security, 65, pp.300-313.
Sumra, I.A., Hasbullah, H.B. and AbManan, J.L.B., 2015. Attacks on security goals (confidentiality,
integrity, availability) in VANET: a survey. In Vehicular Ad-Hoc Networks for Smart Cities (pp. 51-61).
Springer, Singapore.
Tchernykh, A., Schwiegelsohn, U., Talbi, E.G. and Babenko, M., 2019. Towards understanding
uncertainty in cloud computing with risks of confidentiality, integrity, and availability. Journal of
Computational Science, 36, p.100581.
Kumar, M., Meena, J., Singh, R. and Vardhan, M., 2015, October. Data outsourcing: A threat to
confidentiality, integrity, and availability. In 2015 International Conference on Green Computing and
Internet of Things (ICGCIoT) (pp. 1496-1501). IEEE.
Rodrigues-da-Silva, L.H. and Crispim, J.A., 2014. The project risk management process, a
preliminary study. Procedia technology, 16, pp.943-949.
Irimia Diéguez, A.I., Sánchez Cazorla, Á. and Alfalla Luque, R., 2014. Risk management in
megaprojects. Procedia: Social and Behavioral Sciences, 119, 407-416.
Fakis, A., Hilliam, R., Stoneley, H. and Townend, M., 2014. Quantitative analysis of qualitative
information from interviews: A systematic literature review. Journal of Mixed Methods Research, 8(2),
pp.139-161.
Bowers, J. and Khorakian, A., 2014. Integrating risk management in the innovation project. European
Journal of innovation management.
CO404 Cyber Threat and Risk Management CW1 Page 10 of 11
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ENTER YOUR FULL NAME AND YOUR STUDENT ID NUMBER HERE Tuesday 10th March 2020 by 14:00
CO404 Cyber Threat and Risk Management CW1 Page 11 of 11
CO404 Cyber Threat and Risk Management CW1 Page 11 of 11
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





