Smart Grid Cyber Security: Strategies, Threats, and Solutions
VerifiedAdded on 2022/09/22
|46
|10914
|50
Report
AI Summary
This report provides a comprehensive overview of cyber security strategies in the context of smart grid systems. It begins with an introduction to smart grids and their increasing reliance on data and communication technologies, emphasizing the need for robust cyber security measures. The report includes an extensive literature review that explores the evolution of smart grids, the importance of cyber security, and the vulnerabilities that arise from cyber-attacks. It categorizes security threats, including misbehaving and malicious users, and delves into specific attack types such as false data injection and attacks on AGC and smart grid databases. The core of the report focuses on various cyber security strategies, including making smart grids survivable, providing scalable security measures, embedding security controls by design, employing a defense-in-depth approach, and enhancing traditional security measures. The research methodology section outlines the research philosophy, approach, design, data collection methods, and analysis techniques used in the study. The findings and analysis section presents qualitative data analysis, which is followed by conclusions and recommendations for improving cyber security in smart grids. The report underscores the critical need for proactive security measures in the evolving landscape of smart grid technologies.

Running Head: CYBER SECURITY STRATEGIES IN SMART GRID
Cyber Security Strategies in Smart Grid
Name of the Student
Name of the University
Cyber Security Strategies in Smart Grid
Name of the Student
Name of the University
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
CYBER SECURITY STRATEGIES IN SMART GRID
Table of Contents
Preliminary Report...........................................................................................................................5
Introduction......................................................................................................................................5
Background (Literature Review).....................................................................................................5
Research Problems.........................................................................................................................11
Research Methodology..................................................................................................................12
Research Significance....................................................................................................................14
Conclusion.....................................................................................................................................14
Research Planning.........................................................................................................................15
Final Draft......................................................................................................................................16
Chapter 1: Introduction..................................................................................................................16
1.1 Background.....................................................................................................................16
1.2 Aim, Objective and Research question...........................................................................16
1.3 Research Significance.....................................................................................................17
1.4 Research Structure..........................................................................................................17
Chapter 2: Literature Review.........................................................................................................19
2.1 Requirements and Objectives of Cyber Security.....................................................................19
2.2 Cyber Security Threats............................................................................................................20
2.3 Solutions of Cyber Security in Smart Grid..........................................................................21
Network Security...................................................................................................................22
CYBER SECURITY STRATEGIES IN SMART GRID
Table of Contents
Preliminary Report...........................................................................................................................5
Introduction......................................................................................................................................5
Background (Literature Review).....................................................................................................5
Research Problems.........................................................................................................................11
Research Methodology..................................................................................................................12
Research Significance....................................................................................................................14
Conclusion.....................................................................................................................................14
Research Planning.........................................................................................................................15
Final Draft......................................................................................................................................16
Chapter 1: Introduction..................................................................................................................16
1.1 Background.....................................................................................................................16
1.2 Aim, Objective and Research question...........................................................................16
1.3 Research Significance.....................................................................................................17
1.4 Research Structure..........................................................................................................17
Chapter 2: Literature Review.........................................................................................................19
2.1 Requirements and Objectives of Cyber Security.....................................................................19
2.2 Cyber Security Threats............................................................................................................20
2.3 Solutions of Cyber Security in Smart Grid..........................................................................21
Network Security...................................................................................................................22

3
CYBER SECURITY STRATEGIES IN SMART GRID
DoS Detection........................................................................................................................22
DoS Mitigation......................................................................................................................23
2.4 Data Security.......................................................................................................................24
2.5 Key Management.................................................................................................................25
Chapter 3: Research Methodology................................................................................................27
3.1 Introduction..........................................................................................................................27
3.2 Research Philosophy:...........................................................................................................27
3.3 Research Approach:.............................................................................................................28
3.4 Research Design:.................................................................................................................30
3.5 Data Collection Method.......................................................................................................31
3.6 Sampling..............................................................................................................................32
3.7 Data Analysis.......................................................................................................................32
3.8 Ethical Consideration...........................................................................................................32
Chapter 4: Data findings and analysis...........................................................................................33
4.1 Qualitative data analysis......................................................................................................33
Chapter 5: Conclusion and Recommendation...............................................................................39
5.1 Conclusion...........................................................................................................................39
5.2 Recommendations................................................................................................................40
References......................................................................................................................................41
CYBER SECURITY STRATEGIES IN SMART GRID
DoS Detection........................................................................................................................22
DoS Mitigation......................................................................................................................23
2.4 Data Security.......................................................................................................................24
2.5 Key Management.................................................................................................................25
Chapter 3: Research Methodology................................................................................................27
3.1 Introduction..........................................................................................................................27
3.2 Research Philosophy:...........................................................................................................27
3.3 Research Approach:.............................................................................................................28
3.4 Research Design:.................................................................................................................30
3.5 Data Collection Method.......................................................................................................31
3.6 Sampling..............................................................................................................................32
3.7 Data Analysis.......................................................................................................................32
3.8 Ethical Consideration...........................................................................................................32
Chapter 4: Data findings and analysis...........................................................................................33
4.1 Qualitative data analysis......................................................................................................33
Chapter 5: Conclusion and Recommendation...............................................................................39
5.1 Conclusion...........................................................................................................................39
5.2 Recommendations................................................................................................................40
References......................................................................................................................................41
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4
CYBER SECURITY STRATEGIES IN SMART GRID
Preliminary Report
Introduction
Development of data and communication technologies have been changed with utilizing
various technologies. In electricity distribution industry, it depends on intelligent systems and
devices which help in communicating among each other. Smart Grid has been one of the recent
technologies in the electricity distribution network. Smart Grids have been helping enhancing
distribution of electricity (Zhang et al. 2017). The adoption of smart grid technologies has
increase importance of cyber security due to ICT dependencies. Various risks and cyber-attacks
that are faced in the technologies of smart grid. This research has focused on the strategies of
cyber security in smart grid technologies. The service providers need to be attentive and focused
on enhancing their traditional security measures including access control, authentication, data
encryption, firewalls, and log analysis and intrusion detection system. The concept of Smart Grid
has evolved for modernizing electric grid and minimizing issues in power industry. This report
has focused on various cyber security strategies based on smart grid technologies in electronic
systems.
Background (Literature Review)
Smart Grid
As commented by He and Yan (2016), Smart grid engage with a class of technology that
are utilizing electricity delivery system with computers that are based on automation and remote
control. These are the systems that have helped in communication technology that is two-way,
and processing which has been used in industry. Traditionally, power grid used to be designed
for transporting power from power generation plant to end users. One of the five parcels would
CYBER SECURITY STRATEGIES IN SMART GRID
Preliminary Report
Introduction
Development of data and communication technologies have been changed with utilizing
various technologies. In electricity distribution industry, it depends on intelligent systems and
devices which help in communicating among each other. Smart Grid has been one of the recent
technologies in the electricity distribution network. Smart Grids have been helping enhancing
distribution of electricity (Zhang et al. 2017). The adoption of smart grid technologies has
increase importance of cyber security due to ICT dependencies. Various risks and cyber-attacks
that are faced in the technologies of smart grid. This research has focused on the strategies of
cyber security in smart grid technologies. The service providers need to be attentive and focused
on enhancing their traditional security measures including access control, authentication, data
encryption, firewalls, and log analysis and intrusion detection system. The concept of Smart Grid
has evolved for modernizing electric grid and minimizing issues in power industry. This report
has focused on various cyber security strategies based on smart grid technologies in electronic
systems.
Background (Literature Review)
Smart Grid
As commented by He and Yan (2016), Smart grid engage with a class of technology that
are utilizing electricity delivery system with computers that are based on automation and remote
control. These are the systems that have helped in communication technology that is two-way,
and processing which has been used in industry. Traditionally, power grid used to be designed
for transporting power from power generation plant to end users. One of the five parcels would
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
5
CYBER SECURITY STRATEGIES IN SMART GRID
be tested by the switch for building the stream and the entropy measures are determined. The
choice will at that point be taken by the switch for choosing in the event that it was an attacks.
Signal qualities estimated for distinguishing attacks are ordinarily finished with remote gadgets.
With estimating the degree of sign quality, it very well may be chosen by the gadget if genuine
information is being gotten by it or it is a sticking attacks. Choices are made in every gadget by
utilization of exact techniques. A sticking attacks can be of two structures, an intensified
ceaseless sign can be sent by the assailant for sticking the sign or a commotion like sign can be
sent. This concludes that entire power system was one directional and control structure was
centralized. However, this centralization of control system has been affected by the cyber-
attacks. There have been many cases on cyber-attacks in the power grid systems. Physical
component damages have been the most common issues faced in power grid systems.
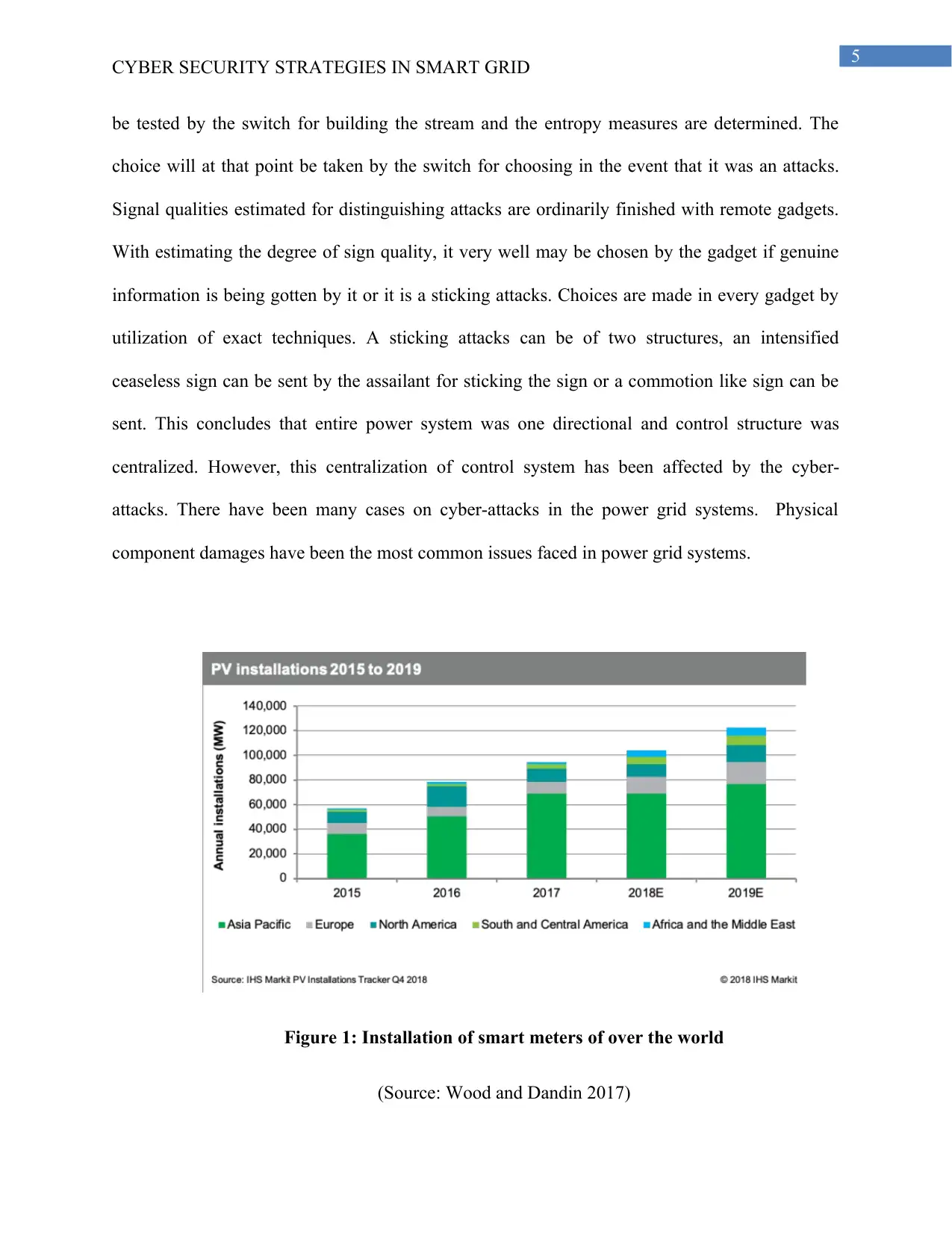
Figure 1: Installation of smart meters of over the world
(Source: Wood and Dandin 2017)
CYBER SECURITY STRATEGIES IN SMART GRID
be tested by the switch for building the stream and the entropy measures are determined. The
choice will at that point be taken by the switch for choosing in the event that it was an attacks.
Signal qualities estimated for distinguishing attacks are ordinarily finished with remote gadgets.
With estimating the degree of sign quality, it very well may be chosen by the gadget if genuine
information is being gotten by it or it is a sticking attacks. Choices are made in every gadget by
utilization of exact techniques. A sticking attacks can be of two structures, an intensified
ceaseless sign can be sent by the assailant for sticking the sign or a commotion like sign can be
sent. This concludes that entire power system was one directional and control structure was
centralized. However, this centralization of control system has been affected by the cyber-
attacks. There have been many cases on cyber-attacks in the power grid systems. Physical
component damages have been the most common issues faced in power grid systems.
Figure 1: Installation of smart meters of over the world
(Source: Wood and Dandin 2017)

6
CYBER SECURITY STRATEGIES IN SMART GRID
Therefore, with the advancement in technology, smart grid system has been introduced in
the power grid industry (Wood and Dandin 2017). This has helped in automation of power
distribution system in the power grid. The modernization of traditional power grid has additional
functionalities including self-healing, resists attacks, increasing power quality, enabling electrical
attacks and optimizes assets and efficient operation. Power grid is considered to be major key
pubic infrastructures and damage to this infrastructure can cause a great loss to the country.
Security issues in Smart grid
Security issues arise from cyber-attacks from the networks that are used for
communication. Therefore, it is necessary to understand the vulnerabilities in the Smart Grid.
Security attacks can be divided into two types including misbehaving users who are selfish and
malicious users. In first case, misbehaving users who are selfish used to acquire more network
resources in an illegal way by violating communicating protocols. Malicious users do not think
about their own profit else they disrupt information from the network (Sanjab et al. 2016).
Malicious behavior has been issues in the smart grid. Some other cyber security risks are given
below:
False Data Injection Attack: During power transmission, state emission gets wrong data
from SACDA network. Therefore, this has been an attack that is unobservable; occur in meters
that are connected in circuit. The original data in meters get changed due to this attack. The false
value of data in the meter causes a huge loss to the power grid set up. The management system of
energy gets affected b tis attack. There might be overload of power transmission in the channel
which can cause damage to physical components of power grid (El Mrabet et al. 2018).
Attacks on AGC: Power grid system include change in load all time in power system.
Therefore, AGC helps in controlling these modifications in system. System frequency has been
CYBER SECURITY STRATEGIES IN SMART GRID
Therefore, with the advancement in technology, smart grid system has been introduced in
the power grid industry (Wood and Dandin 2017). This has helped in automation of power
distribution system in the power grid. The modernization of traditional power grid has additional
functionalities including self-healing, resists attacks, increasing power quality, enabling electrical
attacks and optimizes assets and efficient operation. Power grid is considered to be major key
pubic infrastructures and damage to this infrastructure can cause a great loss to the country.
Security issues in Smart grid
Security issues arise from cyber-attacks from the networks that are used for
communication. Therefore, it is necessary to understand the vulnerabilities in the Smart Grid.
Security attacks can be divided into two types including misbehaving users who are selfish and
malicious users. In first case, misbehaving users who are selfish used to acquire more network
resources in an illegal way by violating communicating protocols. Malicious users do not think
about their own profit else they disrupt information from the network (Sanjab et al. 2016).
Malicious behavior has been issues in the smart grid. Some other cyber security risks are given
below:
False Data Injection Attack: During power transmission, state emission gets wrong data
from SACDA network. Therefore, this has been an attack that is unobservable; occur in meters
that are connected in circuit. The original data in meters get changed due to this attack. The false
value of data in the meter causes a huge loss to the power grid set up. The management system of
energy gets affected b tis attack. There might be overload of power transmission in the channel
which can cause damage to physical components of power grid (El Mrabet et al. 2018).
Attacks on AGC: Power grid system include change in load all time in power system.
Therefore, AGC helps in controlling these modifications in system. System frequency has been
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
7
CYBER SECURITY STRATEGIES IN SMART GRID
monitored and controlled in order to take decision for generation of power in the system (Lei et
al. 2018). The Area Control Error (ACE) used to be analyzed from difference between deviation
of frequency from output and net line power. These are the attacks that helps in targeting this
value in order to change and monitor on it.
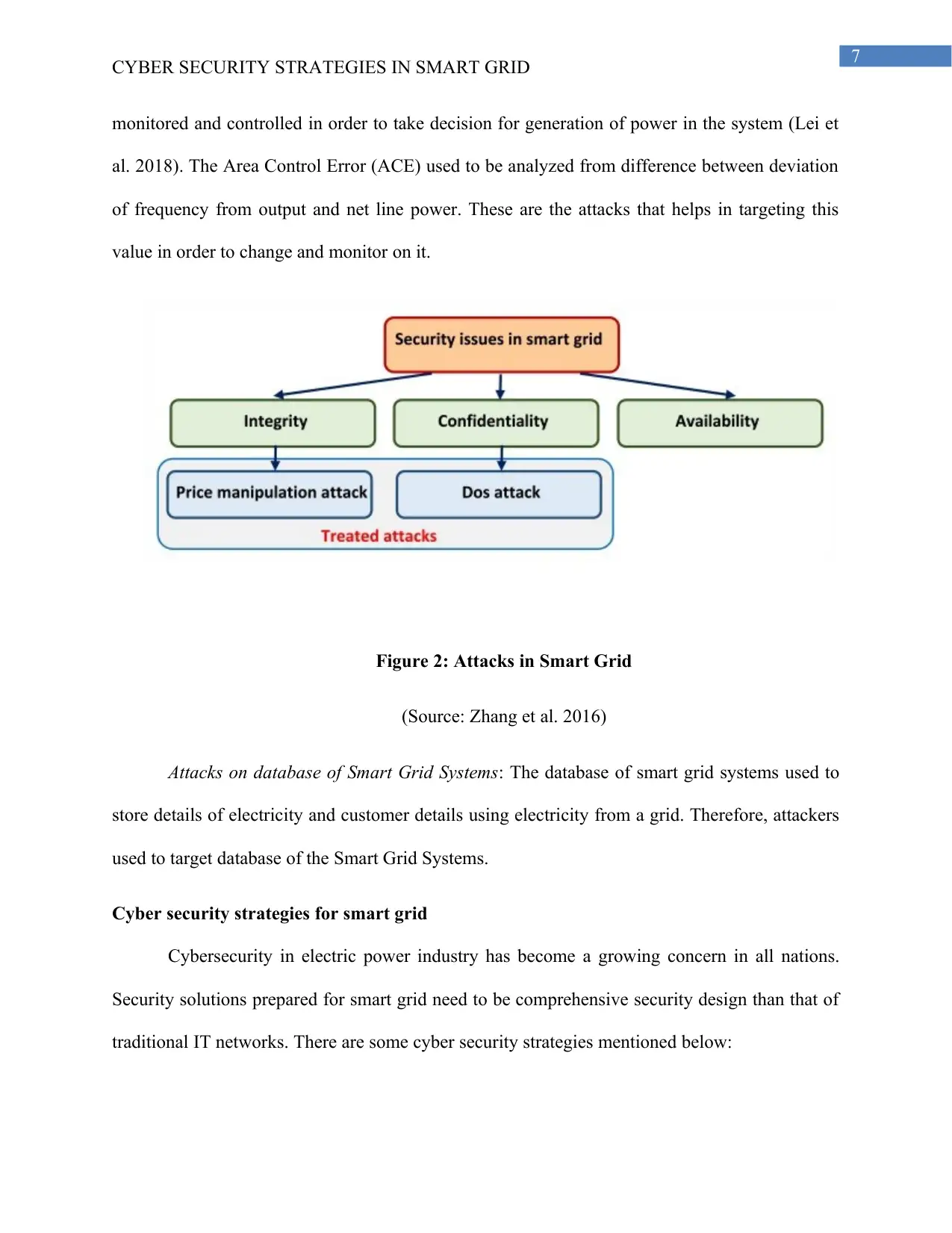
Figure 2: Attacks in Smart Grid
(Source: Zhang et al. 2016)
Attacks on database of Smart Grid Systems: The database of smart grid systems used to
store details of electricity and customer details using electricity from a grid. Therefore, attackers
used to target database of the Smart Grid Systems.
Cyber security strategies for smart grid
Cybersecurity in electric power industry has become a growing concern in all nations.
Security solutions prepared for smart grid need to be comprehensive security design than that of
traditional IT networks. There are some cyber security strategies mentioned below:
CYBER SECURITY STRATEGIES IN SMART GRID
monitored and controlled in order to take decision for generation of power in the system (Lei et
al. 2018). The Area Control Error (ACE) used to be analyzed from difference between deviation
of frequency from output and net line power. These are the attacks that helps in targeting this
value in order to change and monitor on it.
Figure 2: Attacks in Smart Grid
(Source: Zhang et al. 2016)
Attacks on database of Smart Grid Systems: The database of smart grid systems used to
store details of electricity and customer details using electricity from a grid. Therefore, attackers
used to target database of the Smart Grid Systems.
Cyber security strategies for smart grid
Cybersecurity in electric power industry has become a growing concern in all nations.
Security solutions prepared for smart grid need to be comprehensive security design than that of
traditional IT networks. There are some cyber security strategies mentioned below:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
CYBER SECURITY STRATEGIES IN SMART GRID
Make Smart grids survivable: As information system become more complex and their
interdependence increases the availability picture become complicated. This become more
serious in case systems are integrated with Commercial off the Shelf (COTS) products and
services. Organizations that include department of defense (DOD) uses COTS systems for
providing office productivity and Internet services (Li et al. 2017). Traditional approaches have
been ensuring availability that do not meet challenges of giving assured availability in huge
source of data. There has been a need to advanced approach in the cyber security of smart grid
system.
Providing scalable security measures: Current information system have been complex
and better integrated with other systems. Large distributed system includes smart grids have got
huge support from customers in various contexts. The complexity of efficient mechanism needs
to deal with user having several privileges (Neureiter et al. 2016). A conventional identity-based
CYBER SECURITY STRATEGIES IN SMART GRID
Make Smart grids survivable: As information system become more complex and their
interdependence increases the availability picture become complicated. This become more
serious in case systems are integrated with Commercial off the Shelf (COTS) products and
services. Organizations that include department of defense (DOD) uses COTS systems for
providing office productivity and Internet services (Li et al. 2017). Traditional approaches have
been ensuring availability that do not meet challenges of giving assured availability in huge
source of data. There has been a need to advanced approach in the cyber security of smart grid
system.
Providing scalable security measures: Current information system have been complex
and better integrated with other systems. Large distributed system includes smart grids have got
huge support from customers in various contexts. The complexity of efficient mechanism needs
to deal with user having several privileges (Neureiter et al. 2016). A conventional identity-based

9
CYBER SECURITY STRATEGIES IN SMART GRID
approach has been sufficient for this application involves a small support. Scalability of security
systems need to be implemented to large systems and required for smart grids.
Figure 3: How secure is smart grid?
(Source: Zhu 2019)
Embed Security Controls by design: The Securities must be engineered into element of
grid system that are smart from earliest stages of design procedure. Security has been the latest
concern for equipping manufacturers proves to be vulnerable (Zhu 2019). Utility suppliers of
services and products must be aware of these adverse consequences result in huge financial loss.
Authorization, authentication and encryption requirements need to be all products and services
designed for electric power industry.
Employ a defense in depth approach: The principles of security for smart grid which is
converting the attacks that are wholesale that may put the whole system at risk. The smart grid
has been a conglomerate with multiple network with multitude of communication levels between
suppliers, customers and service providers (Lamba, Šimková and Rossi 2019). Multiple layers of
defense and security domains strategy help in providing a better opportunity in security to smart
grid.
Enhance traditional security measures: Reliability and robustness of smart grid services
have been depending in data and information stored in database infrastructure. Therefore,
several security infrastructures including access control, authentication and intrusion detection
system has been monitored properly. The large scalability and mission critical availability of
smart grids need to get enhanced with its traditional security systems. The Role-based Access
CYBER SECURITY STRATEGIES IN SMART GRID
approach has been sufficient for this application involves a small support. Scalability of security
systems need to be implemented to large systems and required for smart grids.
Figure 3: How secure is smart grid?
(Source: Zhu 2019)
Embed Security Controls by design: The Securities must be engineered into element of
grid system that are smart from earliest stages of design procedure. Security has been the latest
concern for equipping manufacturers proves to be vulnerable (Zhu 2019). Utility suppliers of
services and products must be aware of these adverse consequences result in huge financial loss.
Authorization, authentication and encryption requirements need to be all products and services
designed for electric power industry.
Employ a defense in depth approach: The principles of security for smart grid which is
converting the attacks that are wholesale that may put the whole system at risk. The smart grid
has been a conglomerate with multiple network with multitude of communication levels between
suppliers, customers and service providers (Lamba, Šimková and Rossi 2019). Multiple layers of
defense and security domains strategy help in providing a better opportunity in security to smart
grid.
Enhance traditional security measures: Reliability and robustness of smart grid services
have been depending in data and information stored in database infrastructure. Therefore,
several security infrastructures including access control, authentication and intrusion detection
system has been monitored properly. The large scalability and mission critical availability of
smart grids need to get enhanced with its traditional security systems. The Role-based Access
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
CYBER SECURITY STRATEGIES IN SMART GRID
Control (RBAC) mechanism instead of identity-based access control in a smart grid environment
(Kuzlu, Pipattanasompom and Rahman 2017).
Research Problems
Power systems has been facing issues with cyber-attacks in recent years. Various security
vulnerabilities have been raising questions with critical power system infrastructure. The issues
of smart grid need to address challenges that are new in order to have reliable, stable and safe
operation in grid. Major security issues in smart grid have been related to physical components,
control centers and application, protection measures for mitigating risks from cyber threats.
These issues have been challenging the security and reliability of smart grid systems in the
market (Saini et al. 2018). Cyber issues have been creating a large challenge in smart grid
infrastructure.
Aim, Objectives and Research questions
This research has focused on analyzing strategies of cyber security in smart grid
technologies.
Following are objectives of the research:
To identify and critically analyze cyber security issues in smart grid and identify relevant
factors for vulnerability
To recommend strategies for addressing security challenges in smart grid
Following are questions for research:
What are issues of cyber security in smart grid?
What cyber security strategies can be applied in smart grid?
CYBER SECURITY STRATEGIES IN SMART GRID
Control (RBAC) mechanism instead of identity-based access control in a smart grid environment
(Kuzlu, Pipattanasompom and Rahman 2017).
Research Problems
Power systems has been facing issues with cyber-attacks in recent years. Various security
vulnerabilities have been raising questions with critical power system infrastructure. The issues
of smart grid need to address challenges that are new in order to have reliable, stable and safe
operation in grid. Major security issues in smart grid have been related to physical components,
control centers and application, protection measures for mitigating risks from cyber threats.
These issues have been challenging the security and reliability of smart grid systems in the
market (Saini et al. 2018). Cyber issues have been creating a large challenge in smart grid
infrastructure.
Aim, Objectives and Research questions
This research has focused on analyzing strategies of cyber security in smart grid
technologies.
Following are objectives of the research:
To identify and critically analyze cyber security issues in smart grid and identify relevant
factors for vulnerability
To recommend strategies for addressing security challenges in smart grid
Following are questions for research:
What are issues of cyber security in smart grid?
What cyber security strategies can be applied in smart grid?
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11
CYBER SECURITY STRATEGIES IN SMART GRID
How these cyber security strategies can be enhanced in smart grid?
Research Structure
Figure 4: Research Structure
(Source: Created by Author)
Research Methodology
Research methodology refers to the science of deciding about the approach followed in
the research. Research methodology compromises of two categories of approach include
qualitative and quantitative research approach. These approaches help in outlining study in the
research. This research will select positivism philosophy. Positivism philosophy deals with
collection of data with scientific way and a positive manner (Alvesson and Sköldberg 2017).
This research will select deductive approach to analyze cyber security strategies. The
Introduction
Literature Review
Research Methodology
Data findings and analysis
Conclusion and Recommendations
CYBER SECURITY STRATEGIES IN SMART GRID
How these cyber security strategies can be enhanced in smart grid?
Research Structure
Figure 4: Research Structure
(Source: Created by Author)
Research Methodology
Research methodology refers to the science of deciding about the approach followed in
the research. Research methodology compromises of two categories of approach include
qualitative and quantitative research approach. These approaches help in outlining study in the
research. This research will select positivism philosophy. Positivism philosophy deals with
collection of data with scientific way and a positive manner (Alvesson and Sköldberg 2017).
This research will select deductive approach to analyze cyber security strategies. The
Introduction
Literature Review
Research Methodology
Data findings and analysis
Conclusion and Recommendations

12
CYBER SECURITY STRATEGIES IN SMART GRID
quantitative investigation is also done by the deductive approach. A deductive approach is
capable of solving the focal point of the objective. Particular enquiries are also made by the
deductive approach. The deductive approach started from the intro and followed by the
application theory. The research design is used to collect important data through various
components with a logical and coherent way. The research design makes sure that the research
problem has been done correctly with the data analysis (Dang and Pheng 2015). The descriptive
design is one of the essential parts of the design to complete the process properly. The
spellbinding plan has been depicted in the research. The numerical path and the quantitative
examination, the subjective analysis can be completed through the process.
The methods of data gathering are of two types including secondary and primary method.
Primary method deals with raw collection of data from survey. Survey questionnaire used to
create with the help of Google Forms. Secondary collection of data method deals with data
collection from journals, articles and books that are available online. (Bauer 2014). Therefore,
this research will collect data from secondary data collection including online journals, articles
and books. Secondary data collection helps in collecting huge amount of data and information.
There will be 15 online journals related to cyber security strategies in smart grid.
Data analysis is of two types including qualitative and quantitative data analysis.
Quantitative analysis of data refers to analysis of primary data. Qualitative analysis of data refers
to analysis of secondary data. Therefore, qualitative data analysis will be selected in the research.
There will be three themes created using objectives of the research. This research will follow all
ethical consideration under academic research guidelines (Brinkmann 2014). Data will be
secured under Data Protection Act 1998. NO data will be tampered during data analysis method.
All journals will be taken after 2013 and connected to strategies of cyber security in smart grid.
CYBER SECURITY STRATEGIES IN SMART GRID
quantitative investigation is also done by the deductive approach. A deductive approach is
capable of solving the focal point of the objective. Particular enquiries are also made by the
deductive approach. The deductive approach started from the intro and followed by the
application theory. The research design is used to collect important data through various
components with a logical and coherent way. The research design makes sure that the research
problem has been done correctly with the data analysis (Dang and Pheng 2015). The descriptive
design is one of the essential parts of the design to complete the process properly. The
spellbinding plan has been depicted in the research. The numerical path and the quantitative
examination, the subjective analysis can be completed through the process.
The methods of data gathering are of two types including secondary and primary method.
Primary method deals with raw collection of data from survey. Survey questionnaire used to
create with the help of Google Forms. Secondary collection of data method deals with data
collection from journals, articles and books that are available online. (Bauer 2014). Therefore,
this research will collect data from secondary data collection including online journals, articles
and books. Secondary data collection helps in collecting huge amount of data and information.
There will be 15 online journals related to cyber security strategies in smart grid.
Data analysis is of two types including qualitative and quantitative data analysis.
Quantitative analysis of data refers to analysis of primary data. Qualitative analysis of data refers
to analysis of secondary data. Therefore, qualitative data analysis will be selected in the research.
There will be three themes created using objectives of the research. This research will follow all
ethical consideration under academic research guidelines (Brinkmann 2014). Data will be
secured under Data Protection Act 1998. NO data will be tampered during data analysis method.
All journals will be taken after 2013 and connected to strategies of cyber security in smart grid.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 46
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





