Analyzing Cyber Security Strategies for Smart Grid Technologies
VerifiedAdded on 2022/09/22
|19
|1170
|27
Presentation
AI Summary
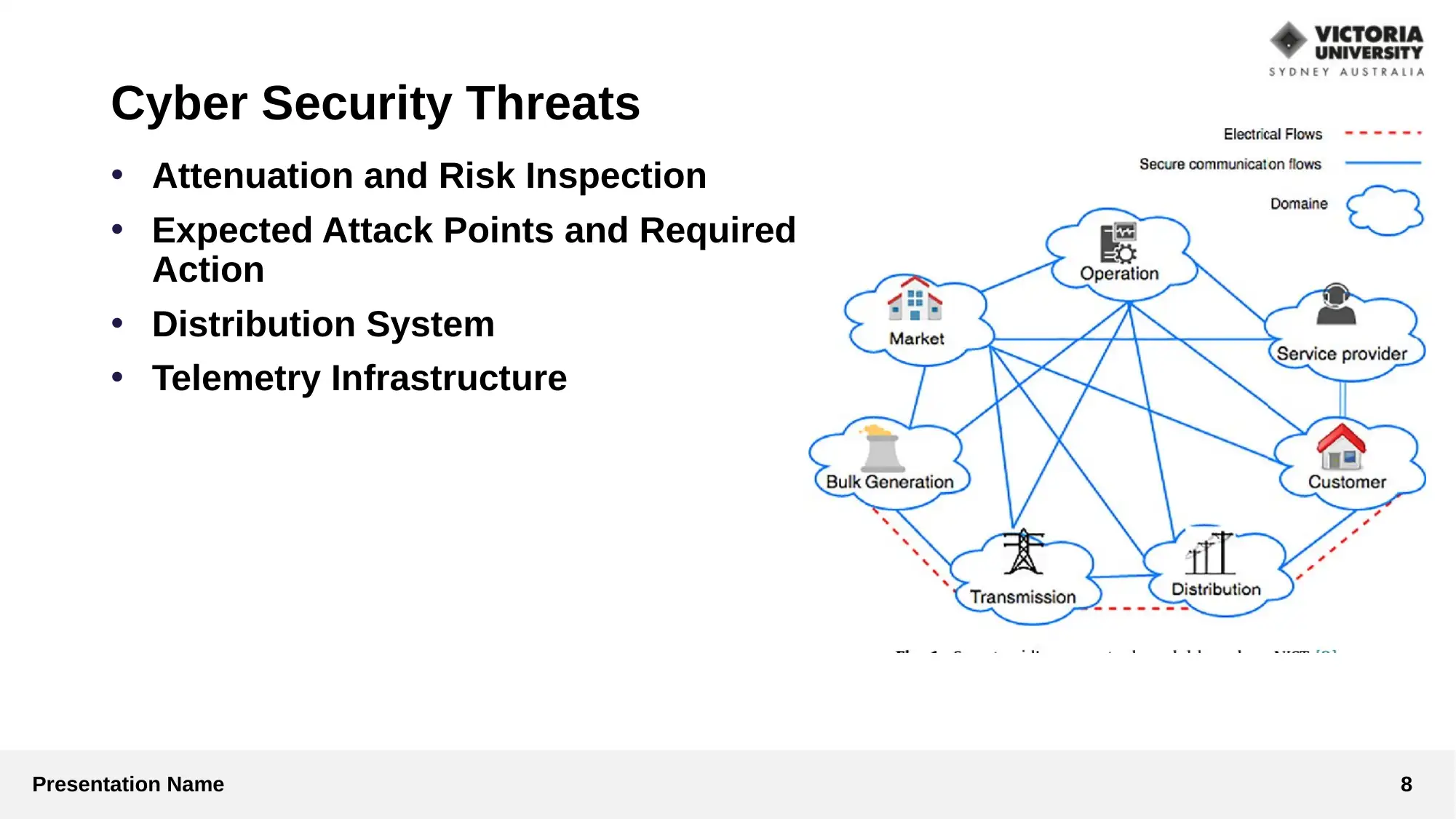
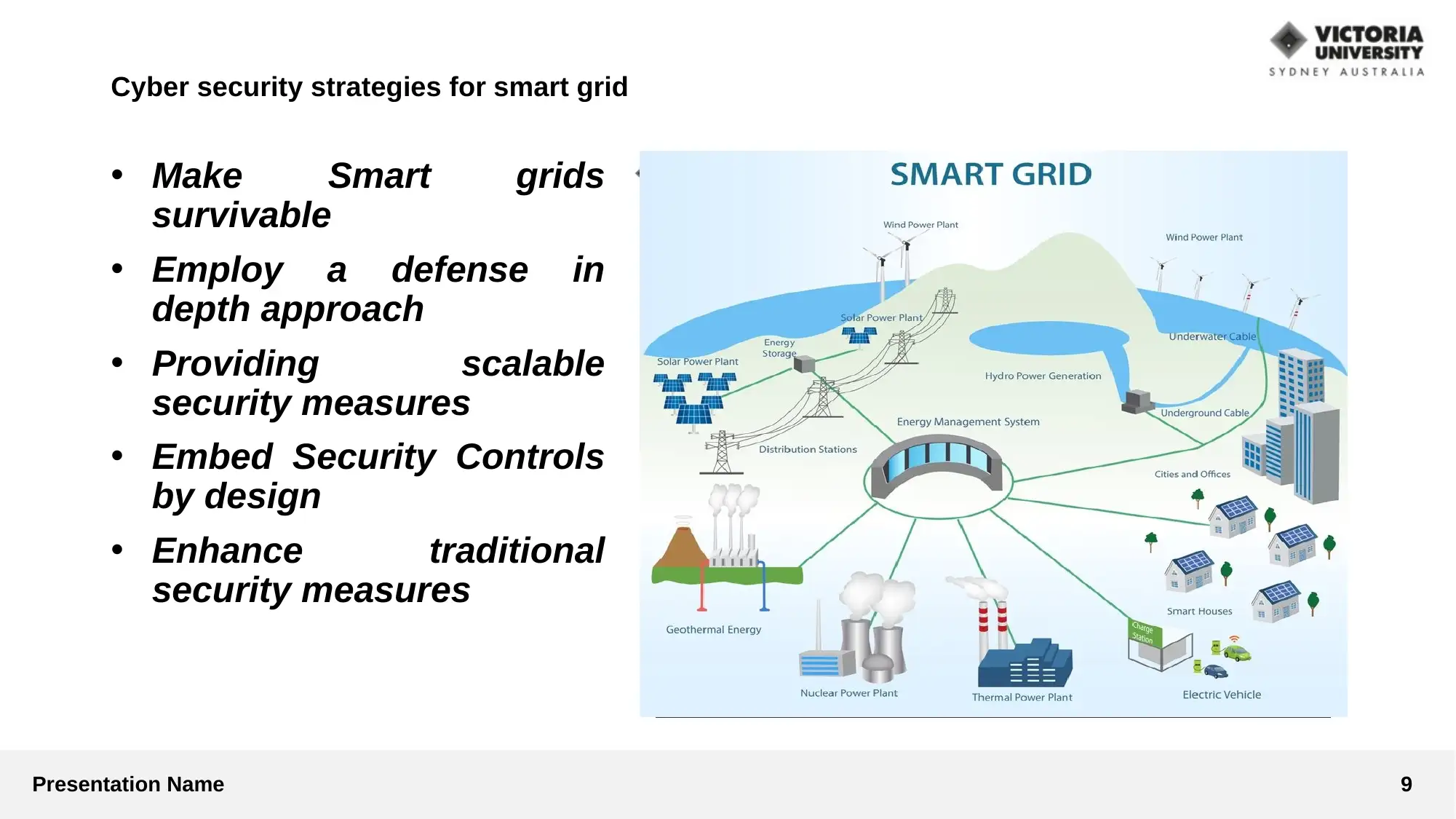
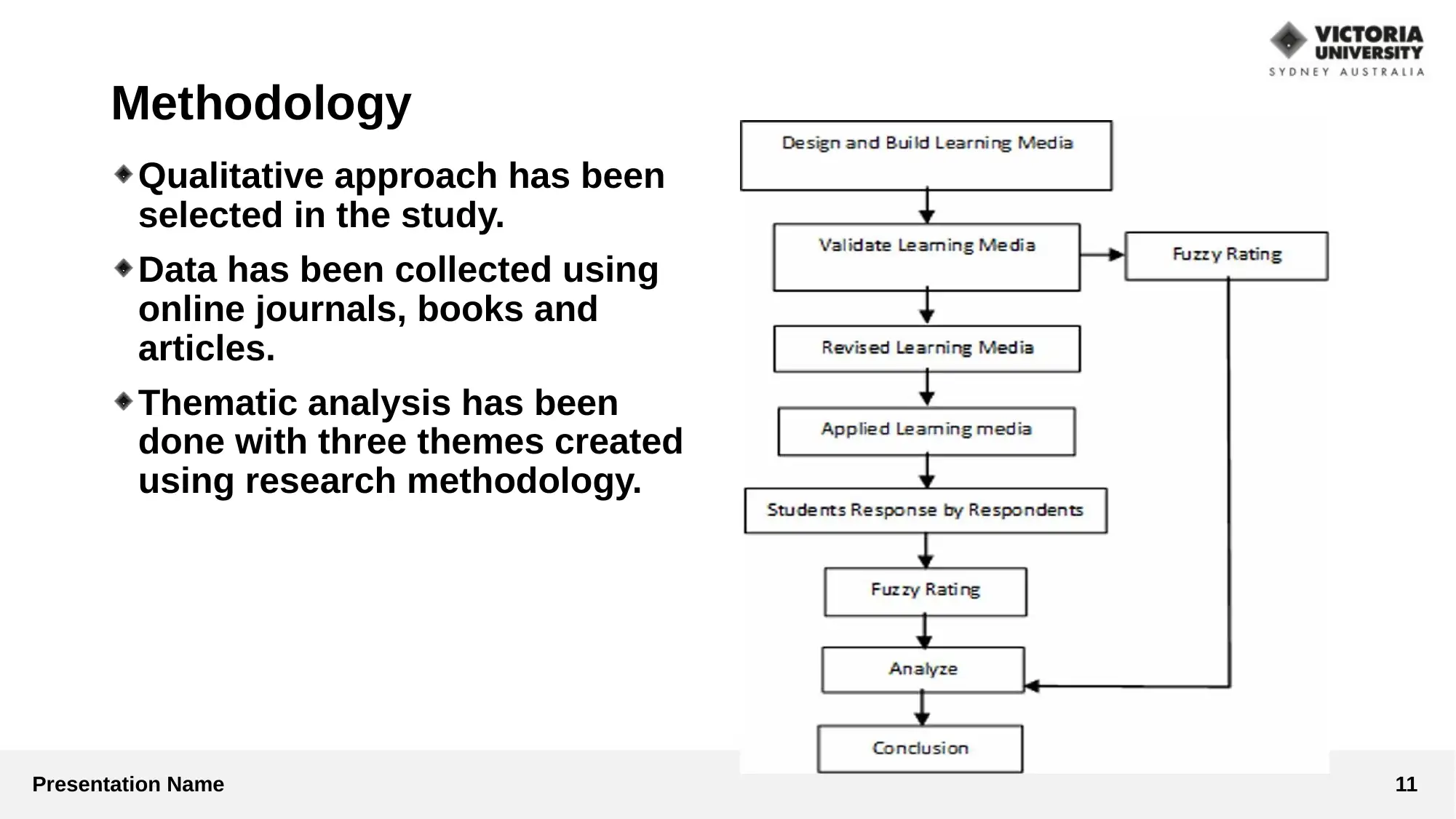
This presentation analyzes cyber security strategies within smart grid technologies. It begins by identifying key cyber security issues, such as false data injection attacks, attacks on AGC, and database vulnerabilities. The presentation then critically examines various strategies, including secure management, efficiency, scalability, and evolve-ability through key management protocols. It explores different approaches like defense-in-depth and the use of malware protection, network intrusion prevention systems, and VPN architectures. The methodology involves a qualitative approach using online journals, books, and articles with thematic analysis. The discussion and analysis highlight vulnerabilities in SCADA systems and the use of protocols like IEC 870-5-10x. The study concludes with recommendations for enhancing security concerns in smart grids, such as article validation, data protection, and the use of cryptography. References to relevant research papers and articles are also provided.
1 out of 19












![[object Object]](/_next/static/media/star-bottom.7253800d.svg)