Cyber Security Management: Risks, Mitigation, and Policies for SMEs
VerifiedAdded on 2020/05/08
|17
|3861
|45
Report
AI Summary
This report provides a comprehensive overview of cyber security management, focusing on the challenges and solutions for Small and Medium Enterprises (SMEs) in the context of cloud computing. It begins with an executive summary and table of contents, followed by an introduction that highlights the increasing importance of cloud security. The report delves into key security issues, including data breaches, account hijacking, insider threats, malware injection, abuse of cloud services, insecure APIs, denial-of-service attacks, shared vulnerabilities, and data loss. It then explores security risks and mitigation techniques, outlining processes to address data breaches, account hijacking, insider threats, malware injection, and abuse of cloud services. The report emphasizes the importance of conforming to external influences, reasoning, and application, including legal considerations and the establishment of relationships with cloud service providers. It also examines the application of current security management principles and methodologies, such as data transit protection, asset resilience, consumer separation, governance frameworks, operational security, personnel security, and secure development. Furthermore, the report discusses risk management frameworks and actionable risk mitigation steps, including examining business contexts, reviewing application security, and constructing a data-centric governance plan. The report concludes by emphasizing the importance of robust security measures for SMEs to protect their software technologies and in-house data.

Running head: CYBER SECURITY MANAGEMENT
Cyber security Management
Name of the student:
Name of the university:
Author Note
Cyber security Management
Name of the student:
Name of the university:
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBER SECURITY MANAGEMENT
Executive summary
The security of cloud computing is a fast developing service providing various functionalities. The
report is developed against the SMEs who needs protect the development the software technologies
and keeping the data in-house. The study analyzes the present methodologies and principles about
the Private Cloud provider organization.
Executive summary
The security of cloud computing is a fast developing service providing various functionalities. The
report is developed against the SMEs who needs protect the development the software technologies
and keeping the data in-house. The study analyzes the present methodologies and principles about
the Private Cloud provider organization.

2CYBER SECURITY MANAGEMENT
Table of Contents
Introduction:..........................................................................................................................................3
1. Security issues:..................................................................................................................................3
2. The security risks and mitigation techniques:...................................................................................5
3. Conforming to the external influences, the reasoning, and the application:.....................................6
4. Application of current security management principles and methodologies:...................................7
5. Risk & techniques:.............................................................................................................................9
6. The generic top-level security policy document:.............................................................................11
7. External factors application and consideration:...............................................................................15
Conclusion:..........................................................................................................................................16
References:..........................................................................................................................................17
Table of Contents
Introduction:..........................................................................................................................................3
1. Security issues:..................................................................................................................................3
2. The security risks and mitigation techniques:...................................................................................5
3. Conforming to the external influences, the reasoning, and the application:.....................................6
4. Application of current security management principles and methodologies:...................................7
5. Risk & techniques:.............................................................................................................................9
6. The generic top-level security policy document:.............................................................................11
7. External factors application and consideration:...............................................................................15
Conclusion:..........................................................................................................................................16
References:..........................................................................................................................................17
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CYBER SECURITY MANAGEMENT
Introduction:
The cloud computing security has been quick progressing service providing various
functionalities. This includes the safeguarding of the critical data from deletion, data leakage, and
theft.
The focus of the report is against the SMEs needing to protect the development the software
technologies and keeping the data in-house. The report investigates the present methodologies and
principles about the Private Cloud provider organization.
1. Security issues:
A small view of the current issues for the cloud-based services is described below according
to priority.
The issues Priorities Discussion
1. Data breaches High The data breaches in all forms have existed for
years. There is a rising concern with the sensitive
information stored online instead than on-premise
has the cloud been less safe inherently. The
overall data breaching has been three times to
occur more likely for the business utilizing the
cloud than those that have not. The cloud has
come with the unique set of properties that have
been more vulnerable (Choo 2014).
2. Hijacking of Accounts High The advent and implementation of the cloud have
Introduction:
The cloud computing security has been quick progressing service providing various
functionalities. This includes the safeguarding of the critical data from deletion, data leakage, and
theft.
The focus of the report is against the SMEs needing to protect the development the software
technologies and keeping the data in-house. The report investigates the present methodologies and
principles about the Private Cloud provider organization.
1. Security issues:
A small view of the current issues for the cloud-based services is described below according
to priority.
The issues Priorities Discussion
1. Data breaches High The data breaches in all forms have existed for
years. There is a rising concern with the sensitive
information stored online instead than on-premise
has the cloud been less safe inherently. The
overall data breaching has been three times to
occur more likely for the business utilizing the
cloud than those that have not. The cloud has
come with the unique set of properties that have
been more vulnerable (Choo 2014).
2. Hijacking of Accounts High The advent and implementation of the cloud have
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
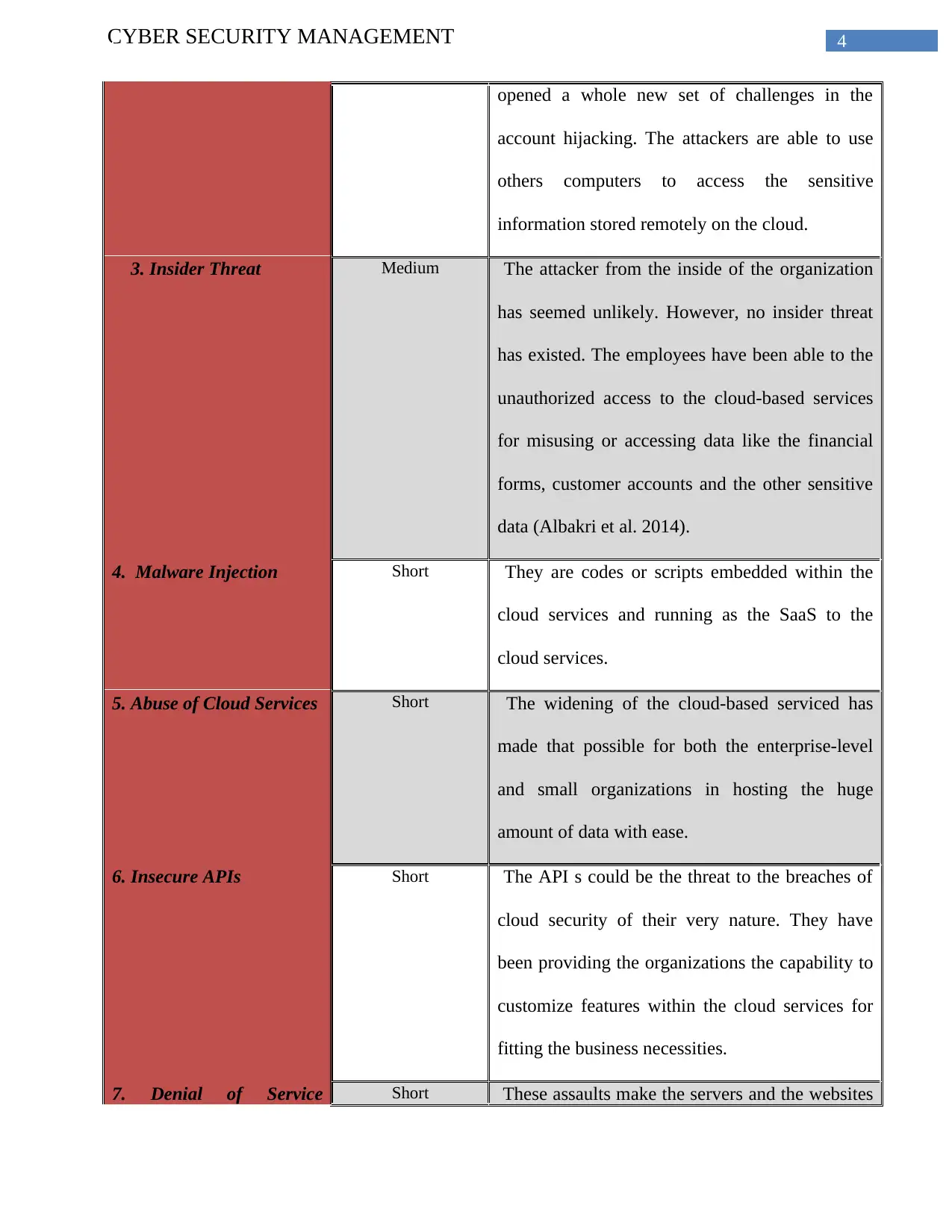
4CYBER SECURITY MANAGEMENT
opened a whole new set of challenges in the
account hijacking. The attackers are able to use
others computers to access the sensitive
information stored remotely on the cloud.
3. Insider Threat Medium The attacker from the inside of the organization
has seemed unlikely. However, no insider threat
has existed. The employees have been able to the
unauthorized access to the cloud-based services
for misusing or accessing data like the financial
forms, customer accounts and the other sensitive
data (Albakri et al. 2014).
4. Malware Injection Short They are codes or scripts embedded within the
cloud services and running as the SaaS to the
cloud services.
5. Abuse of Cloud Services Short The widening of the cloud-based serviced has
made that possible for both the enterprise-level
and small organizations in hosting the huge
amount of data with ease.
6. Insecure APIs Short The API s could be the threat to the breaches of
cloud security of their very nature. They have
been providing the organizations the capability to
customize features within the cloud services for
fitting the business necessities.
7. Denial of Service Short These assaults make the servers and the websites
opened a whole new set of challenges in the
account hijacking. The attackers are able to use
others computers to access the sensitive
information stored remotely on the cloud.
3. Insider Threat Medium The attacker from the inside of the organization
has seemed unlikely. However, no insider threat
has existed. The employees have been able to the
unauthorized access to the cloud-based services
for misusing or accessing data like the financial
forms, customer accounts and the other sensitive
data (Albakri et al. 2014).
4. Malware Injection Short They are codes or scripts embedded within the
cloud services and running as the SaaS to the
cloud services.
5. Abuse of Cloud Services Short The widening of the cloud-based serviced has
made that possible for both the enterprise-level
and small organizations in hosting the huge
amount of data with ease.
6. Insecure APIs Short The API s could be the threat to the breaches of
cloud security of their very nature. They have
been providing the organizations the capability to
customize features within the cloud services for
fitting the business necessities.
7. Denial of Service Short These assaults make the servers and the websites
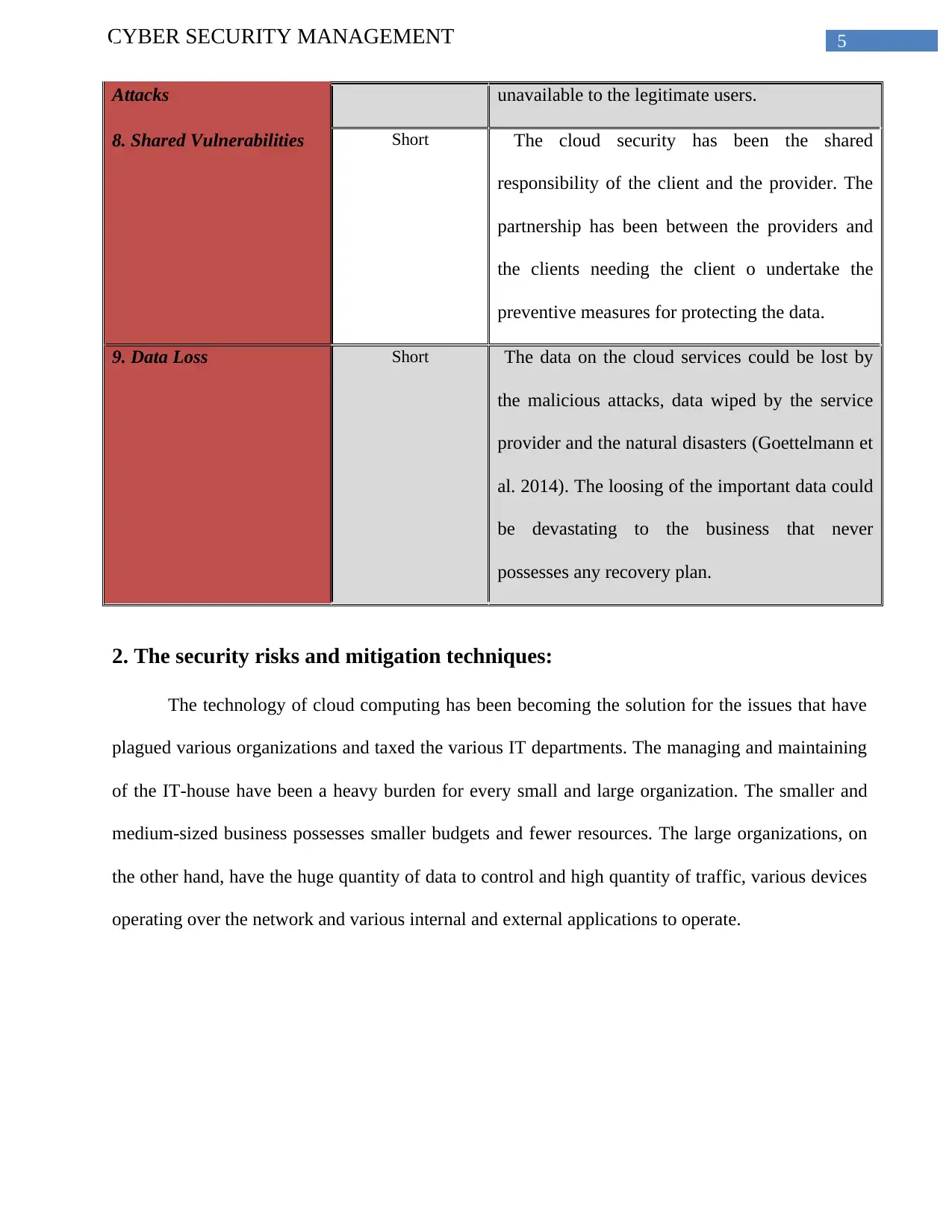
5CYBER SECURITY MANAGEMENT
Attacks unavailable to the legitimate users.
8. Shared Vulnerabilities Short The cloud security has been the shared
responsibility of the client and the provider. The
partnership has been between the providers and
the clients needing the client o undertake the
preventive measures for protecting the data.
9. Data Loss Short The data on the cloud services could be lost by
the malicious attacks, data wiped by the service
provider and the natural disasters (Goettelmann et
al. 2014). The loosing of the important data could
be devastating to the business that never
possesses any recovery plan.
2. The security risks and mitigation techniques:
The technology of cloud computing has been becoming the solution for the issues that have
plagued various organizations and taxed the various IT departments. The managing and maintaining
of the IT-house have been a heavy burden for every small and large organization. The smaller and
medium-sized business possesses smaller budgets and fewer resources. The large organizations, on
the other hand, have the huge quantity of data to control and high quantity of traffic, various devices
operating over the network and various internal and external applications to operate.
Attacks unavailable to the legitimate users.
8. Shared Vulnerabilities Short The cloud security has been the shared
responsibility of the client and the provider. The
partnership has been between the providers and
the clients needing the client o undertake the
preventive measures for protecting the data.
9. Data Loss Short The data on the cloud services could be lost by
the malicious attacks, data wiped by the service
provider and the natural disasters (Goettelmann et
al. 2014). The loosing of the important data could
be devastating to the business that never
possesses any recovery plan.
2. The security risks and mitigation techniques:
The technology of cloud computing has been becoming the solution for the issues that have
plagued various organizations and taxed the various IT departments. The managing and maintaining
of the IT-house have been a heavy burden for every small and large organization. The smaller and
medium-sized business possesses smaller budgets and fewer resources. The large organizations, on
the other hand, have the huge quantity of data to control and high quantity of traffic, various devices
operating over the network and various internal and external applications to operate.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CYBER SECURITY MANAGEMENT
The processes of mitigating the risks:
The risks Process of mitigations
Data breaches It can be mitigated through prioritizing the data protection. This increases the
effectiveness through identifying to secure the most important resources.
Hijacking of
accounts
This can be fought by using the scanning software. This proactively defends
and recognizes the phishing attacks. There can be also the updating of the
current single-factor customer authentication based on passwords to the two-
factor authentication.
Insider Threat This could be defended by detecting the anomalous behavior to recognize the
suspicious activities out of the normal standard of the employees (Ali, Khan and
Vasilakos 2015). Further the hybrid analytics is also helpful here referring to
the assimilation of the threat detecting techniques with the informed behavioral
analytics.
Malware
Injection
The WAF or Web Application Firewall could be deployed at the boundary of
the network. This must also include the reputational and behavioral analysis for
blocking every malware injection attacks on the web applications and sites
(Latif et al. 2014). Moreover, the backdoor protect is useful intercepting the
communication attempts with the backdoor shells on the web server. Through
tracing the requests, the service points out the most dangerous obfuscated
malware.
Abuse of Cloud
Services
A single sign-on SSO is needed to be utilized in the organization (Latif et al.
2014). The organization should be using various applications and cloud service
along with the individual users having various sets of credentials. All of them
could be exposed. The SSO indicates that there have been lesser accounts for
The processes of mitigating the risks:
The risks Process of mitigations
Data breaches It can be mitigated through prioritizing the data protection. This increases the
effectiveness through identifying to secure the most important resources.
Hijacking of
accounts
This can be fought by using the scanning software. This proactively defends
and recognizes the phishing attacks. There can be also the updating of the
current single-factor customer authentication based on passwords to the two-
factor authentication.
Insider Threat This could be defended by detecting the anomalous behavior to recognize the
suspicious activities out of the normal standard of the employees (Ali, Khan and
Vasilakos 2015). Further the hybrid analytics is also helpful here referring to
the assimilation of the threat detecting techniques with the informed behavioral
analytics.
Malware
Injection
The WAF or Web Application Firewall could be deployed at the boundary of
the network. This must also include the reputational and behavioral analysis for
blocking every malware injection attacks on the web applications and sites
(Latif et al. 2014). Moreover, the backdoor protect is useful intercepting the
communication attempts with the backdoor shells on the web server. Through
tracing the requests, the service points out the most dangerous obfuscated
malware.
Abuse of Cloud
Services
A single sign-on SSO is needed to be utilized in the organization (Latif et al.
2014). The organization should be using various applications and cloud service
along with the individual users having various sets of credentials. All of them
could be exposed. The SSO indicates that there have been lesser accounts for
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBER SECURITY MANAGEMENT
managing the users entering and leaving the organization.
3. Conforming to the external influences, the reasoning, and the application:
The legal service providers must consult with the experts of the computer prior to the user of
cloud services. They must make sense of the effective security threats they have been facing. They
must recognize the best available measures of security and the security standards that are generally
accepted. The legal service providers must analyze the various levels of the security sensitivity
related to the communications and data. They must develop the proper plans for managing the
various kinds of communications and data appropriately. Then the organizations should also find
what materials must be retained in the paper form or the hard-copy.
The proper relationships with the providers of cloud services are needed to be established.
Various substantial cares must be applied to select the cloud service providers. Just only the reliable
and reputable service providers must be used. The fully enforceable agreements in written format
must be utilized for defining every term of the service. The legal service providers must fully make
sense of every aspect of the terms of services (Pearson 2013). This is, in particular, the provisions
that are applicable to the procedures, data security related to the security breaches, enhancements.
This must also include the backing-up of systems and the processes in the event of the security
breaches and the other failures in services. The terms of the service must also deliver the extreme
control on the data involved. This must also include the control and ownership of the data while the
service arrangements get ended. This must include the resting with the legal service providers, not
the cloud service providers. The enforceable and the adequate non-disclosure provisions regarding
the proprietary and confidential material must be included within the terms of the services
(Goettelmann, Mayer and Godart 2014).
managing the users entering and leaving the organization.
3. Conforming to the external influences, the reasoning, and the application:
The legal service providers must consult with the experts of the computer prior to the user of
cloud services. They must make sense of the effective security threats they have been facing. They
must recognize the best available measures of security and the security standards that are generally
accepted. The legal service providers must analyze the various levels of the security sensitivity
related to the communications and data. They must develop the proper plans for managing the
various kinds of communications and data appropriately. Then the organizations should also find
what materials must be retained in the paper form or the hard-copy.
The proper relationships with the providers of cloud services are needed to be established.
Various substantial cares must be applied to select the cloud service providers. Just only the reliable
and reputable service providers must be used. The fully enforceable agreements in written format
must be utilized for defining every term of the service. The legal service providers must fully make
sense of every aspect of the terms of services (Pearson 2013). This is, in particular, the provisions
that are applicable to the procedures, data security related to the security breaches, enhancements.
This must also include the backing-up of systems and the processes in the event of the security
breaches and the other failures in services. The terms of the service must also deliver the extreme
control on the data involved. This must also include the control and ownership of the data while the
service arrangements get ended. This must include the resting with the legal service providers, not
the cloud service providers. The enforceable and the adequate non-disclosure provisions regarding
the proprietary and confidential material must be included within the terms of the services
(Goettelmann, Mayer and Godart 2014).
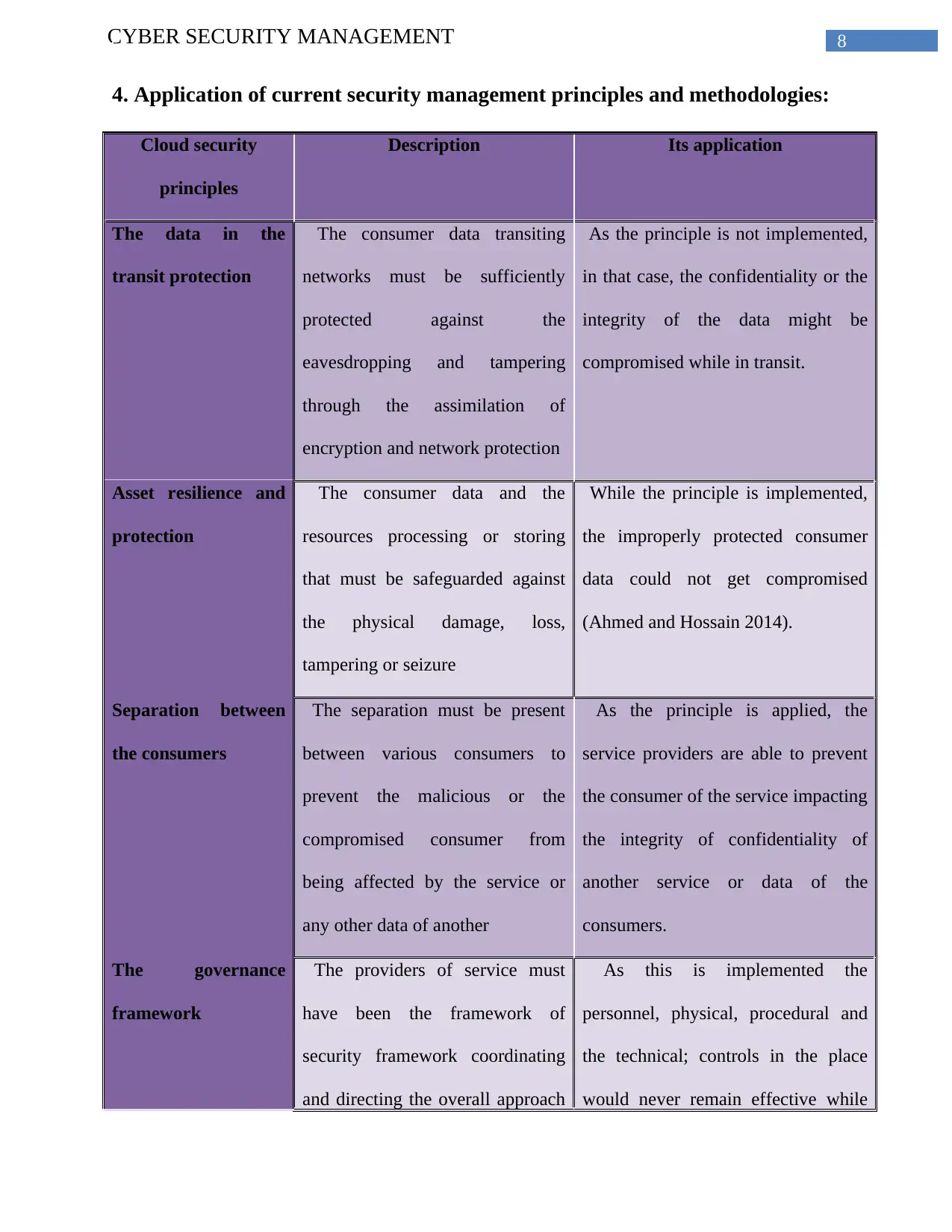
8CYBER SECURITY MANAGEMENT
4. Application of current security management principles and methodologies:
Cloud security
principles
Description Its application
The data in the
transit protection
The consumer data transiting
networks must be sufficiently
protected against the
eavesdropping and tampering
through the assimilation of
encryption and network protection
As the principle is not implemented,
in that case, the confidentiality or the
integrity of the data might be
compromised while in transit.
Asset resilience and
protection
The consumer data and the
resources processing or storing
that must be safeguarded against
the physical damage, loss,
tampering or seizure
While the principle is implemented,
the improperly protected consumer
data could not get compromised
(Ahmed and Hossain 2014).
Separation between
the consumers
The separation must be present
between various consumers to
prevent the malicious or the
compromised consumer from
being affected by the service or
any other data of another
As the principle is applied, the
service providers are able to prevent
the consumer of the service impacting
the integrity of confidentiality of
another service or data of the
consumers.
The governance
framework
The providers of service must
have been the framework of
security framework coordinating
and directing the overall approach
As this is implemented the
personnel, physical, procedural and
the technical; controls in the place
would never remain effective while
4. Application of current security management principles and methodologies:
Cloud security
principles
Description Its application
The data in the
transit protection
The consumer data transiting
networks must be sufficiently
protected against the
eavesdropping and tampering
through the assimilation of
encryption and network protection
As the principle is not implemented,
in that case, the confidentiality or the
integrity of the data might be
compromised while in transit.
Asset resilience and
protection
The consumer data and the
resources processing or storing
that must be safeguarded against
the physical damage, loss,
tampering or seizure
While the principle is implemented,
the improperly protected consumer
data could not get compromised
(Ahmed and Hossain 2014).
Separation between
the consumers
The separation must be present
between various consumers to
prevent the malicious or the
compromised consumer from
being affected by the service or
any other data of another
As the principle is applied, the
service providers are able to prevent
the consumer of the service impacting
the integrity of confidentiality of
another service or data of the
consumers.
The governance
framework
The providers of service must
have been the framework of
security framework coordinating
and directing the overall approach
As this is implemented the
personnel, physical, procedural and
the technical; controls in the place
would never remain effective while
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
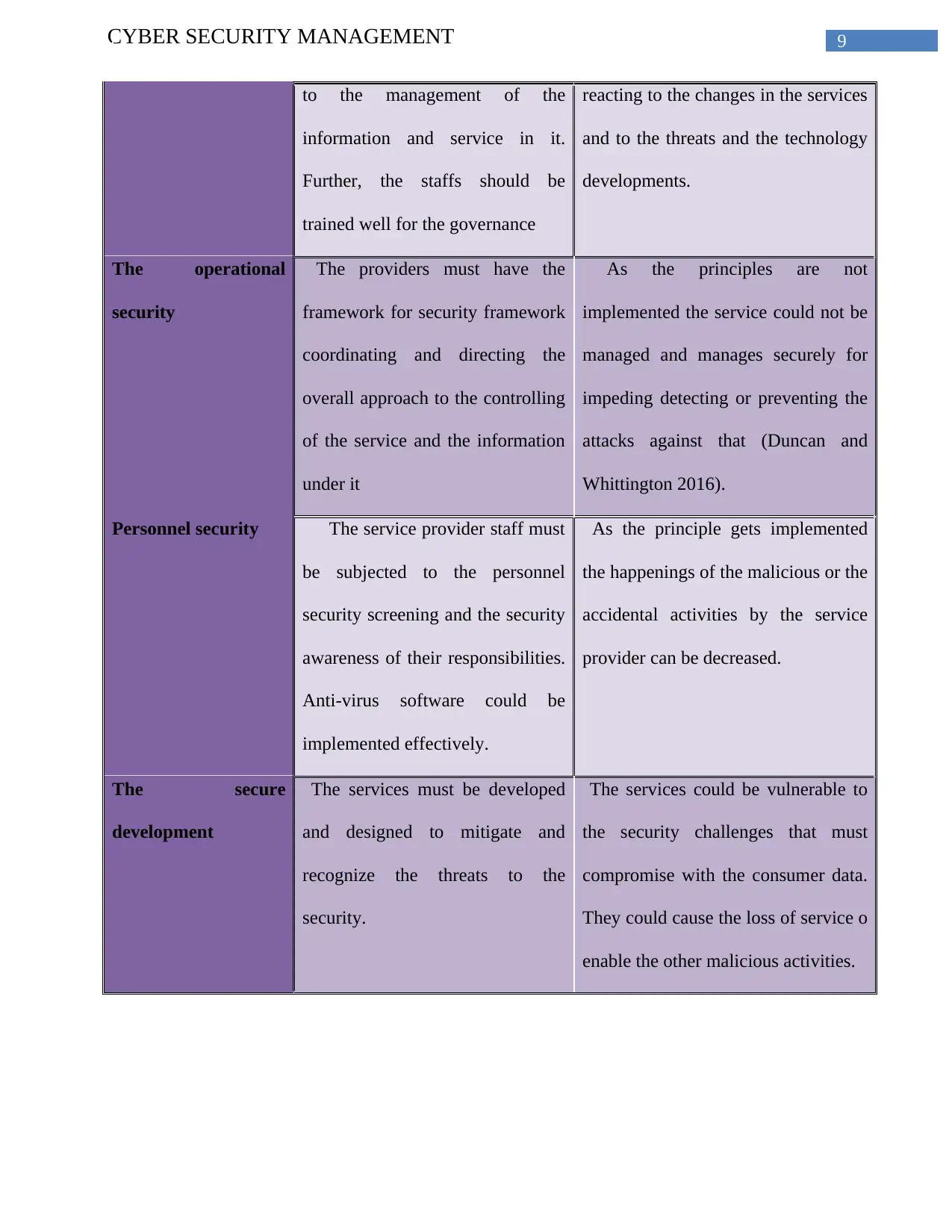
9CYBER SECURITY MANAGEMENT
to the management of the
information and service in it.
Further, the staffs should be
trained well for the governance
reacting to the changes in the services
and to the threats and the technology
developments.
The operational
security
The providers must have the
framework for security framework
coordinating and directing the
overall approach to the controlling
of the service and the information
under it
As the principles are not
implemented the service could not be
managed and manages securely for
impeding detecting or preventing the
attacks against that (Duncan and
Whittington 2016).
Personnel security The service provider staff must
be subjected to the personnel
security screening and the security
awareness of their responsibilities.
Anti-virus software could be
implemented effectively.
As the principle gets implemented
the happenings of the malicious or the
accidental activities by the service
provider can be decreased.
The secure
development
The services must be developed
and designed to mitigate and
recognize the threats to the
security.
The services could be vulnerable to
the security challenges that must
compromise with the consumer data.
They could cause the loss of service o
enable the other malicious activities.
to the management of the
information and service in it.
Further, the staffs should be
trained well for the governance
reacting to the changes in the services
and to the threats and the technology
developments.
The operational
security
The providers must have the
framework for security framework
coordinating and directing the
overall approach to the controlling
of the service and the information
under it
As the principles are not
implemented the service could not be
managed and manages securely for
impeding detecting or preventing the
attacks against that (Duncan and
Whittington 2016).
Personnel security The service provider staff must
be subjected to the personnel
security screening and the security
awareness of their responsibilities.
Anti-virus software could be
implemented effectively.
As the principle gets implemented
the happenings of the malicious or the
accidental activities by the service
provider can be decreased.
The secure
development
The services must be developed
and designed to mitigate and
recognize the threats to the
security.
The services could be vulnerable to
the security challenges that must
compromise with the consumer data.
They could cause the loss of service o
enable the other malicious activities.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CYBER SECURITY MANAGEMENT
5. Risk & techniques:
The organizations are able to pursue the risk management in various frameworks. There have
been various differences in the frameworks with few underlying principles. The risk mitigation has
been could be included typically in the wider risk management processes. The steps could be
retrieved from the process of risk management. They could be considered as their individual risk in
the process of mitigation.
The actionable risk mitigation steps are:
Examining the business contexts:
It indicates the analyzing the kinds of services and the data handled. Then the threats are
considered against those services and the data. The IT leaders have been meeting various questions
while analyzing those threats for every services and data set. Those steps have been including the
implementation of the fundamental management and the operational security controls for the data
and services (Luna et al. 2015). Those controls have been including the related procedures and
security policies, basic audit controls, service-level agreements SLAs and with other forms of
governances.
Reviewing the application security:
Analyzing the application securities has been a critical step in risk mitigation process.
Further, it has been important to find out what has been featuring the application that has been
offered regarding the mitigation risks. It has been important that the IT managers must consider how
robust the features have been. For instance, as the application has been encrypting the data at rest for
protecting the confidentiality, the encryption coding and the key length has been used is needed to be
determined. Along with this how strong the key combination and the algorithm has been needed to
find out.
5. Risk & techniques:
The organizations are able to pursue the risk management in various frameworks. There have
been various differences in the frameworks with few underlying principles. The risk mitigation has
been could be included typically in the wider risk management processes. The steps could be
retrieved from the process of risk management. They could be considered as their individual risk in
the process of mitigation.
The actionable risk mitigation steps are:
Examining the business contexts:
It indicates the analyzing the kinds of services and the data handled. Then the threats are
considered against those services and the data. The IT leaders have been meeting various questions
while analyzing those threats for every services and data set. Those steps have been including the
implementation of the fundamental management and the operational security controls for the data
and services (Luna et al. 2015). Those controls have been including the related procedures and
security policies, basic audit controls, service-level agreements SLAs and with other forms of
governances.
Reviewing the application security:
Analyzing the application securities has been a critical step in risk mitigation process.
Further, it has been important to find out what has been featuring the application that has been
offered regarding the mitigation risks. It has been important that the IT managers must consider how
robust the features have been. For instance, as the application has been encrypting the data at rest for
protecting the confidentiality, the encryption coding and the key length has been used is needed to be
determined. Along with this how strong the key combination and the algorithm has been needed to
find out.
11CYBER SECURITY MANAGEMENT
Constructing a data-centric governance plan:
The data governance has been involving the managing of data via the enterprise like
performing the backups, archiving the old data and then controlling the requests of e-discovery. It
has been researched that about half of the enterprises have no policy of data governance (Modi et al.
2013). It has been increasing the chances that the data would be placed at the wrong place. It has
been making that more susceptible in compromising.
Testing and retesting:
As the data-centric governance plan gets implemented the IT staffs could test that
periodically. It has been including the actions like verification of the integrity of the backups. It has
been assuring that the achieved data has been stored securely and assuring the unnecessary data has
been destroyed efficiently.
6. The generic top-level security policy document:
The security policies must undergo the following:
Policies The risks to
be mitigated.
Discussion ISO
standards
to be used
Type of
the
standard
Reason to use the
standard
It should
be easy to
understan
d
Abuse of cloud
services.
The security
policies
should meet
the perquisites
of the intended
clients. The
ISO/IEC
27000
Normativ
e
references
Every definitions and
specialist terms are
defined in the ISO/IEC
27000. It is mainly
applicable around the
entire ISO27
Constructing a data-centric governance plan:
The data governance has been involving the managing of data via the enterprise like
performing the backups, archiving the old data and then controlling the requests of e-discovery. It
has been researched that about half of the enterprises have no policy of data governance (Modi et al.
2013). It has been increasing the chances that the data would be placed at the wrong place. It has
been making that more susceptible in compromising.
Testing and retesting:
As the data-centric governance plan gets implemented the IT staffs could test that
periodically. It has been including the actions like verification of the integrity of the backups. It has
been assuring that the achieved data has been stored securely and assuring the unnecessary data has
been destroyed efficiently.
6. The generic top-level security policy document:
The security policies must undergo the following:
Policies The risks to
be mitigated.
Discussion ISO
standards
to be used
Type of
the
standard
Reason to use the
standard
It should
be easy to
understan
d
Abuse of cloud
services.
The security
policies
should meet
the perquisites
of the intended
clients. The
ISO/IEC
27000
Normativ
e
references
Every definitions and
specialist terms are
defined in the ISO/IEC
27000. It is mainly
applicable around the
entire ISO27
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


