Cyber Security Threats and Solutions for JL Company Report
VerifiedAdded on 2023/01/09
|15
|3783
|56
Report
AI Summary
This report provides a comprehensive analysis of the cyber security issues faced by JL Company, a small accounting firm in Perth, Australia. The company is experiencing several vulnerabilities, including outdated systems, lack of security software, and reliance on insecure network configurations. The report identifies key threats such as malware, data breaches, and the absence of employee security policies. It proposes a cloud-based solution, emphasizing the benefits of cloud security features like perimeter firewalls, intrusion detection, and data encryption. The report also highlights the importance of addressing issues like spam messages and unauthorized data access. By transitioning to a cloud environment, JL Company can mitigate risks, enhance data protection, and improve its overall security posture, enabling it to safely expand its online presence.

Running head: CYBER SECURITY ISSUES
Cyber security issues
Name of the student:
Name of the university:
Author note:
Cyber security issues
Name of the student:
Name of the university:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBER SECURITY ISSUES
Abstract
The report is prepared to discuss about the current security threats that the organisation of JL
company is facing recently. Among major of the security threats that are mentioned, five
important security issues are identified within the organisation which needs urgent attention.
The report reflects the possible risks that might occur if this risk is not resolved and based on
it possible security approach is recommended in the last part of the report. A brief
comparison is thus mentioned in the report on the different types of approaches that the
company can follow and finally recommending the best approach towards mitigating those
issues.
Abstract
The report is prepared to discuss about the current security threats that the organisation of JL
company is facing recently. Among major of the security threats that are mentioned, five
important security issues are identified within the organisation which needs urgent attention.
The report reflects the possible risks that might occur if this risk is not resolved and based on
it possible security approach is recommended in the last part of the report. A brief
comparison is thus mentioned in the report on the different types of approaches that the
company can follow and finally recommending the best approach towards mitigating those
issues.

2CYBER SECURITY ISSUES
Table of Contents
Introduction:...............................................................................................................................3
Cyber security issues related to the organisation:......................................................................4
Need to address the cyber security issues immediately:........................................................7
Solutions to address the identified cyber security issues:......................................................7
Comparison between the different alternative approaches in order to address the security
issues:.....................................................................................................................................9
Cost breakdown to implement the solution for the identified issues:..................................11
Conclusion:..............................................................................................................................11
References:...............................................................................................................................12
Table of Contents
Introduction:...............................................................................................................................3
Cyber security issues related to the organisation:......................................................................4
Need to address the cyber security issues immediately:........................................................7
Solutions to address the identified cyber security issues:......................................................7
Comparison between the different alternative approaches in order to address the security
issues:.....................................................................................................................................9
Cost breakdown to implement the solution for the identified issues:..................................11
Conclusion:..............................................................................................................................11
References:...............................................................................................................................12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CYBER SECURITY ISSUES
Introduction:
With more and more daily business activities moving online, it is becoming
increasingly important for companies to ensure that no one is attempting to steal their data or
money. That is why cyber security plays a significant role in business. Cyber security
involves the protection of computer-based equipment and information from unintended or
unauthorized access changed mode of destruction (Srinivasan, 2014). A cyber attack takes
several forms including theft or unauthorized access of computers, laptops, tablets or mobile
devices a remote attack on Information technology systems or websites, attacks on
information held in third party systems such as cloud devices. It is very important for
companies to protect themselves from the threat of scams, data thefts and other online
vulnerabilities(Tisdale, 2015). Here the chosen business organisation is named as JL
company on which the further cyber risk assessment is made.
Overview of the company: JL is a small company mainly working on accounting related
works. The company resides in Perth, Western Australia. As a means to progress in the online
marketing field, the company started communicating and transferring some confidential files
and documents to their clients with the help of variety of online services. But recently the
company is facing some kind of problems related to slowing down of computers, random
malware inspired popups and many other failures of the operating systems that are being used
in the company. All these issues that are arising in the company may lead to some serious
cyber related threats that might take up the whole business. The following report is thus
presented based on the possible cyber security issues that are related to the JL company and
those which need immediate attention to be resolved.
Introduction:
With more and more daily business activities moving online, it is becoming
increasingly important for companies to ensure that no one is attempting to steal their data or
money. That is why cyber security plays a significant role in business. Cyber security
involves the protection of computer-based equipment and information from unintended or
unauthorized access changed mode of destruction (Srinivasan, 2014). A cyber attack takes
several forms including theft or unauthorized access of computers, laptops, tablets or mobile
devices a remote attack on Information technology systems or websites, attacks on
information held in third party systems such as cloud devices. It is very important for
companies to protect themselves from the threat of scams, data thefts and other online
vulnerabilities(Tisdale, 2015). Here the chosen business organisation is named as JL
company on which the further cyber risk assessment is made.
Overview of the company: JL is a small company mainly working on accounting related
works. The company resides in Perth, Western Australia. As a means to progress in the online
marketing field, the company started communicating and transferring some confidential files
and documents to their clients with the help of variety of online services. But recently the
company is facing some kind of problems related to slowing down of computers, random
malware inspired popups and many other failures of the operating systems that are being used
in the company. All these issues that are arising in the company may lead to some serious
cyber related threats that might take up the whole business. The following report is thus
presented based on the possible cyber security issues that are related to the JL company and
those which need immediate attention to be resolved.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CYBER SECURITY ISSUES
Cyber security issues related to the organisation:
As far as the current situation of the JL company concerns there are major security
risks that are associated with every step that the company is operating on. The cyber security
issues that are identified within the organisation are mentioned as follows:
1. The SOE of the company consists of Windows 10 laptops, all of which are
currently updated with the most recent Microsoft updates: According to recent
researches, there are some problems going on with the most recent update of the
Microsoft in Windows 10. The last update that came in the year 2019 has more
serious issues than the previous ones (Wash et al., 2014). As most of the computers
now a days are installed with windows 10, hence the security concern is rising day by
day. According to reports, companies like JL who have computers with this kind of
updates are in the verge of experiencing automatic restart of computer systems
leading to activation of the active hour feature in the system. This is a serious
security concern as this kind of behavior of the system may prevent users from
restarting their systems during the automatic operation of the system.
2. None of the laptops used in the company contain any security software:
Information technology security software are essential to use in any business in order
to protect the computer networks used in the business process. It acts as a defense to
prevent unauthorized access in organisations systems (Madzima, Moyo & Abdullah,
2014). As none of the laptops in the company has these features installed among them
hence it may cause a severe security risks in terms of unauthenticated access into their
systems leading to major data breach.
3. The company uses D-Link DSL-2740B wireless router to access internet via
ADSL: According to some reports, the first generation of the ADSL routers are
encompassed with certain flaws which allowed the devices connecting to it to be
Cyber security issues related to the organisation:
As far as the current situation of the JL company concerns there are major security
risks that are associated with every step that the company is operating on. The cyber security
issues that are identified within the organisation are mentioned as follows:
1. The SOE of the company consists of Windows 10 laptops, all of which are
currently updated with the most recent Microsoft updates: According to recent
researches, there are some problems going on with the most recent update of the
Microsoft in Windows 10. The last update that came in the year 2019 has more
serious issues than the previous ones (Wash et al., 2014). As most of the computers
now a days are installed with windows 10, hence the security concern is rising day by
day. According to reports, companies like JL who have computers with this kind of
updates are in the verge of experiencing automatic restart of computer systems
leading to activation of the active hour feature in the system. This is a serious
security concern as this kind of behavior of the system may prevent users from
restarting their systems during the automatic operation of the system.
2. None of the laptops used in the company contain any security software:
Information technology security software are essential to use in any business in order
to protect the computer networks used in the business process. It acts as a defense to
prevent unauthorized access in organisations systems (Madzima, Moyo & Abdullah,
2014). As none of the laptops in the company has these features installed among them
hence it may cause a severe security risks in terms of unauthenticated access into their
systems leading to major data breach.
3. The company uses D-Link DSL-2740B wireless router to access internet via
ADSL: According to some reports, the first generation of the ADSL routers are
encompassed with certain flaws which allowed the devices connecting to it to be

5CYBER SECURITY ISSUES
accessed and controlled remotely. In 2009, a new type of malware had been detected
which targeted the ADSL routers (Στασινόπουλος, 2014). The issues related to
wireless network is a common vulnerability that is affected via the use of this kind of
routers. Hence as the company is using this type of router to access their internet
services hence, they are also in the list of getting attacked by the possible
vulnerabilities related to the use of ADSL router.
4. The company previously was using the windows 2000 server but due to some
power cut problem it is no longer in a functioning state: Now, windows 2000
server is considered to be one of the most secured servers offering features for
securing data stored in the computers (Alnatheer, 2014). It facilitates features with
enhanced security measures that were designed to meet the needs of expanding
businesses online. So, for JL company as they are moving towards online business
hence it would have been beneficial if they used the windows 2000 server again.
5. As the company reported that, each employee receives an average of 40 spam
messages each day: Receiving spam messages on a daily basis in a business
organisation is a signal for the upcoming threats that might take up the business
organisation attacking each computer via the spam messages. This type of attack is
defined to be a particular cyber threat known as Phishing (Arachchilage & Love,
2014).
6. The organization has a previous record of getting attacked by ransomware: It is
being reported by the manager of the organisation that on July 2017, the company
faced a major cyber threat in terms of ransomware attack (Richardson & North,
2017). But no such actions were taken by the higher officials of the business in
order to patch their systems against the future possible attacks instead they paid the
accessed and controlled remotely. In 2009, a new type of malware had been detected
which targeted the ADSL routers (Στασινόπουλος, 2014). The issues related to
wireless network is a common vulnerability that is affected via the use of this kind of
routers. Hence as the company is using this type of router to access their internet
services hence, they are also in the list of getting attacked by the possible
vulnerabilities related to the use of ADSL router.
4. The company previously was using the windows 2000 server but due to some
power cut problem it is no longer in a functioning state: Now, windows 2000
server is considered to be one of the most secured servers offering features for
securing data stored in the computers (Alnatheer, 2014). It facilitates features with
enhanced security measures that were designed to meet the needs of expanding
businesses online. So, for JL company as they are moving towards online business
hence it would have been beneficial if they used the windows 2000 server again.
5. As the company reported that, each employee receives an average of 40 spam
messages each day: Receiving spam messages on a daily basis in a business
organisation is a signal for the upcoming threats that might take up the business
organisation attacking each computer via the spam messages. This type of attack is
defined to be a particular cyber threat known as Phishing (Arachchilage & Love,
2014).
6. The organization has a previous record of getting attacked by ransomware: It is
being reported by the manager of the organisation that on July 2017, the company
faced a major cyber threat in terms of ransomware attack (Richardson & North,
2017). But no such actions were taken by the higher officials of the business in
order to patch their systems against the future possible attacks instead they paid the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CYBER SECURITY ISSUES
ransomware that was demanded by the hackers. This is a major drawback that the
company is facing recently as the matter of security is still not resolved.
7. There are no policies or rules for employees on using the computer systems
effectively without getting attacked by hackers: It is important for every company
to set up some security policies and rules that needs to be followed by employees
while using the computer systems for business purposes (Safa, Von Solms & Furnell,
2016). But the JL company do not have any such measures which is one of the most
important basic security flaws that the organisation is facing.
8. Employees can access each other’s account without any objection: this kind of
practice may lead to future internal theft within the business organisation. It is
important to maintain access of particular database information with respect to
particular roles in the organisation.
9. All types of confidential data of the business are transferred via email without
having any cryptographic techniques: Business data are much confidential and the
loss of which may lead to the fall of the entire business organization. Hence it is
important to implement cryptographic security measures in transferring important
credentials related to the business via email (Gupta, Agrawal & Yamaguchi, 2016).
According to report, the company also fails in implementing this security measure
within their business system.
Among all these issues that are prevailing in the business organisation of JL company,
the main five identified issues that needs immediate attention includes:
1. Lack of security software in the laptops used in the company.
2. Non-functioning of windows 2000 server
3. Receiving of spam messages
4. Lack of policies and rules to guide employees
ransomware that was demanded by the hackers. This is a major drawback that the
company is facing recently as the matter of security is still not resolved.
7. There are no policies or rules for employees on using the computer systems
effectively without getting attacked by hackers: It is important for every company
to set up some security policies and rules that needs to be followed by employees
while using the computer systems for business purposes (Safa, Von Solms & Furnell,
2016). But the JL company do not have any such measures which is one of the most
important basic security flaws that the organisation is facing.
8. Employees can access each other’s account without any objection: this kind of
practice may lead to future internal theft within the business organisation. It is
important to maintain access of particular database information with respect to
particular roles in the organisation.
9. All types of confidential data of the business are transferred via email without
having any cryptographic techniques: Business data are much confidential and the
loss of which may lead to the fall of the entire business organization. Hence it is
important to implement cryptographic security measures in transferring important
credentials related to the business via email (Gupta, Agrawal & Yamaguchi, 2016).
According to report, the company also fails in implementing this security measure
within their business system.
Among all these issues that are prevailing in the business organisation of JL company,
the main five identified issues that needs immediate attention includes:
1. Lack of security software in the laptops used in the company.
2. Non-functioning of windows 2000 server
3. Receiving of spam messages
4. Lack of policies and rules to guide employees
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBER SECURITY ISSUES
5. Unauthorized access of confidential data within the organisation.
Need to address the cyber security issues immediately:
As the business organisation of JL company, is planning to move its business towards
online platforms hence it is necessary that it should work on its basic security measures in
order to prevent any type of attacks in their system. The company need to implement cyber
security measures in order to safe guard their information while working on online business
platforms. Among the five main identified risks, it is important the company first try to
implement a basic policy and rule that would help the employees in using their systems
securely. As many of the employees do not have a proper expertise on information
technology hence, they are unaware of the recent cyber threats that are emerging in the
modern business world.
Solutions to address the identified cyber security issues:
All the above-mentioned cyber issues that are related to the company needs to be
solved immediately. As a measure to solve the issues it is recommended that the company of
JL move its online business platform to a cloud-based environment (Chang, Kuo &
Ramachandran, 2016). E-commerce industries are flourishing day by day and it seems that
there is no stopping in its growth. It is obvious that if the JL company moves its business to
online platform, then it will face more expansion with more consumers coming up for
convenience of online services. The company now needs to manage the rise of unexpected
peaks in the traffic, optimizing load speed and content delivery and most importantly
ensuring data security and protecting them from cyber-attacks. As the business organisation
of JL is facing some major issues with respect to cyber security, moving its business platform
to a more secured cloud environment will be the best option to mitigate all the issues that are
being identified and need immediate attention.
5. Unauthorized access of confidential data within the organisation.
Need to address the cyber security issues immediately:
As the business organisation of JL company, is planning to move its business towards
online platforms hence it is necessary that it should work on its basic security measures in
order to prevent any type of attacks in their system. The company need to implement cyber
security measures in order to safe guard their information while working on online business
platforms. Among the five main identified risks, it is important the company first try to
implement a basic policy and rule that would help the employees in using their systems
securely. As many of the employees do not have a proper expertise on information
technology hence, they are unaware of the recent cyber threats that are emerging in the
modern business world.
Solutions to address the identified cyber security issues:
All the above-mentioned cyber issues that are related to the company needs to be
solved immediately. As a measure to solve the issues it is recommended that the company of
JL move its online business platform to a cloud-based environment (Chang, Kuo &
Ramachandran, 2016). E-commerce industries are flourishing day by day and it seems that
there is no stopping in its growth. It is obvious that if the JL company moves its business to
online platform, then it will face more expansion with more consumers coming up for
convenience of online services. The company now needs to manage the rise of unexpected
peaks in the traffic, optimizing load speed and content delivery and most importantly
ensuring data security and protecting them from cyber-attacks. As the business organisation
of JL is facing some major issues with respect to cyber security, moving its business platform
to a more secured cloud environment will be the best option to mitigate all the issues that are
being identified and need immediate attention.
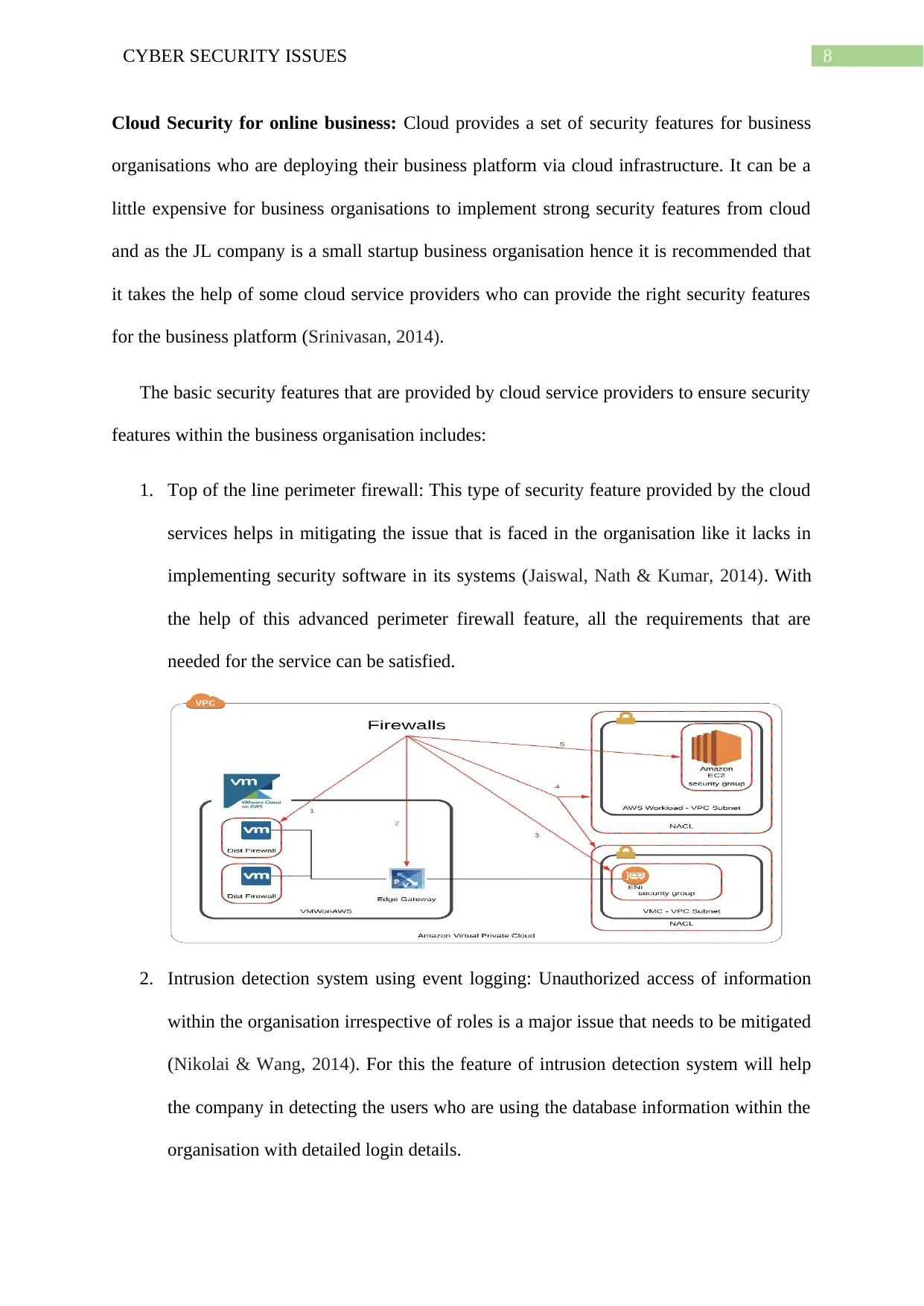
8CYBER SECURITY ISSUES
Cloud Security for online business: Cloud provides a set of security features for business
organisations who are deploying their business platform via cloud infrastructure. It can be a
little expensive for business organisations to implement strong security features from cloud
and as the JL company is a small startup business organisation hence it is recommended that
it takes the help of some cloud service providers who can provide the right security features
for the business platform (Srinivasan, 2014).
The basic security features that are provided by cloud service providers to ensure security
features within the business organisation includes:
1. Top of the line perimeter firewall: This type of security feature provided by the cloud
services helps in mitigating the issue that is faced in the organisation like it lacks in
implementing security software in its systems (Jaiswal, Nath & Kumar, 2014). With
the help of this advanced perimeter firewall feature, all the requirements that are
needed for the service can be satisfied.
2. Intrusion detection system using event logging: Unauthorized access of information
within the organisation irrespective of roles is a major issue that needs to be mitigated
(Nikolai & Wang, 2014). For this the feature of intrusion detection system will help
the company in detecting the users who are using the database information within the
organisation with detailed login details.
Cloud Security for online business: Cloud provides a set of security features for business
organisations who are deploying their business platform via cloud infrastructure. It can be a
little expensive for business organisations to implement strong security features from cloud
and as the JL company is a small startup business organisation hence it is recommended that
it takes the help of some cloud service providers who can provide the right security features
for the business platform (Srinivasan, 2014).
The basic security features that are provided by cloud service providers to ensure security
features within the business organisation includes:
1. Top of the line perimeter firewall: This type of security feature provided by the cloud
services helps in mitigating the issue that is faced in the organisation like it lacks in
implementing security software in its systems (Jaiswal, Nath & Kumar, 2014). With
the help of this advanced perimeter firewall feature, all the requirements that are
needed for the service can be satisfied.
2. Intrusion detection system using event logging: Unauthorized access of information
within the organisation irrespective of roles is a major issue that needs to be mitigated
(Nikolai & Wang, 2014). For this the feature of intrusion detection system will help
the company in detecting the users who are using the database information within the
organisation with detailed login details.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CYBER SECURITY ISSUES
3. Data at rest encryption: All the data that are transferred within the systems of the
company lacks encryption feature. This security feature of cloud will help the
organisation in transferring messages with encryption feature (Ramachandran &
Chang, 2016). Also as the company employees receives about 40 spam messages in
their systems per day, this advanced encryption method will also help them in
mitigating the issue to some extent.
4. Implementing cloud directory service: Another important thing that the company
needs to solve is with the issue of using windows 2000 server (Liao et al., 2016). As it
is planning to move its business to online platform, it is very important to use the
windows 2000 server again in their system but it will cost the company a huge
expenditure hence moving towards a cloud directory service will help the company in
mitigating this issue.
Comparison between the different alternative approaches in order to address the
security issues:
There can be two main approaches in order to mitigate the cyber security issues that
are faced in the JL company. On e is the traditional IT approach and the other is the Cloud
security approach.
3. Data at rest encryption: All the data that are transferred within the systems of the
company lacks encryption feature. This security feature of cloud will help the
organisation in transferring messages with encryption feature (Ramachandran &
Chang, 2016). Also as the company employees receives about 40 spam messages in
their systems per day, this advanced encryption method will also help them in
mitigating the issue to some extent.
4. Implementing cloud directory service: Another important thing that the company
needs to solve is with the issue of using windows 2000 server (Liao et al., 2016). As it
is planning to move its business to online platform, it is very important to use the
windows 2000 server again in their system but it will cost the company a huge
expenditure hence moving towards a cloud directory service will help the company in
mitigating this issue.
Comparison between the different alternative approaches in order to address the
security issues:
There can be two main approaches in order to mitigate the cyber security issues that
are faced in the JL company. On e is the traditional IT approach and the other is the Cloud
security approach.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CYBER SECURITY ISSUES
Traditional IT security approach: In order to create a typical IT infrastructure in a
company, it needs to connect to hardware devices to on-premise servers in order to store their
important information securely. In traditional approach of IT security, the company will need
to incorporate a greater number of physical hardware on-site and this will lead to high
expenditure. As the company is a small startup company, it cannot bear the huge amount of
expenditure in order to provide security facility for its prevailing issues (Sandberg, Amin &
Johansson, 2015).
Cloud security approach: On the other hand, while taking the help of cloud service
providers in deploying their online business platform in the cloud environment, they can help
the company in incorporating the internet for a storage place which will reduce the cost of
buying specific hardware or software requirement for the company (Kalaiprasath, Elankavi &
Udayakumar, 2017).
Traditional way of approach to cyber security does not always provide security measures
ensuring that the data are protected. But the security features in cloud environment meet the
hackers at their level(Ibrahim, Hamlyn-Harris & Grundy, 2016). Cloud security provides the
following benefits in mitigating the issues that are identified within the company of JL-
1. It controls and ensures the security measures like firewall implementation, password
protocols and updating security patches.
2. It helps the staffs in informing about the latest security threats and policies that the
hackers are using.
3. It enables the layered authorization in order to access networks by customers,
employees and mostly by the managers in the company.
Traditional IT security approach: In order to create a typical IT infrastructure in a
company, it needs to connect to hardware devices to on-premise servers in order to store their
important information securely. In traditional approach of IT security, the company will need
to incorporate a greater number of physical hardware on-site and this will lead to high
expenditure. As the company is a small startup company, it cannot bear the huge amount of
expenditure in order to provide security facility for its prevailing issues (Sandberg, Amin &
Johansson, 2015).
Cloud security approach: On the other hand, while taking the help of cloud service
providers in deploying their online business platform in the cloud environment, they can help
the company in incorporating the internet for a storage place which will reduce the cost of
buying specific hardware or software requirement for the company (Kalaiprasath, Elankavi &
Udayakumar, 2017).
Traditional way of approach to cyber security does not always provide security measures
ensuring that the data are protected. But the security features in cloud environment meet the
hackers at their level(Ibrahim, Hamlyn-Harris & Grundy, 2016). Cloud security provides the
following benefits in mitigating the issues that are identified within the company of JL-
1. It controls and ensures the security measures like firewall implementation, password
protocols and updating security patches.
2. It helps the staffs in informing about the latest security threats and policies that the
hackers are using.
3. It enables the layered authorization in order to access networks by customers,
employees and mostly by the managers in the company.

11CYBER SECURITY ISSUES
4. It helps in routing all requests in the network such as the messages and emails
received through a centralized and protected latest security updates of the protocols
and hence helps in blocking threats before entering into the network.
Cost breakdown to implement the solution for the identified issues:
There ae various cloud service providers who provide cloud security services at a very
cheap cost ranging to about $2.50/ month to $10/ month (Mtebe, & Raisamo, 2014). As the
business of JL is a small startup company, it can take the help of service providers such as
Vultr, A2 Hosting, Digital ocean and many more who are known for providing cloud security
services at a lowest cost. The cost for implementing a firewall in cloud environment will be
around $100 and the cost to implement IAM service in cloud is $5000.
Conclusion:
Thus, from the report it can be concluded that using a cloud-based security will
benefit the JL company in mitigating the major security risks that are prevailing in the
company’s scenario. Cloud data security is a shared responsibility between the cloud
providers and the customers. In this case it is the utmost responsibility of the JL company to
secure its data in the cloud environment. Cloud data security adds additional data security to
its users by helping in backing up of files in the off-site, decreasing the potential of the
hackers and mitigating other cyber security issues. Besides using the cloud security services,
it is also necessary that the employees of the organisation should be trained with basic
awareness against using computer systems safely without clicking on an any unwanted links
or any other unauthorized accesses. It is the due responsibility of the company as well to
implement security features within the organisation and make use of standard policies and
rules that the employees are bound to follow.
4. It helps in routing all requests in the network such as the messages and emails
received through a centralized and protected latest security updates of the protocols
and hence helps in blocking threats before entering into the network.
Cost breakdown to implement the solution for the identified issues:
There ae various cloud service providers who provide cloud security services at a very
cheap cost ranging to about $2.50/ month to $10/ month (Mtebe, & Raisamo, 2014). As the
business of JL is a small startup company, it can take the help of service providers such as
Vultr, A2 Hosting, Digital ocean and many more who are known for providing cloud security
services at a lowest cost. The cost for implementing a firewall in cloud environment will be
around $100 and the cost to implement IAM service in cloud is $5000.
Conclusion:
Thus, from the report it can be concluded that using a cloud-based security will
benefit the JL company in mitigating the major security risks that are prevailing in the
company’s scenario. Cloud data security is a shared responsibility between the cloud
providers and the customers. In this case it is the utmost responsibility of the JL company to
secure its data in the cloud environment. Cloud data security adds additional data security to
its users by helping in backing up of files in the off-site, decreasing the potential of the
hackers and mitigating other cyber security issues. Besides using the cloud security services,
it is also necessary that the employees of the organisation should be trained with basic
awareness against using computer systems safely without clicking on an any unwanted links
or any other unauthorized accesses. It is the due responsibility of the company as well to
implement security features within the organisation and make use of standard policies and
rules that the employees are bound to follow.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




