Cyber Security Report: SMS Security, University A, NSW, Australia
VerifiedAdded on 2022/10/18
|13
|410
|13
Report
AI Summary
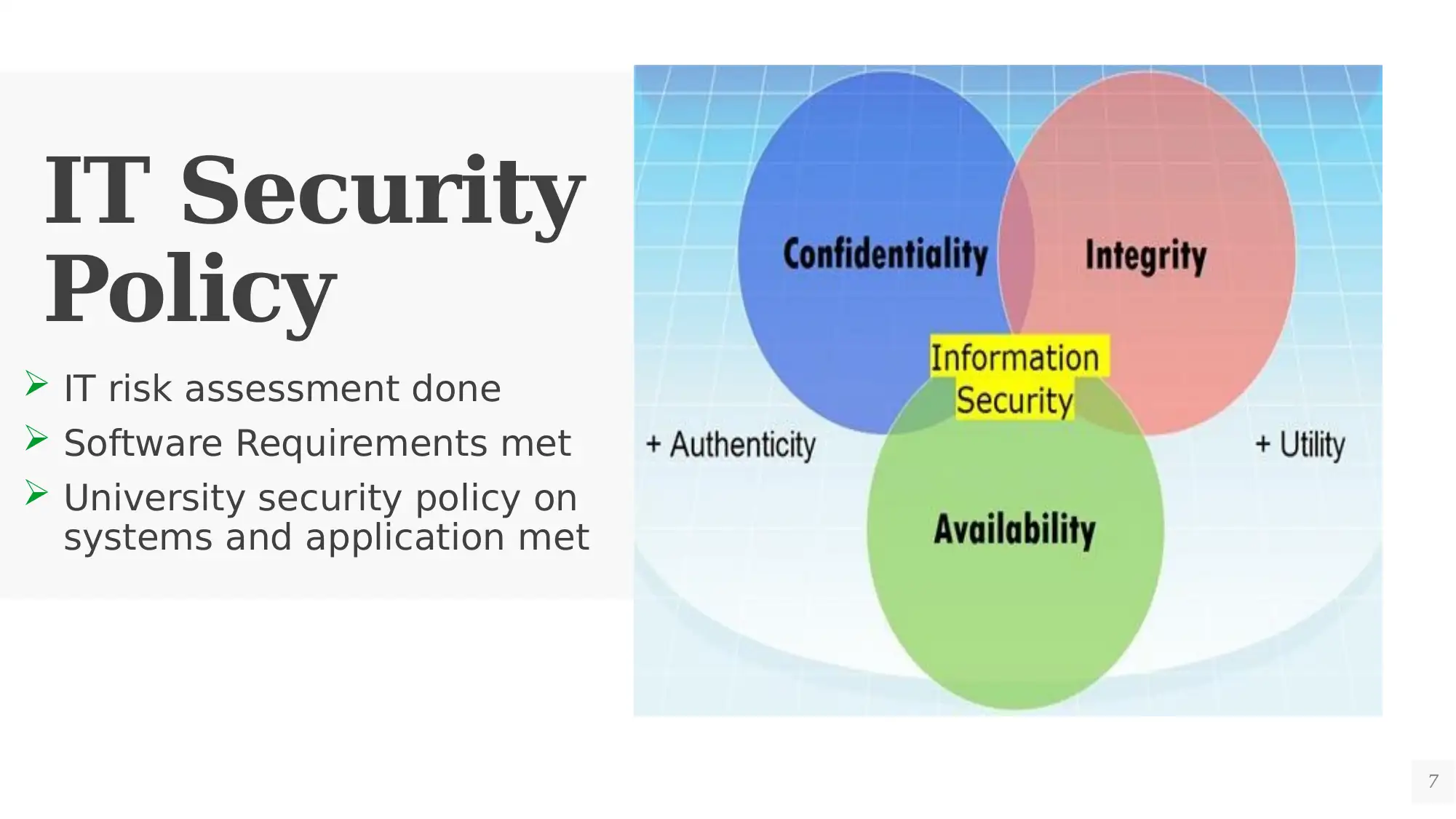
This report analyzes the cyber security considerations for University A's new Student Management System (SMS), focusing on legal and regulatory compliance. It addresses the Privacy Act of 1988 and the Privacy and Data Protection Act of 2014, outlining the requirements for data privacy, confidentiality, and secure storage of student information. The report also covers IT hardware and software acquisition policies, emphasizing the need for adherence to minimum standards and pre-qualification of vendors. Furthermore, it highlights the importance of IT security policies, risk assessments, and the implementation of a robust IT service management framework. The document emphasizes the importance of compliance to mitigate legal and financial risks, improve student experience, and protect the university's reputation. The report provides a detailed overview of the key components of a secure SMS, including data integrity, confidentiality, and the continuous monitoring of IT security.
1 out of 13











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)