Project: Impact of Cyber Spam & Phishing on Facebook's Cybersecurity
VerifiedAdded on 2022/12/06
|22
|7059
|353
Project
AI Summary
This project is a comprehensive analysis of the impact of cyber spam and phishing on Facebook's cybersecurity. The project is divided into three parts: a reflective CPD (Continuing Professional Development) plan, a research log, and a project proposal. The CPD plan outlines personal development goals and strategies to improve skills such as communication, research, decision-making, and analytical abilities. The research log documents the research process and insights gained. The project proposal introduces the research topic, which focuses on the increasing cyber spam and phishing activities targeting Facebook users. It includes an introduction, literature review, research methodology, and conclusion. The proposal aims to analyze the impact of these threats and propose solutions to enhance Facebook's cybersecurity measures, incorporating a case study approach. The research methodology includes both primary and secondary research to gather relevant data and information. The project emphasizes the importance of cybersecurity for social media platforms and the need for advanced practices to mitigate cyber threats, with a focus on Facebook's vulnerabilities and the impact on its users and business operations.

Research Methods for Professional
Practice
Practice
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
PART A: Reflective CPD..........................................................................................................3
PART B: Research Log..............................................................................................................5
PART C: Project Proposal.........................................................................................................6
Introduction............................................................................................................................6
Literature review....................................................................................................................8
Research Methodology and Planning...................................................................................11
Conclusion............................................................................................................................14
References................................................................................................................................16
Appendix..................................................................................................................................18
Project title: “To analysis the impact of increasing cyber spam and phishing on cyber security
technology with the use of advance practices. A case study on Facebook”............................18
PART A: Reflective CPD..........................................................................................................3
PART B: Research Log..............................................................................................................5
PART C: Project Proposal.........................................................................................................6
Introduction............................................................................................................................6
Literature review....................................................................................................................8
Research Methodology and Planning...................................................................................11
Conclusion............................................................................................................................14
References................................................................................................................................16
Appendix..................................................................................................................................18
Project title: “To analysis the impact of increasing cyber spam and phishing on cyber security
technology with the use of advance practices. A case study on Facebook”............................18
PART A: Reflective CPD
Personal Development plan
Personal development plan is basically a process which helps the individual to achieve its
personal objectives effectively by enhancing their skills. Developing the skills of the helps in
the overall development of the individual in the market with the help of personal
development plan individual can easily develop their skills and achieve their goals in the
short period of time if the individual wants to achieve success the they have to develop their
skills and knowledge as per the requirement of the economy so that growth chances of the
individual can be developed. It helps in maintaining a healthy relationships with the collegues
so that confidence of the individual can be developed. Personal development plan helps in
enhancing the knowledge of the individual which will further helps in motivating the
individual. In the below personal development plan there are various skills which i need to
improve as per the requirement there are various areas in which development is required so
that my growth opportunities can developed (WANG, 2017).
PERSONAL DEVELOPEMT PLAN
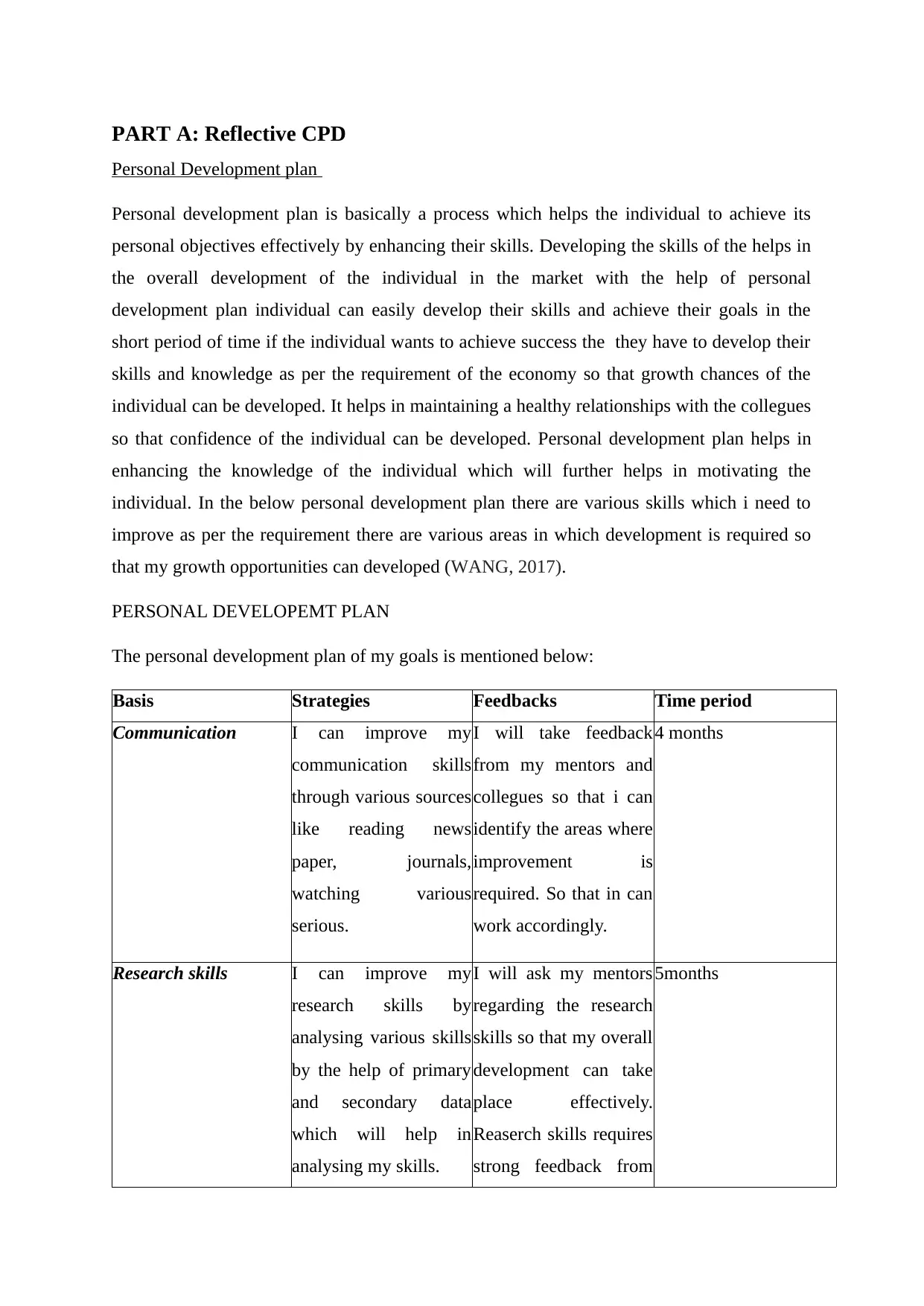
The personal development plan of my goals is mentioned below:
Basis Strategies Feedbacks Time period
Communication I can improve my
communication skills
through various sources
like reading news
paper, journals,
watching various
serious.
I will take feedback
from my mentors and
collegues so that i can
identify the areas where
improvement is
required. So that in can
work accordingly.
4 months
Research skills I can improve my
research skills by
analysing various skills
by the help of primary
and secondary data
which will help in
analysing my skills.
I will ask my mentors
regarding the research
skills so that my overall
development can take
place effectively.
Reaserch skills requires
strong feedback from
5months
Personal Development plan
Personal development plan is basically a process which helps the individual to achieve its
personal objectives effectively by enhancing their skills. Developing the skills of the helps in
the overall development of the individual in the market with the help of personal
development plan individual can easily develop their skills and achieve their goals in the
short period of time if the individual wants to achieve success the they have to develop their
skills and knowledge as per the requirement of the economy so that growth chances of the
individual can be developed. It helps in maintaining a healthy relationships with the collegues
so that confidence of the individual can be developed. Personal development plan helps in
enhancing the knowledge of the individual which will further helps in motivating the
individual. In the below personal development plan there are various skills which i need to
improve as per the requirement there are various areas in which development is required so
that my growth opportunities can developed (WANG, 2017).
PERSONAL DEVELOPEMT PLAN
The personal development plan of my goals is mentioned below:
Basis Strategies Feedbacks Time period
Communication I can improve my
communication skills
through various sources
like reading news
paper, journals,
watching various
serious.
I will take feedback
from my mentors and
collegues so that i can
identify the areas where
improvement is
required. So that in can
work accordingly.
4 months
Research skills I can improve my
research skills by
analysing various skills
by the help of primary
and secondary data
which will help in
analysing my skills.
I will ask my mentors
regarding the research
skills so that my overall
development can take
place effectively.
Reaserch skills requires
strong feedback from
5months
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
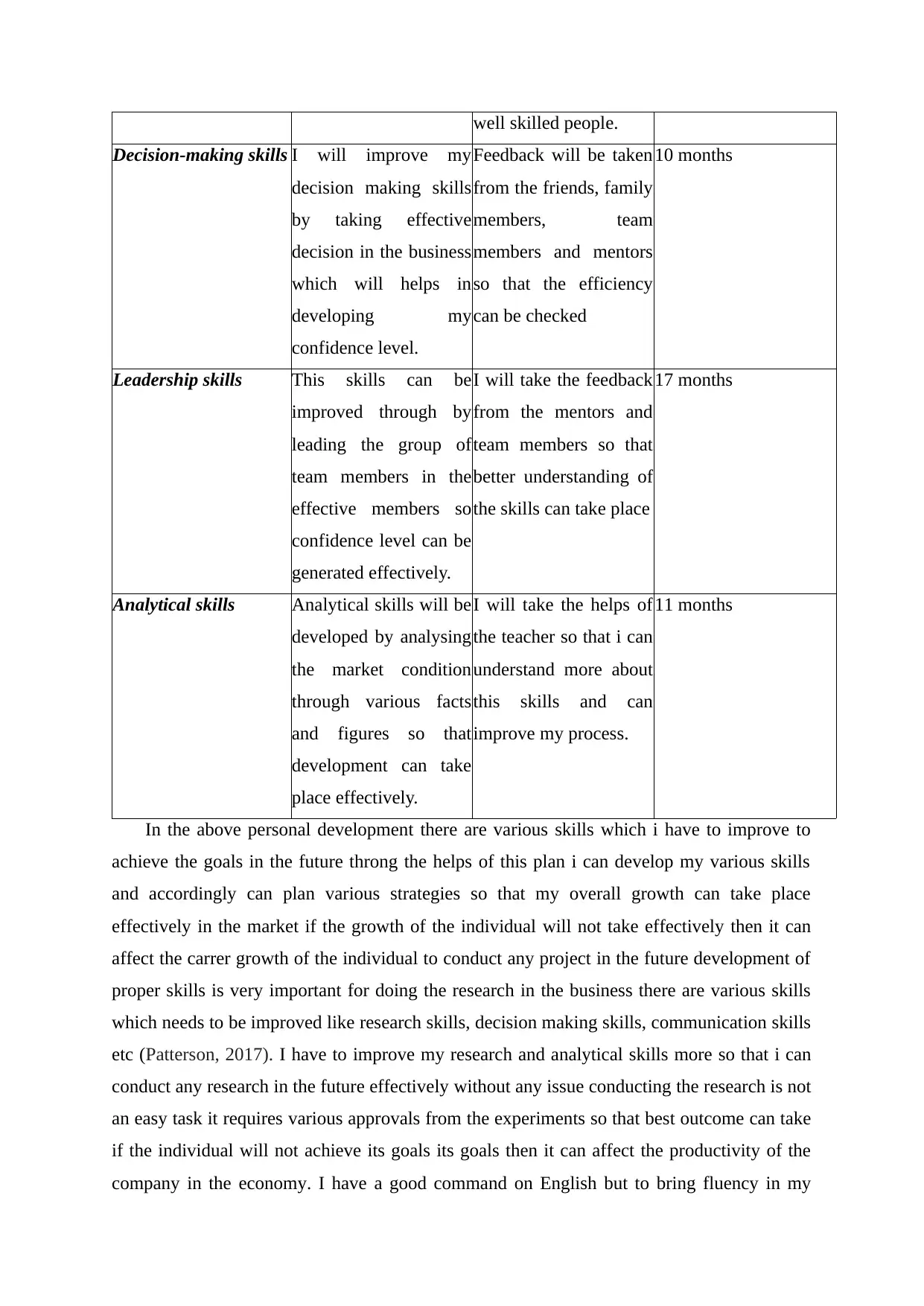
well skilled people.
Decision-making skills I will improve my
decision making skills
by taking effective
decision in the business
which will helps in
developing my
confidence level.
Feedback will be taken
from the friends, family
members, team
members and mentors
so that the efficiency
can be checked
10 months
Leadership skills This skills can be
improved through by
leading the group of
team members in the
effective members so
confidence level can be
generated effectively.
I will take the feedback
from the mentors and
team members so that
better understanding of
the skills can take place
17 months
Analytical skills Analytical skills will be
developed by analysing
the market condition
through various facts
and figures so that
development can take
place effectively.
I will take the helps of
the teacher so that i can
understand more about
this skills and can
improve my process.
11 months
In the above personal development there are various skills which i have to improve to
achieve the goals in the future throng the helps of this plan i can develop my various skills
and accordingly can plan various strategies so that my overall growth can take place
effectively in the market if the growth of the individual will not take effectively then it can
affect the carrer growth of the individual to conduct any project in the future development of
proper skills is very important for doing the research in the business there are various skills
which needs to be improved like research skills, decision making skills, communication skills
etc (Patterson, 2017). I have to improve my research and analytical skills more so that i can
conduct any research in the future effectively without any issue conducting the research is not
an easy task it requires various approvals from the experiments so that best outcome can take
if the individual will not achieve its goals its goals then it can affect the productivity of the
company in the economy. I have a good command on English but to bring fluency in my
Decision-making skills I will improve my
decision making skills
by taking effective
decision in the business
which will helps in
developing my
confidence level.
Feedback will be taken
from the friends, family
members, team
members and mentors
so that the efficiency
can be checked
10 months
Leadership skills This skills can be
improved through by
leading the group of
team members in the
effective members so
confidence level can be
generated effectively.
I will take the feedback
from the mentors and
team members so that
better understanding of
the skills can take place
17 months
Analytical skills Analytical skills will be
developed by analysing
the market condition
through various facts
and figures so that
development can take
place effectively.
I will take the helps of
the teacher so that i can
understand more about
this skills and can
improve my process.
11 months
In the above personal development there are various skills which i have to improve to
achieve the goals in the future throng the helps of this plan i can develop my various skills
and accordingly can plan various strategies so that my overall growth can take place
effectively in the market if the growth of the individual will not take effectively then it can
affect the carrer growth of the individual to conduct any project in the future development of
proper skills is very important for doing the research in the business there are various skills
which needs to be improved like research skills, decision making skills, communication skills
etc (Patterson, 2017). I have to improve my research and analytical skills more so that i can
conduct any research in the future effectively without any issue conducting the research is not
an easy task it requires various approvals from the experiments so that best outcome can take
if the individual will not achieve its goals its goals then it can affect the productivity of the
company in the economy. I have a good command on English but to bring fluency in my
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

skills I have to work as per the product development plan so that overall growth can take
place. Improving the skills will create the positive image of the individual infront of other due
to which growth chances of the employees will get developed in the market. in the personal
development plan there is the time duration which is given for the on the basis of which skill
which be developed if the business will not achieve its goals effectively then it can affect the
productivity of individual. I will take helps of my mentors and teachers to enhance my skills
so that growth chances can be increased. Having good communication skills will helps in
boosting my confidence level if my communication skills will not be good then it will affect
my confidence level due to which i will not be able to communicate effectively with the other
person. In future if i want to achieve success then i have to develop my skills which are
mentioned in the personal development plan so that my career path can be achieved
successfully (Hoang, 2018). If the individual wants to a achieve great height then they have
to analyse their strength and weakness so that goals can be achieved properly. In the future if
I will work in the organisation then i have to work with them as per the skills and knowledge
if my skills and knowledge will be as per the their expectations then it will helps in my carer
growth in the business. I strength is that i can provides various innovative ideas to the
business which will helps in the effective decision making in the business so that and will
also helps in achieving my goals effectively in the business if the goals of the business will
not be achieved successful then it can be a risk factor for the business in the market due to
which achieving the goals of the business is very important so that business can achieve
success. Developing the team management skills will helps in providing effective decision in
the business teams members helps in developing the services they help in providing
innovation in the company. Personal development plan helps in identifying the areas where
improvement is needed so that individual can develop its areas accordingly in the business
and can enhance the productivity of the company in the marketplace. Individual can take
support of their mentors to take the feedback so that growth of the company can be increased
and more profit can be earned. Skills helps the people developing their image in the economy
well skilled employees is more in demand in the society.
PART B: Research Log
Research blog is the platform through which various writers share their view and information
on the topic so that people can get aware about it easily it is the best online platform which
helps the researcher to gain meaningful information so that they can achieve their targets
properly. Researcher can take various information related to the project so that targets of the
place. Improving the skills will create the positive image of the individual infront of other due
to which growth chances of the employees will get developed in the market. in the personal
development plan there is the time duration which is given for the on the basis of which skill
which be developed if the business will not achieve its goals effectively then it can affect the
productivity of individual. I will take helps of my mentors and teachers to enhance my skills
so that growth chances can be increased. Having good communication skills will helps in
boosting my confidence level if my communication skills will not be good then it will affect
my confidence level due to which i will not be able to communicate effectively with the other
person. In future if i want to achieve success then i have to develop my skills which are
mentioned in the personal development plan so that my career path can be achieved
successfully (Hoang, 2018). If the individual wants to a achieve great height then they have
to analyse their strength and weakness so that goals can be achieved properly. In the future if
I will work in the organisation then i have to work with them as per the skills and knowledge
if my skills and knowledge will be as per the their expectations then it will helps in my carer
growth in the business. I strength is that i can provides various innovative ideas to the
business which will helps in the effective decision making in the business so that and will
also helps in achieving my goals effectively in the business if the goals of the business will
not be achieved successful then it can be a risk factor for the business in the market due to
which achieving the goals of the business is very important so that business can achieve
success. Developing the team management skills will helps in providing effective decision in
the business teams members helps in developing the services they help in providing
innovation in the company. Personal development plan helps in identifying the areas where
improvement is needed so that individual can develop its areas accordingly in the business
and can enhance the productivity of the company in the marketplace. Individual can take
support of their mentors to take the feedback so that growth of the company can be increased
and more profit can be earned. Skills helps the people developing their image in the economy
well skilled employees is more in demand in the society.
PART B: Research Log
Research blog is the platform through which various writers share their view and information
on the topic so that people can get aware about it easily it is the best online platform which
helps the researcher to gain meaningful information so that they can achieve their targets
properly. Researcher can take various information related to the project so that targets of the

project can be achieved effectively through research blog user can communicate to the
audience easily which will help in growth of the economy through the helps of online media
researcher can easily share their information and views. Research blogs helps in maintaining
healthy relationship with the employees so that goals of the business can achieved effectively
in the market if the individual want to achieve success then it is important to have good
relation with the members so that goal can be achieved properly. It can helps in improving
the writing skills and demand of the individual in the market if the content of the individual
will attract the attention of the people then it can helps in the success of the individual.
E portfolio
To conduct this research there are various skills which i need to improve like research
skills, analytical skills, communication skills on the basis of which i have created a personal
development plan so that my various skills can be developed effectively in this research i will
learn various cyber spams which are taking place in the economy and how we can overcome
from these scam to live a healthy lifestyle various research will be conducted so that proper
outcome can take place. I have to do various primary and secondary research to complete this
project so that best outcome can be provided to the society if the society will not be aware
about this concept then it can affect the development of the society in the market. companys
like facebook are going through this spam due to which information of user can be corrupted
easily which can affect the image of the brand. I will use my skills and knowledge to conduct
a research so that best result can take place i have also take help of my mentor and team
members so that i can achieve my goals effectively. Research requires advance skills so that
various issues can be identified properly with the helps of personal development i can
enhance my knowledge and skills in the given time period so that goals can be achieved
properly. if my research skills will be developed then it will helps in accomplishing my goals
properly which will further helps in my career development because skills helps in
development of the individual completely.
PART C: Project Proposal
Introduction
In the time of increasing use of social media website it is evaluated that there lots of
criminal who are awaited for making spam and phishing or any unethical activity which are
affect the company reputation in any terms. Within the today’s organisation this has been
very important to understand and analysis the impact of the growth and activities to make a
audience easily which will help in growth of the economy through the helps of online media
researcher can easily share their information and views. Research blogs helps in maintaining
healthy relationship with the employees so that goals of the business can achieved effectively
in the market if the individual want to achieve success then it is important to have good
relation with the members so that goal can be achieved properly. It can helps in improving
the writing skills and demand of the individual in the market if the content of the individual
will attract the attention of the people then it can helps in the success of the individual.
E portfolio
To conduct this research there are various skills which i need to improve like research
skills, analytical skills, communication skills on the basis of which i have created a personal
development plan so that my various skills can be developed effectively in this research i will
learn various cyber spams which are taking place in the economy and how we can overcome
from these scam to live a healthy lifestyle various research will be conducted so that proper
outcome can take place. I have to do various primary and secondary research to complete this
project so that best outcome can be provided to the society if the society will not be aware
about this concept then it can affect the development of the society in the market. companys
like facebook are going through this spam due to which information of user can be corrupted
easily which can affect the image of the brand. I will use my skills and knowledge to conduct
a research so that best result can take place i have also take help of my mentor and team
members so that i can achieve my goals effectively. Research requires advance skills so that
various issues can be identified properly with the helps of personal development i can
enhance my knowledge and skills in the given time period so that goals can be achieved
properly. if my research skills will be developed then it will helps in accomplishing my goals
properly which will further helps in my career development because skills helps in
development of the individual completely.
PART C: Project Proposal
Introduction
In the time of increasing use of social media website it is evaluated that there lots of
criminal who are awaited for making spam and phishing or any unethical activity which are
affect the company reputation in any terms. Within the today’s organisation this has been
very important to understand and analysis the impact of the growth and activities to make a
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

career path for making strategic development. This is very important to study, of cyber
security for the employees for across the country (Alali and et.al.,2018). This is an important
source to make and increase the knowledge to expertise the growing cyber security issue and
demonstrate the security capabilities of cyber spam and phishing through cloud and big data
saver. Further this proposal include the background, aims, objective, research methodology
and Literature review for conducting an effective research. Further all is related to achieve
desired objective and make sure to work on the chosen company. All of the information are
helpful for collecting data and make them effective changes within society to make suitable
changes that could be related to the growth of the company while working through different
cyber-crime and their implication on the society.
Background of the company:
Facebook is the American company which was founded in 2004, and it’s
headquartered in California, United State. Their main function is to iterating the solving
problem, work together and try to connect the people all over the world. The company is
raising by the ideas of mark Zuckerberg and popularly known in a social media services. It is
working and establishing all other application like Watsapp, Instagram and many more. This
is all are helpful in effective and understanding the knowledge which are related to cyber
security and make spam issues which they are facing through across the world. Further
Facebook is helpful for many other small business near about 200 plus million business
strategies are connected through the use of Facebook while connecting more and more
customer (Edgar and Manz, 2017). They are connected all over the world through sharing
their need to across the world in social media. But this is very important for the company to
be secure and use effective security measure action to remove the major challenges and
company’s data with cyber spam and phishing data.
Research Rational:
The main reason to choose this concept is for exploring and detecting the use of cyber
security issues and make advance use of cyber securities technologies within the companies
to minimise the unethical issues and phishing activities. The increasing crime in cyber
security is the biggest problem for the companies to manage and collect the data through
different sources and make them threat free in their computers (Furhtand VillanustreGupta,
2018). This case study is on Facebook as they are facing many unethical cyber related issues
in their company which are directly or indirectly affect the source of data through major
security for the employees for across the country (Alali and et.al.,2018). This is an important
source to make and increase the knowledge to expertise the growing cyber security issue and
demonstrate the security capabilities of cyber spam and phishing through cloud and big data
saver. Further this proposal include the background, aims, objective, research methodology
and Literature review for conducting an effective research. Further all is related to achieve
desired objective and make sure to work on the chosen company. All of the information are
helpful for collecting data and make them effective changes within society to make suitable
changes that could be related to the growth of the company while working through different
cyber-crime and their implication on the society.
Background of the company:
Facebook is the American company which was founded in 2004, and it’s
headquartered in California, United State. Their main function is to iterating the solving
problem, work together and try to connect the people all over the world. The company is
raising by the ideas of mark Zuckerberg and popularly known in a social media services. It is
working and establishing all other application like Watsapp, Instagram and many more. This
is all are helpful in effective and understanding the knowledge which are related to cyber
security and make spam issues which they are facing through across the world. Further
Facebook is helpful for many other small business near about 200 plus million business
strategies are connected through the use of Facebook while connecting more and more
customer (Edgar and Manz, 2017). They are connected all over the world through sharing
their need to across the world in social media. But this is very important for the company to
be secure and use effective security measure action to remove the major challenges and
company’s data with cyber spam and phishing data.
Research Rational:
The main reason to choose this concept is for exploring and detecting the use of cyber
security issues and make advance use of cyber securities technologies within the companies
to minimise the unethical issues and phishing activities. The increasing crime in cyber
security is the biggest problem for the companies to manage and collect the data through
different sources and make them threat free in their computers (Furhtand VillanustreGupta,
2018). This case study is on Facebook as they are facing many unethical cyber related issues
in their company which are directly or indirectly affect the source of data through major
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

changes and strategies in the company. To analysis its impact on the cyber security
technologies are the best advance practices in today’s world in one of the major challenging
nature in companies.
Aim: “To analysis the impact of increasing cyber spam and phishingon cyber security
technology with the use of advance practices. A case study on Facebook. ”
Objectives:
To understand the concept of cyber spam and phishing in social media websites.
To evaluate the major challenges which are face by Facebook due to increasing
impact of cyber spam and phishing.
To determine the various factor which may affect the cyber security technology in the
chosen company.
Questions:
Explain the meaning of cyber threat and phishing in social media?
What are the major challenges face by Facebook due to increasing impact of cyber
threat and phishing?
Which are the main factors that affect the cyber security technology in Facebook?
Literature review
Literature review is one of the basic and essential step to determine the concept and
collection of the secondary data sources. It has been considered that major changes and
sources are used for the growth of the resources and make sure to work and manage the
activities through different sources and make and adaptive style to work and manage forceful
activities in the research.
To understand the concept of cyber spam and phishing in social media websites
As per the view point of Fruhlinger, (2021), Phishing and cyber spam is the method
which has been used to make and gathered different informative information for using
deceptive e-mails, websites and many more attacks. It is one of the known cyber-attack which
are mainly used and disguised the information and work as a weapon. It has been using form
the long time by the hacker and make effective source to manage different attachment and
make something which are related to different sector and declining rate of the company.
Phishing and cyber spam is one of the major consequences to work and manage attach in
technologies are the best advance practices in today’s world in one of the major challenging
nature in companies.
Aim: “To analysis the impact of increasing cyber spam and phishingon cyber security
technology with the use of advance practices. A case study on Facebook. ”
Objectives:
To understand the concept of cyber spam and phishing in social media websites.
To evaluate the major challenges which are face by Facebook due to increasing
impact of cyber spam and phishing.
To determine the various factor which may affect the cyber security technology in the
chosen company.
Questions:
Explain the meaning of cyber threat and phishing in social media?
What are the major challenges face by Facebook due to increasing impact of cyber
threat and phishing?
Which are the main factors that affect the cyber security technology in Facebook?
Literature review
Literature review is one of the basic and essential step to determine the concept and
collection of the secondary data sources. It has been considered that major changes and
sources are used for the growth of the resources and make sure to work and manage the
activities through different sources and make and adaptive style to work and manage forceful
activities in the research.
To understand the concept of cyber spam and phishing in social media websites
As per the view point of Fruhlinger, (2021), Phishing and cyber spam is the method
which has been used to make and gathered different informative information for using
deceptive e-mails, websites and many more attacks. It is one of the known cyber-attack which
are mainly used and disguised the information and work as a weapon. It has been using form
the long time by the hacker and make effective source to manage different attachment and
make something which are related to different sector and declining rate of the company.
Phishing and cyber spam is one of the major consequences to work and manage attach in

history to make change in the activities (What is phishing? How this cyber-attack works and
how to prevent it, 2021). All if basically related to number of different photos, celebrities and
make suggestion for the company to work and manage impact on the growth of the company.
In the time of social media, there are different sources and website which are facing the issue
of cyber spam activities and phishing activities within social media application.
The use of the social media is basically related to ubiquitous and make air we breathe,
Facebook, Twitter and many multitude are the other parts which are usually to keep and
motivated for the growth of the company. Many of the business are useful and effective for
the growth and attract the client information for making successful activities in the business
operations. With the help of natural and body languages are basically related to social media
platform and make cast to phishing the net on the social media platform. Facebook has many
symptoms which are make an impact on the society and make sure to work and assign the
task to work (Hall, 2016). This is the activities which are basically helpful for the company
and make sure to measure and get the success in the company to arise different sources to
assign the task and make phishing protection employability to work and assign the task to
manage activities. All is basically related to the diverse network and make sustainable
activities in the company.
To evaluate the major challenges which are face by Facebook due to increasing impact of
Cyber Spam and phishing
As per the view point of Lin, (2021); Cyber security are make safety and make security
in the major platform of the company. This has been working with the crime and some kind
of computer which are basically related to shape of varieties in order to make different sector
this could be related to major challenges and issues that can be related to increasing impact of
cyber security, spam and phishing changes. Some of the major challenges are basically
related to decline growth and profit of the company:
Cost of the firm: Facebook have been working and measuring different sources
which are highly related to make growth of the company and make sure to adopt the
high cost of the firm (Jain and Boaddh, 2016). Most of the company like Facebook
are working on the high activities which are related to different activities and increase
the cost of the firm while working on cyber security issues.
Scare ware: This is the technique which are used by many of the fraud companies to
pop-up the detected in a virus and make problem on your computers. This is the
how to prevent it, 2021). All if basically related to number of different photos, celebrities and
make suggestion for the company to work and manage impact on the growth of the company.
In the time of social media, there are different sources and website which are facing the issue
of cyber spam activities and phishing activities within social media application.
The use of the social media is basically related to ubiquitous and make air we breathe,
Facebook, Twitter and many multitude are the other parts which are usually to keep and
motivated for the growth of the company. Many of the business are useful and effective for
the growth and attract the client information for making successful activities in the business
operations. With the help of natural and body languages are basically related to social media
platform and make cast to phishing the net on the social media platform. Facebook has many
symptoms which are make an impact on the society and make sure to work and assign the
task to work (Hall, 2016). This is the activities which are basically helpful for the company
and make sure to measure and get the success in the company to arise different sources to
assign the task and make phishing protection employability to work and assign the task to
manage activities. All is basically related to the diverse network and make sustainable
activities in the company.
To evaluate the major challenges which are face by Facebook due to increasing impact of
Cyber Spam and phishing
As per the view point of Lin, (2021); Cyber security are make safety and make security
in the major platform of the company. This has been working with the crime and some kind
of computer which are basically related to shape of varieties in order to make different sector
this could be related to major challenges and issues that can be related to increasing impact of
cyber security, spam and phishing changes. Some of the major challenges are basically
related to decline growth and profit of the company:
Cost of the firm: Facebook have been working and measuring different sources
which are highly related to make growth of the company and make sure to adopt the
high cost of the firm (Jain and Boaddh, 2016). Most of the company like Facebook
are working on the high activities which are related to different activities and increase
the cost of the firm while working on cyber security issues.
Scare ware: This is the technique which are used by many of the fraud companies to
pop-up the detected in a virus and make problem on your computers. This is the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

technique which are face by the Facebook management team while working on the
deciding and make sure to running internet security programme and work for the
growth of company in cyber challenges.
Decline trust: Further one of the biggest challenge in the society is that they are
working and measuring success within society and make sure to manage declining
trust and make scam activities larger in the company. As it will related to make
effective security tip and make strategic changes through different sources and
related to low level of trust in between the employees.
Loss of data: This is basically related to different source and management of
different activities of data relation. Loss of data is basically related to different sector
and make different activities within growth of the company. Facebook is related to
having most of the data of their employees and customer (Jin and et.al., 2016). Which
has been working in loss of data to analysis and make sure to manage different
sources for the growth to the company.
There are different measure activities and challenges which are needed to be measure and
work as per the society culture and arises in the market demand (Cyber security: What Every
CEO and CFO Should Know, 2021). Company has to adopt effective way and challenges to
promote effective sources and capabilities to promote and make effective challenges need in
the company.
To determine the various factor which may affect the cyber security technology in the chosen
company
According to the view point of Leclair, (2021);cyvber security is too often and measure for
the success of the companies. But at the same time there are different factor and growth are
have been considered to make effective factor and make a review on the company’s factor
which are directly affected through the cyber security issue and its technology in Facebook.
Theft of IP: In this high profile competitive world, it is considered that there are
many theft who are able to work and manage different sources and capabilities to
assign the task and increase efficiency for their attack. This has been used and
manage to make effective ecosystem and able to manage their cybercriminal to make
different sources.
Security of third Party vendor:If the third party get hacked and make company to
losing business data and make sure to work and compromising employee information.
deciding and make sure to running internet security programme and work for the
growth of company in cyber challenges.
Decline trust: Further one of the biggest challenge in the society is that they are
working and measuring success within society and make sure to manage declining
trust and make scam activities larger in the company. As it will related to make
effective security tip and make strategic changes through different sources and
related to low level of trust in between the employees.
Loss of data: This is basically related to different source and management of
different activities of data relation. Loss of data is basically related to different sector
and make different activities within growth of the company. Facebook is related to
having most of the data of their employees and customer (Jin and et.al., 2016). Which
has been working in loss of data to analysis and make sure to manage different
sources for the growth to the company.
There are different measure activities and challenges which are needed to be measure and
work as per the society culture and arises in the market demand (Cyber security: What Every
CEO and CFO Should Know, 2021). Company has to adopt effective way and challenges to
promote effective sources and capabilities to promote and make effective challenges need in
the company.
To determine the various factor which may affect the cyber security technology in the chosen
company
According to the view point of Leclair, (2021);cyvber security is too often and measure for
the success of the companies. But at the same time there are different factor and growth are
have been considered to make effective factor and make a review on the company’s factor
which are directly affected through the cyber security issue and its technology in Facebook.
Theft of IP: In this high profile competitive world, it is considered that there are
many theft who are able to work and manage different sources and capabilities to
assign the task and increase efficiency for their attack. This has been used and
manage to make effective ecosystem and able to manage their cybercriminal to make
different sources.
Security of third Party vendor:If the third party get hacked and make company to
losing business data and make sure to work and compromising employee information.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

This will be helpful for the companies to make data breach in the company and
compromised different customer account and make third party to work on different
investigation of the third party contract (Lambaand et.al., 2016). It has been choosing
for the growth of company has been sure and make changes within company to work
and manage cyber security sources to applicable and make society to work and
analysis the growth and achievement of the company.
All of these issue and factor are basically related to different sector to grow by the major
changes. This will be related to different sector and make increased use of mobile
technologies by customer. With the use of major changes and make for the growth of the
company. This is all related to different factor and make affect the growth of cyber security
(The Top 5 Global Forces Affecting Cybersecurity and Cyber Policies Right Now, 2021).
Customer convenience are related to the different sources and make cyber security for the
growth of gap between companies which are basically related to awareness and their
readiness to work and manage in the last few years. All is related to the major changes and
factor of the cyber threat and phishing technique in the company to avoid major changes and
applicability in the growth and sector of major changes.
Research Methodology and Planning
Research methodology and planning is given by researcher to analysis to collect the
information in an ethical manner. This is the process which are used and manage by effective
strategies and helpful for the growth of company to collect the data and make sure to analysis
the objective on time. There are different process and strategies are used for understanding
the role and method of the researcher to complete and analysis the impact on study. Its layer
are explaining in detail:
Research approach: There are mainly two type of researches are used which are
included as deductive and inductive approaches. This research is helpful in conducting
deductive analysis as it will be helpful in analysing quantitative data and make analysis of the
data in an organised manner. As there are different ways to complete the research, deductive
method is used as researcher use positivism approach and make quantitative data of the
collection in an organised way. Inductive method of approach is used for analysing in more
detail and work for the qualitative data of collecting method (Leszczyna, 2018). This has
been used and manage as per the different sources in an organised way and collect the data
for understanding the need and management process of the company.
compromised different customer account and make third party to work on different
investigation of the third party contract (Lambaand et.al., 2016). It has been choosing
for the growth of company has been sure and make changes within company to work
and manage cyber security sources to applicable and make society to work and
analysis the growth and achievement of the company.
All of these issue and factor are basically related to different sector to grow by the major
changes. This will be related to different sector and make increased use of mobile
technologies by customer. With the use of major changes and make for the growth of the
company. This is all related to different factor and make affect the growth of cyber security
(The Top 5 Global Forces Affecting Cybersecurity and Cyber Policies Right Now, 2021).
Customer convenience are related to the different sources and make cyber security for the
growth of gap between companies which are basically related to awareness and their
readiness to work and manage in the last few years. All is related to the major changes and
factor of the cyber threat and phishing technique in the company to avoid major changes and
applicability in the growth and sector of major changes.
Research Methodology and Planning
Research methodology and planning is given by researcher to analysis to collect the
information in an ethical manner. This is the process which are used and manage by effective
strategies and helpful for the growth of company to collect the data and make sure to analysis
the objective on time. There are different process and strategies are used for understanding
the role and method of the researcher to complete and analysis the impact on study. Its layer
are explaining in detail:
Research approach: There are mainly two type of researches are used which are
included as deductive and inductive approaches. This research is helpful in conducting
deductive analysis as it will be helpful in analysing quantitative data and make analysis of the
data in an organised manner. As there are different ways to complete the research, deductive
method is used as researcher use positivism approach and make quantitative data of the
collection in an organised way. Inductive method of approach is used for analysing in more
detail and work for the qualitative data of collecting method (Leszczyna, 2018). This has
been used and manage as per the different sources in an organised way and collect the data
for understanding the need and management process of the company.

Research Strategies: This has to be considered that facilitating the information in
such manner that there are different strategies and applied sources are used for gathering the
information and make resourceful techniques. Questionnaire is used for making an integral
part of survey and make quantitative information to know more about the impact of
cybercrime and their impact on the chosen company (Yadav and et.al., 2016). One of the
main reason to choose this strategies is to make objective clear and authenticate for the
growth of the researcher and collect the data in a right way. These are helpful in analysing the
situation and make effective way to understand the concept and work for effective growth
and time period of the researcher. This is helpful in collecting more data information with
ease and analyses the data effectively.
Research Method:There are mainly two type of research method are used which
include quantitative and qualitative method. In the present research methodology, quantitative
method is used for understanding and organising the concept to gather the information and
make effective use of technologies to work on the cost and structure of high cost. Apart from
this, qualitative method is not helpful for this study as it will be manage and organised for the
large number of research and validate outcome (Lin, Wu and Lee, 2017). As this method take
lots of time and money and valuable for data reliable source within the chosen time limit of
the company.
Research Tools: This is one of the significant and important sector which are helpful
for the researcher to support the researcher and make needed outcome from the chosen topic
and objectives. There are different way and tools which are helpful for collecting and
analysing the data in an organised way. The different tools and method are questionnaire and
interview or survey. All are methods are included in primary sector and research while in
secondary research, research, Literature review and understanding of preview research are
included which are collected through many journals, data sources, previous research and
books. For this researcher has been developed a close-ended questionnaire that must be
supportive and valid for Woking in reliable data sources.
Sampling: This is the process which has been used by the researcher to make large
number of people and make conductive study for completion of the research. There are
mainly two type of method are used which include probability and non-probability method.
Here probability sampling method are used as it will be helpful for the company to collect
and analysis the data structure (Parasol, 2018). With the help of random sampling method 30
such manner that there are different strategies and applied sources are used for gathering the
information and make resourceful techniques. Questionnaire is used for making an integral
part of survey and make quantitative information to know more about the impact of
cybercrime and their impact on the chosen company (Yadav and et.al., 2016). One of the
main reason to choose this strategies is to make objective clear and authenticate for the
growth of the researcher and collect the data in a right way. These are helpful in analysing the
situation and make effective way to understand the concept and work for effective growth
and time period of the researcher. This is helpful in collecting more data information with
ease and analyses the data effectively.
Research Method:There are mainly two type of research method are used which
include quantitative and qualitative method. In the present research methodology, quantitative
method is used for understanding and organising the concept to gather the information and
make effective use of technologies to work on the cost and structure of high cost. Apart from
this, qualitative method is not helpful for this study as it will be manage and organised for the
large number of research and validate outcome (Lin, Wu and Lee, 2017). As this method take
lots of time and money and valuable for data reliable source within the chosen time limit of
the company.
Research Tools: This is one of the significant and important sector which are helpful
for the researcher to support the researcher and make needed outcome from the chosen topic
and objectives. There are different way and tools which are helpful for collecting and
analysing the data in an organised way. The different tools and method are questionnaire and
interview or survey. All are methods are included in primary sector and research while in
secondary research, research, Literature review and understanding of preview research are
included which are collected through many journals, data sources, previous research and
books. For this researcher has been developed a close-ended questionnaire that must be
supportive and valid for Woking in reliable data sources.
Sampling: This is the process which has been used by the researcher to make large
number of people and make conductive study for completion of the research. There are
mainly two type of method are used which include probability and non-probability method.
Here probability sampling method are used as it will be helpful for the company to collect
and analysis the data structure (Parasol, 2018). With the help of random sampling method 30
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


