Research Proposal: Roles of Victims in Cyberbullying Victimisation
VerifiedAdded on 2021/01/01
|14
|2485
|259
Project
AI Summary
This research proposal explores the multifaceted issue of cyberbullying victimisation, focusing on the roles of victims, social media's influence, and the subsequent mental health impacts on adolescents, particularly within the Malaysian context. The study outlines the research background, problem, definitions, aims, objectives, and hypotheses, establishing a clear framework for investigation. It delves into existing literature, examining the concept of cyberbullying, its effects on victims, and the role of social media in shaping perceptions. The theoretical framework incorporates the Victim Precipitation Theory and Routine Activity Theory to provide a criminological perspective. The methodology includes a cross-sectional design, quantitative methods, and a questionnaire-based approach to collect data from 100 Malaysian teenagers, considering ethical approval and data analysis techniques like T-tests and ANOVA. The research aims to understand the dynamics of cyberbullying victimisation, its causes, and its consequences on the victims, with the ultimate goal of contributing valuable insights to the field.

RESEARCH
PROPOSAL
PROPOSAL
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Topic : Understanding The Roles of Victims in Cyberbully Victimisation....................................3
CHAPTER 1 INTRODUCTION.....................................................................................................3
1.1 Research Background.......................................................................................................3
1.2 Research Problem.............................................................................................................3
1.3 Definition of terms...........................................................................................................4
1.3.1 Conceptual definition....................................................................................................4
1.3.2 Operational Definition...................................................................................................4
1.4 Aim and Objectives..........................................................................................................4
1.5 Hypothesis........................................................................................................................4
CHAPTER 2 LITERATURE REVIEW..........................................................................................5
2.1 Concept of cyber-bulling victimisation............................................................................5
2.2 Impact of cyber-bulling activities on victims...................................................................5
2.3 Social media activities which influenced perception of victims......................................5
2.4 Theoretical Framework....................................................................................................6
2.4.1 Victim Precipitation Theory..........................................................................................6
2.4.2 Routine Activity Theory................................................................................................6
CHAPTER 3 METHODOLOGY....................................................................................................6
3.1 Research Design...............................................................................................................6
3.2 Research Participants........................................................................................................7
3.2.1 Sampling frame, area.....................................................................................................7
3.2.3 Recruitment of participants- exclusion & inclusion criteria..........................................7
3.2.3 Sampling size.................................................................................................................7
3.3 Research instruments........................................................................................................7
3.4 Data Analysis....................................................................................................................7
3.5 Ethical Approval...............................................................................................................8
Topic : Understanding The Roles of Victims in Cyberbully Victimisation....................................3
CHAPTER 1 INTRODUCTION.....................................................................................................3
1.1 Research Background.......................................................................................................3
1.2 Research Problem.............................................................................................................3
1.3 Definition of terms...........................................................................................................4
1.3.1 Conceptual definition....................................................................................................4
1.3.2 Operational Definition...................................................................................................4
1.4 Aim and Objectives..........................................................................................................4
1.5 Hypothesis........................................................................................................................4
CHAPTER 2 LITERATURE REVIEW..........................................................................................5
2.1 Concept of cyber-bulling victimisation............................................................................5
2.2 Impact of cyber-bulling activities on victims...................................................................5
2.3 Social media activities which influenced perception of victims......................................5
2.4 Theoretical Framework....................................................................................................6
2.4.1 Victim Precipitation Theory..........................................................................................6
2.4.2 Routine Activity Theory................................................................................................6
CHAPTER 3 METHODOLOGY....................................................................................................6
3.1 Research Design...............................................................................................................6
3.2 Research Participants........................................................................................................7
3.2.1 Sampling frame, area.....................................................................................................7
3.2.3 Recruitment of participants- exclusion & inclusion criteria..........................................7
3.2.3 Sampling size.................................................................................................................7
3.3 Research instruments........................................................................................................7
3.4 Data Analysis....................................................................................................................7
3.5 Ethical Approval...............................................................................................................8

3.6 Significance of study........................................................................................................8
REFERENCES................................................................................................................................9
APPENDIX A (QUESTIONNAIRE) ...........................................................................................10
APPENDIX B (GANTT CHART) ...............................................................................................11
Appendix III (Consent form).........................................................................................................13
REFERENCES................................................................................................................................9
APPENDIX A (QUESTIONNAIRE) ...........................................................................................10
APPENDIX B (GANTT CHART) ...............................................................................................11
Appendix III (Consent form).........................................................................................................13
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Topic : Understanding The Roles of Victims in Cyberbully Victimisation
CHAPTER 1 INTRODUCTION
1.1 Research Background
Cyberbullying is considered as an aggressive and deliberate activity, which is carried out
through digital means. Here, Cybervictimisation in adolescence age is related to psychosocial
variables in negative manner, like loneliness, depressive and aggressive mood. As people
especially of young age, spend more time on social sites and eagerly seek to increase their
follower list, in order to gain popularity (Hood and Duffy, 2018). In this regard, population of
various countries including Malaysia are much affected due to cyberbullying activities.
1.2 Research Problem
Cyberbullying is created a huge impact on metal health and behavioural disparities of
Malaysian and people of other countries (Wachs, 2012). More than half of population, especially
of 11 to 19 years, belong to sexual minorities (eg. Lesbian, gay, bisexual), ethnic and racial one,
are becoming a cyberbully victim during last decades. The research is therefore, conducted to
establish a proof of cyber-bulling or victimisation experience.
1.3 Definition of terms
1.3.1 Conceptual definition
Cyberbully: This concept can be defined as usage of electronic media and other means
of digital communication like social network, instant messaging and other, to harass or do
personal attacks on individuals or a group of people.
Victimisation: It shows the relationship between victim and cyber crime as well as
process of being victimised.
Victims: Those individuals or group members, who have faced harassment and harm
including mental or physical injury, emotional distress and more through cyber-bulling activities.
1.3.2 Operational Definition
Cyberbully: In sociology terms, cyber-bullying can be defined as an electronic form of
bullying through face-to-face communication.
Victimisation: It is defined as form of harassment where individuals or group of people
treated badly through intentional and aggressive comments on social sites.
CHAPTER 1 INTRODUCTION
1.1 Research Background
Cyberbullying is considered as an aggressive and deliberate activity, which is carried out
through digital means. Here, Cybervictimisation in adolescence age is related to psychosocial
variables in negative manner, like loneliness, depressive and aggressive mood. As people
especially of young age, spend more time on social sites and eagerly seek to increase their
follower list, in order to gain popularity (Hood and Duffy, 2018). In this regard, population of
various countries including Malaysia are much affected due to cyberbullying activities.
1.2 Research Problem
Cyberbullying is created a huge impact on metal health and behavioural disparities of
Malaysian and people of other countries (Wachs, 2012). More than half of population, especially
of 11 to 19 years, belong to sexual minorities (eg. Lesbian, gay, bisexual), ethnic and racial one,
are becoming a cyberbully victim during last decades. The research is therefore, conducted to
establish a proof of cyber-bulling or victimisation experience.
1.3 Definition of terms
1.3.1 Conceptual definition
Cyberbully: This concept can be defined as usage of electronic media and other means
of digital communication like social network, instant messaging and other, to harass or do
personal attacks on individuals or a group of people.
Victimisation: It shows the relationship between victim and cyber crime as well as
process of being victimised.
Victims: Those individuals or group members, who have faced harassment and harm
including mental or physical injury, emotional distress and more through cyber-bulling activities.
1.3.2 Operational Definition
Cyberbully: In sociology terms, cyber-bullying can be defined as an electronic form of
bullying through face-to-face communication.
Victimisation: It is defined as form of harassment where individuals or group of people
treated badly through intentional and aggressive comments on social sites.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Victims: They are known as target of cyber-bulling victimisation who experienced
extreme level of anger, sadness, fear and powerlessness.
1.4 Aim and Objectives
Aim: “ To analyse the role of victims in cyber-bulling victimisation”. A research on
Malaysian population.
General Objectives:
To understand the role of victim in cyber-bulling victimisation
Specific Objectives:
To determine the concept of cyber-bullying victimisation
To identify who is real victim in society and their role in cyber-bulling victimisation
To determine social media activities that influenced perception of victims
1.5 Hypothesis
Null Hypothesis:
Drastic changes in social media networking and its huge amount of access, is considered
as main cause behind cyber-bulling victimisation.
Alternative Hypothesis:
Drastic changes in social media networking and its huge amount of access, is not
considered as main cause behind cyber-bulling victimisation.
CHAPTER 2 LITERATURE REVIEW
2.1 Concept of cyber-bulling victimisation
According to view point of Macháčková and et.al. (2013), cyber-bulling victimisation can
be defined as an intentional and aggressive act, which is materialised either by a group of people
or individual. This type of activity leads to cause and damage consequences even in childhood,
due to social anxiety and intentionally bullying by other users. Cyber-bulling is increasing
rapidly from last some decades due to emergence of information and communication
technologies.
2.2 Impact of cyber-bulling activities on victims
According to the article given by Graham Davey, it has ascertained that victimisation is a
significant factor that creates social anxiety (Rise of Cyber-victimisation, 2019). Adults have
founded with social anxiety disorder as they experienced teasing and bulling in their childhood,
extreme level of anger, sadness, fear and powerlessness.
1.4 Aim and Objectives
Aim: “ To analyse the role of victims in cyber-bulling victimisation”. A research on
Malaysian population.
General Objectives:
To understand the role of victim in cyber-bulling victimisation
Specific Objectives:
To determine the concept of cyber-bullying victimisation
To identify who is real victim in society and their role in cyber-bulling victimisation
To determine social media activities that influenced perception of victims
1.5 Hypothesis
Null Hypothesis:
Drastic changes in social media networking and its huge amount of access, is considered
as main cause behind cyber-bulling victimisation.
Alternative Hypothesis:
Drastic changes in social media networking and its huge amount of access, is not
considered as main cause behind cyber-bulling victimisation.
CHAPTER 2 LITERATURE REVIEW
2.1 Concept of cyber-bulling victimisation
According to view point of Macháčková and et.al. (2013), cyber-bulling victimisation can
be defined as an intentional and aggressive act, which is materialised either by a group of people
or individual. This type of activity leads to cause and damage consequences even in childhood,
due to social anxiety and intentionally bullying by other users. Cyber-bulling is increasing
rapidly from last some decades due to emergence of information and communication
technologies.
2.2 Impact of cyber-bulling activities on victims
According to the article given by Graham Davey, it has ascertained that victimisation is a
significant factor that creates social anxiety (Rise of Cyber-victimisation, 2019). Adults have
founded with social anxiety disorder as they experienced teasing and bulling in their childhood,

through social-media users. Today 92% of youngsters are becoming victim of cyber-bulling
victimisation that affect mental health and generate social anxiety disorder. Spending more time
on social media sites make them addicted to get comments and increase follower list. Teenagers
are also become peer-victimised in a traditional face-to-face context, due to growing evidence of
cyber-bulling activities, which leads to social anxiety.
2.3 Social media activities which influenced perception of victims
As per opinion of Balakrishnan (2015), it has evaluated that people who spend their time
on social media sites and other internet websites to make relationship with others, become addict
and influenced by online aggressive comments. Venues like Facebook, Instagram, comments,
forum posts and other features of target influenced nature of online exchange. Therefore, through
online exchange features, teenager become more offensive to upload their pics, videos and
comments on social media sites. In this regard, any negative comment create a huge impact on
minds of them and affect mental health and behaviour also in negative manner.
2.4 Theoretical Framework
2.4.1 Victim Precipitation Theory
This theory is firstly introduced by Wolfgang in 1968 that argued that victims can initiate
victimizer's behavioural. It briefly explains of how behaviour of an individual can contribute to
own victimization. It also known as criminology theory which mainly describes how interaction
of victims with an offender leads crime to being committed.
2.4.2 Routine Activity Theory
It is also known as life-exposure theory that introduced in 1979 by Cohen and Felson. It
is used to determine the generalised patterns of social activities, within a society. It provides a
perceptive on cyber crime that predicts the way economical and social conditions influences the
victimisation and crime rate.
CHAPTER 3 METHODOLOGY
In order to collect data to analyse the concept of cyber-bulling activities and role of
victim in the same, both primary and secondary sources are used. Here, under secondary sources,
literature review is done by analysing different views of professionals and researchers, by
accessing internet sites. While, under primary research, questionnaire method is used to identify
different pattern of victimisation or cyber-bulling activities.
victimisation that affect mental health and generate social anxiety disorder. Spending more time
on social media sites make them addicted to get comments and increase follower list. Teenagers
are also become peer-victimised in a traditional face-to-face context, due to growing evidence of
cyber-bulling activities, which leads to social anxiety.
2.3 Social media activities which influenced perception of victims
As per opinion of Balakrishnan (2015), it has evaluated that people who spend their time
on social media sites and other internet websites to make relationship with others, become addict
and influenced by online aggressive comments. Venues like Facebook, Instagram, comments,
forum posts and other features of target influenced nature of online exchange. Therefore, through
online exchange features, teenager become more offensive to upload their pics, videos and
comments on social media sites. In this regard, any negative comment create a huge impact on
minds of them and affect mental health and behaviour also in negative manner.
2.4 Theoretical Framework
2.4.1 Victim Precipitation Theory
This theory is firstly introduced by Wolfgang in 1968 that argued that victims can initiate
victimizer's behavioural. It briefly explains of how behaviour of an individual can contribute to
own victimization. It also known as criminology theory which mainly describes how interaction
of victims with an offender leads crime to being committed.
2.4.2 Routine Activity Theory
It is also known as life-exposure theory that introduced in 1979 by Cohen and Felson. It
is used to determine the generalised patterns of social activities, within a society. It provides a
perceptive on cyber crime that predicts the way economical and social conditions influences the
victimisation and crime rate.
CHAPTER 3 METHODOLOGY
In order to collect data to analyse the concept of cyber-bulling activities and role of
victim in the same, both primary and secondary sources are used. Here, under secondary sources,
literature review is done by analysing different views of professionals and researchers, by
accessing internet sites. While, under primary research, questionnaire method is used to identify
different pattern of victimisation or cyber-bulling activities.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3.1 Research Design
Cross sectional design: It can be defined as a type of descriptive epidemiologic study
within which is used to determine cause behind pertaining issues. Here, it describes
characteristics which exist in a community not relationship among causes and issues between
variables of research. This method also doesn't involve the manipulating variables and provide
data of what is happening in a current population.
Quantitative method: This method majorly focuses on collecting numerical data and
analysing the same to explain a particular issue. For this purpose, here researchers can use
statistical, mathematical and objectives measurements to analyse data, which is collected either
by questionnaire, survey or manipulation of existing data.
3.2 Research Participants
3.2.1 Sampling frame, area
It defines the procedures to select a sample from total population by using a variety of
sampling techniques. In this research, both exclusion and inclusion criteria are used to select
sample of 100 respondents from Malaysian teenagers.
3.2.3 Recruitment of participants- exclusion & inclusion criteria
For conducting an investigation, it is essential for researchers to recruit an adequate
number of participants from total population. Here, they can use various methods like inclusion
and exclusion criteria as per purpose of study. Inclusion and exclusion criteria defines the
eligibility of participants i.e. inclusion shows who is eligible and exclusion prohibits those who
doesn't possess certain criteria. Therefore, under present research, participants of age between 11
to 19 years are taken who are most active on social sites.
3.2.3 Sampling size
This study consists of 100 Malaysian volunteers that comprising 50 males and 50 females
in the age group of 11–19 years from the three minorities- sexual, racial and ethnic. This age
group is chosen because youngsters spend more time on social sites to gain popularity. Through
perception and conducted psychological studies on this sample, pattern of victimisation,
emotional intelligence and logistic hierarchical regression can be analysed.
Cross sectional design: It can be defined as a type of descriptive epidemiologic study
within which is used to determine cause behind pertaining issues. Here, it describes
characteristics which exist in a community not relationship among causes and issues between
variables of research. This method also doesn't involve the manipulating variables and provide
data of what is happening in a current population.
Quantitative method: This method majorly focuses on collecting numerical data and
analysing the same to explain a particular issue. For this purpose, here researchers can use
statistical, mathematical and objectives measurements to analyse data, which is collected either
by questionnaire, survey or manipulation of existing data.
3.2 Research Participants
3.2.1 Sampling frame, area
It defines the procedures to select a sample from total population by using a variety of
sampling techniques. In this research, both exclusion and inclusion criteria are used to select
sample of 100 respondents from Malaysian teenagers.
3.2.3 Recruitment of participants- exclusion & inclusion criteria
For conducting an investigation, it is essential for researchers to recruit an adequate
number of participants from total population. Here, they can use various methods like inclusion
and exclusion criteria as per purpose of study. Inclusion and exclusion criteria defines the
eligibility of participants i.e. inclusion shows who is eligible and exclusion prohibits those who
doesn't possess certain criteria. Therefore, under present research, participants of age between 11
to 19 years are taken who are most active on social sites.
3.2.3 Sampling size
This study consists of 100 Malaysian volunteers that comprising 50 males and 50 females
in the age group of 11–19 years from the three minorities- sexual, racial and ethnic. This age
group is chosen because youngsters spend more time on social sites to gain popularity. Through
perception and conducted psychological studies on this sample, pattern of victimisation,
emotional intelligence and logistic hierarchical regression can be analysed.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

3.3 Research instruments
To get feedback of Malaysian, open and closed ended questionnaire method is used
where, some questions are asked to them about cyber-bulling activities. Under this process,
questionnaire are mailed to selected respondents through digital technologies. The response rate
of respondents on such investigation is measured as near about 90%.
3.4 Data Analysis
The data collected by using questionnaire used will enter into a spreadsheet (Excel 2010,
Microsoft office) then further analyse through statistical analysis software i.e. IBM SPSS
Statistics. Here, T-test and analysis of variance (ANOVA) will also be used to compare the
average of data. Here, Significance of data is set at 0.05 level.
3.5 Ethical Approval
In order to conduct study in ethical manner and consider all issues which may impact on
outcomes, researchers have signed a consent form with selected respondents. This would help in
conducting research in appropriate and successful manner.
3.6 Significance of study
Today, cyber-bulling activities are increasing at high rate that majorly targets to young
people of age 11 to 19. They are treated badly through aggressive and intentional comments on
social sites which leads to develop social anxiety, fear, suicidal thoughts, under their mind. This
report mainly highlights the consequences faced by victims due to such bullshit i.e. cyber-bulling
activities.
To get feedback of Malaysian, open and closed ended questionnaire method is used
where, some questions are asked to them about cyber-bulling activities. Under this process,
questionnaire are mailed to selected respondents through digital technologies. The response rate
of respondents on such investigation is measured as near about 90%.
3.4 Data Analysis
The data collected by using questionnaire used will enter into a spreadsheet (Excel 2010,
Microsoft office) then further analyse through statistical analysis software i.e. IBM SPSS
Statistics. Here, T-test and analysis of variance (ANOVA) will also be used to compare the
average of data. Here, Significance of data is set at 0.05 level.
3.5 Ethical Approval
In order to conduct study in ethical manner and consider all issues which may impact on
outcomes, researchers have signed a consent form with selected respondents. This would help in
conducting research in appropriate and successful manner.
3.6 Significance of study
Today, cyber-bulling activities are increasing at high rate that majorly targets to young
people of age 11 to 19. They are treated badly through aggressive and intentional comments on
social sites which leads to develop social anxiety, fear, suicidal thoughts, under their mind. This
report mainly highlights the consequences faced by victims due to such bullshit i.e. cyber-bulling
activities.

REFERENCES
Books and Journals
Hood, M. and Duffy, A. L., 2018. Understanding the relationship between cyber-victimisation
and cyber-bullying on Social Network Sites: The role of moderating factors. Personality
and Individual Differences, 133, pp.103-108.
Macháčková, H. and et.al., 2013. Bystanders' support of cyberbullied schoolmates. Journal of
community & applied social psychology. 23(1). pp.25-36.
Wachs, S., 2012. Moral disengagement and emotional and social difficulties in bullying and
cyberbullying: Differences by participant role. Emotional and Behavioural
Difficulties. 17(3-4). pp.347-360.
Balakrishnan, V., 2015. Cyberbullying among young adults in Malaysia: The roles of gender,
age and Internet frequency. Computers in Human Behavior, 46, pp.149-157.
Online
Rise of Cyber-victimisation. 2019. [Online] Available Through
<https://www.psychologytoday.com/us/blog/why-we-worry/201711/the-rise-cyber-
victimization>.
Books and Journals
Hood, M. and Duffy, A. L., 2018. Understanding the relationship between cyber-victimisation
and cyber-bullying on Social Network Sites: The role of moderating factors. Personality
and Individual Differences, 133, pp.103-108.
Macháčková, H. and et.al., 2013. Bystanders' support of cyberbullied schoolmates. Journal of
community & applied social psychology. 23(1). pp.25-36.
Wachs, S., 2012. Moral disengagement and emotional and social difficulties in bullying and
cyberbullying: Differences by participant role. Emotional and Behavioural
Difficulties. 17(3-4). pp.347-360.
Balakrishnan, V., 2015. Cyberbullying among young adults in Malaysia: The roles of gender,
age and Internet frequency. Computers in Human Behavior, 46, pp.149-157.
Online
Rise of Cyber-victimisation. 2019. [Online] Available Through
<https://www.psychologytoday.com/us/blog/why-we-worry/201711/the-rise-cyber-
victimization>.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
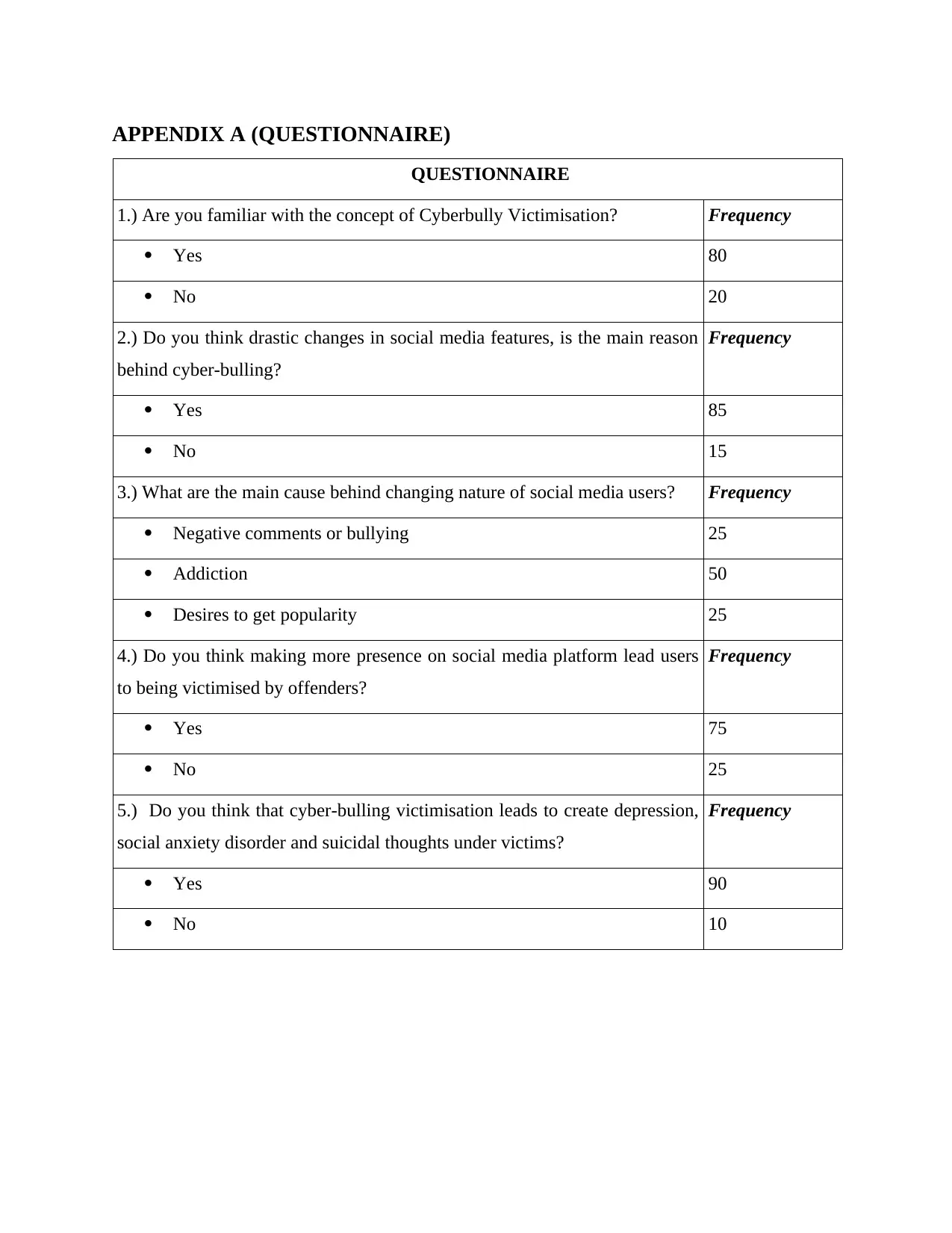
APPENDIX A (QUESTIONNAIRE)
QUESTIONNAIRE
1.) Are you familiar with the concept of Cyberbully Victimisation? Frequency
Yes 80
No 20
2.) Do you think drastic changes in social media features, is the main reason
behind cyber-bulling?
Frequency
Yes 85
No 15
3.) What are the main cause behind changing nature of social media users? Frequency
Negative comments or bullying 25
Addiction 50
Desires to get popularity 25
4.) Do you think making more presence on social media platform lead users
to being victimised by offenders?
Frequency
Yes 75
No 25
5.) Do you think that cyber-bulling victimisation leads to create depression,
social anxiety disorder and suicidal thoughts under victims?
Frequency
Yes 90
No 10
QUESTIONNAIRE
1.) Are you familiar with the concept of Cyberbully Victimisation? Frequency
Yes 80
No 20
2.) Do you think drastic changes in social media features, is the main reason
behind cyber-bulling?
Frequency
Yes 85
No 15
3.) What are the main cause behind changing nature of social media users? Frequency
Negative comments or bullying 25
Addiction 50
Desires to get popularity 25
4.) Do you think making more presence on social media platform lead users
to being victimised by offenders?
Frequency
Yes 75
No 25
5.) Do you think that cyber-bulling victimisation leads to create depression,
social anxiety disorder and suicidal thoughts under victims?
Frequency
Yes 90
No 10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
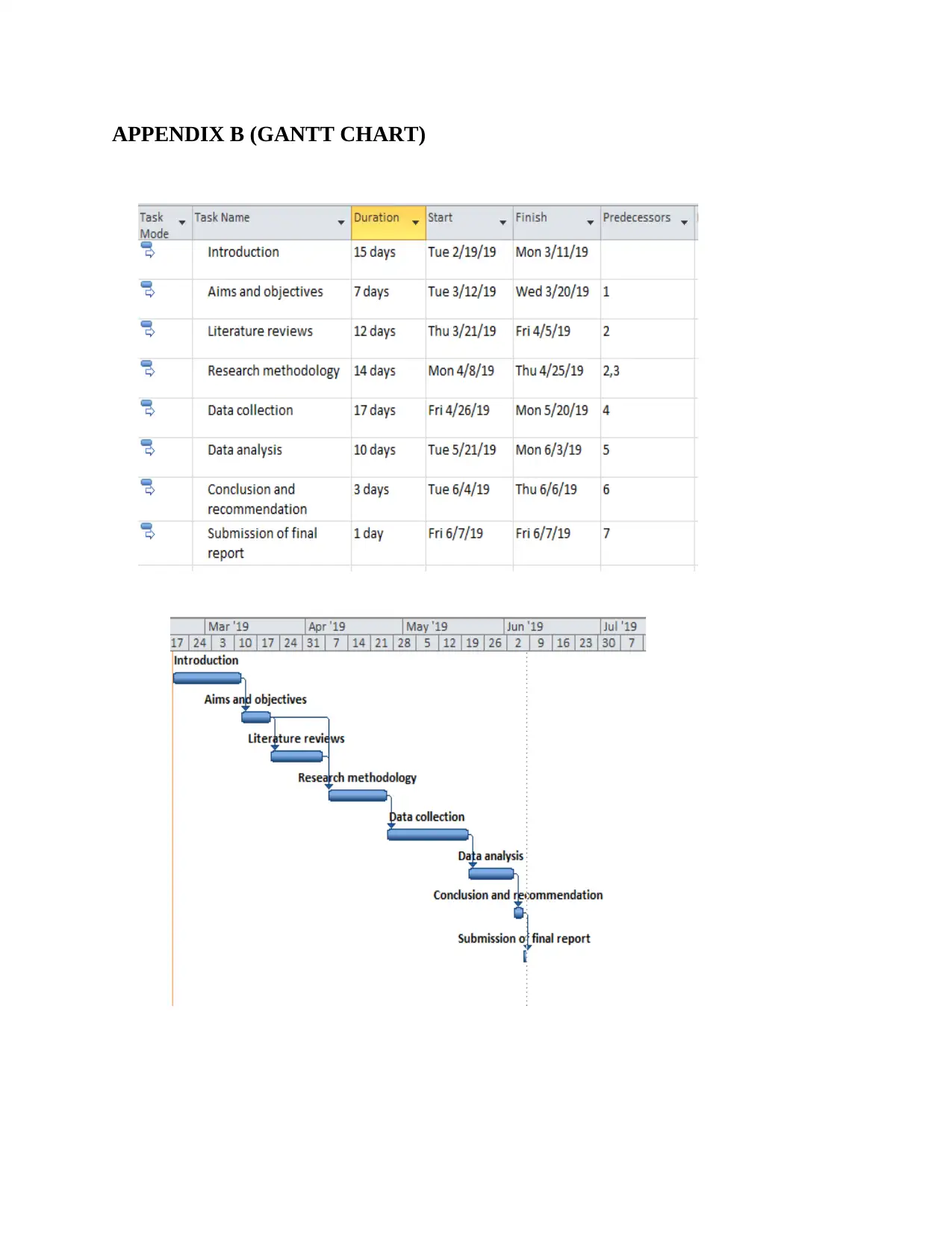
APPENDIX B (GANTT CHART)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





